Palo Alto Networks User-ID: Agentless vs. Agent-Based Deep Dive for PCNSE
User-ID is a cornerstone technology within the Palo Alto Networks Strata security platform, enabling Next-Generation Firewalls (NGFWs) to enforce security policies based on users and groups rather than just IP addresses. This provides granular visibility into application usage, threat exposure, and network activity tied to specific users, significantly enhancing security posture and simplifying incident response. PAN-OS, the operating system powering Palo Alto Networks firewalls, offers two primary methods for collecting user-to-IP address mappings: Agentless User-ID and Agent-Based User-ID. Understanding the intricacies, deployment models, and best practices for each is crucial for effective network security and for success in the PCNSE certification.
Core User-ID Components and Concepts in PAN-OS
Before diving into agentless versus agent-based methods, it's important to understand key User-ID components within the Palo Alto Networks ecosystem:
- User-ID Agent: This term can refer to the Windows-based User-ID agent software, the PAN-OS integrated agent (for agentless functions), or the Terminal Services (TS) agent. Context is important.
- User Mapping: The process of associating an IP address with a username. These mappings are stored in a table on the PAN-OS firewall.
- Group Mapping: The process of retrieving user group information from directory services (e.g., Active Directory, LDAP) to use in policies. This is configured separately but relies on User-ID.
- PAN-OS Data Plane: Enforces policies using the User-IP mappings.
- PAN-OS Management Plane: Responsible for collecting, managing, and sharing User-IP mappings (especially in agentless setups or when Panorama is involved).
- Service Account: A dedicated account with necessary permissions is required for User-ID to query directory services or read event logs. Permissions are critical for successful operation.
Agentless User-ID in PAN-OS
Agentless User-ID allows the PAN-OS firewall (or Panorama for centralized collection) to directly gather User-IP mapping information without requiring dedicated software to be installed on a separate server for the primary collection task. The "agent" functionality is integrated into PAN-OS.
Mechanisms for Agentless User-ID:
PAN-OS supports several methods for agentless User-ID mapping:
-
Server Monitoring (Windows Domain Controllers):
The firewall directly queries Windows Domain Controllers (DCs) for security event logs that indicate user logins (e.g., Event ID 4624 for successful logon, 4768, 4769 for Kerberos events).
- Protocols: Windows Management Instrumentation (WMI) or WinRM (Windows Remote Management). WinRM is generally preferred for performance and security.
-
Configuration:
