Palo Alto Networks URL Filtering Solution
|
Where can I use this? |
What do I need? |
|
Notes:
|
Advanced URL Filtering (preceded by URL Filtering) is a subscription service that protects your network and its users against malicious and evasive web-based threats—both known and unknown. The subscription provides the same functionality as URL Filtering—granular URL filtering control, visibility into user web activity, safe search enforcement, and credential phishing prevention—with the addition of full web content inspection using an inline machine learning-based web security engine. The inline web security engine enables real-time analysis and categorization of URLs that are not present in PAN-DB, Palo Alto Networks cloud-based URL database. Then, the engine determines the action the firewall takes.
Advanced URL Filtering protects against malicious URLs that are updated or introduced before PAN-DB has analyzed and added them to the database. With Advanced URL Filtering enabled, URL requests are:
- Analyzed in real-time using the cloud-based Advanced URL Filtering detection modules. This is in addition to URLs being compared to entries in PAN-DB. The ML-powered web protection engine detects and blocks the malicious websites that PAN-DB cannot.
- Inspected for phishing and malicious JavaScript using local inline categorization , a firewall-based analysis solution, which can block unknown malicious web pages in real-time.
Advanced URL Filtering licenses are supported on next-generation firewalls running PAN-OS 9.1 and later. You can manage URL filtering features on the PAN-OS and Panorama web interface, Prisma Access, and Cloud NGFW platforms. However, some URL filtering features are not available on each platform.
If network security requirements in your enterprise prohibit the firewalls from directly accessing the Internet, Palo Alto Networks provides an offline URL filtering solution with the PAN-DB private cloud . You can deploy a PAN-DB private cloud on one or more M-600 appliances that function as PAN-DB servers within your network; however, the private cloud does not support any of the cloud-based URL analysis features provided by the Advanced URL Filtering solution.
Legacy URL Filtering Subscription
URL Filtering enforces policy rules for websites stored in your local cache or PAN-DB. When a user requests a website, the firewall checks the local cache for its URL category. If the website isn't in the cache, the firewall queries PAN-DB to decide which action to apply. As a result, attackers are better able to launch precision attack campaigns using URLs that aren't present in the cloud-based database.
Legacy subscription holders can continue using their URL filtering deployment until the end of the license term.
URL Filtering Support
Palo Alto Networks URL Filtering Solution
Advanced URL Filtering features are available on next-generation firewalls (virtual and on-premises), Prisma Access (Managed by Strata Cloud Manager), Prisma Access (Managed by Panorama), Cloud NGFW for AWS, and Cloud NGFW for Azure. However, next-generation firewalls and Cloud NGFW for Azure require an Advanced URL Filtering subscription, while all Prisma Access and Cloud NGFW for AWS licenses include Advanced URL Filtering capabilities.
Feature support depends on the platform and type of URL filtering license. Features that are only available with an Advanced URL Filtering license are indicated by an Advanced URL Filtering label.
The following table shows the compatibility of Advanced URL Filtering features with each Palo Alto Networks platform that supports URL Filtering.
|
Feature |
Supported on |
Notes |
|||||
|
NGFW (Managed by Strata Cloud Manager) |
NGFW (Managed by PAN-OS or Panorama) |
Prisma Access (Managed by Strata Cloud Manager) |
Prisma Access (Managed by Panorama) |
Cloud NGFW for AWS |
Cloud NGFW for Azure |
||
|
Inline Categorization
|
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Not supported on the VM-50 or VM50L appliance |
|
Custom URL Categories |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
User Credential Detection |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
Custom URL Filtering Response Pages |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
Safe Search Enforcement
|
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
URL Admin Override |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
SSL/TLS Handshake Inspection |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
Integration with Remote Browser Isolation (RBI) |
No |
No |
Yes |
Yes |
No |
No |
|
|
Log Container Page Only (Log Only the Page a User Visits) |
No |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Local Inline Categorization
How Advanced URL Filtering Works
|
Where can I use this? |
What do I need? |
|
Note: Prisma Access licenses include Advanced URL Filtering capabilities. |
Local inline categorization (previously known as inline ML) enables the firewall dataplane to apply machine learning (ML) on webpages to alert users when phishing variants are detected while preventing malicious variants of JavaScript exploits from entering your network. Local inline categorization dynamically analyzes and detects malicious content by evaluating various webpage details using a series of ML models. Each ML model detects malicious content by evaluating file details, including decoder fields and patterns, to formulate a high probability classification and verdict, which is then used as part of your larger web security policy. URLs classified as malicious are forwarded to PAN-DB for additional analysis and validation. You can specify URL exceptions to exclude any false-positives that might be encountered. This allows you to create more granular rules for your profiles to support your specific security needs. To keep up with the latest changes in the threat landscape, inline ML models are updated regularly and added via content releases. An active Advanced URL Filtering subscription is required to configure inline categorization .
You can also enable inline ML-based protection to detect malicious Portable Executable (PE), ELF and MS Office files, and PowerShell and shell scripts in real-time as part of your Antivirus profile configuration. For more information, refer to: Advanced Wildfire Inline ML .
How Advanced URL Filtering Works
|
Where can I use this? |
What do I need? |
|
Notes:
|
Advanced URL Filtering classifies websites based on site content, features, and safety. A URL can have up to four URL categories that indicate the likelihood that the site will expose you to threats. As PAN-DB, the Advanced URL Filtering URL database, categorizes sites, firewalls with Advanced URL Filtering enabled can leverage that knowledge to enforce your organization’s security policies. In addition to the protection offered by PAN-DB, Advanced URL Filtering provides real-time analysis using machine learning (ML) to defend against new and unknown threats. This provides protection against malicious URLs that are updated or introduced before URL filtering databases have an opportunity to analyze and add the content, giving attackers an open period from which they can launch precision attack campaigns. Advanced URL Filtering compensates for the coverage gaps inherent in database solutions by providing real-time URL analysis on a per request basis. The ML-based models used by advanced URL filtering have been trained, and are continuously updated, to detect various malicious URLs, phishing web pages, and command-and-control (C2).
Websites that indicate the presence of certain advanced threats are additionally processed though a cloud-based inline deep learning system, using detectors and analyzers that complement the ML-models used by Advanced URL Filtering. Deep learning detectors can process larger data sets and can better identify complex malicious patterns and behaviors through multi-layered neural networks. When Advanced URL Filtering receives HTTP response data from the firewall upon receipt of a suspicious web request, the data is further analyzed through the deep learning detectors and provides inline protection against evasive zero-day web attacks. This includes cloaked websites, in which web page contents are surreptitiously retrieved from unknown websites—this can include malicious content that URL databases are unable to account for, multi-step attacks, CAPTCHA challenges, and previously unseen one-time-use URLs. Because evasive malicious websites are in a constant state of flux, the detectors and analyzers used to categorize websites are updated and deployed automatically as Palo Alto Networks threat researchers improve the detection logic, all without requiring the administrator to download update packages.
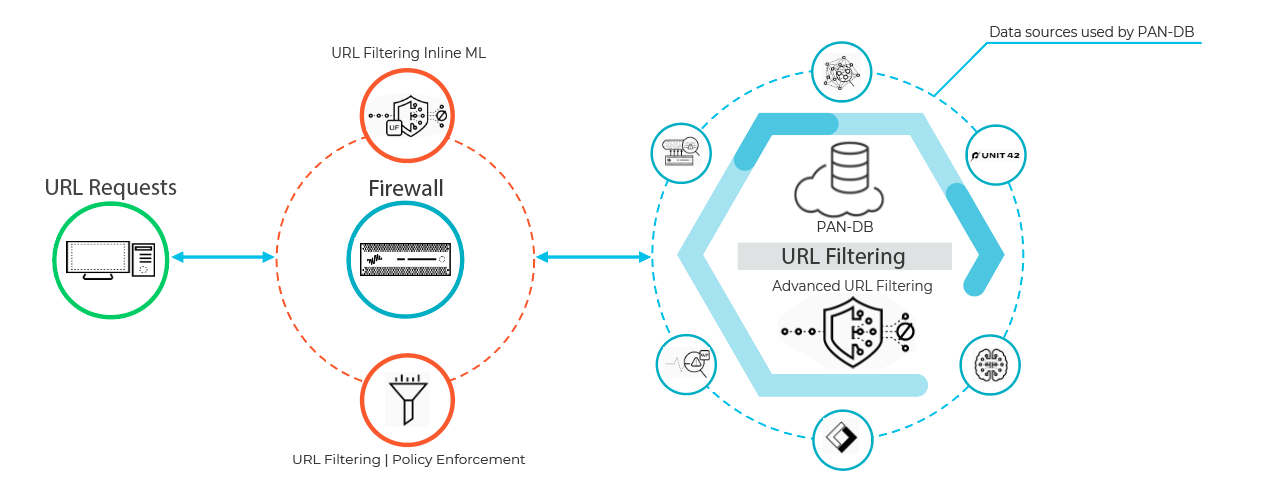
When a user requests a web page, the firewall queries user-added exceptions and PAN-DB for the site’s risk category. PAN-DB uses URL information from Unit 42, WildFire, passive DNS, Palo Alto Networks telemetry data, data from the Cyber Threat Alliance, and applies various analyzers to determine the category. If the URL displays risky or malicious characteristics, the web payload data is also submitted to Advanced URL Filtering in the cloud for real-time analysis and generates additional analysis data. The resulting risk category is then retrieved by the firewall and is used to enforce the web-access rules based on your policy configuration. Additionally, the firewall caches site categorization information for new entries to enable fast retrieval for subsequent requests, while it removes URLs that users have not accessed recently so that it accurately reflects the traffic in your network. Additionally, checks built into PAN-DB cloud queries ensure that the firewall receives the latest URL categorization information. If you do not have Internet connectivity or an active URL filtering license, no queries are made to PAN-DB.
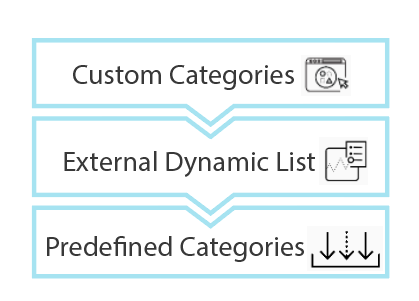
The firewall determines a website’s URL category by comparing it to entries in 1) custom URL categories, 2) external dynamic lists (EDLs), and 3) predefined URL categories, in order of precedence.
Firewalls configured to analyze URLs in real-time using machine learning on the dataplane provides an additional layer of security against phishing websites and JavaScript exploits. The ML models used by local inline categorization identifies currently unknown and future variants of URL-based threats that match the characteristics that Palo Alto Networks has identified as malicious. To keep up with the latest changes in the threat landscape, local inline categorization ML models are added or updated via content releases.
When the firewall checks PAN-DB for a URL, it also looks for critical updates, such as URLs that previously qualified as benign but are now malicious.
If you believe PAN-DB has incorrectly categorized a site, you can submit a change request in your browser through Test A Site or directly from the firewall logs.
Did you know?
Technically, the firewall caches URLs on both the management plane and the dataplane:
- PAN-OS 9.0 and later releases do not download PAN-DB seed databases. Instead, upon activation of the URL filtering license, the firewall populates the cache as URL queries are made.
- The management plane holds more URLs and communicates directly with PAN-DB. When the firewall can't find a URL’s category in the cache and performs a lookup in PAN-DB, it caches the retrieved category information in the management plane. The management plane passes that information along to the dataplane, which also caches it and uses it to enforce policy.
- The dataplane holds fewer URLs and receives information from the management plane. After the firewall checks URL category exception lists (custom URL categories and external dynamic lists) for a URL, it looks in the dataplane. If the firewall doesn't find the URL in the dataplane, it checks the management plane and, if the category information isn't there, PAN-DB.
URL Filtering Profiles
How Advanced URL Filtering Works
|
Where can I use this? |
What do I need? |
|
Notes:
|
URL Filtering profiles define how the firewall handles traffic to specific URL categories. A URL Filtering profile is a collection of URL filtering controls that you apply to individual Security policy rules that allow access to the internet. You can configure site access for URL categories, allow or disallow user credential submissions, enable safe search enforcement, and various other settings. To enforce the actions defined in a URL Filtering profile, apply the profile to Security policy rules. The firewall enforces the profile actions on traffic that matches the Security policy rule (for details, see Configure URL Filtering ).
The firewall comes with a default profile that blocks threat-prone categories, such as malware, phishing, and adult. You can use the default profile in a Security policy rule, clone it to be used as a starting point for new URL Filtering profiles, or add a new URL Filtering profile. You can customize newly-added URL Filtering profiles and add lists of specific websites that should always be blocked or allowed. For example, you can block the social-networking category but allow access to specific websites in that category. By default, site access for all URL categories is set to allow when you create a basic URL Filtering profile . This means that users will be able to browse to all sites freely and the traffic is not logged.
Create a best practice URL Filtering profile to ensure protection against URLs that have been observed hosting malware or exploitative content.
URL Filtering Profile Actions
In a URL Filtering profile, you can define Site Access for URL categories, allow or disallow User Credential Submissions based on URL category (for example, you can block user credential submissions to medium and high-risk sites), and enable safe search enforcement .
|
Action |
Description |
|
Site Access |
|
|
alert |
The website is allowed and a log entry is generated in the URL filtering log. Set alert as the Action for categories of traffic you don’t block to log and provide visibility into the traffic. |
|
allow |
The website is allowed and no log entry is generated. Don’t set allow as the Action for categories of traffic you don’t block because you lose visibility into traffic you don’t log. Instead, set alert as the Action for categories of traffic you don’t block to log and provide visibility into the traffic. |
|
block |
The website is blocked and the user will see a response page and will not be able to continue to the website. A log entry is generated in the URL filtering log. Blocking site access for a URL category also sets User Credential Submissions for that URL category to block. |
|
continue |
The user will be prompted with a response page indicating that the site has been blocked due to company policy, but the user is prompted with the option to continue to the website. The continue action is typically used for categories that are considered benign and is used to improve the user experience by giving them the option to continue if they feel the site is incorrectly categorized. The response page message can be customized to contain details specific to your company. A log entry is generated in the URL filtering log. The Continue page doesn’t display properly on client systems configured to use a proxy server. |
|
override |
The user will see a response page indicating that a password is required to allow access to websites in the given category. With this option, the security admin or help desk person would provide a password granting temporary access to all websites in the given category. A log entry is generated in the URL filtering log. See Allow Password Access to Certain Sites . In earlier release versions, URL Filtering category overrides had priority enforcement ahead of custom URL categories. As part of the upgrade to PAN-OS 9.0, URL category overrides are converted to custom URL categories, and no longer receive priority enforcement over other custom URL categories. Instead of the action you defined for the category override in previous release versions, the new custom URL category is enforced by the Security policy rule with the strictest URL Filtering profile action. From most strict to least strict, possible URL Filtering profile actions are: block, override, continue, alert, and allow. This means that, if you had URL category overrides with the action allow, there’s a possibility the overrides might be blocked after they are converted to custom URL category in PAN-OS 9.0. The Override page doesn’t display properly on client systems configured to use a proxy server. |
|
none |
The none action only applies to custom URL categories. Select none to ensure that if multiple URL profiles exist, the custom category will not have any impact on other profiles. For example, if you have two URL profiles and the custom URL category is set to block in one profile, if you do not want the block action to apply to the other profile, you must set the action to none . Also, in order to delete a custom URL category, it must be set to none in any profile where it is used. |
|
User Credential Permissions These settings require you to first set up credential phishing prevention . |
|
|
alert |
Allow users to submit corporate credentials to sites in this URL category, but generate a URL Filtering alert log each time this occurs. |
|
allow (default) |
Allow users to submit corporate credentials to websites in this URL category. |
|
block |
Block users from submitting corporate credentials to websites in this category. A default anti-phishing response page is displayed to users when they access sites to which corporate credential submissions are blocked. You can customize the block page that displays. |
|
continue |
Display a response page to users that prompts them to select Continue to access to access the site. By default, the Anti Phishing Continue Page is shown to user when they access sites to which credential submissions are discouraged. You can customize the response page to warn users against phishing attempts or reusing their credentials on other websites, for example. |
For categories that you alert on, instead of block, you can strictly control how users interact with site content. For example, give users access to the resources they need (like developer blogs for research purposes or cloud storage services), but take the following precautions to reduce exposure to web-based threats:
- Follow the Anti-Spyware, Vulnerability Protection, and File Blocking best practices . A protective measure would be to block downloads of dangerous file types and obfuscated JavaScript for sites that you're alerting on.
- Target decryption based on URL category. A good start would be to decrypt high-risk and medium-risk sites.
- Display a response page to users when they visit high-risk and medium-risk sites. Alert them that the site they are attempting to access is potentially malicious, and advise them on how to take precautions if they decide to continue to the site.
- Prevent credential phishing by blocking users from submitting their corporate credentials to sites including those that are high-risk and medium-risk.
URL Categories
|
Where can I use this? |
What do I need? |
|
This feature has no prerequisites. |
Palo Alto Networks categorizes websites based on their content, features, and safety. Each URL category corresponds to a set of characteristics that’s useful for creating policy rules. URLs that users on your network access are added to Palo Alto Networks URL filtering database, PAN-DB. PAN-DB assigns up to four URL categories, including risk categories (high, medium, and low), to these websites.
URL categories enable category-based filtering of web traffic and granular policy control of sites. You can configure a URL Filtering profile to define site access for URL categories and apply the profile to Security policy rules that allow traffic to the internet. You can also use URL categories as match criteria in Security policy rules to ensure those rules apply only to websites in the specified categories. For example, you might configure a decryption policy rule that prevents decryption of traffic to the financial-services category.
To check the categories of a specific URL, enter the URL into Test A Site , our URL lookup engine. If you believe a URL is incorrectly categorized, submit a category change request .
Custom URL Categories
You can create a custom URL category to exclude particular websites from category-based enforcement. Custom URL categories can be based on specific URLs (URL List) or other categories (Category Match). Custom URL categories of URL List type function as block and allow lists. Custom URL categories of Category Match type enable targeted enforcement for websites that match all categories defined as part of the custom category.
Predefined URL Categories
The following table lists the predefined URL categories that PAN-DB uses to filter URLs. Some entries describe sites that are excluded from the category.
Security-Focused URL Categories
describes risk categories, which are not assigned to all URLs.
|
URL Category |
Description |
|
Abortion |
Sites that pertain to information or groups in favor of or against abortion, details regarding abortion procedures, help or support forums for or against abortion, or sites that provide information regarding the consequences or effects of pursuing (or not) an abortion. |
|
Abused Drugs |
Sites that promote the abuse of both legal and illegal drugs, the use and sale of drug-related paraphernalia, or the manufacturing or selling of drugs. |
|
Adult |
Sites with any sexually explicit material, media (including language, games, or comics), art, or products, online groups or forums that are sexually explicit in nature, and sites that promote adult services, such as video or telephone conferencing, escort services, and strip clubs. |
|
Alcohol and Tobacco |
Sites that pertain to the sale, manufacturing, or use of alcohol or tobacco products, and related paraphernalia. Includes sites related to electronic cigarettes. |
|
Artificial Intelligence Websites that use machine learning and deep learning models, including large language models, to provide services that typically require human intelligence. The services provided include but are not limited to chatbot, productivity, summarizer, transcriber, no-code, and audio or video editing-related services. Emphasis is given to websites hosting the actual AI service, not informational AI content. Websites whose primary business is not actual AI service but use AI to support their main offering (for example, real-estate platforms with AI-generated descriptions or AI-powered travel sites are not part of this category). You can use this broader category to apply policy rules to the following AI subcategories collectively. |
|
|
AI Code Assistant |
Sites that provide services to assist with code writing, optimization, and generation using artificial intelligence. This may include platforms that support code completion, bug detection, and code suggestions. |
|
AI Conversational Assistant |
AI-driven conversational assistants that utilize natural language processing (NLP) and machine learning to facilitate human-like interactions. These assistants are designed to support a wide range of tasks through conversational interfaces, typically accepting text and files as input and are designed to provide contextual, interactive support |
|
AI Writing Assistant |
Sites that leverage artificial intelligence and machine learning to enhance productivity by providing text based content generation capabilities across industries such as marketing, eCommerce, SEO, and education. These platforms improve efficiency and streamline tasks like SEO-optimized writing, customer service and prompt generation, while also supporting a broad range of content creation needs from creative writing and academic assistance to marketing and customer review management. Language translation services are not part of this category; such sites are covered under the ‘Translation’ category. |
|
AI Media Service |
Sites that utilize artificial intelligence and machine learning to generate, manipulate, edit, and detect various forms of AI-generated media, including images, voice, music, videos, ads, QR codes, AI headshots, and AI avatars, based on text prompts or input images. Sites that use GenAI to generate adult content, including images and videos, will not be categorized under AI-media. Instead, they are covered under the ‘Adult’ category. |
|
AI Data and Workflow Optimizer |
Data optimization sites that utilize artificial intelligence to provide functionalities such as automated data cleaning, transformation, and analysis, as well as streamlining and managing repetitive workflow tasks to improve efficiency and productivity. |
|
AI Platform Service |
Sites that provide comprehensive tools and services for GenAI application development, including chatbot creation, model training, deployment, and optimization, as well as access to pre-trained models and code libraries. These platforms streamline the development process, facilitate collaboration, and enable developers to focus on core application logic without managing infrastructure or building models from scratch. |
|
AI Meeting Assistant |
Sites that leverage artificial intelligence to provide meeting assistance services, including summarizing key points, highlighting action items, and generating follow-up task lists. |
|
AI Website Generator |
Sites that leverage artificial intelligence for creating websites based on user input and preferences include generating content, layout design, and building code for the websites. The category doesn't include sites that lack AI functionalities and rely solely on pre-built templates or manual design tools. |
|
Auctions |
Sites that promote the sale of goods between individuals. Auctions with donation purposes are categorized as Society. |
|
Business and Economy |
Sites with content related to marketing, management, economics, entrepreneurship, or running a business, including the following:
|
|
Command and Control |
Command-and-control (C2) URLs and domains used by malware or compromised systems to surreptitiously communicate with an attacker's remote server to receive malicious commands or exfiltrate data. |
|
Compromised Website |
Benign or legitimate sites that have been hacked or infected with content such as malicious scripts, viruses, trojans, or executables. |
|
Computer and Internet Info |
Sites that provide general information about computers and the internet, including sites about the following topics:
Programming may have some overlap with the Reference and Research category, but the primary category should be Computer and Internet Info. |
|
Content Delivery Networks |
Sites whose primary focus is delivering content, such as advertisements, media, files, and image servers, to third parties. |
|
Copyright Infringement |
Domains with illegal content, such as content that allows the illegal download of software or other intellectual property, which poses a potential liability risk. Sites that provide peer-to-peer file exchange services or general streaming media belong to their own respective categories. |
|
Cryptocurrency |
Sites that promote cryptocurrencies, cryptomining (but not embedded crypto miners) sites, cryptocurrency exchanges and vendors, and sites that manage cryptocurrency wallets and ledgers. Sites referencing cryptocurrency or malicious sites related to cryptocurrency will be categorized separately. For example, sites that explain how cryptocurrencies and blockchain technology work fall under Computer and Internet Info. |
|
Dating |
Sites offering online dating services, advice, or other personal ads. Dating sites that offer sexual chat rooms fall under the Adult category. |
|
Dynamic DNS |
Sites that provide or utilize dynamic DNS services to associate domain names with dynamic IP addresses. Dynamic DNS is often used by attackers for command-and-control communication and other malicious purposes. |
|
Educational Institutions |
Official sites for schools, colleges, universities, school districts, online classes, and other academic institutions. Also includes sites for tutoring academies. This category refers to larger, established educational institutions, such as elementary schools, high schools, and universities. |
|
Encrypted DNS |
Sites for DNS resolver service providers, which offer security and privacy for end users by encrypting DNS requests and responses using protocols like DNS over HTTPS (DoH). |
|
Entertainment and Arts |
Sites for movies, television, radio, videos, programming guides or tools, comics, performing arts, museums, art galleries, or libraries. Includes sites for the following:
|
|
Extremism |
Sites promoting terrorism, racism, fascism, or other views that discriminate against people or groups of different ethnic backgrounds, religions, and other beliefs. In some regions, laws and regulations may prohibit allowing access to extremist sites, and allowing access may pose a liability risk. Websites that discuss controversial political or religious views fall under the Philosophy and Political Advocacy and Religion categories, respectively. |
|
Financial Services |
Sites pertaining to personal finances or advice, such as online banking, loans, mortgages, debt management, credit card companies, foreign currency exchanges (FOREX), and insurance companies. Excludes sites related to health insurance, stock markets, brokerages, or trading services. |
|
Gambling |
Sites that facilitate the exchange of real or virtual money through lotteries or gambling. Includes related sites that provide information, tutorials, or advice on gambling, such as how to bet odds and pools. Corporate websites for hotels and casinos that don't enable gambling fall under the Travel category. |
|
Games |
Sites that provide online play or downloads of video or computer games, game reviews, tips, cheats, or related publications and media. Includes sites that provide instructions for nonelectronic games, facilitate the sale or trade of board games, or support or host online sweepstakes and giveaways. |
|
Government |
Official websites for local, state, and national governments, as well as related agencies, services, or laws. Sites for public libraries and military institutions fall under the Reference and Research and Military categories, respectively. |
|
Grayware |
Sites with content that don't pose a direct security threat but that display other intrusive behavior and tempt end users to grant remote access or perform other unauthorized actions. Grayware includes the following:
|
|
Hacking |
Sites related to the illegal or questionable access to or use of communications equipment or software, including the development and distribution of such programs, how-to-advice, or tips that may result in the compromise of networks and systems. Includes sites that facilitate the bypass of licensing and digital rights systems. |
|
Health and Medicine |
Sites containing information regarding general health, issues, and traditional and nontraditional tips, remedies, and treatments. Includes sites for various medical specialties, practices, facilities (such as gyms and fitness clubs), and professionals. Sites related to medical insurance and cosmetic surgery are also included. |
|
Home and Garden |
Sites with information, products, and services related to home repair and maintenance, architecture, design, construction, decor, and gardening. |
|
Hunting and Fishing |
Sites that provide hunting and fishing tips or instructions or facilitate the sale of related equipment and paraphernalia. Sites that primarily sell firearms (even if they are used for hunting) fall under the Weapons category. |
|
Insufficient Content |
Sites and services that present test pages, have no content, provide API access not intended for end-user display, or require authentication without displaying any other content suggesting a different categorization. |
|
Internet Communications and Telephony |
Sites that support or provide services for video chatting, instant messaging, or other telephony capabilities. |
|
Internet Portals |
Sites that serve as a starting point for users, usually by aggregating a broad set of content and topics. |
|
Job Search |
Sites that provide job listings, employer reviews, interview advice and tips, or related services for both employers and prospective candidates. |
|
Legal |
Sites that provide information, analysis, or advice regarding the law, legal services, legal firms, or other legal-related issues. |
|
Malware |
Sites containing or known to host malicious content, executables, scripts, viruses, trojans, and code. |
|
Marijuana |
Sites that discuss, encourage, promote, offer, sell, supply or otherwise advocate the use, cultivation, manufacture, or distribution of marijuana and its myriad aliases, whether for recreational or medicinal purposes. Includes sites with content regarding marijuana-related paraphernalia. |
|
Military |
Sites with information or commentary on military branches, recruitment, current or past operations, or any related paraphernalia. Includes sites for military and veteran associations. |
|
Motor Vehicles |
Sites with information relating to reviews, sales, trading, modification, parts, and other related discussions of automobiles, motorcycles, boats, trucks, and recreational vehicles (RVs). |
|
Music |
Sites related to music sales, distribution, or information. Includes websites for music artists, groups, labels, events, lyrics, and other information regarding the music business. Excludes music streaming sites. |
|
Newly Registered Domains |
Sites that have been registered within the last 32 days. Newly registered domains are often generated purposely or by domain generation algorithms and can be used for malicious activity. |
|
News |
Online publications, newswire services, and other websites that aggregate current events, weather, or other contemporary issues. Includes the following:
If the magazine or news website focuses on a specific topic like sports, travel, fashion, it gets categorized based on the dominant content on the site. |
|
Not-Resolved |
This category indicates that the website wasn't found in the local URL filtering database or cache and the firewall was unable to connect to the cloud database to check the category. |
|
Nudity |
Sites that contain nude or seminude depictions of the human body, regardless of context or intent, such as artwork. Includes nudist or naturist sites containing images of participants. |
|
Online Storage and Backup |
Sites that provide online storage of files for free or as a service. Includes photo-sharing sites. |
|
Parked |
URLs that host limited content or click-through ads, which may generate revenue for the host entity but generally don't contain content that is useful to end users. Includes domains that are for sale. Parked sites with adult content fall under the Adult category. |
|
Peer-to-peer |
Sites that provide access to or clients for peer-to-peer sharing of torrents, download programs, media files, or other software applications. Primarily applicable to those sites with BitTorrent download capabilities. Excludes shareware or freeware sites. |
|
Personal Sites and Blogs |
Personal websites and blogs by individuals or groups. If such sites have a dominant topic associated with another category, they will be categorized with both categories. |
|
Philosophy and Political Advocacy |
Sites containing information, viewpoints, or campaigns regarding philosophical or political views. |
|
Phishing |
Web content that covertly attempts to harvest information, such as login credentials, credit card information, account numbers, PINs, and other personally identifiable information (PII), voluntarily or involuntarily, from victims using social engineering techniques. Includes technical support scams and scareware. |
|
Private IP Addresses |
This category includes IP addresses defined in RFC 1918, 'Address Allocation for Private Intranets,' which are as follows:
Includes domains not registered with the public DNS system (such as *.local and *.onion). Private IP addresses (and hosts) are unique to the host environment and are invisible to PAN-DB. As a result, Palo Alto Networks does not assign a risk rating to sites in this category, and the default action is allow. |
|
Proxy Avoidance and Anonymizers |
Proxy servers and other methods that bypass URL filtering or monitoring. VPNs with corporate-level usage fall under the Internet Communication and Telephony category. |
|
Questionable |
Sites containing tasteless humor or offensive content targeting specific demographics of individuals or groups of people. |
|
Ransomware |
Sites known to host ransomware or malicious traffic involved in conducting ransomware campaigns that generally threaten to publish private data or keep access to specific data or systems blocked, usually by encrypting it, until the demanded ransom is paid. Includes URLs that deliver related stealers, wipers, and loaders that may carry ransomware payloads. |
|
Real Estate |
Sites that provide information on property rentals, sales, and related tips or information, including sites for the following:
Sites for mortgage and loan servicers fall under the Financial Services category. |
|
Real-Time Detection ( Advanced URL Filtering only ) |
URLs that have been analyzed and detected by real-time inline analysis as part of Advanced URL Filtering. |
|
Recreation and Hobbies |
Sites that consist of information, forums, associations, groups, or publications related to recreational activities and hobbies. Sites that sell products related to recreational activities or hobbies, such as REI.com, fall under the Shopping category. |
|
Reference and Research |
Sites that provide personal, professional, or academic reference portals, materials, or services, including online dictionaries, maps, almanacs, census information, libraries, genealogy, and scientific information. Includes sites for or related to the following:
|
|
Religion |
Sites with information regarding various religions, related activities, or events. Includes sites for religious organizations, religious officials, places of worship, fortune-telling, astrology, horoscopes, and religious paraphernalia. Sites for private primary or secondary schools affiliated with a religious organization, such as Catholic schools, with a curriculum that teaches general religious education and secular subjects fall under the Educational Institutions category. |
|
Remote Access |
Sites that provide tools or information to facilitate authorized remote access to private computers and attached networks. |
|
Scanning Activity ( Advanced URL Filtering only ) |
Campaigns that are conducted by adversaries that can be indicators of compromise, or attempts at conducting targeted attacks or probing for existing vulnerabilities. These are usually part of reconnaissance activity conducted by adversaries. |
|
Search Engines |
Sites that provide a search interface using keywords, phrases, or other parameters that may return information, websites, images, or other files as results. |
|
Sex Education |
Sites that provide information on reproduction, sexual development, safe sex practices, sexually transmitted diseases, birth control, tips for better sex, and any related products or paraphernalia. Includes sites for related groups, forums, or organizations. |
|
Shareware and Freeware |
Sites that provide access to software, screensavers, icons, wallpapers, utilities, ringtones, themes, or widgets for free or donations. Includes open-source projects. |
|
Shopping |
Sites that facilitate the purchase of goods and services. Includes online merchants, sites for department stores, retail stores, catalogs, and price aggregation or monitoring tools. Sites in this category should be online merchants that sell a variety of items (or whose main purpose is online sales). A website for a cosmetics company that happens to allow online purchasing falls under the Cosmetics category. |
|
Social Networking |
User communities or sites where users interact with each other, post messages, pictures, and otherwise communicate with groups of people. Personal sites, blogs, or forums fall under the Personal Sites and Blogs category. |
|
Society |
Sites with content related to the general population or issues that impact a large variety of people, such as fashion, beauty, philanthropic groups, societies, or children. Includes restaurant websites. Corporate websites related to food, such as Burger King, fall under the Business and Economy category. |
|
Sports |
Sites with information about sporting events, athletes, coaches, officials, teams or organizations, scores, schedules, related news, or sports paraphernalia. Includes websites for fantasy sports and virtual sports leagues. Sites with the main purpose of selling sports goods fall under the Shopping category. |
|
Stock Advice and Tools |
Sites with information about the stock market, trading of stocks or options, portfolio management, investment strategies, quotes, or related news. |
|
Streaming Media |
Sites that stream audio or video content for free or purchase, including online radio stations, streaming music services, and the archiving of podcasts. |
|
Swimsuits and Intimate Apparel |
Sites that include information or images concerning swimsuits, intimate apparel, or other suggestive clothing. |
|
Training and Tools |
Sites that provide online education, training, and related materials. Includes driving or traffic schools, workplace training, games, applications, tools with educational purposes, and tutoring academies. Specific skills classes are categorized based on their subject. For example, websites for music classes fall under the Music category. |
|
Translation |
Sites that provide translation services, including both user input and URL translations. These sites can also allow users to circumvent filtering as the target page's content is presented within the context of the translator's URL. |
|
Travel |
Sites that provide information about travel, such as tips, deals, pricing, destination information, tourism, and related services, such as booking or price monitoring tools. Includes websites for the following:
|
|
Unknown |
Sites that have not yet been identified by Palo Alto Networks. If availability of this site is critical to your business and you must allow the traffic, alert on unknown sites, apply the best practice Security profiles to the traffic, and investigate the alerts. PAN-DB Real-Time Updates learn unknown sites after a first attempt to access these sites, so unknown URLs are identified quickly and become known URLs that the firewall can then handle based on the actual URL category. |
|
Weapons |
Sites that handle sales or offer reviews, descriptions of, or instructions regarding weapons, armor, bulletproof vests, and their use. Sites related to clay shooting, shooting ranges, and archery receive the primary category of Weapons and a secondary category of Sports. |
|
Web Advertisements |
Sites with advertisements, media, content, and banners. Includes pages for subscribing and unsubscribing from newsletters or ads. |
|
Web-based Email |
Any website that provides access to an email inbox and the ability to send and receive emails. Emphasis is given to websites that offer free or paid public access to such services. |
|
Web Hosting |
Sites that offer free or paid hosting services for webpages. Includes sites with information about web development, publication, promotion, and other methods of increasing traffic. |
Security-Focused URL Categories
PAN-DB automatically evaluates and assigns a risk category ( high-risk , medium-risk , and low-risk ) to URLs that it either has not classified as malicious or no longer classifies as malicious because they have displayed only benign activity for at least 30 days. Each risk category has specific criteria that must be met for a URL to receive a given category. As site content changes, the risk category and policy enforcement dynamically adapt.
