Palo Alto Networks: Mastering Inter-VSYS Routing
Introduction to Inter-VSYS Routing in PAN-OS
Inter-VSYS (Virtual System) routing is a fundamental capability within Palo Alto Networks' PAN-OS that enables controlled communication between different logical firewall instances (VSYS) residing on a single physical PA-Series or VM-Series firewall. This feature is critical for scenarios requiring network segmentation with distinct administrative domains, security policies, and routing contexts, all while leveraging the same hardware. Common use cases include multi-tenancy, departmental isolation, service provider environments, and phased network consolidations.
The core principle of inter-VSYS routing is to allow traffic to pass from one VSYS to another internally through the firewall's dataplane , without requiring the traffic to physically egress and re-ingress the firewall. This optimizes performance and simplifies network design for specific segmentation needs.
Core Components and Concepts of Inter-VSYS Communication
Effectively implementing inter-VSYS routing requires a solid understanding of several key PAN-OS components and concepts:
-
Virtual Systems (VSYS):
VSYS are logical, independent firewall instances within a single physical Palo Alto Networks firewall. Each VSYS operates with its own:
- Administrative domain (separate administrators can be assigned)
- Configuration (interfaces, zones, policies, routing, objects, logs, reporting)
- Security policies, NAT policies, QoS policies, Decryption policies, etc.
- Virtual Routers (VRs) for routing decisions.
- Log database and reporting capabilities.
VSYS are enabled by a specific license on the firewall. When a firewall is in multi-VSYS mode, one VSYS is designated as `vsys1` (often used for management or shared services), and subsequent VSYS are created (e.g., `vsys2`, `vsys3`).
-
Virtual Routers (VR):
Each VSYS contains one or more Virtual Routers. A VR maintains its own routing table (FIB - Forwarding Information Base) and makes forwarding decisions for traffic within or passing through its associated VSYS. For inter-VSYS routing, static routes are configured within each VSYS's VR to direct traffic destined for another VSYS. While dynamic routing protocols (BGP, OSPF, RIP) can operate within a VR, inter-VSYS routing relies on a special type of static route.
-
External Zones (Inter-VSYS Zones):
This is a pivotal concept for inter-VSYS communication. An "External Zone" in this context is a special type of Security Zone in PAN-OS that does not have any physical or virtual interfaces assigned to it. Instead, it serves as a logical conduit or placeholder representing the connection to another VSYS.
- When configuring inter-VSYS routing from VSYS1 to VSYS2, you create an External Zone in VSYS1 (e.g., `Zone-to-VSYS2`) to represent the "entry point" into VSYS2 from VSYS1's perspective.
- Conversely, in VSYS2, you create an External Zone (e.g., `Zone-from-VSYS1`) to represent traffic arriving from VSYS1.
- Security policies are then written using these external zones as either source or destination zones.
CRITICAL (Palo Alto Networks): External Zones used for inter-VSYS routing are purely logical constructs within PAN-OS. They do not consume physical interfaces and are essential for applying security policies to traffic transiting between virtual systems. -
Static Routes with "Next VSYS":
To direct traffic from one VSYS to another, you configure static routes in the source VSYS's Virtual Router. The key differentiation for inter-VSYS static routes is the "Next Hop" type. Instead of specifying an IP address or interface, you select "Next VSYS" and then choose the target VSYS from a dropdown list (which is populated based on VSYS visibility settings).
-
Example: In VSYS1's VR, to route traffic to network 192.168.100.0/24 located in VSYS2, you would create a static route:
- Destination: 192.168.100.0/24
- Interface: (Leave blank or not applicable for Next VSYS)
- Next Hop Type: Next VSYS
- Next VSYS: `vsys2` (or the appropriate target VSYS name)
-
Example: In VSYS1's VR, to route traffic to network 192.168.100.0/24 located in VSYS2, you would create a static route:
-
Security Policies for Inter-VSYS Traffic:
All traffic passing between VSYS, even though it remains within the same physical firewall, must be explicitly permitted by Security Policies in both the source and destination VSYS.
