Device-ID Overview
According to the 2020 Unit 42 IoT Threat Report , 30% of all network-connected devices in an average enterprise are IoT . This presents a constantly growing area of risk with many possibilities for exploitation by malicious users. Additionally, once you identify these devices, how do you secure them from vulnerabilities such as outdated operating software? Using Device-ID™ on your firewalls, you can get device context for events on your network, obtain policy rule recommendations for those devices, write policy rules based on devices, and enforce Security policy based on the recommendations.
Similar to how User-ID provides user-based policy rules and App-ID provides app-based policy rules, Device-ID provides policy rules that are based on a device , regardless of changes to its IP address or location. By providing traceability for devices and associating network events with specific devices, Device-ID lets you gain context for how events relate to devices and adds policy rules that are associated with devices, instead of users, locations, or IP addresses, which can change over time. You can use Device-ID in Security, Decryption, Quality of Service (QoS), and Authentication policies.
For Device-ID features to be available on a firewall, you must purchase an IoT Security subscription and select the firewall during the IoT Security onboarding process . There are two types of IoT Security subscriptions:
- IoT Security Subscription
- IoT Security – Doesn’t Require Data Lake (DRDL) Subscription
With the first subscription, firewalls send data logs to the logging service , which streams them to IoT Security for analysis and to a Cortex Data Lake instance for storage. The data lake instance can either be a new or existing one. With the second subscription, firewalls send data logs to the logging service, which streams them to IoT Security for analysis but not to a Cortex Data Lake instance for storage. It’s important to note that both IoT Security and IoT Security (DRDL) subscriptions provide the same functionality in terms of IoT Security and Device-ID.
To permit connections to IoT Security, a firewall needs a device license ; and to permit connections to the logging service, it needs a logging service license . A firewall also requires a device certificate to authenticate itself when connecting to IoT Security and the logging service.
If you use PAN-OS version 10.0 or later, you can use Device-ID to obtain IP address-to-device mappings to view device context for network events, use IoT Security to obtain policy rule recommendations for these devices, and gain visibility for devices in reports and the ACC.
You can create a device-based Security policy on any Panorama or firewall that uses PAN-OS version 10.0 or later . To enforce the Security policy, the device must have a valid IoT Security license.
To identify and classify devices, the IoT Security app uses metadata from logs, network protocols, and sessions on the firewall. This does not include private or sensitive information or data that is not relevant for device identification. Metadata also forms the basis of the expected behavior for the device, which then establishes the criteria for the policy rule recommendation that defines what traffic and protocols to allow for that device.
When a firewall imports Security policy rule recommendations and IP address-to-device mappings from IoT Security, the firewall sends its device certificate to an edge server to authenticate itself. The edge server authenticates itself to the firewall by sending its own certificate. The firewall uses Online Certificate Status Protocol (OCSP) to validate the server’s certificate by checking it against the following sites using HTTP on TCP port 80:
- *.o.lencr.org
- x1.c.lencr.org
Panorama performs the same check to validate the edge server’s certificate when Panorama imports policy rule recommendations from IoT Security.
After IoT Security identifies and classifies the devices in your network using the Palo Alto Networks firewalls already there—so you don’t have to implement new devices or third-party solutions—Device-ID can leverage this data to match devices with policy rules and provide device context for network events. Through the visibility that the firewall or Panorama provides for traffic, apps, users, devices, and threats, you can instantly trace network events back to individual devices and obtain Security policy rule recommendations for securing those devices.
All firewall platforms that support PAN-OS 10.0 also support Device-ID and IoT Security with the exception of the VM-50 series, VM-200, and the CN series.
There are six levels of classification (also known as attributes) for devices:
| Attribute | Example |
|---|---|
| Category | Printer |
| Profile | Sharp Printer |
| Model | MX-6070N |
| OS Version | ThreadX 5 |
| OS Family | ThreadX RTOS |
| Vendor | SHARP Corporation |
To obtain policy rule recommendations for devices in your network, the firewall observes traffic to generate Enhanced Application logs (EALs) . The firewall then forwards the EALs to the logging service. IoT Security receives logs from the logging service for analysis, provides IP address-to-device mappings, and generates the latest policy rule recommendations for your devices. Using IoT Security, you can review these policy rule recommendations and create a set of Security policy rules for these devices. After you activate the policy rules in IoT Security, import them to the firewall or Panorama and commit your Security policy.