Device > User Identification > User Mapping > Palo Alto Networks User-ID Agent Setup > Server Monitoring. You'll configure DC server IP addresses and credentials for a service account. - Service Account Permissions: Requires permissions to read security event logs and be a member of "Event Log Readers" and "Distributed COM Users" (for WMI) or "Remote Management Users" (for WinRM).
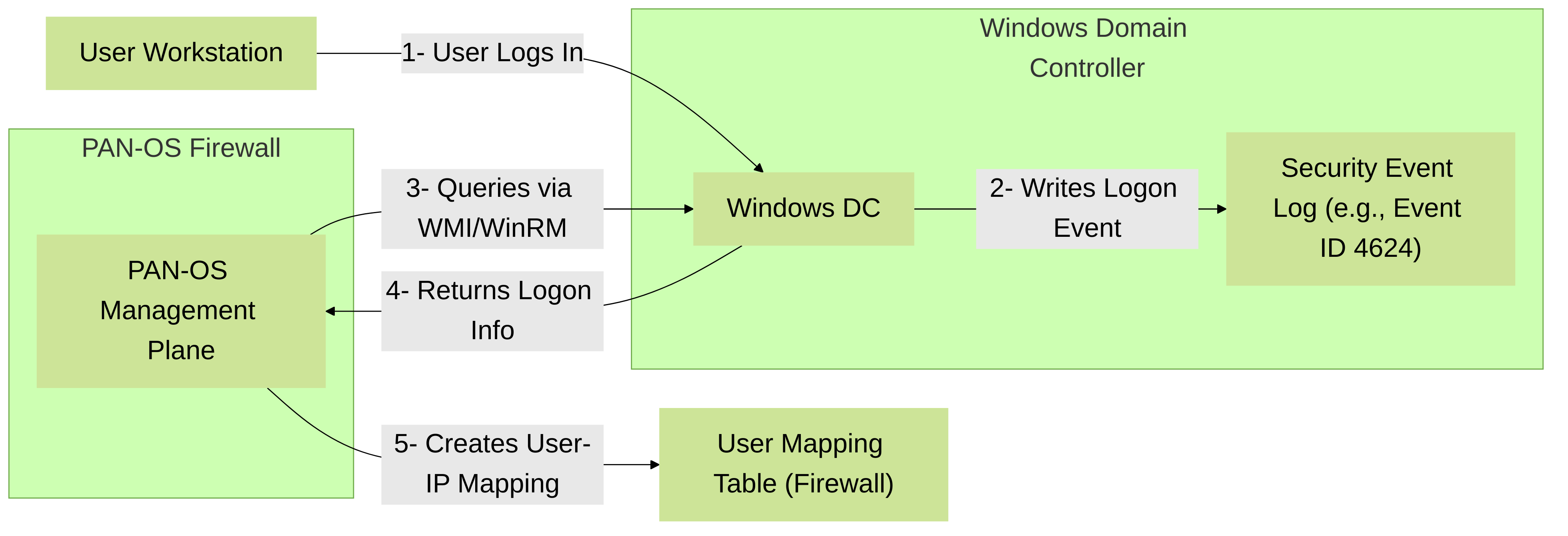
Figure 1: Agentless User-ID using Server Monitoring. The PAN-OS firewall directly queries the Domain Controller for user logon events.
-
Captive Portal:
When a user's identity cannot be determined passively, Captive Portal can actively prompt the user for credentials.
- Use Cases: Guest networks, BYOD environments, or when passive methods fail.
-
Modes:
- Transparent Mode: Users are prompted for credentials without redirection.
- Redirect Mode: Users are redirected to a web form for authentication.
- Authentication: Can use local user database, LDAP, RADIUS, Kerberos, SAML.
-
Configuration:
Device > User Identification > Captive Portal Settings. Policies trigger Captive Portal.
- GlobalProtect: GlobalProtect clients (VPN, endpoint protection) automatically provide user and device information to the firewall/Panorama upon connection. This is a highly reliable source of User-ID.
-
VM Information Sources:
PAN-OS can integrate with virtualization and cloud platforms to gather IP-to-tag mappings, which can include user information if properly tagged.
- Supported Platforms: VMware vCenter/NSX, AWS VPC, Google Cloud Platform (GCP), Microsoft Azure.
- Primary Use: Mapping IP addresses to VM tags (e.g., VM name, OS), which can be used in Dynamic Address Groups. Can indirectly aid User-ID if tags include user context.
-
Syslog Integration:
The firewall can be configured to parse syslog messages from other network access control systems (e.g., 802.1X authenticators, VPN concentrators, wireless controllers) that generate logs containing User-IP mapping information.
-
Configuration:
Device > User Identification > User-ID Agents > Syslog Filters. Requires defining regex patterns to parse the syslog messages.
-
Configuration:
-
XML API / PAN-OS API:
External systems can push User-IP mappings to the firewall using the PAN-OS XML API or REST API. This is common for custom integrations or third-party NAC solutions.
<uid-message> <type>update</type> <payload> <login> <entry name="domain\username" ip="192.168.1.100" timeout="3600"/> </login> </payload> </uid-message> - Client Probing (Part of Agentless): While often associated with the Windows User-ID Agent, PAN-OS can perform limited client probing (NetBIOS, WMI) if Server Monitoring doesn't provide a mapping for an IP. This is less common as a primary method.
-
XFF (X-Forwarded-For) Headers:
If traffic passes through a proxy server before reaching the firewall, the proxy can insert the original client IP address and username (if known) into XFF headers. The firewall can parse these headers.
-
Configuration:
Device > User Identification > User Mapping > Palo Alto Networks User-ID Agent Setup > XFF Headers. - Trust: Only enable from trusted proxy IP addresses.
