Palo Alto Networks: Mastering Authentication Policy and User-ID Data Redistribution
Introduction: The Synergy of Authentication Policy and User-ID
In the Palo Alto Networks security platform, identifying users and controlling their access to resources are fundamental to a robust security posture. **Authentication Policy** and **User-ID™ technology** work in tandem to achieve this. Authentication Policy actively challenges users for credentials, while User-ID passively maps IP addresses to usernames. The information gleaned from both, particularly authentication timestamps, is critical for maintaining consistent security enforcement, especially in distributed network environments. This guide delves into the intricacies of Palo Alto Networks Authentication Policy, the mechanisms of User-ID data redistribution (including authentication timestamps), their configuration, and their significance for the PCNSE certification.
Deep Dive: Palo Alto Networks Authentication Policy
Authentication Policy in PAN-OS™ allows administrators to define rules that require users to authenticate before accessing specific network resources or applications. This is an active authentication mechanism, distinct from the passive IP-to-user mapping provided by User-ID.
Key Components of an Authentication Policy Rule:
- Name: A descriptive name for the rule.
- Source Zones: The zone(s) from which the traffic originates.
- Source Addresses: Specific source IP addresses or address groups.
- Source Users: Usernames or group names. Can be `any`, `known-user`, or specific users/groups. If User-ID already knows the user, the policy might behave differently (e.g., skip re-authentication if timeouts align).
- Destination Zones: The zone(s) to which the traffic is destined.
- Destination Addresses: Specific destination IP addresses or address groups.
- Applications: Specific applications or application filters. Can be `any`.
- Services: Specific L4 ports/protocols (e.g., `tcp/443`, `application-default`).
- Action: Typically `Authentication Enforcement`.
- Authentication Enforcement Object: This object specifies the method of authentication and associated parameters.
Authentication Enforcement Object:
This is a critical part of the Authentication Policy. It defines:
-
Type:
- Web Form (Captive Portal): Redirects HTTP/HTTPS traffic to a web page for credential submission. This is the most common type.
- Browser Challenge (NTLM): For transparent authentication using NTLM (Windows environments). Less common now, often superseded by Kerberos SSO or SAML.
- Client Certificate Authentication: Uses client SSL/TLS certificates for authentication.
- Authentication Profile: Specifies the authentication service (e.g., LDAP, RADIUS, Kerberos, SAML, TACACS+, Local User Database) and server profiles. An **Authentication Sequence** can be used here to try multiple profiles in order.
-
Timeout Settings:
- Authentication Timeout (minutes): How long the user remains authenticated by this specific policy after successful authentication. This generates the crucial "authentication timestamp."
- Idle Timeout (minutes): If the user is inactive for this duration, they might be logged out, depending on overall User-ID settings.
- Redirect Host (for Captive Portal): The FQDN or IP address of the firewall interface (or external portal) serving the Captive Portal page.
- User-ID Timeout Settings within Authentication Profile: Note that the Authentication Profile itself has a "Timeout (min)" setting. This timeout specifically applies to how long the firewall considers the user authenticated against *that specific authentication server/method* for User-ID mapping purposes. This can interact with the Authentication Policy's own timeout.
How Authentication Policy Generates Timestamps:
When a user's traffic matches an Authentication Policy rule and they successfully authenticate via the specified Authentication Enforcement object (e.g., Captive Portal), PAN-OS creates an "authentication record" or "authentication entry." This entry includes:
- The user's IP address.
- The authenticated username.
- The virtual system (VSYS) if applicable.
- An authentication timestamp: This marks the time of successful authentication.
- The authentication timeout value: Derived from the Authentication Enforcement object. The firewall uses this to calculate when this specific authentication grant expires.
This authentication timestamp is vital. It signifies that, for the duration of the configured timeout, the firewall considers this user authenticated for the purpose of this policy. If User-ID redistribution is configured, this timestamp (along with the IP-user mapping) can be shared with other Palo Alto Networks firewalls.
Configuring Authentication Policy in PAN-OS:
Navigation:
Policies > Authentication
- Click "Add" to create a new rule.
- Fill in the general details (Name, Tags, Description).
- Specify Source and Destination criteria (Zones, Addresses).
- Under "User," specify `any`, `known-user`, or specific users/groups. Often, `any` is used to challenge unauthenticated users.
- Specify Services and Applications if needed.
- Under "Actions," set Action to `Authentication Enforcement`.
-
Select or create an "Authentication Enforcement" object.
-
If creating new:
Objects > Authentication > Authentication Enforcement. - Define Type (e.g., Web Form).
-
Select an Authentication Profile (e.g., one pointing to LDAP).
Objects > Authentication > Authentication Profile. - Set Authentication Timeout.
-
If creating new:
- Commit changes.