To identify devices with dynamically assigned network settings, the firewall must be able to observe DHCP broadcast and unicast traffic on your network. IoT Security also supports static IP devices. The more traffic the firewall can observe, the more accurate the policy rule recommendations are for the device and the more rapid and accurate the IP address-to-device mappings are for the device. When a device sends DHCP traffic to obtain its network settings, the firewall observes this type of request and generates EALs to send to the logging service, where IoT Security accesses them for analysis.
To observe traffic on an L2 interface, you must configure a VLAN for that interface. By allowing the firewall to treat the interface as an L3 interface for a DHCP relay, it can observe the DHCP broadcast traffic without impacting traffic or performance.
Because the firewall needs to both detect the devices based on their traffic and then enforce Security policy for those devices, the firewall acts as both a sensor to collect metadata from devices and an enforcer by enforcing your Security policy for the devices. IoT Security automatically detects new devices as soon as they send DHCP traffic and can identify 95% of devices within the first week.
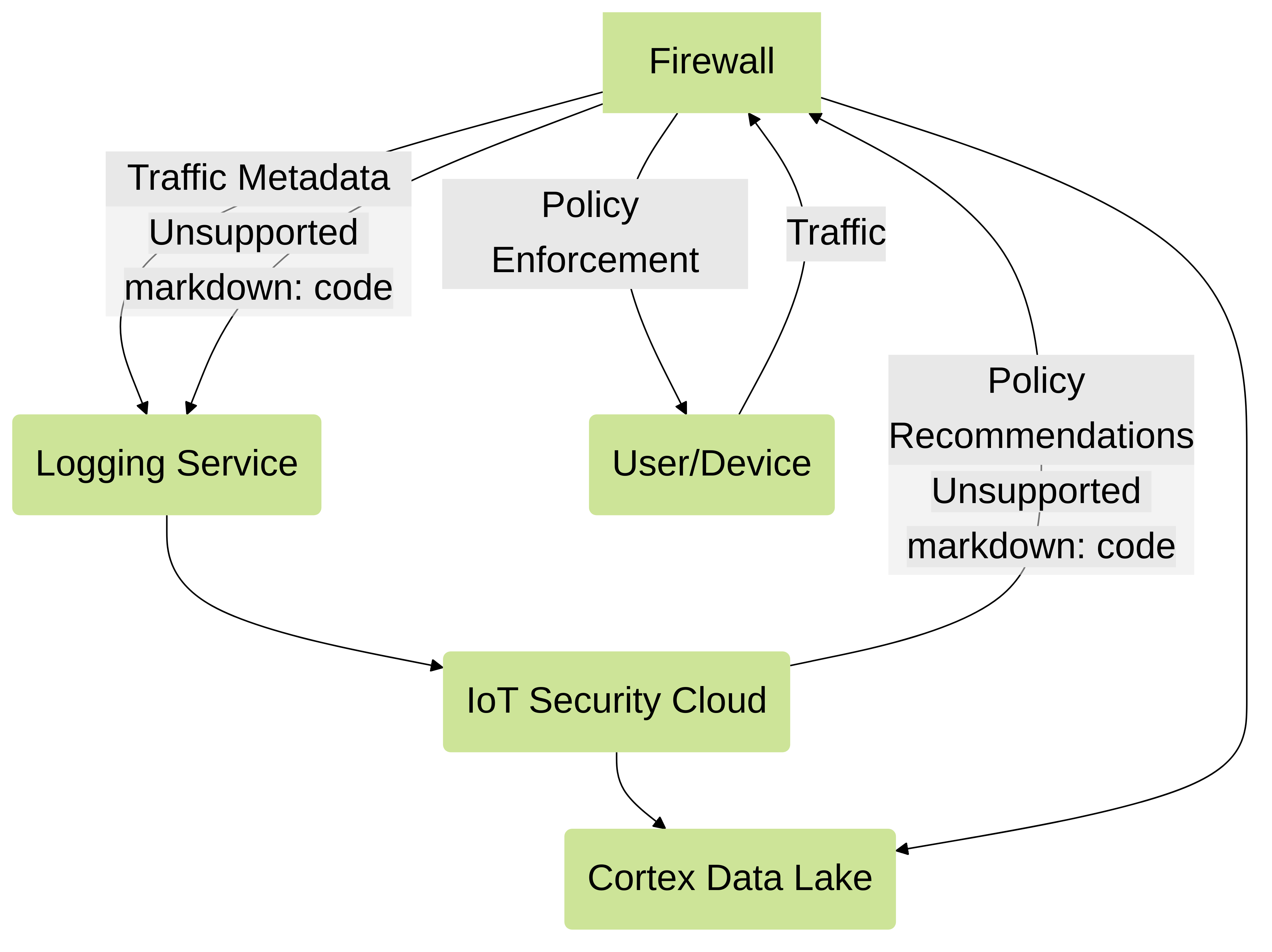
Conceptual data flow illustrating how firewalls act as sensors and enforcers, sending logs to the Logging Service/Cortex Data Lake and IoT Security, which then provides policy recommendations and device mappings back to the firewall.
