Palo Alto Networks Group Mapping Methods: A Comprehensive Guide for PCNSE
Overview of User-ID and Group Mapping
In the Palo Alto Networks security platform, User-ID is a foundational technology that enables visibility and control over network traffic based on user identity rather than just IP addresses. A critical component of User-ID is Group Mapping , which allows PAN-OS Next-Generation Firewalls (NGFWs) and Panorama to integrate with enterprise directory services to retrieve user group membership information. This information is then used to enforce granular security policies, simplify administration, and enhance reporting.
By basing policies on groups, administrators can manage access dynamically. When a user's role changes and they are moved to a different group in the directory service, their network access permissions, as defined by Palo Alto Networks security policies, update automatically without requiring manual changes to firewall rules. This is significantly more scalable and efficient than managing policies based on individual user accounts, especially in large or rapidly changing organizations.
Core Group Mapping Methods in PAN-OS
PAN-OS offers several methods to map users to groups, primarily leveraging existing directory services. The choice of method depends on the organization's infrastructure, directory type, and specific security requirements.
1. LDAP-Based Group Mapping
This is the most common method for integrating with on-premises directory services like Microsoft Active Directory, OpenLDAP, or Novell eDirectory. The Palo Alto Networks firewall directly queries the LDAP server(s) to fetch user and group information.
Key Concepts and Configuration:
-
LDAP Server Profile:
This profile (configured under
Device > Server Profiles > LDAP) contains the necessary information for the firewall to connect and authenticate to the LDAP server. This includes:- Server List: IP addresses or FQDNs of LDAP servers. Up to four servers can be configured for redundancy. The firewall will try them in order.
- Port: Typically 389 for LDAP or 636 for LDAPS (LDAP over SSL/TLS). For Active Directory Global Catalog, ports are 3268 (GC) and 3269 (GCS).
-
Type:
Pre-defined types like
active-directory,edirectory,sun-directory-server,open-ldap, orcustom. Selecting the correct type pre-populates some attribute fields. -
Base DN (Distinguished Name):
The starting point in the LDAP directory tree from which the firewall will search for users and groups. Example:
DC=example,DC=comfor an Active Directory domain namedexample.com.Gotcha! (Palo Alto Networks): An incorrect Base DN is a common cause of group mapping failures. Ensure it accurately reflects the top level of your directory structure where relevant users and groups reside. - Bind DN and Password: Credentials of a service account used by the firewall to bind (authenticate) to the LDAP server. This account needs sufficient permissions to read user and group attributes. Best practice is to use a dedicated service account with read-only access.
- SSL/TLS Encryption: Recommended for securing LDAP communication. Requires selecting LDAPS port and potentially importing the CA certificate of the LDAP server if it's signed by an internal CA.
- Verify Server Certificate: If SSL/TLS is used, this option ensures the firewall validates the LDAP server's certificate.
- Permit Unauthenticated Access: Rarely used and generally not recommended for security reasons. It allows binding without credentials, typically for read-only public LDAP directories.
-
Group Mapping Settings:
Configured under
Device > User Identification > Group Mapping Settings. Here, you link an LDAP Server Profile to a group mapping configuration.- Group Include List: Specifies which LDAP groups the firewall should retrieve and make available for policy. This is crucial for performance and manageability, as it prevents the firewall from fetching all groups from the directory.
- Custom Search Filter (LDAP Query): An advanced option to define a specific LDAP query to find groups. This overrides the Group Include List if used.
-
Object Class (Group):
Defines the LDAP object class for groups (e.g.,
groupfor AD). - User Domain: Can be used to override or set the domain name for users retrieved through this mapping, important in multi-domain environments.
- Update Interval: How often (in seconds) the firewall refreshes group information from the LDAP server. Default is 3600 seconds (1 hour). Frequent changes may require a shorter interval, but too short can increase load on the firewall and LDAP server.
-
User and Group Attributes:
Defines which LDAP attributes correspond to usernames and group memberships (e.g.,
sAMAccountNamefor username,memberormemberOffor group membership in Active Directory). PAN-OS uses these attributes to correctly parse the information returned by the LDAP server.-
Primary Username:
Typically
sAMAccountNamefor AD. -
Alternate Usernames:
Attributes like
userPrincipalName,mail. This allows users to be identified by different usernames they might use. -
Group Name:
Typically
cn(Common Name) orsAMAccountNamefor groups in AD. -
Group Member:
Typically
memberfor groups, ormemberOffor users (if using user-centric queries, less common for group mapping itself).