! Example: CLI representation of an Authentication Policy (conceptual) ! Actual CLI configuration involves setting objects and then referencing them in rules. ! Configure Authentication Profile (LDAP) set authentication profile MyLDAPProfile type ldap server-profile MyLDAPServerProfile login-attribute sAMAccountName timeout 90 set authentication profile MyLDAPProfile allow-list [ group-A group-B ] ! Configure Authentication Enforcement Object set authentication enforcement MyCaptivePortalAuth type web-form authentication-profile MyLDAPProfile auth-timeout 60 redirect-host firewall.company.com ! Configure Authentication Policy Rule set rulebase authentication rules AuthRuleToCorpWeb set from [ trust ] set to [ untrust ] set source [ any ] set destination [ CorpWebServer_IP ] set service [ service-http service-https ] set hip-profiles [ any ] set source-user [ any ] set action authentication-enforcement MyCaptivePortalAuth
User-ID™ Technology: The Foundation for Identity-Based Policies
User-ID is the Palo Alto Networks technology that enables the firewall to identify users and associate their network activity with their usernames, regardless of the device or IP address they use. This information is then used in policies (Security, QoS, Decryption, Authentication) and for logging/reporting.
Key User-ID Information Sources:
- Server Monitoring: User-ID agents (Windows-based or PAN-OS integrated) monitor security event logs from Active Directory Domain Controllers, Novell eDirectory servers, or Microsoft Exchange Servers to map users to IP addresses upon login.
- Authentication Policy / Captive Portal: As discussed, successful authentication via Authentication Policy (typically Captive Portal) directly provides an IP-to-user mapping and an authentication timestamp.
- GlobalProtect™: VPN users authenticating via GlobalProtect provide IP-to-user mappings.
- XML API: External systems can push IP-to-user mappings to the firewall or Panorama via the XML API.
- Client Probing: For Windows clients, if other methods fail, the firewall can attempt to probe the client for user information (NetBIOS or WMI). This is less common and has prerequisites.
- Syslog Integration: The firewall can parse syslog messages from other authentication sources (e.g., wireless controllers, 802.1X NAC solutions) that contain IP-to-user mapping information.
Once User-ID maps an IP address to a user, this mapping has a timeout. The default User-ID timeout is typically 45 minutes of inactivity, but this is configurable.
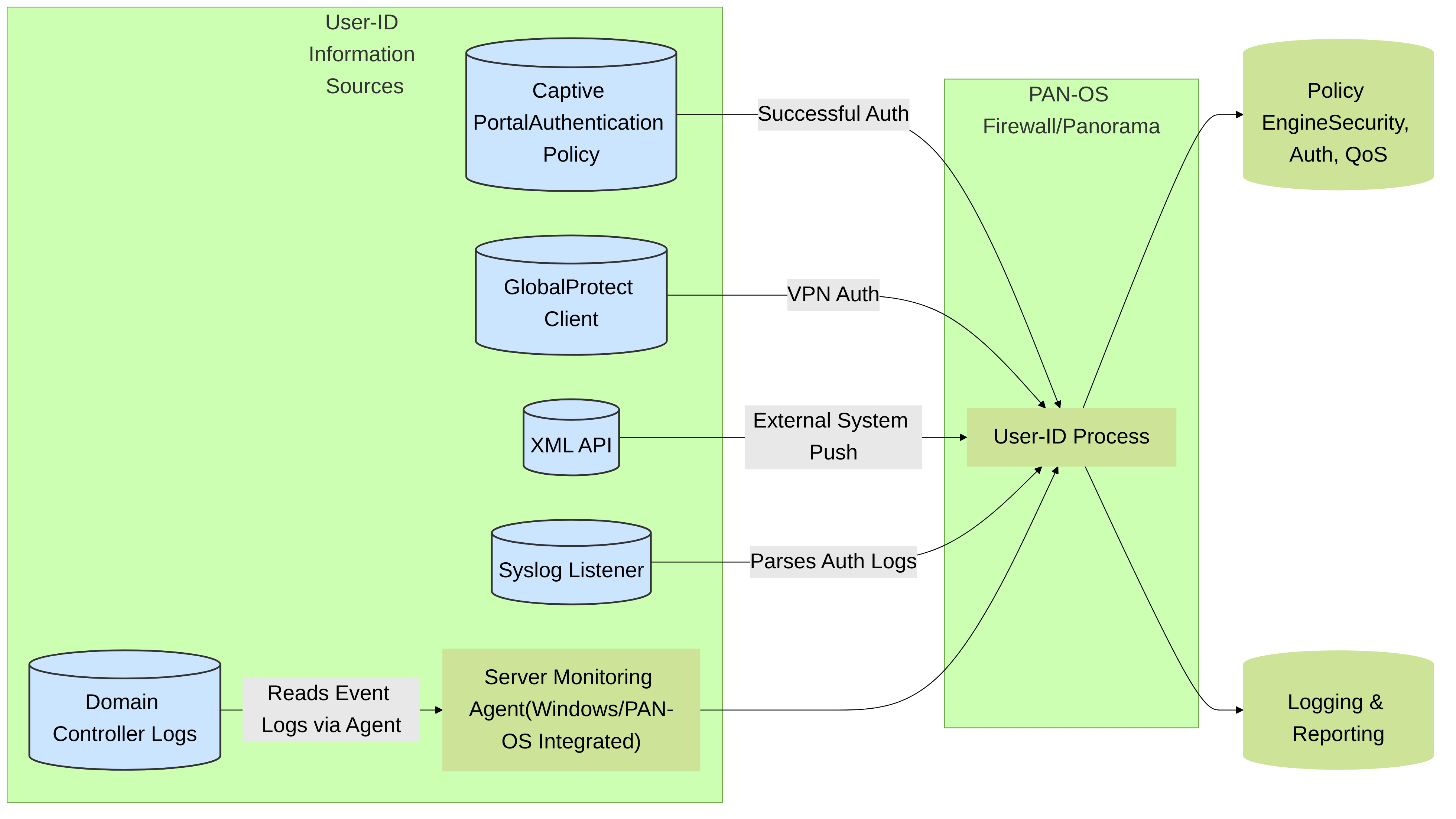
Palo Alto Networks User-ID information sources. The User-ID process on the firewall or Panorama collects mappings from various sources, including active authentication via Captive Portal, to enforce user-based policies.
