Palo Alto Networks User-ID Agents: A Deep Dive Comparison for PCNSE
User-ID is a foundational technology within the Palo Alto Networks Next-Generation Firewall (NGFW) platform, enabling organizations to create and enforce security policies based on users and user groups rather than just IP addresses. This provides granular control, enhanced visibility, and more effective threat prevention. Two primary methods for gathering user-to-IP address mappings via agents are the PAN-OS Integrated User-ID Agent and the Windows-based User-ID Agent. Understanding their differences, capabilities, and deployment considerations is crucial for effective network security and for PCNSE exam success.
Understanding User-ID in Palo Alto Networks
Before comparing the agents, it's important to understand the role of User-ID. The Palo Alto Networks NGFW maintains a dynamic table of IP address-to-username mappings. When traffic hits a security policy, the firewall checks this table. If a mapping exists for the source IP address, the firewall can identify the user and apply user-specific or group-specific rules.
Key benefits of User-ID include:
- Granular Policy Control: Define policies based on Active Directory (or other LDAP-based directory services) users and groups (e.g., "Allow Marketing access to Facebook, Deny Engineering").
- Enhanced Visibility and Reporting: Logs and reports show user activity, making it easier to track down security incidents or understand network usage patterns by user.
- Targeted Threat Prevention: Apply specific threat prevention profiles based on user roles or risk levels.
- Consistent Security: Enforce policies consistently as users roam across different devices and IP addresses within the network.
User-ID obtains mappings from various sources, including:
- Domain Controller / Security Log Monitoring: (Primary focus of this comparison) Agents monitor logon events.
- Exchange Server Monitoring: For users accessing email.
- Syslog: Integration with other authentication systems (e.g., 802.1x, VPNs, web proxies) that can send syslog messages with user mapping information.
- XML API: Programmatic way to push user mappings to the firewall or Panorama.
- GlobalProtect: VPN client that provides user and device information.
- Captive Portal: For authenticating users not identified by other means (e.g., guest users, BYOD).
- Client Probing: (Windows User-ID Agent) Probes Windows clients for logged-in user information.
- Terminal Server Agent: For multi-user environments like Citrix or Microsoft RDS, to map users to specific sessions rather than just the server IP.
This guide focuses on the two primary agent-based methods for Active Directory environments: the PAN-OS Integrated User-ID Agent and the Windows-based User-ID Agent.
PAN-OS Integrated User-ID Agent (Agentless)
The Integrated User-ID Agent is a feature built directly into PAN-OS, the operating system of Palo Alto Networks firewalls. It allows the firewall itself to collect user-to-IP mapping information by querying directory services (primarily Microsoft Active Directory Domain Controllers) and parsing security event logs. This method is often referred to as "agentless" because no separate software needs to be installed on a dedicated server for the agent functionality itself, although the firewall still acts as an "agent" in collecting the information.
Key Characteristics and Implementation:
- Direct Communication: The firewall's management plane directly communicates with Domain Controllers (DCs) using WMI (Windows Management Instrumentation) or a combination of MSRPC and SMB for event log access. For PAN-OS 9.0 and later, WinRM (Windows Remote Management) can also be used, which is often preferred for security and efficiency.
-
Configuration:
Configured under
Device > User Identification > User-ID Agents. You define "PAN-OS Integrated User-ID Agent" configurations, specifying the server monitoring settings (DCs to monitor, authentication credentials). - Resource Consumption: Utilizes the firewall's management plane CPU and memory. This is a critical consideration for firewall sizing.
- Mapping Storage: User-to-IP mappings are stored locally on the firewall. In a high availability (HA) pair, mappings are synchronized between the active and passive firewalls.
-
Group Mapping:
The firewall also needs to retrieve group information. This is configured under
Device > User Identification > Group Mapping Settings, where you connect to an LDAP server (often the DC itself) to fetch group memberships.
Advantages:
- Simplified Deployment: No need for external agent software installation and maintenance on a separate Windows server, reducing administrative overhead for the agent component itself.
- Centralized Management: User-ID configuration and monitoring are done directly through the PAN-OS web interface, CLI, or Panorama for centralized management of multiple firewalls.
- Suitable for Smaller Deployments: Generally recommended for environments with a limited number of Domain Controllers (typically fewer than 10-15 DCs, though PAN-OS can technically monitor up to 100 sources like DCs or syslog servers depending on the version and firewall model). Performance is key here.
- Lower Latency for Local Mappings: Mappings are processed and stored directly on the firewall that monitors the DCs.
Considerations & Limitations:
- Management Plane Impact: Consumes the firewall's management plane resources (CPU and memory). In environments with many DCs, high logon/logoff rates, or on smaller firewall models, this can impact management interface responsiveness or other management plane tasks.
