Palo Alto Networks Decryption Policies: A Deep Dive for PCNSE
The Imperative of Decryption in Modern Network Security
Currently the vast majority of internet traffic is encrypted using protocols like TLS/SSL and SSH. While encryption is vital for confidentiality and integrity, it also creates a significant blind spot for security devices. Threat actors leverage encryption to conceal malware, command-and-control (C2) communications, data exfiltration, and other malicious activities. Palo Alto Networks Next-Generation Firewalls (NGFWs) address this challenge through robust Decryption Policies, enabling deep packet inspection of encrypted traffic to enforce security policies and prevent threats.
Decryption Policies are a cornerstone of the Palo Alto Networks Security Operating Platform, allowing organizations to regain visibility and control over encrypted flows. Without decryption, critical security services like App-ID™, Threat Prevention (IPS, Antivirus, Anti-Spyware), URL Filtering with PAN-DB, WildFire, and Data Loss Prevention (DLP) cannot effectively inspect the content of encrypted sessions, severely limiting their efficacy.
This guide provides a comprehensive exploration of Decryption Policies within the Palo Alto Networks ecosystem, focusing on concepts, configuration, best practices, and troubleshooting essential for PCNSE candidates and network security professionals.
CRITICAL (Palo Alto Networks): Failing to implement decryption means you are likely missing a significant portion of threats traversing your network. Palo Alto Networks strongly advocates for a "decrypt for visibility" approach, especially for outbound internet traffic, to maximize the effectiveness of its security subscriptions.
Understanding Decryption Policy Fundamentals
Decryption Policies on a Palo Alto Networks firewall determine which encrypted traffic should be decrypted, how it should be decrypted (or explicitly not decrypted), and what security checks to apply during and after decryption. They work in conjunction with Decryption Profiles , which define the specific parameters for decryption, such as allowed cipher suites, protocol versions, and certificate validation settings.
Key characteristics of Decryption Policies:
- Granular Control: Rules can be based on source/destination zones, addresses, users (via User-ID™), URL categories, and services.
- Ordered Evaluation: Similar to Security Policies, Decryption Policy rules are evaluated from top to bottom. The first matching rule dictates the action.
-
Action Types:
-
Decrypt: Instructs the firewall to attempt decryption. -
No-decrypt: Explicitly bypasses decryption for matching traffic, often used for policy-based exclusions (e.g., financial, healthcare). -
Block: Blocks the session (less common, usually handled by Security Policy).
-
-
Decryption Types (when action is 'Decrypt'):
- SSL Forward Proxy: For outbound TLS/SSL traffic initiated by internal clients to external servers. The firewall acts as a "man-in-the-middle" (MITM).
- SSL Inbound Inspection: For inbound TLS/SSL traffic destined for internal servers (e.g., web servers, application servers). The firewall uses the server's actual certificate and private key to decrypt.
- SSH Proxy: For SSH traffic, allowing inspection of SSH commands and file transfers.
PCNSE/PCNSA Exam Note (Palo Alto Networks): Understand the difference between a Decryption Policy (what to decrypt) and a Decryption Profile (how to decrypt). You attach a profile to a policy rule. Also, know the three main decryption types: SSL Forward Proxy, SSL Inbound Inspection, and SSH Proxy.
Prerequisites for Implementing Decryption Policies
Before successfully creating and activating Decryption Policy rules, several crucial components must be in place on the PAN-OS device (NGFW or Panorama for managing multiple firewalls).
1. Certificates: The Foundation of Trust
Certificates are fundamental to SSL/TLS decryption. The specific certificates required depend on the decryption type:
-
For SSL Forward Proxy:
-
Forward Trust Certificate:
A Certificate Authority (CA) certificate that the firewall uses to re-sign (impersonate) server certificates presented by external websites. This CA certificate (or its root/issuing CA)
must
be trusted by client browsers/systems in the organization. This is typically a self-signed CA generated on the firewall or an internal subordinate CA certificate signed by an enterprise CA.
PAN-OS Path:Device > Certificate Management > Certificates > Generate(for self-signed) orImport. -
Forward Untrust Certificate:
A CA certificate used by the firewall to re-sign server certificates from sites whose original certificates are untrusted (e.g., expired, self-signed, wrong CN). This presents a clear warning to the user, indicating a problem with the original server certificate.
PAN-OS Path:Device > Certificate Management > Certificates > GenerateorImport.
PCNSE/PCNSA Exam Note (Palo Alto Networks Q191): For SSL Forward Proxy, the Forward Trust certificate is paramount . Without it, or if clients don't trust it, users will receive certificate errors for all decrypted sites, rendering decryption impractical.
-
Forward Trust Certificate:
A Certificate Authority (CA) certificate that the firewall uses to re-sign (impersonate) server certificates presented by external websites. This CA certificate (or its root/issuing CA)
must
be trusted by client browsers/systems in the organization. This is typically a self-signed CA generated on the firewall or an internal subordinate CA certificate signed by an enterprise CA.
-
For SSL Inbound Inspection:
-
Server Certificate(s) and Private Key(s):
The actual SSL/TLS certificate(s) and corresponding private key(s) of the internal servers you want to protect (e.g., your corporate web server). These must be imported onto the firewall. The firewall uses these to decrypt traffic destined for these servers.
PAN-OS Path:Device > Certificate Management > Certificates > Import. Ensure you import both the certificate and its private key.
-
Server Certificate(s) and Private Key(s):
The actual SSL/TLS certificate(s) and corresponding private key(s) of the internal servers you want to protect (e.g., your corporate web server). These must be imported onto the firewall. The firewall uses these to decrypt traffic destined for these servers.
-
For SSH Proxy:
- SSH Proxy does not directly use X.509 certificates in the same way SSL/TLS decryption does for policy creation. However, the firewall acts as an MITM for SSH sessions, managing host keys.
2. Decryption Profiles
Decryption Profiles define the parameters and checks applied to traffic selected for decryption or no-decryption by a Decryption Policy rule. Separate profiles can be created for SSL Forward Proxy, SSL Inbound Inspection, SSH Proxy, and even for "No Decrypt" actions (to enforce minimum checks like blocking sessions with untrusted issuers even if not fully decrypting).
Key settings within Decryption Profiles include:
- SSL Protocol Settings: Min/Max SSL/TLS versions supported.