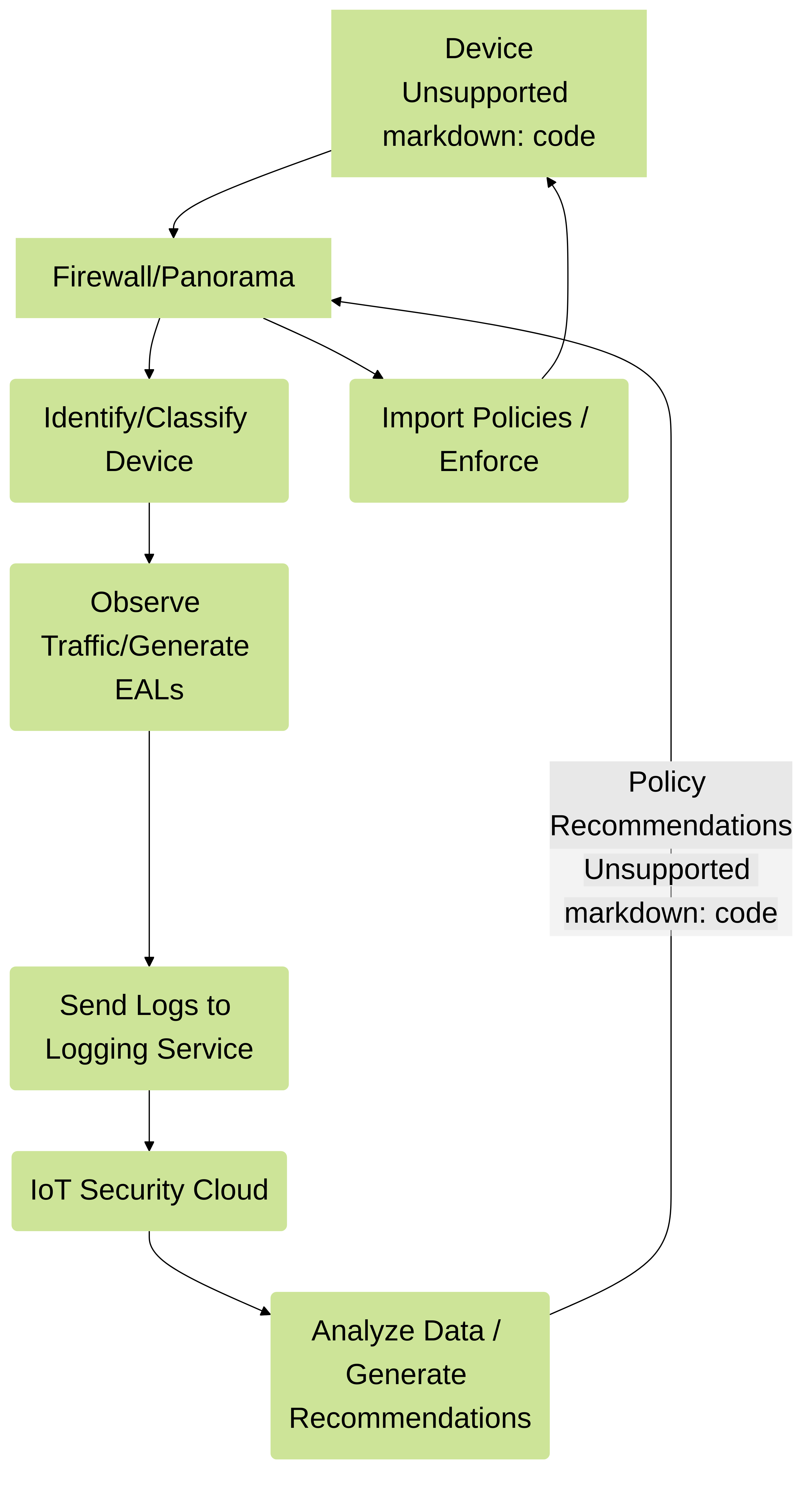
Workflow illustrating the Device-ID process from device traffic observation to policy enforcement.