-
Primary Username:
Typically
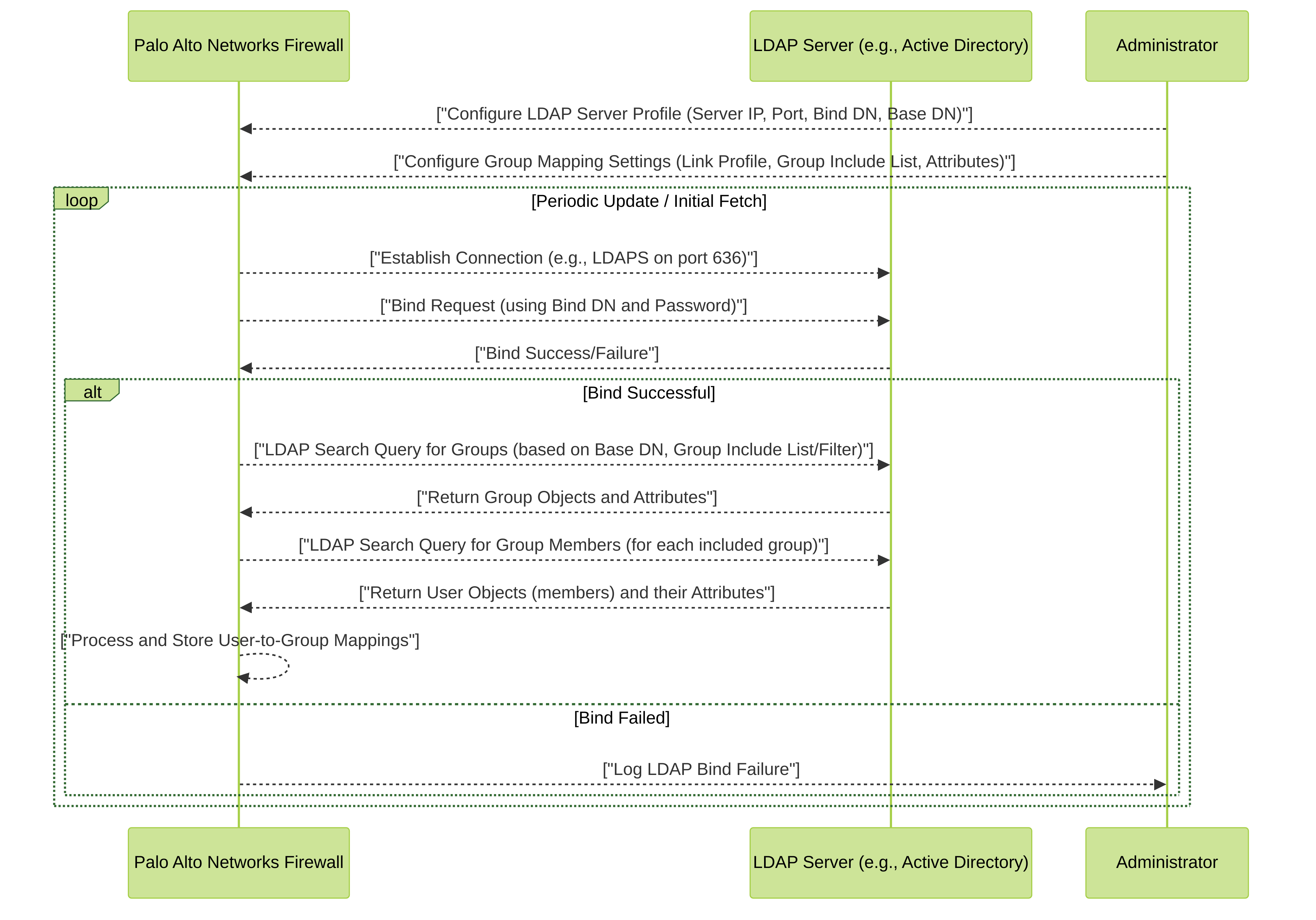
Detailed flow of LDAP-based group mapping where the Palo Alto Networks firewall queries an LDAP server to retrieve group and user membership information after initial configuration by an administrator.
sAMAccountName
,
userPrincipalName
,
memberOf
) and group attributes (like
cn
,
member
). Typically, domain user privileges are sufficient, but explicit read access to relevant OUs is best practice.
2. Custom Group Mapping (Using LDAP Filters on the Firewall)
This method is an extension of LDAP-based group mapping. Instead of relying solely on pre-existing groups in the LDAP directory, administrators can define "custom groups" directly on the Palo Alto Networks firewall using LDAP filters. These custom groups are formed by users who match specific attribute criteria defined in the filter.
Key Characteristics:
- No Directory Changes Needed: Custom groups are defined on the firewall; no new groups need to be created in the LDAP directory.
- Flexibility: Allows grouping users based on attributes that might not be used for standard group definitions (e.g., department, office location, specific project flags).
-
Configuration:
Defined within the Group Mapping settings (
Device > User Identification > Group Mapping Settings) by specifying an LDAP filter in the "Custom Groups" tab.- Group Name: A name you assign to this custom group on the firewall.
-
LDAP Filter:
An LDAP search filter that identifies users belonging to this custom group. For example:
-
(&(objectCategory=person)(objectClass=user)(department=Engineering))- Creates a group of all users in the Engineering department. -
(&(objectCategory=person)(objectClass=user)(physicalDeliveryOfficeName=NewYork))- Creates a group of users in the New York office.
-
When a custom group is defined, the firewall queries the LDAP server using the specified filter. Users matching the filter are considered members of this firewall-defined custom group. These groups can then be used in security policies just like groups retrieved directly from LDAP.
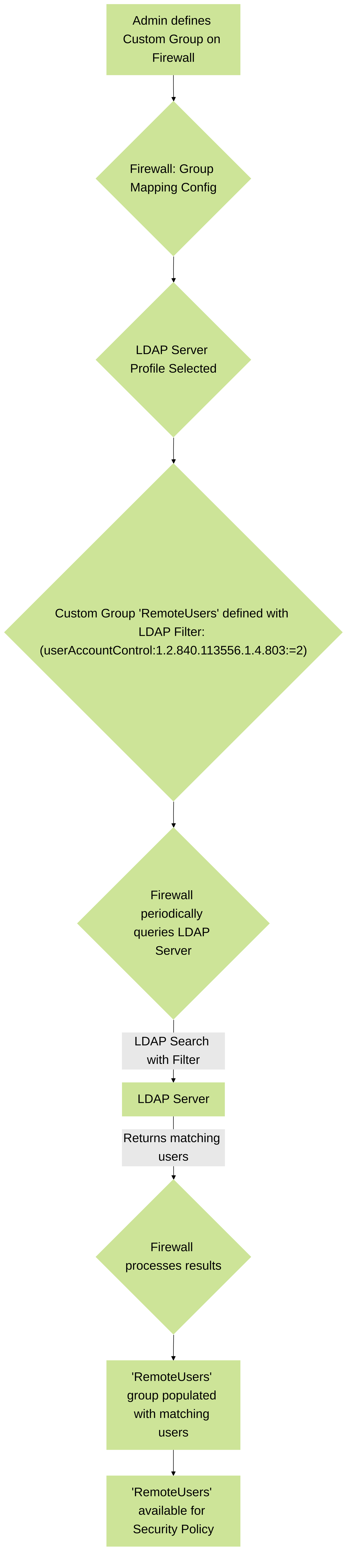
Flow for defining and using custom groups on a Palo Alto Networks firewall. The firewall uses an admin-defined LDAP filter to query the directory and dynamically create a group usable in policies.