- Certificate Revocation Checks: CRL and/OCSP options.
- Blocked Ciphers/Algorithms: Specifying weak or unsupported cryptographic elements.
- Server Certificate Verification Options: Controls for handling expired, untrusted, or CN-mismatch certificates.
- Failure Checks: Actions for unsupported modes, resource limits, etc.
Objects > Decryption > Decryption Profile > Add
.
Gotcha! (Palo Alto Networks): Attaching the default Decryption Profile might not meet your organization's security requirements. Always create custom Decryption Profiles tailored to your policies, especially regarding server certificate validation and protocol versions.
3. Supporting Objects (Optional but Highly Recommended)
For creating granular and effective policies, pre-configuring these objects is beneficial:
- Address Objects/Groups: For defining specific source/destination IP addresses or networks.
- User Groups (User-ID): Leveraging User-ID integration allows policies based on Active Directory groups or other user repositories.
- URL Categories: Utilizing PAN-DB URL filtering categories (requires a license) or custom URL categories for fine-grained control (e.g., decrypt "social-networking" but not "financial-services").
-
Service Objects/Groups:
Defining specific TCP/UDP ports (e.g.,
service-httpsfor TCP/443,service-sshfor TCP/22).
Configuration Steps for Decryption Policies (PAN-OS GUI)
Creating a Decryption Policy rule involves defining match criteria and the action to take. The process is performed via the PAN-OS web interface (or Panorama for centralized management).
- Navigate to Policies > Decryption .
- Click Add at the bottom of the page to create a new rule.
-
General Tab:
-
Name:
Assign a descriptive name (e.g.,
Decrypt_Outbound_HighRisk_Categories,NoDecrypt_Financial_Sites). -
Rule Type:
Typically
Universal. Can beintrazoneorinterzoneif specific zone logic is needed (less common for decryption than security policy). - Tags: Apply tags for organization and filtering.
- Description: Provide details about the rule's purpose.
- Audit Comment: Log changes for auditing.
-
Name:
Assign a descriptive name (e.g.,
-
Source Tab:
-
Source Zone:
Select the zone(s) from which the encrypted traffic originates (e.g.,
trust,lan). -
Source Address:
Specify source IP addresses, address objects, or address groups.
Anyis common for broad outbound rules. -
Source User:
Specify users or user groups if User-ID is configured.
Anycan be used.
-
Source Zone:
Select the zone(s) from which the encrypted traffic originates (e.g.,
-
Destination Tab:
-
Destination Zone:
Select the zone(s) where the encrypted traffic is destined (e.g.,
untrust,internetfor outbound; internal server zones for inbound). -
Destination Address:
Specify destination IP addresses.
Anyfor general outbound SSL Forward Proxy. Specific internal server IPs/objects for SSL Inbound Inspection.
-
Destination Zone:
Select the zone(s) where the encrypted traffic is destined (e.g.,
-
Service/URL Category Tab:
-
Service:
Specify the service. Commonly
service-httpsfor SSL/TLS,service-sshfor SSH. Usingapplication-defaultcan be powerful but ensure it aligns with expectations, as it relies on App-ID to identify the application first.PCNSE/PCNSA Exam Note (Palo Alto Networks): While
application-defaultcan be used in the Service field of a Decryption Policy, remember that for encrypted traffic, App-ID often relies on indicators like Server Name Indication (SNI) or certificate details. Full App-ID might only be available after decryption. -
URL Category:
Select URL categories (e.g.,
malware,phishing,social-networking, or custom categories). This is a very common and effective criterion for SSL Forward Proxy rules.PCNSE/PCNSA Exam Note (Palo Alto Networks Q278): Source User, URL Category, and Source/Destination Address/Zone are all valid match criteria for Decryption Policy rules.
-
Service:
Specify the service. Commonly
-
Options Tab: This is where the core action is defined.
-
Action:
-
Decrypt: Attempts to decrypt the traffic. This enables further inspection by other security services. -
No-decrypt: Traffic matching this rule will not be decrypted. This is for explicit exclusions. -
Block: (Rarely used here) Blocks the session. Security policy is generally preferred for blocking.
-
-
Type (only if Action is 'Decrypt'):
-
SSL Forward Proxy: For outbound TLS/SSL. Requires Forward Trust/Untrust certificates. -
SSL Inbound Inspection: For inbound TLS/SSL. Requires imported server certificate and private key; select the appropriate Server Certificate from the dropdown. -
SSH Proxy: For SSH traffic inspection.
PCNSE/PCNSA Exam Note (Palo Alto Networks Q189): You must know these three decryption 'Types' (SSL Forward Proxy, SSL Inbound Inspection, SSH Proxy) and when each is used. The 'Type' field is only configurable if the 'Action' is 'Decrypt'.
-
-
Decryption Profile:
Select the appropriate Decryption Profile configured in
Objects > Decryption > Decryption Profile
. This is crucial.
- For 'Decrypt' actions, select a profile configured for SSL Forward Proxy, SSL Inbound Inspection, or SSH.
- For 'No-decrypt' actions, you can select a "No Decryption" type profile (which can still perform basic checks like blocking untrusted issuers or specific TLS versions).
-
Log Settings:
- Log unsuccessful TLS/SSL handshakes: Enabled by default. Logs sessions where decryption failed (e.g., client doesn't trust Forward Trust CA, protocol issues).
- Log successful TLS/SSL handshakes: Not enabled by default. Enable this for visibility into successfully decrypted sessions. This can generate significant log volume.
- Log Forwarding: Configure log forwarding to Panorama, SIEM, or syslog servers.
-
Action:
- Click OK to save the rule.
- Rule Order: Drag and drop the rule to its correct position. Policy evaluation is top-down. More specific rules should generally be placed above more general rules. "No-decrypt" rules for sensitive categories should be placed above general decryption rules.
-
Commit:
Commit the changes to activate the policy on the firewall.
CLI:commit
Decryption Policy Evaluation Logic
Understanding how PAN-OS processes traffic in relation to Decryption Policies is critical. The firewall first checks the Security Policy. If a Security Policy rule allows the session, the firewall then evaluates the Decryption Policy.
