PCNSE Study Guide: Mastering Layer 3 Interfaces in Palo Alto Networks Firewalls
Layer 3 interfaces are a cornerstone of network segmentation and routing within Palo Alto Networks Next-Generation Firewalls (NGFWs). For the PCNSE certification, a profound understanding of their configuration, diverse capabilities, operational nuances, and troubleshooting within the PAN-OS environment is absolutely essential. These interfaces enable the firewall to participate in routing, enforce security policies between different IP networks, and connect various network segments.
Core Concepts of PAN-OS Layer 3 Interfaces
Understanding these core concepts is vital for effective deployment and management of Palo Alto Networks firewalls.
-
Virtual Router (VR) Association:
In PAN-OS, every Layer 3 interface, including physical interfaces, subinterfaces, loopback interfaces, and tunnel interfaces configured for Layer 3 mode,
must
be associated with a Virtual Router. The VR contains the routing table (RIB and FIB) used to make forwarding decisions for traffic arriving on or destined for that interface. A firewall can have multiple VRs, providing routing table isolation, which is crucial for multi-tenant environments or complex network segmentation. The 'default' VR is created automatically, but custom VRs can be created for specific routing needs.
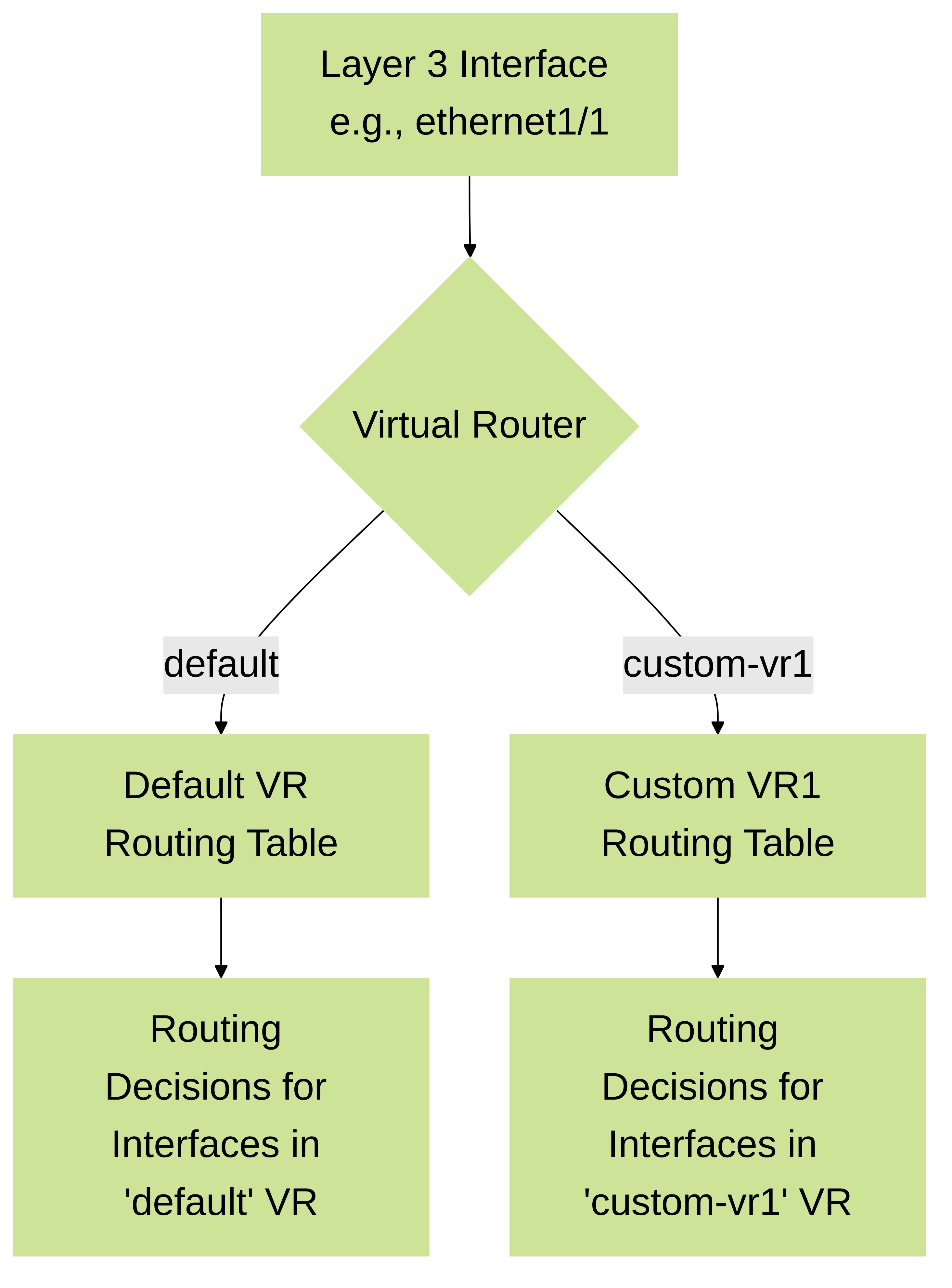
Diagram illustrating how Layer 3 interfaces are assigned to Virtual Routers in PAN-OS, leading to separate routing domains.