3. Cloud Identity Engine (CIE)
The Palo Alto Networks Cloud Identity Engine (CIE) provides a scalable, cloud-based solution for identity information, including group memberships. It allows PAN-OS devices (NGFWs, VM-Series, CN-Series, Prisma Access) to retrieve user and group information from various cloud-based and on-premises identity providers (IdPs) without requiring direct connectivity from each firewall to every IdP.
Key Features and Benefits:
- Centralized Identity: CIE acts as a central broker for identity information. It connects to your IdPs (e.g., Azure AD, Okta, Google Workspace, SAML 2.0 IdPs, SCIM) and makes this information available to subscribed Palo Alto Networks security platforms.
- Scalability and Simplicity: Simplifies configuration, especially in large or distributed environments. Instead of configuring LDAP profiles on numerous firewalls, you configure them to subscribe to CIE.
- Cloud-Native Integration: Ideal for organizations using cloud-based directories and services.
- Dynamic Updates: CIE can receive real-time or near real-time updates from IdPs (e.g., via SCIM), ensuring that group membership changes are quickly reflected in policies.
-
Supported Sources:
- Microsoft Azure Active Directory
- Okta
- Google Workspace
- SAML 2.0 based IdPs (for user attributes)
- SCIM (System for Cross-domain Identity Management) for provisioning users and groups into CIE
- On-premises Active Directory (often via Azure AD Connect or specific CIE agents/integrations)
How it Works:
- CIE Configuration: Administrator configures CIE (typically via the Palo Alto Networks cloud services portal/hub) to connect to various IdPs. CIE fetches and aggregates user and group data.
- PAN-OS Device Subscription: Firewalls, Prisma Access, etc., are configured to subscribe to the CIE service. This usually involves registering the device with the cloud service.
- Information Retrieval: The PAN-OS device queries CIE for user-to-group mappings. CIE provides this information based on the data it has collected from the configured IdPs.
- Policy Enforcement: The PAN-OS device uses the retrieved group information to enforce security policies.
_integrating_with_May_19_2025_08-10PM.png)
Architecture of Cloud Identity Engine (CIE) integrating with various IdPs and providing consolidated user and group information to Palo Alto Networks devices.
Detailed Configuration Steps
This section details the configuration process for LDAP-based group mapping on a PAN-OS firewall. Configuration for CIE involves setup within the Palo Alto Networks cloud services portal and then subscribing the firewall to CIE.
A. Configuring an LDAP Server Profile
The LDAP Server Profile is the first component required for LDAP-based group mapping.
-
Navigate to
Device > Server Profiles > LDAPin the PAN-OS web interface. - Click Add at the bottom of the page.
-
Configure the following parameters:
-
Profile Name:
A descriptive name for the profile (e.g.,
AD-Primary-LDAP). -
Server List Tab:
-
Name:
Name for the server entry (e.g.,
DC1). - LDAP Server: IP address or FQDN of the LDAP server.
-
Port:
Enter the appropriate port (e.g.,
389for LDAP,636for LDAPS,3268for Global Catalog,3269for Global Catalog over SSL/TLS). - Click Add to include more servers for redundancy.
-
Name:
Name for the server entry (e.g.,
-
Type:
Select the directory server type (e.g.,
active-directory). This pre-fills some default LDAP attribute names. -
Base DN:
The starting point in the directory for searches. Example:
OU=Users,DC=corp,DC=paloaltonetworks,DC=comor simplyDC=corp,DC=paloaltonetworks,DC=com. -
Bind DN:
The full Distinguished Name (DN) of the service account used for LDAP authentication. Example:
CN=svc-panldap,OU=ServiceAccounts,DC=corp,DC=paloaltonetworks,DC=com. - Password and Confirm Password: The password for the Bind DN service account.
- Require SSL/TLS encrypted connection: Check this box if using LDAPS (port 636 or 3269).
-
Verify Server Certificate (for SSL/TLS only):
Recommended. If the LDAP server uses a certificate signed by an internal CA, you may need to import that CA certificate into the firewall's certificate store (
Device > Certificate Management > Certificates) and select it in the LDAP Server Profile. - Timeout (sec): Connection timeout for LDAP queries (default is 30 seconds).
- Retry Interval (sec): How long to wait before retrying a failed connection (default is 60 seconds).
- Timelimit (sec): Maximum time the firewall waits for an LDAP query response (default is 30 seconds).
- Bind Timelimit (sec): Maximum time allowed for the bind operation (default is 30 seconds).
-
Profile Name:
A descriptive name for the profile (e.g.,
- Click OK to save the LDAP Server Profile.
DC=domain,DC=com
) is common but can be slow in very large directories if not coupled with efficient filters.
B. Configuring Group Mapping Settings
Once the LDAP Server Profile is created, configure Group Mapping Settings to define how the firewall retrieves and uses group information.
-
Navigate to
Device > User Identification > Group Mapping Settingstab. (On older PAN-OS versions, this might be under the User-ID Agent tab, ensure you are in the correct section for direct firewall group mapping). - Click Add to create a new group mapping configuration.
-
Configure the following parameters in the
Group Mapping
dialog:
-
Name:
A unique name for this group mapping instance (e.g.,
AD-Finance-Groups). - Server Profile: Select the LDAP Server Profile created in the previous step.