- Network Connectivity Requirements: The firewall must have direct network connectivity to the Domain Controllers (e.g., ports for WMI/WinRM, SMB, LDAP/LDAPS). This might be challenging in segmented networks.
- Limited Scalability for Very Large Environments: While PAN-OS can monitor up to 100 DCs (PAN-OS 9.0+), performance can degrade. For very large or geographically distributed environments, a dedicated Windows-based agent might be more efficient.
- No Credential Phishing Prevention: The integrated agent does not support the Credential Phishing Prevention feature, which requires a Windows-based User-ID agent to monitor and act on credential submissions.
- Single Point of Collection (Per Firewall): Each firewall or HA pair collects its own mappings if not using Panorama for redistribution. This can lead to redundant polling if multiple firewalls monitor the same DCs. Panorama can help by redistributing mappings collected by one firewall (acting as a master collector) to others.
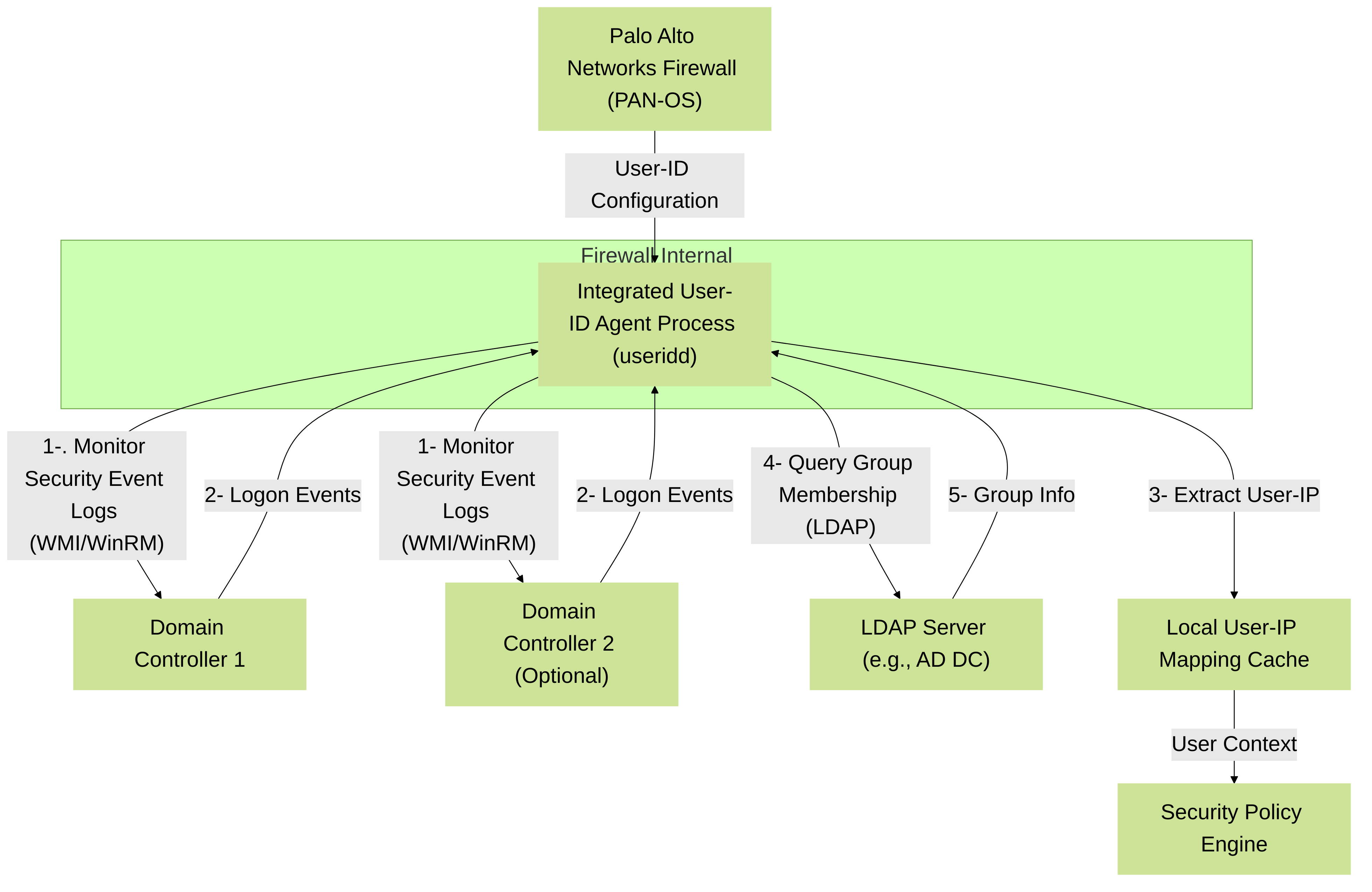
Diagram illustrating the PAN-OS Integrated User-ID Agent process. The firewall directly queries Domain Controllers for logon events and an LDAP server for group memberships, storing mappings locally for policy enforcement.
