Device Telemetry Overview
Device telemetry collects data about your next-generation firewall or Panorama and shares it with Palo Alto Networks by uploading the data to Cortex Data Lake. This data is used to power telemetry apps, which are cloud-based applications that make it easy to monitor and manage your next-generation firewalls and Panoramas. These apps improve your visibility into device health, performance, capacity planning, and configuration. Through these apps, you can maximize the benefits you enjoy from the products and services that Palo Alto Networks delivers.
Telemetry data is also used for sharing threat intelligence, providing enhanced intrusion prevention, evaluation of threat signatures, as well as improved malware detection within PAN-DB URL filtering, DNS-based command-and-control (C2) signatures, WildFire, and to further improve Palo Alto Networks products and services. Review the PAN-OS Privacy information data sheet for details about the data that Palo Alto Networks collects.
PAN-OS version 11.0.1 and later versions of 11.0:
Palo Alto Networks auto-enables device telemetry collection. See Disable Device Telemetry section to manually opt out of device telemetry collection.
Telemetry data is collected and stored locally on your device for a limited period of time. This data is shared with Palo Alto Networks only if you configure a destination region for the data. If your organization has a Cortex Data Lake license, then you can only send the data to the same region as where your Cortex Data Lake instance resides. If your organization does not have a Cortex Data Lake license, then you must install a device certificate in order to share this data. In this case, you can choose any available region, although you must conform to all applicable local laws regarding privacy and data storage.
Palo Alto Networks doesn't include data in transit as telemetry data sent to the Palo Alto Networks cloud and AIOps. Visit the PAN-OS Privacy information sheet for more information about telemetry privacy.
Telemetry data is collected and shared with Palo Alto Networks on predefined collection intervals. You can control whether data is collected and shared by enabling/disabling categories of data. You can also monitor the current status of data collection and transmission.
Finally, you can obtain a live sample of the data that your firewall is collecting for telemetry purposes. For a complete description of all the telemetry metrics that can be shared with Palo Alto Networks, including the privacy implication for each metric, see the PAN-OS Device Telemetry Metrics Reference Guide.
The automatically created user
_cliuser
may appear under
Logged in Admins
on the dashboard while telemetry is enabled. This user is created only for telemetry collection.
Telemetry Data Flow Diagram
graph LR
A[NGFW / Panorama] -- Collects Data --> B{Local Storage - Temporary Bundles};
B -- Transmits Hourly --> C[Cortex Data Lake Region];
C -- Powers --> D(Telemetry Apps - Health - Performance - Config);
C -- Used For --> E(Palo Alto Networks - Threat Intel - Product Improvement);
subgraph "Configuration Options"
F(Enable/Disable Telemetry) --> A;
G(Select Categories) --> A;
H(Set Destination Region) --> C;
I(Service Routes) --> A;
end
J{Device Cert Needed?} -- If No CDL License --> H;
K[CDL License] -- Determines Region --> H;
style A fill:#f9f,stroke:#333,stroke-width:2px
style C fill:#ccf,stroke:#333,stroke-width:2px
style D fill:#cfc,stroke:#333,stroke-width:2px
style E fill:#cfc,stroke:#333,stroke-width:2px
This diagram illustrates the flow of telemetry data from the device to Cortex Data Lake and its usage by apps and Palo Alto Networks, along with key configuration points.
Device Telemetry Collection and Transmission Intervals
PAN-OS collects and sends telemetry data on fixed intervals. Collection frequency is defined on a metric-by-metric basis and can be one of:
-
Default:
Every 5 minutes.
-
Every hour.
-
Daily.
Telemetry is collected into data bundles. Each bundle is an aggregation of all the data collected up to the point of data transmission. These bundles are stored on the device until a transmission event, which occurs
once every 1 hour
. When a bundle has been successfully sent to Palo Alto Networks, it is deleted from the device.
If an error occurs while sending a bundle, the firewall waits 10 minutes and then tries again. The firewall will continue to try to send the bundle until it is either successful, or it needs the storage space for new telemetry data.
At every regular transmission interval, the firewall begins by sending the bundles scheduled for that event. After a successful transfer of those bundles, the firewall sends any failed bundles that it might have stored from previous transmission events.