The Crucial Role of Data Redistribution in Distributed Environments
In networks with multiple Palo Alto Networks firewalls, ensuring consistent user identification and authentication status across all enforcement points is paramount. If a user authenticates on Firewall A, they should ideally not be re-challenged immediately when their traffic traverses Firewall B for a different resource, assuming their session is still valid. This is where User-ID data redistribution comes into play.
What Data is Redistributed?
- IP-to-User Mappings: The core User-ID information.
- User-to-Group Mappings: Group membership information, typically learned from LDAP or Active Directory.
- Authentication Timestamps: Information about when a user last authenticated and the timeout associated with that authentication event (often originating from an Authentication Policy). This is key for consistent session handling.
- Dynamic Address Groups (DAGs) / Tags: IP addresses tagged with specific metadata, which can be used in dynamic policies.
Why Redistribute?
- Consistent Policy Enforcement: All firewalls have the same view of who is on the network, allowing for uniform application of user-based Security, QoS, and Decryption policies.
- Seamless User Experience: Reduces unnecessary re-authentication prompts, improving user productivity.
- Scalability: Allows User-ID information to be collected centrally (or by designated agents/firewalls) and distributed efficiently.
- Reduced Authentication Load: Prevents each firewall from needing to independently authenticate every user for every session if the information is already available.
Mechanisms for Redistribution:
Palo Alto Networks provides several ways to redistribute User-ID data:
-
Panorama™ Network and Security Management:
- Panorama can act as a central hub for User-ID information. Firewalls and User-ID Agents can send their mappings to Panorama.
- Panorama then redistributes this consolidated information to all managed firewalls that are configured to receive it.
- This is a common approach for large-scale deployments.
-
Firewall-to-Firewall Redistribution (User-ID Agent on PAN-OS):
- A PAN-OS firewall can be configured as a User-ID agent itself (an "integrated User-ID agent").
- One or more firewalls can be designated as "collectors" or "redistribution points."
- Other firewalls are configured as "clients" to receive User-ID information from these redistribution points.
- This typically requires configuring User-ID service on an interface and potentially service routes if the User-ID traffic needs to traverse different routing instances or secure fabric.
-
Windows-based User-ID Agent:
- The traditional Windows User-ID agent can also redistribute mappings to multiple firewalls. You configure the firewalls to connect to this agent.
- In larger environments, you might have multiple agents, and they can also share information amongst themselves or via Panorama.
Focus on Authentication Timestamp Redistribution:
When an Authentication Policy rule on Firewall A successfully authenticates a user, it creates an authentication entry with a timestamp and timeout. If Firewall A is configured to redistribute User-ID data (including authentication state) to Firewall B:
- Firewall A sends the IP-user mapping along with the authentication timestamp information (original authentication time, timeout duration) to Firewall B.
-
Firewall B receives this information. If a user, already authenticated on Firewall A, now sends traffic through Firewall B that would normally trigger an Authentication Policy on Firewall B:
- Firewall B checks its local User-ID cache (which includes the redistributed data).
- If it finds a valid, unexpired authentication timestamp for that user's IP address, it may honor this existing authentication and *not* re-challenge the user.
- The decision to honor depends on Firewall B's own Authentication Policy configuration (e.g., if its policy requires a different, stronger authentication method, it might still challenge).