Windows-Based User-ID Agent (Agent-Based)
The Windows-based User-ID Agent is a dedicated software application installed on a Microsoft Windows server (physical or virtual) within the customer's environment. This agent monitors Domain Controllers for user logon events and collects user-to-IP mapping information, which it then forwards to one or more Palo Alto Networks firewalls or Panorama.
Key Characteristics and Implementation:
- Dedicated Software: Requires installation on a Windows Server (member server is typical; installing on a DC is possible but generally not recommended for resource and security isolation reasons).
- Communication: The agent monitors DCs using WMI or reads event logs forwarded by a WinRM forwarder. It then communicates with the Palo Alto Networks firewalls over TCP port 5007 (by default) to send the collected mappings.
-
Configuration:
The agent is configured through its own GUI on the Windows server. Firewalls are then configured to connect to this agent (
Device > User Identification > User-ID Agents, add a new agent configuration pointing to the Windows server's IP and port). - Resource Offload: Processing for monitoring DCs and compiling mappings is offloaded from the firewall's management plane to the Windows server where the agent is installed.
- Centralized Collection: A single Windows-based agent (or a pair for redundancy) can collect mappings for an entire domain or multiple domains and distribute them to many firewalls.
- Advanced Features: Supports features like Credential Phishing Prevention and Client Probing.
Advantages:
- Offloads Firewall Resources: Preserves the firewall's management plane CPU and memory by handling the User-ID collection tasks on a separate server. This is beneficial for heavily loaded firewalls or smaller models.
- Scalability for Large Environments: Better suited for large, distributed, or multi-domain environments. A single agent can monitor a large number of DCs (hundreds) and serve mappings to many firewalls.
-
Support for Advanced Features:
- Credential Phishing Prevention: The agent works in conjunction with PAN-OS to detect and prevent users from submitting corporate credentials to untrusted websites. This requires the Windows-based agent.
- Client Probing: Can actively probe Windows clients (NetBIOS or WMI) to identify logged-on users if server monitoring misses an event.
- VM Information Sources: Can integrate with vCenter or AWS for user mapping in virtualized environments.
- Flexible Deployment: Can be deployed closer to regional DCs in a distributed environment to minimize WAN traffic from DC monitoring, then forward consolidated mappings to central or regional firewalls.
- Potentially Greater Resiliency: Multiple Windows-based agents can be deployed for redundancy, serving the same set of firewalls.
Considerations & Limitations:
- Requires Dedicated Server: Necessitates a Windows server (and associated licensing, patching, and maintenance) to host the agent software.
- Additional Management Point: The agent software itself needs to be managed, configured, and monitored separately from the firewalls (though firewalls still need to be configured to use it).
- Network Connectivity: The agent server needs connectivity to all monitored DCs and to the firewalls it serves (TCP port 5007 by default to firewalls).