Each application has an individual recommendation that automatically gets pushed to the firewall or Panorama as a rule when you activate its Security policy rule set in IoT Security. After you import a policy rule recommendation into the Security policy rulebase , the firewall or Panorama creates at least two objects to define the device behavior from the recommendation:
- A source device object that identifies the device profile where traffic originates
- One or more destination objects that identify the permitted destinations for the traffic, which can be a device profile, IP address, or Fully Qualified Domain Name (FQDN)
If any of the device objects already exist on the firewall or Panorama, the firewall or Panorama updates the device object instead of creating a new one. You can use these device objects in Security, authentication, decryption, and Quality of Service (QoS) policy rules.
Additionally, the firewall assigns two tags to each rule:
- One that identifies the source device, including the category (such as NetworkDevice - TrendNet ).
- One that indicates that the rule is an IoT policy rule recommendation ( IoTSecurityRecommended ).
Because the tags that the firewall assigns to the rule are the only way to restore your mappings if they become out of sync, do not edit or remove them.
For optimal deployment and operation of Device-ID, we recommend the following best practices:
- Deploy Device-ID on firewalls that are centrally located in your network. For example, if you have a large environment, deploy Device-ID on a firewall that is upstream from the IP address management (IPAM) device. If you have a small environment, deploy Device-ID on a firewall that is acting as a DHCP server. For more deployment suggestions, see IoT Security Deployment Design Guide .
- During initial deployment, allow Device-ID to collect metadata from your network for at least fourteen days. If devices are not active daily, the identification process might take longer.
-
Create device-based policy rules in order from your most to least critical devices. Use the following considerations to prioritize them:
- Class (secure networked devices first)
- Critical devices (such as servers or MRI machines)
- Environment-specific devices (such as fire alarms and badge readers)
- Consumer-facing IoT devices (such as a smart watch or smart speaker)
- Enable Device-ID on a per-zone basis for internal zones only.
Prepare to Deploy Device-ID
To prepare your network for Device-ID deployment, complete the following predeployment tasks to enable your firewall to generate and send Enhanced Application logs (EALs) through the logging service to IoT Security for processing and analysis.
The device certificate authenticates the firewall when connecting to the logging service and IoT Security.
If you use Panorama to manage multiple firewalls, Palo Alto Networks strongly recommends upgrading all firewalls in your Device-ID deployment to PAN-OS 10.0 or later. If you create a rule that uses Device as a match criteria and Panorama pushes the rule to a firewall that uses PAN-OS 9.1 or an earlier version, the firewall omits the Device match criteria because it is not supported, which might cause issues with policy rule traffic matching.
- Install a device license and a logging service license on your firewalls.
To do this, click Device > Licenses , and then select Retrieve license keys from license server in the License Management section. This installs the licenses for the logging service and IoT Security on the firewall.
- The logging service license permits a firewall to connect to the logging service.
- The device license permits a firewall to connect to IoT Security.
- ( L2 interfaces only ) Create a VLAN interface for each L2 interface so the firewall can observe the DHCP broadcast traffic.
- ( Optional ) Configure service routes to allow the necessary traffic for Device-ID and IoT Security.
By default, the firewall uses the management interface. To use a different interface, complete the following steps.
- If necessary, configure the data interface you want to use as the source interface for required IoT Security communications.
- Select Device > Setup > Services > Service Route Configuration and then select Customize .
- On the IPv4 tab, select Data Services and then choose the data interface you want to use as the Source Interface.
Its IP address autofills the Source Address field. This service route is for forwarding enhanced application logs (EALs) to the logging service.
Device-ID and IoT Security do not support IPv6.
- Click OK .
- Click IoT , choose the same data interface as the Source Interface, and then click OK .
This service route is for pulling IP address-to-device mappings and policy recommendations from IoT Security.
- Click Palo Alto Networks Services , choose the same data interface, and then click OK .
This service route is for forwarding other logs besides EALs to the logging service and for pulling device dictionary files from the update server.
- Click OK to save your configuration changes.
- ( Optional ) If you created service routes in the previous step, add Security policy rules permitting services required for the firewall to use IoT Security.
- Select Policies > Security > + Add .
- On the General tab, enter a name for the Security policy rule and choose interzone as the Rule Type.
