Advanced Threat Prevention Detection Services
Advanced Threat Prevention is an intrusion prevention system (IPS) solution that can detect and block malware, vulnerability exploits, and command-and-control (C2) across all ports and protocols, using a multi-layered prevention system with components operating on the firewall and in the cloud. The Threat Prevention cloud operates a multitude of detection services using the combined threat data from Palo Alto Networks services to create signatures, each possessing specific identifiable patterns, and are used by the firewall to enforce security policies when matching threats and malicious behaviors are detected. These signatures are categorized based on the threat type and are assigned unique identifier numbers. To detect threats that correspond with these signatures, the firewall operates analysis engines that inspect and classify network traffic exhibiting anomalous traits.
In addition to the signature-based detection mechanism, Advanced Threat Prevention provides an inline detection system to prevent unknown and evasive C2 threats, including those produced through the Empire framework, as well as command injection, SQL injection vulnerabilities, and DNS relay threats. The Advanced Threat Prevention cloud operates extensible deep learning models that enable inline analysis capabilities on the firewall, on a per-request basis to prevent zero-day threats from entering the network as well as to distribute protections. This allows you to prevent unknown threats using real-time traffic inspection with inline detectors. These deep learning, ML-based detection engines in the Advanced Threat Prevention cloud analyze traffic for unknown C2 and vulnerabilities which utilize SQL injection and command injection to protect against zero-day threats. To provide a threat context and comprehensive detection details, reports are generated that can include the tools/techniques used by the attacker, the scope and impact of the detection, as well as the corresponding cyberattack classification as defined by the MITRE ATT&CK® framework.
MITRE ATT&CK® is a curated knowledge base and model for cyber adversary behavior. This work is reproduced and distributed with the permission of The MITRE Corporation. The MITRE Corporation (MITRE) hereby grants you a non-exclusive, royalty-free license to use ATT&CK® for research, development, and commercial purposes. Any copy you make for such purposes is authorized provided that you reproduce MITRE’s copyright designation and this license in any such copy.
By operating cloud-based detection engines, you can access a wide array of detection mechanisms that are updated and deployed automatically without requiring the user to download content packages or operate process intensive, firewall-based analyzers which consume resources. The cloud-based detection engine logic is continuously monitored and updated using C2 traffic datasets from WildFire, with additional support from Palo Alto Networks threat researchers who provide human intervention for highly accurized detection enhancements. Advanced Threat Prevention’s deep learning engines support analysis of C2-based threats over HTTP, HTTP2, SSL, unknown-UDP, and unknown-TCP applications. Additional analysis models are delivered through content updates, however, enhancements to existing models are performed as a cloud-side update, requiring no firewall update.
Advanced Threat Prevention also supports Local Deep Learning, which provides a mechanism to perform fast, local deep learning-based analysis of zero-day and other evasive threats, as a complementary feature to the cloud-based Inline Cloud Analysis component of Advanced Threat Prevention. Known malicious traffic that matches against Palo Alto Networks published signature set are dropped (or have another user-defined action applied to them); however, certain traffic that matches the criteria for suspicious content are rerouted for analysis using the Deep Leaning Analysis detection module. If further analysis is necessary, the traffic is sent to the Advanced Threat Prevention cloud for additional analysis, as well as the requisite false-positive and false-negative checks. The Deep Learning detection module is based on the proven detection modules operating in the Advanced Threat Prevention cloud, and as such, have the same zero-day and advanced threat detection capabilities. However, they also have the added advantage of processing a much higher volume of traffic, without the lag associated with cloud queries. This enables you to inspect more traffic and receive verdicts in a shorter span of time. This is especially beneficial when faced with challenging network conditions.
Palo Alto Networks also offers the Threat Prevention subscription that does not include the features found in the cloud-based Advanced Threat Prevention license.
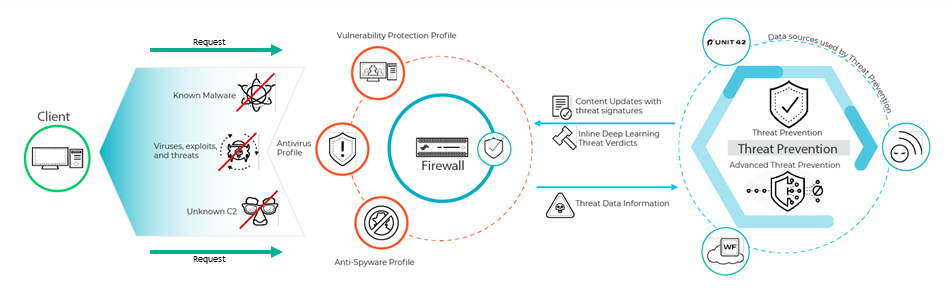
The threat signatures used by the firewall are broadly categorized into three types: antivirus, anti-spyware, vulnerability and are used by the corresponding security profiles to enforce user-defined policies.
Palo Alto Networks cloud-delivered security services also generate WildFire and DNS C2 signatures for their respective services, as well as file-format signatures, which can designate file types in lieu of threat signatures; for example, as signature exceptions.
- Antivirus signatures detect various types of malware and viruses, including worms, trojans, and spyware downloads.
- Anti-Spyware signatures detect C2 spyware on compromised hosts from trying to phone-home or beacon out to an external C2 server.
- Vulnerability signatures detect exploit system vulnerabilities.
Signatures have a default severity level with an associated default action; for example, in the case of a highly malicious threat, the default action is Reset Both. This setting is based on security recommendations from Palo Alto Networks.
In deployments where specialized internal applications are present or in cases where third-party intelligence feeds using open-source Snort and Suricata rules, custom signatures can be created for purpose-built protection.
Firewalls receive signature updates in the form of two update packages : the daily Antivirus Content and weekly Application and Threats Content updates. The antivirus content updates include antivirus signatures and DNS (C2) signatures used by antivirus and anti-spyware security profiles, respectively. Content updates for applications and threats include vulnerability and anti-spyware signatures, used by the vulnerability and anti-spyware security profiles, respectively. The update packages also include additional content leveraged by other services and sub-functions. For more information, refer to Dynamic Content Updates .
Threat Signature Categories
There are three types of Palo Alto Networks threat signatures, each designed to detect different types of threats as the network traffic is scanned:
- Antivirus signatures—Detect viruses and malware found in executables and file types.
- Anti-spyware signatures—Detects command-and-control (C2) activity, where spyware on an infected client is collecting data without the user's consent and/or communicating with a remote attacker.
- Vulnerability signatures—Detects system flaws that an attacker might otherwise attempt to exploit.
A signature's severity indicates the risk of the detected event, and a signature's default action (for example, block or alert) is how Palo Alto Networks recommends that you enforce matching traffic.
You must Set Up Antivirus, Anti-Spyware, and Vulnerability Protection to define what action to take when a threat is detected, and you can easily use the default security profiles to start blocking threats based on Palo Alto Networks recommendations. For each signature type, category, and even specific signatures you can continue to modify or create new profiles to more granularly enforce potential threats.