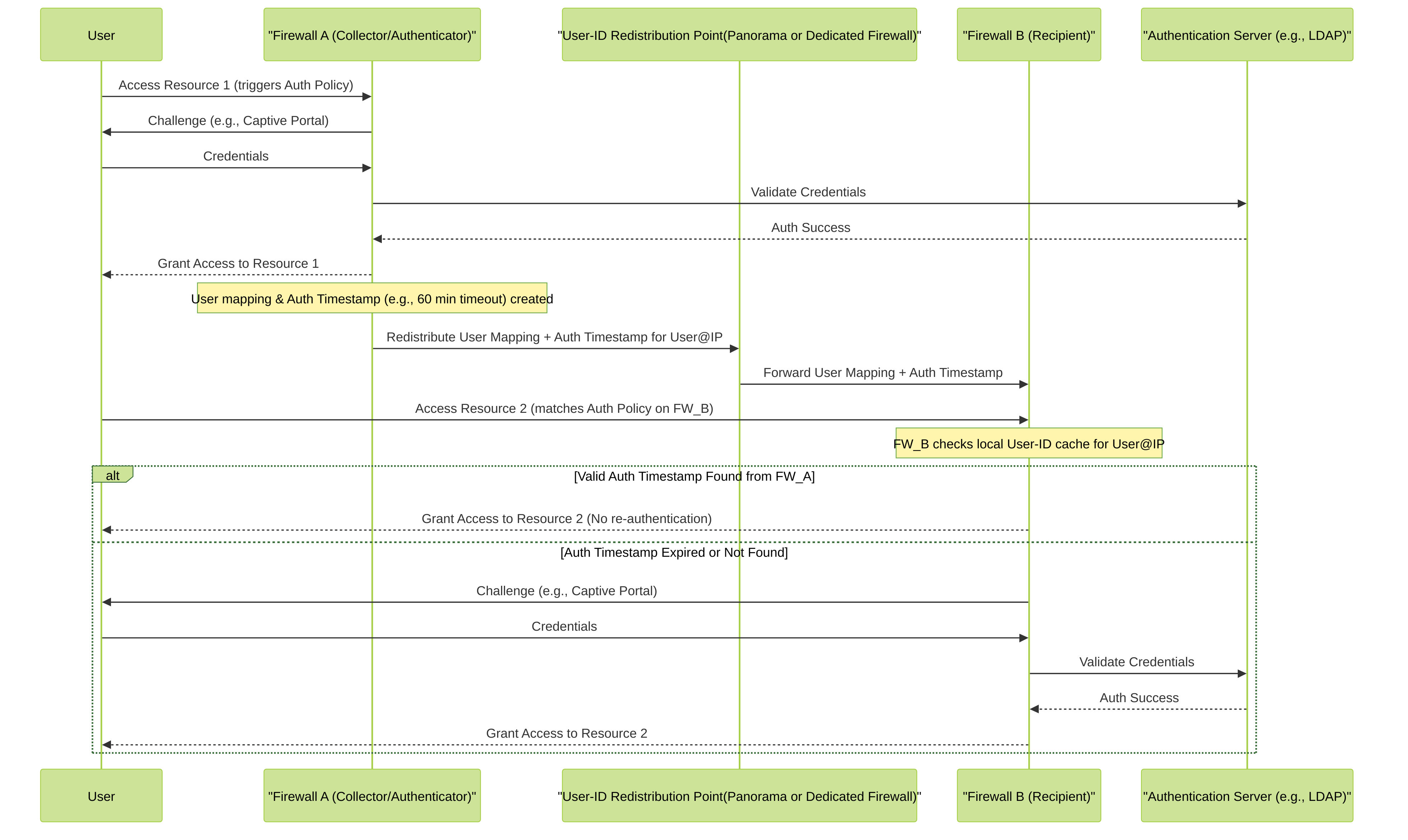
Sequence diagram illustrating authentication timestamp redistribution. User authenticates on Firewall A, which then redistributes the authentication information via a User-ID Redistribution Point (like Panorama or another firewall) to Firewall B. Firewall B can then leverage this information to avoid re-authenticating the user if the timestamp is still valid.
Configuring User-ID Data Redistribution
Configuration varies slightly depending on whether you're using Panorama or direct firewall-to-firewall redistribution. The core concepts involve defining sources of User-ID information and destinations for redistribution.
Scenario 1: Using Panorama for Redistribution
-
Configure Firewalls/User-ID Agents to send to Panorama:
-
On each firewall (
Device > User Identification > User-ID Agents), add Panorama as a User-ID agent. - If using Windows User-ID agents, configure them to send mappings to Panorama.
-
On each firewall (
-
Configure Panorama to collect and redistribute:
-
In Panorama (
Panorama > Collector Groups), define collector groups and add Log Collectors. -
Ensure User-ID data is being forwarded from Log Collectors to Panorama's management plane (
Panorama > Managed Collectors). -
In Panorama (
Panorama > User-ID > User-ID Agents), verify Panorama is listed or configure it to act as a source for redistribution if needed (less common, usually it just aggregates and redistributes what it receives).
-
In Panorama (
-
Configure Managed Firewalls to receive from Panorama:
- This is often implicit. When firewalls are managed by Panorama and Panorama has User-ID data, it distributes this as part of its configuration pushes and updates to the firewalls within the same Collector Group context.
-
Specifically for redistribution settings (
Panorama > User-ID > User-ID Redistribution), you can define how Panorama shares information among different Collector Groups or with external entities.