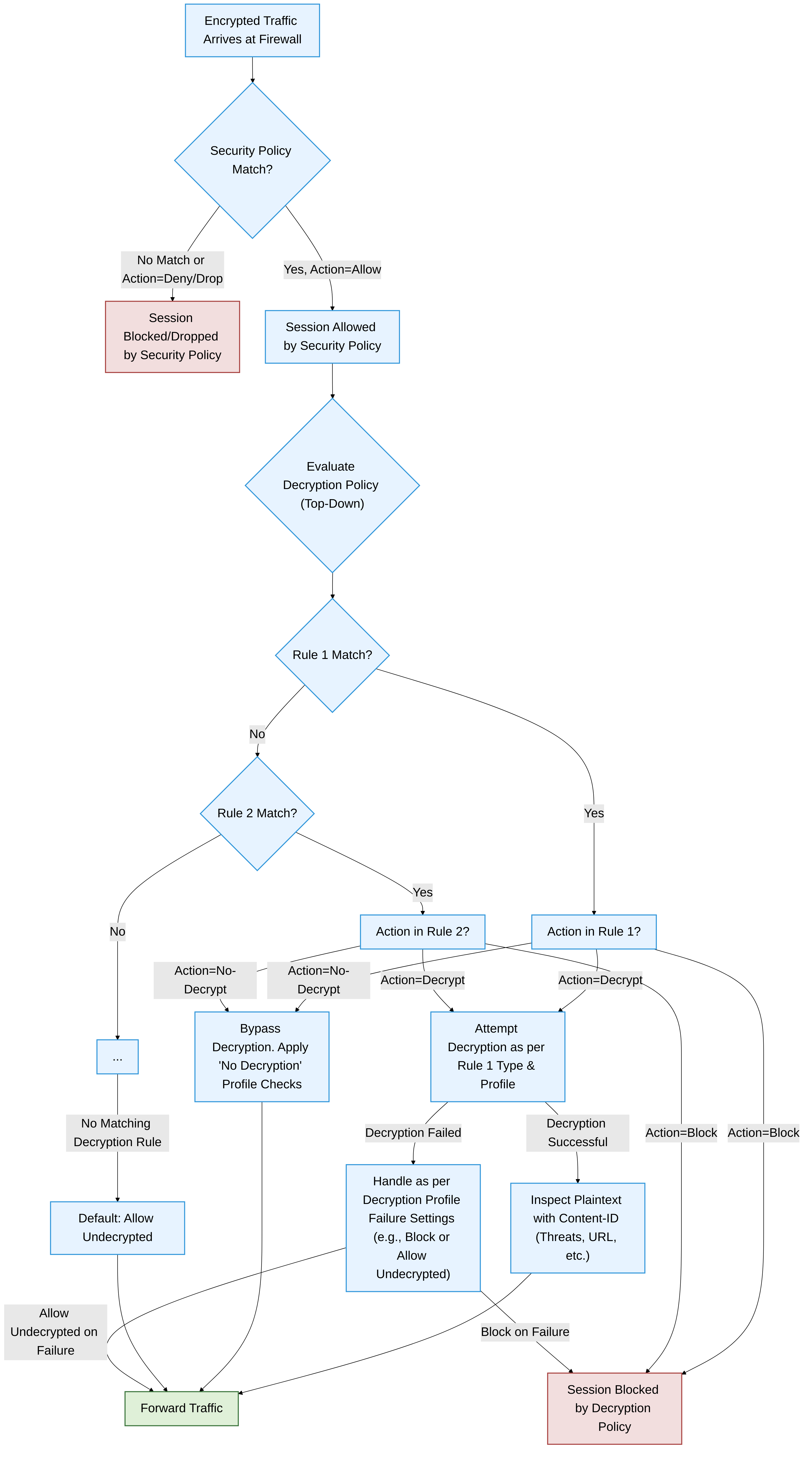
Diagram illustrating the interaction between Security Policy and Decryption Policy evaluation in PAN-OS. If no Decryption Policy rule is matched, traffic allowed by Security Policy passes through undecrypted.
CRITICAL (Palo Alto Networks): If an encrypted session is allowed by Security Policy but does not match any rule in the Decryption Policy, it will be allowed through undecrypted by default . This is a common reason for missed threats if Decryption Policies are not comprehensive.
Deep Dive into Decryption Types
1. SSL Forward Proxy Decryption
SSL Forward Proxy is used to decrypt outbound SSL/TLS traffic initiated by clients within the protected network to external servers (e.g., users browsing HTTPS websites).
-
Mechanism:
The firewall acts as a Man-in-the-Middle (MITM).
- Client initiates an SSL/TLS connection to an external server.
- The firewall intercepts this request.
- The firewall establishes its own SSL/TLS session with the external server, validating the server's certificate.
- The firewall generates a new certificate for the requested domain/server and signs it with its Forward Trust CA certificate .
- This impersonation certificate is presented to the client.
- If the client trusts the firewall's Forward Trust CA, the SSL/TLS session is established between the client and the firewall.
- The firewall now has two SSL/TLS sessions: one with the client and one with the server. It decrypts traffic from one, inspects it, re-encrypts it, and forwards it on the other session.
-
Key PAN-OS Components:
- Forward Trust Certificate (must be trusted by clients).
- Forward Untrust Certificate (for sites with bad original certs).
- SSL Forward Proxy Decryption Profile.
-
Decryption Policy rule with Action:
Decrypt, Type:SSL Forward Proxy.
- Common Use Cases: Inspecting user web browsing for malware, preventing C2 over HTTPS, enforcing URL filtering on encrypted sites, applying WildFire analysis to downloaded files over HTTPS.
-
Challenges:
- Certificate Pinning: Some applications and websites use certificate pinning, where the application expects a specific server certificate or public key. SSL Forward Proxy breaks this, as the client sees the firewall's impersonation certificate. Such sites/applications often need to be excluded from decryption.
- Client Trust: Distributing and ensuring client trust for the Forward Trust CA is a critical deployment step. Without it, users get certificate errors.
- Mutual TLS (mTLS): Sites requiring client certificates for authentication may not work with SSL Forward Proxy unless specific configurations are made, often requiring exclusion.