-
User Domain:
Optionally specify a domain name. If users log in with
DOMAIN\user, this field can be used to populate the domain part if the directory doesn't provide it in the desired format, or if multiple domains are being aggregated. - Update Interval (sec): How often the firewall queries the LDAP server for group membership updates (default is 3600 seconds).
- Enabled: Ensure this checkbox is selected to activate this group mapping.
-
Group Include List Tab:
-
Click
Add
and enter the Distinguished Names (DNs) of the specific groups you want the firewall to recognize. Example:
CN=FinanceUsers,OU=Departments,DC=corp,DC=paloaltonetworks,DC=com.CRITICAL (Palo Alto Networks): Using a well-defined Group Include List is essential for performance. Only include groups that will be used in security policies. Retrieving all groups from a large directory can severely impact firewall performance and LDAP server load.
-
Click
Add
and enter the Distinguished Names (DNs) of the specific groups you want the firewall to recognize. Example:
-
Custom Search Filter / Custom Groups Tab (Optional):
-
Search Filter (LDAP query):
(Under the "Group Objects" tab, or similar name depending on PAN-OS version for group filtering) An LDAP query to filter which groups are retrieved. E.g.,
(description=PolicyGroup_*)could retrieve all groups whose description starts with "PolicyGroup_". - Custom Groups: (Usually a separate tab or section) As described earlier, to define firewall-local groups based on LDAP attributes. Add a name for the custom group and the LDAP filter criteria.
-
Search Filter (LDAP query):
(Under the "Group Objects" tab, or similar name depending on PAN-OS version for group filtering) An LDAP query to filter which groups are retrieved. E.g.,
-
Attributes Tab (often pre-populated by LDAP Server Profile Type):
-
Object Class (User):
e.g.,
userfor Active Directory. -
Primary Username:
e.g.,
sAMAccountName. -
Alternate Usernames:
Click
Add
to include attributes like
userPrincipalName,mail. -
Object Class (Group):
e.g.,
groupfor Active Directory. -
Group Name:
e.g.,
cnorsAMAccountName(for groups). -
Group Member:
e.g.,
member(attribute on the group object listing members) ormemberOf(attribute on the user object listing group memberships). PAN-OS typically uses thememberattribute of group objects.
-
Object Class (User):
e.g.,
-
Name:
A unique name for this group mapping instance (e.g.,
- Click OK to save the group mapping settings.
- Commit the configuration to the firewall.
C. Verifying User and Group Attributes
The correct mapping of LDAP attributes is vital for User-ID to function. The specific attributes depend on your LDAP directory schema.
For Microsoft Active Directory, common attributes include:
-
User Attributes:
-
Primary Username:
sAMAccountName(e.g.,jdoe) -
Alternate Usernames:
userPrincipalName(e.g.,jdoe@corp.paloaltonetworks.com),mail -
User's Group Memberships (if querying user objects for groups, less common for group mapping itself):
memberOf
-
Primary Username:
-
Group Attributes:
-
Group Name:
cn(Common Name) orsAMAccountName(for groups with this attribute) -
Group Members:
member(This attribute on a group object lists the DNs of its members) -
Object Class for Groups:
group
-
Group Name:
For OpenLDAP, common attributes might include:
-
User Attributes:
-
Primary Username:
uid -
Alternate Usernames:
mail
-
Primary Username:
-
Group Attributes:
-
Group Name:
cn -
Group Members:
memberUid(if using posixGroup schema) oruniqueMember(if using groupOfUniqueNames schema) -
Object Class for Groups:
posixGrouporgroupOfUniqueNames
-
Group Name:
You can use an LDAP browser tool (like JXplorer, Softerra LDAP Browser, or even
ldp.exe
on Windows) to inspect your directory's schema and verify attribute names and values before configuring them in PAN-OS.
User-ID Best Practices for Group Mapping
Effective group mapping is key to leveraging User-ID. The following Palo Alto Networks recommended best practices help ensure a stable, secure, and performant configuration:
-
Plan Your Deployment:
- Thoroughly understand your directory service architecture (AD, OpenLDAP, etc.), including domain/forest structure, server locations, and replication topology.
- For Active Directory, identify Domain Controllers (DCs) or Global Catalog (GC) servers with good network connectivity to the firewall. GCs are useful for multi-domain forests if Universal Groups are used.
-
Redundancy for LDAP Servers:
- In the LDAP Server Profile, configure multiple LDAP servers (up to four) for redundancy. The firewall will try them in the order listed.
-
Use LDAPS (SSL/TLS):
- Always prefer LDAPS (port 636 or 3269 for GC) over LDAP (port 389 or 3268) to encrypt communication between the firewall and the LDAP server, protecting credentials and sensitive data.
- Ensure proper certificate management if using internal CAs.
-
Dedicated Service Account:
- Use a dedicated service account for the Bind DN with the principle of least privilege. This account only needs read access to the necessary user and group attributes in the relevant OUs.
- Avoid using administrator accounts for LDAP binding.
- Set the service account password to never expire, or have a process to update it on the firewall when it changes.
-
Optimize Base DN:
- Specify a Base DN that is as specific as possible to the location of user and group objects in your directory. This reduces search scope and improves query performance.
-
Strategic Group Include List:
- This is CRITICAL. Only include groups in the "Group Include List" that are actively used in security policies. Retrieving excessive groups consumes firewall resources (memory, CPU) and increases LDAP query times.
- Avoid fetching all groups unless absolutely necessary and the directory is small.
-
Consider Universal Groups (Active Directory):
- For multi-domain AD forests, using Universal Groups and querying a Global Catalog server (port 3268/3269) can simplify group mapping by providing a forest-wide view of group memberships.
- If not using Universal Groups, you might need separate group mapping configurations for each domain, pointing to DCs in those respective domains. Ensure usernames are unique across forests if users can come from different untrusted forests.
-
Appropriate Update Interval:
- Set the "Update Interval" in Group Mapping Settings based on how frequently group memberships change. The default is 1 hour (3600 seconds).
