🔍 Mastering Layer 2 Interfaces in Palo Alto Networks Firewalls: A Comprehensive Guide for PCNSE
Palo Alto Networks Next-Generation Firewalls (NGFWs) offer robust Layer 2 (L2) interface deployment options, enabling seamless integration into existing network segments without requiring IP address changes. This "bump-in-the-wire" or "transparent mode" capability allows the firewall to operate like a multi-port bridge, inspecting traffic at Layer 2 while applying comprehensive Layer 7 security services such as App-ID™, User-ID™, Content-ID™, and Threat Prevention. This guide provides an in-depth exploration of Layer 2 interfaces, their configuration, use cases, and considerations within the PAN-OS ® environment, tailored for network security professionals and PCNSE aspirants.
🎯 Core Concepts of PAN-OS Layer 2 Interfaces
When an interface on a Palo Alto Networks firewall is configured as Layer 2, it operates at the data link layer of the OSI model. It does not participate in IP routing but forwards frames based on MAC addresses. Key characteristics include:
- No IP Address: Layer 2 interfaces (and their subinterfaces) do not have IP addresses assigned directly to them. Traffic is forwarded based on destination MAC addresses learned by the firewall.
- MAC Address Learning: The firewall learns MAC addresses on its Layer 2 interfaces and maintains a MAC address table, similar to a switch.
- VLAN Tagging Support: IEEE 802.1Q VLAN tagging is fully supported, allowing for the creation of Layer 2 subinterfaces, each associated with a specific VLAN ID.
- Security Zones: Each Layer 2 interface or subinterface must be assigned to a Security Zone. Security policies are then applied between zones to control traffic flow and enforce security.
- Full Security Services: Traffic traversing Layer 2 interfaces is subject to the full suite of Palo Alto Networks security services, including App-ID, Content-ID, User-ID, Threat Prevention (Antivirus, Anti-Spyware, Vulnerability Protection, WildFire ® analysis), URL Filtering, and SSL Decryption.
✅ Best Use Cases for Layer 2 Interfaces
Layer 2 deployment mode is highly versatile. Here are some common scenarios where it excels:
- Transparent Deployment (Stealth Mode): Ideal for inserting a firewall into an existing network segment without changing IP addressing schemes or routing. This minimizes disruption and complexity during initial deployment. For example, placing a firewall between an access layer switch and a distribution layer switch to inspect east-west traffic.
- Inline Security for Internal Segments: Secure traffic between internal network segments (e.g., different departments or server farms) that reside on the same IP subnet but are physically or logically separated by the firewall using VLANs.
- VLAN Segmentation and Inter-VLAN Security: The firewall can connect to a switch trunk port, process traffic for multiple VLANs using Layer 2 subinterfaces, and apply distinct security policies for each VLAN. While the L2 interface itself doesn't route between VLANs, it can be combined with L3 VLAN Interfaces (SVIs) for inter-VLAN routing and security.
- Data Center Segmentation: Inspect traffic between virtual machines or physical servers within the same Layer 2 domain in a data center, providing granular control and threat prevention without altering the network topology.
- Gradual Migration to Full L3 Firewall: Deploy in Layer 2 initially for quick security wins, and then gradually migrate segments to Layer 3 interfaces on the firewall as the network evolves.
