Palo Alto Networks: Mastering Authentication Policy and its Dependencies for PCNSE
Authentication in Palo Alto Networks Next-Generation Firewalls (NGFWs) is a cornerstone of implementing Zero Trust principles and granular access control. Authentication Policy, in conjunction with various interconnected components, allows the firewall to verify user identities before granting access to network resources. Understanding these dependencies is crucial for effective security posture management and for success in the PCNSE certification. This guide delves into the intricate relationships between Authentication Policy and its foundational elements within the PAN-OS environment.
Core Concept: Authentication Policy in PAN-OS
An Authentication Policy in PAN-OS dictates how the firewall challenges users for authentication when their traffic matches specific criteria. It acts as a gatekeeper, ensuring that only verified users gain access to resources as defined by Security Policies. Authentication Policies are evaluated after a Security Policy rule with "Authentication Enforcement" specified is matched.
Key characteristics of Authentication Policies:
- Purpose: To trigger an authentication challenge for users accessing network resources.
- Trigger: Invoked by a Security Policy rule that has an "Authentication Enforcement" profile specified in its action.
- Matching Criteria: Source Zone, Destination Zone, Source Address, Destination Address, Source User (can be 'unknown' to trigger authentication for unauthenticated users), Service/Application (optional).
- Action: Specifies the Authentication Profile to use for challenging the user, and optionally, a timeout override.
Located in the PAN-OS GUI under
Policies > Authentication
.
Dependency 1: Authentication Profiles
Authentication Profiles are fundamental building blocks that define the *method* and *parameters* for authenticating users. An Authentication Policy rule explicitly references an Authentication Profile to use when challenging a user.
Configured under
Device > Authentication Profile
, these profiles specify:
- Name: A unique identifier for the profile.
-
Type:
The primary authentication mechanism. Common types include:
- LDAP: Authenticates against an LDAP directory (e.g., Microsoft Active Directory, OpenLDAP).
- RADIUS: Authenticates against a RADIUS server.
- Kerberos: Authenticates against a Kerberos Key Distribution Center (KDC), often used for single sign-on (SSO) with Active Directory.
- SAML: Enables federated authentication using a SAML Identity Provider (IdP). The firewall acts as a SAML Service Provider (SP).
- TACACS+: Primarily for device administration authentication but can also be used for user authentication in specific scenarios.
- Local Database: Authenticates against a user database configured locally on the firewall. Suitable for small environments or as a fallback.
- Multi-Factor Authentication (MFA): Not a primary type itself, but an MFA Server Profile (e.g., Duo, Okta, RSA SecurID) is linked here to enforce a second factor of authentication after primary authentication succeeds.
- Server Profile (Mandatory for most types): Links to a configured Server Profile (LDAP, RADIUS, Kerberos, SAML IdP, TACACS+) which contains the specific connection details for the authentication server. This is a critical dependency.
-
Login Attributes (LDAP-specific):
Defines the attribute used to identify the user in the LDAP directory (e.g.,
sAMAccountNamefor Active Directory,uidfor OpenLDAP). -
Username Modifier:
Allows modification of the username format before it's sent to the authentication server.
-
%USERINPUT%: Sends the username as entered by the user. -
%USERDOMAIN%\%USERINPUT%: Prepends a domain (e.g., `CORP\username`). -
%USERINPUT%@%USERDOMAIN%: Appends a domain (e.g., `username@corp.com`).
-
- Allow List: Specifies which users or, more commonly, directory groups are permitted to authenticate using this profile. Using `all` is possible but not recommended for security best practices. Group membership is typically retrieved from the authentication server (e.g., LDAP group membership).
- Authentication Protocol (Kerberos-specific): Defines parameters for Kerberos authentication, such as the Realm.
- Advanced Tab: Contains options like Lockout settings (to prevent brute-force attacks), Timer settings (authentication timeout), and MFA configuration (linking to an MFA Server Profile).
