Palo Alto Networks Panorama: A Deep Dive for PCNSE
Welcome! This guide explores Palo Alto Networks Panorama, focusing on its components, deployment strategies, and High Availability. Understanding Panorama is crucial for the PCNSE exam as it's the cornerstone of managing multiple Palo Alto Networks firewalls efficiently. We'll use layman's terms and diagrams to simplify complex topics.
🔧 Panorama Components: The Building Blocks
Think of Panorama as the central command center for your fleet of Palo Alto Networks firewalls. It simplifies management, policy deployment, and log analysis. Its main parts are:
1. Management Server
This is the brain of Panorama. It's what you, the administrator, interact with to:
- Centralized Configuration: Instead of logging into each firewall, you create and manage security policies, objects (like addresses or services), and network settings in one place.
-
Device Groups & Templates:
-
Device Groups:
Group firewalls that need similar security policies (e.g., all datacenter firewalls, all branch office firewalls). Policies applied to a device group are inherited by all firewalls in it. This is for
shared policiesthat define *what* traffic to control.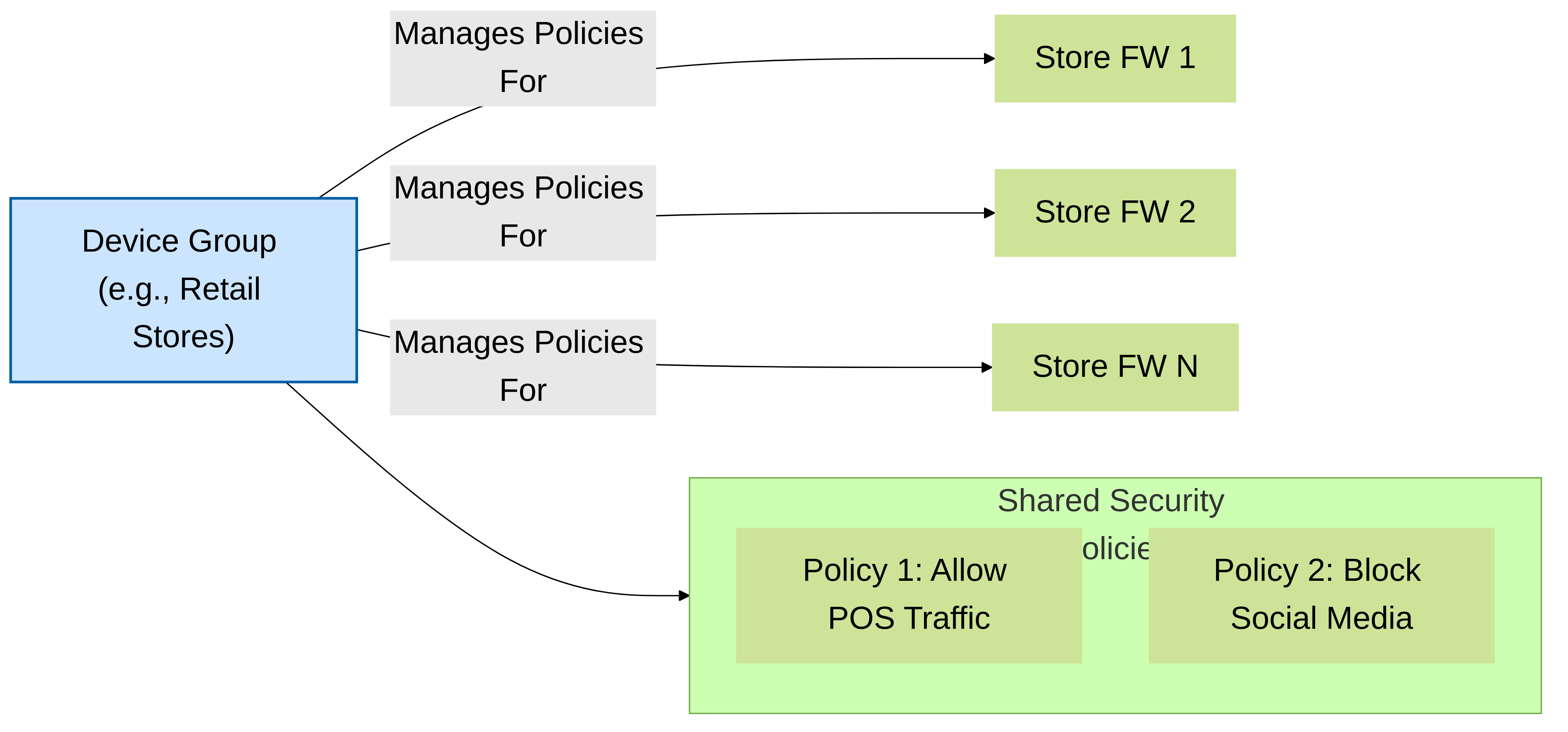
Device Group applying shared security policies.