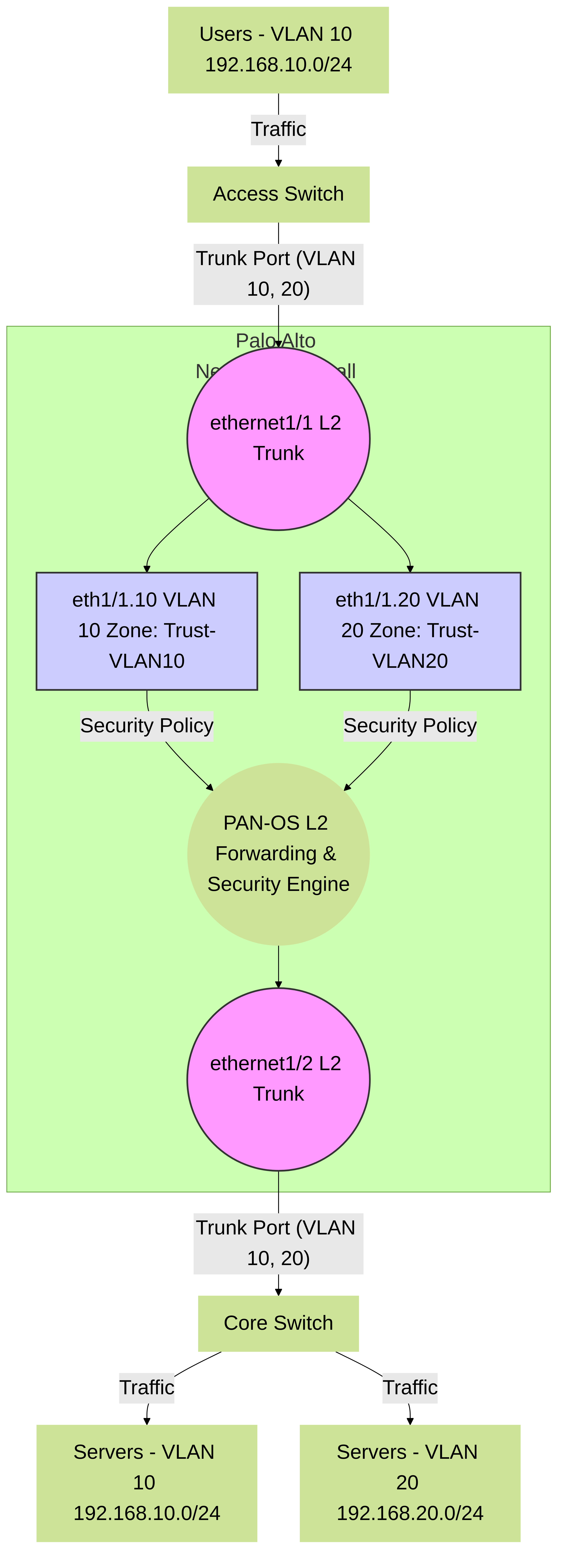
Palo Alto Networks Firewall in Layer 2 mode with VLAN subinterfaces, inspecting traffic between VLANs trunked from an access switch to a core switch.
⚙️ Detailed Configuration Steps in PAN-OS
Configuring a Layer 2 interface involves setting the interface type, assigning it to a security zone, and optionally configuring subinterfaces for VLANs.
Configuring a Physical Layer 2 Interface (No VLANs)
- Navigate to Interface Settings: In the PAN-OS web interface, go to Network > Interfaces > Ethernet .
-
Select and Configure Interface:
Click on the desired physical interface (e.g.,
ethernet1/1).- In the configuration window, set the Interface Type to Layer2 .
- (Optional) Add a Comment for easy identification.
-
On the
Config
tab:
- Under VLAN , leave it as None if this interface will handle untagged traffic or if subinterfaces will be used for tagged traffic.
-
Assign the interface to a new or existing
Security Zone
(e.g.,
L2-Trust). This zone will be used in security policies. - (Optional) Configure Link Speed/Duplex if auto-negotiation is not desired or not working correctly.
- (Optional) Assign a Management Profile if you need to allow management services (HTTPS, SSH, SNMP, Ping) to the firewall *through* this interface (requires a Layer 3 interface with an IP in the same broadcast domain for actual access, or use the management interface). For pure L2 forwarding, this is often not needed on data plane L2 interfaces.
- Click OK .
-
Repeat for Other Interfaces:
If you are creating a simple L2 bridge between two interfaces, configure a second L2 interface (e.g.,
ethernet1/2) and assign it to a different security zone (e.g.,L2-Untrust) or the same zone if appropriate for your policy logic. - Commit Configuration: Click Commit in the top-right corner of the web interface and then Commit again to apply the changes.
Configuring Layer 2 Subinterfaces for VLANs
When the Layer 2 interface needs to process 802.1Q tagged traffic, you create subinterfaces, each corresponding to a VLAN ID.
