Palo Alto Networks NGFW Architecture - PCNSE Focus
1. Single Pass Parallel Processing (SP3) Architecture
The heart of a Palo Alto Networks Next-Generation Firewall (NGFW) is its Single Pass Parallel Processing (SP3) architecture . Think of it as an incredibly efficient assembly line designed specifically for inspecting network traffic. This architecture is fundamental to delivering high throughput (speed) and low latency (delay), even when multiple security functions are enabled. For the PCNSE exam, understanding SP3 is crucial as it explains *how* the firewall maintains performance while providing comprehensive security.
-
Single Pass Software:
Imagine traffic entering the firewall. Instead of being handed off to multiple different engines one after another (which is what multi-pass architectures do, often leading to slower performance), the Single Pass software inspects the traffic
just once
. In this single pass, it performs several key operations simultaneously:
- Application identification (App-ID)
- User identification (User-ID)
- Content inspection (Content-ID - checking for threats like viruses, spyware, vulnerabilities, and also performing URL filtering and file blocking)
- Policy lookup and enforcement
-
Parallel Processing Hardware:
To make the Single Pass software run exceptionally fast, Palo Alto Networks firewalls use dedicated processors for different tasks. This is the "Parallel Processing" part. It means that various aspects of traffic inspection and management happen concurrently, not sequentially. The main components are:
- Network Processor: Handles core networking tasks like routing, NAT (Network Address Translation), QoS (Quality of Service), and managing the flow of traffic.
- Security Processor: Dedicated to security-specific tasks. In many SP3 implementations, this involves App-ID, User-ID, policy enforcement, and decryption/encryption.