-
Templates (and Template Stacks):
Manage network and device-specific settings like interfaces, zones, server profiles, and routing. These define *how* a firewall is configured at the network level.
Template Stacksallow you to layer multiple templates for granular control (e.g., a base template for all firewalls, and a specific template for a region).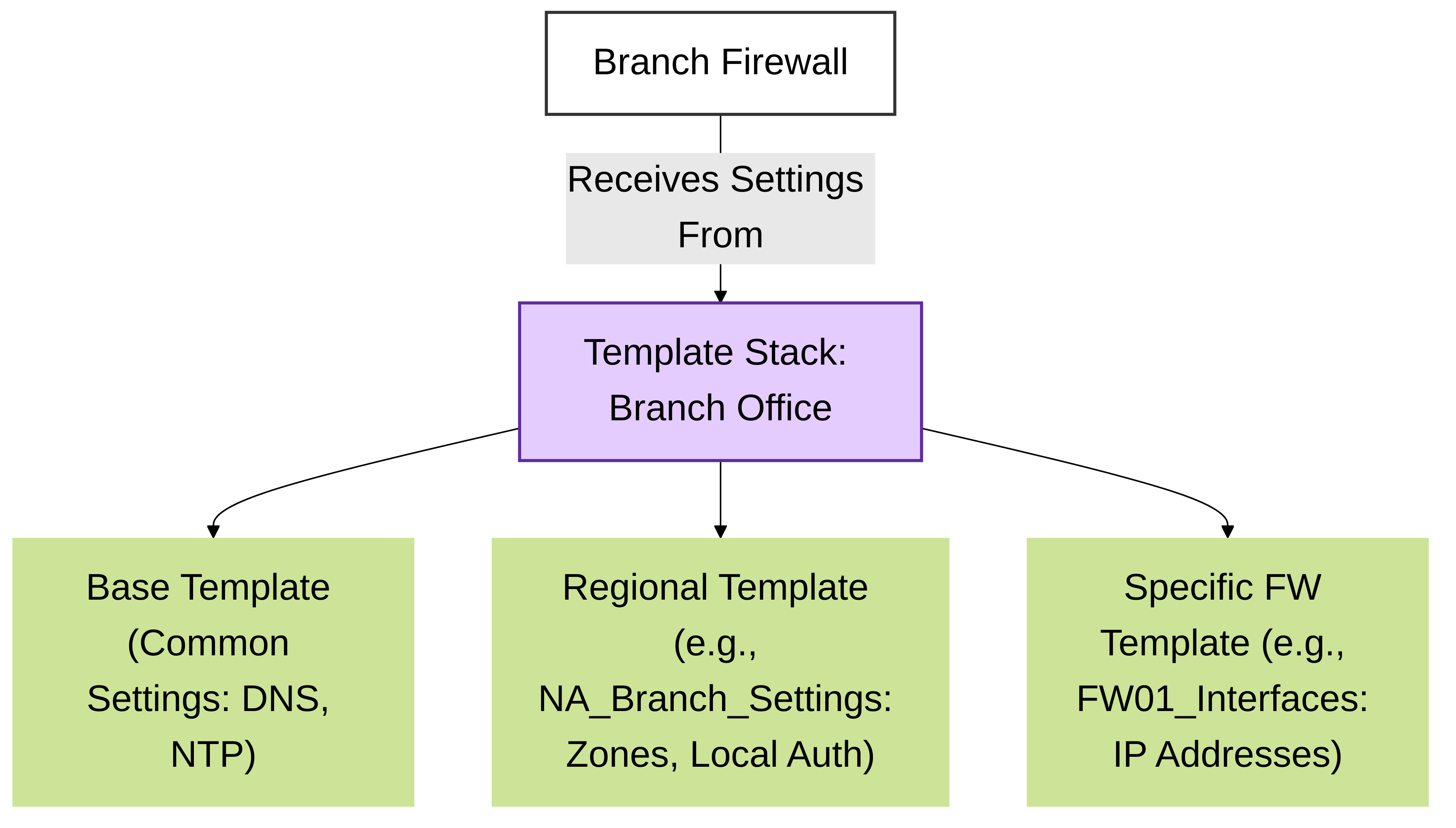
Template Stack layering configurations.