-
Configuration:
Advantages of Agentless User-ID:
- Simplified Deployment: No separate software installation is required on dedicated servers for basic DC monitoring. Configuration is done directly on the PAN-OS firewall or Panorama.
- Centralized Management: User-ID configuration and monitoring are integrated into the PAN-OS/Panorama GUI.
- Reduced Maintenance: Fewer components to patch and maintain (no separate agent OS/software).
- Lower Initial Overhead: Can be quicker to set up for smaller environments with few DCs.
Considerations for Agentless User-ID:
- Management Plane Load: Direct querying of DCs (especially via WMI) can place a significant load on the firewall's management plane, particularly in large environments with many DCs or high logon rates. This can impact GUI responsiveness, commit times, and other management tasks.
- Scalability Limits: Palo Alto Networks generally recommends agentless server monitoring for environments with fewer than 10-15 Domain Controllers and a moderate number of users. WinRM is more scalable than WMI.
- Network Traffic: WMI/WinRM traffic between firewalls and all monitored DCs can be substantial.
- Permissions Complexity: Ensuring the service account has the correct, consistent permissions across all DCs can be challenging.
- Feature Limitations: Agentless User-ID typically does not support advanced features like Credential Phishing Prevention or some sophisticated syslog parsing scenarios which the dedicated Windows User-ID agent can handle.
- Firewall as Single Point of Collection (per firewall): If a firewall is performing agentless collection for its own User-ID needs, it becomes a critical point for that data. Panorama can centralize this.
> show system resources follow | match useridd
Agent-Based User-ID (Windows User-ID Agent)
Agent-Based User-ID involves installing a dedicated Palo Alto Networks User-ID agent software package on a Windows server (physical or virtual) within the network. This agent is responsible for collecting User-IP mapping information from various sources and then forwarding it to one or more PAN-OS firewalls.
Primary Component: Windows User-ID Agent
- Software: A downloadable executable from the Palo Alto Networks support portal. Installs as a service on a Windows Server (member server, not typically a DC itself).
- Function: Collects mappings, filters them, and sends them to configured firewalls.
- Communication with Firewalls: Uses TCP port 5007 (by default) to send User-IP mapping updates to the PAN-OS firewalls. Firewalls must be configured to listen to the agent.
Mechanisms for Agent-Based User-ID (via Windows Agent):
-
Security Log Monitoring (DCs):
The Windows User-ID agent monitors security event logs on configured Windows Domain Controllers. This is similar to the agentless method but performed by the dedicated agent software.
- Protocols: WMI or WinRM from the agent server to the DCs.
- Efficiency: The agent can be more efficient as it's dedicated to this task and can be placed closer to DCs.
-
Client Probing:
The agent can actively probe client systems (using NetBIOS, WMI) to determine the logged-on user if other methods don't provide a mapping. This is useful for non-domain clients or when event logs are missed.
- Configurable: Probing intervals and methods can be tuned.
- Domain Controller Probing (Session Information): The agent can query DCs for active user sessions. This is less common now with robust event log monitoring.
- Exchange Server Monitoring: The agent can monitor Microsoft Exchange Server logs to map users to IPs based on email client activity (e.g., Outlook Web Access, ActiveSync).
- eDirectory Monitoring: The agent can monitor Novell eDirectory logs for user login events.
- Syslog Integration: The Windows User-ID agent can listen for syslog messages from various sources (e.g., VPNs, WLAN controllers, NAC) and parse them to extract User-IP mappings. It often has more flexible parsing options than the firewall's integrated syslog listener.
- XML API Forwarding: The agent can receive User-IP mappings via an XML API from third-party systems and then forward them to the firewalls.
- Credential Phishing Prevention: A key feature enabled by the Windows User-ID Agent. It allows the agent to check submitted corporate credentials against known valid credentials (via AD integration). If a user submits corporate credentials to a site categorized as "phishing" by PAN-DB, an alert can be generated or access blocked. This requires GlobalProtect on endpoints for credential submission.