- Content Processor (Signature Match Processor): This powerful processor is responsible for the heavy lifting of Content-ID: scanning for viruses, spyware, intrusions, and other threats using a uniform signature matching system.
- Control Plane Processor: This is the "brain" for management tasks. It handles things like user interface (web UI, CLI), logging, reporting, and configuration changes. Crucially, the control plane is kept separate from the data plane (where traffic processing happens). This separation ensures that even if the control plane is busy (e.g., an admin running a complex report), it doesn't slow down the actual traffic inspection and forwarding.
PCNSE Tip: Understand that SP3 allows the firewall to apply all security policies in a single, unified pass. This reduces latency and increases throughput. Contrast this with multi-pass architectures which can introduce significant delays as traffic is passed between different inspection engines.
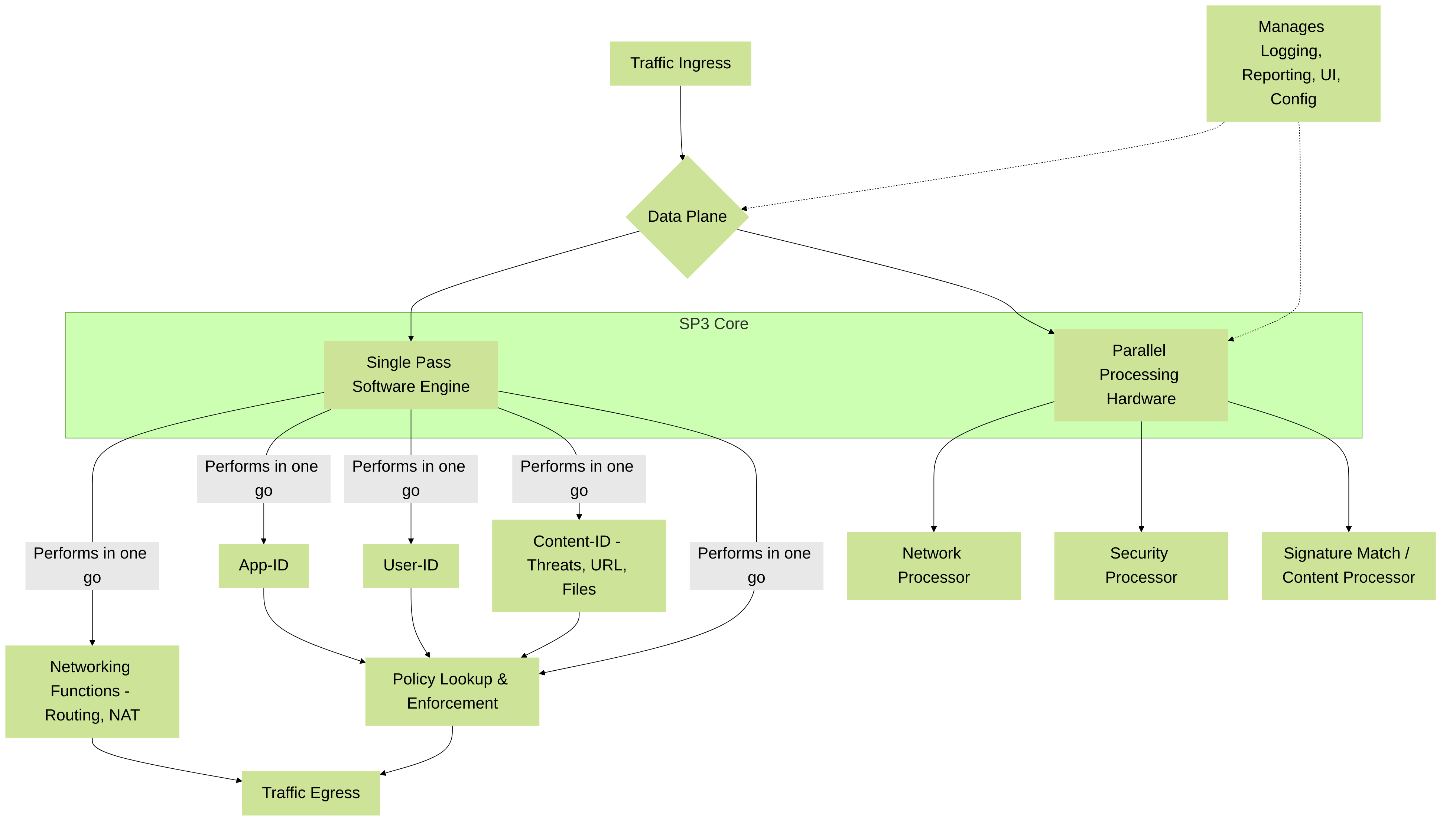
Simplified SP3 Architecture: Traffic is processed once by the software, leveraging parallel hardware processors.
Simplified Packet Flow (Life of a Packet) through SP3:
- Ingress: Packet arrives at a firewall interface. Basic checks are performed.
-
Session Setup (Slow Path - First Packet):
- If it's the first packet of a new flow (new session), it goes through the "slow path" (though it's still very fast!).
- Zone protection and basic TCP state checks occur.
- Forwarding lookup (routing, NAT policy evaluation) happens.
- User-ID information is retrieved.
- Security policy lookup is performed.
- If allowed, a session is created in the data plane.
- Fast Path (Subsequent Packets): Once a session is established, subsequent packets belonging to that same session bypass much of the initial setup and are processed via the "fast path," significantly speeding up processing. Security processing still occurs.