If PAN-DB determines that a URL belongs to a
malicious URL category
, it does not assign the site a risk category. Instead, the firewall automatically blocks the site because it poses an unacceptable risk for most environments.
Private IP addresses (and hosts) are unique to the host environment and are invisible to PAN-DB. As a result, Palo Alto Networks does not assign a risk rating to sites in this category.
Security-focused URL categories facilitate targeted decryption and policy enforcement, helping reduce your attack surface. For example, you can block users from accessing high- and medium-risk websites and newly registered domains or decrypt traffic to these categories if you choose to allow them.
The following table lists descriptions and default and recommended policy actions for each risk category.
You cannot submit a change request for security-focused URL categories.
|
URL Category |
Description |
|
High Risk |
These sites remain high risk until PAN-DB completes site analysis and categorization.
Default and Recommended Policy Action: Alert |
|
Medium Risk |
These IP addresses remain medium risk until PAN-DB completes site analysis and categorization.
Default and Recommended Policy Action: Alert |
|
Low Risk |
Sites that are not medium or high risk. These sites have displayed benign activity for a minimum of 90 days. Default and Recommended Policy Action: Allow |
|
Newly Registered Domains |
Identifies sites that have been registered within the last 32 days. New domains are frequently used as tools in malicious campaigns. Newly registered domains are often generated purposefully or by domain generation algorithms and used for malicious activity. It’s a best practice to block this URL category. Default Policy Action: Alert Recommended Policy Action: Block |
Malicious URL Categories
We strongly recommend that you block the following URL categories, which identify malicious or exploitative content and behavior.
- command-and-control
- compromised-website
- copyright-infringement
- dynamic-dns
- extremism
- grayware
- malware
- newly-registered-domain
- parked
- phishing
- proxy-avoidance-and-anonymizers
- questionable
- ransomware
- scanning-activity
- unknown
For categories that you alert on, instead of block, you can strictly control how users interact with site content. For example, give users access to the resources they need (like developer blogs for research purposes or cloud storage services), but take the following precautions to reduce exposure to web-based threats:
- Follow the Anti-Spyware, Vulnerability Protection, and File Blocking best practices . A protective measure would be to block downloads of dangerous file types and obfuscated JavaScript for sites that you're alerting on.
- Target decryption based on URL category. A good start would be to decrypt high-risk and medium-risk sites.
- Display a response page to users when they visit high-risk and medium-risk sites. Alert them that the site they are attempting to access is potentially malicious, and advise them on how to take precautions if they decide to continue to the site.
- Prevent credential phishing by blocking users from submitting their corporate credentials to sites including those that are high-risk and medium-risk.
The following table lists categories that PAN-DB considers malicious and blocks by default, except for Private IP Addresses . Private IP addresses (and hosts) are unique to the host environment and are invisible to PAN-DB. As a result, Palo Alto Networks does not assign a risk rating to sites in this category.
|
Category |
Default Action |
|
Command and Control |
Block |
|
Grayware |
|
|
Malware |
|
|
Phishing |
|
|
Ransomware |
|
|
Scanning Activity |
|
|
Private IP Addresses |
Allowed (no default action) |
URL Filtering Use Cases
|
Where can I use this? |
What do I need? |
|
Notes:
|
There are many ways to enforce web page access beyond only blocking and allowing certain sites. For example, you can use multiple categories per URL to allow users to access a site, but block particular functions like submitting corporate credentials or downloading files. You can also use URL categories to enforce different types of policy , such as Authentication, Decryption, QoS, and Security.
Read on for more about the different ways that you can deploy URL filtering.
Control web access based on URL category
You can create a URL Filtering profile that specifies an action for a URL category and attach the profile to a Security policy rule. The firewall enforces policy against traffic based on the settings in the profile. For example, to block all gaming websites you would configure the block action for the games category in a URL Filtering profile. After, you’d attach the profile to the Security policy rule(s) that allow web access.
Multi-Category URL Filtering
Every URL can have up to four categories, including a risk category that indicates the likelihood a site will expose you to threats. More granular URL categorizations lets you move beyond a basic “block-or-allow” approach to web access. Instead, you can control how your users interact with online content that, while necessary for business, is more likely to be used as part of a cyberattack.
For instance, you might consider certain URL categories risky to your organization, but are hesitant to block them outright as they also provide valuable resources or services (like cloud storage services or blogs). Now, you can allow users to visit sites that fall into these types of categories while decrypting and inspecting traffic and enforcing read-only access to the content.
You can also define a custom URL category by selecting Category Match and specifying two or more PAN-DB categories of which the new category will consist. Creating a custom category from multiple categories allows you to target enforcement for a website or page that matches all of the categories specified in the custom URL category object.
Block or allow corporate credential submissions based on URL category
Prevent credential phishing by enabling the firewall to detect corporate credential submissions to sites, and then control those submissions based on URL category. Block users from submitting credentials to malicious and untrusted sites, warn users against entering corporate credentials on unknown sites or reusing corporate credentials on non-corporate sites, and explicitly allow users to submit credentials to corporate and sanctioned sites.
Enforce Safe Search Settings
Many search engines have a safe search setting that filters out adult images and videos from search results. You can enable the firewall to block search results or transparently enable safe search for end users that are not using the strictest safe search settings. The firewall supports safe search enforcement for the following search providers: Google, Yahoo, Bing, Yandex, and YouTube. See how to get started with Safe Search Enforcement .
Enforce Password Access to Certain Sites
You can block access to a site for most users while allowing certain users to access the site. See how to allow password access to certain sites .
Block high-risk file downloads from certain URL categories
You can block high-risk file downloads from specific URL categories by creating a Security policy rule with a File Blocking profile attached.
Enforce Security, Decryption, Authentication, and QoS policies based on URL category
You can enforce different types of firewall policies based on URL categories. For example, suppose you have enabled decryption , but want to exclude certain personal information from being decrypted. In this case you could create a Decryption policy rule that excludes websites that match the URL categories financial-services and health-and-medicine from decryption. Another example would be to use the URL category streaming-media in a QoS policy to apply bandwidth controls to websites that fall in to this category.
The following table describes the policies that accept URL categories as match criteria:
|
Policy Type |
Description |
|
You can also use URL categories to phase-in decryption, and to exclude URL categories that might contain sensitive or personal information from decryption (like financial-services and health-and-medicine). Plan to decrypt the riskiest traffic first (URL categories most likely to harbor malicious traffic, such as gaming or high-risk) and then decrypt more as you gain experience. Alternatively, decrypt the URL categories that don’t affect your business first (if something goes wrong, it won’t affect business), for example, news feeds. In both cases, decrypt a few URL categories, listen to user feedback, run reports to ensure that decryption is working as expected, and then gradually decrypt a few more URL categories, and so on. Plan to make decryption exclusions to exclude sites from decryption if you can’t decrypt them for technical reasons or because you choose not to decrypt them. Decrypting traffic based on URL categories is a best practice for both URL Filtering and Decryption . |
|
|
To ensure that users authenticate before being allowed access to a specific category, you can attach a URL category as a match criterion for Authentication policy rules. |
|
|
Use URL categories to allocate throughput levels for specific website categories. For example, you may want to allow the streaming-media category, but limit throughput by adding the URL category to a QoS policy rule. |
|
|
You can use a URL category as match criteria or create a URL Filtering profile that specifies an action for each category and attach it to a Security policy rule. Using URL Categories as Match Criteria vs. Applying URL Filtering Profile to a Security Policy Rule
In a URL Filtering profile, the actions specified for each URL category only apply to traffic destined for the categories specified in the Security policy rule. You can also apply a particular profile to multiple rules. If for example, the IT-security group in your company needs access to the hacking category, but all other users are denied access to the category, you must create the following rules:
You must list the policy that allows access to hacking before the policy that blocks hacking . This is because the firewall evaluates Security policy rules from the top down, so when a user who is part of the security group attempts to access a hacking site, the firewall evaluates the policy rule that allows access first and grants the user access. The firewall evaluates users from all other groups against the general web access rule that blocks access to the hacking sites. |
Configure URL Filtering
Activate Advanced URL Filtering License
|
Where can I use this? |
What do I need? |
|
Notes:
|
After familiarizing yourself with the concepts in URL Filtering Basics , you are ready to get started with URL Filtering . From activating an Advanced URL Filtering license (if applicable) to testing your configuration, this chapter covers what you need for an effective URL filtering deployment. To get the most out of your deployment, follow the URL Filtering best practices .
Activate Advanced URL Filtering License
Get Started with URL Filtering
|
Where can I use this? |
What do I need? |
|
Notes:
|
The Advanced URL Filtering subscription provides real-time URL analysis and malware prevention. In addition to access to PAN-DB, the Palo Alto Networks-developed URL filtering database for high-performance URL lookups, it also offers coverage against malicious URLs and IP addresses.
Advanced URL Filtering features are available on next-generation firewalls (virtual and on-premises), Strata Cloud Manager, Prisma Access (Managed by Panorama), Cloud NGFW for AWS, and Cloud NGFW for Azure. However, next-generation firewalls and Cloud NGFW for Azure require an Advanced URL Filtering subscription, while all Prisma Access and Cloud NGFW for AWS licenses include Advanced URL Filtering capabilities.
To check the compatibility of Advanced URL Filtering features with each Palo Alto Networks platform that supports URL Filtering, review URL Filtering Support .
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there for license activation.
If you’re using Strata Cloud Manager:
- Obtain and install an Advanced URL Filtering license.
The Advanced URL Filtering license includes access to PAN-DB; if the license expires, the firewall ceases to perform all URL filtering functions, URL category enforcement, and URL cloud lookups. Additionally, all other cloud based updates will not function until you install a valid license.
- Select DeviceLicenses and, in the License Management section, select the license installation method:
- Retrieve license keys from license server
- Activate feature using authorization code
- Confirm that the Advanced URL Filtering section, Date Expires field, displays a valid date.
When you activate the Advanced URL Filtering license, your license entitlements for PAN-DB and Advanced URL Filtering might not display correctly on the firewall — this is a display anomaly, not a licensing issue, and does not affect access to the services. You can update the licenses on the firewall to rectify the display issue by using the following CLI command: request license fetch .
- Download and install the latest PAN-OS content release . PAN-OS Applications and Threats content release 8390-6607 and later allows firewalls operating PAN-OS 9.x and later to identify URLs that have been categorized using the real-time-detection category introduced withx Advanced URL Filtering. For more information about the update, refer to the Applications and Threat Content Release Notes. You can also review Content Release Notes for apps and threats on the Palo Alto Networks Support Portal or directly in the firewall web interface: select DeviceDynamic Updates and open the Release Note for a specific content release version.
Follow the Best Practices for Applications and Threats Content Updates when updating to the latest content release version.
- Schedule the firewall to download dynamic updates for Applications and Threats.
A Threat Prevention license is required to receive content updates, which covers Antivirus and Applications and Threats.
- Select DeviceDynamic Updates .
- In the Schedule field in the Applications and Threats section, click the None link to schedule periodic updates.
You can only schedule dynamic updates if the firewall has direct Internet access. If updates are already scheduled in a section, the link text displays the schedule settings.
The Applications and Threats updates sometimes contain updates for URL filtering related to Safe Search Enforcement .
Next Steps:
- Configure URL filtering to define your organization’s web usage policies.
- Test your URL filtering configuration .
Get Started with URL Filtering
Activate Advanced URL Filtering License
|
Where can I use this? |
What do I need? |
|
Notes:
|
The first step to get started with URL filtering is understanding the web activity patterns of users on your network.
To safely observe these patterns, we recommend the following:
- Review Palo Alto Networks predefined URL categories .
- Enter URLs into our Test A Site engine to see how PAN-DB categorizes them.
- Create a (mostly) passive URL Filtering profile that alerts on most categories. When you select the alert setting for a URL category, the firewall logs traffic to that category. Then, you can see the sites your users are accessing and decide on the appropriate site access for URL categories and specific sites.
Alerting on all web activity might create a large number of log files. As a result, you might only want to do this as part of an initial deployment. At that time, you can also reduce URL filtering logs by enabling the Log container page only option in the URL Filtering profile so only the main page that matches the category will be logged, not subsequent pages or categories that may be loaded within the container page.
- Block URL categories that we know are bad: malware, command-and-control, and phishing.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Use Test A Site to check how PAN-DB categorizes a specific website.
You can also use the platform to request a categorization change for any website that you believe has been incorrectly categorized.
- Create a passive URL Access Management profile that alerts on all categories.
The firewall generates a URL filtering log entry for websites in URL categories with an action other than allow .
- Select ManageConfigurationSecurity ServicesURL Access Management .
- Under URL Access Management Profiles, select the checkbox next to the best-practices profile and then Clone the profile.
The cloned profile appears under the profiles with the name best-practices-1 .
- Select the best-practices-1 profile and rename it. For example, rename it to url-monitoring .
- Alert on all categories except malware, command-and-control, and phishing, which should remain blocked.
- Under Access Control , select all categories, then exclude malware , command-and-control , and phishing .
- With the categories still highlighted, click Set Access and choose Alert .
- Block access to malware , command-and-control , and phishing other known dangerous URL categories:
- phishing
- dynamic-dns
- unknown
- extremism
- copyright-infringement
- proxy-avoidance-and-anonymizers
- newly-registered-domain
- grayware
- parked
- Save the profile.
- Apply the URL Access Management profile to Security policy rules that allow traffic from clients in the trust zone to the internet.
A URL Access Management Profile is only active when it’s included in a profile group that a Security policy rule references.
Follow the steps to activate a URL Access Management profile (and any Security profile).
Make sure the Source Zone in the Security policy rules you apply to URL Access Management profiles to is set to a protected internal network.
- Push Config to commit the configuration.
- Check the URL logs to see which website categories your users are accessing. Blocked websites are also logged.
For information on viewing the logs and generating reports, see Monitoring Web Activity .
Select ActivityLog ViewerURL . URL Filtering reports provide a view of web activity in a 24-hour period.
- Next Steps:
- For everything that you don't allow or block, use risk categories to write policy rules based on website safety. PAN-DB categorizes every URL with a risk-level (high, medium, and low). While high and medium-risk sites are not confirmed malicious, they are closely associated with malicious sites. For example, they might be on the same domain as malicious sites or maybe they hosted malicious content until only very recently.
You can take precautionary measures to limit your users’ interaction high-risk sites especially, as there might be some cases where you want to give your users access to sites that might also present safety concerns (for example, you might want to allow your developers to use developer blogs for research, yet blogs are a category known to commonly host malware).
- Pair URL filtering with User-ID to control web access based on organization or department and to block corporate credential submissions to unsanctioned sites:
- URL filtering prevents credential theft by detecting corporate credential submissions to sites based on the site category. Block users from submitting credentials to malicious and untrusted sites, warn users against entering corporate credentials on unknown sites or reusing corporate credentials on non-corporate sites, and explicitly allow users to submit credentials to corporate sites.
- Add or update a Security policy rule with the passive URL Access Management profile so that it applies to a department user group, for example, Marketing or Engineering. Monitor the department activity, and get feedback from department members to understand the web resources that are essential to the work they do.
- Consider all the ways of leveraging URL filtering to reduce your attack surface. For example, a school may use URL filtering to enforce strict safe search for students. Or, if you have a security operations center, you might give only threat analysts password access to compromised or dangerous sites for research.
- Follow URL filtering best practices .
- Use Test A Site to check how PAN-DB categorizes a specific website.
You can also use the platform to request a categorization change for any website that you believe has been incorrectly categorized.
- Create a passive URL Filtering profile that alerts on all categories.
- Select ObjectsSecurity ProfilesURL Filtering .
- Select the default profile, and then click Clone . The new profile will be named default-1 .
- Select the default-1 profile and rename it. For example, rename it to URL-Monitoring.
- Configure the action for all categories to alert , except for malware, command-and-control, and phishing, which should remain blocked.
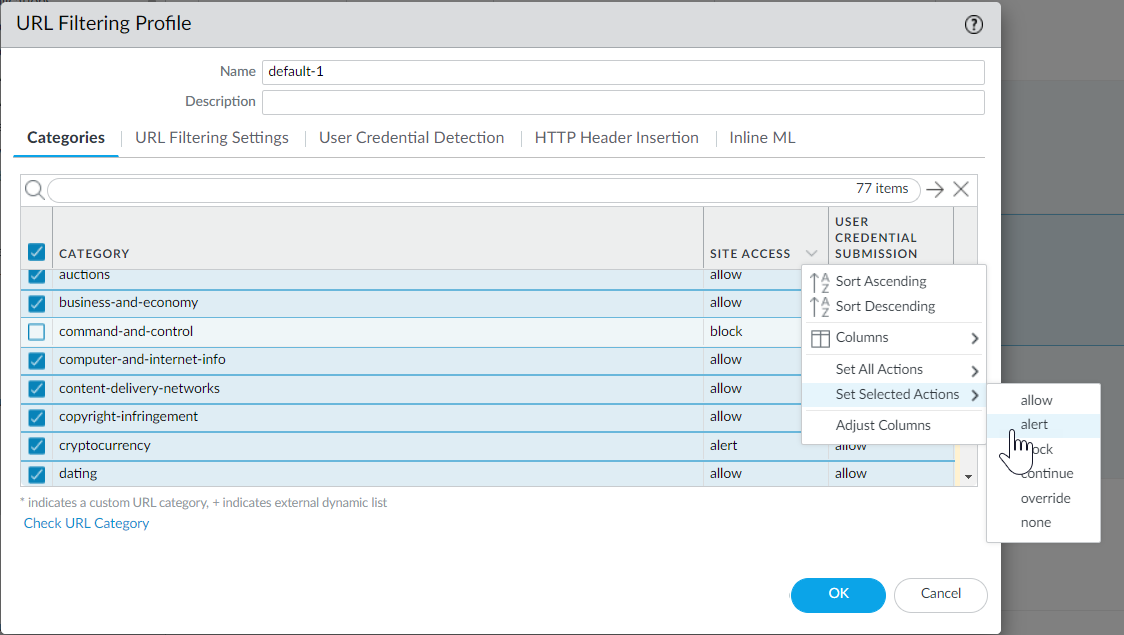
- In the section that lists all URL categories, select all categories and then de-select malware, command-and-control, and phishing.
- To the right of the Action column heading, mouse over and select the down arrow and then select Set Selected Actions and choose alert .
- Block access to known dangerous URL categories.
Block access to malware, phishing, dynamic-dns, unknown, command-and-control, extremism, copyright-infringement, proxy-avoidance-and-anonymizers, newly-registered-domain, grayware, and parked URL categories.
- Click OK to save the profile.
- Apply the URL Filtering profile to Security policy rules that allow traffic from clients in the trust zone to the Internet.
Make sure the Source Zone in the Security policy rules you add URL Access Management profiles to is set to a protected internal network.
- Select PoliciesSecurity . Then, select a Security policy rule to modify.
- On the Actions tab, edit the Profile Setting.
- For Profile Type , select Profiles . A list of profiles appears.
- For URL Filtering profile, select the profile you just created.
- Click OK to save your changes.
- Commit the configuration.
- View the URL filtering logs to see all of the website categories that your users are accessing. The categories you’ve set to block are also logged.
For information on viewing the logs and generating reports, see Monitoring Web Activity .
Select MonitorLogsURL Filtering . A log entry will be created for any website that exists in the URL filtering database that is in a category set to any action other than allow . URL Filtering reports give you a view of web activity in a 24-hour period. ( MonitorReports ).
- Next Steps:
- PAN-DB categorizes every URL with up to four categories, and every URL has a risk category (high, medium, and low). While high and medium-risk sites are not confirmed malicious, they are closely associated with malicious sites. For example, they might be on the same domain as malicious sites or maybe they hosted malicious content until only very recently. For everything that you do not allow or block, you can use risk categories to write simple policy rules based on website safety.
You can take precautionary measures to limit your users’ interaction high-risk sites especially, as there might be some cases where you want to give your users access to sites that might also present safety concerns (for example, you might want to allow your developers to use developer blogs for research, yet blogs are a category known to commonly host malware).
- Pair URL filtering with User-ID to control web access based on organization or department and to block corporate credential submissions to unsanctioned sites:
- URL filtering prevents credential theft by detecting corporate credential submissions to sites based on the site category. Block users from submitting credentials to malicious and untrusted sites, warn users against entering corporate credentials on unknown sites or reusing corporate credentials on non-corporate sites, and explicitly allow users to submit credentials to corporate sites.
- Add or update a Security policy rule with the passive URL Filtering profile so that it applies to a department user group, for example, Marketing or Engineering ( PoliciesSecurityUser ). Monitor the department activity, and get feedback from department members to understand the web resources that are essential to the work they do.
- Consider all the ways of leveraging URL filtering to reduce your attack surface. For example, a school may use URL filtering to enforce strict safe search for students. Or, if you have a security operations center, you might give only threat analysts password access to compromised or dangerous sites for research.
- Follow URL filtering best practices .
Configure URL Filtering
Get Started with URL Filtering
Configure Inline Categorization
|
Where can I use this? |
What do I need? |
|
Notes:
|
After you plan your URL filtering deployment , you should have a basic understanding of the types of websites your users are accessing. Use this information to create a URL Filtering profile that defines how the firewall handles traffic to specific URL categories. You can also restrict the sites to which users can submit corporate credentials or enforce strict safe search . To activate these settings, apply the URL Filtering profile to Security policy rules that allow web access.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
URL filtering is called URL Access Management in Strata Cloud Manager
- Check that your Prisma Access subscription covers Advanced URL Filtering.
- Go to Manage > Service Setup > Overview > Licenses to confirm what’s included with your subscription .
- Explore the URL Access Management Dashboard.
Go to ManageConfigurationSecurity ServicesURL Access Management .
Move between the Access Control , Settings , and Best Practices tabs to explore the available URL filtering features.
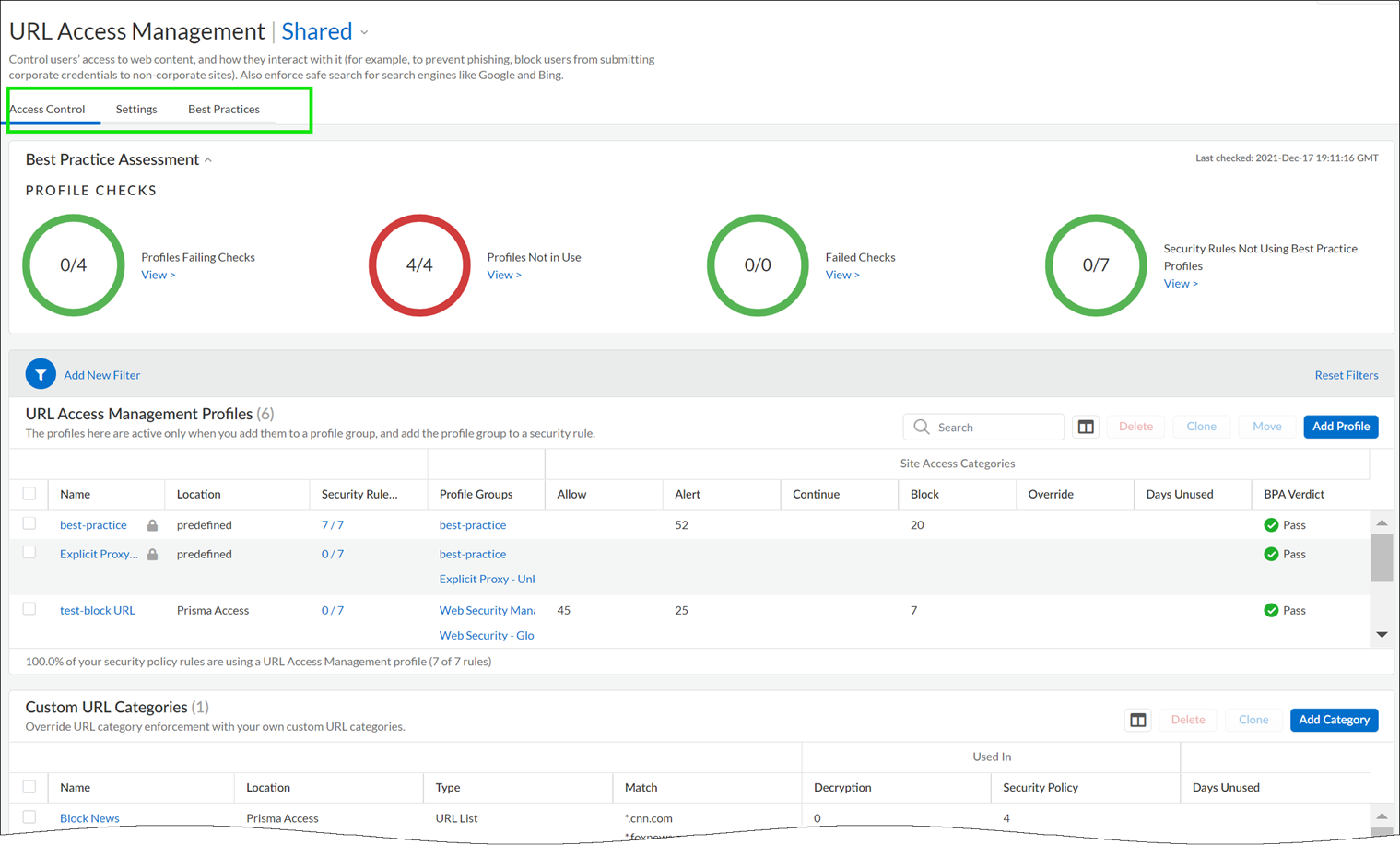
- Review and customize General URL Filtering Settings.
On the dashboard, go to Settings to see the default URL Filtering settings that apply across your Prisma Access environment, including:
- URL Filtering timeout and lookup settings
- URL Filtering overrides for certain admins
- URL Filtering response pages
- Remote Browser Isolation (RBI) settings
Automatically append end tokens to URLs in a custom URL category or external dynamic list
( PAN-OS 10.1 and earlier) If you add URLs to custom URL categories or external dynamic lists (EDLs) of URL list type and don't append a trailing slash (/), you may block or allow more URLs than intended. For example, entering example.com instead of example.com/ expands matching URLs to example.com.website.info or example.com.br. Prisma Access can automatically append a trailing slash to URLs in custom URL categories or EDLs so that, if you enter example.com , Prisma Access treats it as it would treat example.com/ and only considers that domain and its subdirectories matches. Go to SettingsGeneral Settings and enable the Append End Token to Entries option.
( PAN-OS 10.2 and later) Prisma Access automatically adds a trailing slash to domain entries.
You can customize these settings for each deployment type (mobile users, remote networks, or service connections).
- Create a URL Access Management profile.
On the URL Access Management dashboard, Add Profile and continue to specify web access settings:
- Access Control displays the URL categories and lists for which you can define web access and usage policy. By default, the Site Access and User Credential Submission permissions for all categories are set to Allow .
- For each URL category, configure User Credential Detection so that users can submit credentials only to sites in specified URL categories.
- Enable Safe Search Enforcement to enforce strict safe search filtering.
- Enable Log Container Page Only to log only those URLs that match the content type that is specified.
- Enabling HTTP Header Logging provides visibility into the attributes in the HTTP request sent to a server.
- Use the Advanced URL Inline Categorization to enable and configure real-time web page analysis and manage URL exceptions.
- Enable local Inline Categorization —Enables real-time analysis of URL traffic using machine learning models, to detect and prevent malicious phishing variants and JavaScript exploits from entering your network.
- Enable cloud Inline Categorization —Enables real-time analysis of URLs by forwarding suspicious web page contents to the cloud for supplemental analysis, using machine learning based detectors that complement the analysis engines used by local inline ML.
- You can define URL Exceptions for specific web sites to exclude from inline machine learning actions.
Note that:
- Best practice checks are built-in to the profile to give you a live evaluation of your configuration.
- After you’ve finished enabling a profile, you can examine profile usage to see if any security policy rules are referencing the profile.
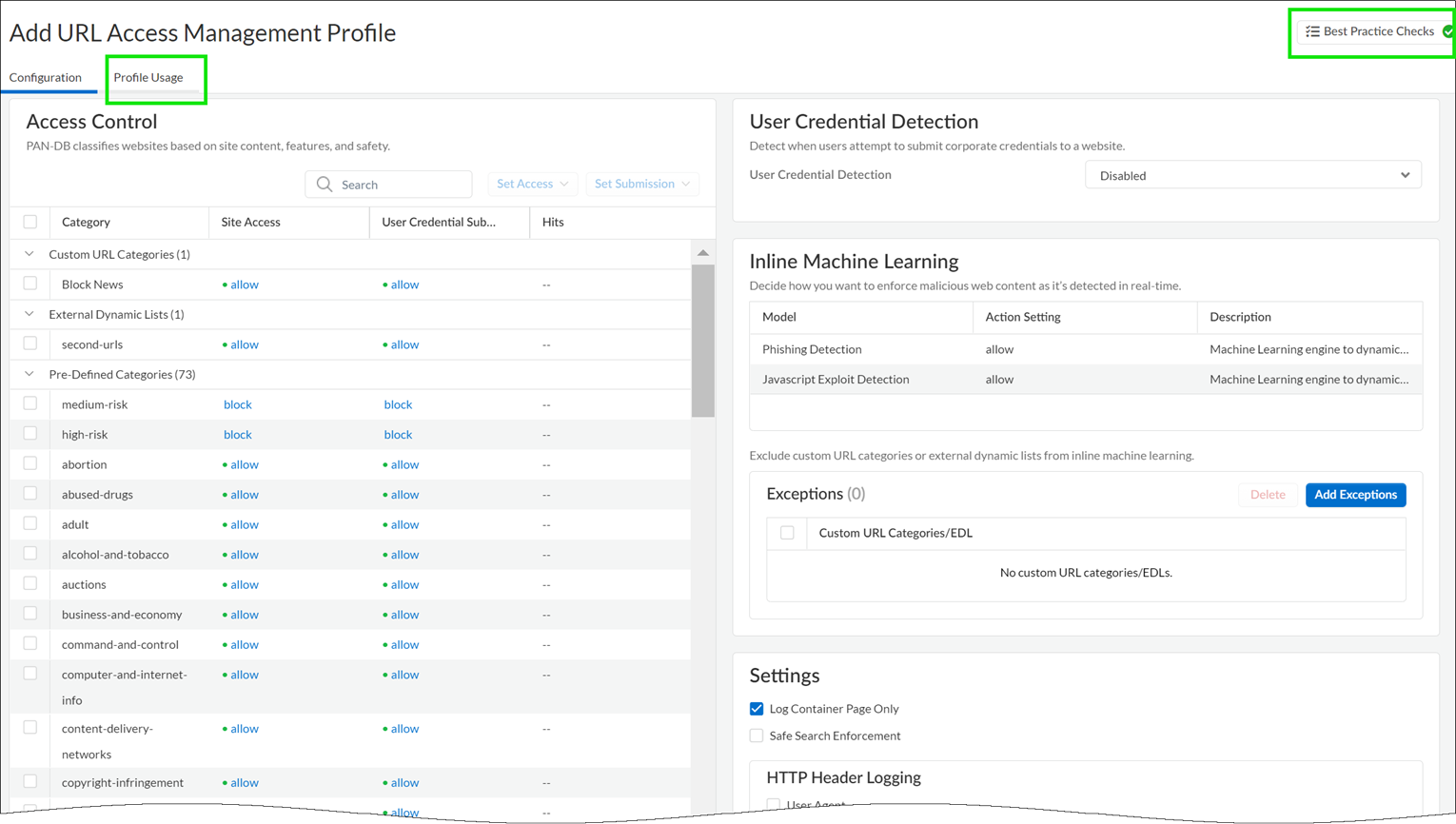
- Apply the URL Access Management profile to a Security policy rule.