-
In the Source VSYS (e.g., VSYS1):
- Source Zone: Internal zone (e.g., `VSYS1-Trust`)
- Source Address: Networks/IPs in VSYS1
- Destination Zone: The External Zone representing the target VSYS (e.g., `Zone-to-VSYS2`)
- Destination Address: Networks/IPs in VSYS2
- Application, Service, Action (Allow), Security Profiles (Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, WildFire, etc.)
-
In the Destination VSYS (e.g., VSYS2):
- Source Zone: The External Zone representing the source VSYS (e.g., `Zone-from-VSYS1`)
- Source Address: Networks/IPs in VSYS1
- Destination Zone: Internal zone (e.g., `VSYS2-Trust`)
- Destination Address: Networks/IPs in VSYS2
- Application, Service, Action (Allow), Security Profiles.
PCNSE/PCNSA Exam Note (Palo Alto Networks): Remember that inter-VSYS traffic is subject to full policy evaluation, including App-ID, Content-ID, and User-ID, in both participating VSYS if configured. This ensures consistent security posture even for internal logical segmentation. -
In the Source VSYS (e.g., VSYS1):
-
VSYS Visibility:
Before one VSYS can route traffic to another or be selected as a "Next VSYS" in a static route, it must be made "visible" to the other VSYS. This is a simple checkbox configuration within the VSYS settings. GUI Path: `Device > Virtual Systems > (select a VSYS) > Inter-VSYS Settings > Visible VSYS`. You need to add the other VSYS to this list. This must be done on both VSYS that need to communicate.
Detailed Configuration Steps for Inter-VSYS Routing
Configuring inter-VSYS routing involves a precise sequence of steps performed across the participating virtual systems. Let's consider an example where we want to enable communication from `VSYS1` (with internal network 10.1.1.0/24 in zone `VSYS1-TRUST`) to `VSYS2` (with internal network 10.2.2.0/24 in zone `VSYS2-TRUST`).
-
Enable Multi-VSYS Mode (if not already enabled):
This is a system-level setting. GUI: `Device > Setup > Management > General Settings > Enable Multi Virtual System Capability`. A reboot is typically required after enabling this.
-
Ensure VSYS Licenses are Applied and VSYS are Created:
Verify that the necessary VSYS licenses are active and that `vsys1`, `vsys2` (and any others) are created. GUI: `Device > Virtual Systems`.
-
Configure VSYS Visibility:
-
In VSYS1:
- Navigate to `Device > Virtual Systems`.
- Select `vsys1` from the list.
- Go to the `Inter-VSYS Settings` tab.
- In the `Visible VSYS` section, click `Add` and select `vsys2`.
- Click `OK`.
-
In VSYS2:
- Navigate to `Device > Virtual Systems`.
- Select `vsys2` from the list.
- Go to the `Inter-VSYS Settings` tab.
- In the `Visible VSYS` section, click `Add` and select `vsys1`.
- Click `OK`.
Gotcha! (Palo Alto Networks): Forgetting to configure VSYS visibility in *both* directions is a common mistake. If VSYS1 cannot "see" VSYS2, you won't be able to select VSYS2 as a "Next VSYS" in VSYS1's static routes, and vice-versa. -
In VSYS1:
-
Create External Zones in Each VSYS:
Ensure you are in the correct VSYS context (top-left VSYS dropdown in PAN-OS GUI).
-
In VSYS1:
- Navigate to `Network > Zones`.
- Click `Add`.
- Name: `EXT-to-VSYS2` (or a descriptive name).
- Type: `External`.
- Important: Do NOT assign any interfaces to this zone.
- Click `OK`.
-
In VSYS2:
- Switch context to `vsys2`.
- Navigate to `Network > Zones`.
- Click `Add`.
- Name: `EXT-from-VSYS1` (or a descriptive name).
- Type: `External`.
- Important: Do NOT assign any interfaces to this zone.
- Click `OK`.
-
In VSYS1:
-
Configure Virtual Routers and Static Routes:
Assume `VR1` in `vsys1` and `VR2` in `vsys2`.
-
In VSYS1 (context `vsys1`):
- Navigate to `Network > Virtual Routers`.
- Select `VR1` (the VR used by `VSYS1-TRUST` zone).
- Go to `Static Routes > IPv4` (or IPv6 if applicable).
- Click `Add`.
- Name: `Route-to-VSYS2-Net`.
