Palo Alto Networks Best Practice Assessment (BPA) and Heatmap: A PCNSE Guide
Introduction to BPA and Heatmaps
The Best Practice Assessment (BPA) and its accompanying heatmap are essential tools for any security professional working with Palo Alto Networks firewalls and Panorama. They provide valuable insights into your security posture, highlighting areas of strength and weakness, ultimately helping you optimize your configurations and strengthen your defenses. This guide provides a deep dive into these tools, tailored for those preparing for the PCNSE exam.
What is the Best Practice Assessment (BPA)?
The BPA is a service provided by Palo Alto Networks that analyzes your firewall and Panorama configurations against a comprehensive set of best practices. It performs numerous checks covering various aspects of your security setup, including security policy rules, security profiles, device settings, and more. The results are presented in a detailed report, providing actionable recommendations for improving your security posture.
- Configuration Analysis: The BPA examines your current configuration, identifying potential misconfigurations, unused objects, and areas for optimization.
- Best Practice Alignment: It checks your configuration against Palo Alto Networks' recommended best practices, ensuring compliance and optimal performance.
- Actionable Recommendations: The BPA report provides clear and concise recommendations on how to address identified issues and improve your security posture. For example, it might suggest enabling specific security profiles, optimizing rule order, or removing unused objects.
- Security Posture Enhancement: By implementing the recommendations from the BPA report, you can significantly enhance your overall security posture, reducing your attack surface and improving your ability to prevent and detect threats.
Understanding the Heatmap
The heatmap provides a visual representation of the BPA results, making it easy to quickly identify areas that require attention. It uses a color-coded system, typically ranging from green (good) to red (poor), to indicate the level of compliance with best practices for different categories.
- Visual Representation: The heatmap presents the BPA findings in an easily digestible visual format, allowing for quick identification of critical areas.
- Prioritization: The color-coding helps prioritize remediation efforts by highlighting the areas that require immediate attention. Red areas usually indicate significant deviations from best practices and should be addressed first.
- Trend Analysis: Running BPAs regularly allows you to track your progress over time and visualize the impact of your security improvements. This is particularly helpful for demonstrating compliance and justifying security investments.
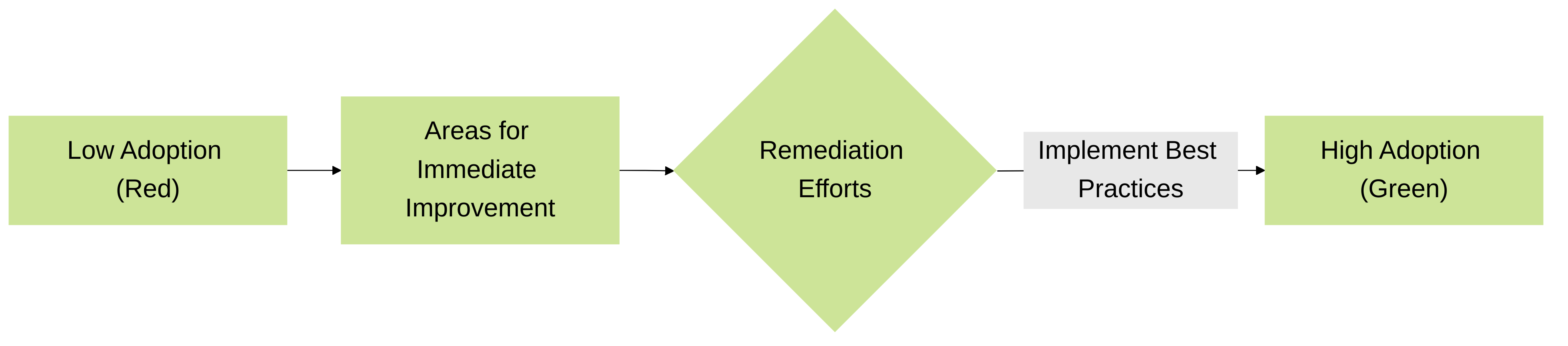
Heatmap Adoption Levels and Remediation Flow
How to Run a BPA
Generating a BPA report involves several key steps:
- Generate a Tech Support File (TSF): Log in to your firewall or Panorama management interface and generate a TSF. This file contains the configuration data needed for the BPA.