-
Single Pass Inspection (Core of SP3):
- App-ID: The application is identified.
- Content-ID: The identified application's content is scanned for threats (viruses, spyware, vulnerabilities), URLs are checked, and file blocking policies are applied, all based on the security policy. This happens in a stream-based manner, meaning the firewall doesn't necessarily have to wait for the entire file to download before it starts scanning.
- Policy Enforcement: Based on all the information gathered (App, User, Content, Source/Destination Zone, etc.), the security policy is enforced (allow, deny, alert, reset, etc.).
- Egress: If allowed, the packet is forwarded out the appropriate egress interface, potentially after NAT and QoS adjustments.
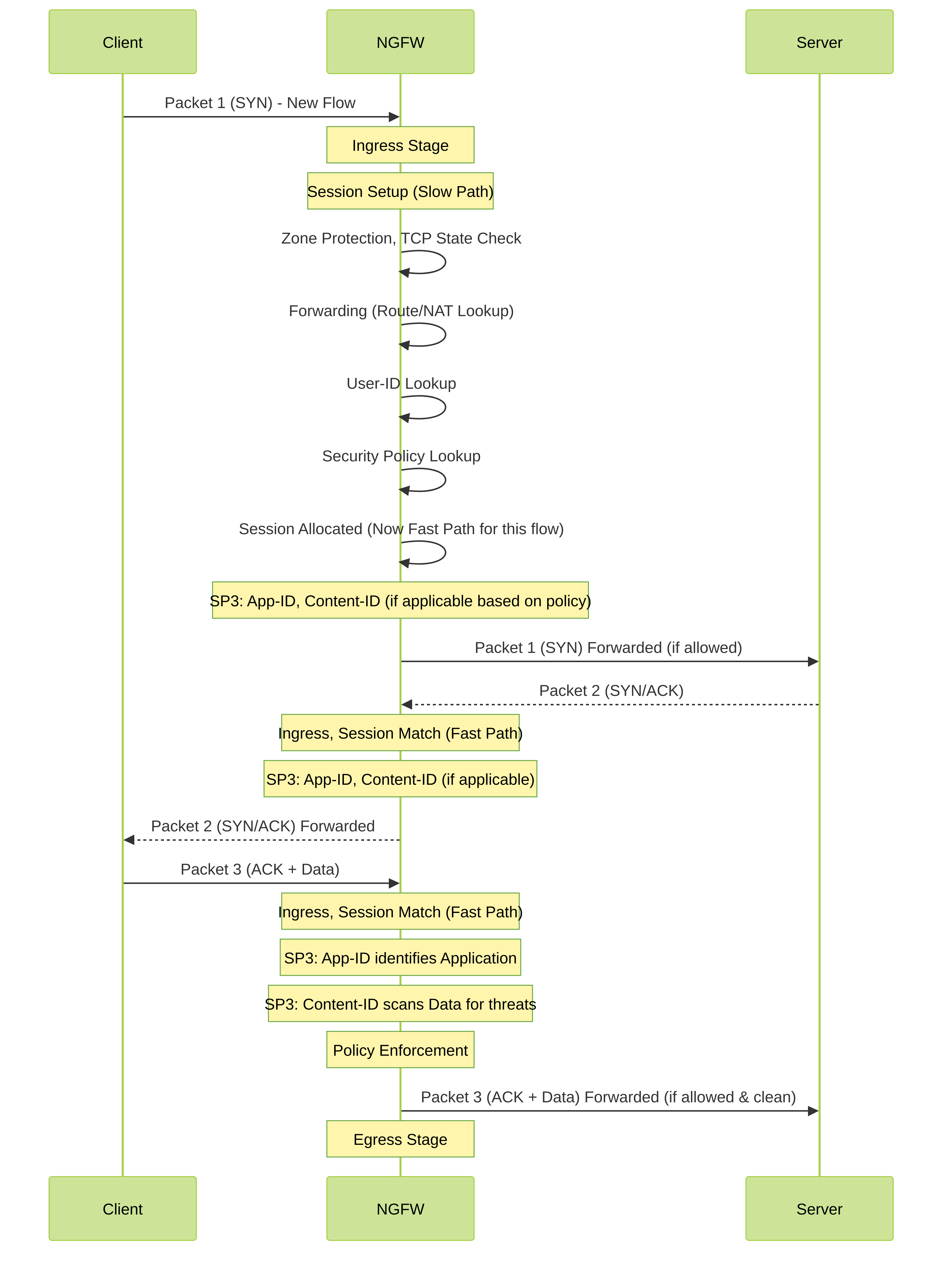
Simplified "Life of a Packet" highlighting key SP3 interactions.
2. Functional Modules
These are the key software "brains" within the Single Pass architecture that enable the NGFW's advanced security capabilities. For the PCNSE, you'll need to know what each module does, its benefits, and generally how to configure or verify its operation.
-
App-ID (Application Identification):
Think of App-ID as the firewall's super-smart traffic detective. Instead of just looking at port numbers (like old firewalls, e.g., TCP port 80 for web), App-ID figures out exactly *which* application is generating the traffic (e.g., Facebook, Salesforce, or even evasive apps trying to hide on standard ports). It uses multiple techniques:
- Signatures: Unique patterns in the traffic that identify known applications.
- Protocol Decoders: Understands how protocols like HTTP or SSL/TLS work to find application details.
- Heuristics: Behavioral analysis for applications that try to evade detection.