A URL Access Management profile is only active when it’s included in a profile group that a Security policy rule references.
Follow the steps to activate a URL Access Management profile (and any Security profile). Be sure to Push Config
- Create a URL Filtering profile.
If you didn’t already, configure a best practice URL Filtering profile to ensure protection against URLs hosting malware or exploitive content.
Select ObjectsSecurity ProfilesURL Filtering and Add or modify a URL Filtering profile.
- Define site access for each URL category.
Select Categories , and then set Site Access:
- Select Allow to permit traffic destined for the URL category; this traffic is not logged.
- Select alert to gain visibility into sites that users are accessing. Traffic matching the category is allowed, and a URL filtering log is generated.
- Select block to deny access to traffic that matches the category and log this traffic.
- Select continue to display a response page to users that requires them to click Continue to proceed to a site in the category.
- To only allow access if users provide a configured password, select override . For more details, see Allow Password Access to Certain Sites .
- Detect corporate credential submissions to websites in allowed URL categories.
To ensure the best performance and a low false positive rate, the firewall automatically skips checking the credential submissions for any App-ID™ associated with sites that have never been observed hosting malware or phishing content—even if you enable checks in the corresponding category. The list of sites for which the firewall skips credential checking is automatically updated through Applications and Threats content updates.
1. In the URL Filtering profile, select the User Credential Detection tab.
2. Select one of the methods to check for corporate credential submissions to web pages from the User Credential Detection drop-down:
- Use IP User Mapping —Checks for valid corporate username submissions and verifies that the username matches the user logged in to the source IP address of the session. The firewall matches the submitted username against its IP address-to-username mapping table. You can use any of the user mapping methods described in Map IP Addresses to Users .
- Use Domain Credential Filter —Checks for valid corporate usernames and password submissions and verifies that the username maps to the IP address of the logged-in user. See Configure Credential Detection with the Windows-based User-ID Agent for instructions on how to set up User-ID to enable this method.
- Use Group Mapping —Checks for valid username submissions based on the user-to-group mapping table populated when you configure the firewall to map users to groups .
With group mapping, you can apply credential detection to any part of the directory or to a specific group, such as groups like IT that have access to your most sensitive applications.
3. This method is prone to false positives in environments that do not have uniquely structured usernames, so you should only use this method to protect your high-value user accounts.
4. Set the Valid Username Detected Log Severity that the firewall uses to log detection of corporate credential submissions (default is medium).
- Detect phishing and malicious JavaScript in real-time using local inline categorization .
- Allow or block users from submitting corporate credentials to sites based on URL category to prevent credential phishing .
To ensure the best performance and a low false positive rate, the firewall automatically skips checking the credential submissions for any App-ID associated with sites that have never been observed hosting malware or phishing content—even if you enable checks in the corresponding category. The list of sites for which the firewall skips credential checking is automatically updated through Applications and Threats content updates.
1. For each URL category to which you allow Site Access , select how you want to treat User Credential Submissions :
- alert —Allow users to submit credentials to the website but generate a URL filtering log each time a user submits credentials to sites in this URL category.
- allow (default)—Allow users to submit credentials to the website.
- block —Displays the anti-phishing block page to block users from submitting credentials to the website.
- continue —Present the anti-phishing continue page , which requires users to click Continue to access the site.
2. Configure the URL Filtering profile to detect corporate credential submissions to websites in allowed URL categories.
- Define URL category exceptions to specify websites that should always be blocked or allowed, regardless of URL category.
For example, to reduce URL filtering logs, you may want to add your corporate websites to the allow list so that no logs are generated for those sites or, if there is a website that is being overly used and is not work-related, you can add that site to the block list.
The policy actions configured for custom URL categories have priority enforcement over matching URLs in external dynamic lists.
Traffic to websites in the block list is always blocked regardless of the action for the associated category and traffic to URLs in the allow list is always allowed.
For more information on the proper format and wildcard usage, review the URL Category Exception Guidelines .
- Enable Safe Search Enforcement .
- Log only the page a user visits for URL filtering events.
1. Select URL Filtering Settings and enable Log container page only (default) so that the firewall logs only the main page that matches the category, not subsequent pages or categories that load within the container page.
2. To enable logging for all pages and categories, disable the Log container page only option.
- Enable HTTP Header Logging for one or more of the supported HTTP header fields.
Select URL Filtering Settings and select one or more of the following fields to log:
- User-Agent
- Referer
- X-Forwarded-For
- Save the URL Filtering profile.
Click OK .
- Apply the URL Filtering profile to Security policy rules that allow traffic from clients in the trust zone to the Internet.
Make sure the Source Zone in the Security policy rules to which you add URL Filtering profiles is set to a protected internal network.
1. Select PoliciesSecurity . Then, select a Security policy rule to modify.
2. On the Actions tab, edit the Profile Setting.
3. For Profile Type , select Profiles . A list of profiles appears.
4. For URL Filtering profile, select the profile you just created.
5. Click OK to save your changes.
- Commit the configuration.
- Test your URL filtering configuration .
- ( Best Practice ) Enable Hold client request for category lookup to block client requests while the firewall performs URL category lookups.
1. Select DeviceSetupContent-ID .
2. Select Hold client request for category lookup .
3. Commit your changes.
- Set the amount of time, in seconds, before a URL category lookup times out.
1. Select DeviceSetupContent-IDgear icon .
2. Enter a number for Category lookup timeout (sec) .
3. Click OK .
4. Commit your changes.
Configure Inline Categorization
|
Where can I use this? |
What do I need? |
|
Notes:
|
To enable inline categorization, attach a URL Filtering profile configured with inline categorization settings to a Security policy rule (see Set Up a Basic Security Policy ).
URL Filtering local inline categorization is not currently supported on the VM-50 or VM50L virtual appliance.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Update or create a URL Access Management profile.
- Go to Manage ConfigurationSecurity ServicesURL Access Management .
- On the URL Access Management dashboard, select a URL Access Management profile or Add Profile .
If you create a new profile, configure settings in the profile, such as site access for URL categories ( Access Control ). Configure URL Filtering (Cloud Management) describes the available settings.
- Under Advanced URL Inline Categorization , select an inline categorization type.
Both options enable real-time web page analysis and manage URL exceptions.
- Enable cloud Inline Categorization —Enables real-time analysis of URLs by forwarding suspicious web page contents to the cloud for supplemental analysis, using machine learning based detectors that complement the analysis engines used by local inline ML.
- Enable local Inline Categorization —Enables real-time analysis of URL traffic using machine learning models, to detect and prevent malicious phishing variants and JavaScript exploits from entering your network.
- You can also define URL Exceptions to exclude specific websites from inline machine learning actions.

- Save the profile.
- Apply the URL Access Management profile to a Security policy rule.
To activate a URL Access Management profile (and any Security profile), add it to profile group and reference the profile group in a Security policy rule.
- Log in to the PAN-OS web interface .
- Verify that you have an active legacy URL filtering or Advanced URL Filtering subscription.
Select DeviceLicenses and confirm that a URL filtering license is available and has not expired.
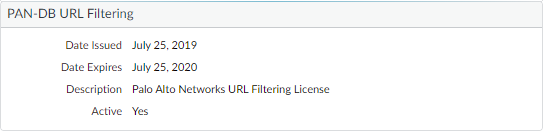
- Configure the URL Filtering Inline ML settings in a URL Filtering profile.
- Select ObjectsSecurity ProfilesURL Filtering , then Add or select a URL Filtering profile.
- Select Inline ML and define an Action for each inline ML model.
There are two classification engines available for each type of malicious webpage content: Phishing and JavaScript Exploit .
- Block —When the firewall detects a website with phishing content, the firewall generates a URL Filtering log entry.
- Alert —The firewall allows access to the website and generates a URL Filtering log entry.
- Allow —The firewall allows access to the website but does not generate a URL Filtering log entry.
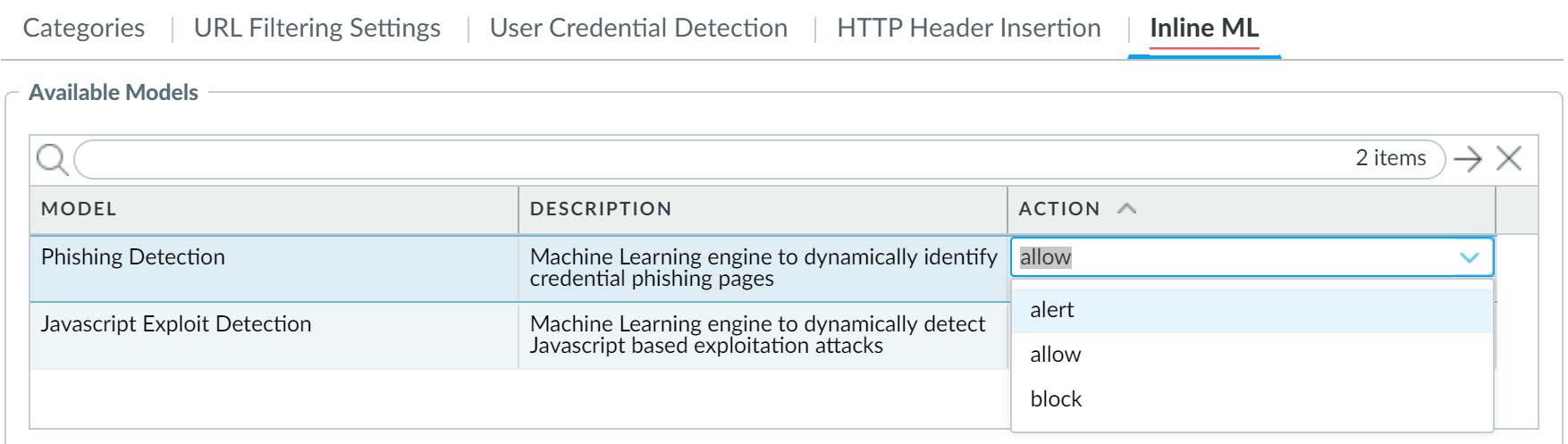
- Click OK to save your changes.
- Commit your changes.
- Optional Add URL exceptions to your URL Filtering profile if you encounter false-positives.
You can add exceptions by specifying an external dynamic list in the URL Filtering profile or by adding a web page entry from the URL Filtering logs to a custom URL category .
- Select Objects > Security Profiles > URL Filtering .
- Select a URL Filtering profile for which you want to exclude specific URLs, then select Inline ML .
- Add a pre-existing external dynamic list of URL type. If none is available, create a new external dynamic list .
- Click OK to save your changes.
- Commit your changes.
Add file exceptions from URL Filtering log entries.
- Select Monitor > Logs > URL Filtering and filter the logs for URL entries with an Inline ML Verdict of malicious-javascript or phishing . Select a URL Filtering log for a URL that you wish to create an exception for.
- Go to the Detailed Log View and scroll down to the Details pane, then select Create Exception located next to the Inline ML Verdict .
![]()
- Select a custom category for the URL exception, then click OK .
The new URL exception can be found in the list to which it was added, under Objects > Custom Objects > URL Category .
- Optional Verify the status of your firewall’s connectivity to the inline ML cloud service.
Use the following CLI command on the firewall to view the connection status.
show mlav cloud-status
For example:
show mlav cloud-status
MLAV cloud
Current cloud server: ml.service.paloaltonetworks.com
Cloud connection: connected
If you are unable to connect to the inline ML cloud service, verify that the ML domain ml.service.paloaltonetworks.com is not blocked.
To view information about web pages that have been processed using URL Filtering inline ML, filter the logs ( Monitor > Logs > URL Filtering ) based on Inline ML Verdict . Web pages that have been determined to contain threats are categorized with verdicts of either phishing or malicious-javascript . For example:
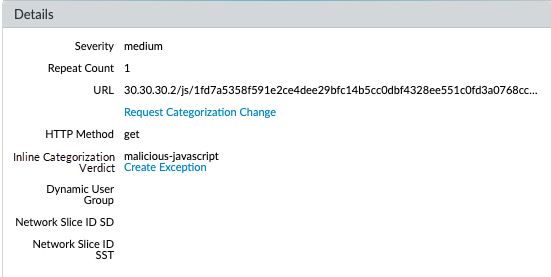
- Log in to the PAN-OS web interface.
- To take advantage of inline categorization, you must have an active Advanced URL Filtering subscription.
Local inline categorization can be enabled if you are a pre-existing holder of a legacy URL Filtering subscription.
Verify that you have an Advanced URL Filtering subscription. To verify subscriptions for which you have currently-active licenses, select DeviceLicenses and verify that the appropriate licenses are available and have not expired.

- Update or create a new URL Filtering profile to enable cloud inline categorization.
The policy action used by local and cloud inline categorization is dependent on the configured settings under the Categories tab.
- Select an existing URL Filtering Profile or Add a new one ( ObjectsSecurity ProfilesURL Filtering ).
- Select your URL Filtering profile and then go to Inline Categorization and enable the inline categorization methods you want to deploy.
- Enable cloud inline categorization —A cloud-based inline deep learning engine that analyzes suspicious web page content in real-time to protect users against zero-day web attacks, including targeted phishing attacks, and other web-based attacks that use advanced evasion techniques.
- Enable local inline categorization —A firewall-based detection engine using machine learning techniques to prevent malicious variants of JavaScript exploits and phishing attacks embedded in webpages.
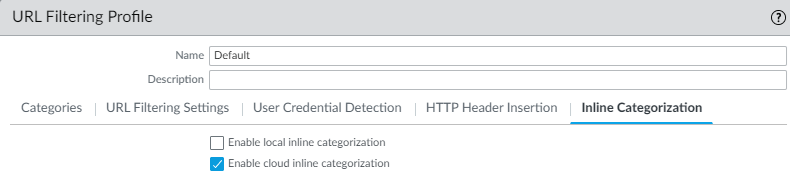
- Click OK and Commit your changes.
- Optional Add URL exceptions to your URL Filtering profile if you encounter false-positives. You can add exceptions by specifying an external dynamic list or custom URL category list in the URL Filtering profile. The specified exceptions apply to both cloud and local inline categorization.
URL exceptions created through other mechanisms that add entries to the custom URL category ( ObjectsCustom ObjectsURL Category )
can also function as exceptions for inline categorization.
- Select Objects > Security Profiles > URL Filtering .
- Select a URL Filtering profile for which you want to exclude specific URLs, then select Inline Categorization .
- Click Add to select a pre-existing URL-based external dynamic list or custom URL category. If none is available, create a new external dynamic list or custom URL category , respectively.
- Click OK to save the URL Filtering profile.
- Commit your changes.
- Required when the firewall is deployed with an explicit proxy server Configure the proxy server used to access the servers that facilitate requests generated by all configured inline cloud analysis features. A single proxy server can be specified and applies to all Palo Alto Networks update services, including all configured inline cloud and logging services.
- PAN-OS 11.2.3 and later Configure the proxy server through PAN-OS.
1. Select DeviceSetupServices and edit the Services details.
2. Specify the Proxy Server settings and Enable proxy for Inline Cloud Services . You can provide either an IP address or FQDN in the Server field.
The proxy server password must contain a minimum of seven characters.
3. Click OK .
- For the following releases only: PAN-OS 10.2.11 and later and PAN-OS 11.1.5 and later Configure the proxy server through the firewall CLI.
2. Configure the base proxy server settings using the following CLI commands:
3. set deviceconfig system secure-proxy-server <FQDN_or_IP>
4. set deviceconfig system secure-proxy-port <1-65535>
5. set deviceconfig system secure-proxy-user <value>
set deviceconfig system secure-proxy-password <value>
The proxy server password must contain a minimum of seven characters.
6. Enable the proxy server to send requests to the inline cloud service servers using the following CLI command:
debug dataplane mica set inline-cloud-proxy enable
7. View the current operational status of proxy support for inline cloud services using the following CLI command:
debug dataplane mica show inline-cloud-proxy
For example:
debug dataplane mica show inline-cloud-proxy
Proxy for Advanced Services is Disabled
- Optional Set the Cloud Content Fully Qualified Domain Name (FQDN) used by the firewall to handle inline categorization service requests. The default FQDN connects to hawkeye.services-edge.paloaltonetworks.com and then resolves to the closest cloud services server. You can override the automatic server selection by specifying a regional cloud content server that best meets your data residency and performance requirements.
The Cloud Content FQDN is a globally used resource and affects how other services that rely on this connection sends traffic payloads.
Verify that the firewall uses the correct Content Cloud FQDN ( DeviceSetupContent-IDContent Cloud Setting ) for your region and change the FQDN if necessary:
- US— us.hawkeye.services-edge.paloaltonetworks.com
- EU— eu.hawkeye.services-edge.paloaltonetworks.com
- UK— uk.hawkeye.services-edge.paloaltonetworks.com
The UK-based cloud content FQDN provides Advanced URL Filtering inline categorization service support by connecting to the backend service located in the EU (eu.hawkeye.services-edge.paloaltonetworks.com).
- APAC— apac.hawkeye.services-edge.paloaltonetworks.com
- Optional Verify the status of your firewall’s connectivity to the inline categorization servers.
- The ml.service.paloaltonetworks.com server provides periodic updates for firewall-based components related to the operation of cloud and local inline categorization.
Use the following CLI command on the firewall to view the connection status.
show mlav cloud-status
For example:
show mlav cloud-status
MLAV cloud
Current cloud server: ml.service.paloaltonetworks.com
Cloud connection: connected
If you are unable to connect to the inline ML cloud service, verify that the following domain is not being blocked: ml.service.paloaltonetworks.com.
- The hawkeye.services-edge.paloaltonetworks.com server is used by cloud inline categorization to handle service requests.
Use the following CLI command on the firewall to view the connection status.
show ctd-agent status security-client
For example:
show ctd-agent status security-client
...
Security Client AceMlc2(1)
Current cloud server: hawkeye.services-edge.paloaltonetworks.com
Cloud connection: connected
...
CLI output shortened for brevity.
If you are unable to connect to the Advanced URL Filtering cloud service, verify that the following domain is not being blocked: hawkeye.services-edge.paloaltonetworks.com.
- Install an updated firewall device certificate used to authenticate to the Advanced URL Filtering cloud service . Repeat for all firewalls enabled for cloud inline categorization.
- Test your URL filtering deployment .
URL Category Exceptions
Configure Inline Categorization
Guidelines for URL Category Exceptions
|
Where can I use this? |
What do I need? |
|
Notes:
|
You can exclude specific websites from URL category enforcement, ensuring that these websites are blocked or allowed regardless of the policy action associated with its URL categories. For example, you might block the social-networking URL category but allow access to LinkedIn. To create exceptions to URL category policy enforcement:
- Add the IP addresses or URLs of sites you want to block or allow to a custom URL category of URL List type. Then, define site access for the category in a URL Filtering profile. Finally, attach the profile to a Security policy rule.
You can also use a custom URL category as match criteria in a Security policy rule. Be sure to place the exception rule above any rules that block or allow the categories to which the URL exceptions belong.
- Add the URLs of sites you want to block or allow to an external dynamic list of URL List type. Then, use the external dynamic list in a URL Filtering profile or as match criteria in a Security policy rule . The benefit to using an external dynamic list is that you can update the list without performing a configuration change or commit on the firewall.
External dynamic lists of URL List type should not be confused with external dynamic lists of Domain List or IP Address List type. While external dynamic lists of URLs permit domains and IP addresses, the reverse is not true and result in invalid entries.
- Guidelines for URL Category Exceptions
- Create a Custom URL Category
- Use an External Dynamic List in a URL Filtering Profile
Guidelines for URL Category Exceptions
|
Where can I use this? |
What do I need? |
|
This feature has no prerequisites. |
The following guidelines describe how to populate URL category exception lists—custom URL categories or external dynamic lists of URLs. We provide examples of how to use wildcards and specific entries.
Basic Guidelines For URL Category Exception Lists
Consider the potential matches an entry might have before adding it to a URL category exception list. The following guidelines specify how to create an entry that blocks or allows the websites and pages you intend.
By default, the firewall automatically appends a trailing slash (/) to domain entries that do not end in a trailing slash (/) or asterisk (*). The addition of the trailing slash changes the URLs that the firewall considers a match and for which it enforces policy. In non-wildcard domain entries, the trailing slash limits matches to the given domain and its subdirectories. For example, example.com ( example.com/ after processing) matches itself and example.com/search .
In wildcard domain entries (entries with asterisks or carets), the trailing slash limits matches to URLs that conform to the specified pattern. For example, to match the entry *.example.com , a URL must include at least one subdomain and end with the root domain, example.com . The pattern is: <subdomain>.example.com ; news.example.com is a match, but example.com is not because it lacks a subdomain.
We recommend manually adding trailing slashes to clarify the intended matching behavior of an entry for anyone who inspects it. The trailing slash is invisible when added by the firewall.
Panorama™ management servers running PAN-OS ® 10.2 can only enable this feature for firewalls on the same software version. To enable this feature for firewalls running PAN-OS 10.1 or earlier, use the following CLI commands on each firewall:
admin@PA-850> debug device-server append-end-token on
admin@PA-850> configure
admin@PA-850# commit
To disable this feature, select DeviceSetupContent-IDURL Filtering . Then, deselect Append Ending Token . You may, however, block or allow access to more URLs than anticipated if you disable this feature. The firewall adds an implicit asterisk to the end of domain entries that do not end in a / or * . For example, if you add example.com to a URL list of allowed websites, the firewall interprets that entry as example.com.* . As a result, the firewall allows access to sites such as example.com.domain.xyz . URL Category Exceptions (PAN-OS 10.1 and earlier) describes the firewall’s behavior when you disable this feature.
- List entries are case-insensitive.
- Omit http and https from URL entries.
- Each URL entry can be up to 255 characters in length.
- Enter an exact match to the IP address or URL you want to block or allow or
use wildcards
to create a pattern match .
Different entries result in different exact matches. If you enter the URL for a specific web page ( example.com/contact ), the firewall limits matches to that page alone. Exact matching for domains restricts matches to the domain itself and its subdirectories.
- Consider adding the URLs most commonly used to access a website or page to your exception list (for example, blog.paloaltonetworks.com and paloaltonetworks.com/blog ) if the original entry is accessible from more than URL.
- The entry example.com is distinct from www.example.com . The domain name is the same, but the second entry contains the www subdomain.
Palo Alto Networks does not support regular expression use in custom URL category or external dynamic list entries. You must know the specific URLs or construct the URL patterns you want to match using wildcards and the following characters: . / ? & = ; + .
Wildcard Guidelines for URL Category Exception Lists
You can use asterisks (*) and carets (^) in URL category exception lists to configure a single entry to match multiple subdomains, domains, top-level domains (TLDs), or pages without specifying exact URLs.
How to Use Asterisk (*) and Caret (^) Wildcards
The following characters are token separators: . / ? & = ; + . Every string separated by one or two of these characters is a token. Use wildcard characters as token placeholders to indicate that a specific token can contain any value. In the entry docs.paloaltonetworks.com , the tokens are “docs”, “paloaltonetworks”, and “com”.
The following table describes how asterisks and carets work and provides examples.
|
* |
^ |
|
Indicates one or more variable subdomains, domains, TLDs, or subdirectories. Can use asterisk after trailing slash, for example, example.com/* . Ex: *.domain.com matches docs.domain.com and abc.xyz.domain.com . |
Indicates one variable subdomain, root domain, or TLD. Cannot use caret after trailing slash. The following entry is invalid: example.com/^ . Ex: ^.domain.com matches docs.domain.com and blog.domain.com . |
|
Key Point: Asterisks match a greater range of URLs than carets. An asterisk corresponds to any number of consecutive tokens, while a caret corresponds to exactly one token. An entry like xyz.*.com matches a greater number of sites than xyz.^.^.com ; xyz.*.com matches sites with any number of tokens between the strings, and xyz.^.^.com matches sites with exactly two tokens. |
|
- A wildcard must be the only character within a token. For example, example*.com is an invalid entry because example and * are in the same token. An entry can contain wildcards in more than one token, however.
- You can use asterisks and carets in the same entry (for example, *.example.^ ).
Do not create an entry with consecutive asterisks (*) or more than nine consecutive carets (^)—entries like these can affect firewall performance.
For example, do not add an entry like mail.*.*.com . Instead, depending on the range of websites you want to control access to, enter mail.*.com or mail.^.^.com .
URL Category Exception List—Examples
The following table displays example URL list entries, matching sites, and explanations for the matching behavior when the firewall automatically appends trailing slashes.
The entries in this table do not contain a trailing slash to reflect that the firewall appends one to applicable entries in the background. Additionally, exception lists may contain entries added before the trailing slash guidance. URL Category Exceptions—Examples (PAN-OS 10.1) shows matching behavior when the firewall does not append trailing slashes by default.
We recommend manually adding trailing slashes to clarify the intended matching behavior of an entry for anyone who inspects it. The trailing slash is invisible if added by the firewall.
|
URL Exception List Entry |
Matching Sites |
Explanation |
|
Example Set 1 |
||
|
paloaltonetworks.com |
paloaltonetworks.com paloaltonetworks.com/network-security/security-subscriptions |
The firewall appends a trailing slash to the entry, limiting matches to the exact domain and its subdirectories. |
|
paloaltonetworks.com/example |
paloaltonetworks.com/example |
The firewall does not append a trailing slash to this entry because the subdirectory example follows the domain. When you enter the URL for a specific web page, the firewall applies the exception action to the specified web page. |
|
Example Set 2—Asterisks |
||
|
*.example.com |
www.example.com docs.example.com support.tools.example.com |
The asterisk expands matches to all example.com subdomains. The firewall appends a trailing slash to entry, excluding matches to the right of example.com , the root domain. |
|
mail.example.* This entry yields the same matches with or without the trailing slash feature enabled. |
mail.example.com mail.example.co.uk mail.example.com/#inbox |
The asterisk expands matches to any URL following the mail.example.<TLD> pattern. |
|
example.*.com |
example.yoursite.com example.es.domain.com example.abc.xyz.com |
The asterisk expands matches to URLs where the left-most subdomain is example and the top-level domain is com . The trailing slash excludes matches to the right of the TLD. |
|
example.com/* |
example.com/photos example.com/blog/latest any example.com subdirectory |
The domain is followed by a / and an asterisk, which indicates that a subdirectory must be present. The asterisk serves as a token placeholder for any example.com subdirectory. The firewall does not append a trailing slash because the entry ends in an asterisk. |
|
Example Set 3—Carets |
||
|
google.^ Patterns such as example.co.^ are typically used to match country-specific domains such as example.co.jp . However, generic top-level domains (gTLDs) result in patterns such as example.co.^ matching example.co.info or example.co.amzn, which may not belong to the same organization. |
google.com google.info google.com/search?q=paloaltonetworks |
The caret expands matches to URLs beginning with google and ending in a single TLD. The trailing slash excludes matches to the right of the last token. |
|
^.google.com |
www.google.com news.google.com |
The caret expands matches to single-level subdomains of google.com . The firewall appends a trailing slash to the entry, excluding matches to the right of the root domain. |
|
^.^.google.com |
www.maps.google.com support.tools.google.com |
The two carets expand matches to URLs that include two consecutive subdomains before google.com . The firewall adds a trailing slash to the entry, excluding matches to the right of the root domain. |
|
google.^.com |
google.example.com google.company.com |
The caret expands matches to URLs where google is the left-most subdomain, followed by one token and .com . The firewall adds a trailing slash to the entry, excluding matches to the right of the TLD. |
Create a Custom URL Category
Guidelines for URL Category Exceptions
Use an External Dynamic List in a URL Filtering Profile
|
Where can I use this? |
What do I need? |
|
This feature has no prerequisites. |
You can create a custom URL category to define exceptions to URL category enforcement or define a new URL category from multiple categories.
Define Exceptions to URL Category Enforcement (URL List)
Specify a list of URLs (grouped under a single custom category) that you wish to enforce independently of their predefined URL categories . You can control access to this category in a URL Filtering profile that you apply to Security policy rules or use the category as match criteria in Security policy rules. For example, you can block the social-networking category but allow access to LinkedIn.
Define a Custom URL Category Based on Multiple PAN-DB Categories (Category Match)
Create a new category to target enforcement for websites or pages that match all of the categories defined as part of the custom category. For example, PAN-DB might classify a developer blog that your engineers use for research as personal-sites-and-blogs , computer-and-internet-info , and high-risk . To allow the engineers to access the blog and similar websites and gain visibility into these websites, you can create a custom URL category based on the three categories and set site access for the category to alert in a URL Filtering profile.
PAN-DB evaluates URLs against custom URL categories before external dynamic lists and predefined URL categories. Accordingly, the firewall enforces the Security policy rules for a URL in a custom URL list over the policy rules associated with the individual URL categories it exists in.
If multiple Security policy rules include a custom URL category, then the firewall enforces the Security policy rule with the strictest URL Filtering profile action for the matching traffic.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Select ManageConfigurationSecurity ServicesURL Access ManagementAccess Control .
- Under Custom URL Categories, select Add Category .
Enter a descriptive Name for the category.
- Set the custom URL category Type to either URL List or Category Match .
- URL List —Use this list type to add URLs that you want to enforce differently than the URL category to which they belong or to define a list of URLs as belonging to a custom category. Consult the Guidelines for URL Category Exceptions as you create URL list entries.
- Category Match —Provide targeted enforcement for websites that match a set of categories. The website or page must match all the categories defined in the custom category.
- Under Items , Add either URLs or existing categories.
- Save the custom URL category.
- Define Site Access and User Credential Submissions settings for the custom URL category.
1. Select ManageConfigurationSecurity ServicesURL Access ManagementURL Access Management Profiles .
2. Select an existing profile to modify or click Add Profile .
3. Under Access Control, select the custom URL category you created earlier. It sits under Custom URL Categories and above Pre-Defined Categories .
4. Set Site Access for the category.
5. Set User Credential Submissions for the category.
6. Save the profile.
- Apply the URL Access Management profile to a Security policy rule.
A URL Access Management profile is only active when it’s included in a profile group that a Security policy rule references.
Follow the steps to activate a URL Access Management profile (and any Security profile). Be sure to Push Config .
You can also use custom URL categories as Security policy rule match criterion. In this scenario, you do not define site access for the URL category in a URL Filtering profile. Instead, after creating a custom URL category, select the Security policy rule you want to add the custom URL category to ( ManageConfiguration Security ServicesSecurity Policy ). Under Applications, Services and URLs and URL Category Entities, click Add URL Categories . Select the custom URL category you created, and then Save the Security policy rule.
test URL Filtering profile action for the matching traffic.
- Select ObjectsCustom ObjectsURL Category .
- Add or modify a custom URL category, and give the category a descriptive Name .
- Set the category Type to either Category Match or URL List :
- URL List —Add URLs that you want to enforce differently than the URL category to which they belong. Use this list type to define exceptions to URL category enforcement or to define a list of URLs as belonging to a custom category. Consult URL Category Exceptions for guidelines on creating URL list entries.
By default, the firewall automatically appends a trailing slash (/) to domain entries ( example.com ) that do not end in a trailing slash or asterisk (*). The trailing slash prevents the firewall from assuming an implicit asterisk to the right of the domain. In non-wildcard domain entries, the trailing slash limits matches to the given domain and its subdirectories. For example, example.com ( example.com/ after processing) matches itself and example.com/search .
In wildcard domain entries (entries using asterisks or carets), the trailing slash limits matches to URLs that conform to the specified pattern. For example, to match the entry *.example.com , a URL must strictly begin with one or more subdomains and end with the root domain, example.com ; news.example.com is a match, but example.com is not because it lacks a subdomain.
We recommend manually adding trailing slashes to clarify the intended matching behavior of an entry for anyone who inspects your URL list. The trailing slash is invisible if added by the firewall. URL Category Exceptions discusses the trailing slash and matching behavior in further detail.
To disable this feature, go to DeviceSetupContent-IDURL Filtering . Then, deselect Append Ending Token . If you disable this feature, you may block or allow access to more URLs than intended. URL Category Exceptions (PAN-OS 10.1 and earlier) describes the firewall’s behavior when this feature is disabled.
- Category Match —Provide targeted enforcement for websites that match a set of categories. The website or page must match all the categories defined in the custom category.
- Click OK to save the custom URL category.
- Select ObjectsSecurity ProfilesURL Filtering and Add or modify a URL Filtering profile.
Your new custom category displays under Custom URL Categories :
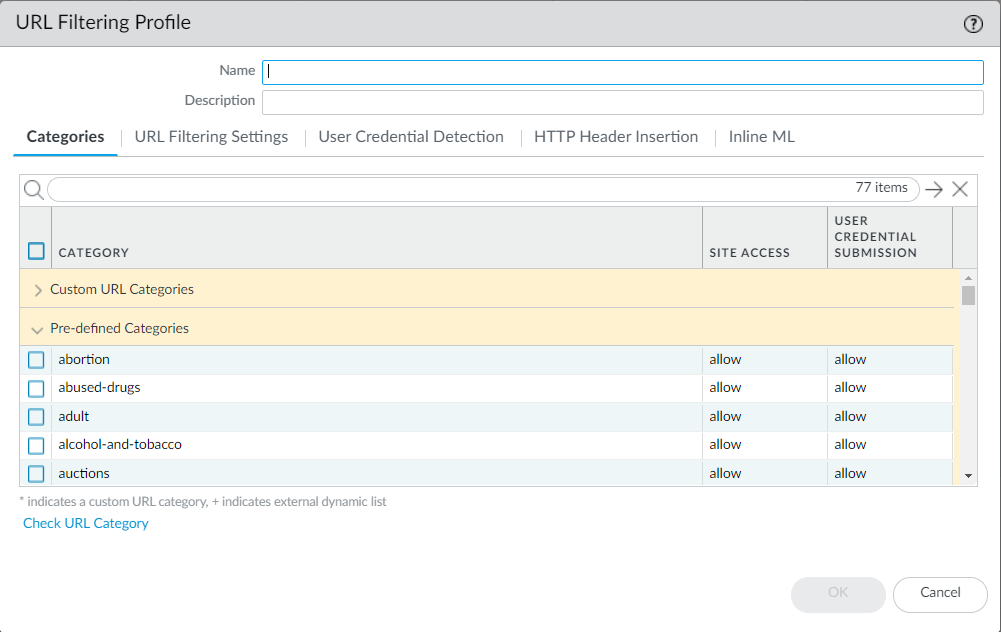
- Decide how you want to enforce Site Access and User Credential Submissions for the custom URL category. (To control the sites to which users can submit their corporate credentials, see Prevent Credential Phishing .)