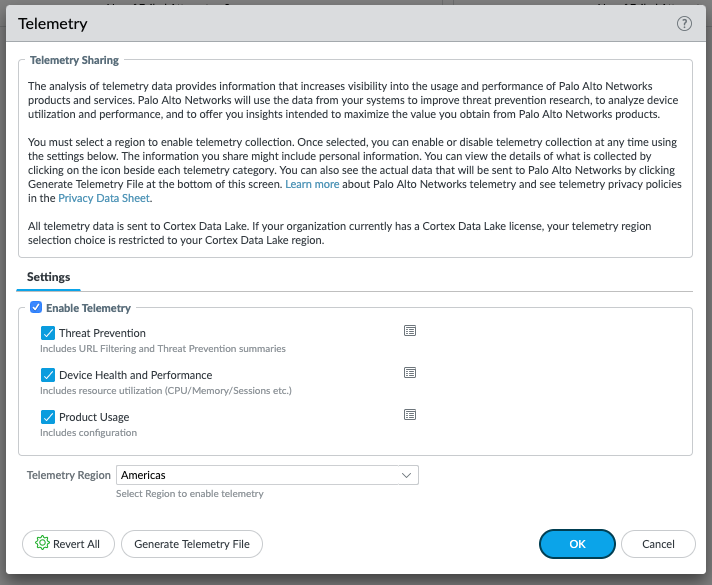
Enable Device Telemetry
PAN-OS version 11.0.1 and later versions of 11.0:
Device Telemetry is automatically enabled.
By default (in earlier versions or if manually disabled), your device does not share data with Palo Alto Networks. To enable sharing:
-
Ensure Cortex Data Lake connectivity is possible:
-
If your organization does
not
have a Cortex Data Lake license, install a device certificate if one is not already installed on your device.
-
If your organization
does
have a Cortex Data Lake license, make sure it is activated.
-
Ensure your network allows traffic to Cortex Data Lake FQDNs/ports.
-
Navigate to
Device > Setup > Telemetry
.
-
Edit the
Telemetry
widget (click the gear icon or similar).
-
In
Telemetry Destination
, select your region. If your organization is using Cortex Data Lake, you must use the same region as your Cortex Data Lake instance.
-
Check the
Enable Telemetry
box (if not already checked).
-
Click
OK
.
-
Commit
your changes.
Note:
_cliuser
may appear as a logged-in admin when the firewall sends telemetry data.
Disable Device Telemetry
If your next-generation firewall is configured to share data with Palo Alto Networks, you can disable this sharing:
-
Navigate to
Device > Setup > Telemetry
.
-
Edit the
Telemetry
widget.
-
Uncheck the
Enable Telemetry
box.
-
Click
OK
.
-
Commit
your changes.
-
Any telemetry data currently stored in Cortex Data Lake is automatically purged one year after your firewall uploaded it. Optionally, if you do not want the data to reside in Cortex Data Lake for this amount of time after you disable telemetry, open a support ticket and ask Palo Alto Networks to purge your telemetry data.
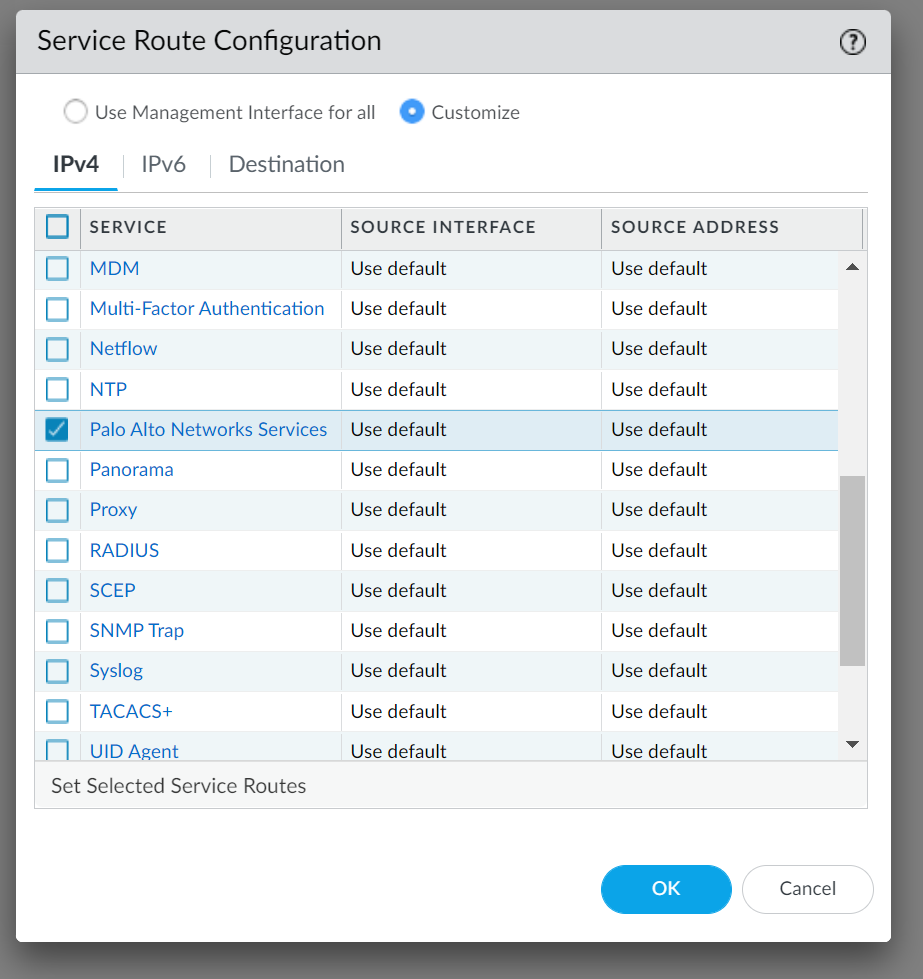
Enable Service Routes for Telemetry
You can configure specific interfaces for outbound telemetry data uploads to Cortex Data Lake, separate from the default management interface route.