- App-ID Cloud Engine (ACE): For very new or rapidly changing cloud applications, the firewall can consult ACE for the latest App-ID information.
PCNSE Relevance: App-ID is fundamental to creating granular security policies. You can allow, deny, scan, shape, or apply QoS based on the actual application, not just the port. Understanding how to convert port-based rules to App-ID rules is a key skill. App-ID is what enables "application enablement" – safely allowing specific applications while blocking or controlling others.
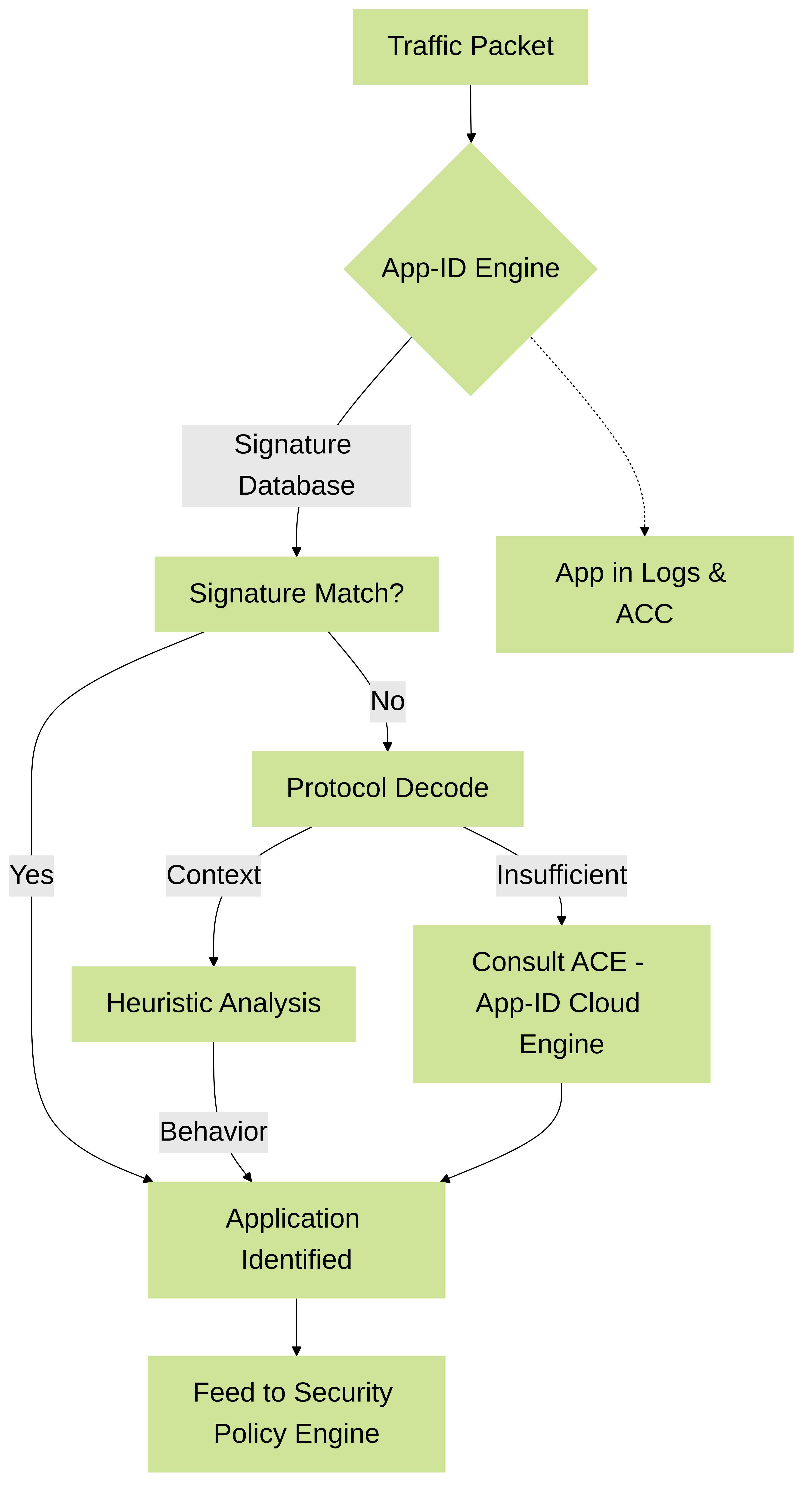
App-ID process for identifying applications.
-
User-ID (User Identification):
User-ID links network traffic to actual users or groups within your organization, rather than just IP addresses (which can change or be shared). Imagine you see suspicious traffic from 10.1.1.50 – User-ID tells you if that's "Bob from Accounting" or "Alice from Engineering." This is incredibly powerful for creating policies and for incident investigation.
User-ID gathers information from various sources:
- Directory Services: Active Directory (Windows), LDAP. The firewall can monitor domain controller security logs or use an agent.
- Captive Portal: For users not in a directory (e.g., guests), they can be prompted to log in.
- GlobalProtect: Remote access users are identified upon connection.
- Syslog, XML API, Explicit Authentication: Other methods to map IPs to users.
- Cloud Identity Engine (CIE): For integrating with cloud-based identity providers.
PCNSE Relevance: You need to understand how to configure different User-ID methods, how the firewall builds its IP-to-user mappings, and how to apply user/group-based security policies. Troubleshooting User-ID is a common PCNSE topic (e.g., why isn't a user being identified?). Enabling User-ID on zones is a critical step.