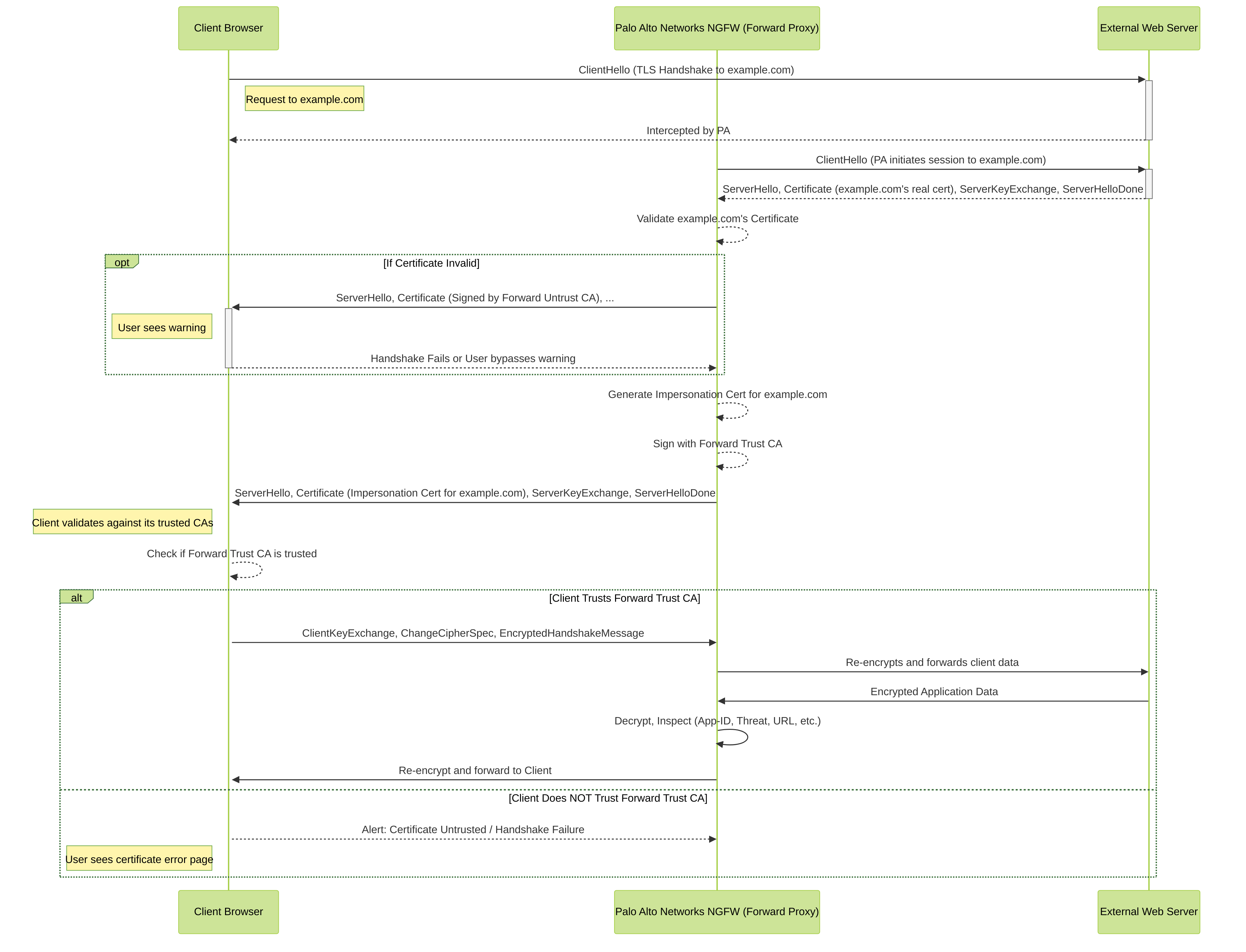
Simplified SSL Forward Proxy handshake sequence showing the Palo Alto Networks NGFW acting as a Man-in-the-Middle. Client trust in the Forward Trust CA is essential.
2. SSL Inbound Inspection
SSL Inbound Inspection is used to decrypt SSL/TLS traffic destined for internal servers that are protected by the Palo Alto Networks firewall (e.g., corporate web servers, application servers, mail servers).
-
Mechanism:
The firewall uses the actual server's certificate and private key to decrypt incoming connections.
-
External client initiates an SSL/TLS connection to an internal server (e.g.,
yourcompany.com). -
The firewall, configured with the certificate and private key for
yourcompany.com, terminates the SSL/TLS session from the client. - The firewall decrypts the traffic and inspects it using its security services (App-ID, Threat Prevention, etc.).
- If the traffic is clean, the firewall can optionally re-encrypt it and forward it to the actual internal server, or forward it in clear text if the connection between firewall and server is on a trusted segment. For true end-to-end encryption visibility with re-encryption to the server, the firewall establishes a new SSL session to the internal server.
-
External client initiates an SSL/TLS connection to an internal server (e.g.,
-
Key PAN-OS Components:
- Server Certificate and Private Key (imported onto the firewall).
- SSL Inbound Inspection Decryption Profile.
-
Decryption Policy rule with Action:
Decrypt, Type:SSL Inbound Inspection, and the specific server certificate selected.
- Common Use Cases: Protecting web servers from attacks hidden in SSL (e.g., SQL injection, XSS over HTTPS), preventing malware uploads to internal systems, inspecting encrypted traffic for data exfiltration attempts from compromised internal servers.
-
Considerations:
- Private Key Security: The private key(s) of your server(s) must be uploaded to the firewall. Secure management of these keys is critical. HSM integration is supported on some PA-Series models for enhanced key protection.
- Performance: Decrypting all inbound traffic to busy servers can be resource-intensive. Apply SSL Inbound Inspection selectively to critical servers or use hardware-assisted decryption available on higher-end PA-Series models.