Dependency 2: Server Profiles
Server Profiles contain the specific details required for the Palo Alto Networks firewall to communicate with various types of authentication, authorization, and accounting (AAA) servers or identity providers. Authentication Profiles rely directly on these Server Profiles.
Located under
Device > Server Profiles
. Key types include:
-
LDAP Server Profile:
Used by Authentication Profiles of type LDAP.
- Server Address & Port: IP or FQDN of the LDAP server (e.g., Domain Controller). Standard ports are 389 (LDAP) and 636 (LDAPS).
- Type: Typically `active-directory` for Microsoft AD.
-
Base DN:
The starting point in the LDAP directory tree for user searches (e.g.,
DC=corp,DC=example,DC=com). - Bind DN & Password: Credentials of a service account used by the firewall to connect and search the LDAP directory. Read-only permissions are usually sufficient.
- SSL/TLS Encrypted Connection: Highly recommended to secure LDAP communication. Requires importing the CA certificate that signed the LDAP server's certificate into the firewall's trust store.
- Verify Server Certificate: Ensures the firewall validates the LDAP server's certificate.
-
RADIUS Server Profile:
Used by Authentication Profiles of type RADIUS.
- Server Address & Port: IP or FQDN of the RADIUS server. Standard ports are 1812/1645 (Authentication) and 1813/1646 (Accounting).
- Shared Secret: A pre-shared key configured on both the firewall and the RADIUS server for secure communication.
- Timeout & Retries: Defines how long the firewall waits for a response and how many times it retries.
- Protocol: PAP, CHAP, MS-CHAPv2 (PAP is most common for user authentication with User-ID).
-
Kerberos Server Profile:
Used by Authentication Profiles of type Kerberos.
- Server Address & Port: IP or FQDN of the Kerberos KDC (often a Domain Controller). Standard port is 88.
-
Realm:
The Kerberos realm, typically the Active Directory domain name in uppercase (e.g.,
CORP.EXAMPLE.COM). - Keytab File (for Kerberos SSO with Authentication Portal): If the firewall itself is authenticating users via Kerberos (e.g., for Authentication Portal with Kerberos SSO), a keytab file for the firewall's service principal name (SPN) must be uploaded.
-
SAML Identity Provider (IdP) Server Profile:
Used by Authentication Profiles of type SAML. Defines how the firewall (as SP) interacts with an external SAML IdP.
- Identity Provider ID: The entityID of the SAML IdP.
- Identity Provider SSO URL: The URL where the firewall redirects users for authentication.
- Identity Provider Certificate: The IdP's signing certificate, used to validate SAML assertions.
- Validate Identity Provider Certificate: Ensures the firewall checks the IdP's certificate against its trust store.
- Service Provider (Firewall) Settings: Defines the firewall's entityID and Assertion Consumer Service (ACS) URLs.
-
TACACS+ Server Profile:
Primarily for authenticating administrators accessing the firewall's management interface, but can also be configured for user authentication.
- Server Address & Port: IP or FQDN of the TACACS+ server. Standard port is 49.
- Shared Secret: A pre-shared key.
- Protocol: Usually PAP or CHAP.
-
MFA Server Profiles:
Found under
Device > Server Profiles > MFA. These define connectivity to external MFA vendors like Okta, Duo, PingID, RSA SecurID. An Authentication Profile will then reference one of these MFA Server Profiles to enforce second-factor authentication.
Dependency 3: Authentication Portal and Redirect Mode
The Authentication Portal is a User-ID™ feature that provides a web-based interface for user authentication when other transparent methods (like Kerberos SSO or User-ID agent-based mapping) are not available or have failed. It is often used for guest networks, BYOD scenarios, or as a fallback. When an Authentication Policy triggers a challenge that requires web-based interaction (e.g., web form, SAML redirect), the Authentication Portal settings come into play.
Configured under
Device > User Identification > Authentication Portal Settings
.
Key aspects related to Authentication Policy dependencies:
-
Mode:
Can be Transparent, Redirect, or Redirect (Transparent for MFA only).