-
Ensure Physical Interface is Layer 2:
The parent physical interface (e.g.,
ethernet1/1) must first be configured with Interface Type: Layer2 . The parent L2 interface itself is typically assigned a security zone, often a "parent" or "trunk" zone. -
Add Subinterface:
Select the configured physical Layer 2 interface (e.g.,
ethernet1/1) in the Network > Interfaces > Ethernet list. Click Add Subinterface . -
Configure Subinterface:
-
Interface Name/Tag:
The subinterface will be named automatically (e.g.,
ethernet1/1.10). Enter the Tag (VLAN ID, e.g.,10). - (Optional) Add a Comment .
-
On the
Config
tab:
-
Assign the subinterface to a new or existing
Security Zone
(e.g.,
VLAN10-L2-Zone). Each subinterface can be in a different zone for granular policy control.
-
Assign the subinterface to a new or existing
Security Zone
(e.g.,
- No IP address configuration is needed for L2 subinterfaces.
- Click OK .
-
Interface Name/Tag:
The subinterface will be named automatically (e.g.,
- Repeat for Additional VLANs: Create more subinterfaces as needed for other VLANs on the same physical port.
- Commit Configuration.
! PAN-OS CLI Example: Configuring a Layer 2 interface and a subinterface configure set network interface ethernet ethernet1/1 layer2 set network interface ethernet ethernet1/1 layer2 units ethernet1/1.10 tag 10 set zone L2-VLAN10 network layer2 ethernet1/1.10 set zone L2-TRUNK-PARENT network layer2 ethernet1/1 ! Assign security zones appropriately in your policies exit
Inter-VLAN Routing with Layer 2 Interfaces and VLAN Interfaces (SVIs)
Pure Layer 2 interfaces forward traffic within the same VLAN (or broadcast domain if untagged). To route traffic between different VLANs that are processed by Layer 2 interfaces/subinterfaces on the firewall, you need Layer 3 VLAN interfaces (often called Switched Virtual Interfaces or SVIs).
-
Configure L2 Interfaces/Subinterfaces:
As described above, configure your physical interface as Layer 2 and create L2 subinterfaces for each VLAN (e.g.,
ethernet1/1.10for VLAN 10,ethernet1/1.20for VLAN 20), assigning them to appropriate L2 security zones (e.g.,L2-VLAN10,L2-VLAN20). - Create VLAN Objects (Optional but Recommended): Navigate to Network > VLANs and click Add . Create VLAN objects (e.g., `VLAN10_Object`, `VLAN20_Object`) and associate them with the respective L2 interfaces/subinterfaces. This step is primarily for logical grouping and is required if you intend to use these VLANs with Virtual Routers for L3 purposes.
-
Create VLAN Interfaces (SVIs):
- Navigate to Network > Interfaces > VLAN . Click Add .
-
A new logical VLAN interface is created (e.g.,
vlan.10). -
Assign this VLAN interface to a
Virtual Router
(e.g.,
default). -
Assign it to a
Security Zone
(e.g.,
L3-VLAN10). This zone will be used for L3 security policies. -
In the
IPv4
tab, assign an IP address that will act as the default gateway for devices in that VLAN (e.g.,
192.168.10.1/24for VLAN 10). - (Optional) Configure a Management Profile if needed.
- Click OK .
-
Repeat for other VLANs (e.g., create
vlan.20with IP192.168.20.1/24in zoneL3-VLAN20).
-
Security Policies:
Create security policies between the L3 zones (e.g., from
L3-VLAN10toL3-VLAN20) to control inter-VLAN traffic. - Commit Configuration.
In this setup, traffic from a host in VLAN 10 destined for VLAN 20 arrives at the L2 subinterface
ethernet1/1.10
, is passed to the L3 VLAN interface
vlan.10
, routed by the virtual router, subjected to security policy checks between
L3-VLAN10
and
L3-VLAN20
, and then forwarded out through
vlan.20
to the L2 subinterface
ethernet1/1.20
and onto the network.