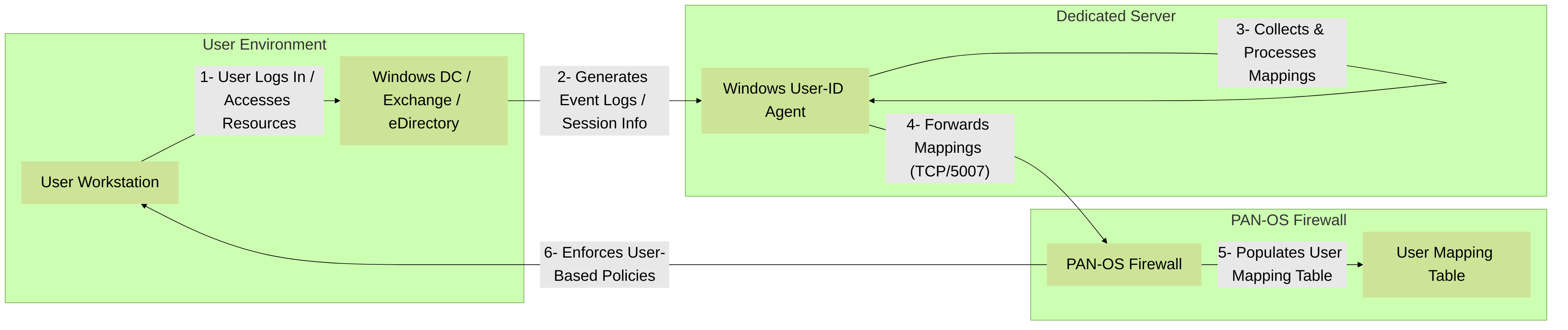
Figure 2: Agent-Based User-ID with a Windows User-ID Agent. The agent collects data from sources like Domain Controllers and forwards it to the PAN-OS firewall.
Configuring Firewalls to Use the Windows User-ID Agent:
-
Navigate to
Device > User Identification > User-ID Agents. - Add the IP address and port (default 5007) of the Windows server running the User-ID agent.
- The firewall will then connect to the agent to receive mappings.
Advantages of Agent-Based User-ID:
- Offloads Processing: Shifts the User-ID collection load from the firewall's management plane to the dedicated agent server, improving firewall performance, especially in large environments.
- Enhanced Scalability: Better suited for large, distributed, or multi-domain environments. A single agent can monitor many DCs and serve many firewalls. Multiple agents can be deployed for redundancy and load distribution.
- Advanced Feature Support: Enables features like Credential Phishing Prevention and potentially more robust syslog parsing.
- Optimized Communication: The agent can be placed strategically within the network (e.g., closer to DCs) to optimize WMI/WinRM traffic. Communication between the agent and firewalls is a consolidated stream.
- Resilience: Multiple User-ID agents can be configured on the firewall for redundancy.
Considerations for Agent-Based User-ID:
- Additional Software: Requires installation, configuration, and maintenance of the User-ID agent software on a Windows server (OS patching, agent updates).
- Server Resources: The Windows server hosting the agent needs adequate CPU, memory, and network resources.
- Deployment Complexity: Adds another component to the overall architecture.
- Potential Single Point of Failure (if not redundant): If only one agent is deployed and it fails, User-IP mapping updates will stop until it's restored (though existing mappings on the firewall will persist until they time out). High availability (HA) for User-ID agents is a best practice.
Palo Alto Networks Terminal Services (TS) Agent
In environments with multi-user systems like Microsoft Remote Desktop Session Hosts (RDSH), Citrix XenApp/XenDesktop, or Linux servers where multiple users share a single IP address, standard User-ID methods are insufficient. The Palo Alto Networks Terminal Services (TS) Agent addresses this.
- Function: Assigns a unique range of TCP/UDP ports to each user session on a multi-user server. It then reports the server's IP address, the user, and their allocated port range to the PAN-OS firewall or User-ID agent.
- Policy Enforcement: Security policies can then be written to include source user AND source port to differentiate traffic from different users on the same server.
- Installation: Installed directly on the terminal servers (Windows, Linux, macOS).
- Reporting: Can send mappings directly to firewalls or to a Windows User-ID agent for redistribution.
