🔐 Mastering IoT Security: Best Practices and PCNSE Preparation
Introduction to IoT Security
The Internet of Things (IoT) has revolutionized industries, connecting billions of devices and generating massive amounts of data. However, this interconnectedness introduces significant security challenges. Securing the IoT landscape requires a comprehensive strategy that addresses the unique vulnerabilities and threats posed by these devices. This guide delves into IoT security best practices, aligning them with the PCNSE (Palo Alto Networks Certified Network Security Engineer) exam objectives, and provides practical examples and interactive exercises to solidify your understanding.
Planning Your IoT Security Deployment
Effective IoT security begins with a well-defined plan. This phase involves understanding your environment, defining objectives, and establishing a roadmap for implementation.
-
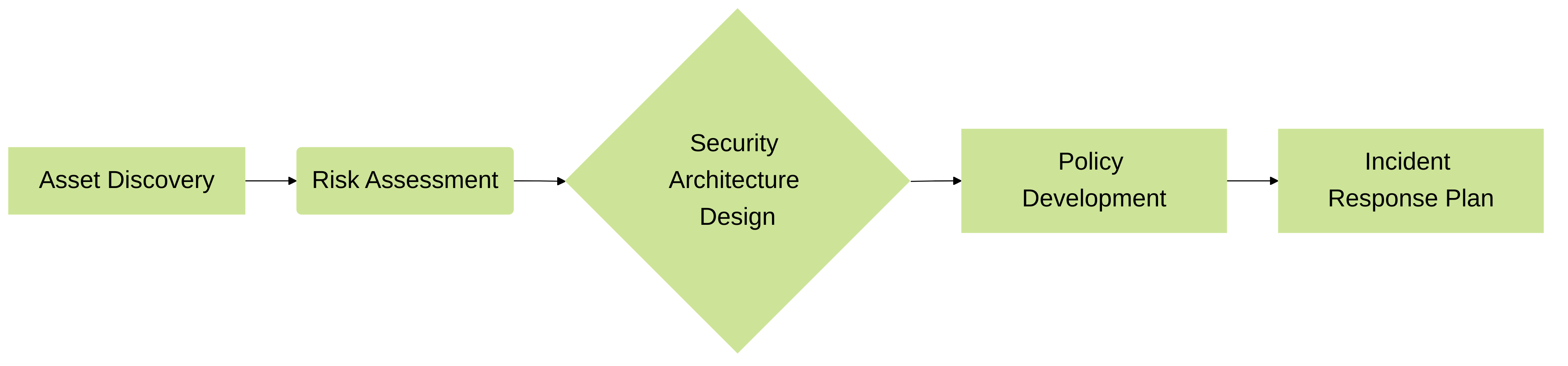
Asset Discovery and Classification:
Identify all IoT devices connected to your network and categorize them based on function, criticality, and risk profile. Tools like the Palo Alto Networks IoT Security module can automate this process.
Gotcha! Simply knowing the number of IoT devices isn't enough. PCNSE questions often focus on understanding the risk associated with different device types and their communication patterns.
- Risk Assessment: Evaluate potential threats and vulnerabilities associated with each device category. Consider factors such as default credentials, insecure communication protocols, and lack of firmware updates. Use vulnerability scanners and penetration testing to identify weaknesses.
- Security Architecture Design: Define the security controls and technologies required to protect IoT devices. This includes network segmentation, access control policies, intrusion prevention systems, and security information and event management (SIEM) solutions.
-
Policy Development:
Develop granular security policies that restrict device communication to only necessary protocols and destinations. Leverage the principle of least privilege.
PCNSE Exam Note: Be prepared to analyze and troubleshoot security policies related to IoT devices.
- Incident Response Plan: Establish a clear plan for handling security incidents involving IoT devices. This should include steps for containment, eradication, and recovery.
IoT Security Planning Process
Deploying IoT Security Effectively with Palo Alto Networks
Palo Alto Networks offers a comprehensive suite of solutions for securing IoT environments. This section focuses on leveraging these tools for effective deployment.