-
Select
Device > Setup > Services
.
-
Click the
Service Route Configuration
link (under the Services tab).
-
Select
Customize
.
-
Select
IPv4
or
IPv6
as appropriate.
-
Find the
Palo Alto Networks Services
row (this often covers multiple cloud services including Telemetry/CDL).
-
Choose the custom
Source Interface
you want to use.
-
Choose the custom
Source Address
associated with that interface.
-
Click
OK
.
-
Commit
the configuration.
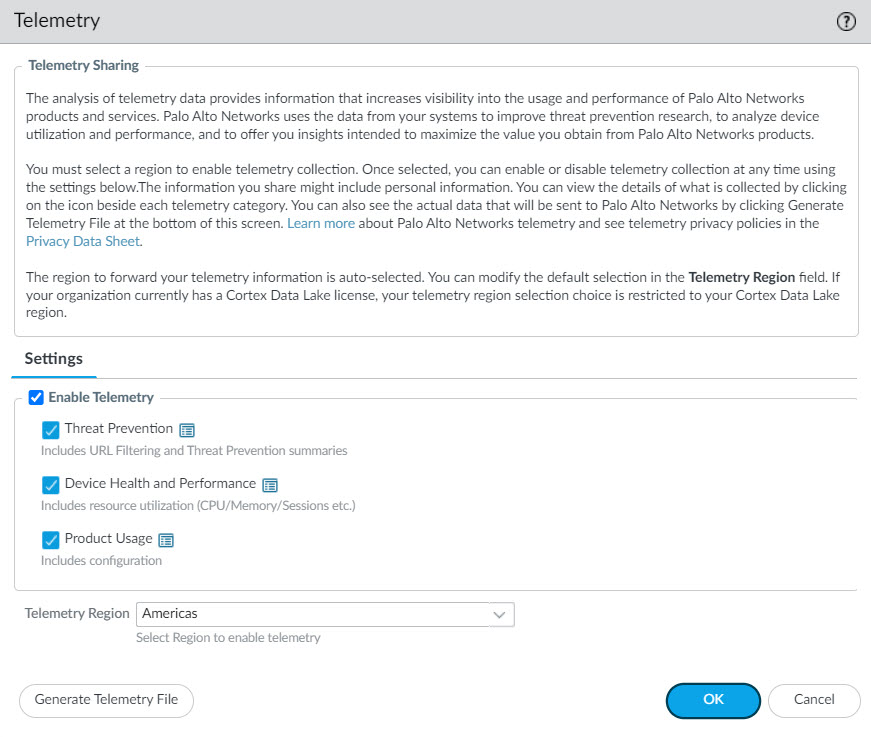
Manage the Data the Device Telemetry Collects
Select
Device > Setup > Telemetry
to see the currently collected telemetry categories. To change these categories, edit the Telemetry widget. Deselect any categories that you don't want the firewall to collect, click
OK
, and then commit the change.
PAN-OS version 11.0.1 and later versions of 11.0:
The telemetry region is auto-selected.
Manage Historical Device Telemetry (Pre-PAN-OS 11.0)
Device Telemetry changed significantly in PAN-OS 11.0. Prior versions collected data primarily focused on threat intelligence. PAN-OS 11.0 extends this to include more device health, performance, and configuration data, and sends it to a different cloud location (effectively standardizing on Cortex Data Lake infrastructure).
