Palo Alto Networks: Management Plane vs. Data Plane Architecture Deep Dive
Architectural Overview: The Foundation of PAN-OS
Palo Alto Networks' Next-Generation Firewalls (NGFWs) are fundamentally built upon a separated architecture, distinguishing between the Management Plane (MP) and the Data Plane (DP) . This architectural design is a cornerstone of PAN-OS, enabling efficient resource utilization, high performance, and robust security. The separation ensures that intensive management tasks do not impede critical traffic processing functions, and vice-versa. This concept is integral to the Single-Pass Parallel Processing (SP3) architecture, which allows the firewall to perform multiple security functions on traffic in a single pass, minimizing latency.
The Management Plane (MP): The Brain of the Firewall
The Management Plane is responsible for all administrative, control, and monitoring functions of the firewall. It provides the interfaces for human administrators and centralized management systems like Panorama to interact with the device.
Key Responsibilities of the Management Plane:
-
Configuration Management:
- Handles the creation, modification, validation, and deployment (commit) of firewall configurations. This includes policies, objects, network settings, and system parameters.
- Manages candidate configurations (changes not yet active) and the running configuration (active on the device).
- Interacts with Panorama for pushing centralized configurations to managed firewalls.
-
Logging and Reporting:
- Collects various types of logs (Traffic, Threat, URL Filtering, WildFire, Data Filtering, System, Configuration, User-ID, etc.) generated by the Data Plane.
- Stores logs locally (on dedicated MP storage) or forwards them to external systems like Panorama, Cortex Data Lake, Syslog servers, or SIEMs.
- Generates reports and provides data for the Application Command Center (ACC) for traffic analysis and visualization.
-
User Interface Operations:
- Manages access via the Web Interface (GUI), Command Line Interface (CLI), and XML/RESTful APIs.
- Authenticates administrative users and enforces Role-Based Access Control (RBAC).
-
System Management:
- Oversees core system processes, PAN-OS software upgrades, and content updates (Applications and Threats, Antivirus, WildFire signatures).
- Monitors overall system health, hardware status, and resource utilization (CPU, memory, disk).
- Manages licensing, High Availability (HA) configuration synchronization, and Panorama connectivity.
- Handles services like NTP, DNS resolution for management services, and SNMP.
-
Authentication Services:
- Manages administrative user authentication against local databases or external services (RADIUS, TACACS+, LDAP, Kerberos).
-
The
useriddprocess on the MP also plays a crucial role in User-ID functionality by communicating with User-ID agents and mapping users to IP addresses.
Key Management Plane Processes:
Several daemons (processes) run on the Management Plane to perform its functions. Some critical ones include:
-
mgmtsrvr: The primary management server process. It handles GUI/CLI/API requests, configuration management, commit operations, and communication with Panorama. -
authd: Manages authentication for administrative users accessing the firewall. -
useridd: Handles User-ID related tasks, including communication with User-ID agents, processing user-to-IP mappings, and distributing this information to the Data Plane. -
configd: Manages the device configuration, including candidate and running configurations, and orchestrates the commit process. -
logrcvr: Receives logs from the Data Plane and processes them for local storage or forwarding. -
devsrvr: (Historically more distinct, functions now largely integrated within `mgmtsrvr` and `configd`) Facilitates communication and configuration synchronization between the Management Plane and Data Plane. - Other processes like `dhcpd` (for management interface DHCP client), `ntpd` (for time synchronization), `snmpd` (for SNMP queries), and `ikemgr` and `rasmgr` (for GlobalProtect management functions) also run on the MP.
Management Plane Hardware Resources:
On physical PA-Series appliances, the Management Plane typically has its own dedicated CPU, RAM, and storage (SSD or HDD). This physical separation ensures that management tasks do not consume resources needed by the Data Plane for traffic processing. The Management (MGT) interface is a dedicated physical port providing out-of-band access to the MP.
! Example: Viewing Management Plane CPU/Memory usage show system resources ! Example: Restarting a Management Plane process (use with extreme caution) debug software restart process mgmtsrvr
The Data Plane (DP): The Engine of Traffic Processing
The Data Plane is the workhorse of the firewall, exclusively dedicated to processing all network traffic that transits the device. It enforces security policies, performs threat prevention, and forwards traffic based on the configuration pushed down from the Management Plane.
Key Responsibilities of the Data Plane:
-
Packet Processing and Forwarding:
- Handles ingress and egress of packets on network interfaces.
- Performs Layer 2 (switching), Layer 3 (routing), Virtual Wire, and Tap mode operations.
- Executes forwarding decisions based on routing tables, PBF (Policy-Based Forwarding) rules, and session state.
-
Session Management:
- Creates and maintains session state for all active connections passing through the firewall. This is central to stateful inspection.
- Leverages hardware offload for established sessions (fast path processing) to maximize throughput.