- Redirect Mode: This is the most common mode when discussing Authentication Policy triggering explicit user logins. The firewall intercepts an HTTP/HTTPS request from an unauthenticated user (matching an Authentication Policy) and redirects the user's browser to a specific IP address or hostname hosted on one of the firewall's interfaces. This interface presents the login page.
- Redirect Host: The IP address or FQDN of the firewall interface that will serve the Authentication Portal login page. This FQDN must be resolvable by clients. If using an FQDN, ensure DNS is configured correctly on client devices and that the firewall has a management interface DNS server configured to resolve its own FQDN if using the default certificate.
- Interface and Zone: You must specify which firewall interface (and thereby, which zone) will host the Authentication Portal. This interface needs an IP address and must be reachable by the users who will be redirected. A common practice is to use a dedicated Layer 3 interface or subinterface in a trusted or DMZ-like zone.
-
SSL/TLS Service Profile:
Crucial for securing the Authentication Portal. This profile defines the server certificate the firewall presents to users when they are redirected to the portal over HTTPS.
- Using a certificate signed by a public CA or an internal enterprise CA trusted by client browsers is highly recommended to avoid browser certificate warnings.
-
The Common Name (CN) or Subject Alternative Name (SAN) in the certificate must match the
Redirect HostFQDN.
Device > Certificate Management > SSL/TLS Service Profiles. - Authentication Profile: While the Authentication Policy rule specifies an Authentication Profile for the challenge, the Authentication Portal settings themselves can also reference an Authentication Profile. This profile is used for specific portal functions like Kerberos SSO for the portal itself or NTLM authentication. For Captive Portal (web form authentication), the profile in the Authentication Policy rule is the primary one.
- Response Pages: The Authentication Portal leverages customizable response pages (Comfort Pages) for the login form, MFA prompts, success messages, etc.
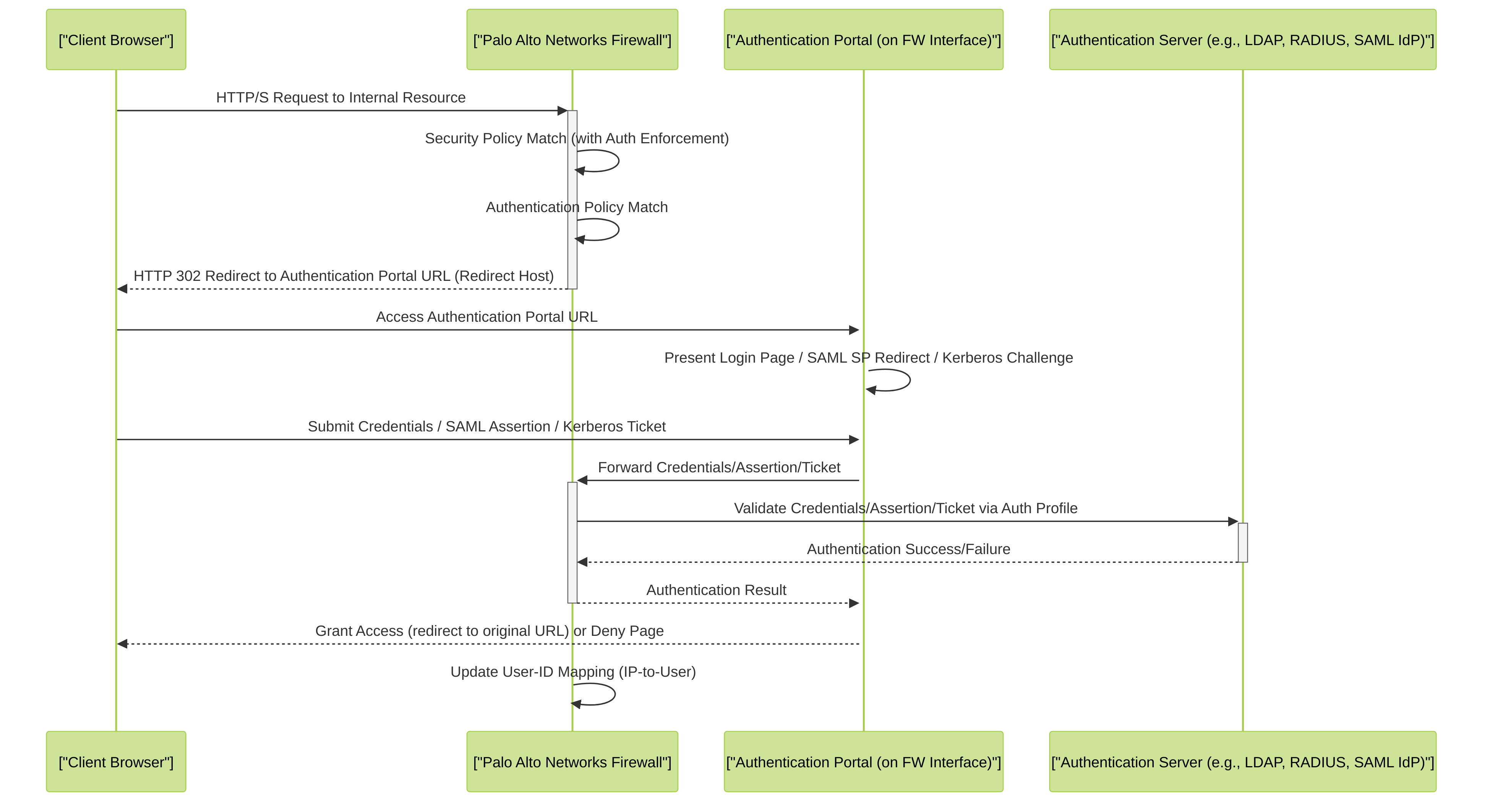
Simplified Authentication Portal redirect workflow. The client attempts to access a resource, is redirected by the firewall (due to matching Security and Authentication Policies) to the Authentication Portal hosted on a firewall interface. The portal handles the credential exchange and validation against an backend Authentication Server via the configured Authentication Profile. Upon success, User-ID mapping is updated.