- Attach the URL Filtering profile to a Security policy rule to enforce traffic that matches that rule.
Select PoliciesSecurityActions and specify the Security policy rule to enforce traffic based on the URL Filtering profile you just updated. Make sure to Commit your changes.
You can also use custom URL categories as Security policy rule match criteria. In this case, you do not define site access for the URL category in a URL Filtering profile. After creating a custom category, go to the Security policy rule to which you want to add the custom URL category ( PoliciesSecurity ). Then, select Service/URL Category to use the custom URL category as match criteria for the rule.
Use an External Dynamic List in a URL Filtering Profile
|
Where can I use this? |
What do I need? |
|
This feature has no prerequisites. |
An external dynamic list is a text file that is hosted on an external web server. You can use this list to import URLs and enforce policy on these URLs. The firewall dynamically imports the list at the configured interval and enforces policy for the URLs (IP addresses or domains are ignored) in the list. When the list is updated on the web server, the firewall retrieves the changes and applies policy to the modified list without requiring a commit on the firewall.
To protect your network from newly-discovered threats and malware, you can use external dynamic lists in URL Filtering profiles. For URL formatting guidelines, see Guidelines for URL Category Exceptions .
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Enable Prisma Access to reference an external dynamic list.
An external dynamic list allows you to define an imported list of IP addresses, URLs, or domain names that you can use in policy rules to block or allow traffic.
To set up an external dynamic list, go to ManageConfigurationObjectsExternal Dynamic Lists :
- Ensure that the list does not include IP addresses or domain names; the firewall skips non-URL entries.
- Use the custom URL list guidelines to verify the list’s formatting.
- Specify the List Type as URL List .
- Use the external dynamic list with URL Filtering.
Go to ManageConfigurationSecurity ServicesURL Access Management .
- Specify Site Access for the URLs in the external dynamic list.
- Exclude URLs in the external dynamic list from advanced inline categorization.
You can also use external dynamic lists to create custom URL categories (return to the URL Access Management dashboard to do this).
If a URL that is included in an external dynamic list is also included in a custom URL category , or block and allow list, the action specified in the custom category takes precedence over the external dynamic list.
- Test that the policy action is enforced.
1. View the external dynamic list entries ( ManageConfigurationObjectsExternal Dynamic Lists ) and try to access a URL from the list.
2. Verify that the action you defined is enforced in the browser.
- Configure the firewall to access an external dynamic list .
- Ensure that the list does not include IP addresses or domain names; the firewall skips non-URL entries.
- Use the custom URL list guidelines to verify the list’s formatting.
- Select URL List from the Type drop-down.
- Use the external dynamic list in a URL Filtering profile.
1. Select ObjectsSecurity ProfilesURL Filtering .
2. Add or modify an existing URL Filtering profile.
3. Name the profile and, in the Categories tab, select the external dynamic list from the Category list.
4. Click Action to select a more granular action for the URLs in the external dynamic list.
If a URL that is included in an external dynamic list is also included in a custom URL category , or block and allow list, the action specified in the custom category takes precedence over the external dynamic list.
5. Click OK .
6. Attach the URL Filtering profile to a Security policy rule.
- Select PoliciesSecurity .
- Select the Actions tab and, in the Profile Setting section, select the new profile in the URL Filtering drop-down.
- Click OK and Commit your changes.
- Test that the policy action is enforced.
1. View the external dynamic list entries and try to access a URL from the list.
2. Verify that the action you defined is enforced in the browser.
3. To monitor the activity on the firewall:
- Select ACC and add a URL Domain as a global filter to view the Network Activity and Blocked Activity for the URL you accessed.
- Select MonitorLogsURL Filtering to access the detailed log view.
- Verify whether entries in the external dynamic list were ignored or skipped.
In a list of type URL, the firewall skips non-URL entries as invalid and ignores entries that exceed the maximum limit for the firewall model.
To check whether you have reached the limit for an external dynamic list type, select ObjectsExternal Dynamic Lists and click List Capacities .
Use the following CLI command on a firewall to review the details for a list.
request system external-list show type url name <list_name>
For example:
request system external-list show type url name My_URL_List
vsys5/My_URL_List:
Next update at: Tue Jan 3 14:00:00 2017
Source: http://example.com/My_URL_List.txt
Referenced: Yes
Valid: Yes
Auth-Valid: Yes
Total valid entries: 3
Total invalid entries: 0
Valid urls:
www.URL1.com
www.URL2.com
www.URL3.com
URL Filtering Best Practices
Use an External Dynamic List in a URL Filtering Profile
Test URL Filtering Configuration
|
Where can I use this? |
What do I need? |
|
Notes:
|
Palo Alto Networks URL filtering solution protects you from web-based threats, and gives you a simple way to monitor and control web activity. To get the most out of your URL filtering deployment, you should start by creating allow rules for the applications you rely on to do business. Then, review the URL categories that classify malicious and exploitive content—we recommend that you block these outright. Then, for everything else, these best practices can guide you how to reduce your exposure to web-based threats, without limiting your users’ access to web content that they need.
- Before you get started, identify the applications you want to allow and create application allow rules as part of building a best practice internet gateway security policy.
Allowed applications include not only the applications you provision and administer for business and infrastructure purposes, but also the applications that your users need to get their jobs done and applications you might want to allow for personal use.
After you’ve identified these sanctioned applications, you can use URL filtering to control and secure all the web activity that is not on the allow list.
- Get visibility in to your users web activity so you can plan the most effective URL filtering policy for your organization. This includes:
- Using Test A Site to see how PAN-DB—the Palo Alto Networks URL filtering cloud database—categorizes a specific URL, and to learn about all possible URL categories.
- Starting with a (mostly) passive URL Filtering profile that alerts on URL categories. This gives you visibility into the sites your users are accessing, so you can decide what you want to allow, limit, and block.
- Monitoring web activity to assess the sites your users are accessing and see how they align with your business needs.
- Block URL categories that classify malicious and exploitive web content . While we know that these categories are dangerous, always keep in mind that the URL categories that you decide to block might depend on your business needs.
- Use URL categories to phase-in decryption, and to exclude sensitive or personal information (like financial-services and health-and-medicine) from decryption.
Plan to decrypt the riskiest traffic first (URL categories most likely to harbor malicious traffic, such as gaming or high-risk) and then decrypt more as you gain experience. Alternatively, decrypt the URL categories that don’t affect your business first (if something goes wrong, it won’t affect business), for example, news feeds. In both cases, decrypt a few URL categories, listen to user feedback, run reports to ensure that decryption is working as expected, and then gradually decrypt a few more URL categories, and so on. Plan to make to exclude sites from decryption if you can’t decrypt them for technical reasons or because you choose not to decrypt them.
Targeting decryption based on URL categories is also a decryption best practice .
- Prevent credential theft by enabling the firewall to detect corporate credential submissions to sites, and then control those submissions based on URL category. Block users from submitting credentials to malicious and untrusted sites, warn users against entering corporate credentials on unknown sites or reusing corporate credentials on non-corporate sites, and explicitly allow users to submit credentials to corporate and sanctioned sites.
- Block malicious variants of JavaScript exploits and phishing attacks in real-time . Enabling local inline categorization allows you to dynamically analyze web pages using machine learning on the firewall.
- Configure inline categorization to enable inline deep learning, ML-based detection engines to analyze suspicious web page content and protect users against zero-day web attacks. Cloud inline categorization is capable of detecting and preventing advanced and targeted phishing attacks, and other web-based attacks that use advanced evasion techniques such as cloaking, multi-step attacks, CAPTCHA challenges, and previously unseen one-time-use URLs.
- Decrypt, inspect, and strictly limit how users interact with high-risk and medium-risk content . If you decide not to block any of the malicious URL categories for business reasons, you should strictly limit how users interact with those categories.
The web content that you sanction and the malicious URL categories that you block outright are just one portion of your overall web traffic. The rest of the content your users are accessing is a combination of benign (low-risk) and risky content (high-risk and medium-risk). High-risk and medium-risk content is not confirmed malicious but is closely associated with malicious sites. For example, a high-risk URL might be on the same domain as a malicious site or may have hosted malicious content in the past.
However, many sites that pose a risk to your organization also provide valuable resources and services to your users (cloud storage services are a good example). While these resources and services are necessary for business, they are also more likely to be used as part of a cyberattack. Here’s how to control how users interact with this potentially-dangerous content, while still providing them a good user experience:
- In a URL Filtering profile, set the high-risk and medium-risk categories to continue to display a response page that warns users they’re visiting a potentially-dangerous site. Advise them how to take precautions if they decide to continue to the site. If you don’t want to prompt users with a response page, alert on the high-risk and medium-risk categories instead.
- Decrypt high-risk and medium-risk sites.
- Follow the Anti-Spyware, Vulnerability Protection, and File Blocking best practices for high-risk and medium-risk sites. A protective measure would be to block downloads of dangerous file types and blocking obfuscated JavaScript.
- Stop credential theft by blocking users from submitting their corporate credentials to high-risk and medium-risk sites.
- Schools or educational institutions should use safe search enforcement to make sure that search engines filter out adult images and videos from search results.
- Hold initial web requests during URL category lookup.
When a user visits a website, Advanced URL Filtering checks cached URL categories to categorize the site. If it doesn’t find the URL’s category in the cache, it performs a lookup in PAN-DB, the Palo Alto Networks URL database. By default, the user’s web request is allowed during this cloud lookup.
But when you choose to hold web requests, you can instead block the request until Advanced URL Filtering either finds the URL category or times out. If the lookup times out, the firewall considers the URL category not-resolved. Find this feature in your URL Filtering settings, Hold client request for category lookup .
Test URL Filtering Configuration
|
Where can I use this? |
What do I need? |
|
Notes:
|
To test your URL filtering policy configurations, use Palo Alto Networks URL filtering test pages . These pages have been created for the safe testing of all predefined URL categories and Advanced URL Filtering real-time-detection categories.
Test pages are accessible through HTTP and HTTPS connections. However, you must enable SSL decryption to view test pages over HTTPS.
You can check the classification of a specific website using Palo Alto Networks URL category lookup tool, Test A Site .
Follow the procedure corresponding to your URL Filtering subscription.
Verify URL Filtering
If you have the legacy URL Filtering subscription, test and verify that the firewall correctly categorizes, enforces, and logs URLs in the categories that end users access.
- Access a website in a URL category of interest.
Consider testing sites in blocked URL categories. You can use a test page (urlfiltering.paloaltonetworks.com/test-<url-category>) to avoid directly accessing a site. For example, to test your block policy for malware, visit https://urlfiltering.paloaltonetworks.com/test-malware.
- Review the Traffic and URL Filtering logs to verify that your firewall processes the site correctly.
For example, if you configured a block page to display when someone accesses a site that violates your organization’s policy, check that one appears when you visit the test site.
Verify Advanced URL Filtering
If you have an Advanced URL Filtering subscription, test and verify that URLs submitted to the Advanced URL Filtering are properly analyzed.
Palo Alto Networks recommends setting the real-time-detection (cloud inline categorization) action setting to alert for active URL Filtering profiles. This provides visibility into URLs analyzed in real-time and will block (or allow, depending on your policy settings) based on the category settings configured for specific web threats.
The firewall enforces the most severe action of the actions configured for detected URL categories of a given URL. For example, suppose example.com is categorized as real-time-detection, command-and-control, and shopping—categories with an alert, block, and allow action configured, respectively. The firewall blocks the URL because block is the most severe action of the detected categories.
- Visit each of the following test URLs to verify that the Advanced URL Filtering service is properly categorizing URLs:
- Malware — http://urlfiltering.paloaltonetworks.com/test-inline-url-analysis-malware
- Phishing — http://urlfiltering.paloaltonetworks.com/test-inline-url-analysis-phishing
- C2 — http://urlfiltering.paloaltonetworks.com/test-inline-url-analysis-command-and-control
- Grayware — http://urlfiltering.paloaltonetworks.com/test-inline-url-analysis-grayware
If Cloud Inline Categorization is enabled, use the following URLs to test the operation of the feature:
- Malware — http://urlfiltering.paloaltonetworks.com/test-inline-content-analysis-malware
- Phishing — http://urlfiltering.paloaltonetworks.com/test-inline-content-analysis-phishing
- Grayware — http://urlfiltering.paloaltonetworks.com/test-inline-content-analysis-grayware
- Parked — http://urlfiltering.paloaltonetworks.com/test-inline-content-analysis-parked
- Adult — http://urlfiltering.paloaltonetworks.com/test-inline-content-analysis-adult
- Monitor web activity to verify that the test URLs have been properly categorized by Advanced URL Filtering:
1. Filter your URL Filtering logs using the following: (url_category_list contains real-time-detection).
Additional web page category matches are also displayed and correspond to the categories as defined by PAN-DB.
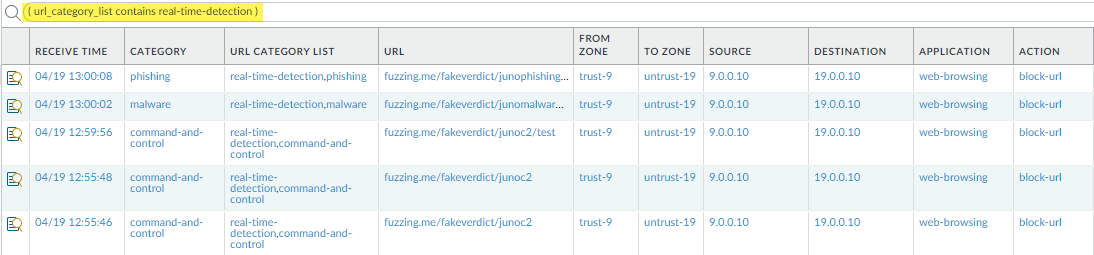
2. Take a detailed look at the logs to verify that each type of web threat is correctly analyzed and categorized.
In the next example, the URL is categorized as having been analyzed in real-time and possessing qualities that define it as command-and-control (C2). Because the C2 category has a more severe action associated with it than real-time-detection (block as opposed to alert), the URL is categorized as command-and-control and blocked.
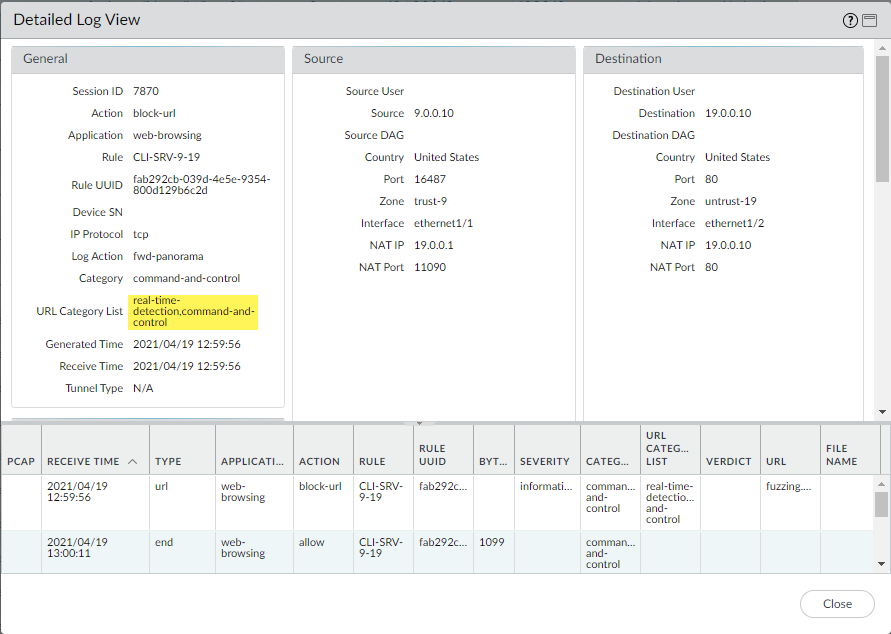
URL Filtering Features
Test URL Filtering Configuration
|
Where can I use this? |
What do I need? |
|
Notes:
|
After you configure the basic components of your URL filtering deployment, consider configuring the following features:
- Inline Categorization
- SSL/TLS Handshake Inspection
- URL Admin Override
- Credential Phishing Prevention
- URL Filtering Response Pages
- Safe Search Enforcement
- ( Prisma Access only ) Remote Browser Isolation (RBI) Integration
Inspect SSL/TLS Handshakes
Allow Password Access to Certain Sites
|
Where can I use this? |
What do I need? |
|
Notes:
|
Examining SSL/TLS handshakes improves network security and optimizes legacy and Advanced URL Filtering subscriptions. When you enable SSL/TLS handshake inspection, Advanced URL Filtering uses data in the handshake to identify the traffic and enforce applicable Security policy rules as early as possible.
Here’s how it works
First, the Client Hello message is scanned for the Server Name Indication (SNI) field, a TLS protocol extension that contains the hostname of a requested website. Then, the URL category and server destination of the traffic is determined from the hostname. Next, traffic is enforced based on its URL category. If a threat is detected, such as a malicious web server in the SNI field, or if a Security policy rule blocks the website, the handshake terminates and the web session ends immediately. If no threat is detected and the traffic is allowed per policy, the SSL/TLS handshake is completed and application data is exchanged through the secure connection.
URL filtering response pages do not display for sites blocked during SSL/TLS handshake inspections because the firewall resets the HTTPS connection. The connection reset ends SSL/TLS handshakes and prevents user notification by response page. The browser displays a standard connection error message instead.
You can find details of successful SSL/TLS handshakes and sessions in the Traffic and Decryption logs. Details of failed sessions can be found in URL filtering logs; Decryption logs aren’t generated for web sessions blocked during SSL/TLS handshakes.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
A requirement of inspecting SSL handshakes is that you decrypt SSL/TLS traffic through either SSL Forward Proxy or SSL Inbound Inspection.
- Confirm that your Prisma Access license includes an Advanced URL Filtering subscription.
- Select ManageService SetupOverview and click on the hyperlinked Quantity value. Information including Security Services appears.
- Under Security Services, confirm that a checkmark is next to URL Filtering.
- Verify that you decrypt SSL/TLS traffic through either SSL Forward Proxy or SSL Inbound Inspection .
- Enable inspection of SSL/TLS handshakes by CTD. By default, this option is disabled.
- Select Manage ConfigurationSecurity ServicesDecryption .
- By Decryption Settings, select the settings icon. Then, select Inspect TLS Handshake Messages .
Alternatively, you can use the set deviceconfig setting ssl-decrypt scan-handshake <yes|no> CLI command.
- Save your changes. Under Decryption Settings, the Inspect TLS handshake message setting should say Enabled.
- Push Config to save and commit your changes.
- Select Device > Licenses to confirm that you have an active Advanced URL Filtering or legacy URL Filtering license.
- Verify that you decrypt SSL/TLS traffic through either SSL Forward Proxy or SSL Inbound Inspection .
- Enable inspection of SSL/TLS handshakes by CTD. By default, the option is disabled.
- Select Device SetupSessionDecryption Settings SSL Decryption Settings .
- Select Send handshake messages to CTD for inspection .
Alternatively, you can use the set deviceconfig setting ssl-decrypt scan-handshake <yes|no> CLI command.
- Click OK .
- Commit your configuration changes.
Allow Password Access to Certain Sites
Credential Phishing Prevention
|
Where can I use this? |
What do I need? |
|
Notes:
|
In some cases, it may be necessary to require password access to websites in certain categories. For example, your company may block URL categories that threaten the safety and wellbeing of employees. However, certain employees may need access to these categories for research or other legitimate purposes. To balance safety and business needs, implementing URL admin overrides can be an effective solution.
To create a URL admin override, set the action for a category to override . Then, create a password that users must enter to access sites in this category. When users attempt to access a website in a category that you have overridden, a Continue and Override response page appears. This page notifies users that a website is blocked and prompts them to enter a password to continue to the site.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Go to the URL Access Management dashboard.
Select ManageConfigurationSecurity ServicesURL Access Management .
- Select Settings .
- Create a URL admin override password.
- Go to URL Admin Overrides, and Add URL Admin Overrides .
- ( Optional ) Select a Mode for prompting users for the password:
- Transparent —The password prompt appears to originate from the original destination URL. The firewall intercepts the browser traffic destined for sites in a URL category set to override and issues an HTTP 302 to prompt for the password, which applies on a per-vsys level.
- Redirect —The password prompt appears from an Address (IP address or DNS hostname) that you specify. The firewall intercepts HTTP or HTTPS traffic to a URL category set to override and uses an HTTP 302 redirect to send the request to a Layer 3 interface on the firewall.
- Enter a Password , then enter it again to Confirm Password .
- ( Optional ) Select an SSL/TLS Service Profile .
You can create and manage SSL/TLS service profiles by clicking Create New and Manage , respectively.
- Save your changes.
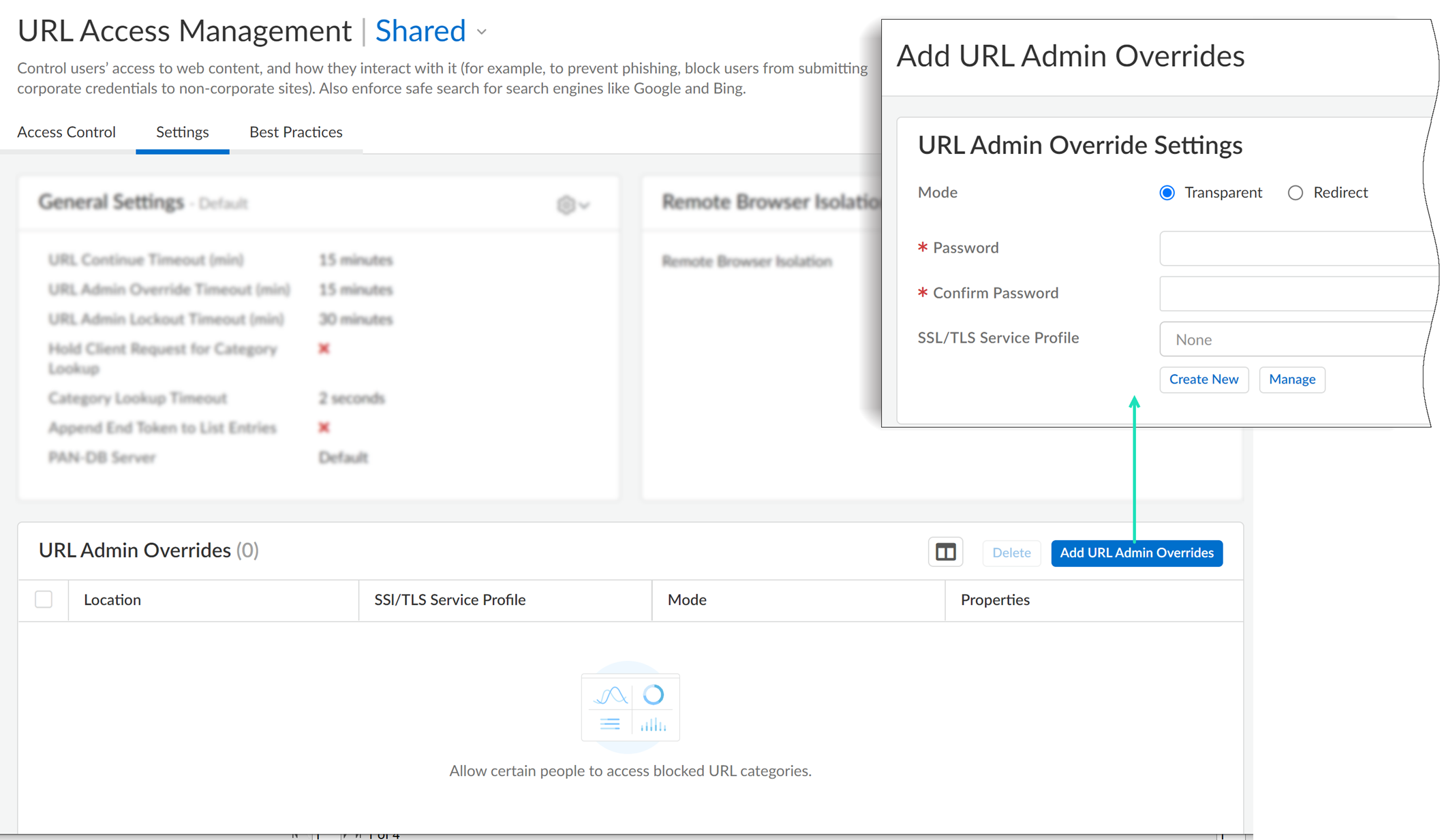
- ( Optional ) Set the duration of override access and password lockouts.
By default, users can access websites in categories for which they have successfully entered an override password for 15 minutes. After the default or custom interval passes, users must re-enter the password.
By default, users are blocked for 30 minutes after three failed password attempts. After the user is locked out for the default or custom duration, they can try to access the websites again.
- Customize the General Settings.
- For URL Admin Override Timeout , enter a value (in minutes) from 1 to 86,400.
- For URL Admin Lockout Timeout , enter a value (in minutes) from 1 to 86,400.
- Save your changes.
- Specify the URL categories that require password access.
- On the URL Access Management dashboard, under the Access Control tab, go to URL Access Management Profiles and modify or Add Profile .
- Under Access Control, select the categories that require password access.
- With all the categories selected, click Set Access and then select Override .
You should see that Site Access for the highlighted categories now say override .
- Save your changes.
- Apply the URL Access Management profile to a Security policy rule.
A URL Access Management profile is only active when it’s included in a profile group that a Security policy rule references.
Follow the steps to activate a URL Access Management profile (and any Security profile). Be sure to Push Config when you are done.
- Set a URL admin override password.
- Select DeviceSetupContent ID .
- In the URL Admin Override section, click Add .
- In the Location field, select the virtual system to which this password applies.
- Enter a Password , then enter it again to Confirm Password .
- Select an SSL/TLS Service Profile .
SSL/TLS service profiles specify the certificate that the firewall presents to the user if the site with the override is an HTTPS site.
- Select a Mode for prompting user for the password:
- Transparent —The password prompt appears to originate from the original destination URL. The firewall intercepts the browser traffic destined for sites in a URL category set to override and issues an HTTP 302 to prompt for the password, which applies on a per-vsys level.
The client browser will display certificate errors if it does not trust the certificate.
- Redirect —The password prompt appears from an Address (IP address or DNS hostname) that you specify. The firewall intercepts HTTP or HTTPS traffic to a URL category set to override and uses an HTTP 302 redirect to send the request to a Layer 3 interface on the firewall.
- Click OK .
- ( Optional ) Set the duration of override access and password lockouts.
By default, users can access websites in categories for which they have successfully entered an override password for 15 minutes. After the default or custom interval passes, users must re-enter the password.
By default, users are blocked for 30 minutes after three failed password attempts. After the user is locked out for the default or custom duration, they can try to access the websites again.
- Edit the URL Filtering section.
- For URL Admin Override Timeout , enter a value (in minutes) from 1 to 86,400. ---By default, users can access sites within the category for 15 minutes without re-entering the password.
- For URL Admin Lockout Timeout , enter a value (in minutes) from 1 to 86,400.
- Click OK .
- ( Redirect mode only ) Create a Layer 3 interface to which to redirect web requests to sites in a category configured for override.
- Create a management profile to enable the interface to display the URL Filtering Continue and Override Page response page:
1. Select NetworkInterface Mgmt and click Add .
2. Enter a Name for the profile, select Response Pages , and then click OK .
- Create the Layer 3 interface. Be sure to attach the management profile you just created (on the AdvancedOther Info tab of the Ethernet Interface dialog).
- ( Redirect mode only ) To transparently redirect users without displaying certificate errors, install a certificate that matches the IP address of the interface to which you are redirecting web requests to a site in a URL category configured for override.You can either generate a self-signed certificate or import a certificate that is signed by an external CA.
To use a self-signed certificate, you must first create a root CA certificate and then use that CA to sign the certificate you will use for URL admin override as follows:
- To create a root CA certificate, select DeviceCertificate ManagementCertificatesDevice Certificates and then click Generate . Enter a Certificate Name , such as RootCA. Do not select a value in the Signed By field (this is what indicates that it is self-signed). Make sure you select the Certificate Authority check box and then click Generate the certificate.
- To create the certificate to use for URL admin override, click Generate . Enter a Certificate Name and enter the DNS hostname or IP address of the interface as the Common Name . In the Signed By field, select the CA you created in the previous step. Add an IP address attribute and specify the IP address of the Layer 3 interface to which you will be redirecting web requests to URL categories that have the override action.
- Generate the certificate.
- To configure clients to trust the certificate, select the CA certificate on the Device Certificates tab and click Export . You must then import the certificate as a trusted root CA into all client browsers, either by manually configuring the browser or by adding the certificate to the trusted roots in an Active Directory Group Policy Object (GPO).
- Specify which URL categories require an override password to enable access.
- Select ObjectsURL Filtering and either select an existing URL Filtering profile or Add a new one.
- On the Categories tab, set the Action to override for each category that requires a password.
- Complete any remaining sections on the URL Filtering profile and then click OK to save the profile.
- Apply the URL Filtering profile to the Security policy rule(s) that allows access to the sites requiring password override for access.
- Select PoliciesSecurity and select the appropriate Security policy to modify it.
- Select the Actions tab and in the Profile Setting section, click the drop-down for URL Filtering and select the profile.
- Click OK to save.
- Commit the configuration.
Credential Phishing Prevention
Allow Password Access to Certain Sites
Methods to Check for Corporate Credential Submissions
|
Where Can I Use This? |
What Do I Need? |
|
Notes:
|
Phishing sites are sites that attackers disguise as legitimate websites with the intent to steal user information, especially the credentials that provide access to your network. When a phishing email enters a network, it takes just a single user to click a link and enter credentials to set a breach into motion. You can detect and prevent in-progress phishing attacks, thereby preventing credential theft, by controlling sites to which users can submit corporate credentials based on the site’s URL category. This allows you to block users from submitting credentials to untrusted sites while allowing credential submissions to corporate and sanctioned sites.
Credential phishing prevention works by scanning username and password submissions to websites and comparing those submissions against valid corporate credentials. You can choose what websites you want to either allow or block corporate credential submissions to based on the URL category of the website. When a user attempts to submit credentials to a site in a category you have restricted, either a block response page prevents the user from submitting credentials or a continue page warns users against submitting credentials to sites in certain URL categories, but still allows them to continue with the submission. You can customize response pages to educate users against reusing corporate credentials, even on legitimate, non-phishing sites.
The following topics describe different credential detection methods you can choose and provide instructions for configuring credential phishing protection.
Methods to Check for Corporate Credential Submissions
Credential Phishing Prevention
Configure Credential Detection with the Windows User-ID Agent
|
Where can I use this? |
What do I need? |
|
Notes:
|
Before you enable credential phishing prevention , decide which method you want to use to check if valid corporate credentials have been submitted to a web page.
|
Method to Check Submitted Credentials |
User-ID Configuration Requirements |
How does this method detect corporate usernames and/or passwords that users submit to websites? |
|
Group Mapping |
Group Mapping configuration on the firewall |
The firewall checks to determine if the username a user submits to a restricted site matches any valid corporate username. To do this, the firewall matches the submitted username to the list of usernames in its user-to-group mapping table to detect when users submit corporate usernames to sites in a restricted category. This method only checks for corporate username submissions based on LDAP group membership, which makes it simple to configure, but more prone to false positives. |
|
IP-User Mapping |
IP address-to- username mappings identified through user mapping , GlobalProtect , or Authentication Policy and Authentication Portal |
The firewall checks to determine if the username a user submits to a restricted site maps to the IP address of the login username. To do this, the firewall matches the IP address of the login username and the username submitted to a web site to its IP address-to-user mapping table to detect when users submit their corporate usernames to sites in a restricted category. Because this method matches the IP address of the login username associated with the session against the IP address-to-username mapping table, it is an effective method for detecting corporate username submissions, but it does not detect corporate password submission. If you want to detect corporate username and password submission, you must use the Domain Credential Filter method. |
|
Domain Credential Filter Prisma Access doesn't support this method. |
Windows User-ID agent configured with the User-ID credential service add-on - AND - IP address-to- username mappings identified through user mapping , GlobalProtect , or Authentication Policy and Authentication Portal |
The firewall checks to determine if the username and password a user submits match the same user’s corporate username and password. To do this, the firewall must be able to match credential submissions to valid corporate usernames and passwords and verify that the username submitted maps to the IP address of the login username as follows:
To learn more about the domain credential method, see Configure Credential Detection with the Windows-based User-ID Agent . |
Configure Credential Detection with the Windows User-ID Agent
Methods to Check for Corporate Credential Submissions
Set Up Credential Phishing Prevention
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
Domain Credential Filter detection enables the firewall to detect passwords submitted to web pages. This credential detection method requires the Windows User-ID agent and the User-ID credential service, an add-on to the User-ID agent, to be installed on a read-only domain controller (RODC) .