-
Security Policy Enforcement:
- Applies Security policy rules to traffic flows.
- Identifies applications using App-ID .
- Identifies users using User-ID information (received from MP).
-
Inspects content using
Content-ID
, which includes:
- Threat Prevention (Antivirus, Anti-Spyware, Vulnerability Protection)
- URL Filtering (PAN-DB or BrightCloud)
- File Blocking and Data Filtering (DLP)
- WildFire analysis submissions and verdict enforcement
- Performs SSL/TLS Decryption and Inspection.
- Enforces Quality of Service (QoS) policies.
-
Traffic Logging:
- Generates detailed logs for traffic, threats, URL filtering, WildFire, etc., based on log forwarding profiles and policy settings.
- Sends these logs to the Management Plane's `logrcvr` process.
-
Network Address Translation (NAT):
- Performs Source NAT (SNAT) and Destination NAT (DNAT) as defined in NAT policies.
- Supports U-Turn NAT.
-
VPN Tunneling:
- Terminates and originates IPsec VPN tunnels.
- Handles GlobalProtect (SSL VPN) tunnels, including gateway and portal functions for traffic processing.
-
Routing Protocol Processing:
- Although routing protocol daemons (e.g., `routed` for OSPF, BGP) run on the Management Plane for control and configuration, the resulting Forwarding Information Base (FIB) is pushed to the Data Plane for actual packet forwarding decisions.
Key Data Plane Processes/Components:
The Data Plane relies on a combination of multi-core general-purpose CPUs and specialized hardware accelerators (on PA-Series). Key software components and their functions include:
-
pan_task(or similar, may vary by platform/PAN-OS version): Core packet processing threads. Multiple instances often run, pinned to specific DP CPU cores. -
flow_ctrl(or equivalent logic): Manages session setup, teardown, and state tracking. Handles the interaction between slow path (first packet processing) and fast path (hardware offload). -
pan_comm: A critical process (or communication channel) that facilitates communication between the Data Plane and the Management Plane. It receives configuration updates from the MP and sends statistics, logs, and status information back to the MP. -
brdagent: Interacts with the hardware network interfaces (Broadcom or other chipsets), managing link status, statistics, and packet buffers. -
dp_monitor: Monitors the health and performance of Data Plane resources and processes. - Specialized hardware engines (NPUs, SPUs, FPGAs in PA-Series): These are not "processes" in the software sense but are crucial hardware components that accelerate specific DP functions like packet forwarding, pattern matching for App-ID/Content-ID, and encryption/decryption. This is the essence of the Single-Pass Parallel Processing (SP3) architecture.
Data Plane Hardware Resources:
PA-Series firewalls utilize a powerful combination of multi-core CPUs and custom ASICs (Application-Specific Integrated Circuits) for Data Plane tasks:
- Network Processing Units (NPUs): Handle high-speed packet forwarding, MAC learning, QoS, and basic firewall tasks.
- Security Processing Units (SPUs) / Content Processors: Dedicated to computationally intensive tasks like App-ID signature matching, Content-ID (IPS, AV, AS), and SSL decryption.
VM-Series firewalls leverage the host server's CPU cores for Data Plane processing. Performance can be significantly enhanced by using technologies like DPDK (Data Plane Development Kit) and SR-IOV (Single Root I/O Virtualization).
! Example: Show all active sessions in the Data Plane show session all ! Example: Show Data Plane CPU utilization (specific command may vary by PAN-OS version/platform) show running resource-monitor ! Example: Check packet counters for troubleshooting show counter global filter packet-filter yes delta yes
Interaction Between Management and Data Planes
The Management and Data Planes, while distinct, are in constant communication to ensure cohesive firewall operation. This interaction is fundamental to the functionality of a Palo Alto Networks NGFW.
-
Configuration Deployment (Commit Process):
- Administrator makes changes in the candidate configuration on the Management Plane (via GUI, CLI, API, or Panorama).
- Administrator initiates a "commit."
-
The MP (
mgmtsrvr/configd) validates the configuration. - The MP translates the relevant portions of the configuration into a format understood by the Data Plane.
- The MP pushes this compiled configuration to the Data Plane(s) via a dedicated internal communication channel (often referred to as `pan_comm`).
- The Data Plane applies the new configuration, updating its policy tables, forwarding logic, and security engines.
- The Data Plane acknowledges successful application to the Management Plane.
- The Management Plane finalizes the commit, and the candidate configuration becomes the new running configuration.
-
Logging and Statistics:
- The Data Plane processes traffic and generates logs (Traffic, Threat, URL, etc.) based on security policies and log forwarding profiles.
- These logs are sent from the DP to the `logrcvr` process on the Management Plane.
- The MP then stores these logs locally or forwards them as configured.