- Shorter intervals provide more up-to-date information but increase load. Longer intervals reduce load but introduce latency in reflecting changes.
-
Primary and Alternate Usernames:
-
Configure the "Primary Username" (e.g.,
sAMAccountName) and relevant "Alternate Usernames" (e.g.,userPrincipalName,mail) in the Group Mapping attributes. This allows User-ID to correctly identify users regardless of the username format provided by various User-ID sources (e.g., GlobalProtect, Captive Portal, XML API).
-
Configure the "Primary Username" (e.g.,
-
Ensure Attribute Uniqueness:
- The attributes used for primary username, alternate usernames, and email should be unique for each user within the scope of User-ID. Duplicate values can lead to misidentification.
-
Avoid Overlapping Group Mapping Configurations:
- If creating multiple group mapping configurations (e.g., for different domains or OUs), ensure their "Group Include Lists" or search filters do not result in the firewall tracking the same group multiple times from the same LDAP server via different mapping configurations pointing to the same Base DN. This can cause conflicts or inefficiencies.
-
Leverage Cloud Identity Engine (CIE) for Cloud Directories:
- For cloud-based IdPs like Azure AD, Okta, or Google Workspace, CIE is the recommended approach. It simplifies integration and is designed for cloud environments.
-
Group Mapping Centralization for Virtual System Hubs:
-
If using virtual systems (vSys) on a firewall, you can configure one vSys as a "hub" to provide group mappings to other "spoke" vSys on the same firewall. This centralizes LDAP queries and conserves resources by avoiding redundant mappings on each vSys. This feature requires specific PAN-OS versions and licensing. (See
Device > Virtual Systems > {vsys_name} > User-ID).
-
If using virtual systems (vSys) on a firewall, you can configure one vSys as a "hub" to provide group mappings to other "spoke" vSys on the same firewall. This centralizes LDAP queries and conserves resources by avoiding redundant mappings on each vSys. This feature requires specific PAN-OS versions and licensing. (See
-
Regularly Monitor and Verify:
-
Use PAN-OS CLI commands to check the status of group mapping and troubleshoot issues:
show user group-mapping state all show user group list show user group name <group_name_from_directory> debug user-id refresh group-mapping all // To force a refresh test ldap-profile profile-name <profile_name> host <host_ip> port <port> username <username_for_test> - Review system logs for any LDAP or User-ID related errors.
-
Use PAN-OS CLI commands to check the status of group mapping and troubleshoot issues:
-
Custom Groups with Indexed Attributes:
- If using custom groups based on LDAP filters, ensure the attributes used in your filters are indexed on the LDAP server. Non-indexed attributes can lead to very slow queries and high load on the directory server.
-
"Custom Groups Only" Optimization:
- If you only intend to use custom groups from a particular directory server (and no groups from its Group Include List), add a non-existent or unused group to the Group Include List. This seemingly counter-intuitive step can prevent User-ID from attempting to retrieve all groups from the directory if the include list is otherwise empty, optimizing the process when only custom, filter-based groups are desired from that source.
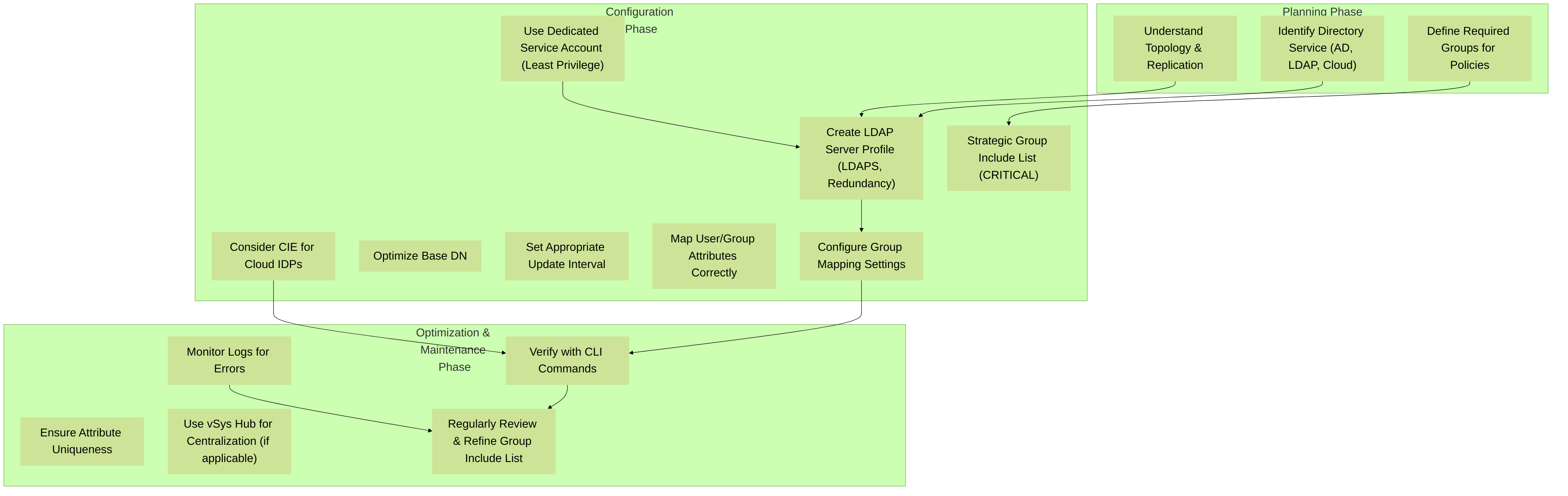
Decision tree highlighting key best practice stages for Palo Alto Networks Group Mapping: Planning, Configuration, and Optimization/Maintenance.