- On the Source tab, select Any as the source zone and then Add 127.168.0.0/16 as the source address.
- On the Destination tab, Add the destination zone with IoT Security, and Add the edge services FQDN for your region as the destination address.
- On the Application tab, Add paloalto-iot-security .
The firewall uses this application to pull IP address-to-device mappings and policy recommendations from IoT Security.
- On the Actions tab, choose Allow and then click OK .
- If you have an intranet policy rule that allows all intranet traffic in the zone where the logging service and update server are, you can use that rule to allow the firewall to forward logs to the logging service and pull dictionary files from the update server.
Otherwise, create an intranet policy rule that allows the firewall to send these three applications to the logging service and update server from the IP address of the firewall interface in the same zone:
- paloalto-shared-services to forward EALs and session logs to the logging service
- paloalto-logging-service to forward other logs besides EALs to the logging service
- paloalto-updates to pull device dictionary files from the update server
- If there’s a third-party firewall between the internet and Panorama and Panorama-managed next-generation firewalls, make sure it allows the necessary traffic for Device-ID and IoT Security.
| Purpose | Address | TCP Port |
|---|---|---|
| ( PAN-OS versions 10.0.3 and later ) Receive the regional FQDN allowing next-generation firewalls to retrieve IP address-to-device mappings and policy rule recommendations from IoT Security. | enforcer.iot.services-edge.paloaltonetworks.com | 443 |
| ( PAN-OS versions 10.0.0 and later ) Let next-generation firewalls receive policy rule recommendations and IP address-to-device mappings from IoT Security. |
United States:
iot.services-edge.paloaltonetworks.com
Canada: ca.iot.services-edge.paloaltonetworks.com EU region: eu.iot.services-edge.paloaltonetworks.com Asia-Pacific region: apac.iot.services-edge.paloaltonetworks.com Japan: jp.iot.services-edge.paloaltonetworks.com Australia: au.iot.services-edge.paloaltonetworks.com |
443 |
| ( PAN-OS versions 10.0.0 and later ) Let next-generation firewalls download device dictionary files from the update server. | updates.paloaltonetworks.com | 443 |
| ( PAN-OS versions 10.0.0 and later ) Let Panorama send queries for logs to the logging service. |
United States:
iot.services-edge.paloaltonetworks.com
Canada: ca.iot.services-edge.paloaltonetworks.com EU region: eu.iot.services-edge.paloaltonetworks.com Asia-Pacific region: apac.iot.services-edge.paloaltonetworks.com Japan: jp.iot.services-edge.paloaltonetworks.com Australia: au.iot.services-edge.paloaltonetworks.com |
443 |
| ( IoT Security subscription + Cortex Data Lake ) Forward logs to Cortex Data Lake. | See TCP Ports and FQDNs Required for Cortex Data Lake . | |
- PAN-OS versions 10.0.0 - 10.0.2 connect to the edge services FQDN in the Americas region by default ( iot.services-edge.paloaltonetworks.com ). For firewalls running these PAN-OS versions to connect to the edge services FQDN in other regions, you must manually configure it (see the FQDNs in the next step). For PAN-OS versions 10.0.3 and later, firewalls automatically discover the correct FQDN to use based on the region set during the IoT Security onboarding process. There is no need to set it manually.
- If there’s a third-party firewall between the internet and next-generation firewalls (without Panorama), make sure it allows the necessary traffic for Device-ID and IoT Security.
| Purpose | Address | TCP Port |
|---|---|---|
| ( PAN-OS versions 10.0.3 and later ) Receive the regional FQDN allowing next-generation firewalls to retrieve IP address-to-device mappings and policy rule recommendations from IoT Security. | enforcer.iot.services-edge.paloaltonetworks.com | 443 |
| ( PAN-OS versions 10.0.0 and later ) Let next-generation firewalls receive policy rule recommendations and IP address-to-device mappings from IoT Security. |
United States:
iot.services-edge.paloaltonetworks.com
Canada: ca.iot.services-edge.paloaltonetworks.com EU region: eu.iot.services-edge.paloaltonetworks.com Asia-Pacific region: apac.iot.services-edge.paloaltonetworks.com Japan: jp.iot.services-edge.paloaltonetworks.com Australia: au.iot.services-edge.paloaltonetworks.com |
443 |
| ( PAN-OS versions 10.0.0 and later ) Let next-generation firewalls download device dictionary files from the update server. | updates.paloaltonetworks.com | 443 |
| ( IoT Security subscription + Cortex Data Lake ) Forward logs to Cortex Data Lake. | See TCP Ports and FQDNs Required for Cortex Data Lake . | |
- Configure your firewall to observe and generate logs for DHCP traffic then forward the logs for processing and analysis by IoT Security.