- Potential Latency: There's an extra hop for mappings (DC -> Agent Server -> Firewall), though this is typically minimal.
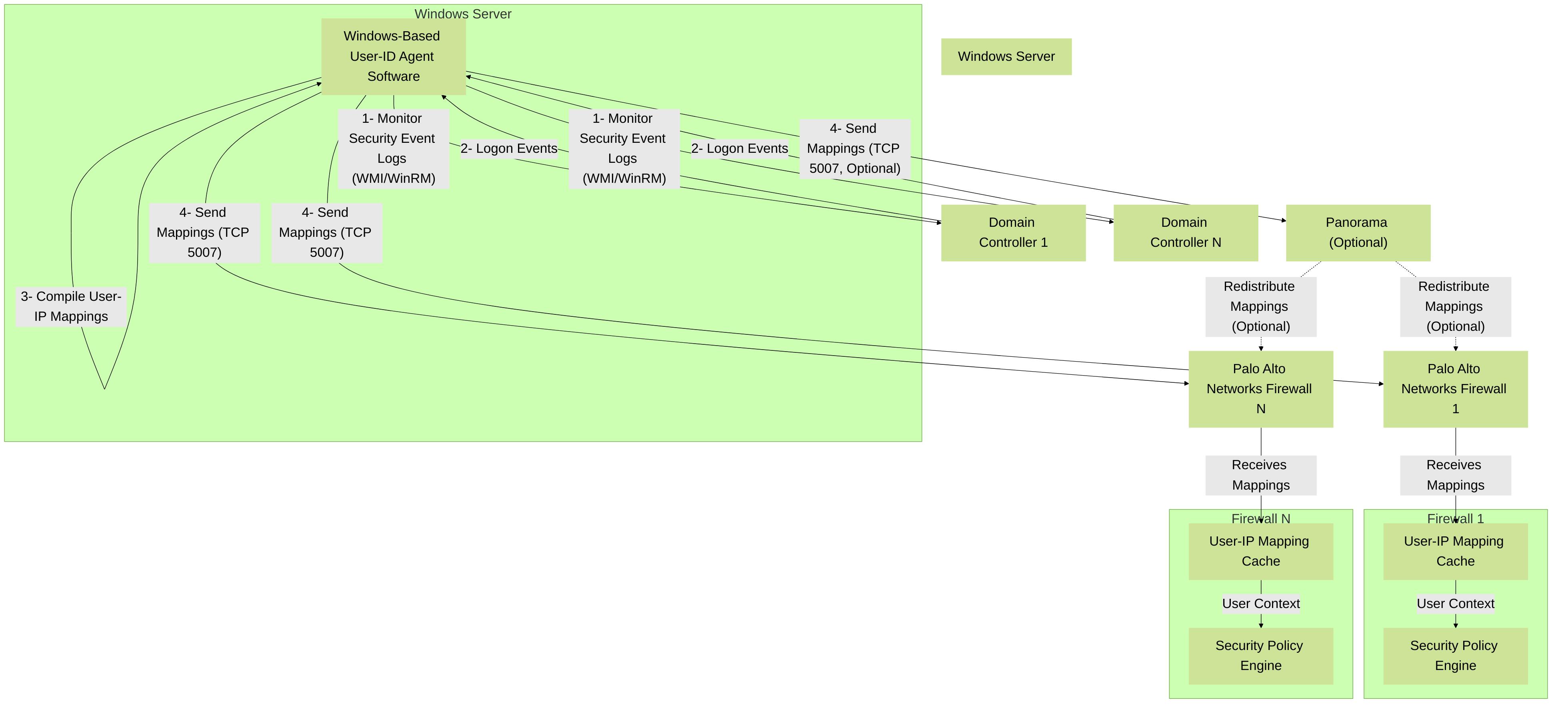
Diagram illustrating the Windows-Based User-ID Agent architecture. The agent on a dedicated server collects mappings from Domain Controllers and forwards them to Palo Alto Networks firewalls and/or Panorama.
Detailed Comparison: Integrated vs. Windows-Based User-ID Agent
| Feature / Aspect | PAN-OS Integrated User-ID Agent | Windows-Based User-ID Agent |
|---|---|---|
| Deployment Model | Built into PAN-OS on the firewall. No separate server software for the agent. | Software installed on a dedicated Windows server. |
| Management | Via firewall GUI/CLI or Panorama. | Agent configured on its Windows host; firewalls configured to connect to the agent. |
| Resource Impact | Consumes firewall management plane (MP) CPU and memory. | Offloads collection processing to the Windows server. Firewall MP primarily handles receiving and storing mappings. |
| Scalability (DC Monitoring) | Good for fewer than 10-15 DCs per firewall/HA pair. Max ~100 sources (PAN-OS 9.0+), but performance is a key factor. | Highly scalable; can monitor hundreds of DCs. Ideal for large and distributed environments. |
| Scalability (Mappings) | Firewall model dependent (e.g., PA-220 supports fewer mappings than a PA-7000 Series). Typically up to 100,000s. | Agent can handle millions of mappings; firewall capacity to store them is still a factor. |
| Advanced Features |
|
|
| Network Requirements | Firewall needs direct access to DCs (WMI/WinRM, SMB, LDAP). | Agent server needs access to DCs. Firewalls need access to agent server (TCP 5007). |
| Ideal Use Cases | Small to medium-sized businesses (SMBs), single-site deployments, environments with limited DCs and direct firewall-to-DC connectivity. | Large enterprises, multi-site/distributed environments, environments requiring credential phishing prevention, or where firewall MP resources are constrained. |
| Redundancy | Relies on firewall HA for agent redundancy. Mappings synced in HA. | Multiple Windows agents can be deployed for redundancy, configured on firewalls with priority. |
| Software Updates | Updated with PAN-OS upgrades. | Agent software updated separately on the Windows server. |
Decision Criteria: Choosing the Right User-ID Agent
Choosing between the Integrated and Windows-Based User-ID Agents depends on a careful evaluation of your environment and security requirements within the Palo Alto Networks ecosystem.
-
Environment Size & Number of Domain Controllers:
- Small to Medium (e.g., <10-15 DCs, <5,000 users): PAN-OS Integrated Agent is often sufficient and simpler if firewall MP resources allow.
- Large (e.g., >15 DCs, many thousands of users, multiple domains): Windows-Based Agent is generally recommended for better scalability and to offload firewall resources.
-
Geographical Distribution:
- Single Site: Integrated Agent can work well.
- Multiple Sites / Distributed DCs: Windows-Based Agent is preferable. Deploy agents regionally to monitor local DCs and minimize WAN traffic. These agents can then send mappings to regional firewalls or a central Panorama for redistribution.