Scenario 2: Firewall-to-Firewall Redistribution (PAN-OS Integrated User-ID Agent)
Let's say Firewall-A is the collector/source and Firewall-B is the recipient.
-
On Firewall-A (Source/Redistribution Server):
-
Enable User-ID on the relevant interface(s) that will communicate with Firewall-B:
Network > Interfaces > [Interface Name] > Advanced > User-ID(ensure "Enable User-ID" is checked under Service). -
Configure Firewall-A to act as a User-ID Agent Server:
Device > User Identification > User-ID Agents. While it's collecting, it also needs to be able to serve this data. No specific "server" mode is set here, rather, clients connect to it. Ensure the necessary service (typically `paloalto-userid-agent` on TCP/5007) is allowed through security policies if firewalls are in different zones. - Ensure Firewall-A is collecting User-ID information (e.g., via Server Monitoring, Captive Portal, etc.).
-
Enable User-ID on the relevant interface(s) that will communicate with Firewall-B:
-
On Firewall-B (Recipient/Client):
-
Configure Firewall-B to connect to Firewall-A as a User-ID Agent:
Device > User Identification > User-ID Agents. - Click "Add."
- Enter a Name.
- For "Host/IP Address," enter the IP address of Firewall-A's interface that is enabled for User-ID service.
- The default Port is 5007.
- Commit changes on both firewalls.
-
Configure Firewall-B to connect to Firewall-A as a User-ID Agent:
-
Verify Communication:
-
On Firewall-B: Use CLI command
show user user-id-agent state all. You should see the connection to Firewall-A as "connected." - On Firewall-A: You might see connection logs or status indicating Firewall-B is connected, though the client-side verification is more direct.
-
On Firewall-B: Use CLI command
! CLI command on Firewall-B (recipient) to check User-ID Agent connection status:
admin@Firewall-B> show user user-id-agent state all
Agent: UID-Agent-FW-A (vsys: vsys1) Host: 192.168.1.253:5007
Version : 1
num of connection tried : 1
num of connection succeeded : 1
num of connection failed : 0
last connect tried time : xxxx
last connect succeeded time : xxxx
last connect failed time :
last disconnect time :
Status : connected <-- Look for this!
num of ip : 150
num of group : 20
num of host : 0
num of hip : 0
is_primary : no
group_include_list :
group_exclude_list :
Filtering Redistributed Data:
In some scenarios, you may not want to redistribute all User-ID information. PAN-OS allows filtering:
- Group Include List: Only redistribute mappings for users belonging to specified groups. This is configured on the client firewall (the one receiving the data) under its User-ID Agent settings for the connection to the source.
-
Network Address (Permit List):
On the source firewall or User-ID agent, you can configure which client firewalls (by IP address) are allowed to connect and receive User-ID information. This is a security measure. (
Device > User Identification > Setup > Client Probing / Redistribution- Permit List)
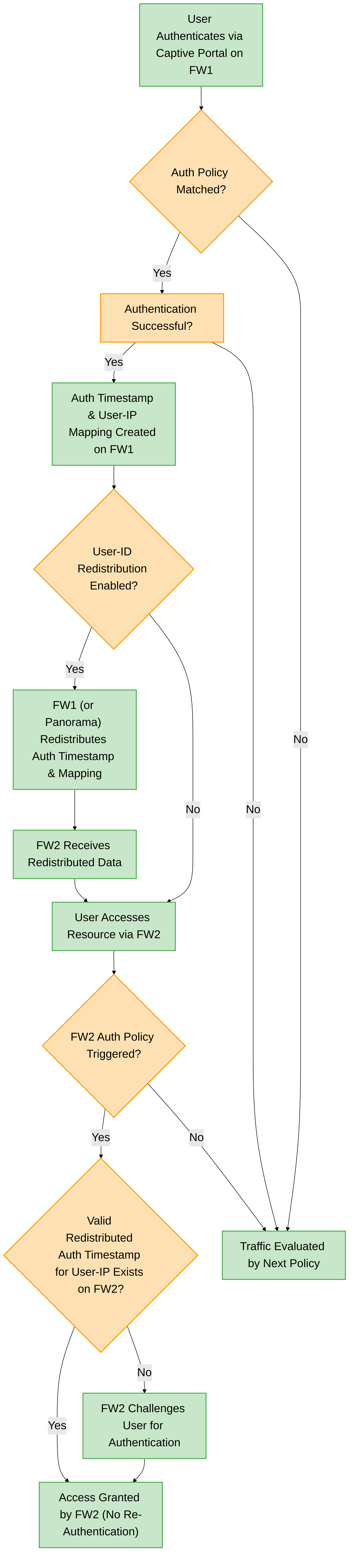
Decision tree for user authentication flow with timestamp redistribution between Palo Alto Networks firewalls (FW1 and FW2). This illustrates how a valid redistributed authentication timestamp can prevent re-authentication on a second firewall.