The following table lists all possible signature categories by type—Antivirus, Spyware, and Vulnerability—and includes the content update (Applications and Threats, Antivirus, or WildFire) that provides the signatures in each category. You can also go to the Palo Alto Networks Threat Vault to Learn More About Threat Signatures .
|
Threat Category |
Content Update that Provides These Signatures |
Description |
|
Antivirus Signatures |
||
|
apk |
Antivirus WildFire |
Malicious Android Application (APK) files. |
|
MacOSX |
Antivirus WildFire |
Malicious MacOSX files, including:
|
|
flash |
Antivirus Wildfire or WildFire Private |
Adobe Flash applets and Flash content embedded in web pages. |
|
jar |
Antivirus Wildfire |
Java applets (JAR/class file types). |
|
ms-office |
Antivirus Wildfire or WildFire Private |
Microsoft Office files, including documents (DOC, DOCX, RTF), workbooks (XLS, XLSX), and PowerPoint presentations (PPT, PPTX). This also includes Office Open XML (OOXML) 2007+ documents. |
|
|
Antivirus Wildfire or WildFire Private |
Portable Document Format (PDF) files. |
|
pe |
Antivirus Wildfire or WildFire Private |
Portable executable (PE) files can automatically execute on a Microsoft Windows system and should be only allowed when authorized. These files types include:
|
|
linux |
Antivirus Wildfire |
Executable and Linkable Format (ELF) files. |
|
archive |
Antivirus Wildfire |
Roshal Archive (RAR) and 7-Zip (7z) archive files. |
|
Spyware Signatures |
||
|
adware |
Applications and Threats |
Detects programs that display potentially unwanted advertisements. Some adware modifies browsers to highlight and hyperlink the most frequently searched keywords on web pages-these links redirect users to advertising websites. Adware can also retrieve updates from a command-and-control (C2) server and install those updates in a browser or onto a client system. Newly-released protections in this category are rare. |
|
autogen |
Antivirus |
These payload-based signatures detect command-and-control (C2) traffic and are automatically-generated. Importantly, autogen signatures can detect C2 traffic even when the C2 host is unknown or changes rapidly. |
|
backdoor |
Applications and Threats |
Detects a program that allows an attacker to gain unauthorized remote access to a system. |
|
botnet |
Applications and Threats |
Indicates botnet activity. A botnet is a network of malware-infected computers (“bots”) that an attacker controls. The attacker can centrally command every computer in a botnet to simultaneously carry out a coordinated action (like launching a DoS attack, for example). |
|
browser-hijack |
Applications and Threats |
Detects a plugin or software that is modifying browser settings. A browser hijacker might take over auto search or track users’ web activity and send this information to a C2 server. Newly-released protections in this category are rare. |
|
cryptominer |
Applications and Threats |
(Sometimes known as cryptojacking or miners) Detects the download attempt or network traffic generated from malicious programs designed to use computing resources to mine cryptocurrencies without the user's knowledge. Cryptominer binaries are frequently delivered by a shell script downloader that attempts to determine system architecture and kill other miner processes on the system. Some miners execute within other processes, such as a web browser rendering a malicious web page. |
|
data-theft |
Applications and Threats |
Detects a system sending information to a known C2 server. Newly-released protections in this category are rare. |
|
dns |
Antivirus |
Detects DNS requests to connect to malicious domains. dns and dns-wildfire signatures detect the same malicious domains; however, dns signatures are included in the daily Antivirus content update and dns-wildfire signatures are included in the WildFire updates that release protections every 5 minutes. |
|
dns-security |
Antivirus |
Detects DNS requests to connect to malicious domains. dns-security includes signatures from dns and dns-wildfire in addition to the unique signatures generated by the DNS Security service. |
|
dns-wildfire |
Wildfire or WildFire Private |
Detects DNS requests to connect to malicious domains. dns and dns-wildfire signatures detect the same malicious domains; however, dns signatures are included in the daily Antivirus content update and dns-wildfire signatures are included in the WildFire updates that release protections every 5 minutes. |
|
downloader |
Applications and Threats |
(Also known as droppers, stagers, or loaders) Detects programs that use an internet connection to connect to a remote server to download and execute malware on the compromised system. The most common use case is for a downloader to be deployed as the culmination of stage one of a cyber attack, where the downloader’s fetched payload execution is considered second stage . Shell scripts (Bash, PowerShell, etc.), trojans, and malicious lure documents (also known as maldocs) such as PDFs and Word files are common downloader types. |
|
fraud |
Applications and Threats |
(Including form-jacking, phishing, and scams) Detects access to compromised websites that have been determined to be injected with malicious JavaScript code to collect sensitive user information. (for example, Name, address, email, credit card number, CVV, expiration date) from payment forms that are captured on the checkout pages of e-commerce websites. |
|
hacktool |
Applications and Threats |
Detects traffic generated by software tools that are used by malicious actors to conduct reconnaissance, attack or gain access to vulnerable systems, exfiltrate data, or create a command and control channel to surreptitiously control a computer system without authorization. These programs are strongly associated with malware and cyber attacks. Hacking tools might be deployed in a benign manner when used in Red and Blue Team operations, penetration tests, and R&D. The use or possession of these tools may be illegal in some countries, regardless of intent. |
|
keylogger |
Applications and Threats |
Detects programs that allow attackers to secretly track user activity, by logging keystrokes and capturing screenshots. Keyloggers use various C2 methods to periodically sends logs and reports to a predefined e-mail address or a C2 server. Through keylogger surveillance, an attacker could retrieve credentials that would enable network access. |
|
networm |
Applications and Threats |
Detects a program that self-replicates and spreads from system to system. Net-worms might use shared resources or leverage security failures to access target systems. |
|
phishing-kit |
Applications and Threats |
Detects when a user attempts to connect to a phishing kit landing page (likely after receiving an email with a link to the malicious site). A phishing website tricks users into submitting credentials that an attacker can steal to gain access to the network. In addition to blocking access to phishing kit landing pages, enable Multi-Factor Authentication and Prevent Credential Phishing to prevent phishing attacks at all stages. |
|
post-exploitation |
Applications and Threats |
Detects activity that indicates the post-exploitation phase of an attack, where an attacker attempts to assess the value of a compromised system. This might include evaluating the sensitivity of the data stored on the system, and the system’s usefulness in further compromising the network. |
|
webshell |
Applications and Threats |
Detects web shells and web shell traffic, including implant detection and command and control interaction. Web shells must first be implanted by a malicious actor onto the compromised host, most often targeting a web server or framework. Subsequent communication with the web shell file frequently enables a malicious actor to establish a foothold in the system, conduct service and network enumeration, data exfiltration, and remote code execution in the context of the web server user. The most common web shell types are PHP, .NET, and Perl markup scripts. Attackers can also use web shell-infected web servers (the web servers can be both internet-facing or internal systems) to target other internal systems. |
|
spyware |
Applications and Threats |
Detect outbound C2 communication. These signatures are either auto-generated or are manually created by Palo Alto Networks researchers. Spyware and autogen signatures both detect outbound C2 communication; however, autogen signatures are payload-based and can uniquely detect C2 communications with C2 hosts that are unknown or change rapidly. |
|
Vulnerability Signatures |
||
|
brute force |
Applications and Threats |
A brute-force signature detects multiple occurrences of a condition in a particular time frame. While the activity in isolation might be benign, the brute-force signature indicates that the frequency and rate at which the activity occurred is suspect. For example, a single FTP login failure does not indicate malicious activity. However, many failed FTP logins in a short period likely indicate an attacker attempting password combinations to access an FTP server. You can tune the action and trigger conditions for brute force signatures. |
|
code execution |
Applications and Threats |
Detects a code execution vulnerability that an attacker can leverage to run code on a system with the privileges of the logged-in user. |
|
code-obfuscation |
Applications and Threats |
Detects code that has been transformed to conceal certain data while retaining its function. Obfuscated code is difficult or impossible to read, so it’s not apparent what commands the code is executing or with which programs its designed to interact. Most commonly, malicious actors obfuscate code to conceal malware. More rarely, legitimate developers might obfuscate code to protect privacy, intellectual property, or to improve user experience. For example, certain types of obfuscation (like minification) reduce file size, which decreases website load times and bandwidth usage. |
|
dos |
Applications and Threats |
Detects a denial-of-service (DoS) attack, where an attacker attempts to render a targeted system unavailable, temporarily disrupting the system and dependent applications and services. To perform a DoS attack, an attacker might flood a targeted system with traffic or send information that causes it to fail. DoS attacks deprive legitimate users (like employees, members, and account holders) of the service or resource to which they expect access. |
|
exploit-kit |
Applications and Threats |
Detects an exploit kit landing page. Exploit kit landing pages often contain several exploits that target one or many common vulnerabilities and exposures (CVEs), for multiple browsers and plugins. Because the targeted CVEs change quickly, exploit-kit signatures trigger based on the exploit kit landing page, and not the CVEs. When a user visits a website with an exploit kit, the exploit kit scans for the targeted CVEs and attempts to silently deliver a malicious payload to the victim’s computer. |
|
info-leak |
Applications and Threats |
Detects a software vulnerability that an attacker could exploit to steal sensitive or proprietary information. Often, an info-leak might exist because comprehensive checks do not exist to guard the data, and attackers can exploit info-leaks by sending crafted requests. |
|
insecure-credentials |
Applications and Threats |
Detects the use of weak, compromised, and manufacturer default passwords for software, network appliances, and IoT devices. |
|
overflow |
Applications and Threats |
Detects an overflow vulnerability, where a lack of proper checks on requests could be exploited by an attacker. A successful attack could lead to remote code execution with the privileges of the application, server or operating system. |
|
phishing |
Applications and Threats |
Detects when a user attempts to connect to a phishing kit landing page (likely after receiving an email with a link to the malicious site). A phishing website tricks users into submitting credentials that an attacker can steal to gain access to the network. In addition to blocking access to phishing kit landing pages, enable Multi-Factor Authentication and Prevent Credential Phishing to prevent phishing attacks at all stages. |
|
protocol-anomaly |
Applications and Threats |
Detects protocol anomalies, where a protocol behavior deviates from standard and compliant usage. For example, a malformed packet, poorly-written application, or an application running on a non-standard port would all be considered protocol anomalies, and could be used as evasion tools. It is a best practice to block protocol anomalies of any severity. |
|
sql-injection |
Applications and Threats |
Detects a common hacking technique where an attacker inserts SQL queries into an application’s requests, in order to read from or modify a database. This type of technique is often used on websites that do not comprehensively sanitize user input. |
Best Practices for Securing Your Network from Layer 4 and Layer 7 Evasions
To monitor and protect your network from most Layer 4 and Layer 7 attacks, here are a few recommendations.