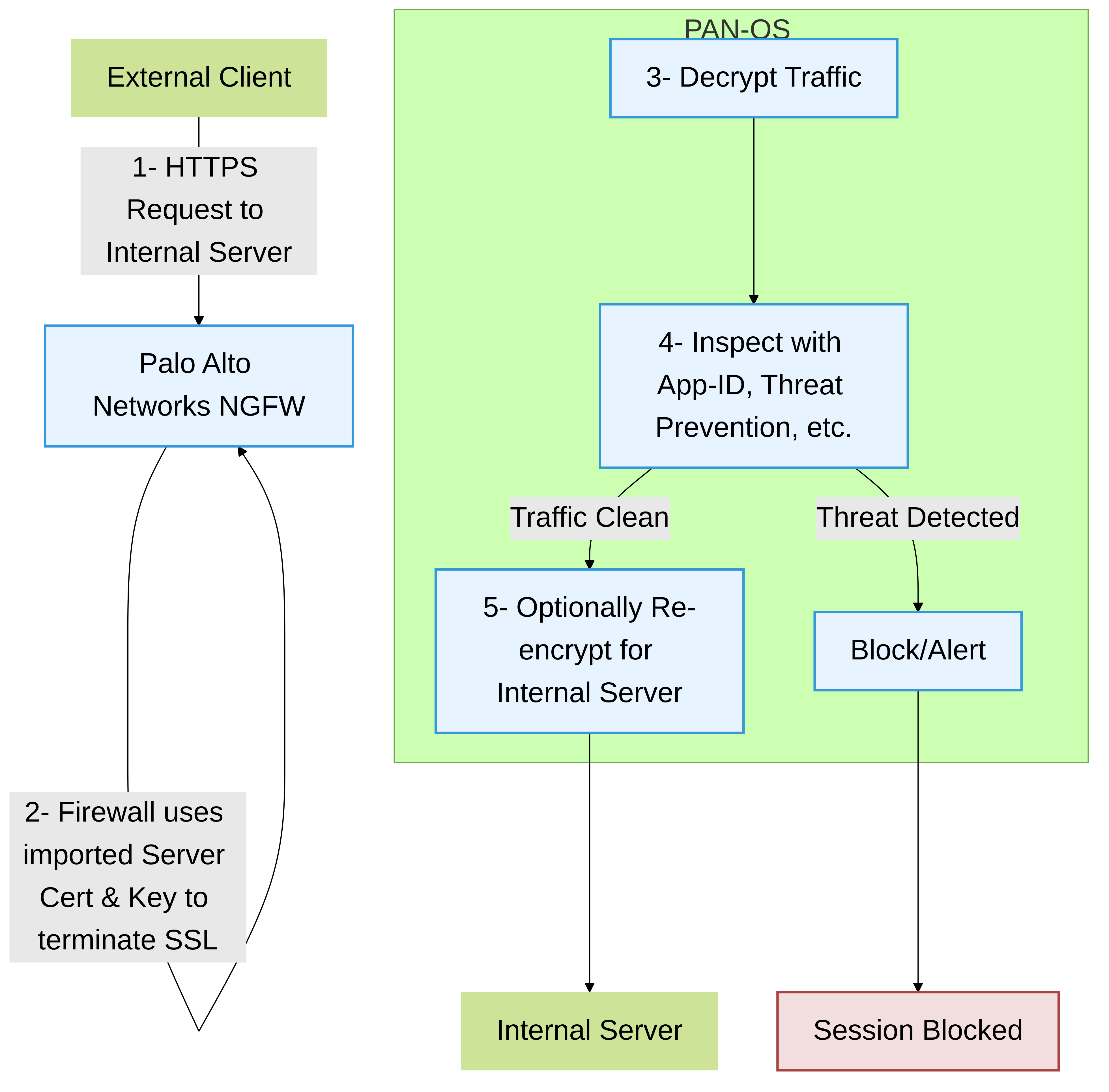
SSL Inbound Inspection flow. The Palo Alto Networks firewall uses the server's certificate and private key to decrypt and inspect traffic before forwarding it to the internal server.
3. SSH Proxy (SSH Decryption)
SSH Proxy allows the Palo Alto Networks firewall to decrypt and inspect SSH (Secure Shell) traffic. This provides visibility into commands executed, files transferred (SFTP/SCP), and port forwarding attempts within SSH sessions.
-
Mechanism:
The firewall acts as an MITM for SSH sessions. It terminates the client's SSH connection and establishes a new SSH connection to the destination server.
- When a client connects, the firewall presents its own SSH host key.
- Users might see a warning about a changed host key on their first connection through the proxy.
-
Key PAN-OS Components:
- SSH Proxy Decryption Profile (defines allowed algorithms, key exchange methods, etc.).
-
Decryption Policy rule with Action:
Decrypt, Type:SSH Proxy.
-
Inspection Capabilities:
- Command Logging: Log executed commands (requires specific configuration in the profile).
- File Transfer Control: Block or allow file transfers, log transferred filenames.
- Port Forwarding Control: Block or allow SSH port forwarding (tunneling).
- Common Use Cases: Auditing administrator access to sensitive systems, preventing unauthorized file transfers over SSH, blocking malicious SSH tunneling.
Gotcha! (Palo Alto Networks): SSH Proxy changes the server host key that the client sees. This can cause warnings for users if they have previously connected directly to the server. Communication and potentially pre-distributing the firewall's SSH proxy host key might be necessary in some environments.
4. "No Decrypt" Action: Policy-Based Exclusions
The
No-decrypt
action in a Decryption Policy rule explicitly tells the firewall
not
to decrypt matching traffic. This is used for
policy-based exclusions
rather than technical ones.
-
Purpose:
- Privacy Concerns: Excluding categories like financial services, healthcare, or government due to privacy regulations or corporate policy.
- User Experience: Some sensitive applications (e.g., banking apps) might behave unexpectedly or raise alarms if traffic is decrypted, even if technically possible.
-
Decryption Profile for "No Decrypt":
Even when not decrypting, you can attach a "No Decryption" type Decryption Profile. This profile can still enforce certain checks, such as:
- Blocking sessions with untrusted issuers or expired certificates.
- Blocking sessions using weak SSL/TLS protocol versions or ciphers.
- Placement: "No Decrypt" rules for sensitive categories should typically be placed above broader "Decrypt" rules in the policy set to ensure they are matched first.
Managing Decryption Exclusions: Policy vs. Technical
PAN-OS provides two primary mechanisms for excluding traffic from SSL/TLS decryption:
-
Decryption Policy Rule with "No-decrypt" Action:
- Purpose: For policy-driven exclusions (e.g., privacy, legal compliance for specific URL categories like finance or healthcare).
- Criteria: Based on standard policy match criteria (zones, addresses, users, URL categories, services).
-
Configuration:
Policies > Decryption > Add Rule (Action: No-decrypt).