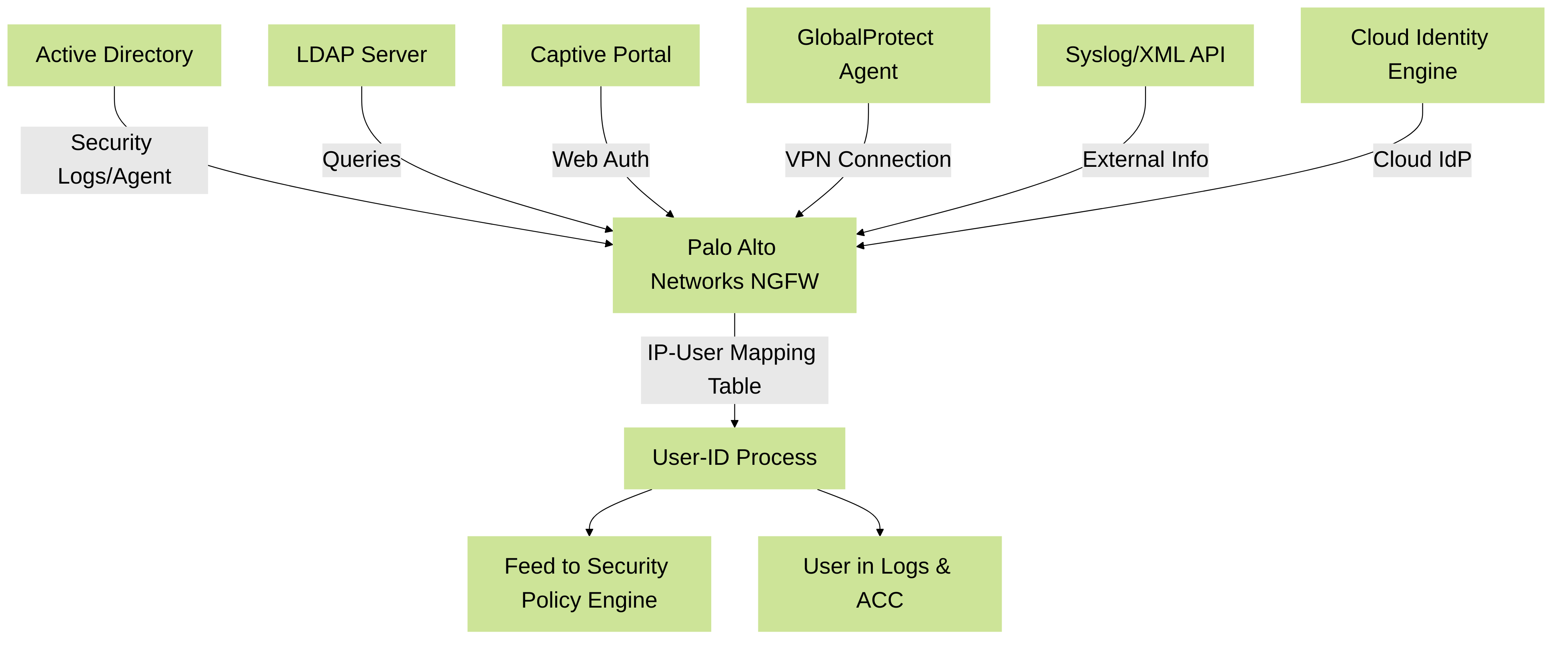
User-ID gathering identity information from various sources.
-
Content-ID (Content Inspection):
Once App-ID identifies the application and User-ID tells you who is using it, Content-ID inspects the *content* of that allowed traffic for threats. It's like having a security guard who not only checks *who* is coming in and *what* they say they're doing, but also inspects their bags for dangerous items. Content-ID combines several security subscriptions and engines:
- Antivirus: Blocks known viruses, worms, and trojans.
- Anti-Spyware: Detects and blocks spyware, adware, and other malicious software that might exfiltrate data or monitor activity.
- Vulnerability Protection: Protects against known software exploits that target vulnerabilities in applications and operating systems (think of it like a virtual patch).
- URL Filtering (PAN-DB or Advanced URL Filtering): Blocks access to malicious websites (phishing, malware distribution) and allows control over web categories (e.g., block gambling, allow news). Advanced URL Filtering uses ML for real-time detection.
- File Blocking: Controls which file types can be uploaded or downloaded (e.g., block .exe files from being downloaded from certain sites).
- Data Filtering: Helps prevent sensitive data (like credit card numbers or social security numbers) from leaving the network (a form of Data Loss Prevention - DLP).
PCNSE Relevance: You must know how to configure Security Profiles (which house Content-ID settings) and attach them to Security Policy Rules. Understanding the order of operations (App-ID first, then Content-ID on allowed traffic) is key. Knowing which subscription enables which feature is also important.
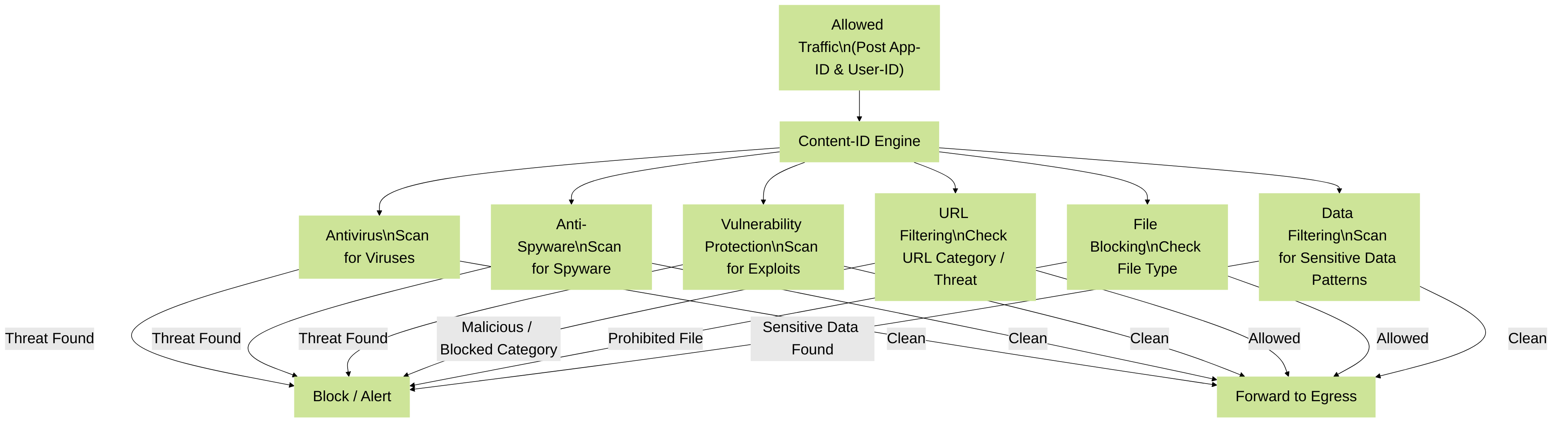
Content-ID inspecting allowed traffic through various security profiles.