-
Requirement for Advanced Features:
- Credential Phishing Prevention: This feature requires the Windows-Based User-ID Agent. If this is a security goal, the decision is made.
- Client Probing, VM Information Sources: These are also exclusive to the Windows-Based Agent.
-
Firewall Resource Constraints:
- If the firewall's management plane is already heavily utilized (e.g., extensive logging, frequent configuration changes, many VPN tunnels, smaller hardware model), the Windows-Based Agent is a better choice to avoid further burdening the MP.
-
Monitor
show system resources followon the firewall CLI to assess MP load. Highuseriddprocess CPU usage with the integrated agent might indicate a need to switch.
-
Network Architecture & Segmentation:
- If firewalls cannot directly reach all necessary Domain Controllers (due to network segmentation, security policies restricting firewall access to DCs), a Windows-Based Agent placed in a segment with DC access can bridge this gap.
-
Administrative Overhead and Simplicity:
- Integrated Agent: Simpler initial setup as no extra server is involved. Configuration is unified within PAN-OS/Panorama.
- Windows-Based Agent: Requires managing an additional Windows server and the agent software. However, for large environments, this centralized agent can simplify the overall User-ID architecture.
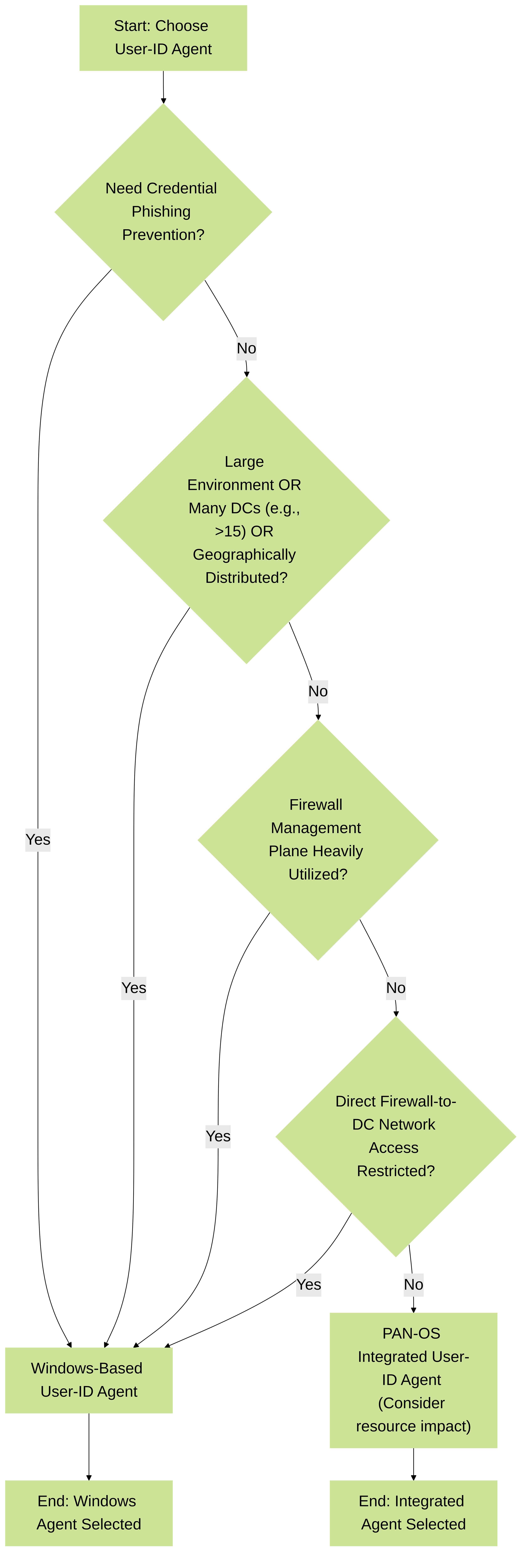
Decision tree for selecting between PAN-OS Integrated and Windows-Based User-ID Agents based on common Palo Alto Networks deployment considerations.
Palo Alto Networks Configuration Highlights
Configuring User-ID involves several components on the Palo Alto Networks firewall and, if applicable, the Windows-based agent.
PAN-OS Integrated User-ID Agent Configuration (Firewall):
-
Enable User-ID on Zones:
Navigate to
Network > Zones. For each zone where you want to identify users, edit the zone and check "Enable User Identification". -
Configure Server Monitoring:
-
Go to
Device > User Identification. In the "User-ID Agents" tab (or "PAN-OS Integrated Agent Setup" in older PAN-OS versions). - Specify your Domain Controllers to monitor. Provide credentials for an account with permissions to read security event logs (typically a domain user in Event Log Readers and Distributed COM Users groups, or use WinRM).
- Select the appropriate connection method (WMI or WinRM). WinRM is generally preferred.