The Domain Credential Filter detection method is supported with the Windows User-ID agent only. You cannot use the PAN-OS integrated User-ID agent to configure this method of credential detection.
An RODC is a Microsoft Windows server that maintains a read-only copy of an Active Directory database that a domain controller hosts. When the domain controller is located at a corporate headquarters, for example, RODCs can be deployed in remote network locations to provide local authentication services. Installing the User-ID agent on an RODC can be useful for a few reasons: access to the domain controller directory is not required to enable credential detection and you can support credential detection for a limited or targeted set of users. Because the directory the RODC hosts is read-only, the directory contents remain secure on the domain controller.
Because you must install the Windows User-ID agent on the RODC for credential detection, as a best practice deploy a separate agent for this purpose. Do not use the User-ID agent installed on the RODC to map IP addresses to users.
After you install the User-ID agent on an RODC, the User-ID credential service runs in the background and scans the directory for the usernames and password hashes of group members that are listed in the RODC password replication policy (PRP)—you can define who you want to be on this list. The User-ID credential service then takes the collected usernames and password hashes and deconstructs the data into a type of bit mask called a bloom filter . Bloom filters are compact data structures that provide a secure method to check if an element (a username or a password hash) is a member of a set of elements (the sets of credentials you have approved for replication to the RODC). The User-ID credential service forwards the bloom filter to the Windows User-ID agent; the firewall retrieves the latest bloom filter from the User-ID agent at regular intervals and uses it to detect usernames and password hash submissions. Depending on your settings, the firewall then blocks, alerts, or allows on valid password submissions to web pages, or displays a response page to users warning them of the dangers of phishing, but allowing them to continue with the submission.
Throughout this process, the User-ID agent does not store or expose any password hashes, nor does it forward password hashes to the firewall. Once the password hashes are deconstructed into a bloom filter, there is no way to recover them.
To enable credential detection, you must install the Windows User-ID agent on an RODC. Refer to the Compatibility Matrix for a list of supported servers. Install a separate User-ID agent for this purpose.
Important items to remember when setting up User-ID to enable Domain Credential Filter detection:
- The effectiveness of credential phishing detection is dependent on your RODC setup. Make sure to review best practices and recommendations for RODC Administration .
- Download User-ID software updates :
- User-ID Agent Windows installer—UaInstall-x.x.x-x.msi.
- User-ID Agent Credential Service Windows installer—UaCredInstall64-x.x.x-x.msi.
- Install the User-ID agent and the User Agent Credential service on an RODC using an account that has privileges to read Active Directory via LDAP (the User-ID agent also requires this privilege).
- The User-ID Agent Credential Service requires permission to log on with the local system account. For more information, refer to Create a Dedicated Service Account for the User-ID Agent .
- The service account must be a member of the local administrator group on the RODC.
- Enable the User-ID agent and the User Agent Credential service (which runs in the background to scan permitted credentials) to share information.
1. On the RODC server, launch the User-ID Agent.
2. Select Setup and edit the Setup section.
3. Select the Credentials tab. This tab only displays if you have already installed the User-ID Agent Credential Service.
4. Select Import from User-ID Credential Agent . This enables the User-ID agent to import the bloom filter that the User-ID credential agent creates to represent users and the corresponding password hashes.
5. Click OK , Save your settings, and Commit .
- In the RODC directory, define the group of users for which you want to support credential submission detection.
- Confirm that the groups that should receive credential submission enforcement are added to the Allowed RODC Password Replication Group.
- Check that none of the groups in the Allowed RODC Password Replication Group are also in the Denied RODC Password Replication Group by default. Groups listed in both will not be subject to credential phishing enforcement.
- Continue to the next task.
Set up credential phishing prevention on the firewall.
Set Up Credential Phishing Prevention
Configure Credential Detection with the Windows User-ID Agent
|
Where can I use this? |
What do I need? |
|
Notes:
|
After you decide which user credential detection method to configure, follow these steps to prevent successful credential phishing attacks.
Before enabling credential phishing prevention, verify that the Primary Username that you configure on the firewall uses the sAMAccountName attribute. Credential phishing prevention does not support alternate attributes.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Configure the user credential detection method you want to use.
Review Methods to Check for Corporate Credential Submissions for details about each method.
- For IP User Mapping, set up local users and groups , Identity Redistribution , or Authentication with Prisma Access .
- To use Domain Credential Filter, set up Identity Redistribution and local users and groups or Authentication .
- To use Group Mapping, set up local users and groups or Authentication .
- Create a Decryption policy rule that decrypts the traffic you want to monitor for user credential submissions.
- Create or modify a URL Access Management Profile.
1. Select ManageConfigurationNGFW and Prisma AccessSecurity ServicesURL Access Management .
2. Under URL Access Management Profiles, click Add Profile or select an existing profile.
- Configure the User Credential Detection settings.
1. Under User Credential Detection, select a User Credential Detection method.
- Use IP User Mapping —Checks for valid corporate username submissions and verifies that the login username maps to the source IP address of the session. To do this, Prisma Access matches the submitted username and source IP address of the session against its IP-address-to-username mapping table.
- Use Domain Credential Filter —Checks for valid corporate username and password submissions and verifies that the username maps to the IP address of the logged-in user.
- Use Group Mapping —Checks for valid username submissions based on the user-to-group mapping table populated when you map users to groups. You can apply credential detection to any part of the directory or for specific groups that have access to your most sensitive applications, such as IT.
This method is prone to false positives in environments that do not have uniquely structured usernames. Because of this, you should only use this method to protect your high-value user accounts.
2.
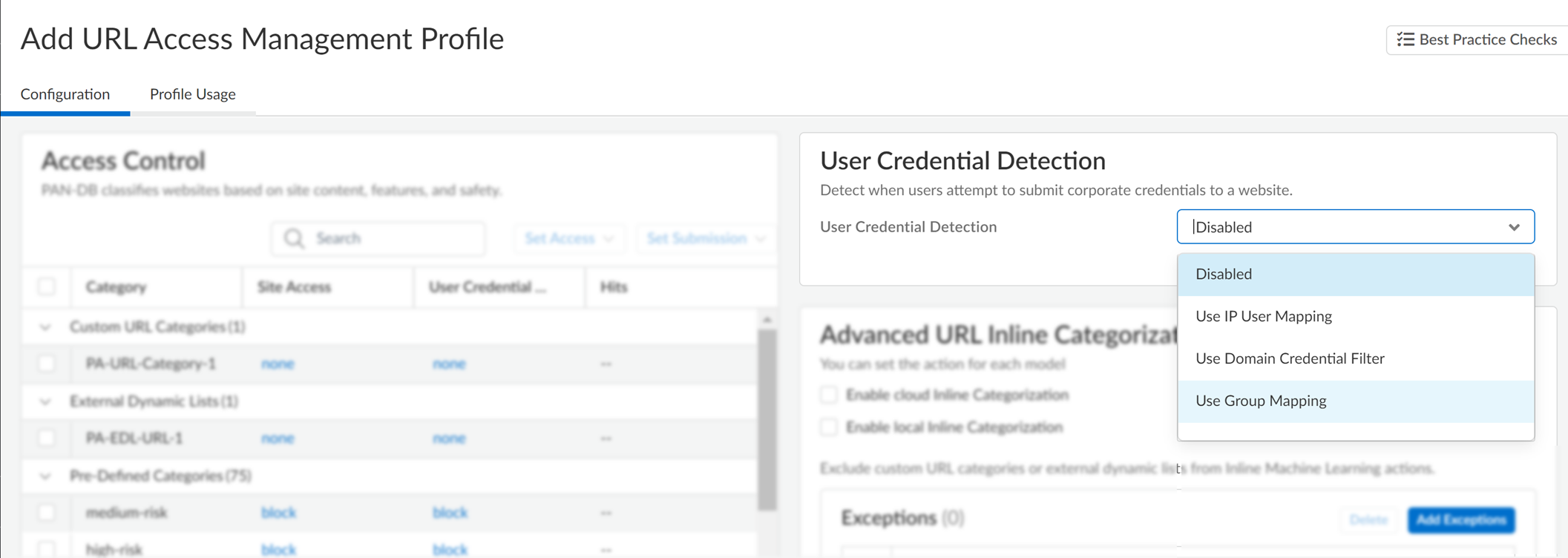
3. For Valid Username Detected Log Severity , select the severity level that the firewall records in log when it detects corporate credential submissions:
- high
- ( default ) medium
- low
- Configure the action taken when the firewall detects corporate credential submissions.
1. Under Access Control, select an action for User Credential Submission for each URL category with its Site Access set to allow or alert.
You can select from the following actions:
- ( Recommended ) alert —Lets users submit credentials to websites in the given URL category but generates a URL Filtering log each time this happens.
- ( Default ) allow –Lets users submit credentials to the website.
- ( Recommended ) block —Prevents users from submitting credentials to websites in the given URL category. When a user tries to submit credentials, the firewall displays the anti-phishing block page .
- continue —Presents the anti-phishing continue page to users when they attempt to submit credentials. Users must select Continue on the response page to proceed to the website.
2. Save the profile.
- Apply the URL Access Management profile to your Security policy rules.
1. Select ManageConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy .
2. Under Security Policy Rules, create or select a Security policy rule.
3. Select ActionsProfile Group , and then select a URL Access Management profile group.
4. Save the rule.
- Click Push Config .
Each of the methods to check for corporate credential submissions requires a different User-ID configuration:
- Group Mapping—detects whether a user is submitting a valid corporate username and requires you to map users to groups .
- IP User Mapping—detects whether a user is submitting a valid corporate username and that the username matches the login username—requires you to map IP addresses to users .
- Domain Credential Filter—detects whether a user is submitting a valid username and password and that those credentials belong to the logged-in user— requires you to configure credential detection with the Windows-based User-ID agent and map IP addresses to users .
- Configure a best practice URL Filtering profile to ensure protection against URLs that have been observed hosting malware or exploitive content.
1. Select ObjectsSecurity ProfilesURL Filtering and Add or modify a URL Filtering profile.
2. Block access to all known dangerous URL categories: malware, phishing, dynamic-dns, unknown, command-and-control, extremism, copyright-infringement, proxy-avoidance-and-anonymizers, newly-registered-domain, grayware, and parked.
- Create a Decryption policy rule that decrypts the traffic you want to monitor for user credential submissions.
- Detect corporate credential submissions to websites that are in allowed URL categories.
To provide the best performance, the firewall does not check credential submissions for trusted sites, even if you enable the checks for the URL categories for these sites. The trusted sites represent sites where Palo Alto Networks has not observed any malicious or phishing attacks. Updates for this trusted sites list are delivered through Application and Threat content updates.
1. Select a URL Filtering profile ( ObjectsSecurity ProfilesURL Filtering ) to modify.
2. Select User Credential Detection and choose one of the user credential detection methods .
Confirm that the format for the primary username is the same as the username format that the User-ID source provides.
- Use IP User Mapping— Checks for valid corporate username submissions and verifies that the login username maps to the source IP address of the session. To do this, the firewall matches the submitted username and source IP address of the session against its IP-address-to-username mapping table. To use this method, configure any of the user mapping methods listed in Map IP Addresses to Users .
- Use Domain Credential Filter —Checks for valid corporate usernames and password submissions and verifies that the username maps to the IP address of the logged-in user. For instructions on how to set up this method, see Configure Credential Detection with the Windows-based User-ID Agent .
- Use Group Mapping —Checks for valid username submissions based on the user-to-group mapping table populated when you configure the firewall to map users to groups .
With group mapping, you can apply credential detection to any part of the directory or for specific groups that have access to your most sensitive applications, such as IT.
This method is prone to false positives in environments that do not have uniquely structured usernames. Because of this, you should only use this method to protect your high-value user accounts.
3. Set the Valid Username Detected Log Severity the firewall uses to log detection of corporate credential submissions. By default, the firewall logs these events as medium severity.
- Block (or alert) on credential submissions to allowed sites.
1. Select Categories .
2. For each Category to which Site Access is allowed, select how you want to treat User Credential Submissions :
- alert —Allow users to submit credentials to the website, but generate a URL Filtering log each time a user submits credentials to sites in this URL category.
- allow —(default) Allow users to submit credentials to the website.
- block —Block users from submitting credentials to the website. When a user tries to submit credentials, the firewall displays the anti-phishing block page , preventing the submission.
- continue —Present the anti-phishing continue page to users when they attempt to submit credentials. Users must select Continue on the response page to continue with the submission.
3. Select OK to save the URL Filtering profile.
- Apply the URL Filtering profile with the credential detection settings to your Security policy rules.
1. Select PoliciesSecurity and Add or modify a Security policy rule.
2. On the Actions tab, set the Profile Type to Profiles .
3. Select the new or updated URL Filtering profile to attach it to the Security policy rule.
4. Select OK to save the Security policy rule.
- Commit the configuration.
- Monitor credential submissions the firewall detects.
Select ACCHosts Visiting Malicious URLs to see the number of users who have visited malware and phishing sites.
Select MonitorLogsURL Filtering .
The new Credential Detected column indicates events where the firewall detected a HTTP post request that included a valid credential:
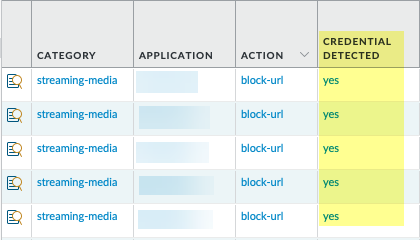
To display this column, hover over any column header and click the arrow to select the columns you’d like to display.
Log entry details also indicate credential submissions:
- Validate and troubleshoot credential submission detection.
- Use the following CLI command to view credential detection statistics:
> show user credential-filter statistics
The output for this command varies depending on the method configured for the firewall to detect credential submissions. For example, if the Domain Credential Filter method is configured in any URL Filtering profile, a list of User-ID agents that have forwarded a bloom filter to the firewall is displayed, along with the number of credentials contained in the bloom filter.
- ( Group Mapping method only ) Use the following CLI command to view group mapping information, including the number of URL Filtering profiles with Group Mapping credential detection enabled and the usernames of group members that have attempted to submit credentials to a restricted site.
> show user group-mapping statistics
- ( Domain Credential Filter method only ) Use the following CLI command to see all Windows-based User-ID agents that are sending mappings to the firewall:
> show user user-id-agent state all
The command output now displays bloom filter counts that include the number of bloom filter updates the firewall has received from each agent, if any bloom filter updates failed to process, and how many seconds have passed since the last bloom filter update.
- ( Domain Credential Filter method only ) The Windows-based User-ID agent displays log messages that reference BF (bloom filter) pushes to the firewall. In the User-ID agent interface, select MonitoringLogs .
URL Filtering Response Pages
Set Up Credential Phishing Prevention
Predefined URL Filtering Response Pages
|
Where Can I Use This? |
What Do I Need? |
|
Notes:
|
URL filtering response pages notify users when access to a requested URL has been restricted. Access may be restricted if a site belongs to a category that has been configured with a block, continue, or override action or credential submissions to the site or category has been blocked. If a user doesn't have the strictest safe search settings configured for a search engine and a Security policy rule enforces safe search, access is also restricted. Five predefined response pages exist to account for these reasons. Some response pages outright block access, while others allow conditional access. For example, if the URL Filtering Continue and Override Page or Anti Phishing Continue Page appears, users can click Continue to enter the site (unless URL Admin Override is enabled).
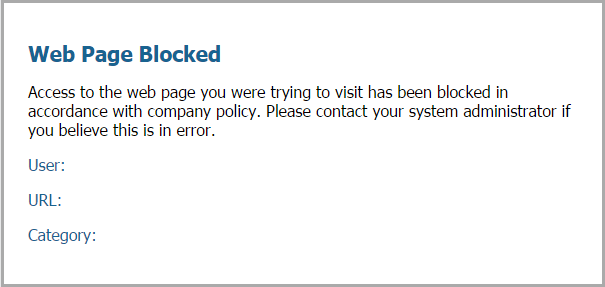
In general, the response pages state why the page cannot be accessed and list the user, URL, and URL category. However, you can customize the content and appearance of the response pages. For example, you can change the notification message, link to your acceptable use policy, or add corporate branding.
You may observe variations in the appearance of the response pages across different PAN-OS software releases. However, the functionality remains the same.
Remember that you can customize the response pages to meet your specific needs.
Browsers do not display response pages if SSL/TLS handshake inspections are enabled.
- Predefined URL Filtering Response Pages
- URL Filtering Response Page Objects
- Customize URL Filtering Response Pages
Predefined URL Filtering Response Pages
URL Filtering Response Page Objects
|
Where can I use this? |
What do I need? |
|
Notes:
|
URL filtering response pages display on web browsers when access to a requested URL has been restricted. Each response page explains why the page cannot be accessed, and most pages list information about the user, the requested URL, and the URL category that triggered the blocking action.
You may observe variations in the appearance of the response pages across different PAN-OS software releases. However, the functionality remains the same.
Remember that you can customize the response pages to meet your specific needs.
- URL Filtering and Category Match Block Page
Access blocked by a URL Filtering profile or because the URL category is blocked by a Security policy rule.

- URL Filtering Continue and Override Page
Page with initial block policy that allows users to bypass the block by clicking Continue . With URL Admin Override enabled ( Allow Password Access to Certain Sites ), after clicking Continue , the user must supply a password to override the policy that blocks the URL.
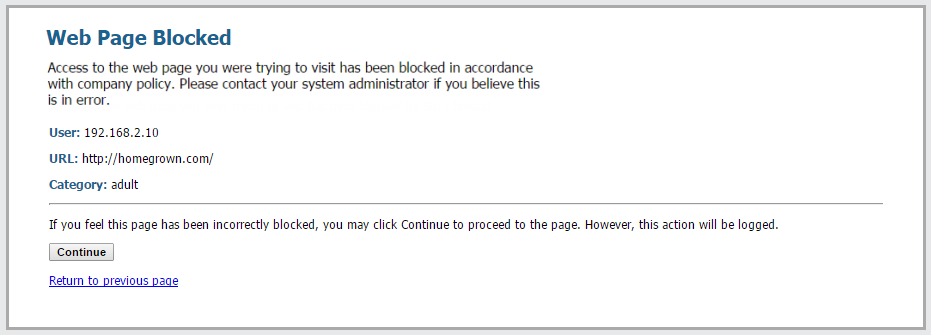
- URL Filtering Safe Search Block Page
Access blocked by a Security policy rule with a URL Filtering profile that has the Safe Search Enforcement option enabled (see Safe Search Enforcement ). The user will see this page if a search is performed using Google, Bing, Yahoo, or Yandex and their browser or search engine account setting for Safe Search is not set to strict.
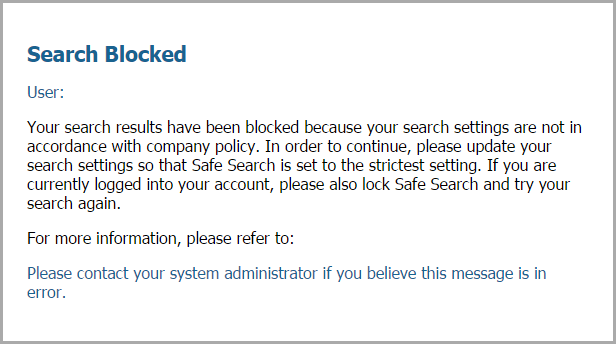
- Anti Phishing Block Page
This page displays to users when they attempt to enter corporate credentials (usernames or passwords) on a web page in a category for which credential submissions are blocked. The user can continue to access the site but remains unable to submit valid corporate credentials to any associated web forms. To control the sites to which users can submit corporate credentials, you must configure User-ID and enable credential phishing prevention based on URL category.
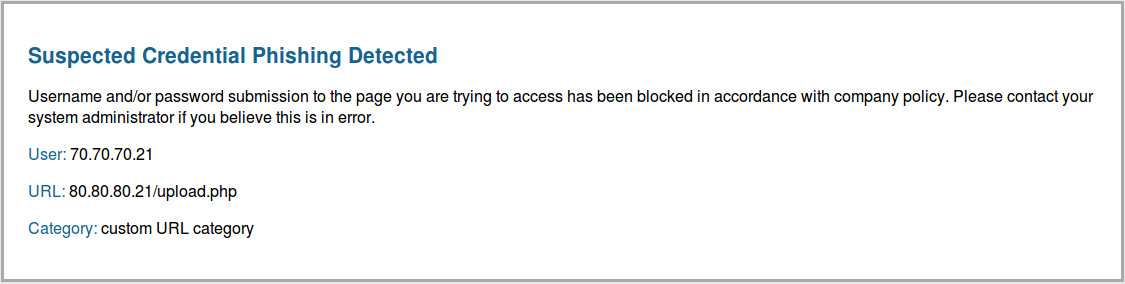
- Anti Phishing Continue Page
This page warns users against submitting credentials (usernames and passwords) to a web site. Warning users against submitting credentials can help to discourage them from reusing corporate credentials and to educate them about possible phishing attempts. They must select Continue to proceed to credentials on the site. To control the sites to which users can submit corporate credentials, you must configure User-ID and enable credential phishing prevention based on URL category.
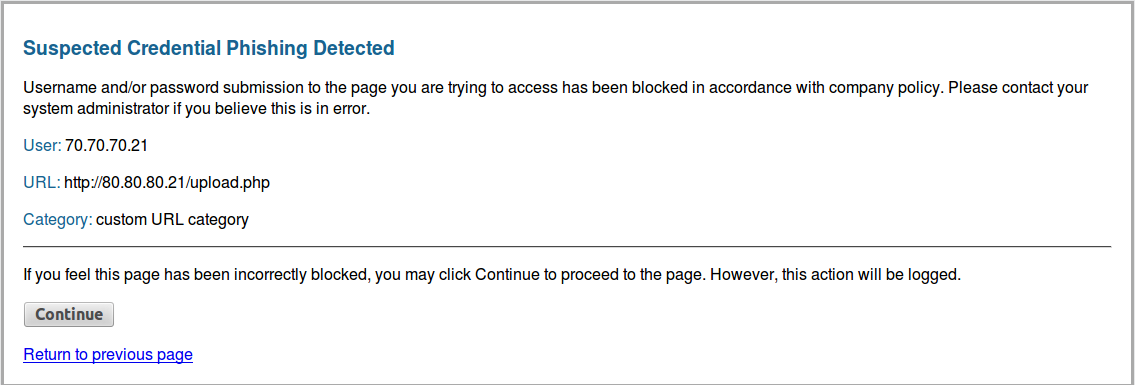
URL Filtering Response Page Objects
Predefined URL Filtering Response Pages
Customize URL Filtering Response Pages
|
Where can I use this? |
What do I need? |
|
Notes:
|
Use the variables and references described in the following sections to customize URL filtering response pages. The response page variables display different information about URL requests. For example, the firewall replaces the <category/> variable in the HTML code for the response pages with the URL categories of a requested URL. Response page references enable you to add external images, sounds, style sheets, and links.
Response Page Variables
The following table lists response page variables and the information or object that the system substitutes each variable with during a block event. Each URL filtering response page uses the following variables by default: user, url, and category. However, response pages are customizable. For example, you can modify the order of the variables or add different messages for specific URL categories.
|
Variable |
Usage |
|
<user/> |
The firewall replaces the variable with the username (if available via User-ID) or IP address of the user when displaying the response page. |
|
<url/> |
The firewall replaces the variable with the requested URL when displaying the response page. |
|
<category/> |
The firewall replaces the variable with the URL filtering category of the blocked request. |
|
<pan_form/> |
HTML code for displaying the Continue button on the URL Filtering Continue and Override page. |
You can also add code that triggers the firewall to display different messages depending on what URL category the user is attempting to access. For example, the following code snippet from a response page specifies to display Message 1 if the URL category is games, Message 2 if the category is travel, or Message 3 if the category is kids:
var cat = "<category/>";
switch(cat)
{
case 'games':
document.getElementById("warningText").innerHTML = "Message 1";
break;
case 'travel':
document.getElementById("warningText").innerHTML = "Message 2";
break;
case 'kids':
document.getElementById("warningText").innerHTML = "Message 3";
break;
}
Response Page References
Only a single HTML page can be loaded into each virtual system for each type of block page. However, other resources such as images, sounds, and cascading style sheets (CSS files) can be loaded from other servers at the time the response page is displayed in the browser. All references must include a fully qualified URL.
|
Reference Type |
Example HTML Code |
|
Image |
<img src="http://virginiadot.org/images/Stop-Sign-gif.gif"> |
|
Sound |
<embed src="http://simplythebest.net/sounds/WAV/WAV_files/ movie_WAV_files/ do_not_go.wav" volume="100" hidden="true" autostart="true"> |
|
Style Sheet |
<link href="http://example.com/style.css" rel="stylesheet" type="text/css" /> |
|
Hyperlink |
<a href="http://en.wikipedia.org/wiki/Acceptable_use_policy">View Corporate Policy</a> |
Customize URL Filtering Response Pages
URL Filtering Response Page Objects
|
Where can I use this? |
What do I need? |
|
Notes:
|
By default, URL filtering response pages explain why a requested URL can't be accessed and show the user's IP address, the requested URL, and the URL category. You can customize the response pages to meet the needs of your enterprise. For example, you can change the message displayed to users, add corporate branding, or link to an acceptable use policy.
To customize a page, export it from a platform and modify it in a text editor. You can make updates using the provided response page variables and references . Response page variables correspond to the specific user, URL, and category that was blocked. Response page references enable the use of images, sounds, style sheets, and links.
The Panorama ™ web interface does not support the export of response pages.
Custom response pages larger than the maximum supported size are not decrypted or displayed to users. In PAN-OS 8.1.2 and earlier PAN-OS 8.1 releases, custom response pages on a decrypted site can't exceed 8,191 bytes; the maximum size is 17,999 bytes in PAN-OS 8.1.3 and later releases.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Export the default response pages you want to customize.
- Select ManageConfigurationNGFW and Prisma AccessSecurity ServicesURL Access ManagementSettings .
- In the Response Pages pane, click Export HTML Template for each response page you want to edit.
- Save the files to your system.
- Edit an exported response page.
- Using the HTML text editor of your choice, edit the page:
- To display custom information about the specific user, URL, or category that was blocked, add one or more response page variables .
- To include custom images, sounds, style sheets, or links, include one or more response page references .
- Save the edited page with a new filename.
Make sure that the page retains its UTF-8 encoding. For example, in Notepad you'd select UTF-8 from the Encoding drop-down in the Save As dialog.
- Import the customized response page.
- Select ManageConfigurationNGFW and Prisma AccessSecurity ServicesURL Access ManagementSettings .
- In the Response Pages pane, click the type of response page you customized. A file selection dialog appears.
For example, if you customized the URL Access Management Block Page, you'd click URL Access Management Block Page .
- Click Choose File , and then select the file you customized.
- Click Save .
- Click Push Config .
- Verify that the customized response page displays.
From a web browser, visit a URL that will trigger the response page. For example, to verify a customized URL Access Management Block Page, visit a URL blocked by your Security policy rules.
The firewall uses the following ports to display the URL Access Management response pages:
- HTTP —6080
- Default TLS with firewall certificate —6081
- Custom SSL/TLS profile —6082
- Export the predefined response pages you want to customize.
The Panorama web interface does not support the export of response pages. You can export response pages directly from the web interface of a specific firewall or use the Context drop-down on the Panorama web interface to quickly switch to the web interface of a managed firewall.
- Select DeviceResponse Pages .
- Select the Type of response page you want to edit. A dialog for the specific response page appears.
- Select Predefined , and then select Export .
- Close the dialog.
( Optional ) Repeat steps two through four for additional response pages.
- Save the files to your system.
- Customize an exported HTML response page.
- Open the file in a preferred text editor.
- To display custom information about a specific user, requested URL, or blocked URL category, use response page variables .
- To integrate custom images, sounds, style sheets, or links, use response page references .
- Save the edited file with a new name.
Make sure that the page retains its UTF-8 encoding. For example, in Notepad you would select UTF-8 from the Encoding drop-down in the Save As dialog.
- Import the customized response page.
- Select DeviceResponse Pages .
- Select the Type of response page you edited. A dialog for the specific response page appears.
- Select Predefined , and then select Import . An Import File dialog appears.
For Import File , Browse for the edited response page.
- ( Optional ) For Destination , select the virtual system that will use the response page, or select shared to make it available to all virtual systems.
- Click OK , and then Close the dialog.
- Commit your changes.
- Test the customized response page.
From a web browser, visit a URL that triggers the particular response page. For example, to verify a URL Filtering and Category Match response page, visit a URL blocked in a Security policy rule. Verify that your changes appear.
The firewall uses the following ports to display the URL filtering response pages:
- HTTP —6080
- Default TLS with firewall certificate —6081
- Custom SSL/TLS profile —6082
Safe Search Enforcement
Customize URL Filtering Response Pages
Safe Search Settings for Search Providers
|
Where Can I Use This? |
What Do I Need? |
|
Notes:
|
Many search engines offer a safe search setting that enables you to filter out adult content from search results. Filter settings typically include Moderate , Strict , and Off . You can use the moderate setting to filter out only adult images and videos or the strict setting, which additionally filters out explicit text. Educational institutions, workplaces, children, and adults all benefit from this safe search functionality. However, allowing users in your network to configure the safe search settings does not always provide the protection you need.
To protect your network from adult-oriented content, you can enforce the strictest safe search setting for all end users regardless of their current individual settings. The strictest safe search setting provides the safest browsing experience. First, select the Safe Search Enforcement option in a URL Filtering profile. Then, apply the profile to any Security policy rules that allow traffic from clients in the trust zone to the internet.
Neither search engine providers nor Palo Alto Networks can guarantee complete filtering accuracy. Search engines classify websites as safe or unsafe. As a result, a website classified as safe may contain explicit content. Palo Alto Networks enforces filtering based only on the filtering mechanisms of the search engine.
The firewall can enforce the following options when users search with Bing, Yahoo, Yandex, or YouTube and haven't set the safe search setting for these engines to the strictest level:
- Block Search Results When Strict Safe Search Is Off ( Default )—The firewall prevents end users from seeing search results until they set their safe search setting to the strictest available option. In this scenario, the browser displays the URL filtering safe search block page . This response page lets end users know why their search results were blocked and includes a link to the search settings of the search engine used for the search.
Palo Alto Networks no longer can detect whether Google SafeSearch is enabled due to changes in the Google safe search implementation. As a result, the block method does not work for Google searches. Instead, you can configure Google SafeSearch using the methods described in Safe Search Settings for Search Providers .
- Force Strict Safe Search ( Supported for Yahoo and Bing search engines only )—The firewall automatically and transparently enforces the strictest safe search settings. Specifically, the firewall redirects search queries to URLs that return strictly filtered search results and changes the safe search preference for the search engine used. To enable this functionality, replace the URL filtering safe search block page text with the text specified in the procedure. The replacement text includes JavaScript code that rewrites search query URLs with the strict safe search parameter for the search engine used for the search.
The browser does not display the URL filtering safe search block page when you use this method.
- Transparent SafeSearch ( Prisma Access Deployments Only )—In cases where traffic cannot be decrypted (for example, at a store that provides guest internet access) and you want to prevent users with unmanaged devices, including display devices, from searching for restricted, inappropriate, or offensive material, you can use transparent SafeSearch in Prisma Access, which resolves mobile users' search engine queries to the engine's SafeSearch portal by performing an FQDN-to-IP mapping.
Get started with safe search enforcement by reviewing the safe search settings of each supported search engine. Then, decide which enforcement method is best for your context.
Safe Search Settings for Search Providers
Block Search Results When Strict Safe Search Is Off
|
Where can I use this? |
What do I need? |
|
Notes:
|
Safe search settings differ for each search provider—review the following settings to learn more.
|
Search Provider |
Safe Search Setting Description |
|
Google/YouTube |
Offers safe search on individual computers or network-wide through Google’s safe search virtual IP address: Safe Search Enforcement for Google Searches on Individual Computers In the Google Search Settings , the Filter explicit results setting enables safe search functionality. When enabled, the setting is stored in a browser cookie as FF= and passed to the server each time the user performs a Google search. Appending safe=active to a Google search query URL also enables the strictest safe search settings. Safe Search Enforcement for Google and YouTube Searches using a Virtual IP Address Google provides servers that Lock SafeSearch (forcesafesearch.google.com) settings in every Google and YouTube search. By adding a DNS entry for www.google.com and www.youtube.com (and other relevant Google and YouTube country subdomains) that includes a CNAME record pointing to forcesafesearch.google.com to your DNS server configuration, you can ensure that all users on your network are using strict safe search settings every time they perform a Google or YouTube search. Keep in mind, however, that this solution is not compatible with Safe Search Enforcement on the firewall. Therefore, if you are using this option to force safe search on Google, the best practice is to block access to other search engines on the firewall by creating custom URL categories and adding them to the block list in the URL Filtering profile.
|
|
Yahoo |
Offers safe search on individual computers only. The Yahoo Search Preferences includes three SafeSearch settings: Strict , Moderate , or Off . When enabled, the setting is stored in a browser cookie as vm= and passed to the server each time the user performs a Yahoo search. Appending vm=r to a Yahoo search query URL also enables the strictest safe search settings. When performing a search on Yahoo Japan ( yahoo.co.jp ) while logged into a Yahoo account, end users must also enable the SafeSearch Lock option. |
|
Bing |
Offers safe search on individual computers. The Bing Settings include three SafeSearch settings: Strict , Moderate , or Off . When enabled, the setting is stored in a browser cookie as adtl= and passed to the server each time the user performs a Bing search. Appending adlt=strict to a Bing search query URL also enables the strictest safe search settings. The Bing SSL search engine does not enforce the safe search URL parameters and you should therefore consider blocking Bing over SSL for full safe search enforcement. |
Block Search Results When Strict Safe Search Is Off
Safe Search Settings for Search Providers
|
Where can I use this? |
What do I need? |
|
Notes:
|
If you enable Safe Search Enforcement, the default behavior of the firewall is to block search results for end users searching on Bing, Yahoo, Yandex, or Youtube search engines until they set their safe search setting to the strictest available option. By default, the URL filtering safe search block page displays in their browser. The predefined block page provides a link to the search settings for the search engine used, so that users can adjust the safe search setting. You can customize the safe search block page to meet your organization’s specific needs.