- Destination: `10.2.2.0/24` (network in VSYS2).
- Interface: (Leave blank - not used for Next VSYS type).
- Next Hop Type: Select `Next VSYS`.
- Next VSYS: Select `vsys2` from the dropdown.
- Administrative Distance/Metric: Use defaults or adjust as needed.
- Click `OK`.
-
In VSYS2 (context `vsys2`):
- Navigate to `Network > Virtual Routers`.
- Select `VR2` (the VR used by `VSYS2-TRUST` zone).
- Go to `Static Routes > IPv4` (or IPv6 if applicable).
- Click `Add`.
- Name: `Route-to-VSYS1-Net`.
- Destination: `10.1.1.0/24` (network in VSYS1).
- Interface: (Leave blank).
- Next Hop Type: Select `Next VSYS`.
- Next VSYS: Select `vsys1` from the dropdown.
- Click `OK`.
-
In VSYS1 (context `vsys1`):
-
Define Security Policies:
-
In VSYS1 (context `vsys1`):
- Navigate to `Policies > Security`.
- Click `Add`.
- Name: `Allow-to-VSYS2`.
- Source Zone: `VSYS1-TRUST`.
- Source Address: `10.1.1.0/24` (or specific hosts).
- Destination Zone: `EXT-to-VSYS2` (the external zone created in VSYS1).
- Destination Address: `10.2.2.0/24` (or specific hosts in VSYS2).
- Application: `any` (or specific applications).
- Service/URL Category: `application-default` or specific services.
- Action: `Allow`.
- Profile Setting: Apply desired Security Profiles.
- Log Setting: Enable `Log at Session Start` and `Log at Session End`.
- Click `OK`.
-
In VSYS2 (context `vsys2`):
- Navigate to `Policies > Security`.
- Click `Add`.
- Name: `Allow-from-VSYS1`.
- Source Zone: `EXT-from-VSYS1` (the external zone created in VSYS2).
- Source Address: `10.1.1.0/24` (or specific hosts in VSYS1).
- Destination Zone: `VSYS2-TRUST`.
- Destination Address: `10.2.2.0/24` (or specific hosts).
- Application: `any` (or specific applications).
- Service/URL Category: `application-default` or specific services.
- Action: `Allow`.
- Profile Setting: Apply desired Security Profiles.
- Log Setting: Enable logging.
- Click `OK`.
PCNSE/PCNSA Exam Note (Palo Alto Networks): Pay close attention to the source and destination zones in security policies for inter-VSYS traffic. The "External Zone" is key. Traffic flows *from* an internal zone *to* an external zone in the source VSYS, and then *from* an external zone *to* an internal zone in the destination VSYS. -
In VSYS1 (context `vsys1`):
-
Commit Changes:
After all configurations are complete, perform a `Commit` operation on the firewall to apply the changes. A Panorama commit might be needed if managed by Panorama, ensuring policies are pushed to the correct VSYS on the firewall device group.
Inter-VSYS Traffic Flow Explained
Understanding the packet flow is crucial for troubleshooting and grasping how PAN-OS handles inter-VSYS traffic.