-
Go to
-
Configure Group Mapping:
-
Go to
Device > User Identification > Group Mapping Settings. - Add an LDAP Server Profile pointing to your Active Directory (or other LDAP) server.
- Configure Group Include/Exclude lists as needed.
-
Go to
-
User-ID Timeout Settings:
Configure timeouts under
Device > User Identification > User Identification(tab) to control how long mappings are considered valid. - Commit Changes.
! Example PAN-OS CLI commands (conceptual - actual commands depend on specific setup)
! To check User-ID agent status (Integrated)
> show user user-id-agent state all
! To check IP-user mappings
> show user ip-user-mapping all
! To check group mappings
> show user group list
> show user group name "your_group_name"
Windows-Based User-ID Agent Configuration:
- Install the Agent: Download the User-ID agent software from the Palo Alto Networks support portal and install it on a Windows server.
-
Configure the Agent (on Windows Server):
- Launch the Palo Alto Networks User-ID Agent GUI.
- Discovery: Add Domain Controllers to monitor under "Server Monitoring". Provide credentials.
- Client Probing (Optional): Configure under "Client Probing".
- Syslog (Optional): Configure under "Syslog Filters" if receiving mappings via syslog.
- Palo Alto Networks Firewalls: Under "Palo Alto Networks Firewalls", add the IP addresses of the firewalls (or Panorama) that will receive mappings from this agent. A pre-shared key can be configured for secure communication.
- Service Account: Ensure the User-ID Agent service runs with appropriate permissions.
-
Configure Firewall to Use Windows Agent:
-
On the firewall, navigate to
Device > User Identification > User-ID Agents. - Add a new agent configuration. Enter a name, the IP address of the Windows server running the agent, and the port (default 5007). If a pre-shared key was set on the agent, configure it here.
-
On the firewall, navigate to
- Group Mapping (Firewall): Still configured on the firewall as described for the integrated agent, unless you are sending group information through the agent (less common for AD).
- Commit Changes on Firewall.
User-ID Integration with Security Policy
Once User-ID is configured and mappings are populated, you can leverage this information in Security Policies for granular control.
-
Source User:
In a Security Policy rule (
Policies > Security), the "Source" tab allows you to specify users or groups. - When traffic arrives, the firewall looks up the source IP in its User-ID mapping table.
- If a user is identified, the firewall checks if that user (or any group they belong to) matches the "Source User" field in any policy rule.
-
This allows policies like:
-
Source Zone: Trust, Source Address: any, Source User: 'Domain Admins', Destination Zone: Untrust, Application: ssh, Action: Deny -
Source Zone: Trust, Source Address: any, Source User: 'Marketing_Users', Destination Zone: Untrust, URL Category: social-networking, Action: Allow
-
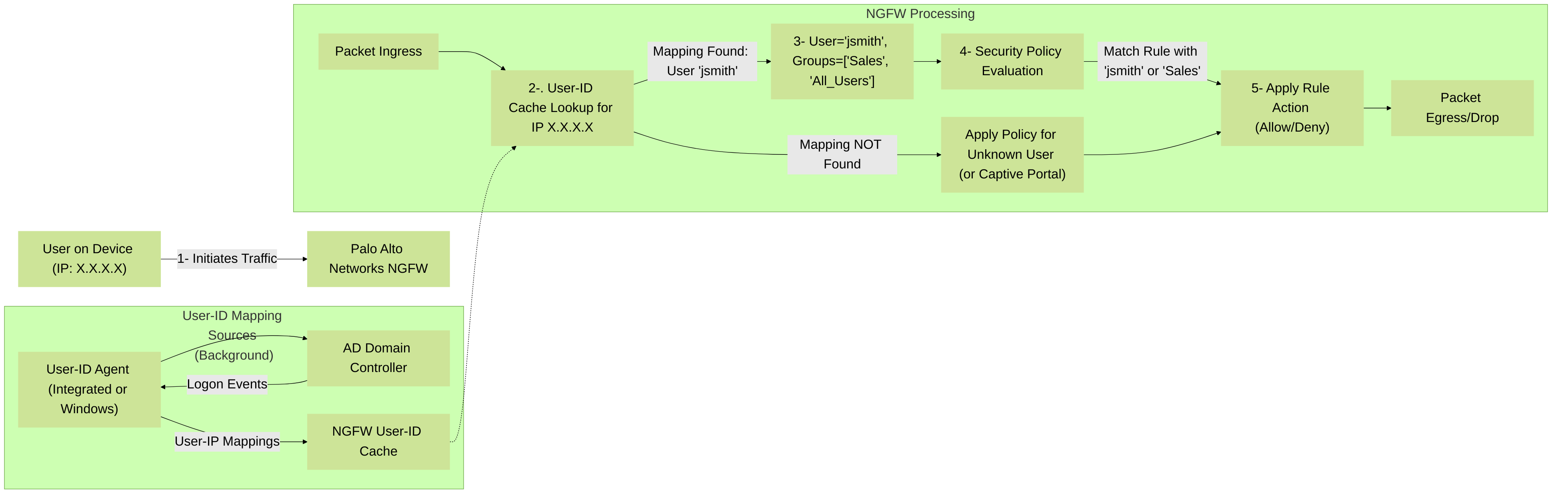
High-level flow showing how a Palo Alto Networks NGFW utilizes User-ID mappings in Security Policy enforcement. Traffic from a user's IP address is matched against the User-ID cache to identify the user and their groups, which are then used for policy evaluation.