- The DP also collects various statistics (interface counters, session counts, resource utilization) and sends them to the MP for display and monitoring.
-
Content Updates (App-ID, Threat-ID, Antivirus, WildFire):
- The Management Plane periodically checks for and downloads new content updates from the Palo Alto Networks Update Cloud.
- Once downloaded and validated, the MP pushes these updates to the Data Plane.
- The Data Plane loads the new signatures and rules into its security engines, often in a hitless manner, to ensure continuous protection with the latest intelligence.
-
User-ID Information:
- The `useridd` process on the MP gathers user-to-IP address mappings from various sources (AD User-ID Agent, Syslog, GlobalProtect, etc.).
- The MP then distributes these mappings to the Data Plane.
- The DP uses this information to enforce User-ID based security policies.
-
High Availability (HA) State Synchronization:
- In an HA pair, configuration is synchronized between the MPs of the active and passive firewalls.
- Runtime state information crucial for failover (e.g., session tables, IPsec SAs, ARP tables) is often synchronized directly between the Data Planes of the HA peers via HA links (HA1 for MP control/config, HA2 for DP state/session sync).
Palo Alto Networks Single-Pass Parallel Processing (SP3) Architecture
The separation of MP and DP is a foundational element of Palo Alto Networks' Single-Pass Parallel Processing (SP3) architecture. SP3 is designed to perform all security functions—networking, policy lookup, App-ID, User-ID, Content-ID (threat prevention, URL filtering, file blocking)—in a single pass through the traffic stream.
Key aspects of SP3 related to MP/DP architecture:
- Single Pass: Traffic is processed once by the DP. The packet is parsed, and then various security engines inspect it concurrently or in a highly optimized sequence. This avoids the latency issues of architectures that pass traffic through multiple separate inspection engines or cards sequentially.
- Parallel Processing: Within the Data Plane, specialized hardware (NPUs and SPUs on PA-Series) and multi-core software processing enable parallel execution of different inspection tasks. For example, while one core/engine identifies the application (App-ID), another can simultaneously check for threats (Content-ID) relevant to that application.
- Stream-Based Inspection: Content inspection is performed on the stream of data, not just individual packets, allowing for more accurate threat detection and application identification.
The Management Plane's role in SP3 is to provide the configuration and intelligence (policies, signatures) that the Data Plane uses for its high-speed, single-pass processing. This efficient architecture is what allows Palo Alto Networks NGFWs to deliver comprehensive security without becoming a bottleneck.
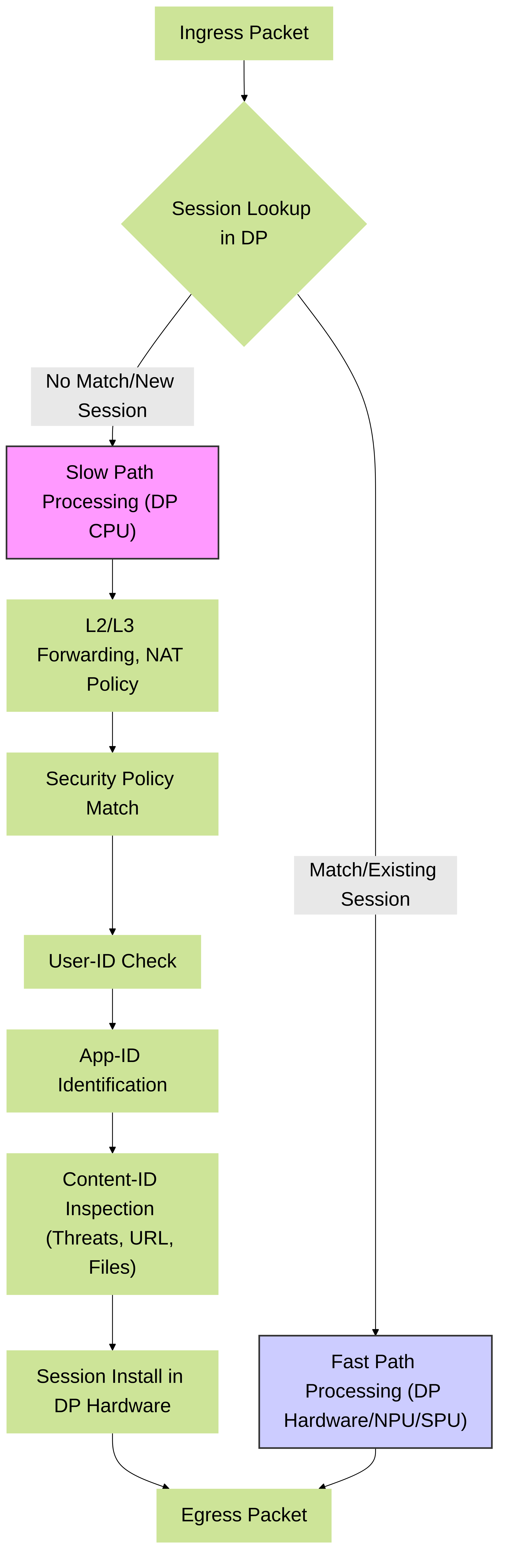
Simplified representation of PAN-OS SP3 packet flow. New sessions go through the "Slow Path" for full policy evaluation and App-ID/Content-ID. Once established, sessions can be offloaded to the "Fast Path" for accelerated processing.