- Access the BPA Tool: The BPA tool can be accessed through the Customer Support Portal (CSP) or through AIOps for NGFW (formerly Strata Cloud Manager).
- Upload the TSF: Upload the generated TSF to the BPA tool. The tool will then analyze the configuration data.
- Review the Report and Heatmap: Once the analysis is complete, you'll receive a detailed report and a heatmap summarizing the findings and providing recommendations.
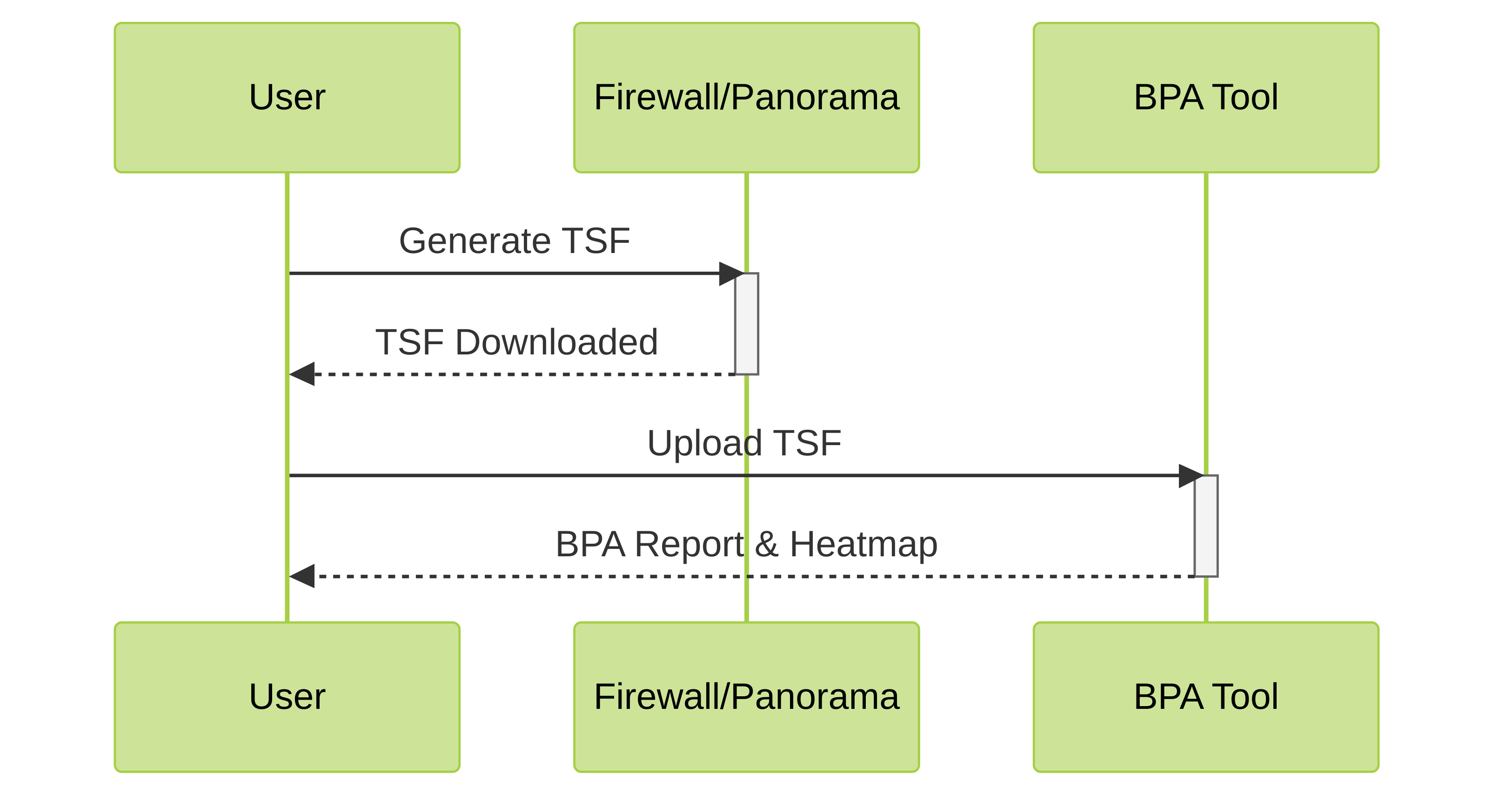
BPA Generation Process
Key BPA Categories and Checks (PCNSE Focus)
The BPA covers a wide range of security areas. Here are some key categories and checks relevant to the PCNSE exam:
- Security Policy Optimization: Checks for rule shadowing, redundant rules, overly permissive rules, and best practice compliance in security policy configuration.