-
If the firewall is acting as a DHCP server:
- Enable Enhanced Application logging.
- Create a Log Forwarding profile to forward the logs to the logging service for processing.
- Enable the DHCP Broadcast Session option ( Device > Setup > Session > Session Settings ).
This setting is supported from PAN-OS 11.0.1 on the PA-5450 and PA-7000 series and on all other firewalls running any version of PAN-OS 11.0.
- Create a Security policy rule to allow dhcp as the Application type.
- If the firewall is not a DHCP server, configure an interface as a DHCP relay agent so that the firewall can generate EALs for the DHCP traffic it receives from clients.
-
If your DHCP server is on the same network segment as the interface your firewall,
deploy a virtual wire interface
in front of the DHCP server to ensure the firewall generates EALs for all packets in the initial DHCP exchange with minimal performance impact.
- Configure a virtual wire interface with corresponding zones and enable the Multicast Firewalling option ( Network > Virtual Wires > Add ).
- Configure a rule to allow DHCP traffic to and from the DHCP server between the virtual wire zones. The policy must allow all existing traffic that the server currently observes and use the same Log Forwarding profile as the rest of your rules.
- To allow the DHCP servers to check if an IP address is active before assigning it as a lease to a new request, configure a rule to allow pings from the DHCP server to the rest of the subnet.
- Configure a rule to allow all other traffic to and from the DHCP server that does not forward logs for traffic matches.
- Configure the DHCP server host to use the first virtual wire interface and the network switch to use the second virtual wire interface. To minimize cabling, you can use an isolated VLAN in the switching infrastructure instead of connecting the DHCP server host directly to the firewall.
-
If you want to use a
tap interface
to gain visibility into DHCP traffic that the firewall doesn’t usually observe due to the current configuration or topology of the network, use the following configuration as a best practice.
- Configure a tap interface and corresponding zone.
- Configure a rule to match DHCP traffic that uses the same Log Forwarding profile as the rest of your rules.
- To minimize the session load on the firewall, configure a rule to drop all other traffic.
- Connect the tap interface to the port mirror on the network switch.
-
If you want to collect data about devices whose network traffic isn’t visible to a firewall, employ one or both of these options:
- Use Encapsulated Remote Switched Port Analyzer (ERSPAN) to send mirrored traffic from a network switch through a Generic Routing Encapsulation (GRE) tunnel to the firewall.
- Configure DHCP servers to send their server logs containing IP address-to-MAC address bindings to the firewall.
- Apply a Log Forwarding profile to your Security policy rules.
Apply a predefined Log Forwarding profile for IoT Security to your rules—or update an existing profile or create a new one—so that they forward the required types of logs to the logging service.
Configure Device-ID
Complete the following tasks to import the IP address-to-device mappings and policy rule recommendations from IoT Security to your firewall or Panorama.
If you use Panorama to manage multiple firewalls, Palo Alto Networks strongly recommends upgrading all firewalls in your Device-ID deployment to PAN-OS 10.0 or a later version. If you create a rule that uses Device as a match criteria and Panorama pushes the rule to a firewall that uses PAN-OS 9.1 or an earlier version, the firewall omits the Device match criteria because it is not supported, which may cause issues with policy rule traffic matching. (This is a repeat from the previous section, reinforcing the point).
- Activate your IoT Security license on the hub.
Follow the instructions that you received in your email to activate your IoT Security license.
Initialize your IoT Security app. For more information, refer to Get Started with IoT Security and IoT Security Best Practices .
- Define your Security policy rules set in IoT Security.
Create a new set of policy rules for the source device object.
For information about creating security policy rule recommendations in IoT Security, refer to Recommend Security Policies .
- Activate the Security policy rules set.
When you activate a policy rules set, IoT Security automatically generates policy rule names by concatenating the policy rules set name with the name of the application in each rule. It then automatically pushes the set of rules to Panorama and all next-generation firewalls subscribed to the IoT Security service.
- Import the policy rule recommendations to the Security policy rulebase on the firewall or in Panorama.
Open or refresh the Policy Recommendation (IoT) page.