-
Device Groups:
Group firewalls that need similar security policies (e.g., all datacenter firewalls, all branch office firewalls). Policies applied to a device group are inherited by all firewalls in it. This is for
- Role-Based Access Control (RBAC): Define who can do what. For example, a junior admin might only view settings, while a senior admin can make changes.
- Software, Content, and License Updates: Centrally manage and push updates (PAN-OS upgrades, threat signatures, WildFire updates) to your firewalls.
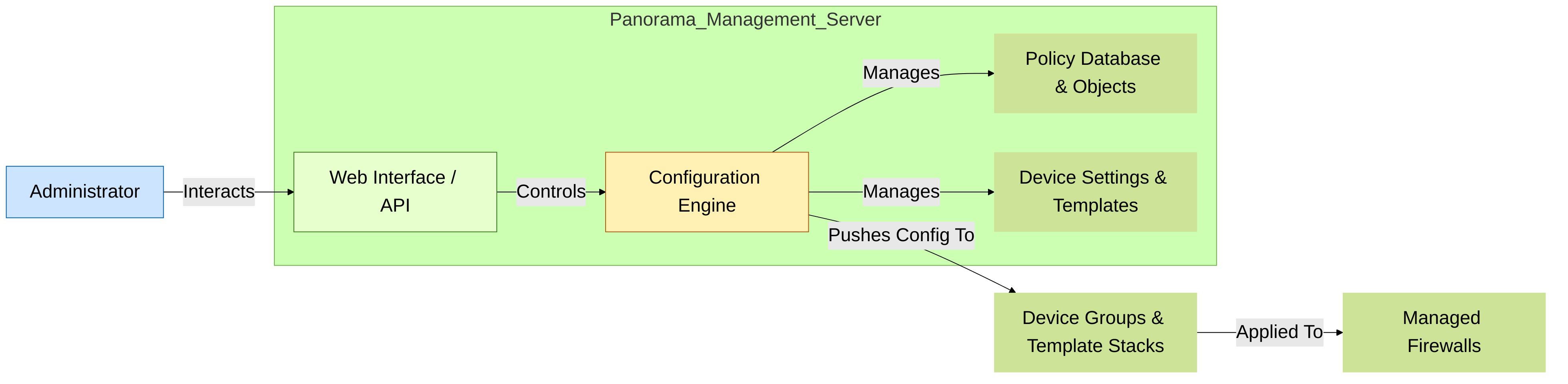
Simplified view of Panorama Management Server components and interactions.
2. Log Collector
This is the central diary keeper for your firewalls. It:
- Aggregates Logs: Collects various logs (traffic, threat, URL, WildFire, system, etc.) from many firewalls. Without this, you'd have to check logs on each firewall individually.
- Log Storage & Forwarding: Stores logs for a defined period and can forward them to external systems like SIEMs (Security Information and Event Management).
- Centralized Reporting & Analytics: Enables you to run reports and analyze traffic patterns across your entire network from one place, using the data gathered by log collectors.
Log Collectors can be dedicated M-Series hardware appliances or Panorama virtual appliances running in "Log Collector Mode."
3. Panorama Operating Modes
Panorama can operate in different modes depending on your needs:
- Panorama Mode: The all-in-one option. This instance acts as both a Management Server AND a Log Collector. Good for smaller deployments or when simplicity is key.
- Management Only Mode: This instance only manages firewalls (policies, device settings). It does NOT collect logs itself. It relies on separate, dedicated Log Collectors. This is common in larger, distributed environments for scalability.
- Log Collector Mode: This instance is dedicated solely to log collection . It doesn't manage devices. It receives logs from firewalls and makes them available to a Panorama in Management Only Mode (or Panorama Mode) for viewing and reporting.