-
WildFire:
WildFire is Palo Alto Networks' cloud-based threat analysis service that protects against unknown malware and zero-day exploits . When the firewall encounters a file or link it hasn't seen before and suspects might be malicious, it can forward it to the WildFire cloud for analysis.
Here's the simplified process:
- Firewall sees an unknown file (based on its hash not being in known databases).
- Firewall forwards the file (or just its hash, depending on configuration and license) to the WildFire cloud sandbox.
- WildFire executes the file in a safe, virtual environment and observes its behavior (static and dynamic analysis).
- If the file is malicious, WildFire creates a new signature.
- This new signature is distributed globally to all Palo Alto Networks firewalls with an active WildFire subscription, typically within minutes.
- Now, what was an "unknown" threat becomes "known," and other firewalls can block it proactively.
PCNSE Relevance: Understand the WildFire submission process, the types of verdicts (benign, malware, grayware, phishing), and how WildFire signatures are used by Antivirus and Anti-Spyware profiles to block newly discovered threats. Knowing what a WildFire Analysis Profile does versus an Antivirus profile is important (WildFire *identifies* new threats, Antivirus *blocks* based on signatures including those from WildFire).
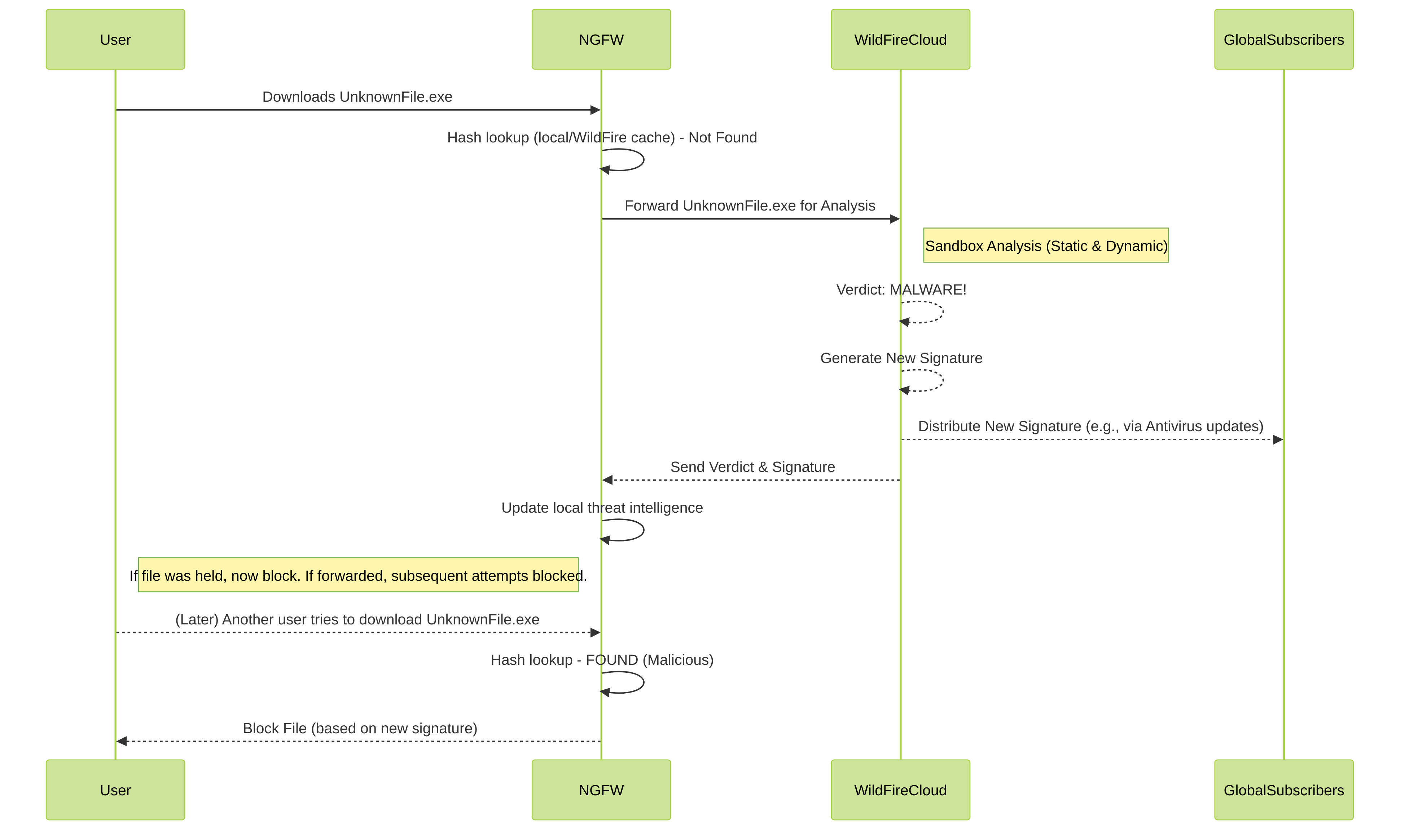
WildFire analysis and signature distribution workflow.