Hardware Architecture and Planes: PA-Series vs. VM-Series
PA-Series Physical Appliances:
Palo Alto Networks PA-Series firewalls have varying hardware architectures depending on the model, but all maintain the logical separation of MP and DP, often with dedicated physical resources:
- Entry-Level (e.g., PA-220, PA-400 Series): Often use a System-on-Chip (SoC) design where MP and DP functions might share some physical CPU cores but are still logically distinct. The MGT port is dedicated.
- Mid-Range (e.g., PA-800, PA-3200, PA-3400 Series): Typically feature a dedicated multi-core CPU for the Management Plane and a separate, more powerful multi-core CPU coupled with specialized NPUs and SPUs for the Data Plane. This provides significant resource isolation.
- High-End (e.g., PA-5200, PA-5400, PA-7000, PA-7500 Series): Employ highly modular and scalable architectures. They have robust, dedicated Management Plane processors and multiple Data Plane processing cards, each with its own set of CPUs, NPUs, and SPUs, interconnected by a high-speed switch fabric. This allows for massive throughput and session capacity.
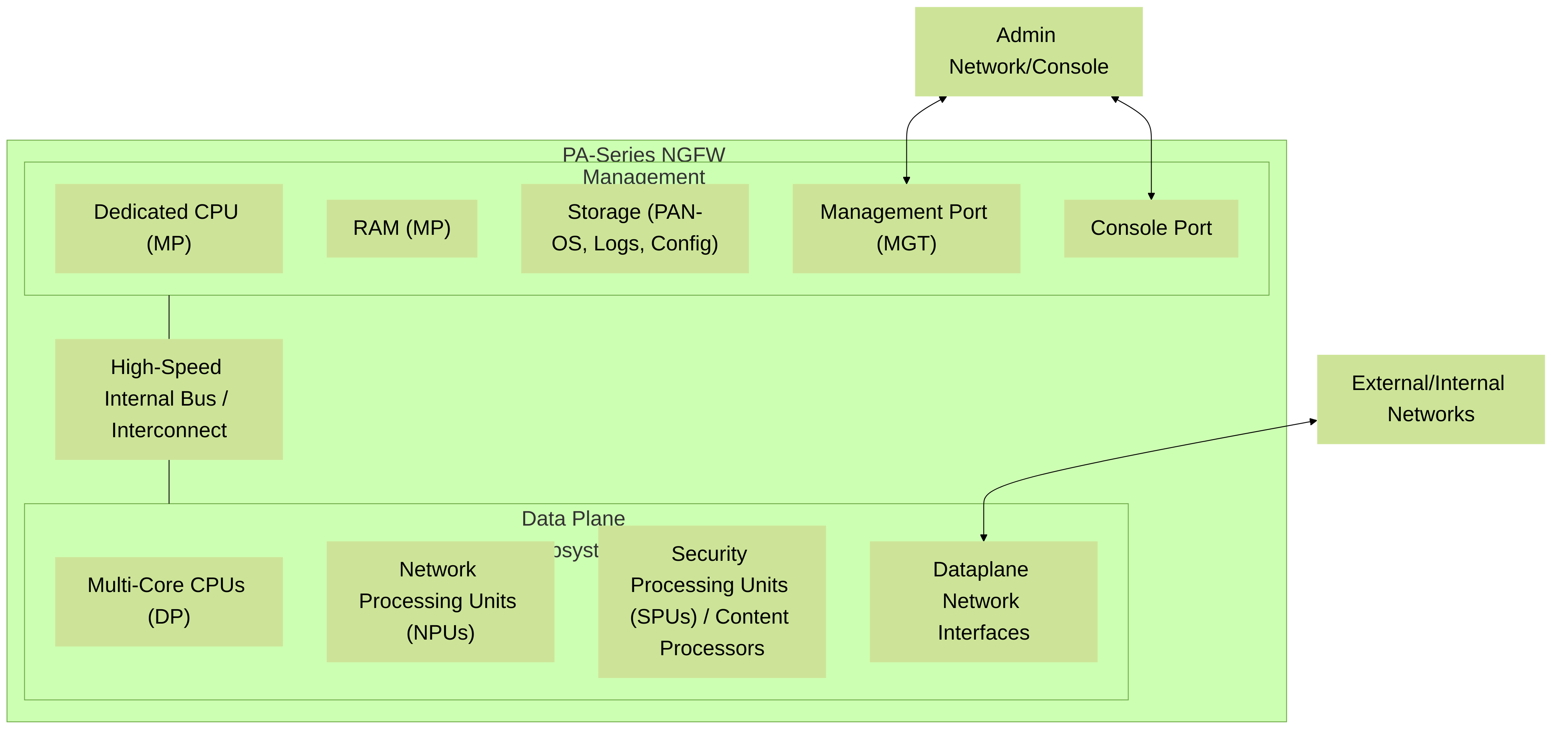
A high-level representation of a typical mid-range PA-Series hardware architecture, showcasing the distinct MP and DP subsystems with their dedicated resources.