If you plan to use this method to enforce safe search, communicate this policy to your end users before implementing it. If you prefer to automatically redirect end users’ search query URLs to strict safe search versions, then enable strict safe search transparently .
Palo Alto Networks can no longer detect if Google SafeSearch is on due to changes in Google’s implementation. As a result, the firewall cannot enforce safe search using this method. You may still enforce safe search transparently. However, we cannot guarantee that Google will filter out explicit images and content.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Enable Safe Search Enforcement in a URL Access Management profile.
- Select ManageConfiguration Security ServicesURL Access Management .
- Under URL Access Management Profiles, select an existing profile or Add Profile to create a new one. Configuration options appear.
- Under Settings , select Safe Search Enforcement .
- Save the profile.
- ( Optional ) Restrict the search engines that end users can access.
- Select ManageConfiguration Security ServicesURL Access Management .
- Under Access Control , Search (
![]()
) for the search-engines category.
- Set Site Access for the search-engines category to block .
In a later
step
, you’ll create a custom URL category (URL List type) with the search engines you want to allow.
- Save the profile.
- Apply the URL Access Management profile to Security policy rules that allow traffic from clients in the trust zone to the internet.
To activate a URL Access Management profile (and any Security profile), add it to profile group and reference the profile group in a Security policy rule.
- Create a custom URL category for the supported search engines.
In the next step, you’ll configure the firewall to decrypt traffic to this custom category.
- Select ManageConfiguration Security ServicesURL Access Management .
- Under Access Control , for Custom URL Categories, Add Category .
- Enter a Name for the category, such as SearchEngineDecryption .
- For Type of custom URL category, select URL List .
- Under Items , Add the following entries to the URL list:
- www.bing.*
- search.yahoo.*
- yandex.com.*
- Save the custom category.
- Configure Site Access for the new custom URL category.
1. Under URL Access Management Profiles, select the profile you configured earlier.
2. Under Access Control, select the new custom URL category. It appears in the Custom URL Categories section above External Dynamic URL Lists and Pre-Defined Categories.
3. Set Site Access to allow .
4. Save your changes.
- Configure SSL Forward Proxy decryption.
Because most search engines encrypt their search results, you must enable SSL Forward Proxy decryption so the firewall can inspect the search traffic and detect the safe search settings.
Under the Services and URLs section of the Decryption policy rule, click Add URL Categories . Then, select the custom URL category you created earlier. New custom categories sit at the top of the list.
Save the Decryption policy rule.
- Select Push Config to activate your changes.
- Verify the Safe Search Enforcement configuration.
This verification step only works if you use block pages to enforce safe search. There is an alternative verification step if you enable safe search transparently.
- From a computer behind the firewall, disable the strict search settings for a supported search provider. For example, on bing.com, click the Preferences icon on the Bing menu bar.
- Set the SafeSearch option to Moderate or Off , and click Save .
- Perform a Bing search (or search using another provider) to see if the URL Access Management safe search block page displays instead of search results:
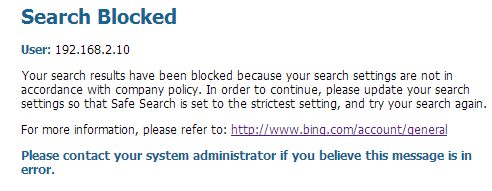
- Use the link on the block page to update the safe search setting to the strictest setting ( Strict in the case of Bing), and then click Save .
- Perform a search again from Bing and verify that filtered search results display instead of the block page.
- Enable Safe Search Enforcement in a URL Filtering profile.
- Select ObjectsSecurity ProfilesURL Filtering .
- Select an existing profile to modify or clone the default profile to create a new profile.
- On the URL Filtering Settings tab, select Safe Search Enforcement .
- ( Optional ) Restrict the search engines that end users can access in the same URL Filtering profile.
- On the Categories tab, Search (
![]()
) for the search-engines category.
- Set Site Access for the search-engines category to block .
In a later
step
, you’ll create a custom URL category (URL List type) with the search engines you want to allow.
- Click OK to save the profile.
- Apply the URL Filtering profile to Security policy rules that allow traffic from clients in the trust zone to the internet.
- Select PoliciesSecurity . Then, click the rule to which you want to apply the URL Filtering profile.
- On the Actions tab, find Profile Setting. For Profile Type , select Profiles . A list of profiles appears.
- For URL Filtering profile, select the profile you created earlier.
- Click OK to save the Security policy rule.
- Create a custom URL category for the supported search engines.
In the following step, you’ll specify that you want to decrypt traffic to the sites in the custom category.
- Select ObjectsCustom ObjectsURL Category and Add a custom category.
- Enter a Name for the category, such as SearchEngineDecryption .
- Add the following entries to the Sites list:
- www.bing.*
- search.yahoo.*
- yandex.com.*
- Click OK to save the custom category.
- Configure Site Access for the new custom URL category.
1. Go to ObjectsSecurity ProfilesURL Filtering and select the URL Filtering profile you configured earlier.
2. On the Category tab, select the new custom URL category. It appears in the Custom URL Categories section above External Dynamic URL Lists and Pre-defined Categories.
3. Set Site Access to allow .
4. Click OK to save your changes.
- Configure SSL Forward Proxy decryption.
Because most search engines encrypt their search results, you must enable SSL Forward Proxy decryption so the firewall can inspect the search traffic and detect the safe search settings.
On the Service/URL Category tab of the Decryption policy rule, Add the custom URL category you created earlier. Then, click OK .
- Commit your changes.
- Verify the Safe Search Enforcement configuration.
This verification step only works if you use block pages to enforce safe search. There is an alternative verification step if you enable safe search transparently.
- From a computer behind the firewall, disable the strict search settings for a supported search provider. For example, on bing.com, click the Preferences icon on the Bing menu bar.

- Set the SafeSearch option to Moderate or Off , and click Save .
- Perform a Bing search (or search using another provider) to see if the URL Filtering Safe Search Block page displays instead of search results:

- Use the link on the block page to update the safe search setting to the strictest setting ( Strict in the case of Bing), and then click Save .
- Perform a search again from Bing and verify that the filtered search results display instead of the block page.
Force Strict Safe Search
Block Search Results When Strict Safe Search Is Off
Use Transparent SafeSearch in Prisma Access
|
Where can I use this? |
What do I need? |
|
Notes:
|
You can provide a secure and seamless search experience for Bing and Yahoo end users by transparently enabling strict safe search. Instead of blocking search results when end users search without having enabled strict safe search, the firewall automatically turns on strict safe search and returns only strictly filtered search results. Schools and libraries, for example, can benefit from automatic enforcement that ensures a consistent learning experience.
To activate transparent safe search enforcement, you’ll need to enable Safe Search Enforcement in a URL Filtering profile and replace text in the URL filtering safe search block page file with text provided in the following procedure. The replacement text contains JavaScript that appends search query URLs with strict safe search parameters for the search engine used to search.
The URL filtering safe search block page does not display in the browser.
After completing these steps, the firewall executes the JavaScript whenever an end user searches. For example, suppose a student’s Bing SafeSearch preference is set to Off when they research a concept likely to yield inappropriate results. Detecting the safe search preference, the firewall appends &adlt=strict to the search query URL. Then, the search engine displays appropriate results and the SafeSearch preference changes to Strict .
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Enable Safe Search Enforcement in a URL Access Management profile.
- Select ManageConfiguration Security ServicesURL Access Management .
- Under URL Access Management Profiles, select an existing profile or Add Profile to create a new one. Configuration options appear.
- Under Settings , select Safe Search Enforcement .
- Save the profile.
- ( Optional ) Restrict the search engines that end users can access.
- Select ManageConfiguration Security ServicesURL Access Management .
- Under Access Control , Search (
![]()
) for the search-engines category.
- Set Site Access for the search-engines category to block .
In a later
step
, you’ll create a custom URL category (URL List type) with the search engines you want to allow.
- Save the profile.
- Apply the URL Access Management profile to Security policy rules that allow traffic from clients in the trust zone to the internet.
To activate a URL Access Management profile (and any Security profile), add it to profile group and reference the profile group in a Security policy rule.
- Edit the URL Access Management safe search block page, replacing the existing code with JavaScript for rewriting search query URLs.
- Select ManageConfiguration Security ServicesURL Access ManagementResponse Pages .
- Export HTML Template for URL Access Management Block Page.
- Use an HTML editor and replace all of the existing block page text with the following text. Then, save the file.
Copy
<html>
<head>
<title>Search Blocked</title>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<meta http-equiv="pragma" content="no-cache">
<meta name="viewport" content="initial-scale=1.0">
<style>
#content {
border:3px solid#aaa;
background-color:#fff;
margin:1.5em;
padding:1.5em;
font-family:Tahoma,Helvetica,Arial,sans-serif;
font-size:1em;
}
h1 {
font-size:1.3em;
font-weight:bold;
color:#196390;
}
b {
font-weight:normal;
color:#196390;
}
</style>
</head>
<body bgcolor="#e7e8e9">
<div id="content">
<h1>Search Blocked</h1>
<p>
<b>User:</b>
<user/>
</p>
<p>Your search results have been blocked because your search settings are not in accordance with company policy. In order to continue, please update your search settings so that Safe Search is set to the strictest setting. If you are currently logged into your account, please also lock Safe Search and try your search again.</p>
<p>
For more information, please refer to:
<a href="<ssurl/>">
<ssurl/>
</a>
</p>
<p id="java_off"> Please enable JavaScript in your browser.<br></p>
<p><b>Please contact your system administrator if you believe this message is in error.</b></p>
</div>
</body>
<script>
// Grab the URL that's in the browser.
var s_u = location.href;
//bing
// Matches the forward slashes in the beginning, anything, then ".bing." then anything followed by a non greedy slash. Hopefully the first forward slash.
var b_a = /^.*\/\/(.+\.bing\..+?)\//.exec(s_u);
if (b_a) {
s_u = s_u + "&adlt=strict";
window.location.replace(s_u);
document.getElementById("java_off").innerHTML = 'You are being redirected to a safer search!';
}
//yahoo
// Matches the forward slashes in the beginning, anything, then ".yahoo."" then anything followed by a non greedy slash. Hopefully the first forward slash.
var y_a = /^.*\/\/(.+\.yahoo\..+?)\//.exec(s_u);
if (y_a) {
s_u = s_u.replace(/&vm=p/ig,"");
s_u = s_u + "&vm=r";
window.location.replace(s_u);
document.getElementById("java_off").innerHTML = 'You are being redirected to a safer search!';
}
document.getElementById("java_off").innerHTML = ' ';
</script>
</html>
Copy
- Import the edited URL Access Management safe search block page onto the firewall.
- Select ManageConfiguration Security ServicesURL Access ManagementResponse Pages .
- Click URL Access Management Safe Search Block Page. A dialog appears with a Choose File option.
- Select the safe search block page file you edited earlier and click Save .
- Create a custom URL category for the supported search engines.
In the next step, you’ll configure the firewall to decrypt traffic to this custom category.
- Select ManageConfiguration Security ServicesURL Access Management .
- Under Access Control , for Custom URL Categories, Add Category .
- Enter a Name for the category, such as SearchEngineDecryption .
- For Type of custom URL category, select URL List .
- Under Items , Add the following entries to the URL list:
- www.bing.*
- search.yahoo.*
- yandex.com.*
- Save the custom category.
- Configure Site Access for the new custom URL category.
1. Under URL Access Management Profiles, select the profile you configured earlier.
2. Under Access Control, select the new custom URL category. It appears in the Custom URL Categories section above External Dynamic URL Lists and Pre-Defined Categories.
3. Set Site Access to allow .
4. Save your changes.
- Configure SSL Forward Proxy decryption.
Because most search engines encrypt their search results, you must enable SSL Forward Proxy decryption so the firewall can inspect the search traffic and detect the safe search settings.
Under the Services and URLs section of the Decryption policy rule, click Add URL Categories . Then, select the custom URL category you created earlier. New custom categories sit at the top of the list.
Save the Decryption policy rule.
- Select Push Config to activate your changes.
- Verify the Safe Search Enforcement configuration.
From a computer behind a firewall, open a browser and perform a search using Bing, Yahoo, or Yandex. Then, use one of the following methods to verify your configuration:
- Examine the query string of the URL for safe search parameters. Safe Search Settings for Search Providers lists the safe search parameter appended to each search query URL.
- Go to the safe search settings for a supported search engine and verify that the selected SafeSearch preference is the strictest level ( Strict in most cases).
- Make sure the firewall is running Content Release version 475 or later.
- Select DeviceDynamic Updates .
- Check the Applications and Threats section to determine what update is currently running.
- If the firewall is not running the required update or later, click Check Now to retrieve a list of available updates.
- Locate the required update and click Download .
- After the download completes, click Install .
- Enable Safe Search Enforcement in a URL Filtering profile.
- Select ObjectsSecurity ProfilesURL Filtering .
- Select an existing profile to modify or clone the default profile to create a new profile.
- On the URL Filtering Settings tab, select Safe Search Enforcement .
- ( Optional ) Restrict the search engines that end users can access in the same URL Filtering profile.
- On the Categories tab, Search (
![]()
) for the search-engines category.
- Set Site Access for the search-engines category to block .
In a later
step
, you’ll create a custom URL category (URL List type) with the search engines you want to allow.
- Click OK to save the profile.
- Apply the URL Filtering profile to Security policy rules that allow traffic from clients in the trust zone to the internet.
- Select PoliciesSecurity . Then, click the rule to which you want to apply the URL Filtering profile.
- On the Actions tab, find Profile Setting. For Profile Type , select Profiles . A list of profiles appears.
- For the URL Filtering profile, select the profile you created earlier.
- Click OK to save the Security policy rule.
- Edit the URL filtering safe search block page, replacing the existing code with JavaScript for rewriting search query URLs.
- Select DeviceResponse PagesURL Filtering Safe Search Block Page .
- Select Predefined and then click Export to save the file locally.
- Use an HTML editor and replace all of the existing block page text with the following text. Then, save the file.
- <html>
- <head>
- <title>Search Blocked</title>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
- <meta http-equiv="pragma" content="no-cache">
- <meta name="viewport" content="initial-scale=1.0">
- <style>
- #content {
- border:3px solid#aaa;
- background-color:#fff;
- margin:1.5em;
- padding:1.5em;
- font-family:Tahoma,Helvetica,Arial,sans-serif;
- font-size:1em;
- }
- h1 {
- font-size:1.3em;
- font-weight:bold;
- color:#196390;
- }
- b {
- font-weight:normal;
- color:#196390;
- }
- </style>
- </head>
- <body bgcolor="#e7e8e9">
- <div id="content">
- <h1>Search Blocked</h1>
- <p>
- <b>User:</b>
- <user/>
- </p>
- <p>Your search results have been blocked because your search settings are not in accordance with company policy. In order to continue, please update your search settings so that Safe Search is set to the strictest setting. If you are currently logged into your account, please also lock Safe Search and try your search again.</p>
- <p>
- For more information, please refer to:
- <a href="<ssurl/>">
- <ssurl/>
- </a>
- </p>
- <p id="java_off"> Please enable JavaScript in your browser.<br></p>
- <p><b>Please contact your system administrator if you believe this message is in error.</b></p>
- </div>
- </body>
- <script>
- // Grab the URL that's in the browser.
- var s_u = location.href;
- //bing
- // Matches the forward slashes in the beginning, anything, then ".bing." then anything followed by a non greedy slash. Hopefully the first forward slash.
- var b_a = /^.*\/\/(.+\.bing\..+?)\//.exec(s_u);
- if (b_a) {
- s_u = s_u + "&adlt=strict";
- window.location.replace(s_u);
- document.getElementById("java_off").innerHTML = 'You are being redirected to a safer search!';
- }
- //yahoo
- // Matches the forward slashes in the beginning, anything, then ".yahoo."" then anything followed by a non greedy slash. Hopefully the first forward slash.
- var y_a = /^.*\/\/(.+\.yahoo\..+?)\//.exec(s_u);
- if (y_a) {
- s_u = s_u.replace(/&vm=p/ig,"");
- s_u = s_u + "&vm=r";
- window.location.replace(s_u);
- document.getElementById("java_off").innerHTML = 'You are being redirected to a safer search!';
- }
- document.getElementById("java_off").innerHTML = ' ';
- </script>
</html>
Copy
- Import the edited URL filtering safe search block page onto the firewall.
- Select DeviceResponse PagesURL Filtering Safe Search Block Page .
- Click Import . Then, Browse for the block page file or enter the path and filename in the Import File field.
- ( Optional ) For Destination , select either the virtual system on which the login page will be used or shared to make it available to all virtual systems.
- Click OK to import the file.
- Create a custom URL category for the supported search engines.
In the next step, you’ll configure the firewall to decrypt traffic to this custom category.
- Select ObjectsCustom ObjectsURL Category and Add a custom category.
- Enter a Name for the category, such as SearchEngineDecryption .
- Add the following entries to the Sites list:
- www.bing.*
- search.yahoo.*
- yandex.com.*
- Click OK to save the custom URL category.
- Configure SSL Forward Proxy decryption.
Because most search engines encrypt their search results, you must enable SSL Forward Proxy decryption so the firewall can inspect the search traffic and detect the safe search settings.
On the Service/URL Category tab of the Decryption policy rule, Add the custom URL category you created earlier. Then, click OK .
- Commit your changes.
- Verify the Safe Search Enforcement configuration.
From a computer behind a firewall, open a browser and perform a search using Bing or Yahoo. Then, use one of the following methods to verify your configuration works as intended:
- Examine the query string of the URL for safe search parameters. Safe Search Settings for Search Providers lists the safe search parameter appended to each search query URL.
- Go to the Safe Search settings for the search engine and verify that the selected SafeSearch preference is the strictest level ( Strict in the case of Bing).
Use Transparent SafeSearch in Prisma Access
Integrate with a Third-Party Remote Browser Isolation Provider
|
Where Can I Use This? |
What Do I Need? |
If you'd like to use this feature in your Prisma Access environment, get in touch with your account team to learn more. |
|
Prisma Access allows you to resolve mobile users' search engine queries to the engine's SafeSearch portal by performing an FQDN-to-IP mapping. Use transparent SafeSearch as an alternative to implementing strict SafeSearch when traffic cannot be decrypted (for example, at a store that provides guest internet access) and you want to prevent users with unmanaged devices, including display devices, from searching for restricted, inappropriate, or offensive material.
To configure transparent SafeSearch support for Prisma Access in Strata Cloud Manager, complete the following steps. You can configure transparent SafeSearch for either remote networks or GlobalProtect mobile users.
- Choose the deployment type (mobile users or remote networks) for which you want to configure SafeSearch.
- For Mobile Users—GlobalProtect deployments, go to ManageService SetupMobile Users ; then, select GlobalProtect SetupInfrastructure Settings .
If you're using Strata Cloud Manager, go to WorkflowsPrisma Access SetupMobile Users ; then, select GlobalProtect SetupInfrastructure Settings .
- For Remote Network deployments, go to ManageService SetupRemote Networks .
If you're using Strata Cloud Manager, go to WorkflowsPrisma Access SetupRemote Networks .
- Select Advanced Settings .
- Use Static Entries to resolve FQDNs to specific IP addresses.
- Enter a unique Name for the static entry rule, the FQDN for the search engine, and the search engine's SafeSearch IP Address where the FQDN request should be directed.
To configure transparent SafeSearch support for Prisma Access in Panorama, complete the following steps. You can configure transparent SafeSearch for either remote networks or GlobalProtect mobile users.
- Choose the deployment type (remote networks or mobile users) for which you want to configure SafeSearch.
- For Mobile Users—GlobalProtect deployments, go to PanoramaCloud ServicesConfigurationMobile Users—GlobalProtect , select Configure in the Onboarding area; then, select Network Services .
- For Remote Network deployments, go to PanoramaCloud ServicesConfigurationRemote Networks , click the gear to edit the Settings ; then, select DNS Proxy .
- Enter Static IP Entries by entering a unique Name for the static entry rule, the FQDN for the search engine, and the search engine's SafeSearch IP Address where the FQDN request should be directed.
Integrate with a Third-Party Remote Browser Isolation Provider
Use Transparent SafeSearch in Prisma Access
|
Where can I use this? |
What do I need? |
|
Note: Prisma Access licenses include Advanced URL Filtering capabilities. |
While it’s the most secure action, blocking unknown and risky sites can disrupt your users’ experience and productivity. Remote Browser Isolation (RBI) redirects users from unknown or risky sites to an isolated environment hosted by an RBI provider. The website is rendered for the user and they can view the resources they need, without directly accessing the unknown or risky site from their endpoint.
Prisma Access easily integrates with RBI providers for this type of browser redirection. In just a step or two, you can choose the RBI provider to integrate with, and then choose the URL categories that you want to direct to the RBI provider’s hosted environment.
In addition to third-party RBI Providers, Remote Browser Isolation (RBI) by Palo Alto Networks is available to natively integrate with Prisma Access. Unlike other isolation solutions, RBI uses next-generation isolation technologies to deliver near-native experiences for users accessing websites without compromising on security.
Here are the RBI providers Prisma Access integrates with—some providers might require you to add RBI environment details (like a vanity URL or tenant ID) to Strata Cloud Manager to set up the integration:
- RBI by Palo Alto Networks
To integrate with RBI by Palo Alto Networks, you will need to configure Remote Browser Isolation .
- Authentic8
To integrate with Authentic8, have the vanity URL for the Authentic8 RBI environment at hand.
- Proofpoint
To integrate with Proofpoint, be ready to choose to use the Proofpoint production or PoC environment for RBI.
- Ericom
To integrate with Ericom, have the tenant ID for the Ericom RBI environment at hand.
- Menlo Security
You don’t need to configure any settings for the Menlo Security RBI environment; all you need to do is enable the integration.
Here’s how to add your third-party RBI provider to Strata Cloud Manager and specify the URL categories that will redirect users to the RBI environment.
- Set up Remote Browser Isolation (RBI).
- Go to ManageConfigurationNGFW and Prisma AccessSecurity ServicesURL Access ManagementSettings and open the Third Party Remote Browser Isolation Settings .
- IF YOU’RE A WEB SECURITY ADMIN : Navigate to ManageConfigurationWeb SecurityThreat Management and open the Third Party Remote Browser Isolation Settings .
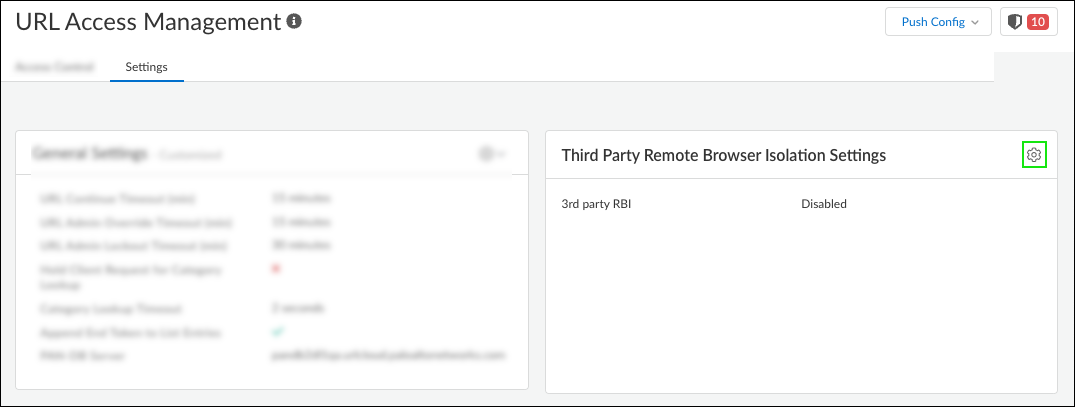
- Check if your RBI requires you to specify the RBI environment you want to use; if so, enter the required settings.
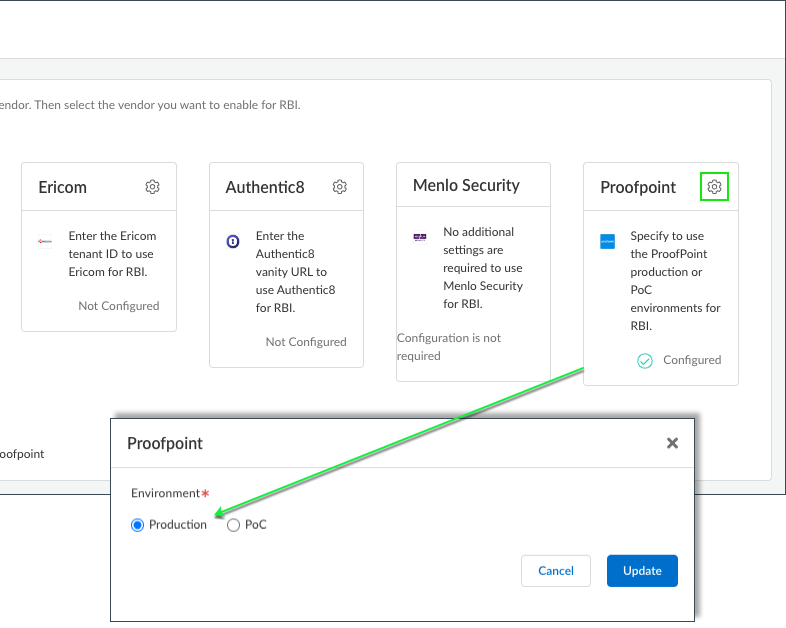
- Then, choose the third-party RBI provider you want to enable and Save . That’s it! When you next Push Config , your RBI provider will integrate with Prisma Access.
You can also Configure Remote Browser Isolation if you already purchased and activated the license for RBI by Palo Alto Networks . However, you cannot use both RBI by Palo Alto Networks and a third-party RBI vendor for isolation. If you choose to use RBI by Palo Alto Networks, select None , otherwise, select a third-party RBI vendor from Selected Third Party Vendor for Remote Browser Isolation .
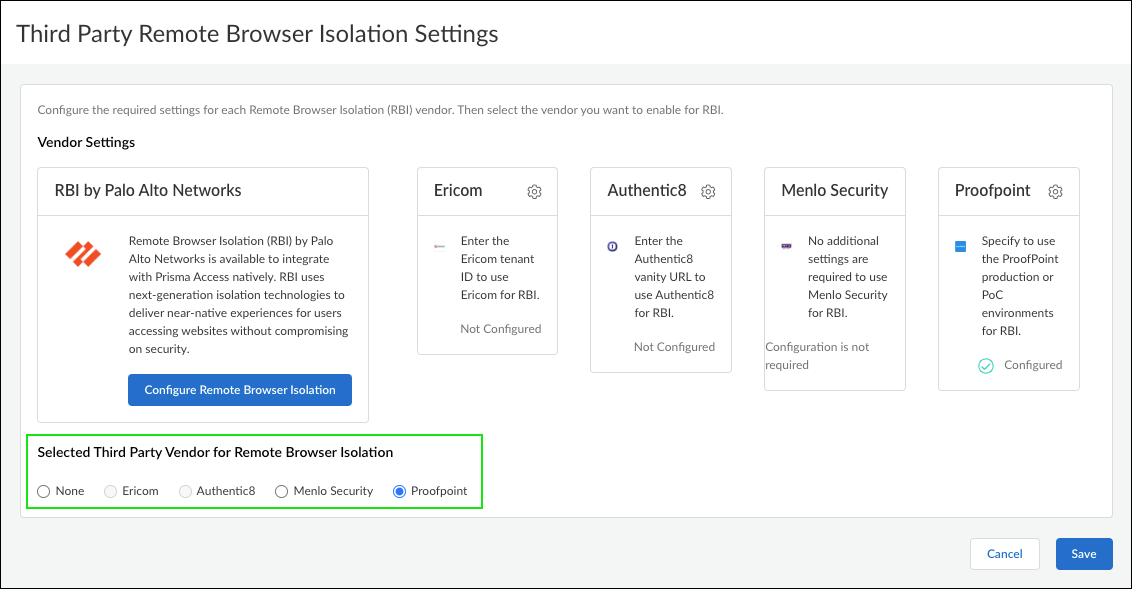
- Now, specify the URL categories that will redirect users to the RBI environment.
Go to URL Access Management > Access Control and add or edit a URL Access Management Profile .
In the Access Control settings, update Site Access to Redirect .
The new Redirect action redirects users to the RBI environment instead of presenting them with a block page.
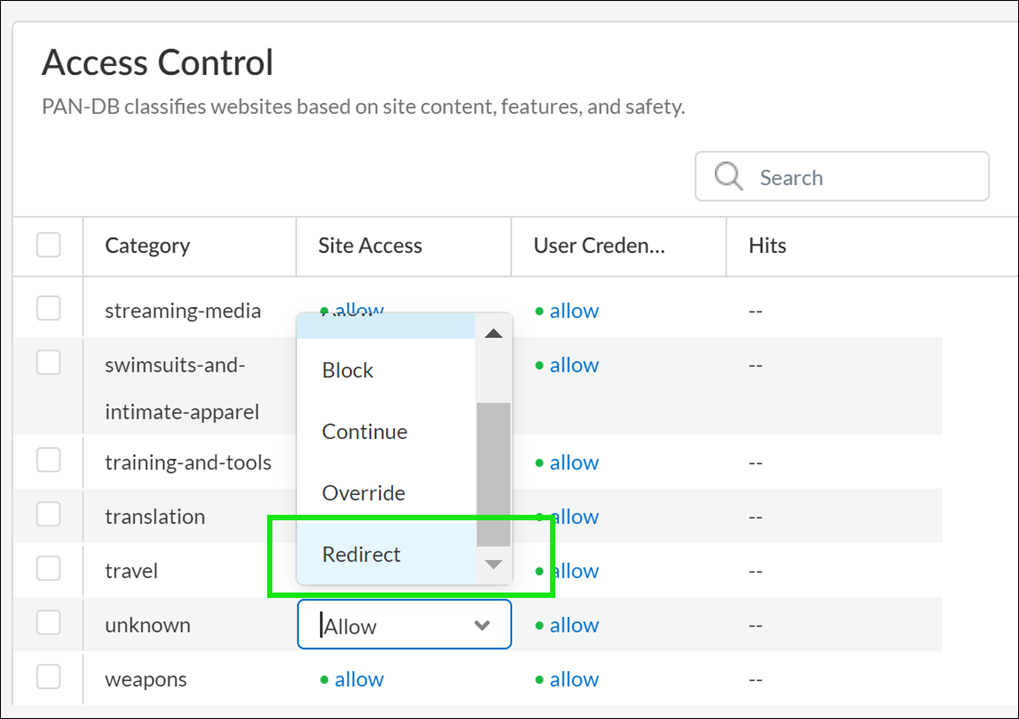
Monitoring
Integrate with a Third-Party Remote Browser Isolation Provider
|
Where can I use this? |
What do I need? |
|
Notes:
|
Monitoring web activity on your network is essential for protecting your organization and ensuring the efficacy of your URL filtering policy. Palo Alto Networks platforms generate detailed logs, which serve as a source for dashboards and reports. You can customize logs, dashboards, and reports to meet your specific monitoring and reporting needs. If necessary, you can request URL category changes from URL Filtering logs. Use the insights offered by our monitoring tools to fine-tune web access policy rules and analyze and take action on any suspicious activity.
The HTTP header logging and log container page only features offer control over log detail and volume. HTTP header logging increases the granularity of logs. Logging only the main page users access reduces the number of generated logs.
Explore the following topics to learn more about web activity monitoring tools and features.
Monitoring Web Activity
|
Where can I use this? |
What do I need? |
|
Notes:
|
You can view various dashboards, reports, and logs to review and analyze web activity on your network. For example, on PAN-OS next-generation firewalls, the Application Command Center (ACC), URL filtering logs and reports show all user web activity for URL categories that are set to alert , block , continue , or override . By monitoring user activity with the following tools, you can gain a better understanding of the web activity of your user base and determine appropriate web access policy rules.
|
Platform |
Ways to View User Web Activity |
|
PAN-OS & Panorama |
|
|
Prisma Access |
|
Regardless of the interface you’re using to manage Prisma Access (Panorama or Strata Cloud Manager), the Activity pane in Strata Cloud Manager provides a comprehensive view of what’s happening in your network. Various dashboards compose the Activity pane, which is available in the Strata Cloud Manager and Device Insights application. You can also share Activity data with other users in your organization.
The following interactive dashboards help you monitor and analyze web activity on your network:
- Threat Insights —A holistic view of all threats that Advanced URL Filtering and other Palo Alto Networks security services detected and blocked in your network. You can view threat trends, impacted applications, users, and Security policy rules that are allowing or blocking threats.
- Log Viewer —Your logs provide an audit trail for system, configuration, and network events. Jump from an Activity dashboard to your logs to get details and investigate findings.
- Application Usage —See an overview of the applications on your network, including their risk, sanction status, bandwidth consumed, and the top users of these applications.
- Executive Summary (URL Filtering) —See which URL categories account for the most web activity in your network, the top 10 malicious URLs, and top 10 high-risk URLs.
- User Activity —See individual users’ browsing patterns: their most frequently visited sites, the sites with which they’re transferring data, and attempts to access high-risk sites. The data from your URL Filtering logs and the Cloud Identity Engine enable this visibility.