-
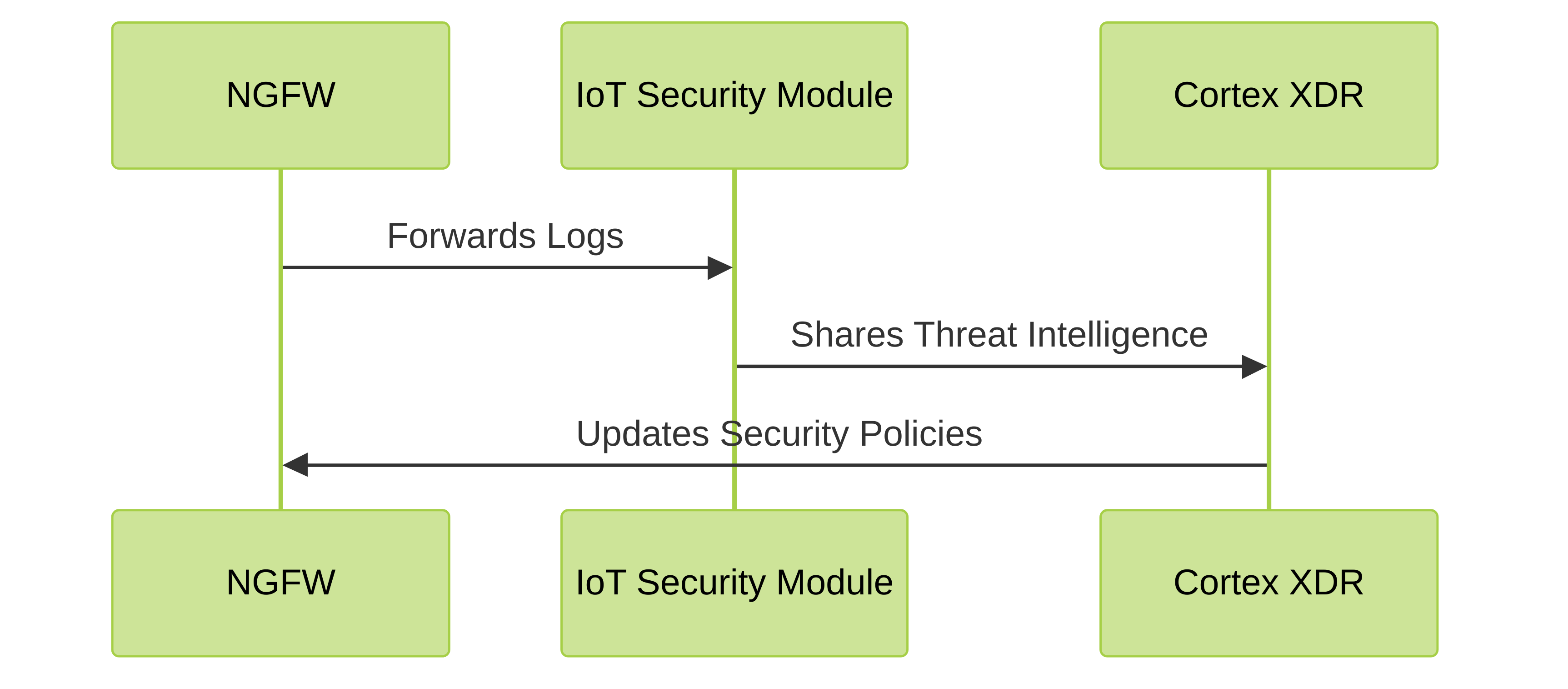
IoT Security Module:
This module provides visibility and control over IoT devices. It uses machine learning to identify devices, analyze their behavior, and recommend security policies.
PCNSE Exam Note: Understanding the functionality and configuration of the IoT Security module is essential.
- Next-Generation Firewalls (NGFWs): NGFWs enforce security policies and prevent unauthorized access to IoT devices. Features like App-ID, User-ID, and Content-ID enable granular control over traffic.
- Cortex XDR: This platform provides advanced threat detection and response capabilities. It integrates with IoT Security to provide a unified security posture across the network and endpoints.
- Zero Trust Segmentation: Segment the network to isolate IoT devices from critical systems. Implement micro-segmentation to control communication between individual devices.
-
Automated Policy Enforcement:
Use dynamic address groups and security policy rules to automatically apply appropriate security measures based on device identification and risk profile.
Gotcha! Be mindful of potential performance impacts when deploying highly granular policies.
Interaction between Palo Alto Networks Security Components
Monitoring and Maintaining IoT Security
Continuous monitoring and maintenance are critical for ensuring the effectiveness of your IoT security posture.