- Security Profile Usage: Evaluates the usage and configuration of security profiles like Anti-virus, Anti-spyware, URL Filtering, Vulnerability Protection, and WildFire. The BPA might recommend enabling or configuring specific profiles to enhance security.
- Network Configuration: Assesses network settings for best practice compliance, including management interface security, IP address usage, and routing configuration.
- Device Settings: Examines various device settings such as logging, SNMP, NTP, and administrative access controls.
- High Availability (HA): If applicable, evaluates the HA configuration for proper setup and functionality.
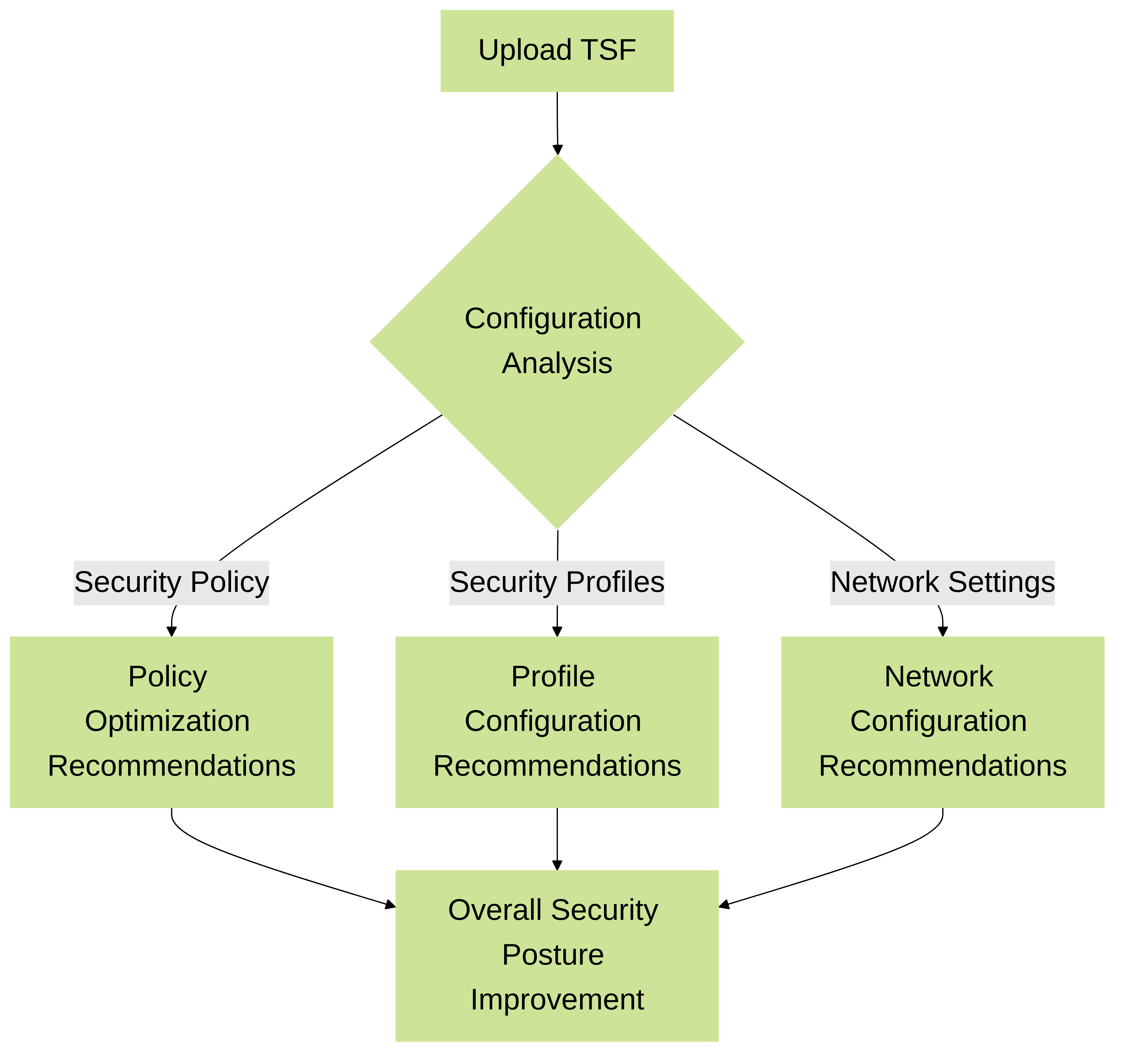
BPA Analysis and Recommendation Flow
Leveraging BPA for Continuous Improvement
Regularly performing BPAs is a critical aspect of maintaining a strong security posture. It allows you to proactively identify and address potential vulnerabilities, adapt to evolving threats, and demonstrate compliance with security best practices.