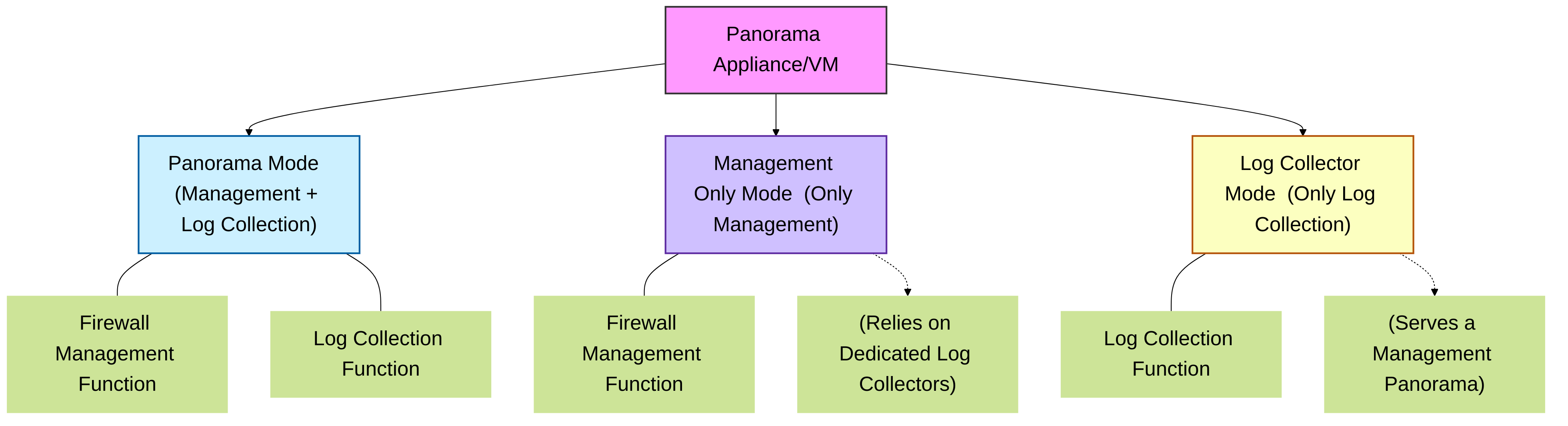
Panorama Operating Modes: Choose based on scale and function.
🛠️ Deployment Options
How you set up Panorama depends on the size and complexity of your network.
1. Centralized Deployment
Imagine a single headquarters managing everything. One Panorama instance (or an HA pair for redundancy) handles both management and log collection. This is simpler to set up and manage.
- Suitable for: Small to mid-sized organizations.
- Pros: Simpler architecture, potentially lower initial cost.
- Cons: Can become a bottleneck for log processing and management if the number of firewalls or log volume grows too large.
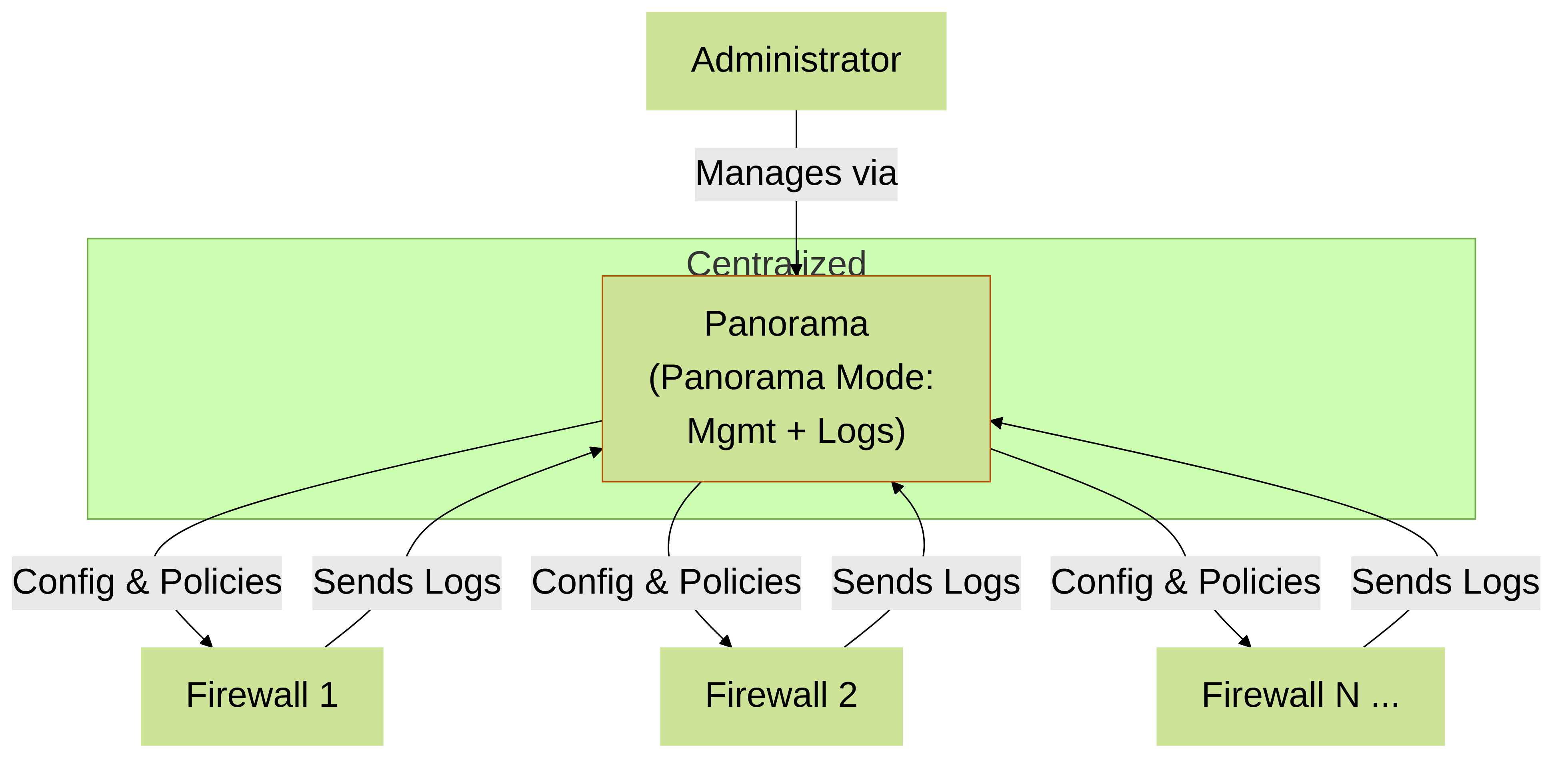
Centralized Deployment: One Panorama instance for management and logging.
2. Distributed Deployment
Think of this as having a central command (Management Panorama) and regional data centers (Log Collectors) . You separate the management tasks from the heavy lifting of log collection.
- Panorama in Management Only Mode: Manages devices and policies.
- Dedicated Log Collectors: Panorama VMs in Log Collector mode or M-Series appliances handle log storage, aggregation, and querying. They are geographically distributed or scaled out as needed.
- Suitable for: Large enterprises with many firewalls, high log volumes, or geographically dispersed networks.
- Pros: Highly scalable, better performance for log processing, fault isolation (management issues don't necessarily stop logging, and vice-versa).
- Cons: More complex to set up and manage initially.