VM-Series Virtual Appliances:
VM-Series firewalls run PAN-OS as a virtual machine on standard hypervisors (VMware ESXi, KVM, Hyper-V, AWS, Azure, GCP).
- Management Plane: Runs as part of the PAN-OS virtual machine, utilizing vCPUs and RAM allocated from the host.
-
Data Plane:
Also utilizes vCPUs and RAM allocated from the host. Performance is heavily influenced by:
- Number and speed of allocated vCPUs.
- RAM allocation.
- Underlying host hardware.
-
Use of performance-enhancing technologies:
- DPDK (Data Plane Development Kit): Allows the DP to bypass the hypervisor's kernel networking stack for faster packet processing directly in user space.
- SR-IOV (Single Root I/O Virtualization): Allows the VM-Series direct access to physical NICs, reducing hypervisor overhead and improving throughput and latency.
Mermaid Sequence Diagram: Configuration Deployment
This diagram illustrates the high-level flow of deploying configuration changes from an administrator to the firewall's Data Plane.
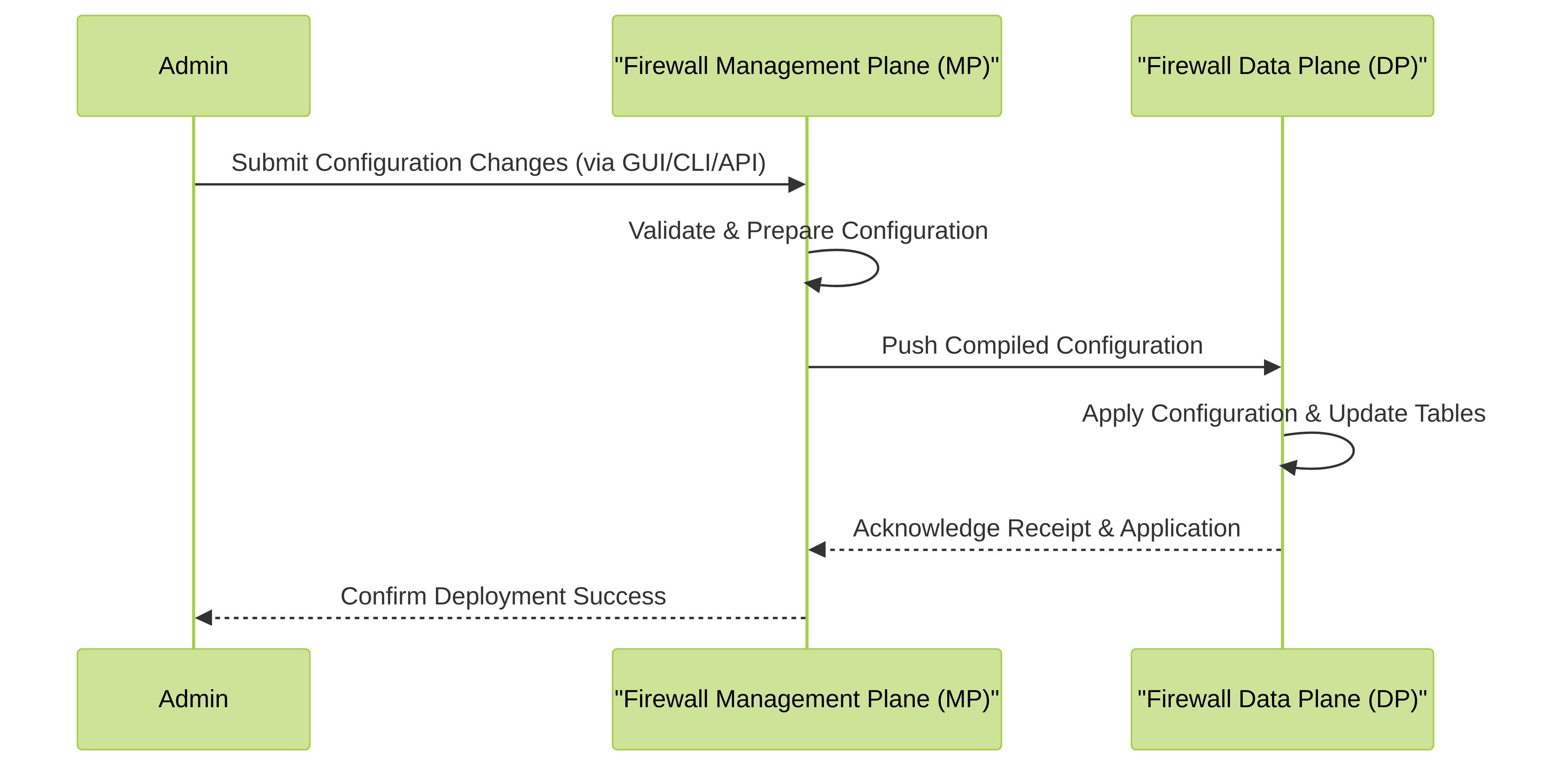
Sequence of events during a configuration commit on a Palo Alto Networks firewall.