Interaction of Timeouts and Redistribution
Understanding how different timeouts interact is crucial for predictable behavior, especially when redistribution is involved.
Key Timeouts in Play:
- Authentication Policy Authentication Timeout: Set in the Authentication Enforcement object. This is the lifetime of the authentication grant from *that specific policy*. This is the primary timeout whose associated timestamp is redistributed for authentication state sharing.
- Authentication Profile Timeout: Set within the Authentication Profile itself (e.g., LDAP, RADIUS server profile). This contributes to the User-ID mapping lifetime for users authenticated via this profile. If an Authentication Policy uses an Auth Profile with a 30-min timeout, and the Auth Policy itself has a 60-min timeout, the User-ID mapping based purely on the Auth Profile might expire sooner, but the *authentication grant* from the Auth Policy could still be valid. Redistribution primarily concerns the Authentication Policy's grant.
-
User-ID Timeout (Global or per VSYS):
(
Device > User Identification > Setup > User Identification Timeout SettingsorDevice > Virtual Systems > [vsys] > Setup > User-ID Timeout). This is the inactivity timeout for general IP-to-user mappings in the User-ID table. If a user is inactive for this period, their IP-user mapping might be removed, *unless* an active authentication timestamp from an Authentication Policy keeps it alive. - Captive Portal Session Timeout: Can be configured for the Captive Portal itself. Typically aligns with or is influenced by the Authentication Policy timeout.
- Idle Timeout (Authentication Policy): An optional timeout in the Authentication Enforcement object that can log out a user due to inactivity, separate from the main Authentication Timeout.
| Timeout Type | Configured Location | Primary Purpose | Impact on Redistribution |
|---|---|---|---|
| Authentication Policy Auth Timeout | Authentication Enforcement Object | Duration of the specific authentication grant by the policy. | Key data for redistribution. Determines how long other firewalls honor this authentication. |
| Authentication Profile Timeout | Authentication Profile (e.g., LDAP, RADIUS) | Lifetime of User-ID mapping from this specific auth method. | Contributes to the overall User-ID mapping, but the Auth Policy timeout is more direct for auth state. |
| User-ID Timeout (Global/VSYS) | Device > User Identification > Setup / VSYS Setup | General inactivity timeout for IP-user mappings in User-ID. | An active, redistributed auth timestamp can override this, keeping the mapping "fresh" beyond the User-ID inactivity timeout. |
| Idle Timeout (Auth Policy) | Authentication Enforcement Object | Logs out user from the specific auth session due to inactivity. | If triggered, invalidates the auth grant, which would affect redistributed state. |
When Firewall B receives a redistributed authentication timestamp for User X from Firewall A, it knows User X authenticated at Time T and the grant is valid for Duration D (from Firewall A's Auth Policy). Firewall B will honor this until Time T+D, provided its own policies don't mandate a different action (e.g., requiring step-up authentication).
Troubleshooting Authentication and Redistribution
Effective troubleshooting requires understanding the data flow and using PAN-OS tools.
Common Issues and Troubleshooting Steps:
-
Users repeatedly prompted for Captive Portal:
- Check Authentication Policy timeouts. Are they too short?
-
Verify User-ID redistribution is working. Is the authenticating firewall sharing timestamps with other firewalls the user traverses?
admin@FW-Receiving> show user ip-user-mapping ip
Look for the `Auth Succeeded At` and `Auth Timeout` fields. Is the source correct? - Check if the Authentication Policy on the subsequent firewalls is configured to honor existing authentications or if it's always forcing a new challenge.
- Ensure User-ID service is enabled on interfaces involved in redistribution (TCP/5007).
- Check Security Policies to ensure User-ID redistribution traffic is allowed.
-
User-ID mappings not appearing on recipient firewalls:
-
On recipient firewall:
show user user-id-agent state all. Is the connection to the source (Panorama, another FW, Windows Agent) "connected"? - On source: Check if it's correctly configured to send. Check logs for connection attempts from clients.
- Network connectivity: Ping, traceroute between User-ID components.
-
Service routes: If User-ID traffic needs to use a non-default VR or specific egress interface, ensure service routes are configured (
Device > Setup > Services > Service Route Configuration). - Filtering: Check if group include lists or permit lists are unintentionally blocking expected mappings.
-
On recipient firewall:
-
Authentication Policy not triggering:
- Rule order: Is a broader, less specific rule (e.g., allow all) placed above the intended Auth Policy rule?
- Matching criteria: Double-check zones, addresses, users, services, applications. Use traffic logs to see if session details match the rule.
- Is the referenced Authentication Enforcement object correctly configured?
-
Is Captive Portal correctly configured (e.g., redirect host, interface enabled for response pages)?
Device > Response Pages.