Configuring a Master Device in Panorama for User and Group Mapping
Panorama, the Palo Alto Networks network security management solution, can leverage group mapping information for centralized policy creation across multiple managed firewalls. To enable this, one of the managed firewalls within a Device Group is designated as a "Master Device." Panorama then retrieves user and group mapping information from this Master Device.
Purpose and Benefits:
- Centralized Policy Management: Allows administrators to create security policies in Panorama using group names, which are then pushed to managed firewalls.
- Consistency: Ensures consistent use of group-based policies across the device group.
- Simplified Configuration: Avoids the need for Panorama to have direct connectivity to all directory services if the Master Device can already reach them.
Steps to Configure a Master Device in Panorama:
-
Enable and Configure Group Mapping on the Intended Master Firewall:
- On the specific firewall that will serve as the Master Device, ensure User-ID is enabled and Group Mapping is configured correctly (e.g., via LDAP or CIE subscription) and successfully retrieving groups. This firewall must have network connectivity to the relevant directory services.
-
Designate the Master Device in Panorama:
-
In Panorama, navigate to
Panorama > Managed Devices > Summary. Ensure the firewall intended to be the Master Device is connected and in sync. -
Navigate to
Panorama > Device Groups. - Select the Device Group for which you want to configure the Master Device, then click its name or an edit icon.
- In the Device Group settings window, under the General tab (or a similar tab like "User-ID" or "Master Device" depending on Panorama version), find the Master Device settings.
- From the "Master Device" dropdown list, select the serial number of the firewall you want to designate as the Master Device.
- There might be an option like "Import user and group information from master device" or "Enable User-ID and Group Mapping data collection from Master Device" . Ensure this is enabled. (The exact wording from the provided HTML "Store users and groups from the master device if reporting and filtering of groups is enabled in Panorama settings" implies a dependency, let's stick to that). So ensure you also:
-
In Panorama, navigate to
-
Enable Reporting and Filtering on Groups in Panorama Settings:
-
Navigate to
Panorama > Setup > Management. - In the Panorama Settings section, click Edit (or the gear icon).
- Under the "User Identification" or "Logging and Reporting" section, enable the option "Enable reporting and filtering on groups" . This allows Panorama to store and use group information for reporting and policy.
-
Navigate to
-
Commit and Push Changes:
-
Commit the changes in Panorama (
Commit > Commit to Panorama). -
Then, push this configuration to the Device Group containing the Master Device (
Commit > Push to Devices, select the appropriate Device Group, and ensure "Include Device and Network Templates" and "Include Policies and Objects" are selected as needed).
-
Commit the changes in Panorama (
Once these steps are completed and changes are committed and pushed, Panorama will start polling the designated Master Device for user and group mapping information. This information will then populate the group lists available when creating Security, NAT, QoS, and other policies in Panorama for that Device Group.
Alternative: Panorama as a User-ID Hub (with Dedicated Log Collectors): In larger deployments, Panorama itself (especially when paired with Dedicated Log Collectors or M-Series appliances in Panorama mode) can act as a User-ID hub, collecting IP-to-user mappings from various sources (including User-ID agents on firewalls). While this is more about IP-to-user mapping distribution, group mapping information from the Master Device complements this by providing the group context for those users.
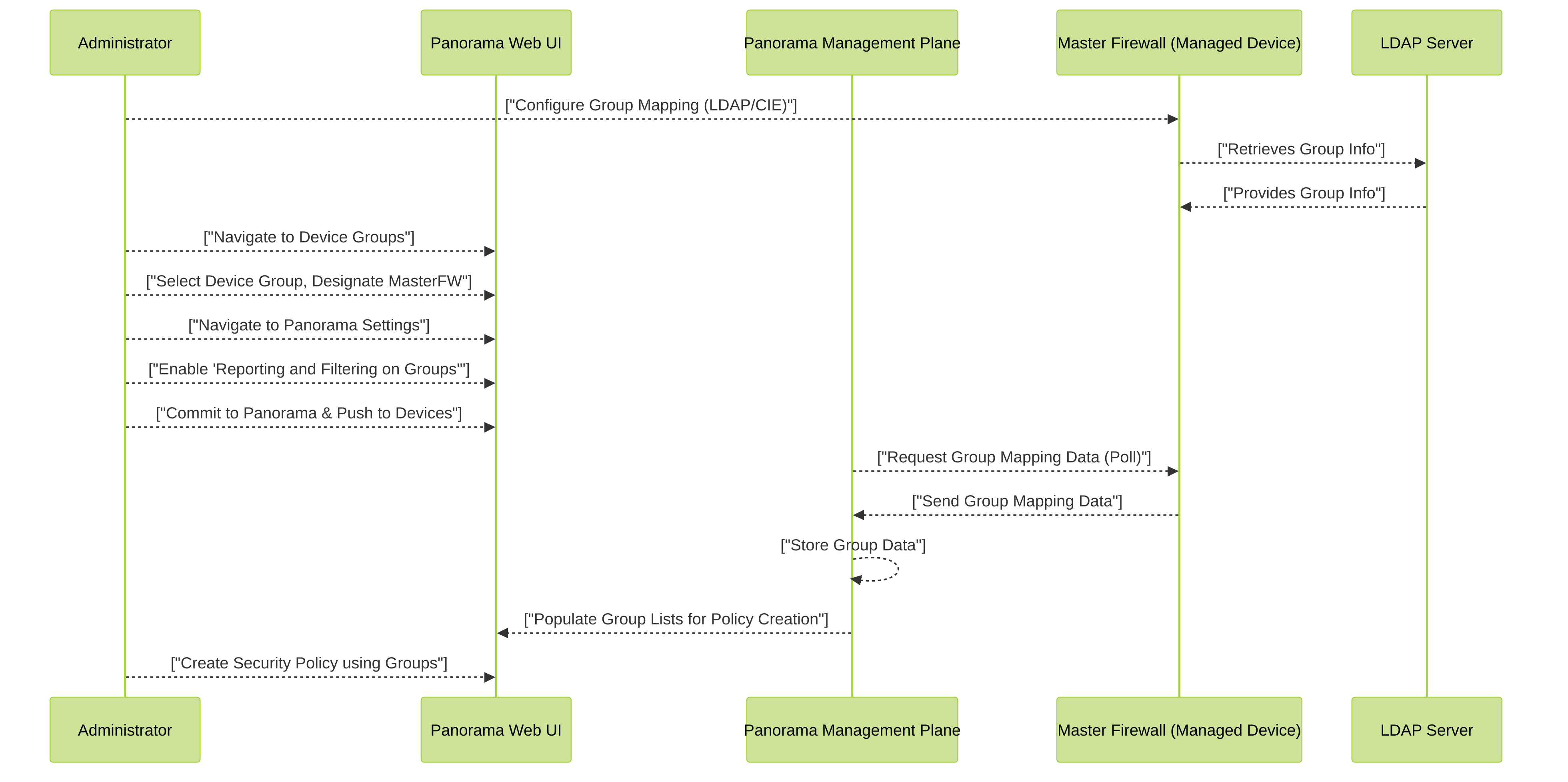
Process flow for configuring a Master Device in Panorama. The Master Firewall retrieves group information from LDAP, and Panorama polls the Master Firewall for this data to enable centralized group-based policy creation.