Dependency 4: User Prompt Mechanisms & Experience
The actual method used to prompt the user for credentials depends on the Authentication Profile type, Authentication Portal settings, and client capabilities. Authentication Policies leverage these underlying mechanisms.
-
Browser Challenge (Kerberos Single Sign-On - SSO):
- How it works: When an Authentication Policy using a Kerberos Authentication Profile is triggered, and Authentication Portal is configured for Kerberos SSO, the firewall can respond to the client's browser with an HTTP 401 Unauthorized response, including a `WWW-Authenticate: Negotiate` header.
- Client Action: If the client machine is domain-joined, the browser can automatically obtain a Kerberos service ticket for the firewall's Service Principal Name (SPN) from the KDC and send it back to the firewall.
- Firewall Action: The firewall validates the ticket. If successful, authentication is transparent to the user.
- Fallback: If Kerberos SSO fails (e.g., client not domain-joined, browser misconfiguration, KDC unreachable), the system can fall back to NTLM (if enabled and configured, less secure) or present a Web Form via the Authentication Portal.
- PAN-OS Configuration: Requires a Kerberos Server Profile, an Authentication Profile of type Kerberos, and Authentication Portal settings enabling Kerberos SSO (including uploading the firewall's keytab file).
-
Web Form (Captive Portal):
- How it works: The most common method when SSO is not feasible. After being redirected to the Authentication Portal, the user is presented with an HTML login page (a "comfort page").
- User Action: The user manually enters their username and password.
- Firewall Action: The firewall validates these credentials against the backend authentication server defined in the Authentication Profile (e.g., LDAP, RADIUS, Local Database).
- Multi-Factor Authentication (MFA) Integration: If MFA is configured in the Authentication Profile, after successful primary credential validation, the user will be prompted for a second factor on another web page (e.g., enter OTP, push notification approval).
-
Client Certificate Authentication:
- How it works: Users are authenticated based on a valid client digital certificate presented by their browser or device.