- Scheduled Assessments: Implement a schedule for regular BPA execution, such as monthly or quarterly, to ensure continuous monitoring and improvement.
- Post-Change Validation: Run a BPA after making significant configuration changes to validate the impact on your security posture and ensure no new vulnerabilities have been introduced.
- Compliance Reporting: BPA reports can be used to demonstrate compliance with industry regulations and internal security policies.
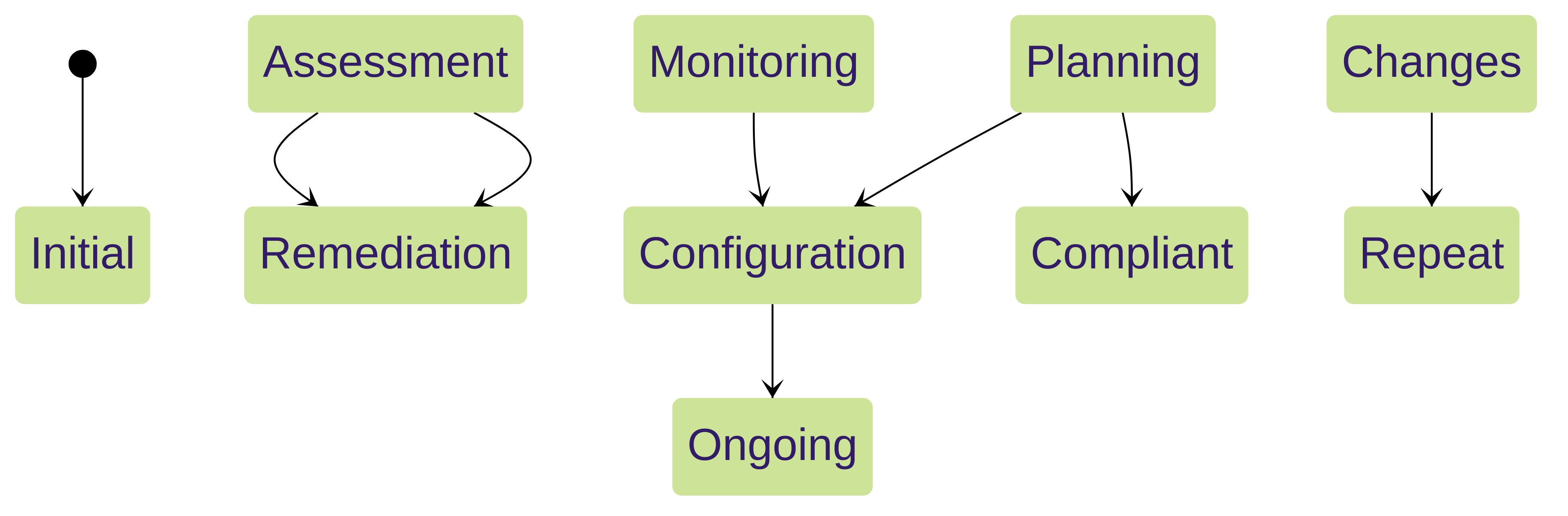
Continuous Improvement Cycle with BPA