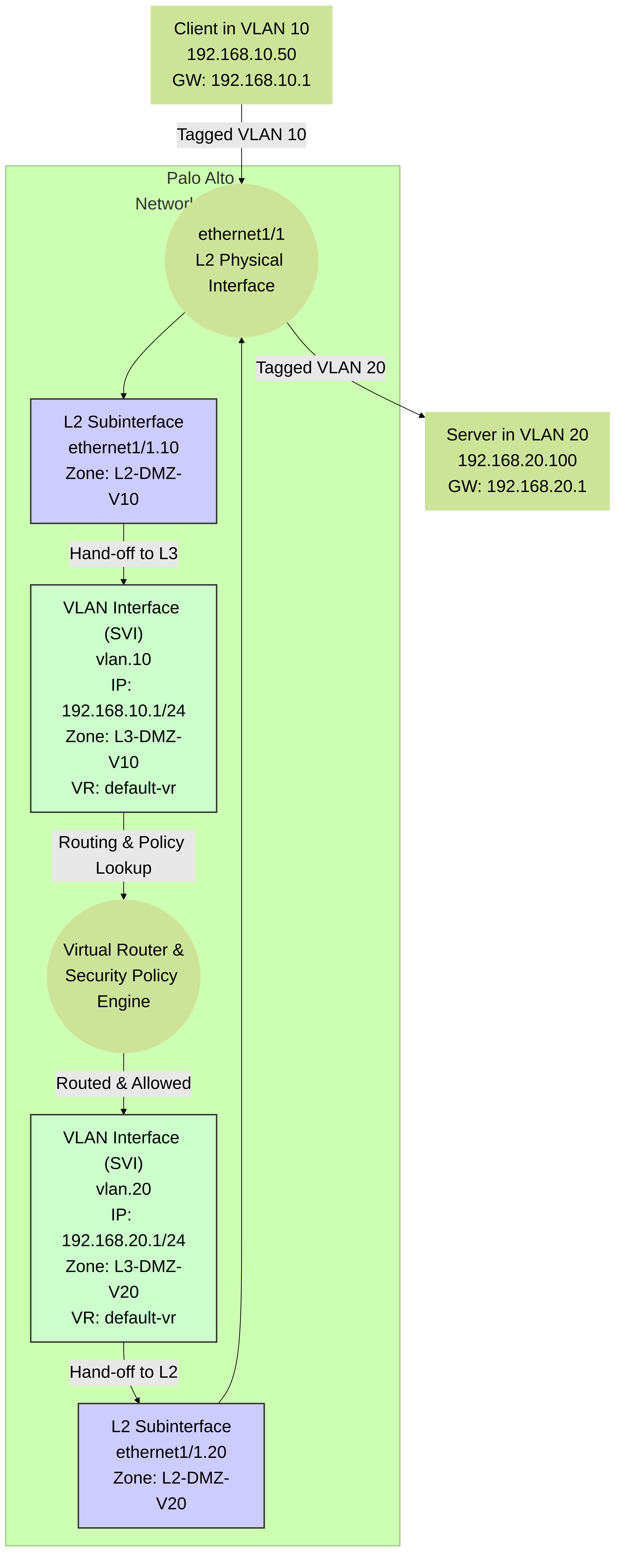
Inter-VLAN routing using Palo Alto Networks L2 subinterfaces and L3 VLAN interfaces (SVIs). Traffic flows from L2 subinterface to its corresponding SVI, is routed, policy-checked, and then passed to the destination SVI and its L2 subinterface.
⚠️ Considerations and Implications
-
High Availability (HA):
- In an HA Active/Passive pair, Layer 2 interfaces on both firewalls connect to the same Layer 2 network segment(s). MAC addresses learned on the active firewall are synchronized to the passive firewall.
- Path monitoring can be configured for Layer 2 interfaces. Failure of a monitored L2 link can trigger an HA failover.
- For L2 interfaces participating in an Aggregate Ethernet (AE) group with LACP, ensure LACP is configured correctly on both the firewall and the connected switches. HA LACP Pre-Negotiation can speed up failover.
- In HA Active/Active, L2 deployment is more complex and typically less common than Virtual Wire or L3 for A/A. Careful design is needed to manage traffic flows and session ownership.