- Upgrade to the most current PAN-OS software version and content release version to ensure that you have the latest security updates. See Install Content and Software Updates .
- Enable DNS Security (requires a Threat Prevention and DNS Security subscription license) to sinkhole malicious DNS requests. Palo Alto Networks recommends using the following DNS Security category configuration settings in your Anti-Spyware profile:
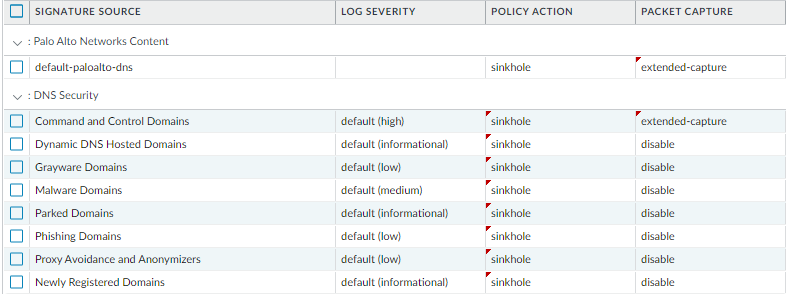
- For the log severity settings, use the default settings:
- For the policy action, set all signature sources to sinkhole .
- For packet capture, set Command and Control Domains to extended-capture . Leave all other categories to default settings.
For more information on related anti-spyware settings, see Best Practice Internet Gateway Anti-Spyware Profile .
- If you have an active Advanced Threat Prevention subscription, enable Inline Cloud Analysis and Local Deep Learning , where available, to block advanced C2 and spyware threats in real-time. The default action for each analysis engine is alert , which generates a threat log when a corresponding threat is detected; however, Palo Alto Networks recommends setting all analysis model actions to Reset-Both . This drops matching packets and sends an RST to the client and server, breaking the connection, as well as generating a threat log entry.
- Set up the firewall to act as a DNS proxy and enable evasion signatures:
DNS proxy is not part of the firewall security policy engine; instead, it directs the firewall to resolve DNS hostnames, while maintaining domain to IP mapping, which is crucial for preventing TLS/HTTP evasion.
When acting as a DNS proxy, the firewall resolves DNS requests and caches hostname-to-IP address mappings to quickly and efficiently resolve future DNS queries.
Evasion signatures that detect crafted HTTP or TLS requests can send alerts when clients connect to a domain other than the domain specified in the original DNS request. Make sure to configure DNS proxy before you enable evasion signatures. Without DNS proxy, evasion signatures can trigger alerts when a DNS server in the DNS load balancing configuration returns different IP addresses—for servers hosting identical resources—to the firewall and client in response to the same DNS request.
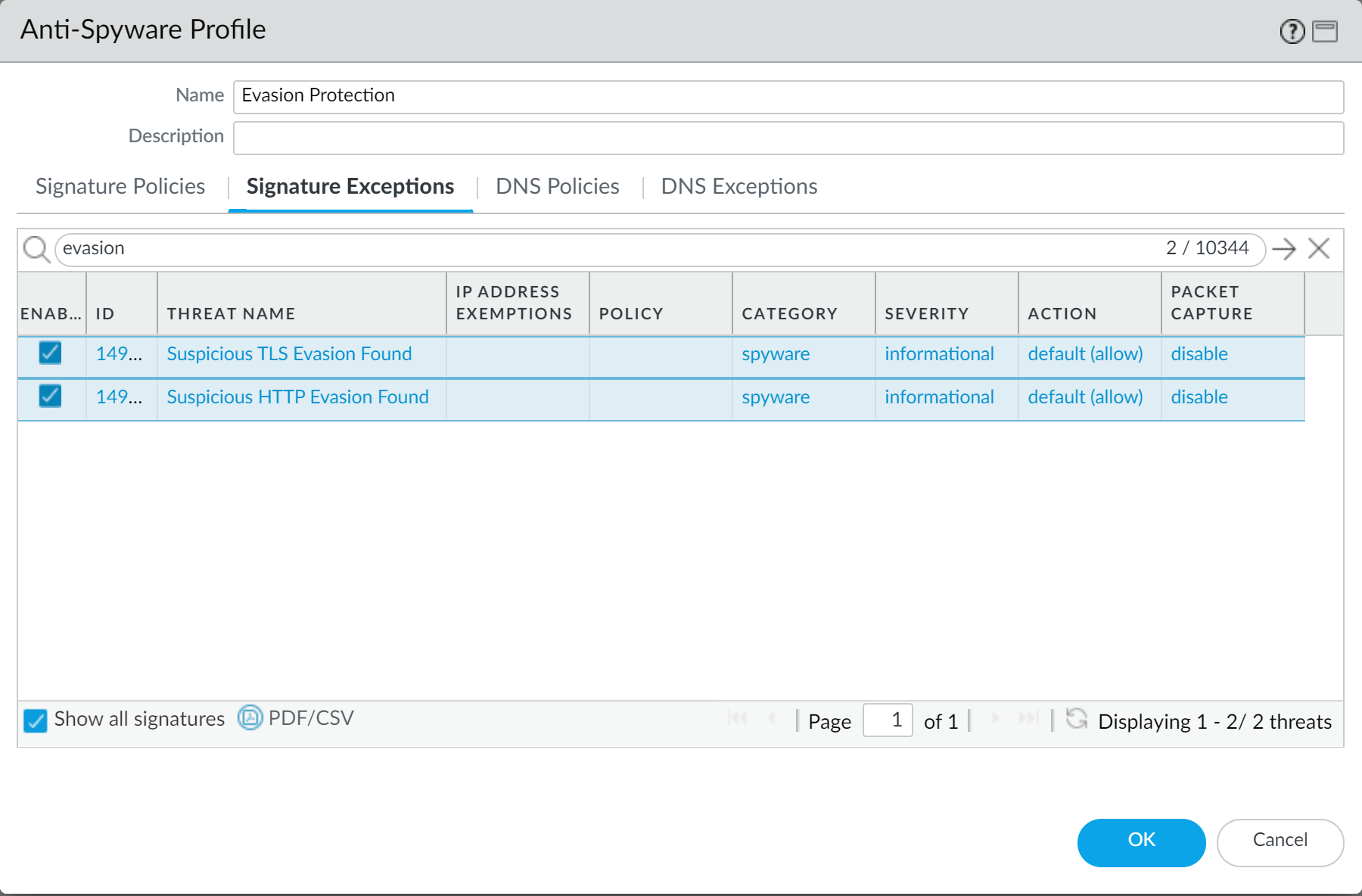
- For deployments operating Prisma Access or networks without an internal DNS server, configure your DNS policy to use the Palo Alto Networks sinkhole IP address (72.5.65.111) instead of the default sinkhole FQDN (sinkhole.paloaltonetworks.com).