- To access user activity data and share reports easily and securely, we recommend activating and configuring the Cloud Identity Engine .
Additional Visibility and Methods of Monitoring:
- The Reports pane includes options for scheduling report delivery or downloading and sharing a report at any time for offline viewing.
- You can also Search for a security artifact (an IP address, domain, URL, or file hash) to interact with data just for that artifact, drawn from both your network and global threat intelligence findings.
- Open an Activity dashboard.
- Select ActivityThreat Insights | Application Usage | User Activity | Executive Summary .
To view the executive summary for URL Filtering, you’ll need to click the URL Filtering tab upon landing on the dashboard.
- To access the Log Viewer, select ActivityLogsLog Viewer .
- Download, share, and schedule Activity reports .
- For a quick view of the most common categories users access in your environment, check the ACC widgets. Most Network Activity widgets allow you to sort on URLs. For example, in the Application Usage widget, you can see that the networking category is the most accessed category, followed by encrypted tunnel, and ssl. You can also view the list of Threat Activity and Blocked Activity sorted on URLs.
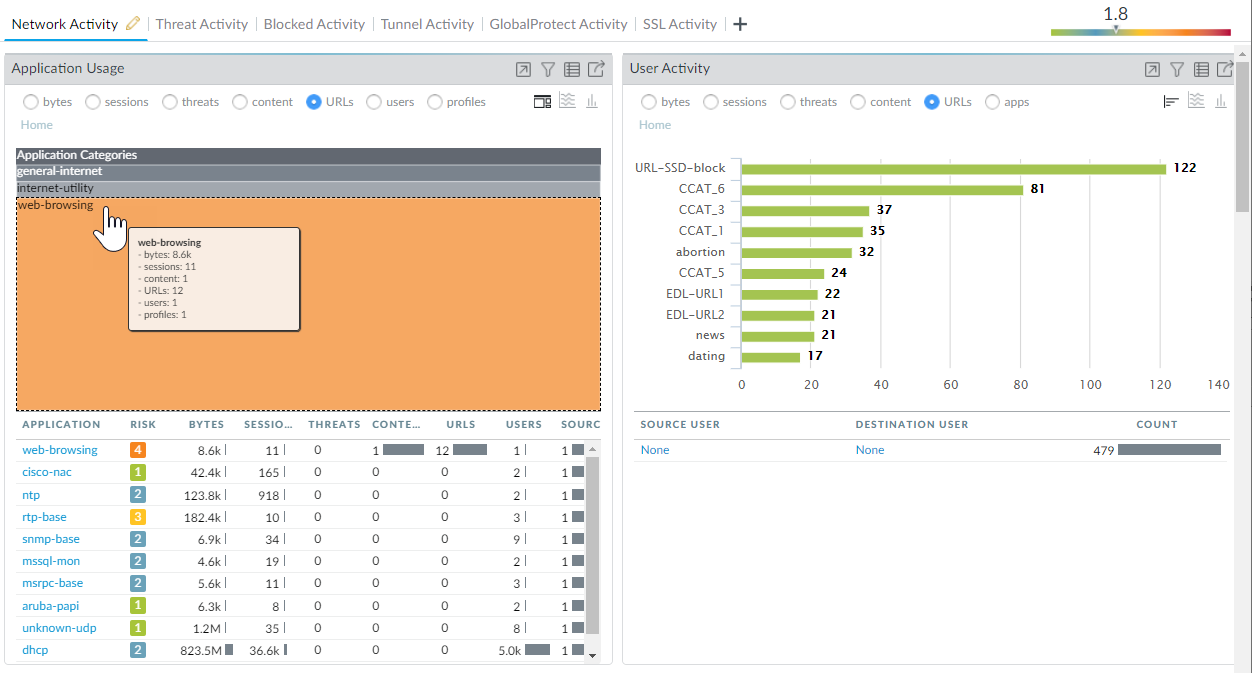
View logs and configure log options:
- From the ACC, you can jump directly to the logs (
![]()
) or select MonitorLogsURL Filtering .
The log action for each entry depends on the Site Access setting you defined for the corresponding category:
- Alert log —In this example, the computer-and-internet-info category is set to alert.
- Block log —In this example, the insufficient-content category is set to continue. If the category had been set to block instead, the log Action would be block-url.
- Alert log on encrypted website —In this example, the category is private-ip-addresses and the application is web-browsing. This log also indicates that the firewall decrypted this traffic.
- The [local] Inline ML verdict (PAN-OS 10.0/10.1) and [local and cloud] Inline Categorization verdict (PAN-OS 10.2 and later) indicate the verdict determined by inline ML-based analyzers.
- The Inline ML verdict applies to URLs that have been categorized using the locally operated URL Filtering Inline ML on PAN-OS 10.0/10.1.
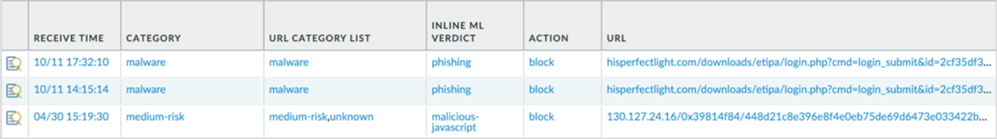
The following verdicts are available:
- Phishing —phishing attack content detected by local inline ML.
- Malicious-javascript —malicious javascript content detected by local inline ML.
- Unknown —URL was categorized and content determined to be benign.
- The Inline Categorization verdict applies to URLs that have been categorized using both the locally operated URL Filtering Inline ML (which was renamed to local Inline Categorization in PAN-OS 10.2) as well as cloud Inline Categorization, operating in the Advanced URL Filtering cloud. The specific type of attack is specified under the category column in the log.
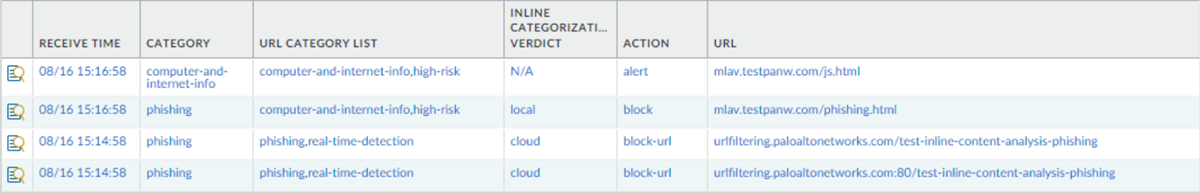
The following verdicts are available:
- Local —malicious content detected using local inline categorization.
- Cloud —malicious content detected using the cloud inline categorization engine located in the Advanced URL Filtering cloud.
- N/A —URL was not analyzed by the local or cloud inline categorization engines.
- You can also add several other columns to your URL Filtering log view, such as: to and from zone, content type, and whether or not a packet capture was performed. To modify what columns to display, click the down arrow in any column and select the attribute to display.
- To view the complete log details and/or request a category change for the given URL that was accessed, click the log details icon in the first column of the log.
- Generate predefined URL filtering reports on URL categories, URL users, Websites accessed, Blocked categories, and more.
Select MonitorReports and under the URL Filtering Reports section, select one of the reports. The reports cover the 24-hour period of the date you select on the calendar. You can also export the report to PDF, CSV, or XML.
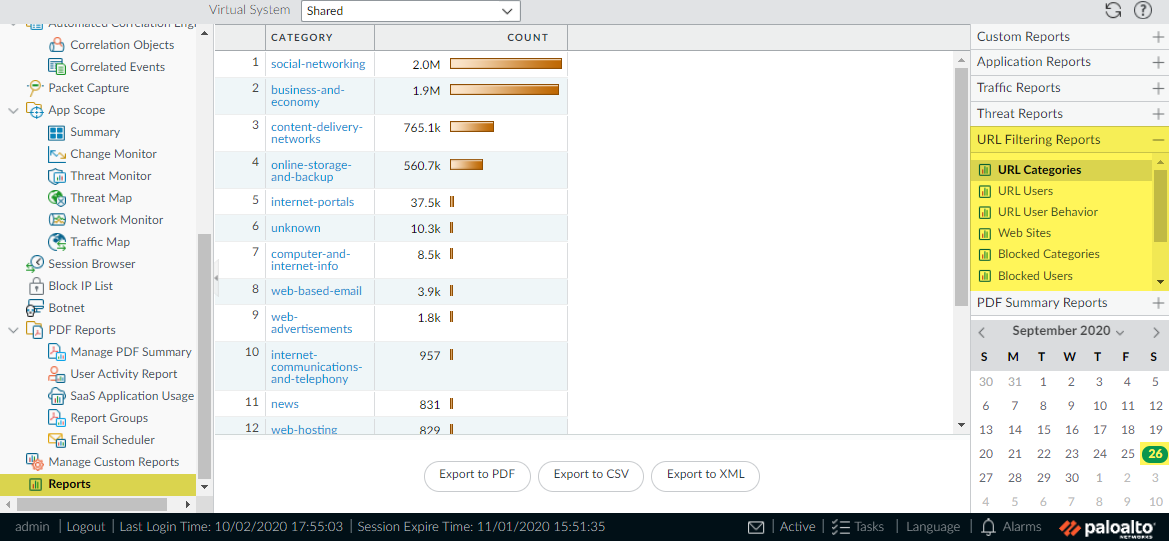
View the User Activity Report
Schedule and Share URL Filtering Reports
|
Where can I use this? |
What do I need? |
|
Notes:
|
This report provides a quick method of viewing user or group activity and also provides an option to view browse time activity.
Whether you're using Panorama or Strata Cloud Manager to manage Prisma Access, you can go to the Strata Cloud Manager app to generate a user activity report. In the app, go to Activity to find the User Activity Report dashboard. Access to user activity data requires an active Cloud Identity Engine tenant.
- Activate the Cloud Identity Engine .
- Set up the Cloud Identity Engine .
- Configure a User Activity Report.
- Select ActivityUser Activity .
- Enter Username to generate a report for one person.
- Select the report Type :
- Select User to generate a report for one person.
- Select Group for a group of users.
You must enable User-ID in order to be able to select user or group names. If User-ID is not configured, you can select the type User and enter the IP address of the user’s computer.
- Enter the Username/IP Address for a user report or enter the group name for a user group report.
- Select the time period. You can select an existing time period, or select Custom .
- Select the Include Detailed Browsing check box, so browsing information is included in the report.
- Run the report.
- Click Run Now .
- When the firewall finishes generating report, click one of the links to download it:
- Click Download User Activity Report to download a PDF version of the report.
- Click Download URL Logs to download a CSV file of the corresponding log entries.
- After downloading the report, click Cancel .
- If you want to save the user activity report settings so you can run the same report again later, click OK ; otherwise click Cancel .
- View the user activity report by opening the file that you downloaded. The PDF version of the report shows the user or group on which you based the report, the report time frame, and a table of contents:
- Click an item in the table of contents to view the report details. For example, click Traffic Summary by URL Category to view statistics for the selected user or group.
- Configure a User Activity Report.
- Select MonitorPDF ReportsUser Activity Report .
- Add a report and enter a Name for it.
- Select the report Type :
- Select User to generate a report for one person.
- Select Group for a group of users.
You must enable User-ID to be able to select user or group names. If User-ID is not configured, you can select the type User and enter the IP address of the user’s computer.
- Enter the Username/IP Address for a user report or enter the group name for a user group report.
- Select the time period. You can select an existing time period, or select Custom .
- Select the Include Detailed Browsing check box, so browsing information is included in the report.
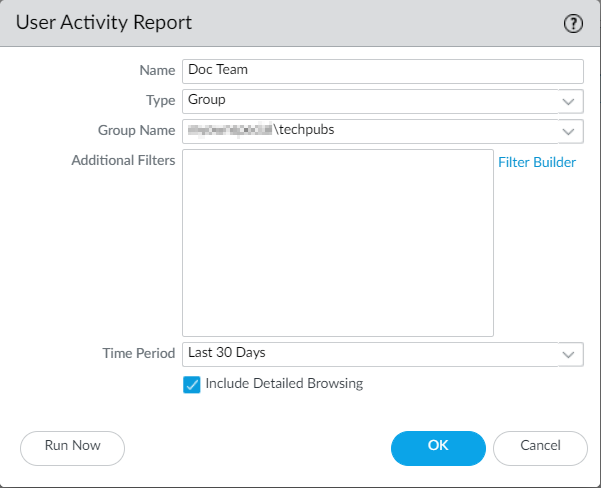
- Run the report.
- Click Run Now .
- When the firewall finishes generating report, click one of the links to download it:
- Click Download User Activity Report to download a PDF version of the report.
- Click Download URL Logs to download a CSV file of the corresponding log entries.
- After downloading the report, click Cancel .
- If you want to save the user activity report settings to run the same report again later, click OK ; otherwise click Cancel .
- View the user activity report by opening the file that you downloaded. The PDF version of the report shows the user or group on which you based the report, the report time frame, and a table of contents:
- Click an item in the table of contents to view the report details. For example, click Traffic Summary by URL Category to view statistics for the selected user or group.
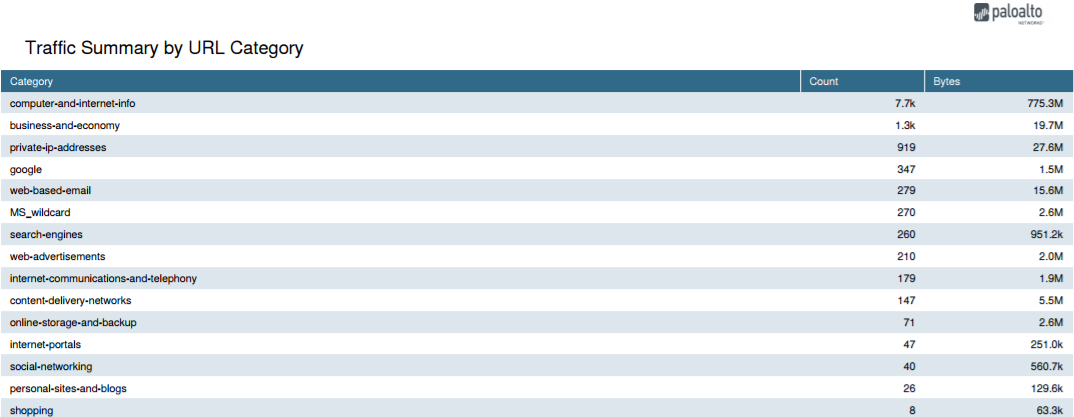
Schedule and Share URL Filtering Reports
Log Only the Page a User Visits
|
Where can I use this? |
What do I need? |
|
Notes:
|
You can schedule, generate, and share various reports related to URL filtering and web activity.
Whether you're using Panorama or Strata Cloud Manager to manage Prisma Access, you can use Strata Cloud Manager for URL Filtering reports. In Strata Cloud Manager, go to Activity for interactive URL Filtering data and reports. You can share Activity reports within your organization and also schedule them for regular updates. Here are the Prisma Access dashboards and tools that leverage and are most relevant to URL Filtering:
- Executive Summary —See which URL categories account for the most web activity in your network, the top 10 malicious URLs, and top 10 high-risk URLs.
- User Activity —See individual users’ browsing patterns: their most frequently visited sites, the sites with which they’re transferring data, and attempts to access high-risk sites. The data from your URL Filtering logs and the Cloud Identity Engine enable this visibility.
- Search for a security artifact (an IP address, domain, URL, or file hash) to interact with data just for that artifact, drawn from both your network and global threat intelligence findings.
To access user activity data and share reports easily and securely, we recommend activating and configuring the Cloud Identity Engine .
- Download, share, and schedule Activity reports .
- Access the URL filtering executive summary.
Select ActivityExecutive Summary and click the URL Filtering tab.
- Add a new custom report.
- Select MonitorManage Custom Reports and Add a report.
- Give the report a unique Name , and optionally a Description .
- Select the Database you want to use to generate the report. To generate a detailed URL Filtering report, select URL from the Detailed Logs section:
- Configure report options.
- Select a predefined Time Frame or select Custom .
- Select the log columns to include in the report from the Available Columns list add them (
![]()
) to the Selected Columns. For example, for a URL Filtering report you might select:
- Action
- App Category
- Category
- Destination Country
- Source User
- URL
- If the firewall is enabled to prevent credential phishing , select the Attribute Flags , the Operator has and the Value Credential Detected to also include events in the report that record when a user submitted a valid corporate credential to a site.
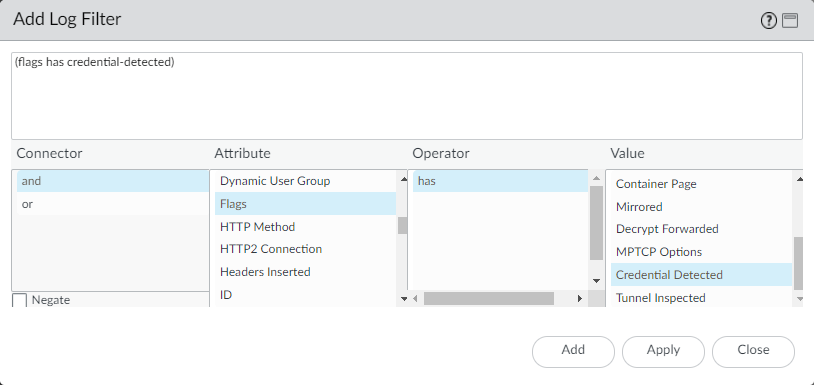
- ( Optional ) Select a Sort By option to set the attribute to use to aggregate the report details. If you do not select an attribute to sort by, the report will return the first N number of results without any aggregation. Select a Group By attribute to use as an anchor for grouping data. The following example shows a report with Group By set to App Category and Sort By set to a Count of Top 5 .
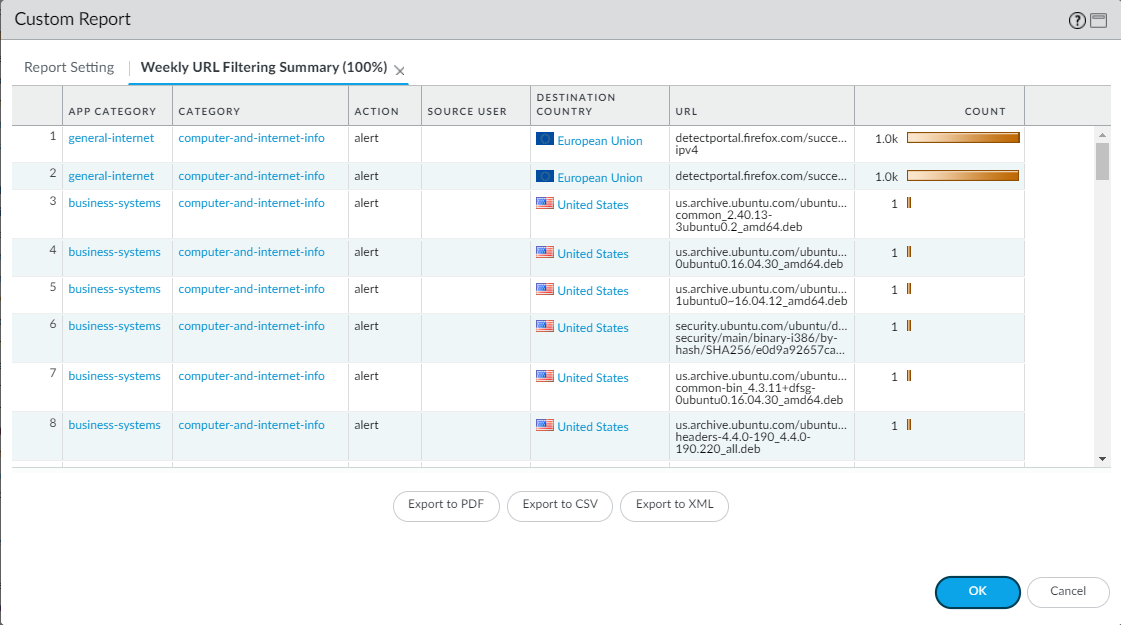
- Run the report.
- Click the Run Now icon to immediately generate the report, which opens in a new tab.
- When you are done reviewing the report, go back to the Report Setting tab and either tune the settings and run the report again, or continue to the next step to schedule the report.
- Select the Schedule check box to run the report once per day. This will generate a daily report that details web activity over the last 24 hours.
- Commit the configuration.
- View the custom report.
- Select MonitorReports .
- Expand the Custom Reports pane in the right column and select the report you want to view. The latest report displays automatically.
- To view the report for a previous date, select the date from the calendar. You can also export the report to PDF, CSV, or XML.
Log Only the Page a User Visits
Schedule and Share URL Filtering Reports
|
Where can I use this? |
What do I need? |
|
Notes:
|
A container page is the main page that a user accesses when visiting a website, but additional pages might be loaded along with the main page. If the Log Container page only option is enabled in a URL Filtering profile (URL Access Management profile for Prisma Access), only the main container page will be logged, not subsequent pages that may be loaded within the container page. Because URL filtering can potentially generate a lot of log entries, you may want to turn on this option, so log entries will only contain those URIs where the requested page file name matches the specific mime-types. The default set includes the following mime-types:
- application/pdf
- application/soap+xml
- application/xhtml+xml
- text/html
- text/plain
- text/xml
If you enable the Log container page only option, there may not always be a correlated URL log entry for threats detected by antivirus or vulnerability protection.
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- In a URL Access Management profile, select Log Container Page Only .
- Apply the URL Access Management profile to a Security policy rule.
A URL Access Management profile is only active when it’s included in a profile group that a Security policy rule references.
Follow the steps to activate a URL Access Management profile (and any Security profile). Be sure to Push Config .
- Create or select a URL Filtering profile to modify.
Select ObjectsSecurity ProfilesURL Filtering .
- Enable Log container page only .
- Click OK to save the profile.
- Commit your changes.
HTTP Header Logging
Log Only the Page a User Visits
Request to Change the Category of a URL
|
Where can I use this? |
What do I need? |
|
Notes:
|
URL filtering provides visibility and control over web traffic on your network. For improved visibility into web content, you can configure the URL Filtering profile to log HTTP header attributes included in a web request. When a client requests a web page, the HTTP header includes the user agent, referer, and x-forwarded-for fields as attribute-value pairs and forwards them to the web server. When enabled for logging HTTP headers, the firewall logs the following attribute-value pairs in the URL Filtering logs.
You can also use HTTP headers to manage access to SaaS applications. You don’t need a URL Filtering license to do this, but you must use a URL Filtering profile to turn this feature on.
|
Attribute |
Description |
|
User-Agent |
The web browser that the user used to access the URL, for example, Internet Explorer. This information is sent in the HTTP request to the server. The HTTP header does not contain the full string for the User Agent. The maximum logged bytes from the packet preceding the packet containing the header-end is 36 bytes. |
|
Referer |
The URL of the web page that linked the user to another web page; it is the source that redirected (referred) the user to the web page that is being requested. |
|
X-Forwarded-For (XFF) |
The option in the HTTP request header field that preserves the IP address of the user who requested the web page. If you have a proxy server on your network, the XFF allows you to identify the IP address of the user who requested the content, instead of only recording the proxy server’s IP address as source IP address that requested the web page. |
|
Headers Inserted |
The type of header and the text of the header that the firewall inserts. |
Request to Change the Category of a URL
|
Where can I use this? |
What do I need? |
|
Notes:
|
If you think a domain or URL has been incorrectly categorized, you can submit a recategorization request through your firewall or Test A Site , our URL category lookup tool. You can also submit bulk recategorization requests through Test A Site. Both methods require you to suggest at least one new category for the URL you want reviewed.
You cannot request a change to the risk category a URL receives, or for URLs categorized as insufficient content or newly-registered domains .
On the firewall, you can request a URL category change from the Detailed Log View of a URL filtering log entry. On Test A Site, you must enter the website you want to recategorize to view its PAN-DB categorization. The request form link follows the search results. Similarly, in Strata Cloud Manager, a link to the Test A Site form displays with the results from queries to the internal Test A Site tool available when editing URL Access Management profiles. To access the bulk change request form, you'll need to log in to Test A Site. After logging in, the webpage displays a link to the bulk request form.
Immediately after someone submits a change request, an automated crawler analyzes the URL. If the crawler validates your category suggestion, Palo Alto Networks approves your request and immediately updates PAN-DB with the new category. If not, human editors from Palo Alto Networks threat research and data science teams review your request. They may decide to keep the original category, agree with your suggested category, or change the category (if they disagree with both the original and the suggested category).
After submitting a change request, you’ll receive an email confirmation. After the investigation is complete, you’ll receive a second email with the results.
- Access the URL Filtering logs ( MonitorLogsURL Filtering ).
- Open the Detailed Log View for a URL filtering log entry with URL categorization you would like to change.
- Click the spyglass (
![]()
) corresponding to the log entry. The Detailed Log View appears.
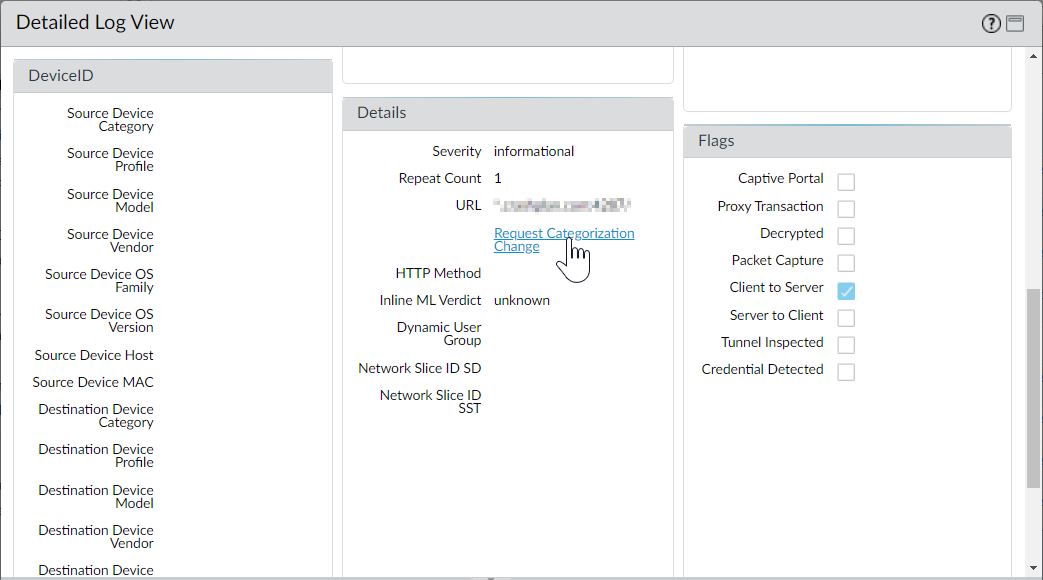
- Under Details, click Request Categorization Change .
- Complete the request form, and submit it.
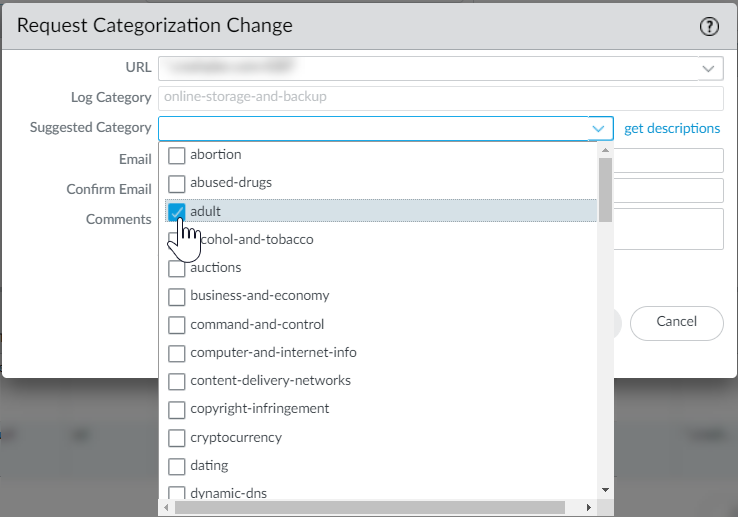
- Go to Test A Site .
Log in to avoid completing a CAPTCHA test and entering your email on the change request form. Note that logging in is the only way to access the bulk change request form.
- Select a change request form to complete.
- Change Request for a Single URL —Enter the URL you want to recategorize, and click Search . Underneath the URL category results, click Request Change .
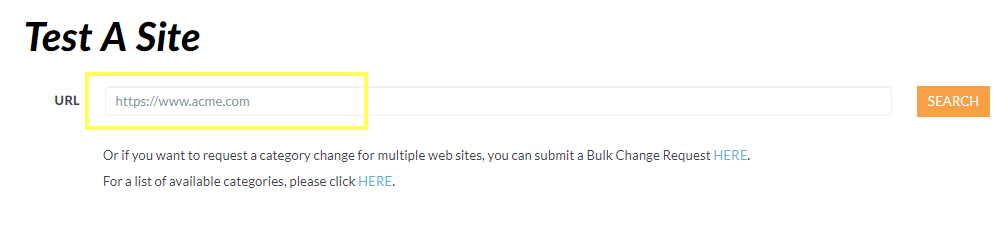
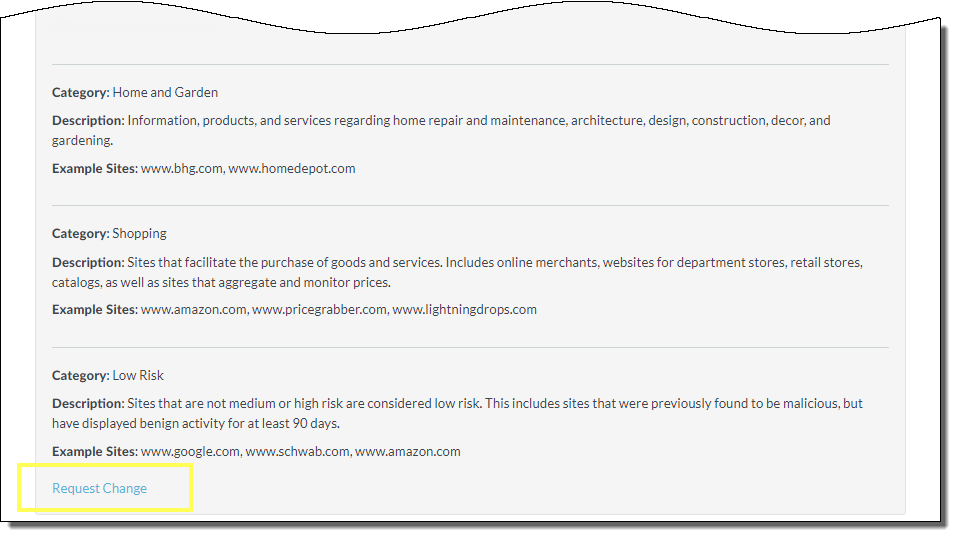
- Bulk Change Request — Log-in to Test A Site. Then, click submit a Bulk Change Request HERE .
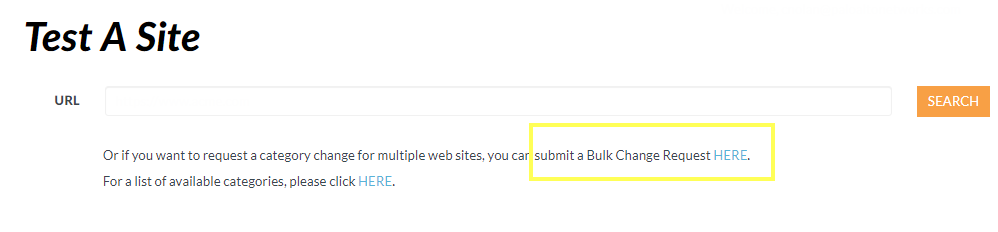
- Complete the change request form.
- Change Request for a Single URL —Suggest up to two new categories for the URL. Click Select category (from a list) , and select one category at a time. Optionally, leave a Comment about your request. You can explain why your suggestion is appropriate, for example.
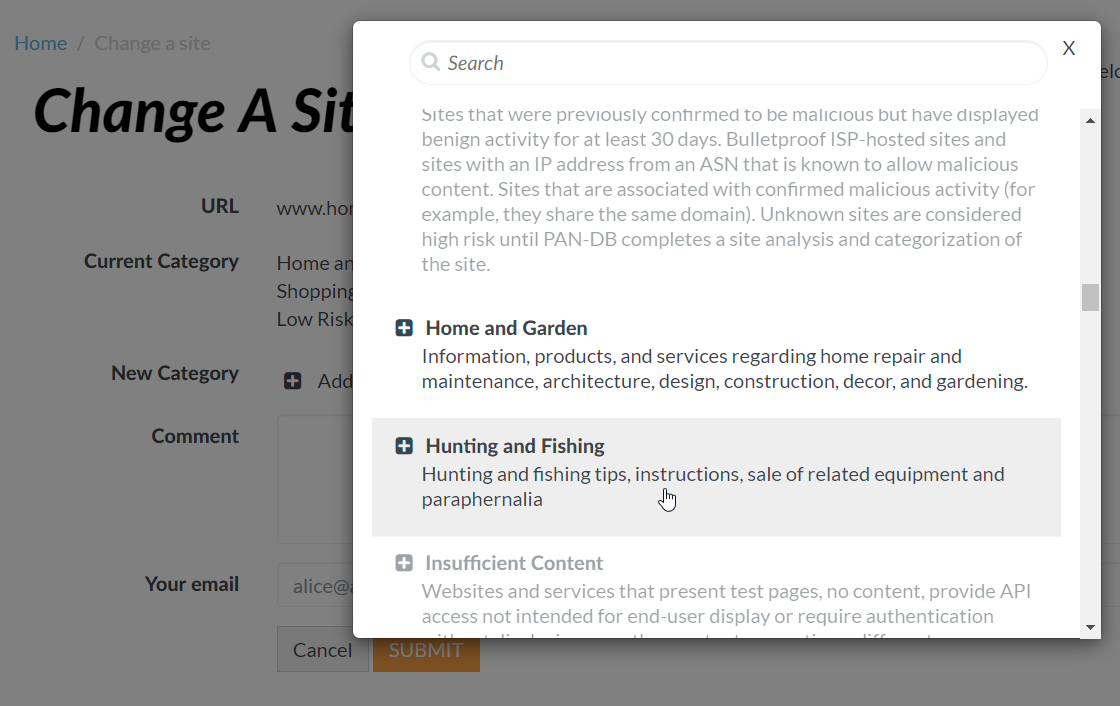
- Bulk Change Request —Choose a File Format . Select Multiple Category if your change request includes two or more categories. For example, if you want to recategorize half of the URLs in your list to business-and-economy and the other half to personal-sites-and-blogs .