- PAN-OS Configuration: Requires an Authentication Profile configured for Client Certificate Authentication. This involves setting up a Certificate Profile (under `Device > Certificate Management > Certificate Profile`) to define trusted CAs for client certificates and how to extract the username (e.g., from CN or SAN fields of the certificate).
- User Experience: Can be seamless if the client certificate is automatically presented. The browser might prompt the user to select a certificate if multiple are available.
- Use Case: Often used in high-security environments or for authenticating non-interactive clients.
-
SAML Authentication:
- How it works: When an Authentication Policy using a SAML Authentication Profile is triggered, the firewall (as SP) redirects the user's browser to the configured external SAML Identity Provider (IdP).
- User Action: The user authenticates at the IdP (which might involve its own MFA).
- IdP Action: The IdP sends a SAML assertion (a signed XML document containing authentication and attribute statements) back to the firewall's Assertion Consumer Service (ACS) URL via the user's browser.
- Firewall Action: The firewall validates the SAML assertion (signature, issuer, audience, conditions) and extracts the username. If valid, authentication is successful.
- Use Case: Centralized identity management, integration with cloud IdPs (e.g., Azure AD, Okta), and providing SSO across multiple applications.
Dependency 5: SSL/TLS Service Profiles
SSL/TLS Service Profiles are critical for securing communication channels involving authentication, particularly for the Authentication Portal and GlobalProtect. While not directly part of an Authentication Policy rule, they are a crucial dependency for the infrastructure that Authentication Policies rely on.
Configured under
Device > Certificate Management > SSL/TLS Service Profiles
.
An SSL/TLS Service Profile specifies:
- Name: A unique identifier.
-
Certificate:
The server certificate that the firewall will present to clients. This certificate, along with its private key, must be imported into the firewall (
Device > Certificate Management > Certificates).- For the Authentication Portal, the CN/SAN of this certificate must match the `Redirect Host` FQDN used in the Authentication Portal settings to avoid browser certificate errors.
- For GlobalProtect (Portal and Gateway), it must match the FQDNs used by clients to connect.
- Protocol Settings: Minimum and maximum versions of SSL/TLS to support (e.g., TLSv1.2, TLSv1.3). Palo Alto Networks best practice is to disable older, insecure protocols like SSLv3 and TLSv1.0/1.1.
- Authentication: Can be configured to request or require client certificates (used for Client Certificate Authentication).
Dependency 6: User-ID™ Integration
User-ID technology is fundamental to Palo Alto Networks' security model. Authentication Policies and their dependent components are intrinsically linked to User-ID.
- Source of Mappings: Successful authentication via Authentication Portal, GlobalProtect, or even command-line initiated authentication (e.g., `request authentication login`) results in the firewall creating an IP-address-to-username mapping. This mapping is stored in the User-ID mapping table.
- Consumer of Mappings: Once a user is authenticated and mapped, Security Policies can use this User-ID information (username or group membership) as matching criteria for more granular access control.
- Authentication Policy's Role: If an Authentication Policy has `Source User` set to `unknown` (or a specific user/group), it effectively says, "If traffic matches these zone/address criteria and the user is currently unknown (or not the specified user/group), then trigger this authentication challenge."
-
Group Mapping:
After successful authentication, the firewall often queries the authentication server (e.g., LDAP) to retrieve the user's group memberships. These group memberships are also stored and can be used in Security Policies. Group Mapping Profiles are configured under
Device > User Identification > Group Mapping Settings.