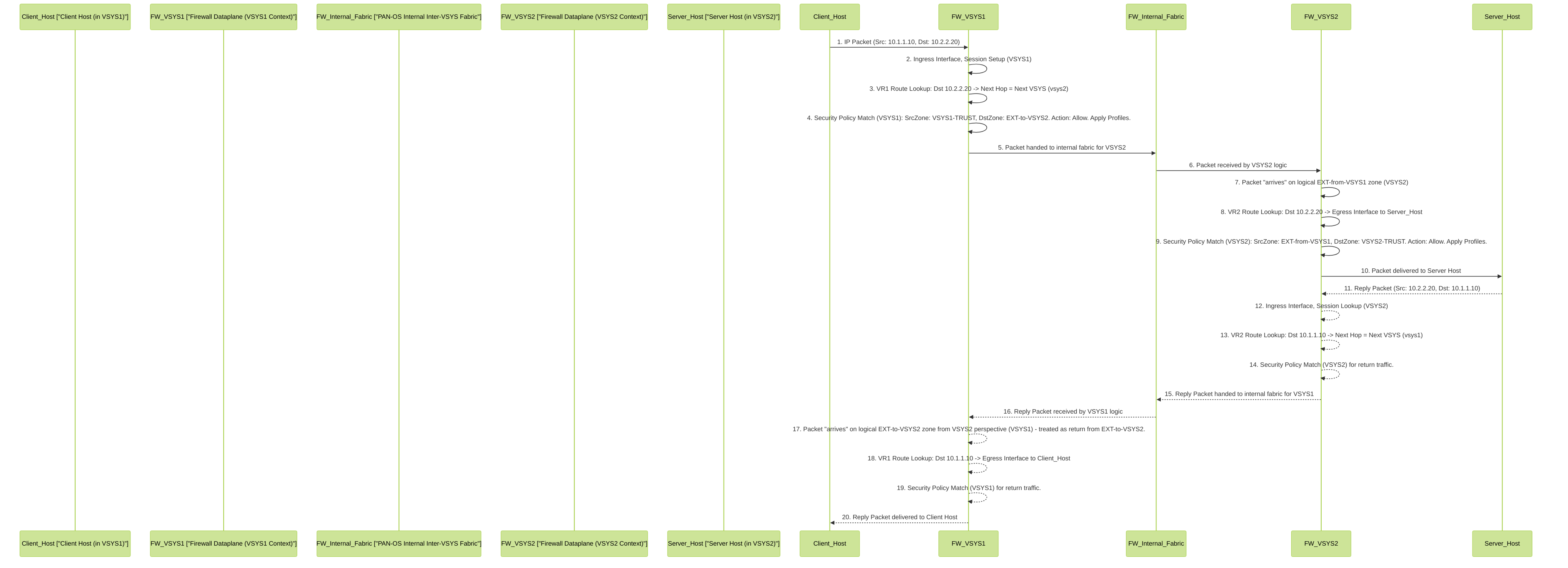
Detailed packet flow for inter-VSYS communication between a client in VSYS1 and a server in VSYS2. Note the two stages of policy lookup and routing, one in each VSYS.
Key stages in the flow:
-
Initiation (Source VSYS):
- Traffic ingresses an interface in the source VSYS (e.g., VSYS1).
- A session is created in VSYS1.
- The Virtual Router in VSYS1 performs a route lookup. The static route pointing to "Next VSYS" (e.g., VSYS2) is matched.
- A security policy lookup is performed in VSYS1. The policy must allow traffic from the source internal zone to the designated "External Zone" representing VSYS2.
- If allowed, traffic is passed internally by PAN-OS to the target VSYS.
-
Processing (Destination VSYS):
- The traffic logically "arrives" in the destination VSYS (e.g., VSYS2) via its corresponding "External Zone" (representing VSYS1).
- A new session (or related session, depending on PAN-OS version and specific handling) might be established in VSYS2 context.
- The Virtual Router in VSYS2 performs a route lookup to find the path to the final destination within its own network segments.
- A security policy lookup is performed in VSYS2. The policy must allow traffic from its "External Zone" (representing VSYS1) to the destination internal zone.
- If allowed, traffic is forwarded to the destination host.
- Return Traffic: The process is reversed for return traffic, requiring appropriate static routes and security policies in VSYS2 to send traffic back to VSYS1, and in VSYS1 to receive it.
Logical Inter-VSYS Architecture Diagram
This diagram illustrates the key logical components involved in connecting two Virtual Systems (VSYS1 and VSYS2) for inter-VSYS communication.