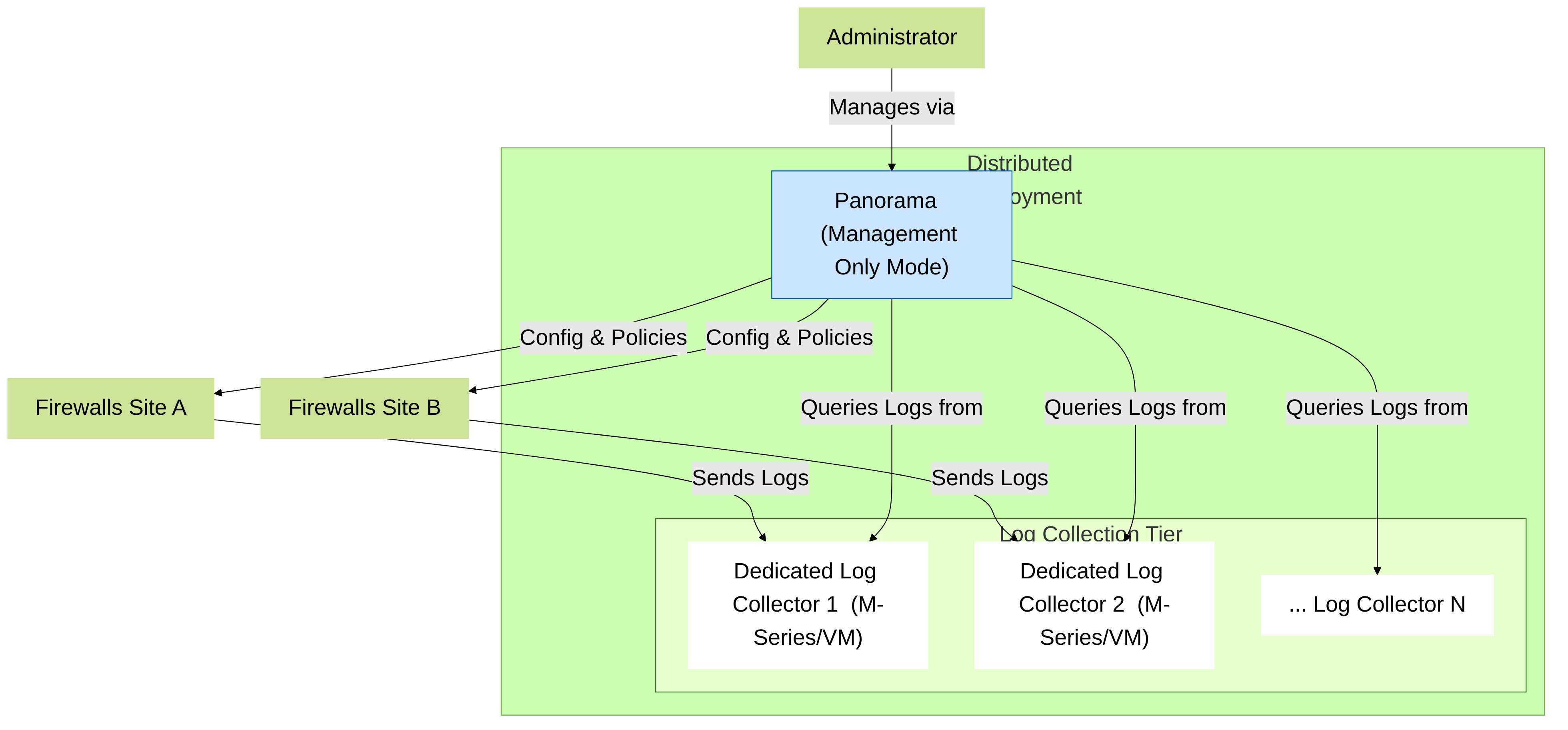
Distributed Deployment: Separate Panorama for management and dedicated Log Collectors for scalability.
3. High Availability (HA)
This is your backup plan for Panorama itself . You don't want your central management or logging to be a single point of failure.
- Uses an Active/Passive pair of Panorama nodes (they must be the same model, PAN-OS version, and operating in the same mode).
- Synchronization: Configurations, logs (if Panorama is in Panorama Mode or it's an HA pair of Log Collectors), and reporting data are continuously synced from the Active to the Passive node. Key sync links: HA1 (Control Link), HA2 (Data Link - for logs, configs).
-
Failover:
If the Active Panorama fails, the Passive node takes over, minimizing downtime for management and/or logging.
- For management, firewalls will connect to the new active Panorama.
- For logging, firewalls will send logs to the new active Panorama (if it's handling logs) or continue sending to Collector Groups (which can also be in HA).
- HA can be configured for Panorama managing devices, for Log Collectors, or for both.
(Primary)"] Pano_Passive["Panorama Passive
(Secondary/Standby)"] end FWs["Managed Firewalls"] Admin["Administrator"] Pano_Active -- "HA1 (Control), HA2 (Data)" <--> Pano_Passive Admin -- Accesses --> Pano_Active Pano_Active -- Manages/Collects Logs --> FWs alt On Failover of Active Node Pano_Passive -- Becomes Active --> Admin Pano_Passive -- Takes Over Management/Logging --> FWs end style Pano_Active fill:#ccffcc,stroke:#38761d,stroke-width:2px style Pano_Passive fill:#ffcccc,stroke:#c0392b,stroke-width:2px note right of Pano_Passive: If Active fails,
Passive becomes Active.
Firewalls then connect to it.
Panorama High Availability: Active/Passive pair for redundancy and minimal downtime.
📦 Log Collectors & Collector Groups
When log volumes are high, dedicated Log Collectors (physical M-Series appliances or Panorama VMs in Log Collector mode) are essential. To manage these efficiently and provide redundancy, you use Collector Groups .
- Dedicated Log Collectors: These are specialized systems optimized for ingesting and storing massive amounts of log data from firewalls.
-
Collector Groups:
- A logical grouping of multiple Log Collectors. Think of it as a team of log recorders .
- Firewalls are configured to forward logs to a Collector Group, not an individual Log Collector directly (for redundancy). Panorama assigns a primary and secondary LC from the group to each firewall.
- Log Distribution: Panorama distributes the firewalls across the Log Collectors within the group. Each firewall sends its logs to its assigned primary Log Collector in the group.
- Redundancy: If a firewall's primary Log Collector in the group fails, it will automatically start sending logs to its assigned secondary Log Collector from the same group. This ensures you don't lose logs.
- Scalability: As your logging needs grow, you can simply add more Log Collectors to a Collector Group. Panorama will redistribute the load.