When you select Policy Recommendation (IoT), the firewall or Panorama communicates with IoT Security to obtain the latest policy rule recommendations. The policy rule recommendations are not cached on the firewall or Panorama. If you are already on this page when a new policy rule set was activated or modified in IoT Security, refreshing the page retrieves the new or updated recommendations from IoT Security.
- (Firewall) Select Device > Policy > Recommendation (IoT) .
- (Panorama) Select Panorama > Policy > Recommendation (IoT) .
Select policy rule recommendations to import into the Security policy rulebase.
Verify that the destination and permitted applications are correct in each rule you want to import. Then select up to ten policy rule recommendations to import into the rulebase. For Panorama you can import policy rule recommendations into multiple firewall rulebases in multiple device groups.
Select Import Policy Rule(s) , enter the following, and then click OK :
- (Firewall)
Choose the name of a rule in the rulebase after which you want PAN-OS to place the imported rules. If you choose No Rule Selection , the firewall imports the selected rules to the top.
- (Panorama)
Location: Choose one or more device groups where you want to import the policy rules.
Suggested Location: IoT Security learns about zones and device groups in the logs it receives from next-generation firewalls and suggests device groups for various policy rules accordingly. You can choose these suggested device groups among those available in the Location list or any other device groups if you prefer.
Destination Type: Select either Pre-Rulebase to add the recommended policy rules before rules defined locally on a firewall or Post-Rulebase to add them after rules defined locally.
After Rule: Choose a rule after which you want to add the imported rule or rules. If you choose No Rule Selection , the firewall imports the selected rules to the top. This is an optional setting. If you don’t choose a rule, the imported rules are added to the top of the rulebase.
Device-ID rules must precede any existing rules that apply to the same devices in the rulebase. Because IoT Security creates the policy rule recommendation using the trusted behaviors for the device, the default action for each rule is allow .
Repeat this process to import more rules to allow devices to communicate with the specified destinations with the specified applications.
Click OK and Commit your changes.
- Enable Device-ID in each zone where you want to use Device-ID to detect devices and enforce your Security policy rules.
By default, Device-ID maps all subnetworks in the zones where you enable it. You can modify which subnetworks Device-ID maps in the Include List and Exclude List.
As a best practice, enable Device-ID in the source zone to detect devices and enforce Device-ID Security policy rules. Only enable Device-ID for internal zones.
- Select Network > Zones .
- Select the zone where you want to enable Device-ID.
- Enable Device Identification then click OK .
Repeat this as necessary for other zones for which you want to enforce Device-ID Security policy rules.
Commit your changes.
- Verify your Security policy rules are correct.
Select Policies and then select one of the rules you created from the policy rule recommendations.
IoT Security assigns a Description that contains the source device object and Tags to identify the source device object and that this rule is a recommendation from IoT Security.
- Select the Source tab, then verify the source device profile.
- Select the Destination tab and verify the destination.
- Select the Application tab and verify the application.
- Select the Actions tab and verify the action (default is Allow).
- Use Explore to verify that the logging service receives your logs and review which logs it gets.
- Create custom device objects for any devices that do not have IoT Security policy rule recommendations.
For example, you cannot secure traditional IT devices such as laptops and smartphones using policy rule recommendations, so you must manually create device objects for these types of devices to use in your Security policy rules. For more information on custom device objects, see Manage Device-ID .
- Use the device objects to enforce policy rules and monitor and identify potential issues.
The following list includes some example use cases for device objects.
- Use source device objects and destination device objects in Security, Authentication, QoS, and decryption policies.
- Use the decryption log to identify failures and which assets are the most critical to decrypt.
- View device object activity in ACC to track new devices and device behavior.
- Use device objects to create a custom report (for example, for incident reports or audits).
Manage Device-ID
Perform the following tasks as needed to ensure your policy rule recommendations and device objects are current or to restore policy rule recommendation mappings.
- Update your policy rule recommendations as necessary.
As IoT devices gain new capabilities, IoT Security updates its policy rule recommendations to advise what additional traffic or protocols firewalls should allow. Check IoT Security daily for changes and update your policy rule recommendations as soon as possible. The update procedure differs depending on whether you’re using Panorama to manage your firewalls.
When using firewalls with Panorama management:
- ( IoT Security ) Edit the policy rules in an activated policy rules set and then click Next .
- Select any new recommendations, click Next , and then Save your changes.
- ( Panorama ) Select Panorama > Policy > Recommendation (IoT) and then Import Policy Rules .
- Choose one or more device groups and then click Yes to confirm that you want to overwrite current rule recommendations and previously imported rules in the rulebase.