The DNS sinkhole used by the Anti-Spyware Profile enables the firewall to forge a response to a DNS query for domains that match the category configured for a sinkhole action to the specified sinkhole server, to assist in identifying compromised hosts. When the default sinkhole FQDN is used, the firewall sends the CNAME record as a response to the client, with the expectation that an internal DNS server will resolve the CNAME record, allowing malicious communications from the client to the configured sinkhole server to be logged and readily identifiable. However, if clients are operating Prisma Access, are in networks without an internal DNS server, or using other software or tools that cannot be properly resolve a CNAME into an A record response, the DNS request is dropped, resulting in incomplete traffic log details that are crucial for threat analysis.
- For servers, create Security policy rules to allow only the application(s) that you sanction on each server. Verify that the standard port for the application matches the listening port on the server. For example, to ensure that only SMTP traffic is allowed to your email server, set the Application to smtp and set the Service to application-default . If your server uses only a subset of the standard ports (for example, if your SMTP server uses only port 587 while the SMTP application has standard ports defined as 25 and 587), create a new custom service that includes only port 587 and use that new service in your security policy rule instead of application-default. Additionally, make sure you restrict access to specific source and destinations zones and sets of IP addresses.
- Block all unknown applications and traffic using the Security policy. Typically, the only applications classified as unknown traffic are internal or custom applications on your network and potential threats. Unknown traffic can be either non-compliant applications or protocols that are anomalous or abnormal or it can be known applications that are using non-standard ports, both of which should be blocked. See Manage Custom or Unknown Applications .
- Set Up File Blocking to block Portable Executable (PE) file types for internet-based SMB (Server Message Block) traffic from traversing trust to untrust zones (ms-ds-smb applications).
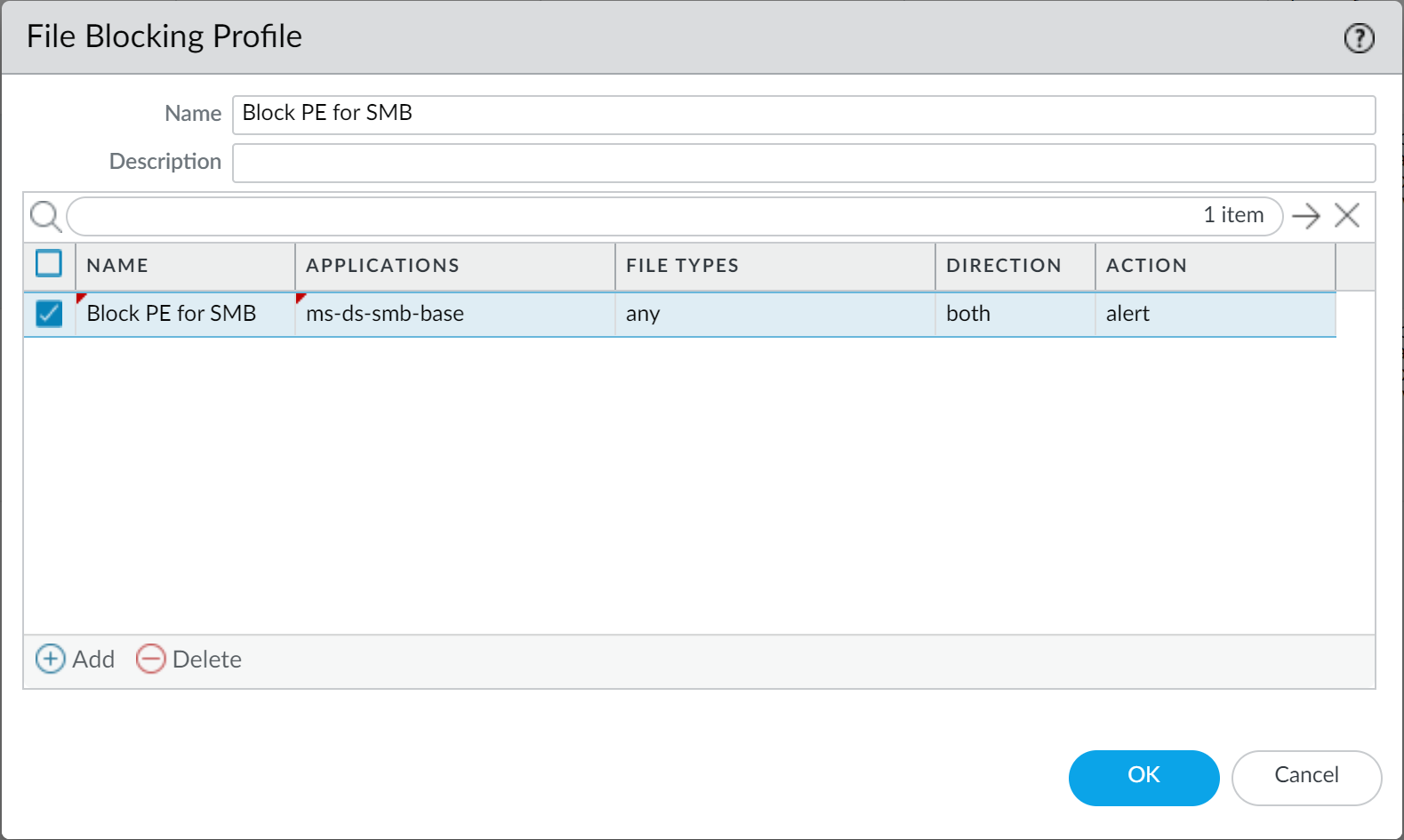
- Block malicious variants of PE (portable executables), ELF and MS Office files, and PowerShell and shell scripts in real-time. Enabling WildFire Inline ML allows you to dynamically analyze files using machine learning on the firewall. This additional layer of antivirus protection complements the WildFire-based signatures to provide extended coverage for files of which signatures do not already exist.
- Create a Zone Protection profile that is configured to protect against packet-based attacks ( NetworkNetwork ProfilesZone Protection ):
- Select the option to drop Malformed IP packets ( Packet Based Attack ProtectionIP Drop ).