If you upgrade a firewall running PAN-OS 10.x or earlier with historical telemetry enabled to PAN-OS 11.0, it will continue to collect and share that older category of data. The PAN-OS 11.0 GUI (
Device > Setup > Telemetry
) does not manage these historical settings.
To turn
off
this historical telemetry data sharing after upgrading to PAN-OS 11.0, use the following CLI commands:
set deviceconfig system update-schedule statistics-service application-reports no
set deviceconfig system update-schedule statistics-service threat-prevention-reports no
set deviceconfig system update-schedule statistics-service threat-prevention-information no
set deviceconfig system update-schedule statistics-service threat-prevention-pcap no
set deviceconfig system update-schedule statistics-service passive-dns-monitoring no
set deviceconfig system update-schedule statistics-service url-reports no
set deviceconfig system update-schedule statistics-service health-performance-reports no
set deviceconfig system update-schedule statistics-service file-identification-reports no
To turn
on
this historical telemetry data sharing on a PAN-OS 11.0 firewall (if previously disabled), use the same commands with
yes
:
set deviceconfig system update-schedule statistics-service application-reports yes
set deviceconfig system update-schedule statistics-service threat-prevention-reports yes
# ... (and so on for other categories)
To check the status of historical telemetry sharing, use this CLI command:
show deviceconfig system update-schedule statistics-service
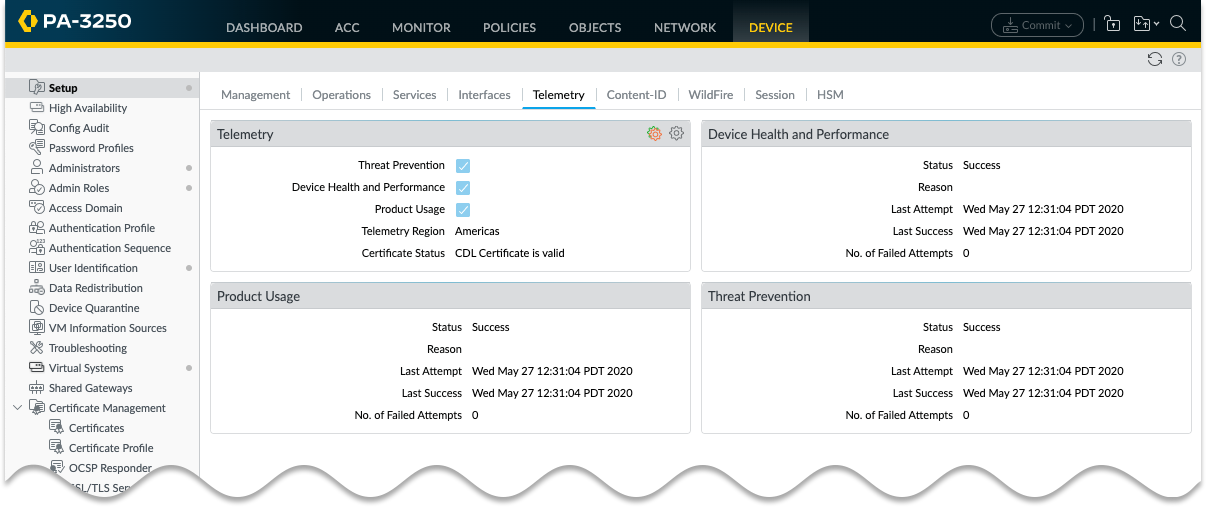
Monitor Device Telemetry
PAN-OS shows the sharing status for each modern telemetry category (enabled in PAN-OS 11.0+) in widgets at
Device > Setup > Telemetry
.