-
Incorrect User-to-Group Mappings:
-
Check LDAP/AD server profile connectivity:
test authentication authentication-profile <profile_name> username <user> password. -
Verify Group Mapping settings:
Device > User Identification > Group Mapping Settings. Correct Base DN, filter, attributes. -
Refresh group mappings:
clear user-id group all(use with caution, forces re-query).admin@FW> show user group list
admin@FW> show user group name "
"
-
Check LDAP/AD server profile connectivity:
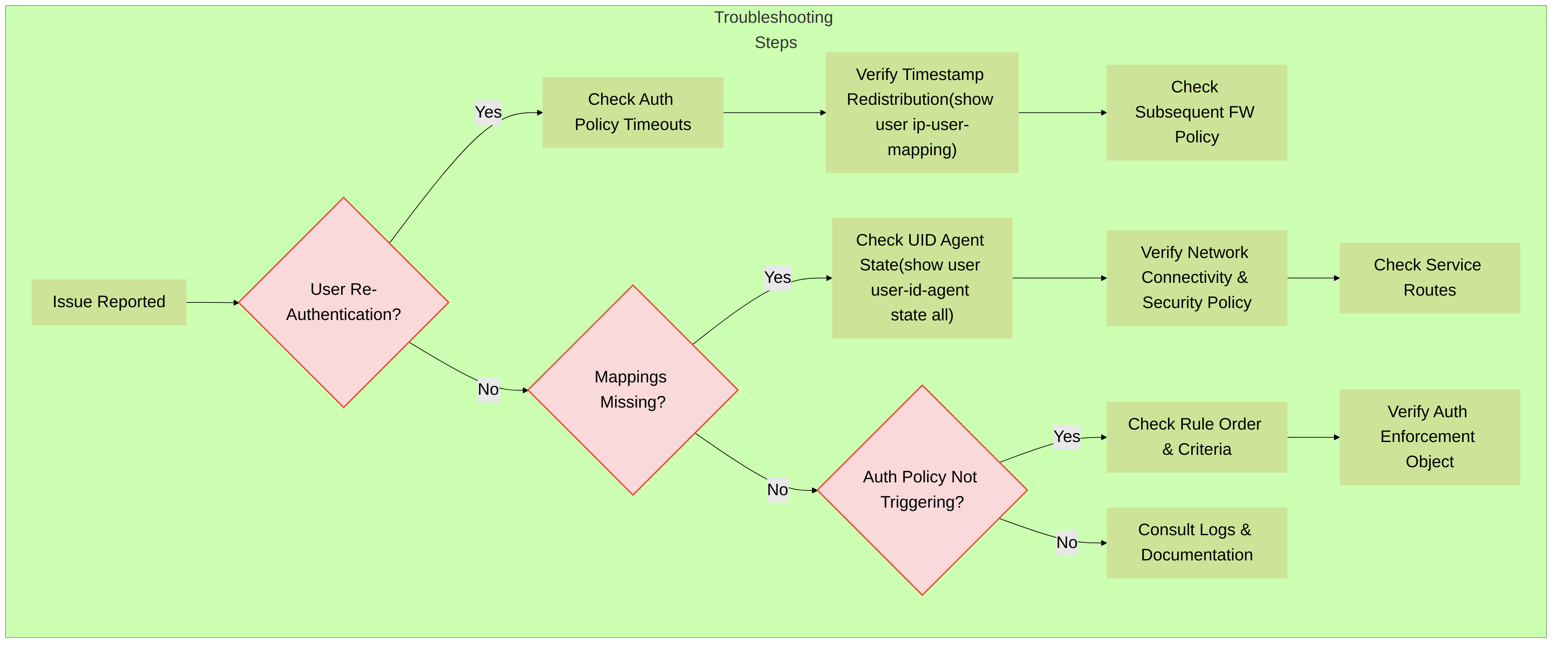
A simplified troubleshooting flowchart for common Palo Alto Networks Authentication Policy and User-ID redistribution issues.
Best Practices for Authentication Policy and Data Redistribution
- Use Panorama for Large-Scale Deployments: Centralizes User-ID collection and redistribution, simplifying management and ensuring consistency.
- Align Timeouts Logically: Ensure Authentication Policy timeouts provide a good user experience while meeting security requirements. Avoid excessively short timeouts that cause frequent re-prompts.
-
Secure User-ID Communication:
- Use dedicated interfaces for User-ID agent communication where possible.
- Implement strict Security Policies allowing User-ID traffic (TCP/5007) only between authorized User-ID components.
- Consider SSL/TLS for securing communication between User-ID agents and firewalls if traffic traverses untrusted networks (configure on User-ID agent and firewall).
- Start with Broad Authentication, then Refine: Initially, you might apply Authentication Policy broadly to sensitive zones/applications and then refine rules based on specific needs.
- Leverage User-ID for Granular Control: Use the User-ID information (users, groups) gathered through authentication and redistribution to create granular Security Policies.
- Regularly Monitor User-ID State: Use CLI commands and Panorama/firewall GUIs to monitor the status of User-ID agents, mappings, and redistribution.
- Plan for Redundancy: In critical environments, deploy redundant User-ID agents or configure multiple redistribution points. Panorama HA also provides redundancy.