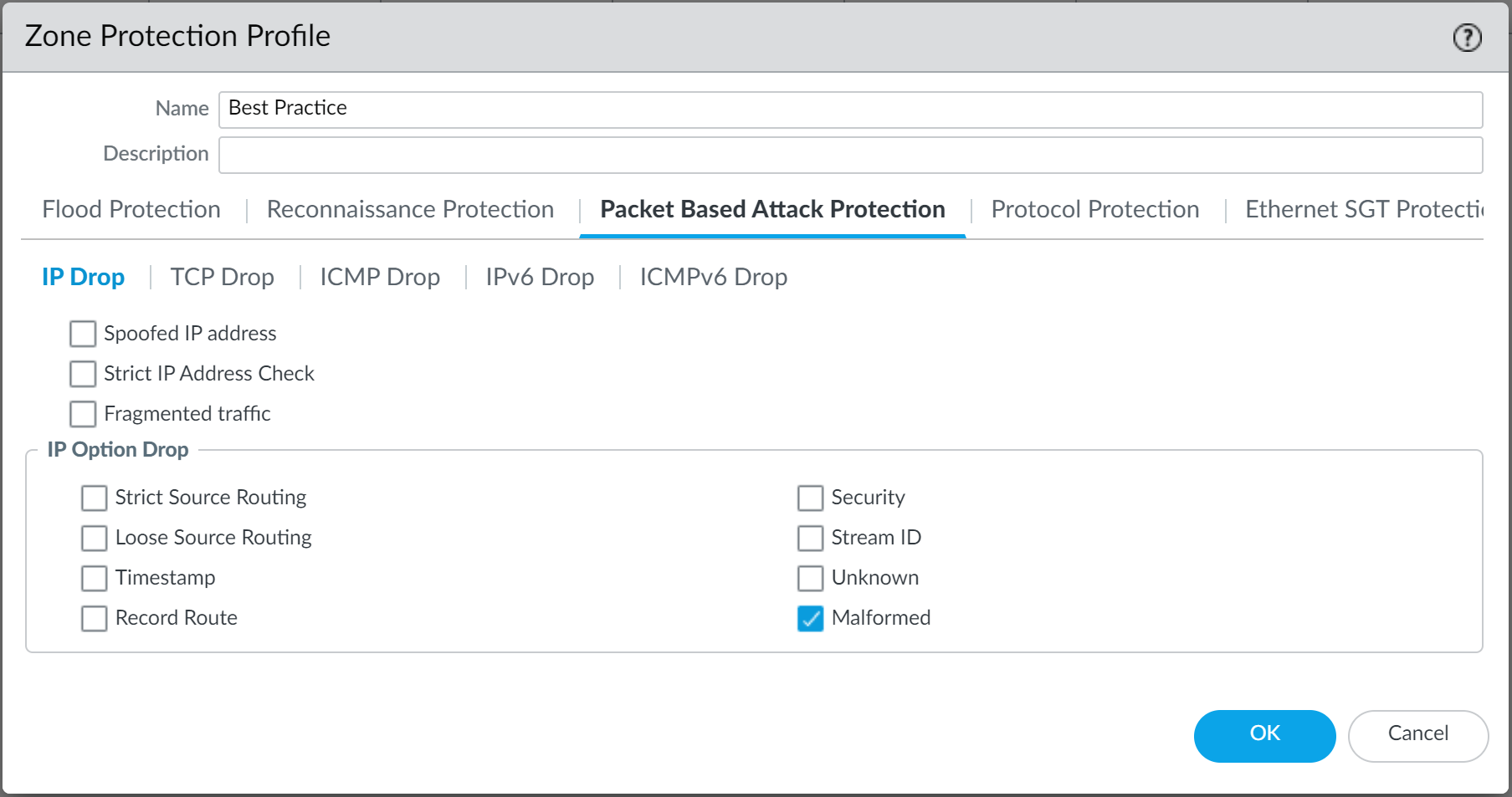
- Enable the drop Mismatched overlapping TCP segment option ( Packet Based Attack ProtectionTCP Drop ).
By deliberately constructing connections with overlapping but different data in them, attackers attempt to cause misinterpretation of the intent of the connection and deliberately induce false positives or false negatives. Attackers also use IP spoofing and sequence number prediction to intercept a user's connection and inject their own data into that connection. Selecting the Mismatched overlapping TCP segment option specifies that PAN-OS discards frames with mismatched and overlapping data. Received segments are discarded when they are contained within another segment, when they overlap with part of another segment, or when they contain another complete segment.
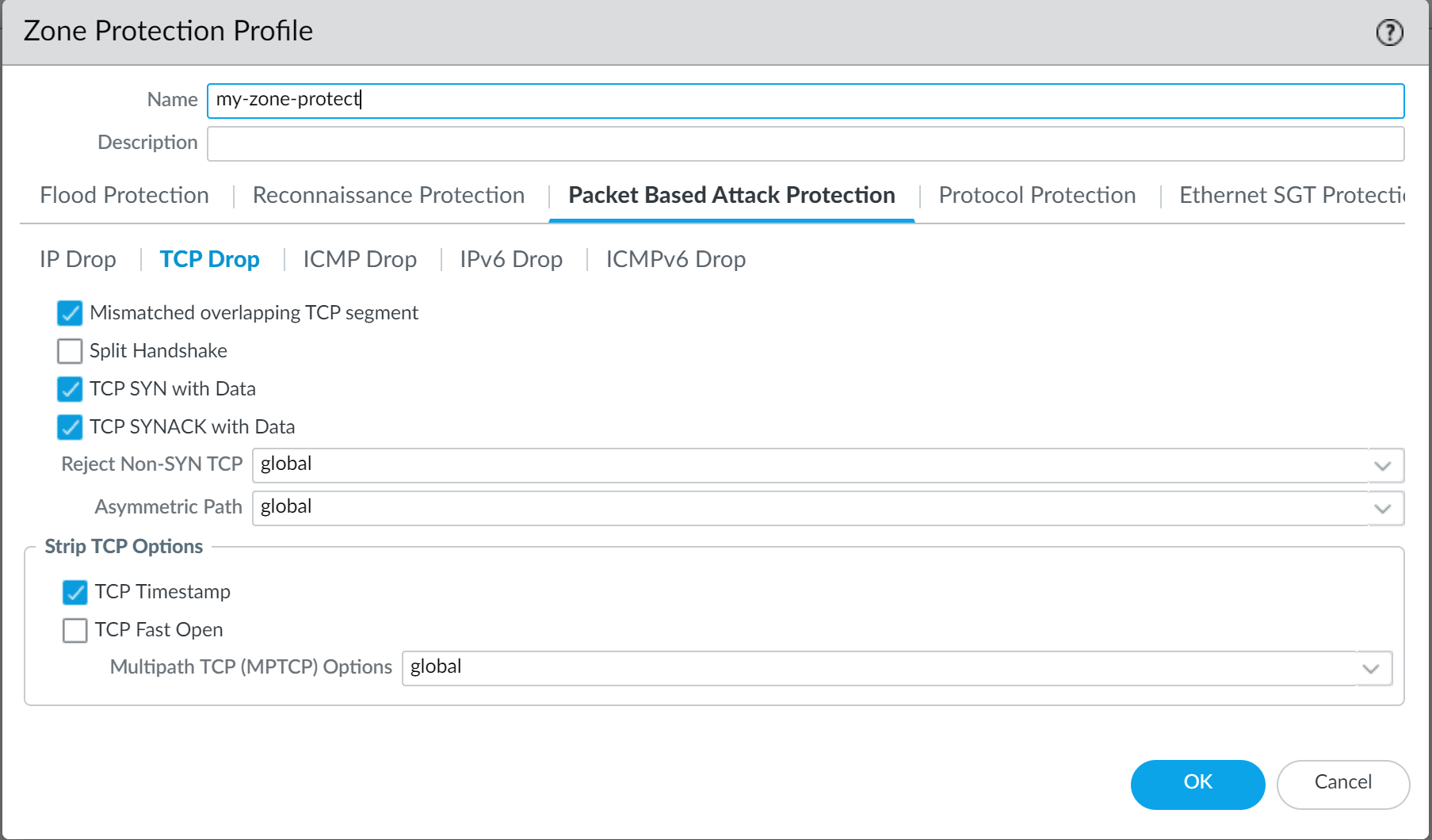
- Enable the drop TCP SYN with Data and drop TCP SYNACK with Data options ( Packet Based Attack ProtectionTCP Drop ).
Dropping SYN and SYN-ACK packets that contain data in the payload during a three-way handshake increases security by blocking malware contained in the payload and preventing it from extracting unauthorized data before the TCP handshake is completed.