(e.g., 10.1.1.0/24)"/] VSYS1_VR_NOD [("VR1
Virtual Router")] VSYS1_EXT_ZONE_NOD [/"EXT-to-VSYS2 Zone
(External, No Interface)"/] VSYS1_POLICY_NOD {{"Security Policy:
From VSYS1-TRUST
To EXT-to-VSYS2
Allow"}} VSYS1_INT_ZONE_NOD --- VSYS1_VR_NOD VSYS1_VR_NOD --- VSYS1_POLICY_NOD VSYS1_POLICY_NOD --- VSYS1_EXT_ZONE_NOD VSYS1_VR_NOD -->|Static Route:
Dst: 10.2.2.0/24
Next-Hop: Next VSYS (vsys2)| VSYS1_EXT_ZONE_NOD end subgraph VSYS2 ["VSYS2 Context"] direction LR VSYS2_EXT_ZONE_NOD [/"EXT-from-VSYS1 Zone
(External, No Interface)"/] VSYS2_POLICY_NOD {{"Security Policy:
From EXT-from-VSYS1
To VSYS2-TRUST
Allow"}} VSYS2_VR_NOD [("VR2
Virtual Router")] VSYS2_INT_ZONE_NOD [/"VSYS2-TRUST Zone
(e.g., 10.2.2.0/24)"/] VSYS2_EXT_ZONE_NOD --- VSYS2_POLICY_NOD VSYS2_POLICY_NOD --- VSYS2_VR_NOD VSYS2_VR_NOD --- VSYS2_INT_ZONE_NOD VSYS2_VR_NOD -->|Static Route:
Dst: 10.1.1.0/24
Next-Hop: Next VSYS (vsys1)| VSYS2_EXT_ZONE_NOD end VSYS1_EXT_ZONE_NOD -.->|PAN-OS Internal Fabric
Logical Traffic Path| VSYS2_EXT_ZONE_NOD VSYS2_EXT_ZONE_NOD -.->|PAN-OS Internal Fabric
Logical Return Path| VSYS1_EXT_ZONE_NOD note1[VSYS1 Visibility: vsys2 enabled] note2[VSYS2 Visibility: vsys1 enabled] classDef vsys fill:#e6f3ff,stroke:#333,stroke-width:2px; class VSYS1,VSYS2 vsys; classDef zoneStyle fill:#lightgrey,stroke:#666,stroke-width:1px,rx:5px,ry:5px; class VSYS1_INT_ZONE_NOD,VSYS1_EXT_ZONE_NOD,VSYS2_EXT_ZONE_NOD,VSYS2_INT_ZONE_NOD zoneStyle; classDef vrStyle fill:#fff0b3,stroke:#666,stroke-width:1px,shape:cylinder; class VSYS1_VR_NOD,VSYS2_VR_NOD vrStyle; classDef policyStyle fill:#d4fada,stroke:#666,stroke-width:1px,shape:diamond; class VSYS1_POLICY_NOD,VSYS2_POLICY_NOD policyStyle;
Logical representation of Inter-VSYS routing setup between VSYS1 and VSYS2. This shows the external zones, virtual routers with static routes, and security policies facilitating the communication. The "PAN-OS Internal Fabric" represents the internal mechanism handling traffic transfer between VSYS.
Use Cases for Inter-VSYS Routing
Palo Alto Networks firewalls employ inter-VSYS routing for several strategic advantages:
- Multi-Tenancy: Service providers or large enterprises can host multiple tenants (customers, departments) on a single firewall. Each tenant gets a dedicated VSYS with its own policies, administration, and routing, while inter-VSYS routing allows for controlled shared services or communication if needed.
- Administrative Segregation: Different IT teams can manage their respective VSYS without impacting others. For example, one team manages the "Perimeter-VSYS" and another manages the "Datacenter-VSYS".
- Service Chaining (Internal): While more complex service chaining might involve dedicated appliances or VM-Series in a service chain, simpler forms can be achieved by forcing traffic through a specific VSYS for a particular type of inspection before it reaches another VSYS or its final destination.
- Regulatory Compliance: Isolating networks with specific compliance requirements (e.g., PCI-DSS) into their own VSYS, with strictly controlled inter-VSYS communication to other parts of the network.
- Phased Network Migration/Consolidation: When consolidating multiple physical firewalls or network segments onto a single Palo Alto Networks platform, VSYS can initially replicate the old segmented structure, with inter-VSYS routing maintaining connectivity.
- Testing and Development Environments: Creating isolated VSYS for testing new policies or configurations without affecting production VSYS. Inter-VSYS routing can allow controlled access to shared resources if necessary.