Troubleshooting User-ID related to authentication involves checking:
show user ip-user-mapping all show user group list show user group name <group_name> debug authenticationd on debug debug user-id on debug
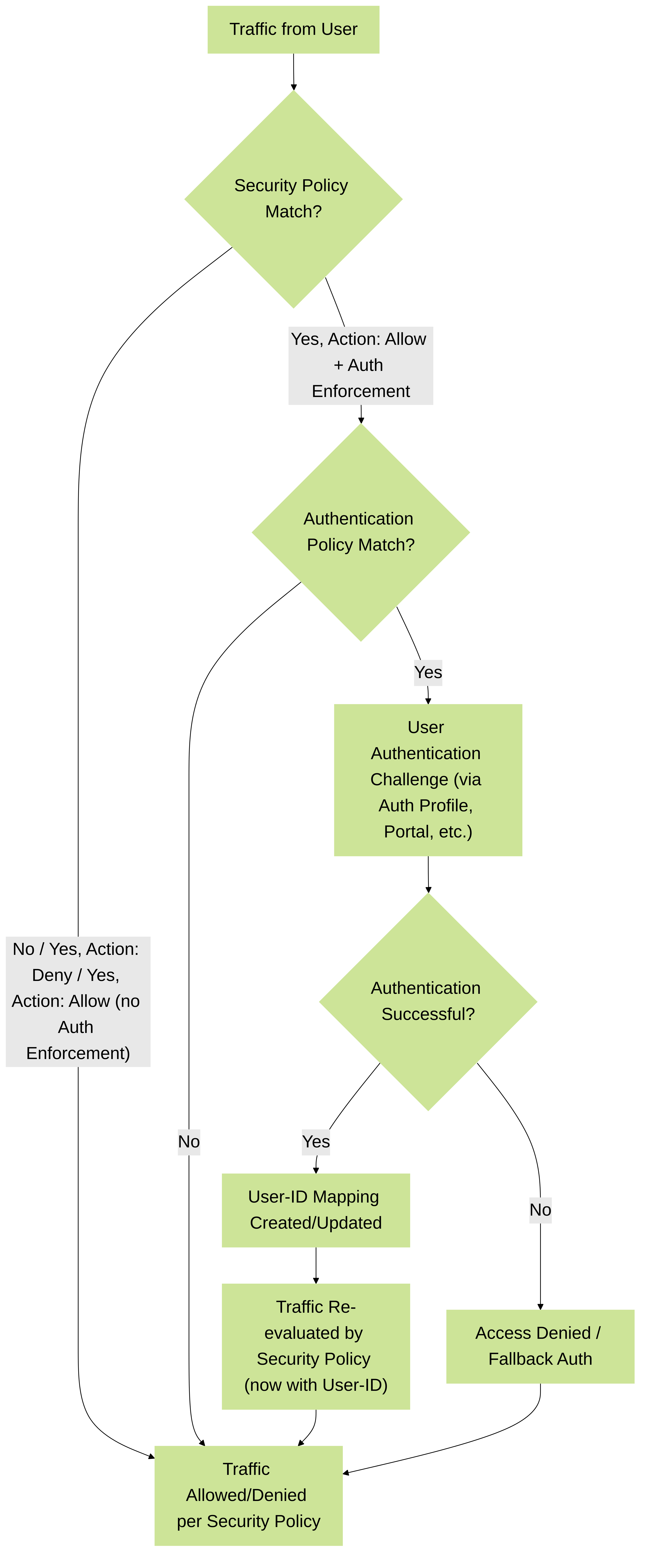
Flow demonstrating the interplay between Security Policy, Authentication Policy, and User-ID. Successful authentication leads to a User-ID mapping, which can then be used for more granular Security Policy enforcement.
Dependency 7: Zone and Interface Configuration
The configuration of network interfaces and zones plays a vital role:
- Authentication Portal Host Interface: As mentioned, the interface hosting the Authentication Portal must have an IP address, be in an "up" state, and be reachable by users who will be redirected. It also needs an Interface Management Profile permitting relevant services.
- Source/Destination Zones in Authentication Policy: Authentication Policies use source and destination zones as matching criteria. Traffic must originate from and be destined for zones specified in a matching Authentication Policy rule for it to apply.
-
User-ID Enabled Zones:
For User-ID to effectively map users, User-ID should be enabled on the zones where users reside. This is configured under
Network > Zones > [Zone Name] > Enable User Identification. While Authentication Portal can function without this on the source zone (as it's a direct challenge), enabling User-ID on zones is best practice for comprehensive user visibility.