- Strip TCP timestamps from SYN packets before the firewall forwards the packet ( Packet Based Attack ProtectionTCP Drop ).
When you enable the Strip TCP Options - TCP Timestamp option, the TCP stack on both ends of the TCP connection will not support TCP timestamps. This prevents attacks that use different timestamps on multiple packets for the same sequence number.
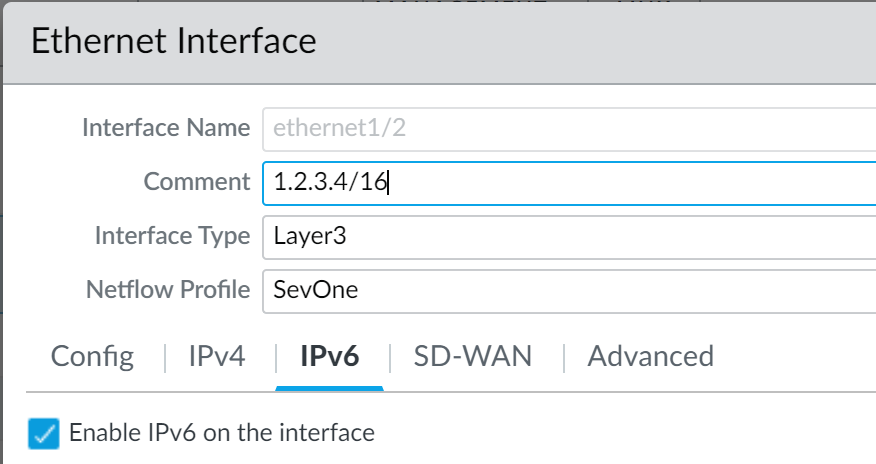
- If you configure IPv6 addresses on your network hosts, be sure to enable support for IPv6 if not already enabled ( NetworkInterfacesEthernet > IPv6 ).
Enabling support for IPv6 allows access to IPv6 hosts and also filters IPv6 packets encapsulated in IPv4 packets, which prevents IPv6 over IPv4 multicast addresses from being leveraged for network reconnaissance.
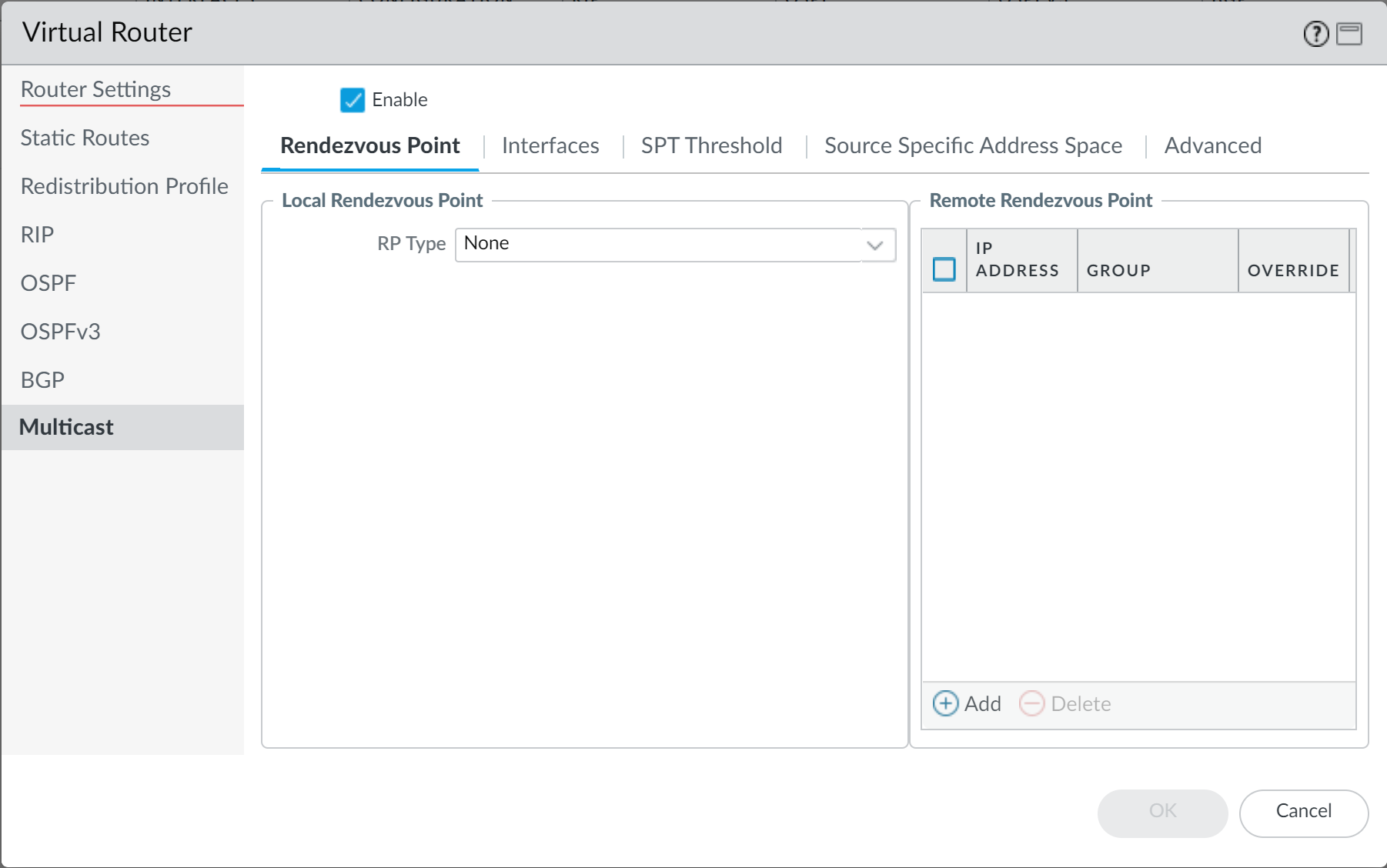
- Enable support for multicast traffic so that the firewall can enforce policy on multicast traffic ( NetworkVirtual RouterMulticast ).
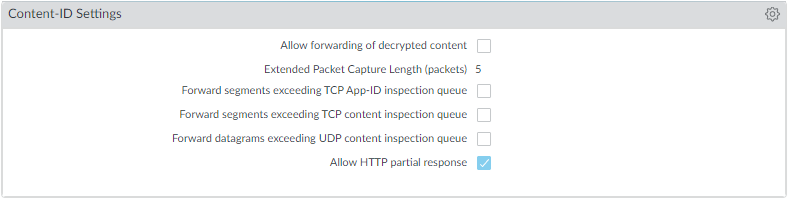
- Disable the options to Forward datagrams exceeding UDP content inspection queue and Forward segments exceeding TCP content inspection queue ( DeviceSetupContent-IDContent-ID Settings ).
By default, when the TCP or UDP content inspection queues are full, the firewall skips content inspection for TCP segments or UDP datagrams that exceed the queue limit of 64. Disabling this option ensures content inspection for all TCP and UDP datagrams that the firewall allows. Only under specific circumstances—for example, if the firewall platform is not sized appropriately to align with a use case—could disabling this setting impact performance.
- Disable the Allow HTTP partial response ( DeviceSetupContent-IDContent-ID Settings ).
The HTTP partial response option allows a client to fetch only part of a file. When a next-generation firewall in the path of a transfer identifies and drops a malicious file, it terminates the TCP session with an RST packet. If the web browser implements the HTTP header range option, it can start a new session to fetch only the remaining part of the file, which prevents the firewall from triggering the same signature again due to the lack of context into the initial session and, at the same time, allows the web browser to reassemble the file and deliver the malicious content. Disabling this option prevents this from happening.