-
Spanning Tree Protocol (STP):
Palo Alto Networks firewalls do not participate in STP (i.e., they don't run STP or generate/process BPDUs for STP calculations). They forward STP BPDUs transparently like any other multicast traffic if not explicitly blocked by policy.
Gotcha! (Palo Alto Networks): Because the firewall doesn't participate in STP, you CAN create Layer 2 loops if you connect multiple Layer 2 interfaces of the firewall to the same broadcast domain without proper loop prevention mechanisms on the connecting switches (like STP). The firewall will not break the loop. Always ensure your physical network design prevents loops.By default, BPDUs are forwarded. If you need to block BPDUs, you can use a Security Policy with an Application Override policy to block STP, or configure BPDU Filtering on the firewall interface (Network > Interfaces > Ethernet > Select Interface > Advanced > Other Info > BPDU Filtering).
-
MAC Address Table:
The firewall maintains a MAC address table for its Layer 2 interfaces. You can view this table using the CLI command:
show mac all
Or for a specific interface:show mac interface ethernet1/1.10
There are limits to the MAC table size, which vary by platform. If the table fills up, unknown unicast frames might be flooded, similar to a switch. - ARP Handling: In a pure Layer 2 deployment, the firewall forwards ARP requests and replies. It does not respond to ARPs for hosts behind it unless a Layer 3 interface (like an SVI) is configured for that subnet.
- Broadcast and Multicast Traffic: Broadcast and multicast traffic are forwarded across Layer 2 interfaces within the same VLAN/broadcast domain, subject to security policy rules if they create sessions (some multicast might not, depending on configuration).
- MTU (Maximum Transmission Unit): Ensure the MTU configured on the firewall's Layer 2 interfaces and subinterfaces matches the MTU of the connected network devices. The default Ethernet MTU on Palo Alto Networks firewalls is typically 1500 bytes. This can be adjusted under Network > Interfaces > Ethernet > (select interface) > Advanced > MTU . For subinterfaces, MTU is inherited from the physical parent but can sometimes be adjusted depending on PAN-OS version and platform.
💡 Feature Support on PAN-OS Layer 2 Interfaces
A key advantage of Palo Alto Networks L2 deployment is the broad feature support:
| Feature | Support on L2 Interfaces | Palo Alto Networks Specific Notes |
|---|---|---|
| App-ID™ | ✅ Supported | Full application identification and control. |
| User-ID™ | ✅ Supported | User mapping and policy enforcement based on user/group. |
| Content-ID™ (Threat Prevention, WildFire, URL Filtering, File Blocking) | ✅ Supported | Comprehensive threat inspection and content filtering. |
| SSL Decryption (Forward Proxy) | ✅ Supported | Ability to decrypt and inspect SSL/TLS traffic. |
| Security Policies | ✅ Supported | Zone-based policies to control traffic flow. Policies match on L2 interface/subinterface zones. |
| Zone Protection Profiles | ✅ Supported | Protect zones associated with L2 interfaces from floods and reconnaissance. |
| Quality of Service (QoS) | ✅ Supported | QoS can be applied to physical L2 interfaces and L2 subinterfaces. Policies are typically applied on egress. |
| NAT (Network Address Translation) | ❌ Not Directly Supported | NAT is a Layer 3 function. To perform NAT for traffic traversing L2 segments, you must use associated Layer 3 VLAN Interfaces (SVIs) where NAT policies can be applied. |
| Routing Protocols (OSPF, BGP, etc.) | ❌ Not Supported | Routing protocols operate at Layer 3 and are configured on L3 interfaces or VLAN Interfaces. |
| VPN Tunnels (IPSec, SSL VPN) | ❌ Not Terminated | VPN tunnels terminate on Layer 3 interfaces (physical L3, Tunnel, or Loopback interfaces with IP addresses). L2 interfaces can pass VPN traffic through if allowed by policy. |
| GlobalProtect Gateway/Portal | ❌ Not Directly Hosted | GlobalProtect services require L3 interfaces for termination. Traffic from GP clients can be inspected via L2 interfaces if it passes through them post-termination. |
| DHCP Server/Relay | ❌ Not Directly Supported | DHCP services are Layer 3 functions, configured on L3 interfaces or VLAN interfaces. |
🔗 Link Aggregation (LAG/Port-Channel) with Layer 2 Interfaces
Palo Alto Networks firewalls support IEEE 802.1AX (formerly 802.3ad) Link Aggregation Control Protocol (LACP) for bundling multiple physical Ethernet interfaces into a single logical interface called an Aggregate Ethernet (AE) interface. AE interfaces can be configured as Layer 2.