-
GlobalProtect:
GlobalProtect extends the firewall's security policies to users outside the corporate network (e.g., remote workers, mobile users). It creates a secure VPN connection back to the firewall, ensuring that traffic from these remote users is inspected with the same App-ID, User-ID, and Content-ID policies as if they were on the local network.
Key components:
- GlobalProtect Portal: Authenticates users and provides them with the agent software and a list of available gateways.
- GlobalProtect Gateway(s): Terminates the VPN tunnels and enforces security policies.
- GlobalProtect Agent: Software installed on the endpoint (laptop, mobile device) that establishes and maintains the secure connection.
PCNSE Relevance: You should understand the roles of the portal and gateway, different agent connection methods, how to configure GlobalProtect for secure remote access, and how it integrates with User-ID. Concepts like split-tunneling are also important.
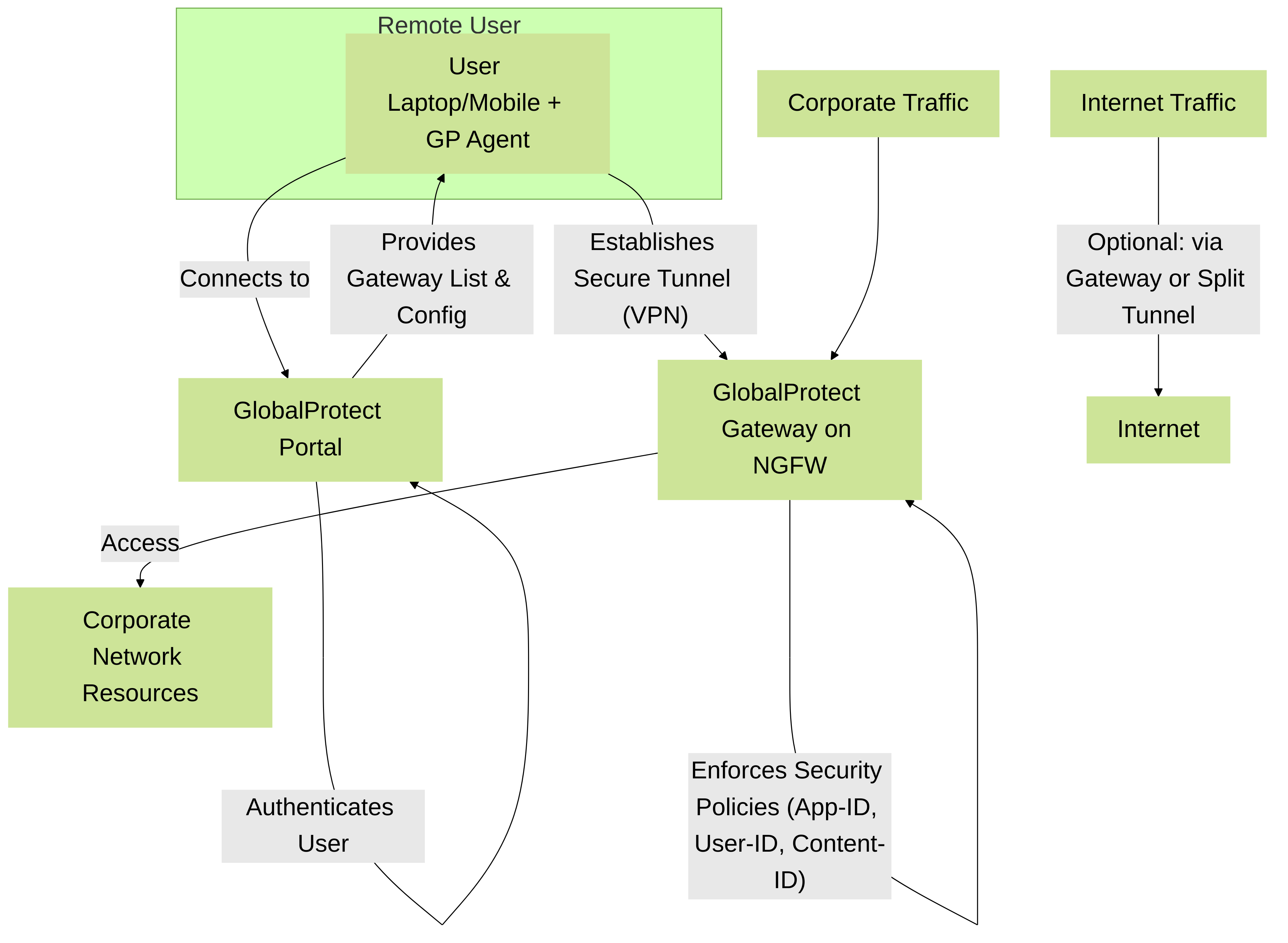
GlobalProtect architecture for secure remote access.