Allow HTTP partial response is enabled on the firewall by default. This provides maximum availability but increases the risk of a successful cyberattack. For maximum security, disable this option to prevent the web browser from starting a new session to fetch the rest of a file after the firewall terminates the original session due to malicious activity. Disabling HTTP partial response affects HTTP-based data transfers which use the RANGE header, which may cause service anomalies for certain applications. After you disable HTTP partial response, validate the operation of your business-critical applications.
If you experience HTTP data transfer disruption on a business-critical application, you can create an Application Override policy for that specific application. Because Application Override bypasses App-ID (including threat and content inspection), create an Application Override policy for only the specific business-critical application, and specify sources and destinations to limit the rule (principle of least privilege access). Do not create Application Override policy unless you must. For information about Application Override policies, refer to https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVLCA0 .
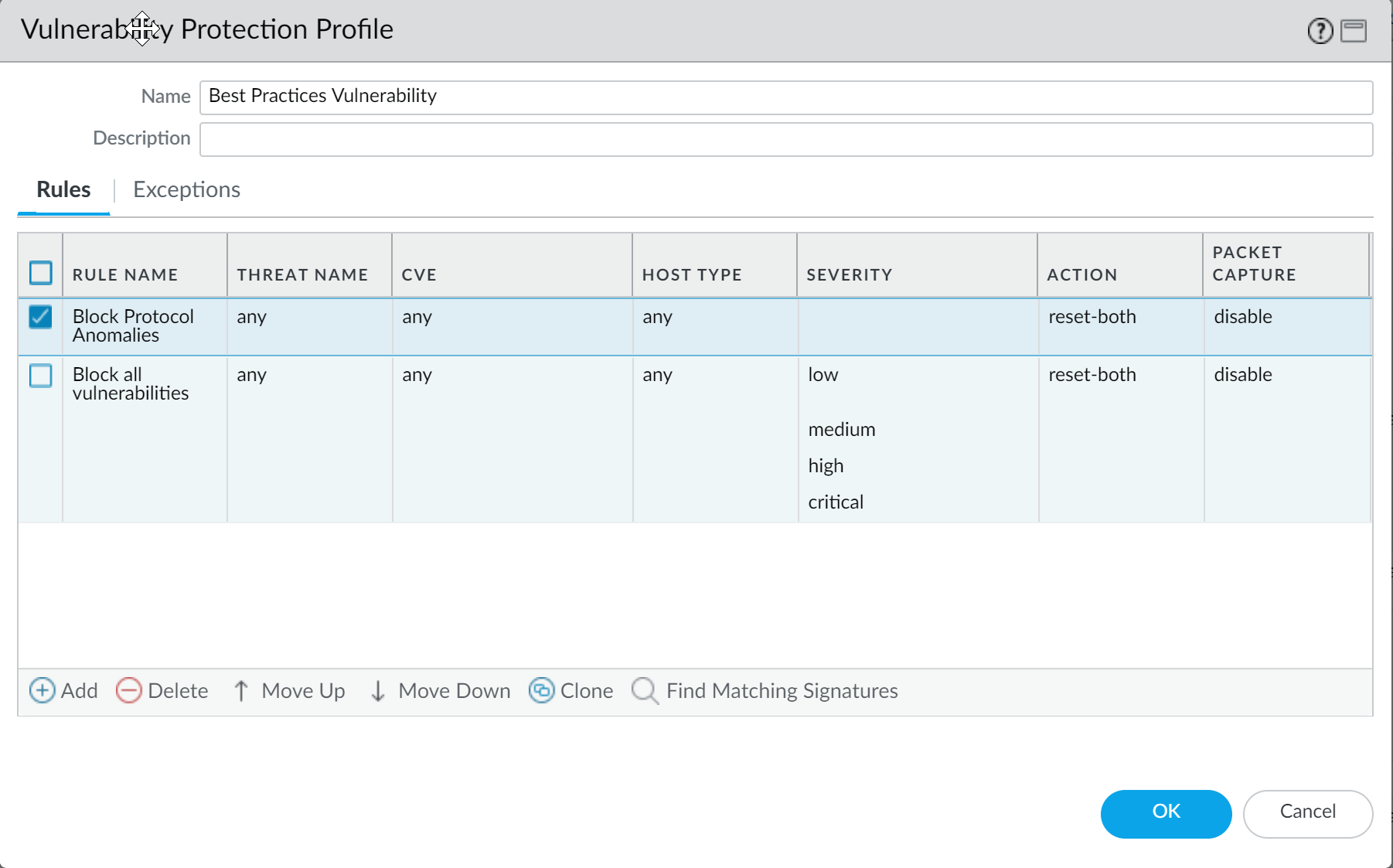
- Create a Vulnerability Protection Profile that blocks protocol anomalies and all vulnerabilities with low and higher severities.
A protocol anomaly occurs when a protocol behavior deviates from standard and compliant usage. For example, a malformed packet, poorly written application, or an application running on a non-standard port would all be considered protocol anomalies, and could be used as evasion tools.
If yours is a mission-critical network, where the business’s highest priority is application availability, you should begin by alerting on protocol anomalies for a period of time to ensure that no critical internal applications are using established protocols in a non-standard way. If you find that certain critical applications trigger protocol anomaly signatures, you can then exclude those applications from protocol anomaly enforcement. To do this, add another rule to the Vulnerability Protection Profile that allows protocol anomalies and attach the profile to the security policy rule that enforces traffic to and from the critical applications.
Make sure that Vulnerability Protection Profile rules and security policy rules that allow protocol anomalies for critical internal applications are listed above rules that block protocol anomalies. Traffic is evaluated against security policy rules and associated Vulnerability Protection Profiles rules from top to bottom, and is enforced based on the first matching rule.
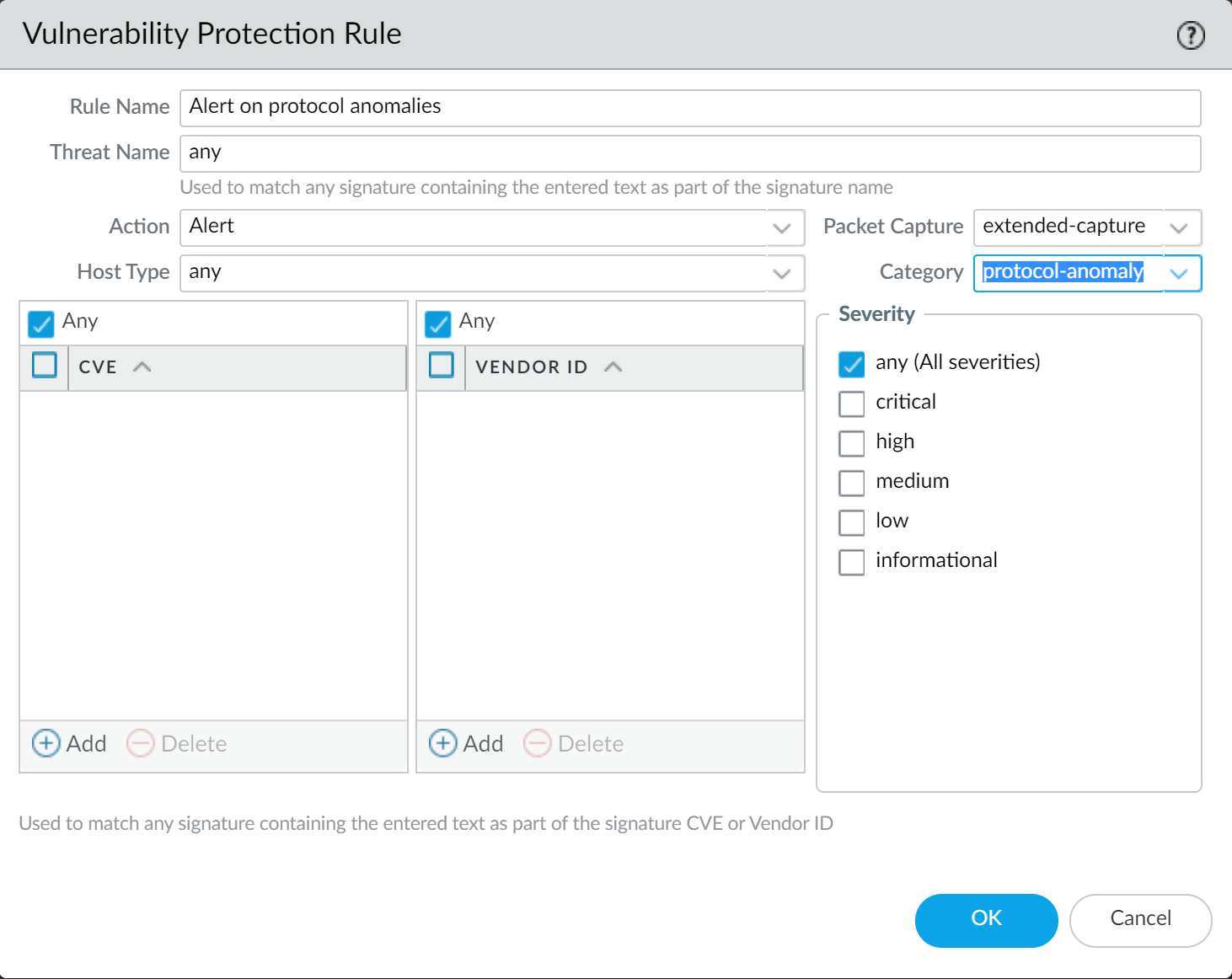
- Begin by alerting on protocol anomalies:
Create a Vulnerability Protection Profile rule with the Action set to Alert, the Category set to protocol-anomaly, and the Severity set to Any. Monitor your traffic to determine if any critical internal applications are using established protocols in non-standard ways. If you find this to be true, continue to allow protocol anomalies for those applications, and then block protocol anomalies for all other applications.