Mermaid Sequence Diagram: Traffic Processing and Logging
This diagram shows how network traffic is processed by the Data Plane and how corresponding logs are sent to the Management Plane.
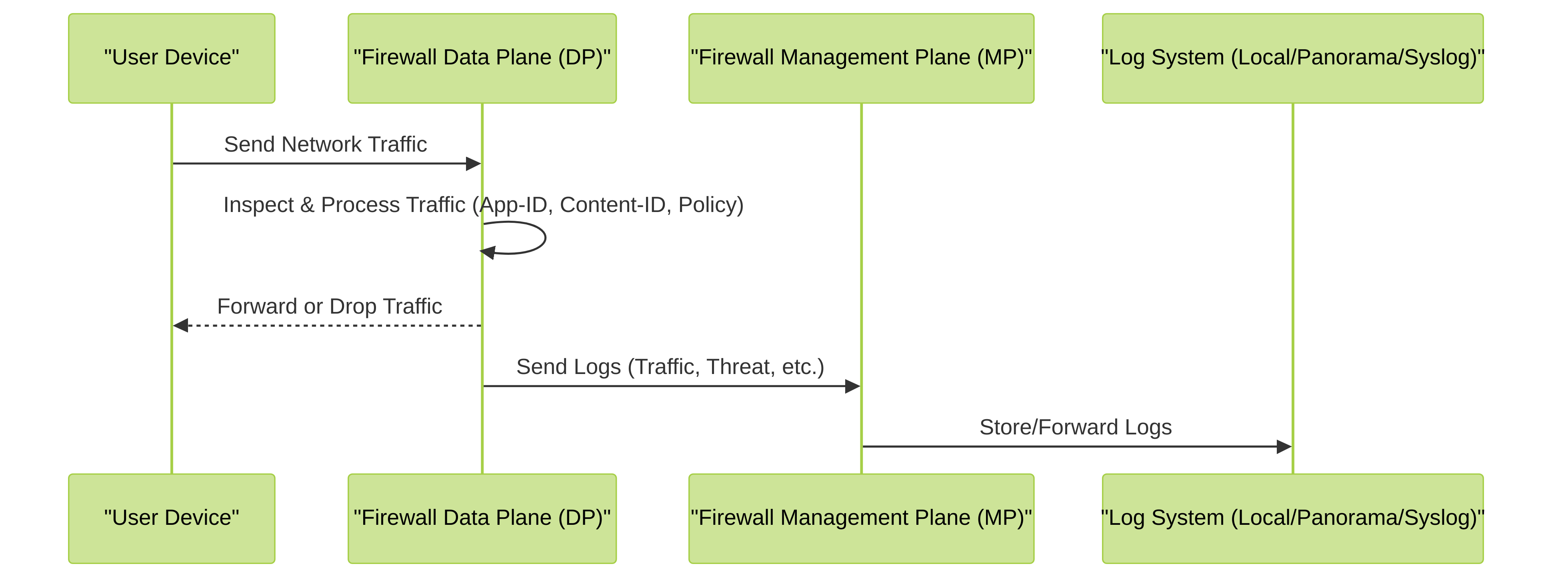
Flow of network traffic processing by the Data Plane and subsequent log generation and handling by the Management Plane.
Mermaid Diagram: Content Update Process
This diagram illustrates how the firewall receives and applies content updates (e.g., Applications and Threats, Antivirus).