Dependency 8: Response Pages (Comfort Pages)
Response Pages, often called "Comfort Pages," are customizable HTML pages displayed to users during various stages of the authentication process or when web access is blocked. While they don't dictate *if* authentication occurs, they are crucial for the user experience *during* authentication triggered by an Authentication Policy.
Administrators can customize these pages under
Device > Response Pages
.
Types relevant to Authentication Policy workflows:
-
Authentication Portal Pages:
-
Captive Portal Login Page: The primary login form where users enter credentials. -
Captive Portal Authentication Success Page: Shown after successful login. -
Captive Portal Authentication Denied Page: Shown if authentication fails.
-
-
Multi-Factor Authentication Pages:
-
Multi-Factor Authentication Login Page: Prompts for the second factor (e.g., OTP). - Various MFA vendor-specific response pages if using features like MFA push notifications.
-
- SAML Related Pages: Pages related to SAML processing errors or messages.
- GlobalProtect Pages: Login pages, messages for GlobalProtect agent connections.
Customization allows organizations to:
- Align the look and feel with corporate branding.
- Provide clear instructions and help information to users.
- Include acceptable use policy reminders.
Management Plane vs. Dataplane in Authentication
It's important to distinguish the roles of the management plane (MP) and dataplane (DP) in the authentication process:
-
Management Plane:
- Hosts the Authentication Portal web server.
- Communicates with backend authentication servers (LDAP, RADIUS, SAML IdP, etc.) via Server Profiles. This communication typically originates from a management interface or a service route.
- Processes authentication credentials.
- Updates the User-ID agent process (also on MP) with successful IP-to-user mappings.
- Handles administrative logins to the firewall.
-
Dataplane:
- Enforces Security Policies and Authentication Policies.
- Intercepts traffic matching an Authentication Policy and redirects it to the Authentication Portal (hosted on MP).
- Receives IP-to-user mappings from the User-ID agent on the MP.
- Uses these mappings to enforce user-based Security Policies.
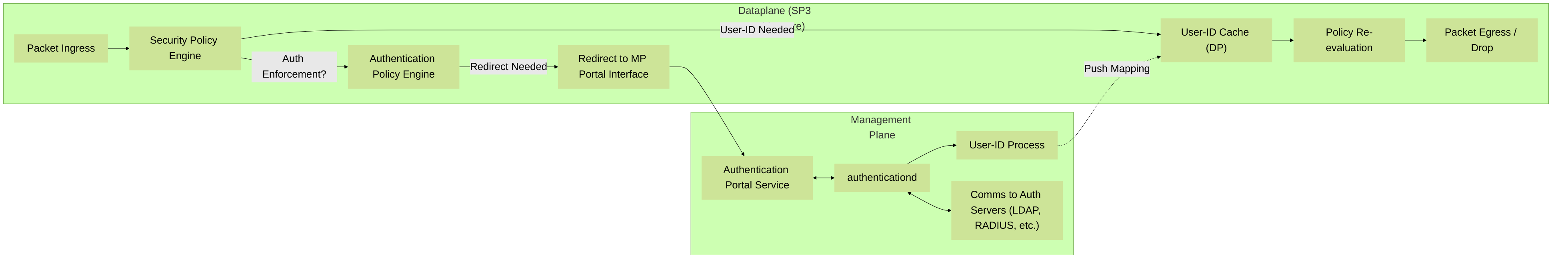
High-level interaction between Management Plane and Dataplane during an Authentication Portal redirect scenario. The Dataplane identifies traffic needing authentication and redirects it. The Management Plane handles the actual authentication process and updates User-ID, which is then used by the Dataplane.
Troubleshooting Authentication Policy Dependencies
A systematic approach is crucial when troubleshooting authentication issues:
- Verify Security Policy Hit: Ensure traffic is hitting the intended Security Policy rule that has Authentication Enforcement configured. Check Traffic logs.