-
SSL Decryption Exclusion List (Global Exclusion List):
-
Purpose:
For
technical
exclusions where decryption breaks applications or websites. This is often due to:
- Certificate Pinning
- Mutual TLS (mTLS) where the client presents a certificate
- Applications with non-standard TLS implementations
- Specific embedded applications or updaters that fail if the certificate chain is altered.
- Criteria: Based on Server Name Indication (SNI) in the Client Hello, or Common Name (CN)/Subject Alternative Name (SAN) in the server certificate. Can also exclude based on applications identified by App-ID.
-
Configuration:
Device > Setup > Content-ID > SSL Decryption Exclusion. Here you can add hostnames (e.g.,*.example.com,specific.service.net) or select applications.
-
Purpose:
For
technical
exclusions where decryption breaks applications or websites. This is often due to:
PCNSE/PCNSA Exam Note (Palo Alto Networks): Know the difference and appropriate use cases for "No-decrypt" policy rules versus the global SSL Decryption Exclusion list. Policy-based exclusions (e.g., "Don't decrypt financial sites for privacy reasons") use a "No-decrypt" rule. Technical exclusions (e.g., "This app breaks if decrypted due to certificate pinning") use the SSL Decryption Exclusion list found under Device settings.
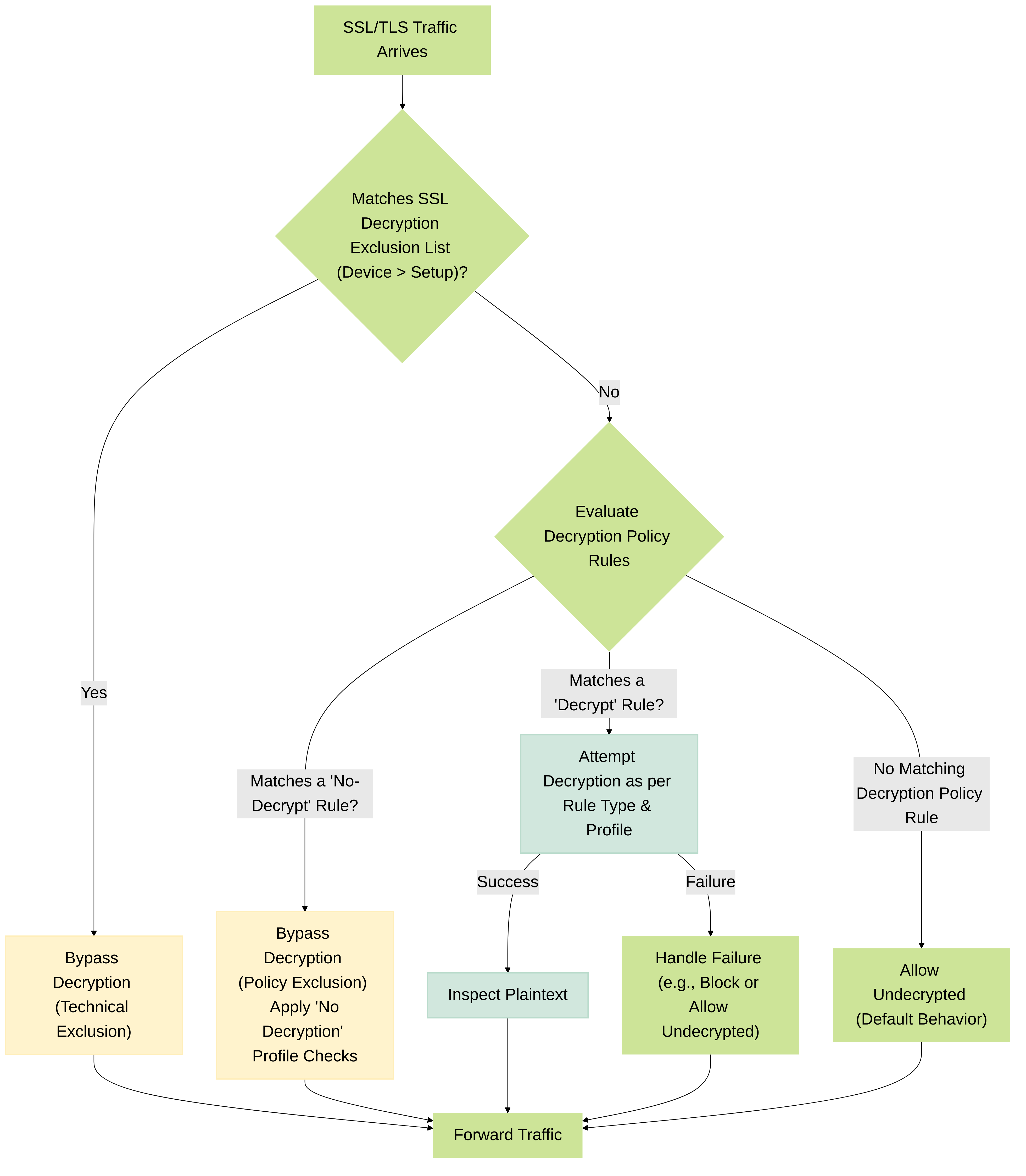
Decision flow showing how PAN-OS handles SSL/TLS traffic with respect to both the global SSL Decryption Exclusion list and Decryption Policy rules.
Best Practices for Creating and Managing Decryption Policies
-
Start with a Phased Approach:
- Begin by decrypting high-risk URL categories (e.g., malware, phishing, questionable, newly-registered-domains).
- Pilot decryption with a small group of users or non-critical systems to identify potential issues.
- Gradually expand decryption scope based on risk appetite and observed impact.
-
Be Specific with "No Decrypt" Rules:
- Clearly define categories that should not be decrypted for policy reasons (e.g., financial, healthcare). Place these rules high in the policy list.
- Use a dedicated "No Decryption" profile for these rules to still block sessions with invalid certificates or weak protocols if desired.
-
Use the SSL Decryption Exclusion List for Technical Breakage:
Do not clutter your Decryption Policy with "No Decrypt" rules for sites that break due to pinning or mTLS. Add these to the global exclusion list under
Device > Setup > Content-ID. - Educate Users: Inform users about SSL Forward Proxy decryption. Explain that they might see certificate warnings if they try to access sites with invalid certificates (as the firewall's Forward Untrust certificate will be presented). Explain the purpose of the Forward Trust CA.