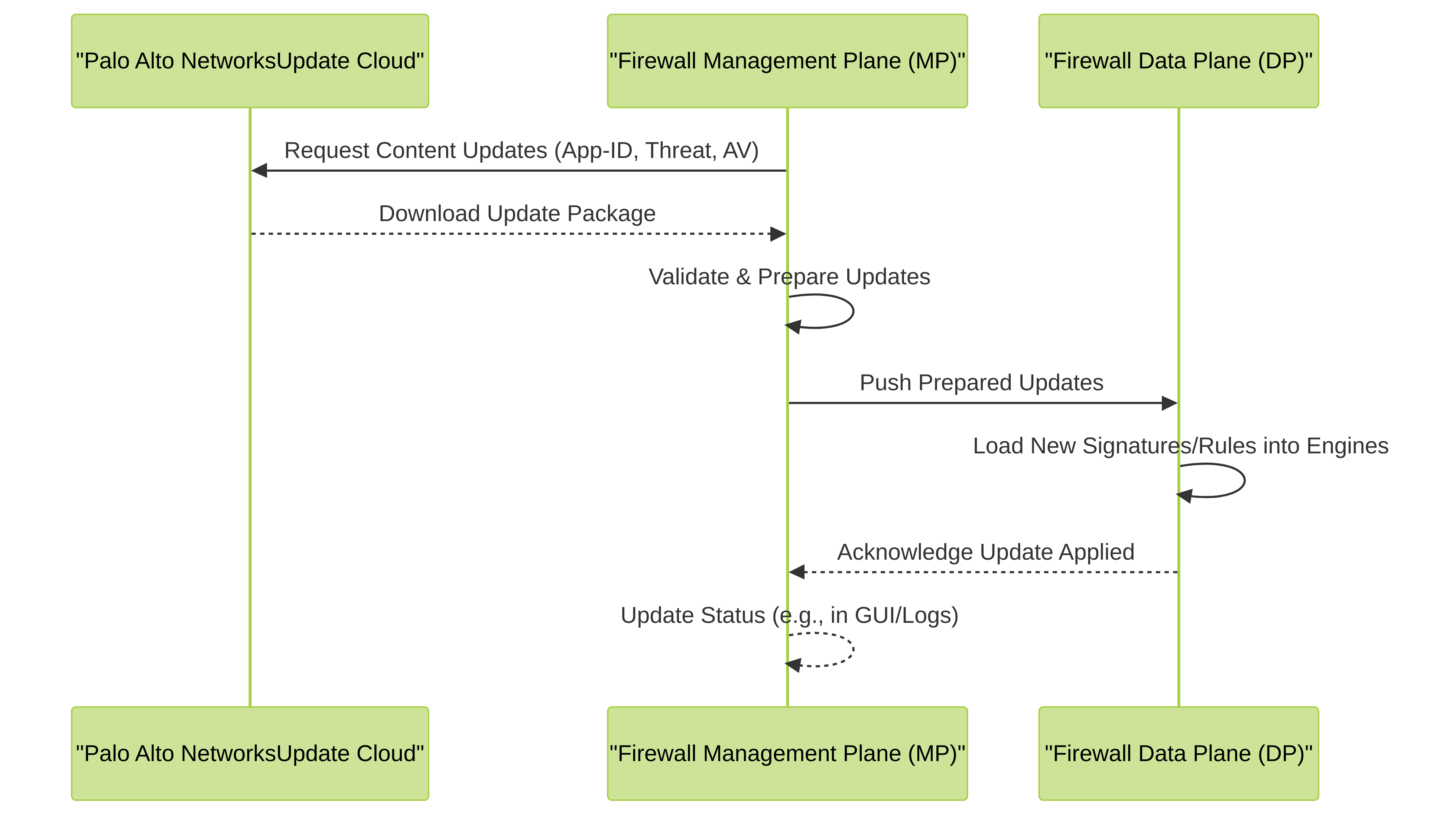
Shows the process of the Management Plane downloading content updates from the Palo Alto Networks Update Cloud and distributing them to the Data Plane for activation.
Troubleshooting Common Management Plane and Data Plane Issues
Understanding how to troubleshoot issues related to MP and DP resource utilization is crucial for maintaining firewall health and performance.
Management Plane High CPU/Memory Utilization:
- Symptoms: Slow or unresponsive WebUI/CLI, long commit times, Panorama disconnections, failures in log forwarding or report generation.
-
Common Causes:
- Excessive logging to the firewall's local disk (especially debug logs).
- Frequent or large configuration commits.
- Numerous active administrative sessions (GUI/CLI/API).
- Intensive reporting or ACC queries.
- High rate of FQDN object refreshes.
- Panorama communication overhead in large environments.
- System tasks like PAN-OS upgrades or content updates (temporary).
show system resources
show system statistics session | match mgmt
show jobs all
show running resource-monitor
less mp-log mgmtsrvr.log
less mp-log pan_gp_agent.log // If GlobalProtect is heavily used for management
Data Plane High CPU/Packet Buffer Utilization:
- Symptoms: Increased network latency, packet drops, slow application performance, session drops, high CPU alarms from DP cores.
-
Common Causes:
- Traffic volume exceeding firewall capacity.
- High percentage of "slow path" traffic (e.g., many new, short-lived sessions, or traffic not eligible for hardware offload).