- Commit your changes.
When using firewalls without Panorama management:
- ( IoT Security ) Edit the policy rules in an activated policy rules set and then click Next .
- Select any new recommendations, click Next , and then Save your changes.
- ( PAN-OS UI ) Select Device > Policy > Recommendation (IoT) , note details of any policy rule recommendations with Yes in the New Updates Available column, and then edit and save the corresponding imported policy rule on the Policies page.
- Select Device > Policy > Recommendation (IoT) and then Sync Policy Rules to refresh the mapping between the edited rules and the rule recommendations.
When the corresponding rules on the Policies page and Policy Recommendation (IoT) page match, the New Updates Available column changes from Yes to No .
- Commit your changes.
- Review, update, and maintain the device objects in the Device Dictionary.
You must create device objects for any devices that do not have an IoT Security policy rule recommendation. For example, you cannot secure traditional IT devices such as laptops and smartphones using IoT Security policy rule recommendations, so you must create device objects for these types of devices and use them in your Security policy to secure these devices.
- Select Objects > Devices .
- Add a device object.
- Browse the list or Search using keywords.
The search results can include multiple types of device object attributes (for example, both Category and Profile ).
- To add a custom device object, enter a Name and optionally a Description for the device object.
Always use a unique name for each device object. Do not change the tags in the description for device objects from policy rule recommendations.
- ( Panorama only ) Select the Shared option to make this device object available to other device groups.
- Select the attributes for the device object ( Category , OS , Profile , OS Family , Model , and Vendor ).
- Click OK to confirm your changes.
- Delete any policy rule recommendations that are no longer needed.
If policy rule recommendations no longer apply, you can remove the recommendations and the rules mapped to the recommendations.
- In IoT Security, delete one or more policy rule recommendations from a policy rule set.
Edit the policy set, clear the policy rules you want to remove, and then Save the policy set.
- Remove the mapping between rule recommendations and the related rules in the rulebase.
( Firewall ) Select Device > Policy > Recommendation (IoT) , select up to ten policy rule recommendations to remove, and then Remove Policy Mapping .
( Panorama ) Select Device > Policy > Recommendation (IoT) , select up to ten policy rule recommendations to remove, Remove Policy Mapping , and then select the Location from which you want to remove the mapping.
- Click Yes to confirm the mapping removal.
- Select Policies > Security . For Panorama, select Policies > Security > Pre-Rules/Post-Rules .
- Select the rules you want to remove from the rulebase and then Delete them.
- Commit your changes.
- Use CLI commands to troubleshoot any issues between the firewall and IoT Security.
CLI Commands for Device-ID
Use the following CLI commands to view information for troubleshooting any issues between the firewall and IoT Security. In general, CLI commands that include eal show counters for outgoing data and CLI commands that include icd show counters for incoming data.
| Example | Command |
|---|---|
| View Enhanced Application Logging (EAL) counters, such as the number of connections between the firewall and the Cortex Data Lake and the volume of the logs. | show iot eal all |
| View more details about the connection between the firewall and Cortex Data Lake. | show iot eal conn |
| View a summary of the EAL counters by plane (dataplane or management plane), such as the PAN-OS version and serial number. | show iot eal dpi-eal |
| View EAL counters by plane (dataplane or management plane) and by protocol. | show iot eal dpi-stats all |
| View EAL counters by protocol. | show iot eal dpi-stats subtype dhcp|http |
| View a summary of Host Information Profile (HIP) Match report counters. | show iot eal hipreport-eal |
| View EAL log response time counters. | show iot eal response-time |
| View details for the health of the connection to the edge service between the firewall and the IoT Security app and counters for the IP address-to-device mappings and policy rule recommendations. | show iot icd statistics all |
| View counters for the connection to the edge service. | show iot icd statistics conn |
| View counters for the IP address-to-device mappings. | show iot icd statistics verdict |
| View all IP address-to-device mappings on the management plane. | show iot ip-device-mapping-mp all |
| View the IP address-to-device mapping for a specific IP address. | show iot ip-device-mapping-mp ip <IP-address> |
| View a list of IP address-to-device mappings on the data plane. | show iot ip-device-mapping all |
| Clear the IP address-to-device mappings on the management plane. | debug iot clear-all type device |
| Clear the IP address-to-device mappings on the data plane. | clear user-cache all |
Device-ID Quiz
Test your knowledge on Palo Alto Networks Device-ID.