Troubleshooting Inter-VSYS Routing
When inter-VSYS communication fails, a systematic approach is needed. Focus on verifying each component in the traffic path within both participating VSYS.
| Symptom | Palo Alto Networks Checks & Commands (PAN-OS CLI) | Potential Issue |
|---|---|---|
| Cannot ping/connect from host in VSYS1 to host in VSYS2 |
Within VSYS1 context (`set system setting target-vsys vsys1`):
show counter global filter delta yes packet-filter yes show session all filter source <src_ip_vsys1> destination <dst_ip_vsys2> show routing route destination <dst_ip_vsys2> test routing fib-lookup virtual-router <vr_name_vsys1> ip <dst_ip_vsys2> show log traffic direction equal forward source <src_ip_vsys1> destination <dst_ip_vsys2> debug dataplane packet-diag set filter match source <src_ip_vsys1> destination <dst_ip_vsys2> debug dataplane packet-diag set capture stage firewall file inter_vsys_capture.pcap debug dataplane packet-diag set capture on (Reproduce issue, then `debug dataplane packet-diag set capture off`)Repeat similar checks in VSYS2 context for return traffic. |
- Missing/incorrect static route in VSYS1 VR.
- Security policy in VSYS1 blocking (source internal to dest external zone). - Missing/incorrect static route in VSYS2 VR for return path. - Security policy in VSYS2 blocking (source external to dest internal zone). - VSYS visibility not set correctly. - Incorrect External Zone configuration. - NAT issues if NAT is involved. |
| "Next VSYS" option not available in static route configuration | GUI: `Device > Virtual Systems > (select source VSYS) > Inter-VSYS Settings > Visible VSYS`. | Target VSYS is not added to the "Visible VSYS" list of the source VSYS. |
| Traffic logged as allowed in VSYS1, but no session in VSYS2 or no response |
Check logs and session table in VSYS2 (`set system setting target-vsys vsys2`):
show session all filter source <src_ip_vsys1> destination <dst_ip_vsys2> show log traffic direction equal forward source <src_ip_vsys1> destination <dst_ip_vsys2> |
- Routing issue in VSYS2 (cannot reach final destination).
- Security policy in VSYS2 blocking (from external zone to internal). - Asymmetric routing for return traffic. |
| Intermittent connectivity |
Check resource utilization:
show running resource-monitorCheck for commit failures or partial commits if using Panorama. |
- Resource exhaustion on the firewall.
- Unstable routes (though less likely with static inter-VSYS routes). - Conflicting configurations. |
Key Troubleshooting Steps:
- Verify VSYS Visibility: Ensure both VSYS can "see" each other (`Device > Virtual Systems > [VSYS] > Inter-VSYS Settings`).
- Check External Zones: Confirm they are type `External` and have no interfaces assigned, and are used correctly in policies.
-
Validate Static Routes:
- Source VSYS: Route to destination network with `Next Hop Type: Next VSYS` and correct target VSYS.
- Destination VSYS: Route back to source network with `Next Hop Type: Next VSYS` and correct target VSYS.
- Use `show routing route` and `test routing fib-lookup` in each VSYS context.
-
Inspect Security Policies:
- Source VSYS: Policy from internal zone to external zone (for target VSYS), action `Allow`.
- Destination VSYS: Policy from external zone (for source VSYS) to internal zone, action `Allow`.
- Check policy hit counts and traffic logs. Pay attention to rule order.
- Examine Traffic Logs: Filter by source/destination IP and VSYS. Look for denied traffic or traffic not matching expected policies. Traffic logs will show the source and destination VSYS for inter-VSYS sessions.
-
Session Browser:
Use `show session id
` or `show session all filter ...` to see session details, including ingress/egress VSYS and security rule matched. - Packet Captures: If necessary, use `debug dataplane packet-diag` to capture traffic. Capturing at `stage firewall` can show policy evaluation. This is an advanced technique.
NAT and Inter-VSYS Routing
Network Address Translation (NAT) can be applied to inter-VSYS traffic just like any other traffic passing through a Palo Alto Networks firewall. NAT policies are configured per-VSYS.
Consider a scenario where VSYS1 (internal 10.1.1.0/24) needs to communicate with VSYS2 (internal 10.2.2.0/24), but VSYS2 expects all traffic from VSYS1 to appear as if it's coming from 192.168.100.1.
-
In VSYS1:
- A Source NAT policy would be configured.