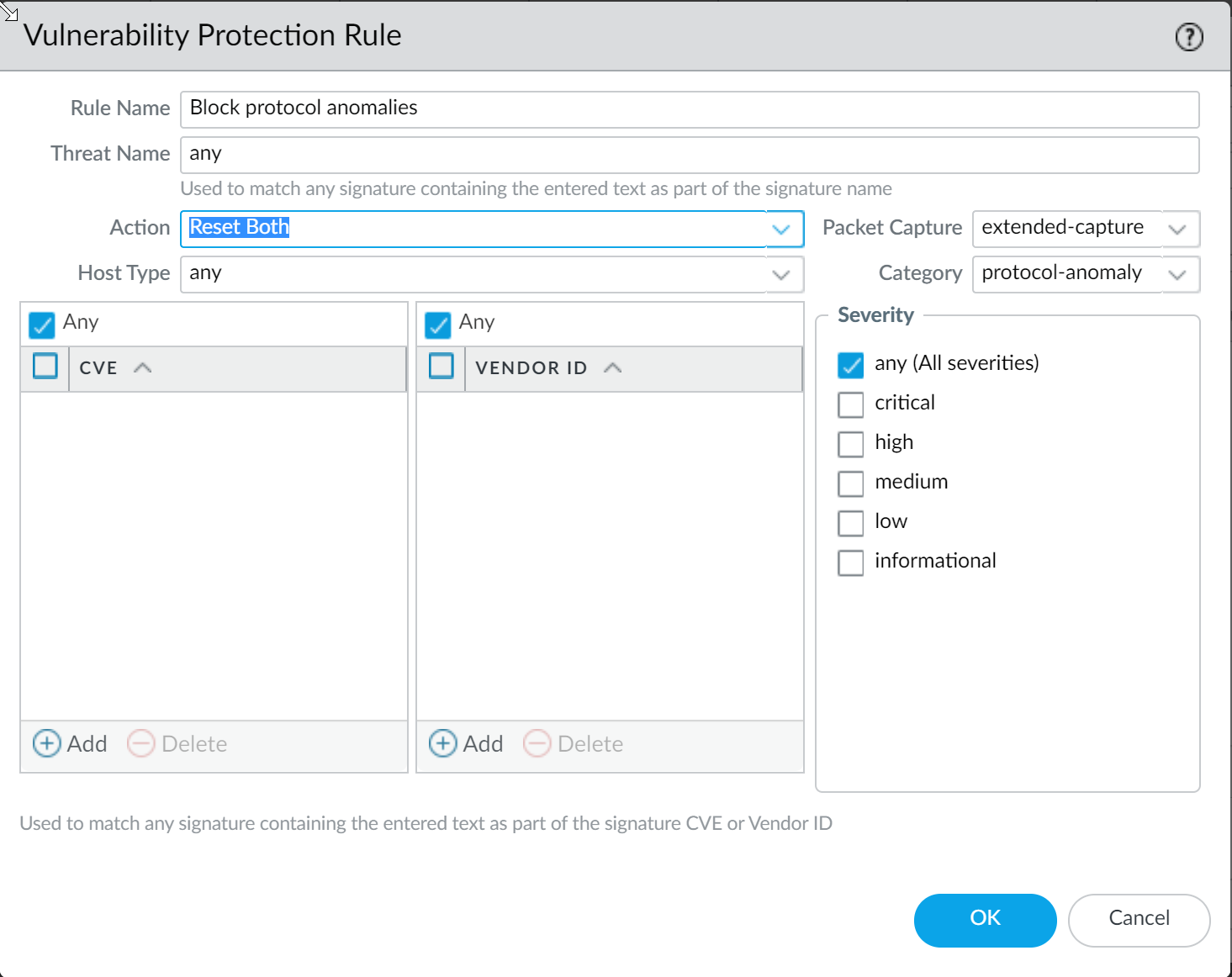
- Block protocol anomalies:
Create a Vulnerability Protection Profile rule with the Category set to protocol-anomaly, the rule Action set to Reset Both, and the Severity set to Any.
- Optionally allow protocol anomalies for critical applications that use established protocols in a non-standard way. To do this, create a Vulnerability Protection Profile rule that allows protocol anomalies: set the rule Action to Allow, the Category to protocol-anomaly, and the Severity to any. Attach the Vulnerability Protection Profile rule to the security policy rule that enforces traffic to and from critical applications.
- Add another rule to the Vulnerability Protection profile to block all vulnerabilities with low and higher severity. This rule must be listed after the rule that blocks protocol anomalies.
- Continue to attach the following security profiles to your Security policy rules to provide signature-based protection:
- An Anti-Spyware profile to block all spyware with severity low and higher.
- An Antivirus profile to block all content that matches an antivirus signature.
Share Threat Intelligence with Palo Alto Networks
Telemetry is the process of collecting and transmitting data for analysis. When you enable telemetry on the firewall, the firewall periodically collects and sends information that includes applications, threats, and device health to Palo Alto Networks. Sharing threat intelligence provides the following benefits:
- Enhanced vulnerability and spyware signatures delivered to you and other customers worldwide. For example, when a threat event triggers vulnerability or spyware signatures, the firewall shares the URLs associated with the threat with the Palo Alto Networks threat research team, so they can properly classify the URLs as malicious.
- Rapid testing and evaluation of experimental threat signatures with no impact to your network, so that critical threat prevention signatures can be released to all Palo Alto Networks customers faster.
- Improved accuracy and malware detection abilities within PAN-DB URL filtering, DNS-based command-and-control (C2) signatures, and WildFire.
Palo Alto Networks uses the threat intelligence extracted from telemetry to deliver these benefits to you and other Palo Alto Networks users. All Palo Alto Networks users benefit from the telemetry data shared by each user, making telemetry a community-driven approach to threat prevention. Palo Alto Networks does not share your telemetry data with other customers or third-party organizations.
To read more about telemetry, including its benefits, usages, and configuration, see Device Telemetry .