- Maintain Certificate Health: Ensure your Forward Trust and Forward Untrust certificates are not expired. Regularly review and update imported server certificates for SSL Inbound Inspection.
- Leverage User-ID: Integrate User-ID to create policies based on user groups, allowing for different decryption strategies for different departments or roles (e.g., decrypt more for standard users, less for developers working with sensitive code repositories).
- Customize Decryption Profiles: Don't rely on default profiles. Create profiles that enforce your organization's security standards for TLS versions, cipher suites, and certificate validation.
-
Enable Logging:
- Log unsuccessful TLS/SSL handshakes (enabled by default) to identify issues like clients not trusting the Forward Trust CA or sites using unsupported protocols/ciphers.
- Consider logging successful handshakes for a period during rollout or for specific high-interest traffic, but be mindful of log volume.
- Forward decryption logs to Panorama or a SIEM for analysis and alerting.
-
Regularly Review and Audit:
- Periodically review decryption logs to identify sites causing issues or new applications that might need exclusion.
- Audit decryption policies and profiles to ensure they align with current security requirements and best practices.
- Check the Palo Alto Networks Applipedia™ for applications known to have issues with decryption.
-
Monitor Performance:
Decryption is CPU-intensive. Monitor firewall CPU utilization (
show system resourcesCLI, or ACC/Dashboard in GUI) after implementing decryption. Ensure your firewall model is adequately sized for your decryption needs.CRITICAL (Palo Alto Networks): Decryption significantly increases the processing load on the firewall. Always factor in decryption requirements when sizing a Palo Alto Networks NGFW. Refer to the PA-Series datasheets for decryption throughput numbers.
- Backup Certificates and Private Keys: Securely backup all critical certificates and their private keys, especially the Forward Trust CA key and any server private keys imported for Inbound Inspection.
Impact of Decryption on Firewall Performance
Decrypting and re-encrypting traffic consumes significant CPU resources on the firewall. The impact varies based on:
- Volume of Encrypted Traffic: More traffic being decrypted means higher CPU load.
- Cipher Suites Used: Some ciphers are more computationally expensive than others (e.g., RSA key exchange vs. ECDHE).
- Firewall Model and Hardware Capabilities: Higher-end PA-Series models have dedicated hardware acceleration for cryptographic operations, significantly improving decryption throughput and reducing CPU impact. Mid-range and branch office models may have more limited hardware assistance.
- Number of Concurrent Decrypted Sessions: Each decrypted session consumes memory and processing cycles.
Palo Alto Networks provides decryption throughput metrics in its product datasheets. It's crucial to select a firewall model that can handle the anticipated decrypted traffic load without impacting other essential security functions or overall network performance. Monitor CPU utilization closely during and after decryption deployment.
admin@PA-VM> show system resources
Output will show CPU load, memory usage, and other system statistics.
Look for `dp0` (dataplane 0) or similar `dpX` CPU utilization.
If performance becomes an issue, consider:
- Reducing the scope of decryption (e.g., decrypting fewer URL categories).
- Upgrading to a more powerful firewall model.
- Optimizing Decryption Profiles (e.g., avoiding overly restrictive cipher checks if not necessary, though security should be prioritized).
Troubleshooting Common Decryption Issues
When decryption is implemented, various issues can arise. Here are common problems and PAN-OS tools for troubleshooting:
Common Issues:
-
Certificate Errors in Client Browsers:
- Cause: Client does not trust the Forward Trust CA certificate (most common for SSL Forward Proxy). Original server certificate is invalid, and client sees Forward Untrust CA signed cert.
- Troubleshooting: Verify Forward Trust CA is correctly deployed to client systems. Check firewall's Decryption log for details on why the original cert might be untrusted.
-
Applications Breaking:
- Cause: Certificate pinning, mTLS, or non-standard TLS implementations by the application.
-
Troubleshooting:
Identify the problematic application/hostname (Traffic logs, Decryption logs, client reports). Add the FQDN/hostname to the SSL Decryption Exclusion list (
Device > Setup > Content-ID > SSL Decryption Exclusion).
-
Website Accessibility Issues:
- Cause: Unsupported ciphers, TLS versions, or server expecting specific TLS extensions not handled by the current Decryption Profile.
- Troubleshooting: Review Decryption logs for error messages. Adjust Decryption Profile settings (e.g., allow a broader range of TLS versions or ciphers if secure). Packet captures on the firewall can reveal handshake failures.
-
High CPU Utilization on Firewall:
- Cause: Volume of decrypted traffic exceeds firewall capacity.
-
Troubleshooting:
Review
show system resources. Reduce decryption scope or upgrade hardware.
-
SSL Inbound Inspection Not Working:
- Cause: Incorrect server certificate/private key imported. Decryption Profile misconfiguration. NAT/Security policy issues.
- Troubleshooting: Verify correct certificate and key pair. Check Decryption and Traffic logs. Ensure Security Policy allows traffic to the VIP/server IP and that NAT is correct.
PAN-OS Troubleshooting Tools:
-
Logs:
-
Decryption Log (
Monitor > Logs > Decryption): Primary source for decryption-related events. Shows successful/failed handshakes, reasons for failure (e.g., "unsupported cipher suite", "certificate validation error", "policy denied decrypt"), decryption type, profile used. -
Traffic Log (
Monitor > Logs > Traffic): Shows session details, including whether a session was decrypted (look for "Flags" column or session details). -
URL Filtering Log (
Monitor > Logs > URL Filtering): Shows URL categories for decrypted HTTPS traffic. -
Threat Log (
Monitor > Logs > Threat): Shows threats found in decrypted traffic. -
System Log (
Monitor > Logs > System): May contain messages related to certificate management or decryption engine issues.
-
Decryption Log (
-
CLI Commands:
-
show counter global filter aspect Ssl_proxy | match err: Shows various SSL proxy error counters. -
show counter global filter aspect Ssl_decrypt | match err: Shows SSL decryption error counters. -
show session id <session_id>: Displays detailed information about a specific session, including decryption status and flags. -
debug dataplane packet-diag set filter ...anddebug dataplane packet-diag set capture ...: Advanced packet capture and diagnostic tools. Can be used to see packet flow and SSL handshake details. Use with caution as it can impact performance. -
less mp-log dpdecrypt.log(ordp0-dpdecrypt.log, etc.): View dataplane decryption debug logs (requires debug levels to be enabled, typically done under guidance from Palo Alto Networks support). -
show running decryption-policy: Displays the current decryption policy configuration.