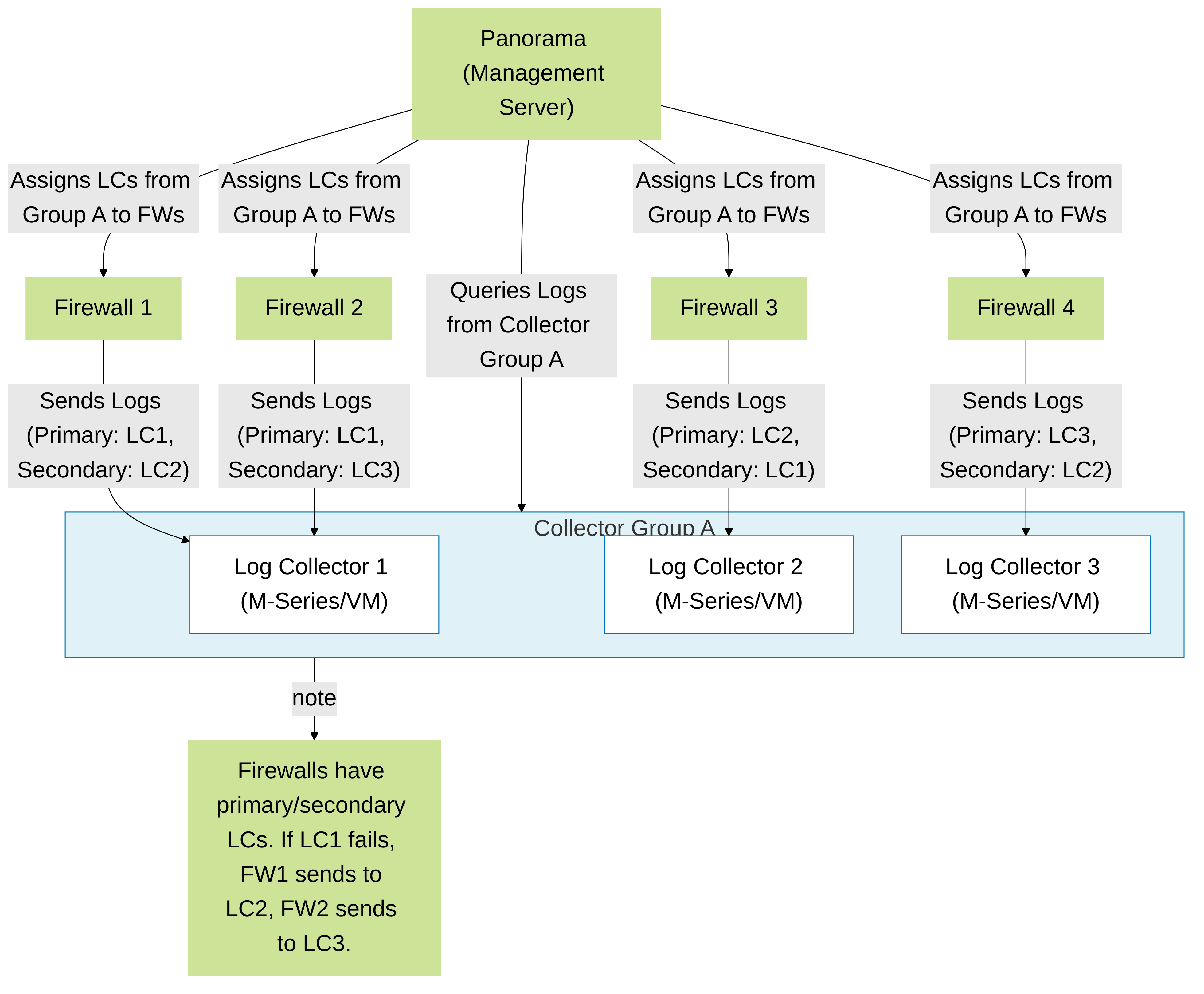
Collector Group: Distributing logs across multiple Log Collectors for scalability and redundancy. Firewalls have preferred Log Collectors within the group.
📊 Panorama Log Flow and Component Interaction
This sequence diagram illustrates how Panorama components like the management server and log collectors interact with firewalls and administrators. This is a high-level view of the day-to-day operations.