- Port Allocation: Admins define the starting port number and the number of ports per user. PAN-OS uses this information to map traffic to specific users. Example: User A gets ports 20000-20099, User B gets 20100-20199 on server 10.1.1.5. Traffic from 10.1.1.5:20050 is mapped to User A.
_Agent_ope_May_19_2025_07-36PM.png)
Figure 3: Palo Alto Networks Terminal Services (TS) Agent operation. The TS Agent allocates port ranges to individual user sessions on a shared server, allowing the firewall to differentiate user traffic.
Comparison Table: Agentless vs. Agent-Based User-ID (Palo Alto Networks Context)
| Feature/Aspect | Agentless User-ID (PAN-OS Integrated) | Agent-Based User-ID (Windows Agent) |
|---|---|---|
| Primary Collection Mechanism | Firewall/Panorama directly queries sources (e.g., DCs via WMI/WinRM). | Dedicated Windows User-ID Agent software queries sources and forwards to firewalls. |
| Scalability (DCs/Users) | Lower; recommended for <10-15 DCs. Performance sensitive to management plane load. WinRM improves scalability over WMI. | Higher; designed for large, complex environments with many DCs and users. Can scale with multiple agents. |
| Firewall Resource Impact | Higher impact on firewall's Management Plane CPU/memory. | Minimal impact on firewall's Management Plane; processing is offloaded to the agent server. |
| Deployment Complexity | Simpler initial setup, configured directly on firewall/Panorama. | Requires dedicated Windows server, agent installation, and configuration. |
| Maintenance | Primarily firewall/Panorama OS updates. | Agent software updates, Windows server OS patching and maintenance. |
| Supported User-ID Sources | Server Monitoring (DCs), Captive Portal, GlobalProtect, XML API, Syslog (firewall parsed), VM Info Sources, XFF. | Server Monitoring (DCs), Client/DC Probing, Exchange Monitoring, eDirectory Monitoring, Syslog (agent parsed), XML API. |
| Credential Phishing Prevention | Not directly supported by agentless server monitoring. Requires agent for credential checking. | Supported. Agent facilitates checking submitted credentials. |
| Syslog Parsing Flexibility | Basic to moderate via firewall's syslog filters. | Potentially more advanced and flexible parsing capabilities on the agent. |
| Redundancy | Firewall HA provides redundancy for the collection process if managed by that HA pair. Panorama can act as a central collector. | Achieved by deploying multiple User-ID agents; firewalls can connect to multiple agents. |
| Network Traffic | WMI/WinRM traffic from each firewall/Panorama to multiple DCs. | WMI/WinRM traffic from agent server(s) to DCs. Consolidated mapping stream from agent(s) to firewalls. |
Decision Criteria for Palo Alto Networks Environments
Choosing between agentless and agent-based User-ID in a Palo Alto Networks deployment depends on several factors:-
Environment Size & Complexity:
- Small to Medium (e.g., <10-15 DCs, <5,000 users): Agentless User-ID (using WinRM for server monitoring) might be sufficient if the firewall's management plane has capacity.
- Large/Enterprise (e.g., >15 DCs, >5,000 users, multiple domains/forests): Agent-Based User-ID is generally recommended to offload processing and improve scalability.
-
Number of Domain Controllers:
- Fewer DCs make agentless more manageable.
- A large number of DCs significantly increases the load for agentless methods; an agent provides a more scalable collection point.
-
Firewall Management Plane Resources:
-
If the firewall's management plane CPU is already heavily utilized, choose Agent-Based to avoid further impacting performance. Monitor
mp-cpuinshow system resources.
-
If the firewall's management plane CPU is already heavily utilized, choose Agent-Based to avoid further impacting performance. Monitor
-
Geographical Distribution:
- Centralized DCs: Agentless might work if firewalls have good connectivity.
- Distributed DCs/Firewalls: Strategically placed User-ID agents can optimize data collection by being closer to regional DCs and then sending consolidated updates to firewalls, potentially reducing WAN traffic compared to each firewall polling remote DCs. User-ID Redistribution via Panorama or dedicated agents also plays a role here.