-
-
Packet Captures (
Monitor > Packet Capture): Capture traffic on specific interfaces to analyze SSL/TLS handshakes in Wireshark. Look for client/server hellos, certificate exchanges, and alert messages.
Gotcha! (Palo Alto Networks): When troubleshooting, always check the Decryption Log first. It often provides specific error messages that pinpoint the cause of the problem (e.g., "SSL_VERSION_ALERT_PROTOCOL_VERSION", "TLSV1_ALERT_UNKNOWN_CA", "TLSV1_ALERT_BAD_CERTIFICATE").
Decryption and its Role in the Palo Alto Networks Security Ecosystem
Decryption is not just a standalone feature; it's a critical enabler for many other security services on the Palo Alto Networks platform. Without visibility into encrypted payloads, the effectiveness of these services is severely diminished.
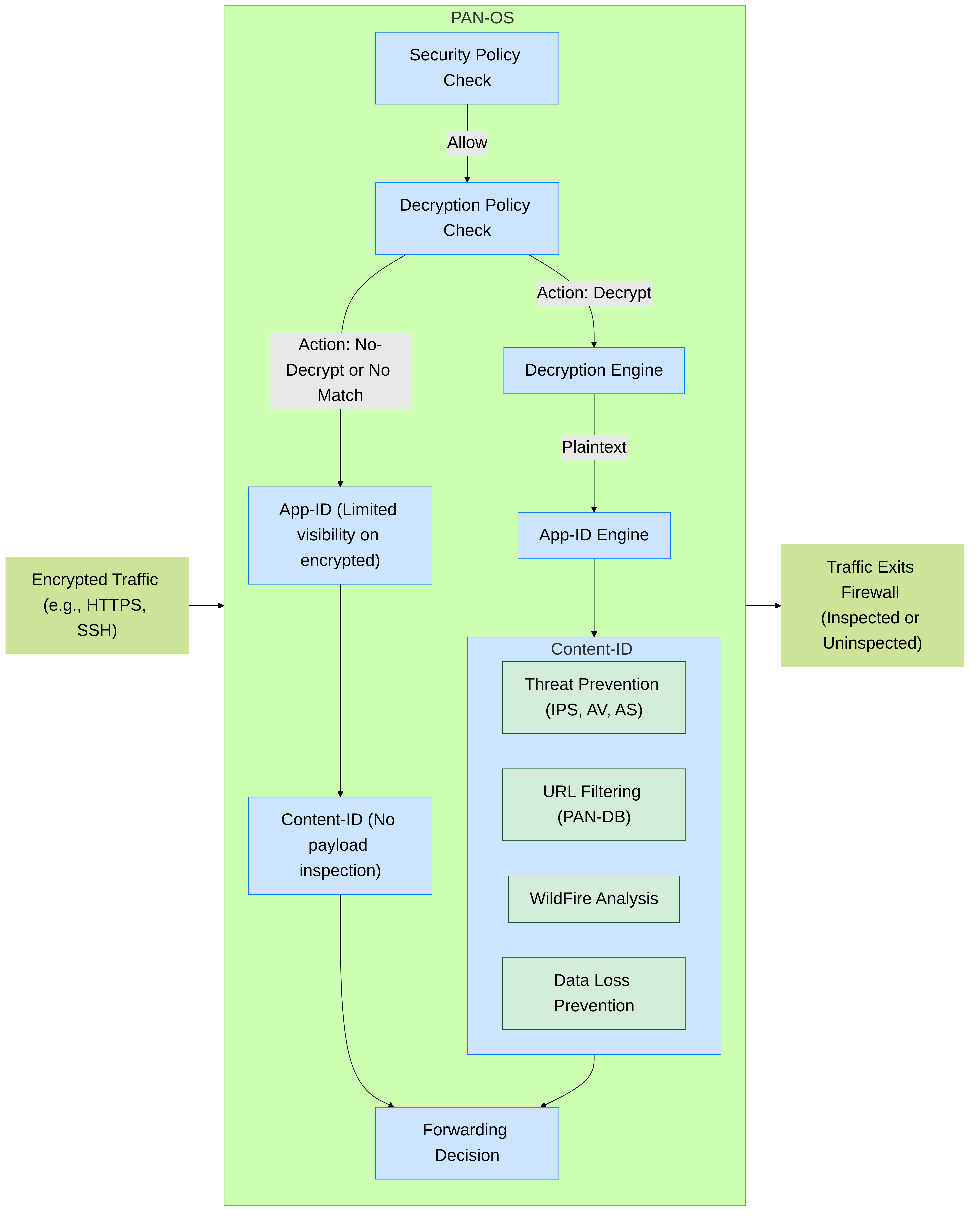
Simplified Palo Alto Networks packet flow showing how decryption enables full App-ID and Content-ID inspection. Without decryption, App-ID has limited visibility (e.g., SNI, cert info), and Content-ID cannot inspect payloads.
- App-ID™: While App-ID can identify some applications over SSL/TLS using SNI or certificate information, full application identification (especially for tunneled apps or custom apps) and detection of application functions often requires decryption.
- Threat Prevention: Antivirus, Anti-Spyware, and Vulnerability Protection (IPS) rely on inspecting file contents and network payloads. If this traffic is encrypted, these threats pass undetected. Decryption exposes the payload to these engines.
- URL Filtering with PAN-DB: While the initial request's SNI might give the domain for URL categorization, decryption allows inspection of the full URL path and content, which is crucial for identifying malicious pages hosted on otherwise legitimate domains.
- WildFire™ Malware Analysis: WildFire analyzes unknown files to identify zero-day malware. If malicious files are transferred over encrypted channels, the firewall cannot forward them to WildFire without decryption.
- Data Loss Prevention (DLP): If your organization uses Palo Alto Networks DLP (requires a license), decryption is essential to inspect the content of outbound encrypted traffic for sensitive data patterns.
- User-ID™: While User-ID itself doesn't require decryption, applying user-based decryption policies (e.g., decrypting for some user groups but not others) enhances granular control.
In essence, implementing Decryption Policies unlocks the full potential of the Palo Alto Networks Next-Generation Firewall to protect against modern, sophisticated threats that hide within encrypted traffic.