-
Original Packet:
- Source Zone: `VSYS1-TRUST`
- Destination Zone: `EXT-to-VSYS2` (the external zone for inter-VSYS traffic)
- Source Address: `10.1.1.0/24`
- Destination Address: `10.2.2.0/24`
-
Translated Packet (Source IP Translation):
- Type: Dynamic IP and Port (DIPP) or Static IP
- Translated Address: A specific IP like `192.168.100.1` (if using an address object of that IP)
- Traffic arriving in VSYS2: The source IP will appear as `192.168.100.1`. Security policies and routing in VSYS2 must be configured to handle this translated source IP.
Similarly, Destination NAT can be applied if services hosted in one VSYS need to be presented with different IP addresses to another VSYS.
Advanced Considerations and Best Practices
- Panorama Management: For firewalls with many VSYS, or multiple firewalls in multi-VSYS mode, Panorama is highly recommended for centralized management, policy deployment, and logging. Ensure Device Group hierarchies and Template Stacks are designed to accommodate VSYS-specific configurations.
- Resource Allocation: While VSYS are logical, they share the physical firewall's resources (CPU, memory, session capacity). Monitor resource utilization (`show running resource-monitor`) to ensure performance. QoS profiles can be applied per VSYS, but overall capacity is shared.
- Logging and Reporting: Configure log forwarding for each VSYS, potentially to different Syslog servers or Panorama instances if required for tenant separation. Custom reports can be generated per VSYS.
- Administrative Roles: Utilize role-based access control (RBAC) to define granular administrative permissions for different VSYS administrators.
- Naming Conventions: Adopt a clear and consistent naming convention for VSYS, External Zones (e.g., `EXT-to-VSYS_TargetName`, `EXT-from-VSYS_SourceName`), routes, and policies. This greatly aids in readability and troubleshooting.
- Scalability: Be mindful of the maximum number of VSYS supported by the firewall platform. As the number of VSYS and inter-VSYS routes increases, configuration complexity can grow.
- Security Profiles: Always apply appropriate Security Profiles (Threat Prevention, URL Filtering, WildFire, etc.) to inter-VSYS security policies. Just because traffic is internal to the firewall doesn't mean it's inherently safe. Treat inter-VSYS boundaries as security checkpoints.
Mermaid Diagram: Inter-VSYS Configuration Overview
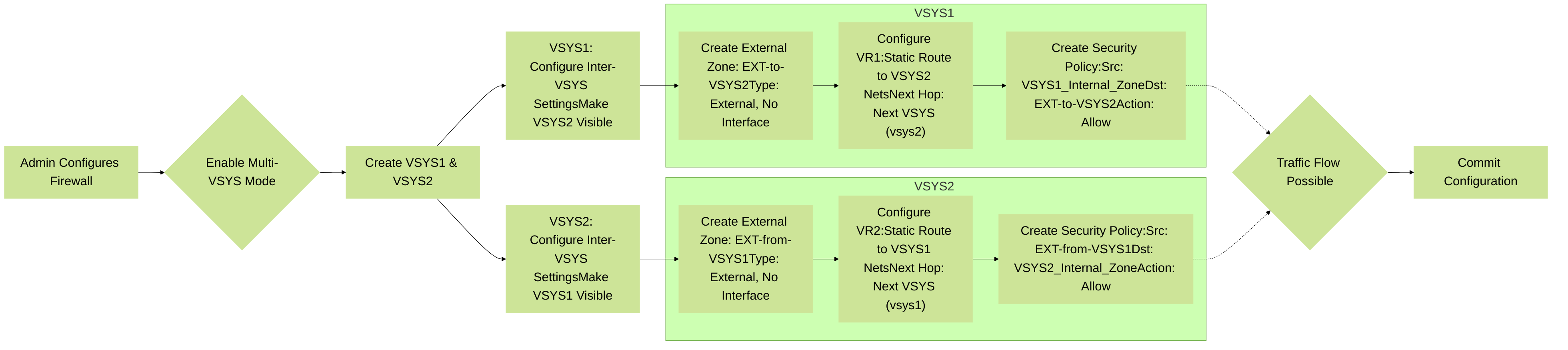
High-level overview of the administrative steps required to configure inter-VSYS routing between VSYS1 and VSYS2 on a Palo Alto Networks firewall.