-
Required Features:
- Credential Phishing Prevention: Requires the Windows User-ID Agent and GlobalProtect.
- Advanced Syslog Parsing: The Windows User-ID agent might offer more flexibility than the firewall's built-in syslog parser for complex log formats.
-
Administrative Overhead & Expertise:
- Agentless has less infrastructure to manage initially.
- Agent-based requires managing the agent server(s) but can simplify User-ID management at scale.
-
Existing Infrastructure:
- Availability of suitable Windows servers for deploying the User-ID agent.
-
Redundancy Requirements:
- Both can be made redundant. Agentless relies on firewall HA or Panorama. Agent-based allows multiple agents for firewalls to connect to.
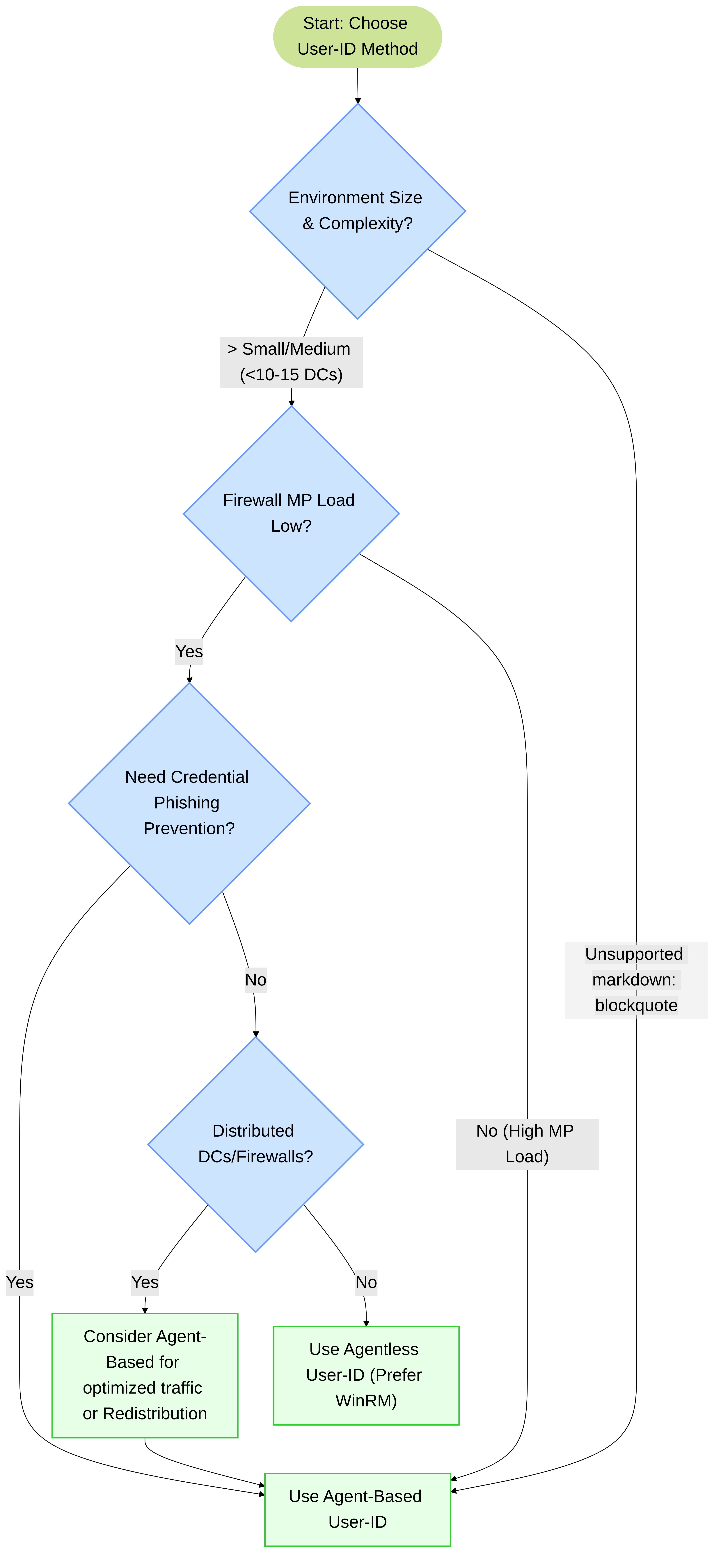
Figure 4: Simplified decision tree for choosing between Agentless and Agent-Based User-ID in Palo Alto Networks deployments.