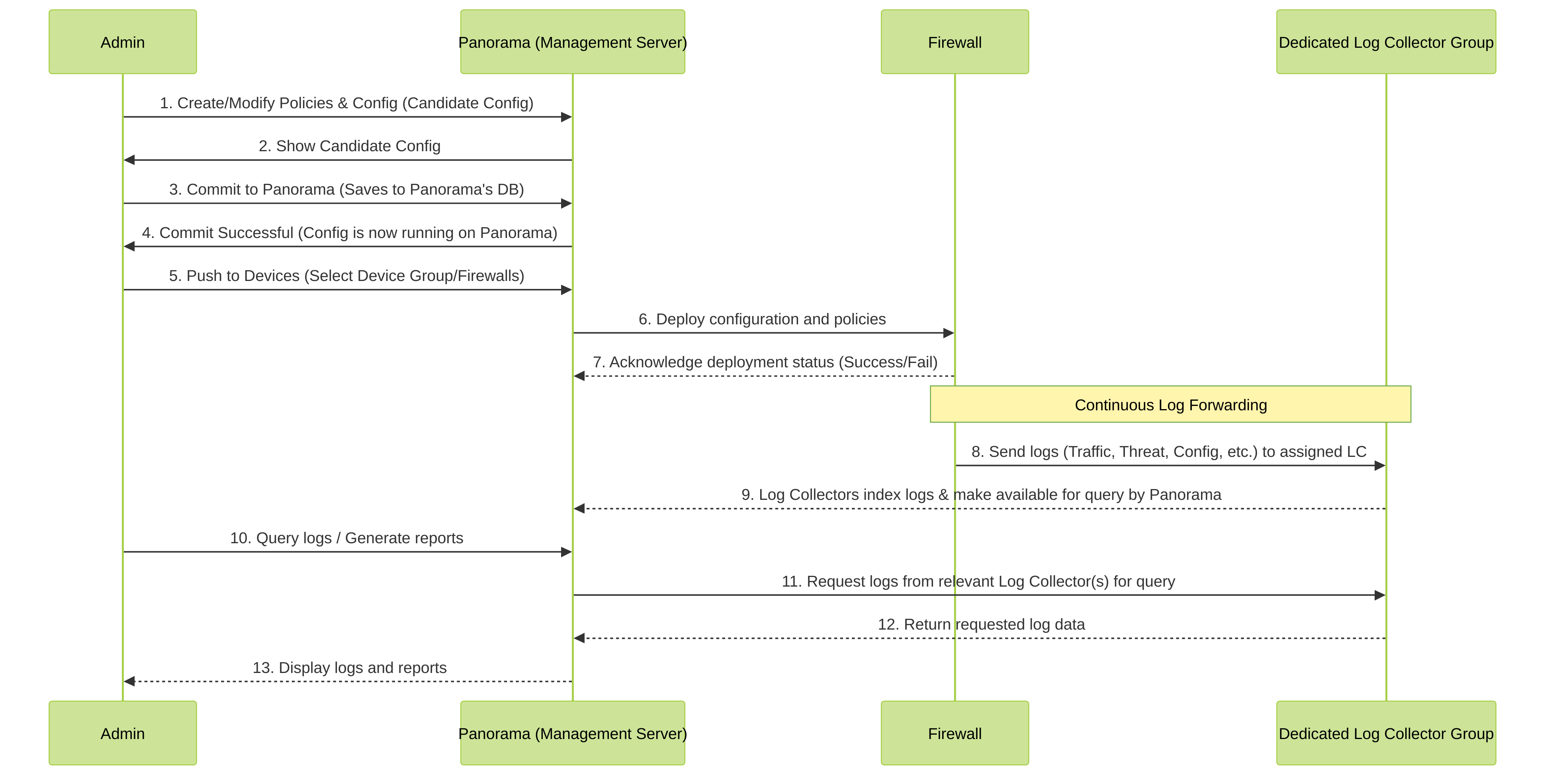
Sequence of operations involving Admin, Panorama, Firewalls, and Log Collectors.
📝 Interactive Panorama Quiz
Test your understanding of Panorama! (Focus: PCNSE relevant topics)
📚 References & Further Learning
For the most accurate and detailed information, always refer to the official Palo Alto Networks documentation for the Panorama version you are working with or studying for.
- Panorama Administrator's Guide (example: 11.1)
- Distributed Log Collection Details
- Panorama High Availability Details
- Panorama Modes Explained
- Panorama Datasheet
📽️ Recommended Video
Visual aids can be very helpful. Check out official Palo Alto Networks channels or trusted community contributors for video tutorials.
- Panorama Baseline High Availability Configuration – Palo Alto Networks (YouTube)
- Search YouTube for "Panorama deployment options Palo Alto Networks" or "Panorama for PCNSE".