-
Panorama:
Panorama is a centralized management solution for managing multiple Palo Alto Networks firewalls (physical, virtual, and cloud-based). If you have more than a few firewalls, Panorama becomes essential for consistent policy deployment, software updates, log collection, and reporting.
Key functions:
- Device Groups: Group firewalls that share common policies (e.g., all branch office firewalls).
- Templates & Template Stacks: Manage common network and device settings across multiple firewalls.
- Centralized Policy Management: Create policies (pre-rules, post-rules) and push them to managed firewalls.
- Centralized Logging & Reporting: Aggregate logs from all managed firewalls for a network-wide view of traffic and threats. Can use dedicated Log Collectors.
- Software/Content Update Management: Centrally manage PAN-OS upgrades and content (threat, App-ID) updates.
PCNSE Relevance: Understanding Panorama's role, its different modes (Panorama, Management Only, Log Collector), how Device Groups and Templates work, and the concept of pre-rules and post-rules are critical for the PCNSE exam. The PCNSE heavily tests Panorama knowledge.

Panorama providing centralized management for multiple firewalls using Device Groups and Templates, with optional Log Collectors.
3. Hardware, Virtual, and Cloud-Delivered Platforms
Palo Alto Networks offers its NGFW capabilities across various form factors to suit different deployment needs. For the PCNSE, you should be aware of the different series and their general use cases, rather than memorizing specific throughput numbers for every model.
-
PA-Series (Physical Appliances):
These are hardware firewalls ranging from small branch office devices to large, high-performance chassis for data centers and service providers.
- PA-220/PA-220R (Ruggedized): For small offices, retail, or harsh industrial environments.
- PA-400 Series: Compact appliances for branch offices and mid-sized businesses.
- PA-800 Series: Mid-range appliances for small to medium enterprises.
- PA-1400 Series: New generation for mid-size enterprise branches and smaller enterprise edges.
- PA-3200 Series / PA-3400 Series: High-performance for large branch, regional offices, and smaller enterprise data centers.
- PA-5200 Series / PA-5400 Series: Designed for data centers, large campus segmentation, and service provider deployments requiring high throughput.
- PA-7000 Series / PA-7500 Series: Modular, chassis-based systems for the most demanding high-throughput environments like large data centers and service provider cores.
-
VM-Series (Virtualized Firewalls):
The VM-Series is the virtualized version of the NGFW. It allows you to deploy firewall protection in private clouds (e.g., VMware ESXi, KVM, Hyper-V) and public clouds (e.g., AWS, Azure, GCP). This is crucial for protecting east-west traffic within virtualized environments and securing cloud workloads.
PCNSE Relevance: Understand that VM-Series provides the same PAN-OS features as hardware firewalls. Know its use cases in cloud and virtualized data centers. Licensing models (e.g., BYOL, PAYG) might be relevant.
-
CN-Series (Containerized Firewalls):
As organizations adopt containers and Kubernetes, the CN-Series provides NGFW capabilities specifically designed for these environments. It helps secure traffic between containerized applications and prevents threats from spreading across Kubernetes namespace boundaries.
PCNSE Relevance: Be aware of CN-Series as the solution for container security and its integration with Kubernetes.
-
Cloud NGFW (Cloud-Delivered Services):
Palo Alto Networks also offers cloud-delivered security services, such as Cloud NGFW for AWS and Azure. These are managed services that make it easier to deploy and consume NGFW capabilities directly within cloud provider environments.
PCNSE Relevance: Know that these exist as an option for simplified cloud security deployment, often managed through Panorama or Strata Cloud Manager.
Palo Alto Networks NGFW platform availability across different form factors.