Advanced User-ID Concepts in PAN-OS
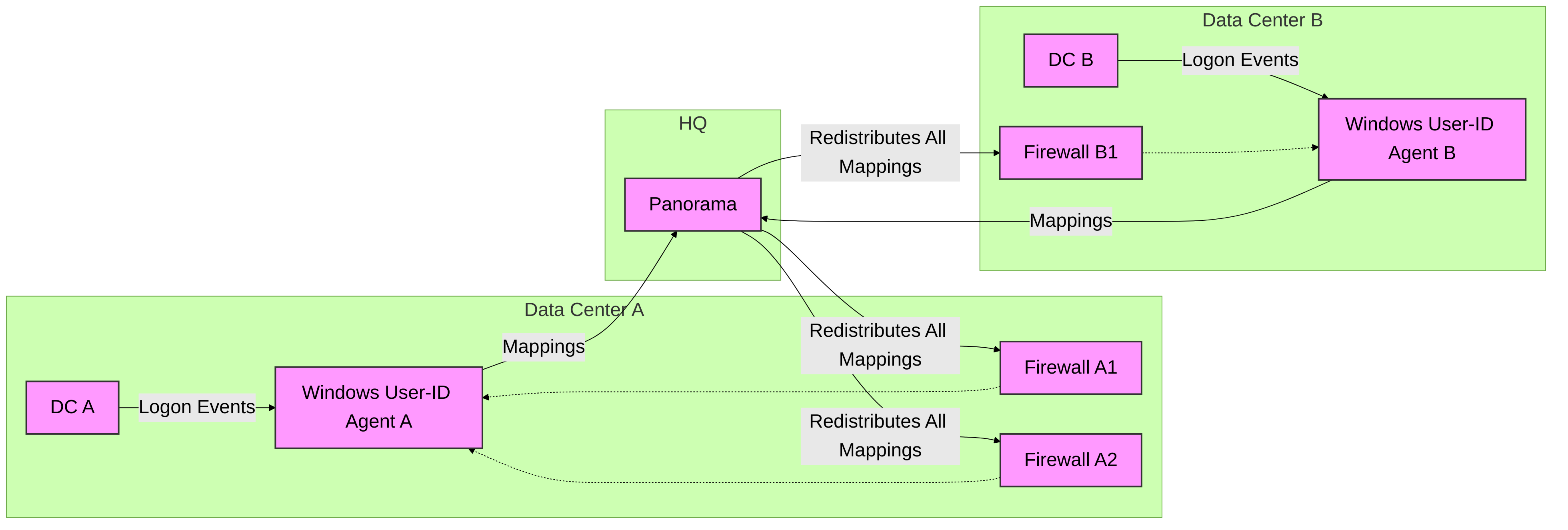
Beyond the basic collection methods, several advanced concepts enhance User-ID functionality:1. User-ID Redistribution
In large or distributed environments, collecting User-ID information at every firewall can be inefficient. Redistribution allows mappings collected by one source to be shared with others.
-
Panorama as Redistributor:
Panorama can collect User-IP mappings from multiple sources (firewalls configured for agentless collection, dedicated User-ID agents) and redistribute them to all managed firewalls. This centralizes collection and distribution.
- Configure User-ID settings within a Panorama Device Group Template Stack.
- Panorama itself can also have a User-ID Agent configuration to collect mappings.
- Dedicated User-ID Agents as Redistributors: A Windows User-ID agent can be configured to collect mappings from other User-ID agents (acting as a central hub) and then redistribute them to firewalls.
- Firewall-to-Firewall Redistribution (Limited): While not a primary method for large scale, firewalls can share mappings to a limited extent in certain HA or specific designs.