- Computationally intensive features enabled on a large volume of traffic (e.g., SSL decryption, certain App-IDs, comprehensive threat prevention profiles on all rules).
- Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attacks.
- Misconfigured policies or routing leading to traffic loops or inefficient paths.
- Hardware issues with DP components (rare).
- High packet buffer utilization can lead to drops even if CPU is not maxed out.
-
PAN-OS CLI Commands for Investigation:
show running resource-monitor // Shows DP CPU load per core, packet buffer usage show session info // Overview of session table, throughput show counter global filter aspect flow // Flow-related counters show counter global filter packet-filter yes delta yes // Real-time packet statistics show system setting session resource-limit current // Check current session limits debug dataplane pool statistics // Detailed DP memory pool usage show running security-policy
statistics // Packet/byte counts per rule show high-availability state // Check HA path monitoring if applicable show system state filter sys.sX.pX.mp // For detailed per-core MP stats (X is DP number, X is core number) show system state filter sys.sX.pX.dp // For detailed per-core DP stats
Management Plane - Data Plane Communication Issues:
- Symptoms: Commit failures (often with generic errors), statistics not updating in GUI/Panorama, policy enforcement inconsistencies, stale User-ID mappings.
- Common Causes: These are rare on physical appliances unless there's a severe underlying hardware or software bug. On VM-Series, resource starvation on the host could theoretically impact internal communication.
-
PAN-OS CLI Commands for Investigation:
less mp-log pan_commd.log // Management plane side of pan_comm less dp0-log pan_comm.log // Data plane side of pan_comm (dp0, dp1, etc.) show system setting PCHB link // Check physical channel heartbeat link status (MP-DP link on some platforms)
Securing the Management Plane
Since the Management Plane controls the firewall's configuration and operations, securing it is paramount. Compromise of the MP can lead to a full compromise of the network security posture.
Palo Alto Networks Best Practices:
- Dedicated Management Interface (MGT): Always use the dedicated MGT interface for management access. Do not enable management services on data interfaces if avoidable.
- Network Segmentation: Place the MGT interface in a secure, isolated management network, separate from user and server networks.
- Interface Management Profiles: Apply an Interface Management Profile to the MGT interface (and other interfaces if necessary) to restrict allowed services (HTTPS, SSH, SNMP, Ping) and source IP addresses/networks.
- Service Route Configuration: Ensure that management services (Panorama, DNS, NTP, Updates, Syslog) use the MGT interface by configuring appropriate service routes.
-
Strong Credentials and RBAC:
- Use strong, unique passwords for all administrative accounts.
- Implement Role-Based Access Control (RBAC) to grant administrators only the permissions necessary for their roles.
- Leverage external authentication (TACACS+, RADIUS, LDAP with MFA) for administrative access.
- Secure Protocols: Use HTTPS for WebUI and SSH for CLI. Disable HTTP, Telnet, and weak SSL/TLS ciphers.
- Regular Updates: Keep PAN-OS software and content versions up to date to patch vulnerabilities.
- Audit Logging: Ensure configuration logs are enabled and regularly reviewed (or sent to a SIEM) to detect unauthorized changes.
- Panorama for Centralized Management: Using Panorama can enhance security by centralizing policy and providing a single point for secure management access, reducing direct exposure of individual firewalls.
! Example: Basic Interface Management Profile configuration configure set network profiles interface-management-profile SecureMGT permit ssh yes set network profiles interface-management-profile SecureMGT permit https yes set network profiles interface-management-profile SecureMGT permit snmp no set network profiles interface-management-profile SecureMGT permitted-ip 192.168.1.10/32 set network profiles interface-management-profile SecureMGT permitted-ip 10.0.0.0/24 set deviceconfig system services service-route-configuration source-interface Management commit
Panorama and its Relationship with Firewall Planes
Panorama, Palo Alto Networks' network security management solution, interacts primarily with the Management Plane of the firewalls it manages.
- Centralized Configuration: Panorama pushes device group and template configurations to the MPs of managed firewalls. The MP then processes and commits these configurations, subsequently pushing them to its local DP.
- Policy and Object Management: Shared policies and objects are managed in Panorama and deployed to the MPs of relevant firewalls.
- Software and Content Updates: Panorama can act as a distribution point for PAN-OS software and content updates, pushing them to the MPs of managed devices.
- Log Collection: Firewalls (specifically their MPs via `logrcvr`) forward logs to Panorama's Log Collectors (or Cortex Data Lake). Panorama's management server then queries these Log Collectors for reporting and analysis.
- Monitoring and Reporting: Panorama provides a centralized view of device health, traffic, and threats by collecting data from the MPs of managed firewalls.
The Data Plane of a firewall does not directly communicate with Panorama. Its interaction is mediated by its local Management Plane.