Troubleshooting User-ID on Palo Alto Networks Firewalls
Effective troubleshooting is key to maintaining a reliable User-ID deployment.
Common PAN-OS CLI Commands:
-
show user ip-user-mapping all: Displays all current IP-to-user mappings on the firewall. Use options likeip <ip_address>oruser <domain\username>to filter. -
show user user-id-agent state all: Shows the status of configured User-ID agents (both integrated and Windows-based connections). Look for "connected" state. -
show user server-monitor state all: (For Integrated Agent) Shows the status of connections to monitored servers (DCs, Exchange). -
show user group list: Lists all groups known to the firewall via group mapping. -
show user group name "<group_name>": Shows users belonging to a specific group. -
debug user-id dump user-mapping: Dumps the entire user mapping table (can be very large). -
debug user-id dump group-mapping: Dumps group mapping information. -
debug user-id agent <agent_name> statistics: Shows statistics for a specific User-ID agent. -
test user-id-agent ldap-proxy ldap-profile <profile_name> user <username>: Tests LDAP group lookup. -
show counter global filter aspect useridd: Shows various counters related to User-ID processing. -
less mp-log useridd.log: View the User-ID daemon logs on the management plane. -
less dp-log userid.pcap: (Dataplane, if redistribution is used) View User-ID related packet captures on the dataplane.
Common Issues and Troubleshooting Steps:
-
No Mappings or Missing Mappings:
-
Verify agent status (
show user user-id-agent state all). -
Check server monitor status (
show user server-monitor state all) if using integrated agent. - Ensure correct service account permissions on DCs (Event Log Readers, DCOM Users for WMI; WinRM configuration for WinRM).
- Verify network connectivity between firewall/agent and DCs (ports for WMI, WinRM, LDAP).
- Check security logs on DCs for logon events. Are they being generated?
- On Windows Agent: Check agent logs for errors.
- Ensure User-ID is enabled on the relevant zones.
-
Verify agent status (
-
Incorrect Group Mappings:
- Verify LDAP server profile configuration and connectivity.
- Check group include/exclude lists.
-
Use
show user group name "group_in_question"to see if users are listed. -
Ensure the user attribute in LDAP (e.g.,
sAMAccountName) matches what's being mapped.
-
High Management Plane CPU (Integrated Agent):
-
show system resources followand look for highuseriddCPU usage. - Reduce the number of DCs monitored by a single firewall if possible.
- Consider switching to a Windows-based User-ID agent.
- Adjust User-ID refresh timers if appropriate, but be mindful of stale mappings.
-
-
Intermittent Connectivity to Agent/DCs:
- Check for network issues (latency, packet loss) between components.
- Ensure no intermediate firewalls or security devices are blocking necessary ports.
Palo Alto Networks Best Practices for User-ID Deployment
-
Use Redundancy:
- For Windows-based agents, deploy at least two agents for high availability. Configure firewalls to use both, with one as primary.
- For Integrated Agent, rely on firewall HA.
- Principle of Least Privilege: Use dedicated service accounts for User-ID with only the necessary permissions to read event logs and/or query LDAP. Avoid using domain admin accounts.
- Monitor Agent Health: Regularly check the status of User-ID agents and server monitoring connections (via firewall CLI/GUI, Panorama, or SNMP).
-
Keep Software Updated:
- Ensure PAN-OS is on a recommended release.
- Keep Windows-based User-ID agent software updated to the latest version for bug fixes and new features.
-
Optimize Server Monitoring:
- Monitor only necessary DCs. Avoid monitoring Read-Only Domain Controllers (RODCs) if writable DCs are available, as RODCs may not have all logon events. However, in some distributed scenarios monitoring RODCs might be necessary if they are the primary authentication point for a location. The User-ID agent primarily looks for Event ID 4768, 4769 (Kerberos TGT/Service tickets) and 4624 (Successful logon).
- For Windows Agents, deploy them geographically close to the DCs they monitor to reduce WAN latency for log polling.
- Understand Mapping Timeouts: Configure User-ID timeouts (Idle Timeout, Max Age) appropriately for your environment to balance accuracy with resource usage. Shorter timeouts mean more frequent updates but can also increase load.