Group Mapping in Virtual Systems (vSys)
Palo Alto Networks firewalls support Virtual Systems (vSys), allowing a single physical firewall to be partitioned into multiple logical firewalls. User-ID and group mapping can be configured in vSys environments in a couple of ways:
- Per-vSys Configuration: Each vSys can have its own independent User-ID configuration, including its own LDAP Server Profiles and Group Mapping settings. This is suitable when different vSys serve entirely separate tenants or departments with distinct directory services.
-
Shared User-ID Information (vSys Hub):
One vSys can be configured as a "User-ID Hub" (or "Group Mapping Hub"). This hub vSys performs the User-ID and group mapping functions (e.g., queries LDAP servers) and shares this information with other "spoke" vSys on the same physical firewall.
-
Benefits:
- Resource Efficiency: Reduces the number of LDAP queries and connections, as only the hub vSys communicates with the directory service.
- Simplified Management: Centralizes User-ID and group mapping configuration.
- Scalability: Optimizes the use of firewall resources by avoiding redundant User-ID processes across multiple vSys.
-
Configuration:
-
Navigate to
Device > Virtual Systems. Select the vSys intended to be the hub. -
Under the vSys settings, go to the
User-IDtab. - Enable the option "Act as User-ID Hub" (or similar wording).
-
For spoke vSys, navigate to their
User-IDtab and select the option to "Use User-ID Hub" , specifying the hub vSys.
-
Navigate to
-
Benefits:
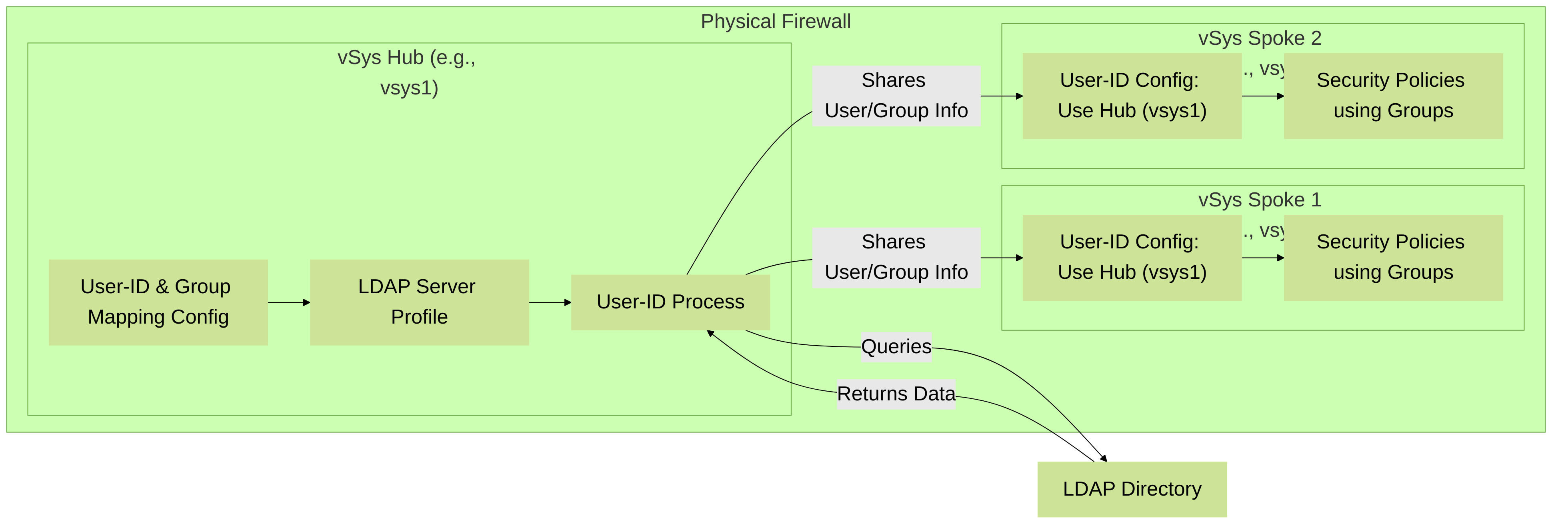
Architecture of Group Mapping Centralization using a vSys Hub on a Palo Alto Networks firewall. The Hub vSys handles LDAP communication and shares User-ID information with Spoke vSys.
Monitoring and Troubleshooting Group Mapping
Effective monitoring and troubleshooting are essential for maintaining reliable group mapping.