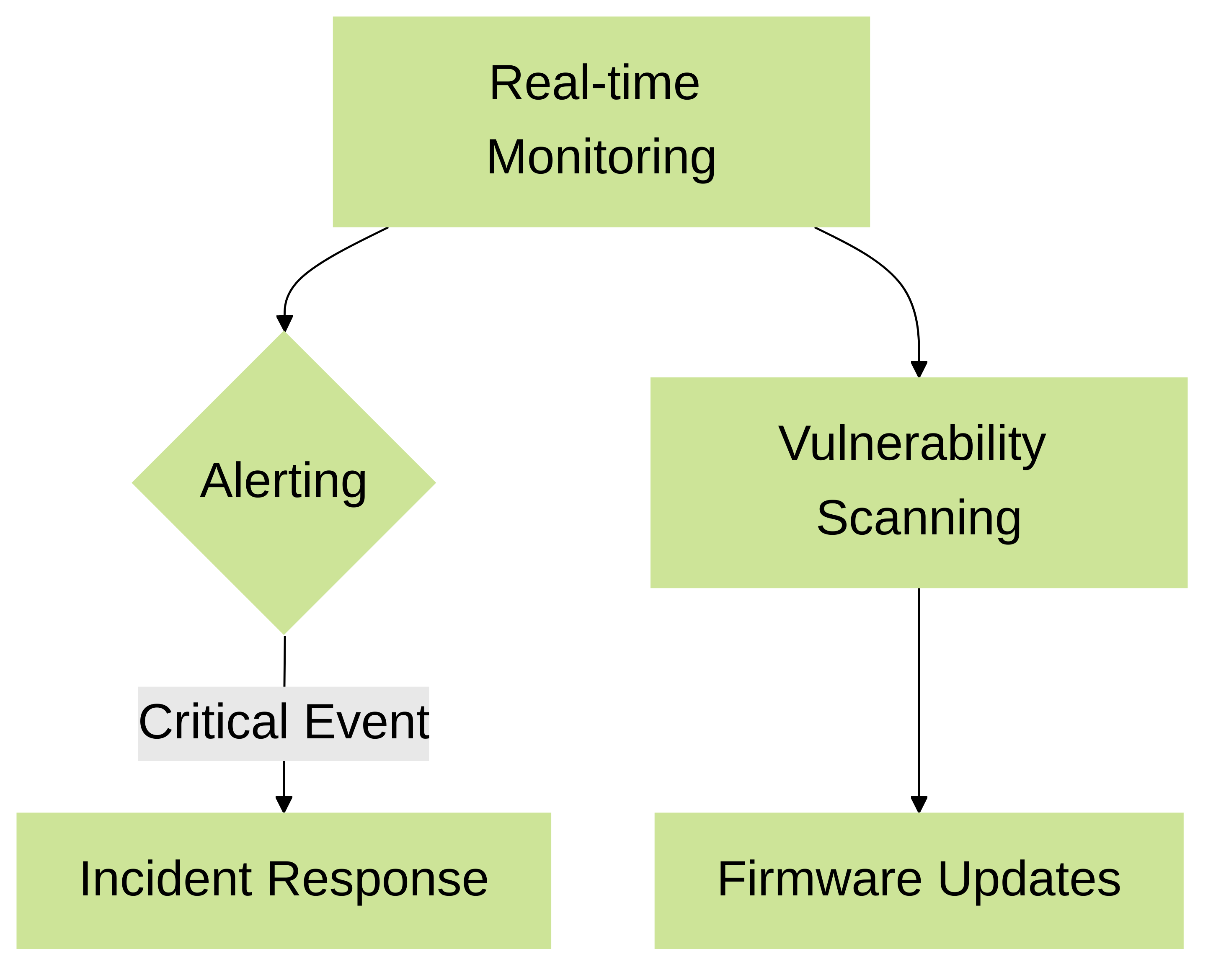
- Real-time Monitoring: Utilize dashboards and reports provided by the IoT Security module to track device activity, identify anomalies, and monitor security events.
- Alerting and Notifications: Configure alerts for critical security events and ensure prompt response. Integrate with SIEM solutions for centralized event management.
- Regular Vulnerability Scanning: Conduct regular vulnerability scans to identify and address weaknesses in IoT devices. Utilize tools that are specifically designed for IoT environments.
-
Firmware Updates:
Implement a process for patching and updating firmware on IoT devices. This is crucial for mitigating known vulnerabilities.
Gotcha! Firmware updates can be challenging in large IoT deployments. Consider using automated patching solutions.
-
Security Audits:
Perform periodic security audits to assess the effectiveness of your IoT security strategy and identify areas for improvement.
PCNSE Exam Note: Be familiar with security audit best practices and common auditing tools.
IoT Security Monitoring and Maintenance Workflow
Configuring Firewalls for Device-ID™
The Device-ID™ feature on Palo Alto Networks firewalls plays a vital role in identifying and classifying IoT devices. Proper configuration is essential for leveraging its full potential.
- Enhanced Application Logging (EAL): Enable EAL to capture detailed information about network traffic, which is crucial for device identification.
- DHCP Monitoring: Monitor DHCP traffic to map IP addresses to MAC addresses, aiding in device identification.
- Device Identification on Zones: Enable Device-ID™ on relevant firewall zones where IoT device traffic is present.
- Service Routes: Configure service routes to ensure communication between the firewall and the IoT Security cloud service.
- Security Policy Rules: Create security policy rules to allow necessary traffic for Device-ID™ and IoT Security operations.
Device-ID™ Workflow on Palo Alto Networks Firewalls