- Use Panorama for Centralized Management: If you have multiple firewalls, use Panorama to manage User-ID agent configurations and potentially redistribute User-ID mappings. Panorama can act as a "User-ID Hub," collecting mappings from agents or integrated firewalls and distributing them to other connected firewalls.
- Implement Group Mapping Effectively: Only map groups that are actually used in security policies to reduce clutter and processing load. Use Group Include Lists.
- Consider WinRM over WMI: For integrated agent monitoring of DCs, WinRM (Windows Remote Management) is generally more secure and efficient than WMI. It's the preferred method from PAN-OS 9.0 onwards.
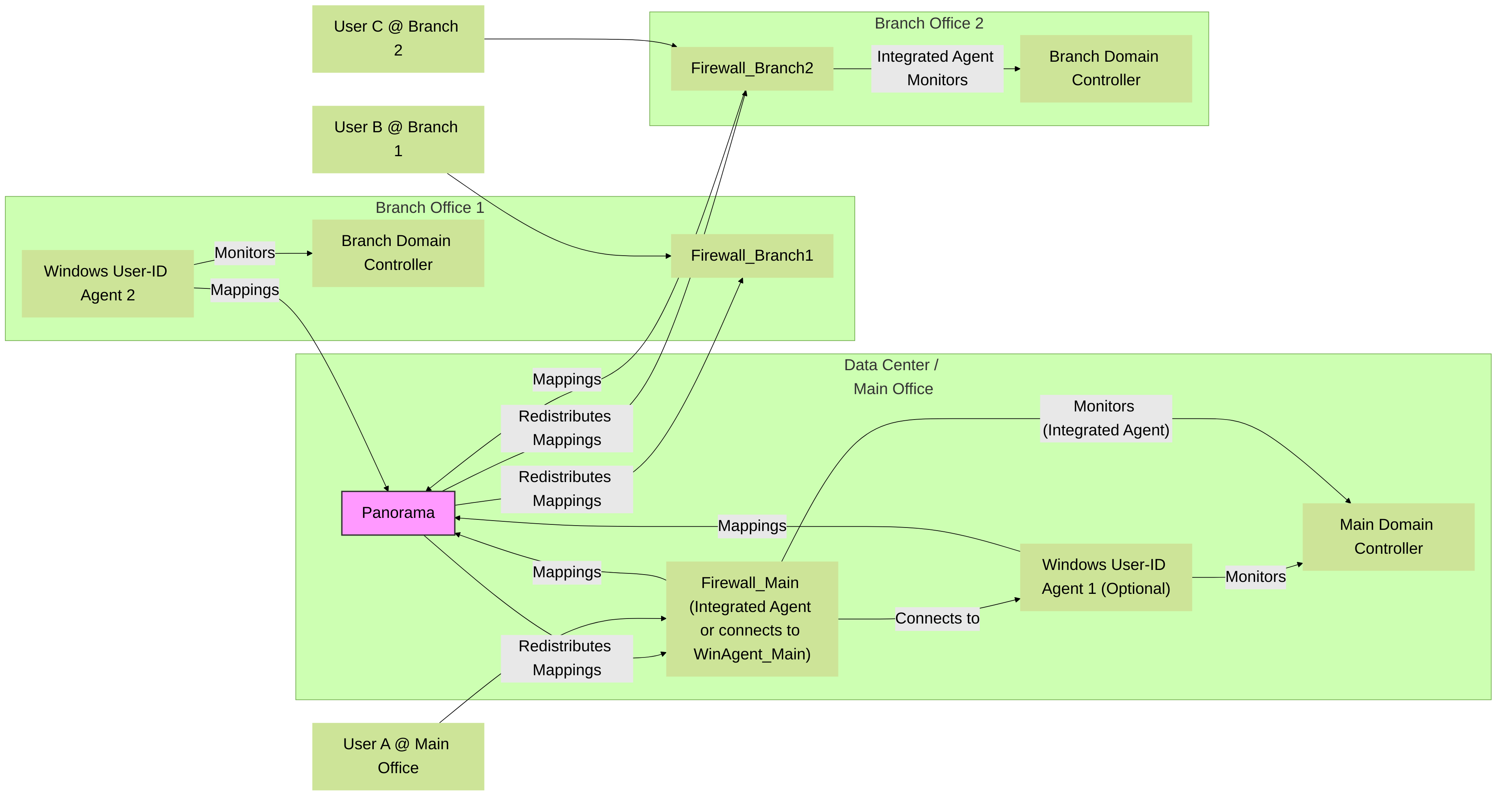
Conceptual diagram showing a distributed User-ID deployment strategy with Panorama. Regional Windows-based agents or firewalls with Integrated Agents collect local mappings. Panorama aggregates these mappings and redistributes them, ensuring all firewalls have a comprehensive User-ID view. This optimizes WAN traffic and centralizes management.