PAN-OS CLI Commands:
The following CLI commands are invaluable for checking status and diagnosing issues:
| Command | Description |
|---|---|
show user group-mapping state all
|
Displays the status of all configured group mapping instances, including the LDAP server, Base DN, filter, number of groups found, and last update time. Look for "success" status. |
show user group list
|
Lists all groups currently known to the firewall through group mapping. Provides the group name as known by the firewall. |
show user group name "<group-name>"
|
Displays detailed information about a specific group, including its source and the users who are members of that group. The group name should be in the format
DOMAIN\group
or just
group
as seen in
show user group list
.
|
show user ip-user-mapping all
|
Shows the IP-to-user mappings. While not directly group mapping, it helps confirm if users are being identified. The group information is then correlated with these identified users. |
show user user-id-agent state all
|
If using User-ID agents, shows their status. Not directly for firewall group mapping but part of overall User-ID health. |
test ldap-profile profile-name <profile_name> host <host_ip_or_fqdn> port <port> [username <test_username_to_lookup>]
|
Tests connectivity to the LDAP server using a specified LDAP Server Profile. Can optionally lookup a specific username. This helps verify bind credentials, server reachability, and SSL/TLS setup. |
debug user-id refresh group-mapping all
|
Forces an immediate refresh of all group mapping information from the configured sources. Useful after making changes to LDAP or group mapping settings. |
debug user-id dump group-mapping [name <mapping_name>]
|
Dumps detailed information about the group mapping cache, including raw data retrieved from LDAP. Can be verbose but very useful for deep troubleshooting. |
less mp-log useridd.log
|
Views the User-ID daemon log on the management plane. Contains detailed logging about LDAP queries, responses, and errors. |
less dp-log useridd.log
|
Views the User-ID daemon log on the dataplane (for specific dataplane if multiple). Contains logs related to dataplane processing of User-ID information. |
admin@PA-VM> show user group-mapping state all
Group Mapping: LDAP-AD-Corp
Type: ldap
Server Profile: AD-Primary-LDAP
Base: dc=corp,dc=example,dc=com
Filter: (objectClass=group)
User Domain:
Group Include List:
cn=Domain Admins,cn=users,dc=corp,dc=example,dc=com
cn=Engineering,ou=departments,dc=corp,dc=example,dc=com
cn=Sales,ou=departments,dc=corp,dc=example,dc=com
State: success
Last Action Time: 2023/10/27 10:00:00
Action: Query
Total Groups Found:3
Groups:
corp\Domain Admins
corp\Engineering
corp\Sales
admin@PA-VM> show user group name "corp\Engineering"
Users for group corp\Engineering:
corp\user1
corp\user2
corp\user5
Total: 3 users
Common Issues and Troubleshooting Steps:
-
No Groups Found / Incorrect Group List:
-
Verify LDAP Server Profile: Correct IP/FQDN, port, Bind DN, password. Use
test ldap-profile. - Verify Base DN: Ensure it's correct and encompasses the groups.
- Verify Group Include List: DNs must be exact. Check for typos.
- Check LDAP Filters: If using custom filters, ensure syntax is correct and attributes exist.
- Permissions: Ensure Bind DN account has read access to group and user objects and their attributes.
- Connectivity: Firewall must be able to reach LDAP server(s) on the specified port. Check routing and Security Policies on the firewall itself if it's blocking its own traffic.
-
Verify LDAP Server Profile: Correct IP/FQDN, port, Bind DN, password. Use
-
LDAP Bind Failures:
- Incorrect Bind DN or password.
- Service account locked out or password expired.
- Network connectivity issues (firewall rules, routing).
- SSL/TLS issues: If using LDAPS, ensure firewall trusts the LDAP server's certificate CA. Import CA if necessary. Check "Verify Server Certificate".
-
Users Not Appearing in Groups:
- Ensure user accounts are actually members of the included groups in the directory.
- Check attribute mapping (Primary Username, Alternate Usernames, Group Member attribute) in Group Mapping settings.
- Case sensitivity: Some LDAP servers are case-sensitive. Ensure names match exactly. While PAN-OS often attempts case-insensitive matching, the directory itself might be strict.
-
User-ID not identifying the user: If IP-to-user mapping is failing, the firewall won't know which user is associated with traffic, and thus cannot apply group-based policies. Check
show user ip-user-mapping.
-
High CPU/Memory Usage on Firewall or LDAP Server:
- Group Include List too broad (fetching too many groups).
- Update Interval too short for the size of the directory and number of groups.
- Inefficient LDAP filters for custom groups (e.g., using non-indexed attributes).
-
Changes in Directory Not Reflected:
-
Wait for the "Update Interval" to elapse or manually refresh using
debug user-id refresh group-mapping all. - Check LDAP replication if changes were made on a DC that hasn't replicated to the DC being queried by the firewall.
-
Wait for the "Update Interval" to elapse or manually refresh using
useridd.log
(
less mp-log useridd.log
) for detailed error messages when troubleshooting group mapping. It often provides specific reasons for failures that are not visible in the GUI or basic show commands.
References (Internal - Based on Palo Alto Networks Documentation Principles)
This guide is developed based on established Palo Alto Networks principles and knowledge derived from official PAN-OS Administrator's Guides, User-ID Technical Documentation, Cloud Identity Engine Documentation, and Panorama Administrator's Guides. For the most current and detailed information, always refer to the official Palo Alto Networks documentation portal for your specific PAN-OS, Panorama, or CIE version.
- PAN-OS Administrator's Guide: User-ID section, specifically chapters on Group Mapping and LDAP Server Profiles.
- User-ID Concepts and Deployment Guides.
- Cloud Identity Engine (CIE) Administration Guide.
- Panorama Administrator's Guide: User Identification and Policy Management sections.
- Palo Alto Networks Knowledge Base and Live Community for troubleshooting articles and discussions.