Configuring a Layer 2 AE Interface
-
Create Aggregate Group:
- Navigate to Network > Interfaces > Ethernet . Click Add Aggregate Group (or it might be under a separate "Aggregate Ethernet" tab in some PAN-OS versions).
-
An AE interface will be created (e.g.,
ae1). - Set the Interface Type to Layer2 .
-
Assign Member Interfaces:
-
Select the newly created AE interface (e.g.,
ae1). - In the Aggregate Group tab, click Add to select physical Ethernet interfaces that will be members of this LAG.
- All member interfaces must be of the same type (e.g., all Ethernet) and speed. They must not be configured for any other purpose.
-
Select the newly created AE interface (e.g.,
-
Configure LACP (Recommended):
- On the AE interface's configuration, enable LACP .
-
Set
LACP Mode
:
- Active: The firewall actively initiates LACP negotiations.
- Passive: The firewall only responds to LACP negotiations initiated by the peer. (At least one side must be Active).
- Set LACP Rate (Fast/Slow) to match the switch. 'Fast' (1 second) provides quicker detection of link failures.
- System Priority and Max Ports can usually be left at defaults unless specific design requirements exist.
- In HA deployments, consider enabling LACP Pre-Negotiate (or "Enable in HA Passive State" in older PAN-OS) on the passive firewall to speed up LACP convergence upon failover.
-
Configure Layer 2 Properties:
- Just like a physical L2 interface, assign the AE interface to a Security Zone .
- If handling tagged traffic, add Layer 2 Subinterfaces to the AE interface, specifying VLAN tags and assigning them to zones.
- Switch Configuration: Ensure the connected switch ports are configured as a port-channel with matching LACP settings.
- Commit Changes.
_interface_with_LACP.png)
Palo Alto Networks Layer 2 Aggregate Ethernet (AE) interface with LACP, bundling two physical ports. Subinterfaces are configured on the AE interface for VLAN segmentation.
🚦 Packet Flow in Layer 2 Mode
Understanding packet flow is crucial for troubleshooting and policy design.
- Ingress: A frame arrives on a Layer 2 interface (physical or subinterface).
-
VLAN Processing:
- If it's a subinterface, the frame's VLAN tag must match the subinterface's configured tag.
- If it's a physical L2 interface configured for untagged traffic, an untagged frame is processed.
- MAC Learning/Lookup: The source MAC address is learned and added to the MAC table for the ingress interface/VLAN if not already present. The destination MAC address is looked up in the MAC table.
- Zone Determination: The source zone is determined by the ingress L2 interface/subinterface.
-
Session Lookup (Slow Path/Fast Path):
-
Slow Path (First Packet):
If no existing session matches, the packet goes through the full policy evaluation:
- Security Policy Lookup: Based on source zone, destination zone (derived from egress interface determined by MAC lookup or flooding if unknown), source/destination IP, application (App-ID), and user (User-ID).
- If allowed, security profiles (Threat Prevention, URL Filtering, etc.) are applied.
- A session is created in the session table.
- Fast Path (Subsequent Packets): If an existing session matches, the packet bypasses some of the slower policy lookups and is processed according to the established session parameters, still undergoing content inspection.
-
Slow Path (First Packet):
If no existing session matches, the packet goes through the full policy evaluation:
-
Forwarding Decision:
- If the destination MAC is known and associated with another L2 interface/subinterface in a different zone, policies permitting, the frame is forwarded there.