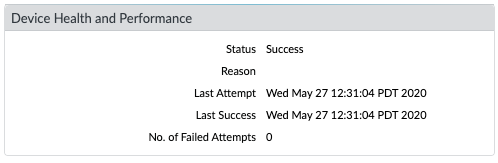
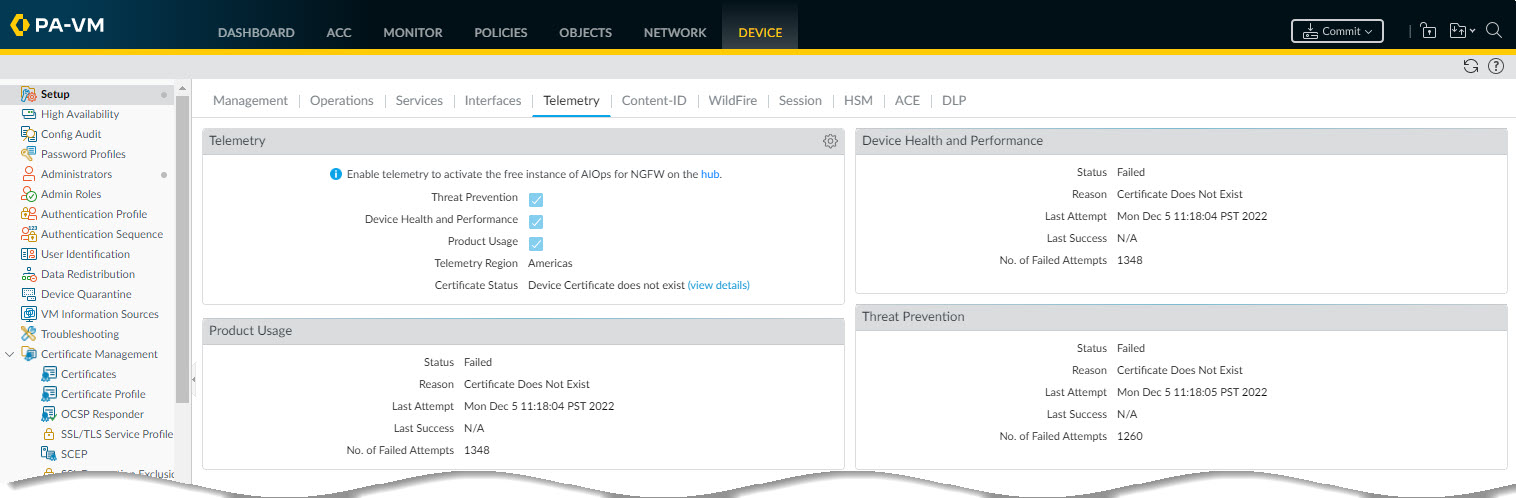
In the event of a transmission failure, your device will retry the send attempt at the next hourly interval. If the problem persists, check your network configuration and prerequisites:
-
If using a Cortex Data Lake license, ensure it's activated and the firewall is correctly onboarded/configured to use it.
-
If not using a Cortex Data Lake license, ensure a valid device certificate is installed.
-
Verify network connectivity (firewall rules, routing) allows traffic to the appropriate Cortex Data Lake FQDNs/ports for your selected region.
Sample the Data that Device Telemetry Collects
You can download a live example of the data that device telemetry collects and shares. Go to
Device > Setup > Telemetry
, and edit the
Telemetry
widget. Then click
Generate Telemetry File
.
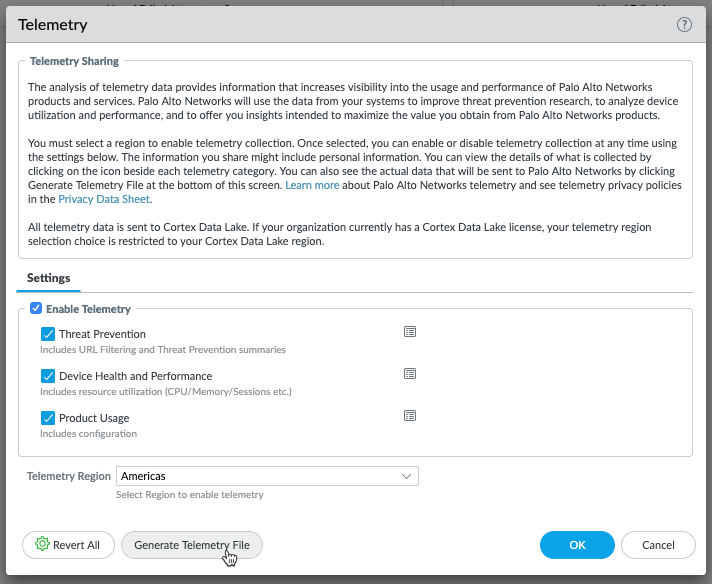
PAN-OS version 11.0.1 and later versions of 11.0:

Data collection takes a few minutes. When complete, click
Download Device Telemetry Data
. The telemetry bundle (a compressed tar ball) will be saved to your browser's download directory.
For a description of every metric collected, see the PAN-OS Device Telemetry Metrics Reference Guide.
?? Device Telemetry Interactive Quiz