-
Verify Authentication Policy Hit:
Check Authentication logs (
Monitor > Logs > Authentication) to see if the Authentication Policy rule is being matched. -
Test Server Profile:
Navigate to
Device > Server Profiles, select the relevant profile, and use the "Test" button. This isolates issues with connectivity to the backend authentication server. -
Test Authentication Profile:
Use the CLI command:
test authentication authentication-profile <profile-name> username <user> password
This tests the Authentication Profile independently of policies. -
Check Authentication Portal Settings:
- Is the correct interface selected for hosting? Is the interface up?
- Is the Redirect Host FQDN resolvable by clients to the portal interface IP?
- Is the SSL/TLS Service Profile correctly configured with a valid, trusted certificate matching the Redirect Host?
- Does the Interface Management Profile on the portal interface permit "Response Pages" or "HTTP OCSP" and "User-ID Agent"?
- Review Client-Side Configuration (for Kerberos SSO): Browser settings (Integrated Windows Authentication enabled, portal FQDN in Local Intranet zone), SPN existence, client domain membership.
-
Examine Logs:
- Traffic Logs: Shows Security Policy hits, source/destination IP/port, zone.
- Authentication Logs: Shows Authentication Policy hits, username attempts, success/failure, reason for failure.
- User-ID Logs: Shows IP-to-user mapping activity, agent communication.
- System Logs: General system events, can indicate issues with processes like `authenticationd` or `useridd`.
- Packet Captures: Capture traffic on the client, the firewall interface hosting the portal, and the firewall interface communicating with the backend authentication server to diagnose network-level or protocol-level issues.
-
Debug Logs (use with caution in production):
debug authenticationd on debug debug user-id on debug less mp-log authd.log less mp-log userid.log
Device > Certificate Management > Certificates
and ensure the LDAP Server Profile is configured to use SSL/TLS and verify the server certificate.
Authentication Sequence Summary
The overall sequence when Authentication Policy is involved is critical to understand:
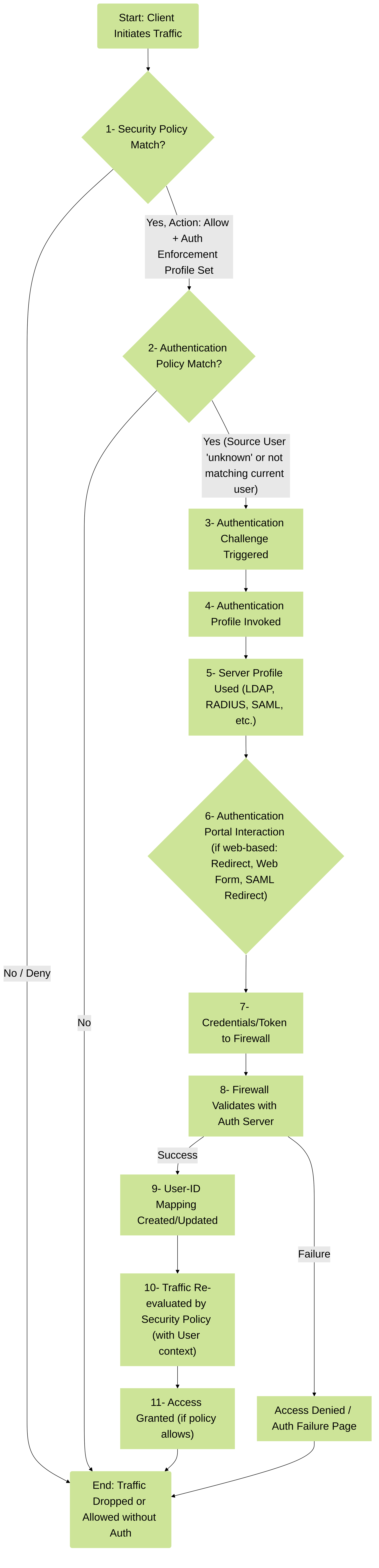
Detailed sequence of events from initial traffic to final access decision when Authentication Policy is triggered. This flow highlights the dependencies at each step.