- If the destination MAC is known and associated with another L2 interface/subinterface in the same zone, intra-zone traffic is allowed by default (unless explicitly blocked by an intra-zone policy). Security inspection still applies.
- If the destination MAC is unknown, the frame is flooded out all other Layer 2 interfaces/subinterfaces within the same VLAN/broadcast domain (that are in zones allowed by policy relative to the source zone).
- Egress: The frame is transmitted out the determined egress L2 interface.
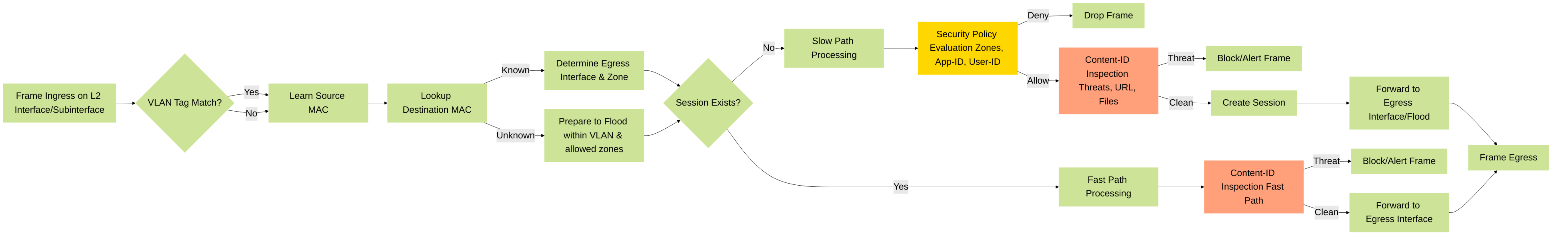
Simplified packet flow for a Palo Alto Networks firewall in Layer 2 mode. Note that even for L2, comprehensive security inspection occurs.
🛠️ Troubleshooting Layer 2 Deployments
Common PAN-OS CLI commands useful for troubleshooting L2 interface issues:
-
Interface Status:
show interface ethernet <interface_name>
show interface <interface_name> (provides more detail, including counters)
Look for admin/link status, speed/duplex, errors, drops. -
VLAN Configuration:
show vlan all
show vlan <vlan_id>
Verify VLANs and associated L2 interfaces/subinterfaces. -
MAC Address Table:
show mac all
show mac interface <interface_name_or_subinterface>
show mac vlan <vlan_id>
Check if expected MACs are being learned on correct interfaces/VLANs. -
Session Table:
show session all filter interface <interface_name>
show session id <session_id>
See if traffic is creating sessions and what policy/action is applied. -
Traffic Counters:
show counter interface <interface_name>
show counter global filter delta yes packet-filter yes "(ether.dst==<mac_addr> or ether.src==<mac_addr>)"
To see if specific MAC traffic is hitting the firewall. -
Global Counters (for drops):
show counter global | match drop
Look for various drop reasons. -
LACP Status (for AE interfaces):
show lacp aggregate-ethernet <ae_interface_name>
Verify LACP state, member port status, and partner information. -
Packet Diagnostics (Advanced):
debug dataplane packet-diag set filter on match DestIP=<IP> SrcIP=<IP> debug dataplane packet-diag set filter on match ether.src==<mac_addr> debug dataplane packet-diag show setting show counter global filter packet-filter yes delta yes "(ether.dst==<mac_addr> or ether.src==<mac_addr>) and (vlan.id==<vlan_id>)"
Use `debug dataplane packet-diag` cautiously in production as it can impact performance. The `show counter global filter` method is often safer for live troubleshooting. -
ARP Table (Relevant if SVIs are used):
show arp all
show arp interface <vlan_interface_name e.g., vlan.10>
📚 Additional Palo Alto Networks Resources
For further information, always refer to the official Palo Alto Networks documentation for your specific PAN-OS version:
- Palo Alto Networks TechDocs: PAN-OS Administrator's Guides (Networking section)
- Palo Alto Networks Knowledge Base: knowledgebase.paloaltonetworks.com
- Palo Alto Networks Live Community: live.paloaltonetworks.com