- Understand the Order of Operations: Remember that Authentication Policy is evaluated before Security Policy. A user must pass Authentication Policy (if applicable) before their traffic is evaluated against Security Policy rules that might use their User-ID.
Mermaid Sequence Diagram: Original Authentication Timestamp Redistribution
This diagram, provided in the base, illustrates the fundamental flow when a user authenticates on one firewall and that authentication information is shared, preventing re-authentication on a second firewall.
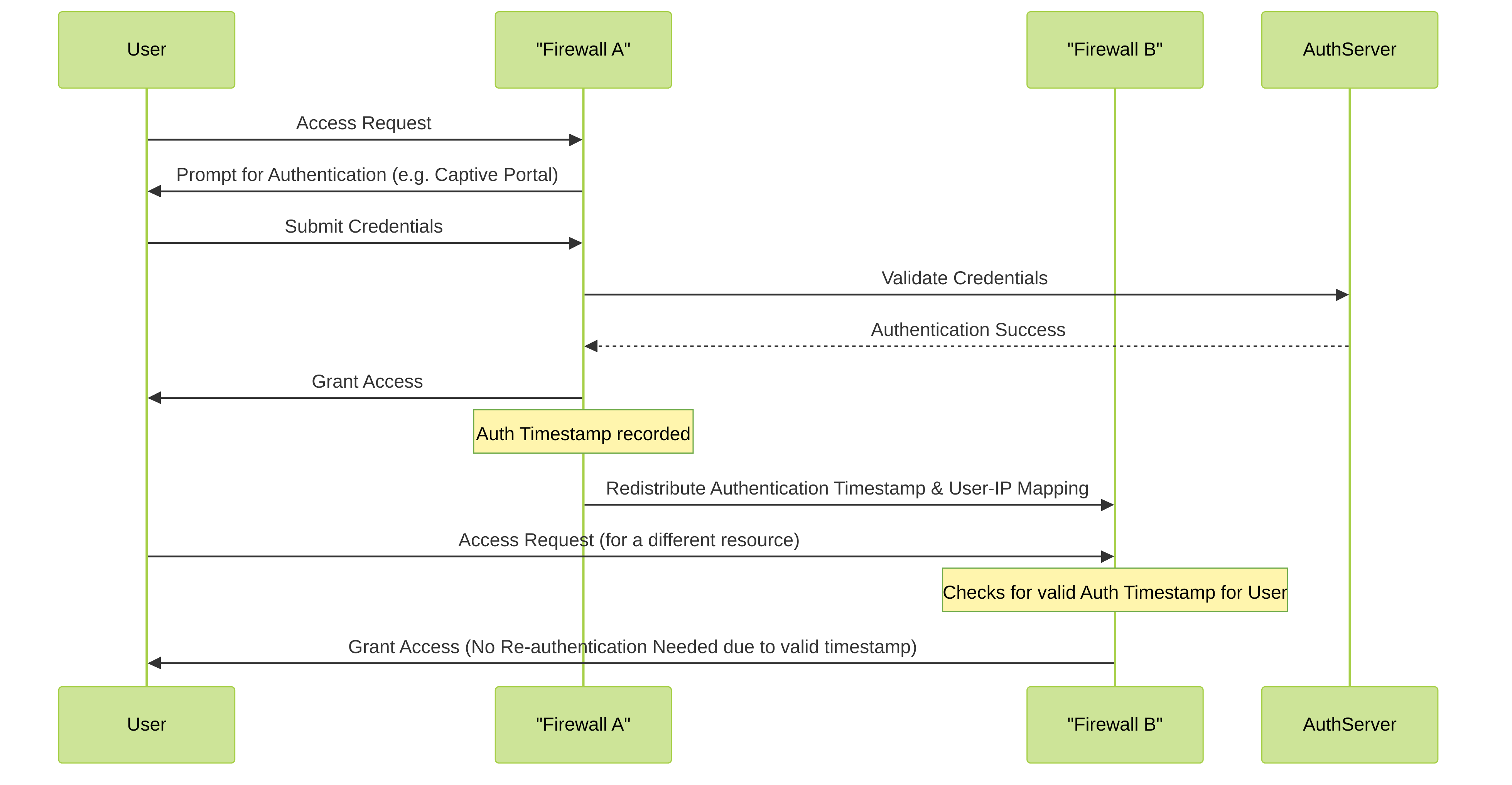
This sequence shows User authenticating via Firewall A. Firewall A then redistributes the authentication timestamp. When the User accesses a resource via Firewall B, Firewall B uses the redistributed timestamp to grant access without requiring a new authentication, assuming the timestamp is still valid and Firewall B's policies permit it.
PCNSE Knowledge Check: Palo Alto Networks Authentication Policy & Data Redistribution
References
For further information, consult the official Palo Alto Networks documentation on the Palo Alto Networks TechDocs portal , specifically searching for topics like "Authentication Policy," "User-ID," "User-ID Redistribution," and your PAN-OS version.