Then, click Choose File , and select a CSV file to upload. The file should have one change request per line in this format: <URL>,<first suggested category>,<second suggested category>,<(optional) comment> . The file cannot exceed 1000 entries or be larger than 1MB. Optionally, leave a Comment about your request.
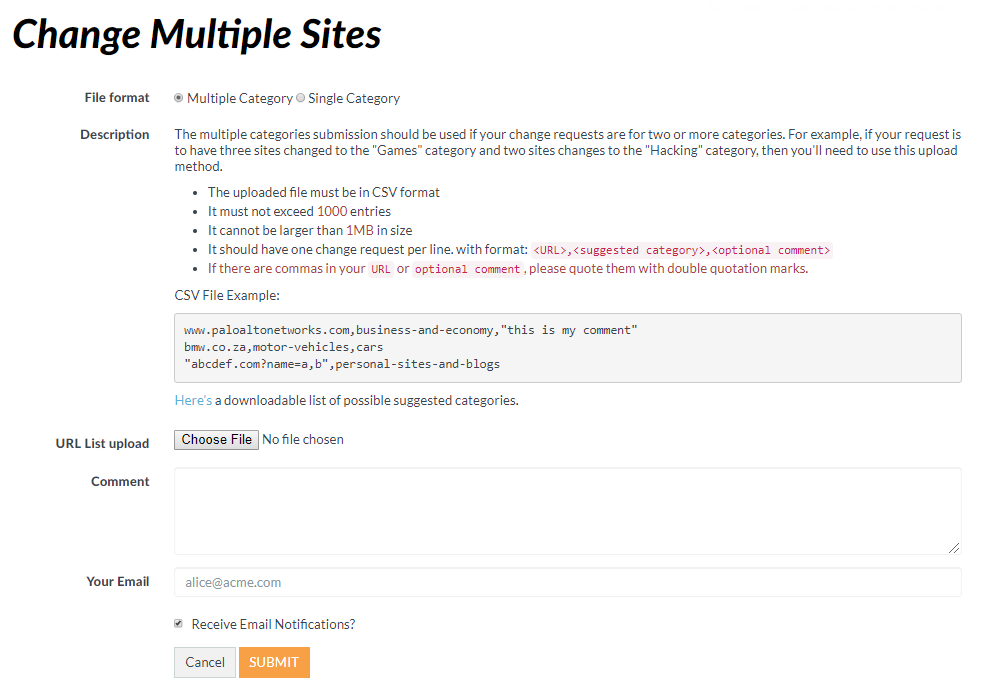
- Submit the form.
Troubleshooting
Request to Change the Category of a URL
Problems Activating Advanced URL Filtering
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
This chapter shares tasks for diagnosing and resolving common URL filtering problems for Palo Alto Networks next-generation firewalls. Before you reach out to Palo Alto Networks support regarding these issues, complete the steps in the relevant tasks. If you still need to reach out to support, be sure to include all information you learned from performing troubleshooting tasks.
Troubleshooting and monitoring web activity often go hand-in-hand. Leverage monitoring and logging tools often to identify and troubleshoot issues that this chapter does not explicitly discuss. Familiarize yourself with monitoring tools and tasks in the Monitoring chapter.
Problems Activating Advanced URL Filtering
PAN-DB Cloud Connectivity Issues
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
Use the following workflow to troubleshoot Advanced URL Filtering activation issues.
- Access the PAN-OS CLI .
- Verify whether Advanced URL Filtering has been activated by running the following command:
show system setting url-database
If the response is paloaltonetworks , PAN-DB, the Palo Alto Networks URL filtering database, is the active vendor.
- Verify that the firewall has a valid Advanced URL Filtering license.
Run the request license info CLI command.
You should see the license entry Feature: Advanced URL Filtering . If the license is not installed, you will need to obtain and install a license. See Configure URL Filtering .
- Check the PAN-DB cloud connection status .
PAN-DB Cloud Connectivity Issues
Problems Activating Advanced URL Filtering
URLs Classified as Not-Resolved
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
To help ensure connectivity to PAN-DB cloud, create a dedicated Security policy rule that allows all Palo Alto Management Service traffic. This will avoid management traffic from being classified as not-resolved and prevent the traffic from being blocked when routed through the dataplane.
To check connectivity between the firewall and the PAN-DB cloud:
show url-cloud status
If the cloud is accessible, the expected response is similar to the following:
show url-cloud status
PAN-DB URL Filtering
License : valid
Current cloud server : serverlist.urlcloud.paloaltonetworks.com
Cloud connection : connected
Cloud mode : public
URL database version - device : 20200624.20296
URL database version - cloud : 20200624.20296 ( last update time 2020/06/24 12:39:19 )
URL database status : good
URL protocol version - device : pan/2.0.0
URL protocol version - cloud : pan/2.0.0
Protocol compatibility status : compatible
If the cloud is not accessible, the expected response is similar to the following:
show url-cloud status
PAN-DB URL Filtering
License : valid
Cloud connection : not connected
URL database version - device : 0000.00.00.000
URL protocol version - device : pan/0.0.2
Use the following checklist to identify and resolve connectivity issues:
- Does the PAN-DB URL Filtering license field shows as invalid? Obtain and install a valid PAN-DB license.
- Does the URL protocol version show as not compatible? Upgrade PAN-OS to the latest version.
- Can you ping the PAN-DB cloud server from the firewall? Run the following command to check:
ping source <ip-address> host serverlist.urlcloud.paloaltonetworks.com <
For example, if your management interface IP address is 10.1.1.5, run the following command:
ping source 10.1.1.5 host serverlist.urlcloud.paloaltonetworks.com
- Is the firewall in an HA configuration? Verify that the HA state of the firewalls is in the active, active-primary, or active-secondary state. Access to the PAN-DB cloud will be blocked if the firewall is in a different state. Run the following command on each firewall in the pair to see the state:
show high-availability state
If you still have problems with connectivity between the firewall and the PAN-DB cloud, contact Palo Alto Networks support.
URLs Classified as Not-Resolved
PAN-DB Cloud Connectivity Issues
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
URLs are classified as not-resolved if your firewall cannot connect to the PAN-DB URL filtering cloud service to perform lookups, or if PAN-DB takes too long to respond to URL queries. The cloud connection status and URL classification does not apply to expired subscription licenses or unlicensed users. For a detailed explanation of the URL categorization process, see How URL Filtering Works .
Use the following workflow to troubleshoot why some or all of the URLs being identified by PAN-DB are classified as Not-resolved:
- Check the PAN-DB cloud connection by running the show url-cloud status CLI command.
The Cloud connection: field should show connected . If you see anything other than connected , then any URL that does not exist in the management plane cache will be categorized as not-resolved . To resolve this issue, see PAN-DB Cloud Connectivity Issues .
- If the cloud connection status shows connected , check the current utilization of the firewall.
If firewall utilization is spiking, URL requests may be dropped (may not reach the management plane) and will be categorized as not-resolved .
To view system resources, run the show system resources CLI command. Then, view the %CPU and %MEM columns.
You can also view system resources on the System Resources widget on the Dashboard in the web interface.
- Consider increasing the Category lookup timeout (sec) value.
Increasing the category lookup timeout value improves the likelihood that the URL category gets resolved and reduces the frequency of not-resolved URLs in logs.
- Select DeviceSetupContent-ID and edit the URL Filtering settings.
- Click OK and Commit your changes.
You can also update the value using the set deviceconfig setting ctd url-wait-timeout CLI command.
- If the problem persists, contact Palo Alto Networks support.
Incorrect Categorization
URLs Classified as Not-Resolved
Troubleshoot Website Access Issues
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
Sometimes you may come across a URL that you believe is categorized incorrectly. Use the following workflow to determine the URL categorization for a site and request a category change, if appropriate.
- Verify the category in the dataplane by running the following command:
show running url <URL>
For example, to view the category for the Palo Alto Networks website, run the following command:
show running url paloaltonetworks.com
If the URL stored in the dataplane cache has the correct category (computer-and-internet-info in this example), then the categorization is correct and no further action is required. If the category is not correct, continue to the next step.
- Verify if the category in the management plane by running the command:
test url-info-host <URL>
For example:
test url-info-host paloaltonetworks.com
If the URL stored in the management plane cache has the correct category, remove the URL from the dataplane cache by running the following command:
clear url-cache url <URL>
The next time the firewall requests the category for this URL, the request will be forwarded to the management plane. This will resolve the issue and no further action is required. If this does not solve the issue, go to the next step to check the URL category on the cloud systems.
- Verify the category in the cloud by running the following command:
test url-info-cloud <URL>
- If the URL stored in the cloud has the correct category, remove the URL from the dataplane and the management plane caches.
Run the following command to delete a URL from the dataplane cache:
clear url-cache url <URL>
Run the following command to delete a URL from the management plane cache:
delete url-database url <URL>
The next time the firewall queries for the category of the given URL, the request will be forwarded to the management plane and then to the cloud. This should resolve the category lookup issue. If problems persist, see the next step to submit a categorization change request.
- To submit a change request from the web interface, go to the URL log and select the log entry for the URL you would like to have changed.
- Click the Request Categorization change link and follow instructions. You can also request a category change from Palo Alto Networks Test A Site website by searching for the URL and then clicking the Request Change icon. To view descriptions of each category, refer to Predefined URL Categories .
If your change request is approved, you will receive an email notification. You then have two options to ensure that the URL category is updated on the firewall:
- Wait until the URL in the cache expires and the next time the URL is accessed by a user, the new categorization update will be put in the cache.
- Run the following command to force an update in the cache:
request url-filtering update url <URL>
Troubleshoot Website Access Issues
Troubleshoot URL Filtering Response Page Display Issues
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
End users may encounter issues accessing a website for various reasons, including a missing URL filtering license, policy rule misconfiguration, PAN-DB connectivity issues, or miscategorization of a website. Use the following steps to diagnose and resolve issues with accessing a website.
It's possible the issue may not be URL Filtering related. The "What to do next" section that follows the steps in this task lists additional areas in which to focus your troubleshooting.
- Verify that you have an active Advanced URL Filtering or legacy URL filtering license.
An active URL filtering license is needed for next-generation firewalls to accurately categorize websites and applications. If you don't have a URL filtering license, then the website access issue is unrelated to URL filtering.
Select DeviceLicenses and look for the Advanced URL Filtering (or PAN-DB URL Filtering) license. An active license displays an expiration date later than the current date.
Alternatively, use the request license info CLI command. If the license is active, the interface displays license information, including expiration status: Expired?: no .
- Verify the PAN-DB cloud connection status on your CLI.
The Cloud connection: field should show connected . Otherwise, any URL that doesn't exist in the management plane (MP) cache will be categorized as not-resolved and may be blocked by the URL Filtering profile settings in your Security policy rules.
- Clear the MP and dataplane (DP) cache for the specific URL.
Clearing the cache can be resource-intensive. Consider clearing the cache during a maintenance window.
- To clear the MP cache, use the delete url-database url <affected url> CLI command.
- To clear the DP cache, use the clear url-cache url <affected url> CLI command.
- Review the URL filtering logs to verify if the URL category that the website belongs to has been blocked.
- Select MonitorURL Filtering .
- Search for the affected URL, and then select the most recent log entry.
- Review the Category and Action columns.
Has the URL been categorized correctly? Verify its categories using Test A Site , Palo Alto Networks URL category lookup tool. If you still believe the categorization is incorrect, submit a change request .
If the Action column displays block-url , then note the name of the Security policy rule associated with the log entry.
- Review the Security policy rule and update it, if necessary.
- Select PoliciesSecurity , and select the policy rule with the name you noted in the previous step.
- Verify that the Security policy rule allows access to the requested URL or its URL category.
Look for one of two configurations:
- URL Category as Match Criteria: Under Service/URL Category , one of the specified categories contains the requested URL. Under Actions , the Action Setting is set to Allow .
- URL Filtering Profile: Under Actions , the Profile Setting is set to a URL Filtering profile that allows access to the requested URL.
- Test your Security policy rules .
If the above steps don't highlight or resolve the issue, additional troubleshooting might be required to further isolate the issue. Areas of focus should include:
- Basic IP address connectivity
- Routing configuration
- DNS resolution
- Proxy configuration
- Upstream firewall or inspection devices in the packet path
For intermittent or complex issues, contact Palo Alto Networks support for further assistance.
Troubleshoot URL Filtering Response Page Display Issues
Troubleshoot Website Access Issues
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
URL filtering response pages may not display for various reasons, including:
- SSL/TLS handshake inspections are enabled.
- The website was blocked during the inspection of an SSL/TLS handshake. URL filtering response pages do not display in this case because the firewall resets the HTTPS connection.
- The website uses the HTTPS protocol or contains content served over HTTPS (such as ads) but the website or URL category was not decrypted.
- The custom response page is larger than the maximum supported size.
Use the following steps as a starting point for troubleshooting a URL filtering response page that fails to display. If the problem persists, contact Palo Alto Networks support.
- Determine the scope of the issue.
Is the issue specific to a particular website or a subset of web pages? Check if a response page displays when you visit a different page on the website.
- Identify the website's protocol (HTTP or HTTPS).
This distinction aids in further isolating and diagnosing the issue.
- ( HTTPS sites or HTTP sites with HTTPS content ) Verify that an SSL/TLS decryption policy rule decrypts traffic to the website or URL category.
In general, the firewall can't serve response pages on HTTPS websites unless it can decrypt the websites.
Some websites may serve its primary page over HTTP but serve ads or other content over HTTPS. These websites should also be decrypted to ensure the display of response pages.
- Log in to the web interface.
- Select PoliciesDecryption , and verify that the relevant rule decrypts traffic to the specific website or URL category.
If this is not the case, update the decryption policy rule to decrypt the website or URL category.
- If SSL/TLS decryption is enabled and the response page still doesn't display, then enable inspection of SSL/TLS handshakes .
- To serve a URL filtering response page over an HTTPS session without enabling SSL/TLS decryption, follow these steps .
- Verify that the URL category that the website belongs to has been blocked.
If the category has been blocked in a URL Filtering profile applied to a Security policy rule or by a Security policy rule with the specific URL category as match criteria, the value in the Action column for a given entry displays block-url .
- Select MonitorURL Filtering .
- Search for the affected website, and select the most recent log entry.
- Examine the Category and Action columns.
Are the categories assigned to the website accurate? Verify its categories using Test A Site , Palo Alto Networks URL category lookup tool. If you still believe the website is categorized incorrectly, submit a change request .
Is the Action value block-url ? If not, update the URL Filtering profile or Security policy rule .
- For future reference, note the rule associated with this log entry.
- Determine if a custom response page is the cause of this issue.
- Select DeviceResponse Pages .
- Confirm that only Predefined is selected.
A custom response page is active if shared is listed (in addition to Predefined ) in either of these places:
- DeviceResponse Pages : Under the Location column corresponding to a given response page.
- DeviceResponse PagesType : Under Location.
- ( If Shared is listed ) Revert the custom page to its default state to confirm that the custom response page is the issue.
1. Delete the custom page.
2. Commit your changes.
3. Visit the affected website to see if the default response page displays.
If the problem persists, call support for further investigation.
If the above steps fail to correct the issue, contact Palo Alto Networks support. Additional troubleshooting may be necessary to pinpoint the issue. For example, analyzing the traffic through a packet capture (pcap) tool alongside support may be helpful if a response page fails to function for some web pages but works for others.
PAN-DB Private Cloud
Troubleshoot URL Filtering Response Page Display Issues
How PAN-DB Private Cloud Works
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
The PAN-DB private cloud provides an on-premises solution for organizations that restrict the usage of public cloud services. Notably, firewalls query PAN-DB private cloud servers during URL lookups instead of PAN-DB public cloud servers. To implement this solution, you'll need to deploy one or more M-600 or M-700 appliances as PAN-DB servers within your network or data center. Only firewalls running PAN-OS 9.1 or later versions can communicate with the PAN-DB private cloud.
PAN-DB private cloud deployments do not support the cloud-based URL analysis features of the Advanced URL Filtering subscription.
The following table describes the differences between the PAN-DB public cloud and the PAN-DB private cloud.
|
Differences Between the PAN-DB Public Cloud and PAN-DB Private Cloud Differences |
PAN-DB Public Cloud |
PAN-DB Private Cloud |
|
Content and Database Updates |
Content (regular and critical) updates and full URL database updates are published multiple times a day. The PAN-DB public cloud updates the malware and phishing URL categories every five minutes. The firewall also checks for critical updates whenever it queries the cloud servers for URL lookups. |
Content updates and full URL database updates are available once a day during the work week. |
|
URL Categorization Requests |
You can request a URL categorization change through:
|
You can request a URL categorization change through Palo Alto Networks Test A Site website. |
|
Unresolved URL Queries |
If the firewall can't resolve a URL query, the request is sent to the servers in the public cloud. |
If the firewall can't resolve a query, the request is sent to the appliances in the PAN-DB private cloud. If there isn't a match for the URL, the PAN-DB private cloud sends an unknown category response to the firewall; the request isn't sent to the public cloud unless you've configured your appliances to access the PAN-DB public cloud. If the appliances in your PAN-DB private cloud operate completely offline, the firewall doesn't send any data or analytics to the public cloud. |
How PAN-DB Private Cloud Works
PAN-DB Private Cloud Appliances
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
When you set up the PAN-DB private cloud , you can configure your M-600 or M-700 appliances to have direct internet access or remain offline. The appliances require database and content updates to perform URL lookups. If the appliances don't have an active internet connection, you must manually download the updates to a server on your network and import the updates into each M-600 or M-700 appliance in the PAN-DB private cloud using SCP. In addition, the appliance must be able to obtain the seed database and any other regular or critical content updates for the firewalls it services.
The URL lookup process is the same for firewalls in both private and public cloud deployments. However, in private cloud deployments, firewalls query servers in the PAN-DB private cloud. You'll need to specify the IP address or FQDN of each M-600 or M-700 server they can query to grant your firewalls access to the private cloud servers .
The M-600 and M-700 appliance use prepackaged server certificates to authenticate firewalls connecting to the PAN-DB private cloud. You can't import or use another server certificate for authentication. If you change the hostname on an appliance, the appliance automatically generates a new set of certificates to authenticate the firewalls.
PAN-DB Private Cloud Appliances
How PAN-DB Private Cloud Works
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
To deploy a PAN-DB private cloud, you need one or more M-600 or M-700 appliances . Both appliances ship in Panorama mode, but to be deployed as a PAN-DB private cloud, you must configure them to operate in PAN-URL-DB mode. In PAN-URL-DB mode, the appliance provides URL categorization services for enterprises that do not want to use the PAN-DB public cloud.
The M-600 and M-700 appliance, when deployed as a PAN-DB private cloud, uses two ports—MGT (Eth0) and Eth1; Eth2 is not available for use. The management port is used for administrative access to the appliance and for obtaining the latest content updates from the PAN-DB public cloud or a server on your network. For communication between the PAN-DB private cloud and the firewalls on your network, you can use the MGT port or Eth1.
The M-200 appliance cannot be deployed as a PAN-DB private cloud.
The M-600 and M-700 appliance in PAN-URL-DB mode:
- Does not have a web interface, it only supports a command line interface (CLI).
- Cannot be managed by Panorama.
- Cannot be deployed in a high availability pair.
- Does not require a URL Filtering license. The firewalls, must have a valid PAN-DB URL Filtering license to connect with and query the PAN-DB private cloud.
- Ships with a set of default server certificates that are used to authenticate the firewalls that connect to the PAN-DB private cloud. You cannot import or use another server certificate for authenticating the firewalls. If you change the hostname on either appliance, the appliance automatically generates a new set of certificates to authenticate the firewalls that it services.
- Can be reset to Panorama mode only. If you want to deploy the appliance as a Dedicated Log Collector, switch to Panorama mode, and then set it in Log Collector mode.
Set Up PAN-DB Private Cloud
PAN-DB Private Cloud Appliances
Configure the PAN-DB Private Cloud
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
To deploy one or more M-600 or M-700 appliances as a PAN-DB private cloud within your network or data center, you must complete the following tasks:
Configure the PAN-DB Private Cloud
Configure Firewalls to Access the PAN-DB Private Cloud
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
- Rack mount the M-600 or M-700 appliance.
Refer to the rack installation instructions in the relevant hardware reference guide .
- Register the appliance.
- Perform initial configuration of the appliance.
The M-600 and M-700 appliances, in PAN-DB mode, use two ports—MGT (Eth0) and Eth1; Eth2 is not used in PAN-DB mode. The management port is used for administrative access to the appliance and for obtaining the latest content updates from the PAN-DB public cloud. For communication between the appliance (PAN-DB server) and the firewalls on the network, you can use the MGT port or Eth1.
- Connect to the appliance in one of the following ways:
- Attach a serial cable from a computer to the Console port on the appliance and connect using a terminal emulation software (9600-8-N-1).
- Attach an RJ-45 Ethernet cable from a computer to the MGT port on the appliance. From a browser, go to https://192.168.1.1. Enabling access to this URL might require changing the IP address on the computer to an address in the 192.168.1.0 network (for example, 192.168.1.2).
- When prompted, log in to the appliance. Log in using the default username and password (admin/admin). The appliance will begin to initialize.
- Configure network access settings including the IP address for the MGT interface:
Use the following CLI command: set deviceconfig system ip-address <server-IP> netmask <netmask> default-gateway <gateway-IP> dns-setting servers primary <DNS-IP> .
Descriptions of the variables:
- <server-IP> is the IP address you want to assign to the management interface of the server
- <netmask> is the subnet mask
- <gateway-IP> is the IP address of the network gateway, and <DNS-IP> is the IP address of the primary DNS server
- <DNS-IP> is the IP address of the DNS server
- Configure network access settings, including the IP address for the Eth1 interface.
Use the following command: set deviceconfig system eth1 ip-address <server-IP> netmask <netmask> default-gateway <gateway-IP> dns-setting servers primary <DNS-IP> .
- Save your changes to the PAN-DB server.
Use the commit command.
- Switch to PAN-DB private cloud mode.
You can switch from Panorama mode to PAN-DB mode and back; and from Panorama mode to Log Collector mode and back. Switching directly from PAN-DB mode to Log Collector mode or vice versa is not supported. Switching operational modes triggers a data reset. Except for the Management Access settings, all existing configurations and logs are deleted upon restart.
- To switch to PAN-DB mode, use the request system system-mode pan-url-db command.
- To verify the mode switch, use the show system info command.
If you've successfully switched to PAN-DB private cloud mode, the system-mode field displays PAN-URL-DB .
admin@M-600> show system info
hostname: M-600
ip-address: 1.2.3.4
public-ip-address:
netmask: 255.255.255.0
default-gateway: 1.2.3.1
ipv6-address: unknown
ipv6-link-local-address: fe80:00/64
ipv6-default-gateway:
mac-address: 00:56:90:e7:f6:8e
time: Mon Apr 27 13:43:59 2015
uptime: 10 days, 1:51:28
family: m
model: M-600
serial: 0073010000xxx
sw-version: 7.0.0
app-version: 492-2638
app-release-date: 2015/03/19 20:05:33
av-version: 0
av-release-date: unknown
wf-private-version: 0
wf-private-release-date: unknown
wildfire-version: 0
wildfire-release-date:
logdb-version: 7.0.9
platform-family: m
pan-url-db: 20150417-220
system-mode: Pan-URL-DB
operational-mode: normal
licensed-device-capacity: 0
device-certificate-status: None
- To check the version of the cloud database on the appliance, use the show pan-url-cloud-status command.
The pan-url-db field in the system-info display contains the same information.
- Install content and database updates.
The appliance only stores the version of the content that is currently running and one earlier version.
Pick one of the following installation methods:
- If the PAN-DB server has direct Internet access, use the following commands:
- To check whether a new version is published: request pan-url-db upgrade check
- To check the version that is currently installed on your server: request pan-url-db upgrade info .
- To download the latest version: request pan-url-db upgrade download latest .
To install the latest version: request pan-url-db upgrade install <version latest | file> .
- To schedule the appliance to automatically check for updates: set deviceconfig system update-schedule pan-url-db recurring weekly action download-and-install day-of-week <day of week> at <hr:min> .
- If the PAN-DB server is offline, access Palo Alto Networks customer support website to download and save content updates to an SCP server on your network. You can then import and install the updates using the following commands:
- scp import pan-url-db remote-port <port-number> from username@host:path
- request pan-url-db upgrade install file <filename>
- Set up administrative access to the PAN-DB private cloud.
The appliance has a default admin account. Any additional administrative users that you create can either be superusers (with full access) or superusers with read-only access.
PAN-DB private cloud does not support the use of RADIUS VSAs. If the VSAs used on the firewall or Panorama are used for enabling access to the PAN-DB private cloud, an authentication failure will occur.
- To set up a local administrative user on the PAN-DB server, use the following commands:
1. configure
2. set mgt-config users <username> permissions role-based <superreader | superuser> yes
3. set mgt-config users <username> password
4. Enter password:xxxxx
5. Confirm password:xxxxx
6. commit
- To set up an administrative user with RADIUS authentication, use the following commands:
1. To create a RADIUS server profile: set shared server-profile radius <server_profile_name> server <server_name> ip-address <ip_address> port <port_no> secret <shared_password> .
2. To create an Authentication profile: set shared authentication-profile <auth_profile_name> user-domain <domain_name_for_authentication> allow-list <all> method radius server-profile <server_profile_name> .
3. To attach the Authentication profile to a user: set mgt-config users <username> authentication-profile <auth_profile_name> .
4. To commit your changes: commit .
- To view the list of users, use the show mgt-config users command.
Configure Firewalls to Access the PAN-DB Private Cloud
Configure the PAN-DB Private Cloud
Configure Authentication with Custom Certificates on the PAN-DB Private Cloud
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
When using the PAN-DB public cloud, each firewall accesses the PAN-DB servers in the AWS cloud to download the list of eligible servers to which it can connect for URL lookups. With the PAN-DB private cloud, you must configure the firewalls with a (static) list of your PAN-DB private cloud servers that will be used for URL lookups. The list can contain up to 20 entries; IPv4 addresses, IPv6 addresses, and FQDNs are supported. Each entry on the list— IP address or FQDN—must be assigned to the management port or eth1 of the PAN-DB server.
- From the PAN-OS CLI , add a list of static PAN-DB private cloud servers used for URL lookups.
- Use the following CLI command to add the IP addresses of the private PAN-DB servers:
> configure
# set deviceconfig setting pan-url-db cloud-static-list <IP addresses>
Alternatively, in the web interface for each firewall, select DeviceSetupContent-ID , edit the URL Filtering section, and then enter the IP addresses or FQDNs of the PAN-DB servers. The list must be comma-separated.
- To delete the entries for the private PAN-DB servers, use the following CLI command:
# delete deviceconfig setting pan-url-db cloud-static-list <IP addresses>
Deleting the list of private PAN-DB servers triggers a reelection process on the firewall. The firewall first checks for the list of PAN-DB private cloud servers and when it can't find one, the firewall accesses the PAN-DB servers in the AWS cloud to download the list of eligible servers to which it can connect.
- Enter # commit to save your changes.
- To verify that the change is effective, use the following CLI command on the firewall:
- > show url-cloud status
- Cloud status: Up
URL database version: 20150417-220
Configure Authentication with Custom Certificates on the PAN-DB Private Cloud
Configure Firewalls to Access the PAN-DB Private Cloud
|
Where can I use this? |
What do I need? |
|
Note: Legacy URL filtering licenses are discontinued, but active legacy licenses are still supported. |
By default, a PAN-DB server uses predefined certificates for mutual authentication to establish the SSL connections used for management access and interdevice communication. However, you can configure authentication using custom certificates instead. Custom certificates allow you to establish a unique chain of trust to ensure mutual authentication between your PAN-DB server and firewalls. In the case of a PAN-DB private cloud, the firewall acts as the client and the PAN-DB server acts as the server.
- Obtain key pairs and certificate authority (CA) certificates for the PAN-DB server and firewall.
- Import the CA certificate to validate the certificate on the firewall.
- Log in to the CLI on the PAN-DB server and enter configuration mode.
admin@M-600> configure
- Use TFTP or SCP to import the CA certificate.
admin@M-600# {tftp | scp} import certificate from <value> file <value> remote-port <1-65535> source-ip <ip/netmask> certificate-name <value> passphrase <value> format {pkcs12 | pem}
- Use TFTP or SCP to import the key pair that contains the server certificate and private key for the private cloud appliance.
admin@M-600# {tftp | scp} import keypair from <value> file <value> remote-port <1-65535> source-ip <ip/netmask> certificate-name <value> passphrase <value> format {pkcs12 | pem}
- Configure a certificate profile that includes the root CA and intermediate CA. This certificate profile defines the device authentication between the PAN-DB server and the firewall.
- In the CLI of the PAN-DB server, enter configuration mode.
admin@M-600> configure
- Name the certificate profile.
admin@M-600# set shared certificate-profile <name>
- ( Optional ) Set the user domain.
admin@M-600# set shared certificate-profile <name> domain <value>
- Configure the CA.
Default-ocsp-url and ocsp-verify-cert are optional parameters.
admin@M-600# set shared certificate-profile <name> CA <name>
admin@M-600# set shared certificate-profile <name> CA <name> [default-ocsp-url <value>]
admin@M-600# set shared certificate-profile <name> CA <name> [ocsp-verify-cert <value>]
- Configure an SSL/TLS service profile for the appliance. This profile defines the certificate and protocol range that PAN-DB and client devices use for SSL/TLS services.
- Identify the SSL/TLS service profile.
admin@M-600# set shared ssl-tls-service-profile <name>
- Select the certificate.
admin@M-600# set shared ssl-tls-service-profile <name> certificate <value>
- Define the SSL/TLS range.
PAN-OS 8.0 and later releases support TLSv1.2 and later TLS versions only. You must set the max version to TLS 1.2 or max .
admin@M-600# set shared ssl-tls-service-profile <name> protocol-settings min-version {tls1-0 | tls1-1 | tls1-2
admin@M-600# set shared ssl-tls-service-profile <name> protocol-settings max-version {tls1-0 | tls1-1 | tls1-2 | max
- Configure secure server communication on PAN-DB.
- Set the SSL/TLS service profile. This profile applies to all SSL connections between PAN-DB and firewalls.
admin@M-600# set deviceconfig setting management secure-conn-server ssl-tls-service-profile <ssltls-profile>
- Set the certificate profile.
admin@M-600# set deviceconfig setting management secure-conn-server certificate-profile <certificate-profile>
- Set the disconnect wait time. This is the number of minutes that PAN-DB waits before breaking and reestablishing the connection with its firewall (range is 0 to 44,640).
admin@M-600# set deviceconfig setting management secure-conn-server disconnect-wait-time <0-44640
- Import the CA certificate to validate the certificate for the appliance.
- Log in to the firewall web interface.
- Import the CA certificate .
- Configure a local or a SCEP certificate for the firewall.
- If you are configuring a local certificate, import the key pair for the firewall .
- If you are configuring a SCEP certificate, configure a SCEP profile .
- Configure the certificate profile for the firewall. You can configure this on each firewall individually or you can push the configuration from Panorama to the firewalls as part of a template.
- Select DeviceCertificate ManagementCertificate Profile for firewalls or PanoramaCertificate ManagementCertificate Profile for Panorama.
- Configure a Certificate Profile .
- Deploy custom certificates on each firewall. You can either deploy certificates centrally from Panorama or configure them manually on each firewall.
- Log in to the firewall web interface.
- Select DeviceSetupManagement for a firewall or PanoramaSetupManagement for Panorama and Edit the Secure Communication settings.
- Select the Certificate Type , Certificate , and Certificate Profile from the respective drop-downs.
- In the Customize Communication settings, select PAN-DB Communication .
- Click OK .
- Commit your changes.
After committing your changes, the firewalls don't terminate their current sessions with the PAN-DB server until after the Disconnect Wait Time . The disconnect wait time begins counting down after you enforce the use of custom certificates in the next step.
- Enforce custom certificate authentication.
- Log in to the CLI on the PAN-DB server and enter configuration mode.
admin@M-600> configure
- Enforce the use of custom certificates.
admin@M-600# set deviceconfig setting management secure-conn-server disable-pre-defined-cert yes
- After committing this change, the disconnect wait time begins counting down (if you configured this setting on PAN-DB). When the wait time ends, PAN-DB and its firewall connect using only the configured certificates.
- You have two choices when adding new firewalls or Panorama to your PAN-DB private cloud deployment.
- If you did not enable Custom Certificates Only , you can add a new firewall to the PAN-DB private cloud and then deploy the custom certificate.
- If you enabled Custom Certificates Only on the PAN-DB private cloud, you must deploy the custom certificates on the firewalls before connecting them to the PAN-DB private cloud.