-
Security Zone Assignment:
Each Layer 3 interface must be assigned to a Security Zone. Zones are logical containers for one or more interfaces that represent segments of your network with similar security requirements (e.g., Trust, Untrust, DMZ). Security policies in PAN-OS are defined based on source and destination zones, not IP addresses directly (though IP addresses can be used as criteria within policies). Traffic traversing between interfaces in different zones requires an explicit security policy to be permitted. Traffic between interfaces within the same zone (intrazone) is allowed by default, but this can be changed with an intrazone policy.
PCNSE/PCNSA Exam Note (Palo Alto Networks): Understanding the relationship between interfaces, zones, and virtual routers is critical for policy creation and troubleshooting. Exam questions often test scenarios where traffic isn't flowing due to incorrect zone assignment or missing inter-zone security policies.
-
IP Address Configuration:
Layer 3 interfaces require IP addressing to participate in IP routing. PAN-OS supports several methods:
- Static IP: Manually assigning an IPv4 or IPv6 address and netmask/prefix length. This is the most common method for internal and DMZ interfaces.
- DHCP Client (IPv4/IPv6): The firewall interface can obtain an IP address, default gateway, and DNS server information from a DHCP server. This is often used for external interfaces connecting to an ISP. You can configure PAN-OS to automatically add a default route learned via DHCP.
- PPPoE Client (IPv4): The interface can establish a Point-to-Point Protocol over Ethernet session, typically used with DSL or other broadband connections. It involves authentication (PAP/CHAP) and IP address assignment from the ISP.
-
Interface Management Profiles:
To allow management access (e.g., HTTPS, SSH, SNMP, Ping) to the firewall *through a dataplane Layer 3 interface*, an Interface Management Profile must be configured and applied. These profiles specify which management services are permitted and, crucially, from which source IP addresses or subnets. This is distinct from managing the firewall via its dedicated MGT (management) interface.
Gotcha! (Palo Alto Networks): Forgetting to apply an Interface Management Profile or restricting permitted IPs too much is a common reason for being unable to manage the firewall via a dataplane interface. Always ensure "Ping" is enabled in the profile for basic connectivity testing.
-
Advanced Settings (per interface):
- MTU (Maximum Transmission Unit): Defines the largest PDU size an interface can transmit without fragmentation. Default is typically 1500 bytes for Ethernet. Mismatched MTUs can cause performance issues or connectivity problems, especially with VPN tunnels or when traversing networks with smaller MTUs. PAN-OS allows MTU configuration per Layer 3 interface.
- Adjust TCP MSS (Maximum Segment Size): The firewall can actively adjust the MSS value in TCP SYN packets. This is useful to prevent IP fragmentation, particularly when traffic passes through tunnels (like IPsec VPNs) that add overhead, effectively reducing the path MTU. By reducing the MSS, endpoints negotiate smaller TCP segments. PAN-OS allows enabling this feature and optionally setting a specific MSS value.
- LLDP (Link Layer Discovery Protocol): PAN-OS firewalls can participate in LLDP, allowing them to discover and be discovered by adjacent LLDP-enabled network devices. An LLDP Profile defines what information is sent and received. This is useful for network mapping and troubleshooting.
- Enable ECMP (Equal Cost Multi-Path): For Layer 3 interfaces, ECMP settings can be configured at the virtual router level, allowing the firewall to load balance traffic across multiple equal-cost paths to the same destination.
Types of Layer 3 Interfaces in PAN-OS
Palo Alto Networks firewalls support various types of interfaces that can operate in Layer 3 mode:
- Physical Interfaces (Ethernet): Standard RJ-45 or SFP/SFP+ ports on the firewall.
-
Layer 3 Subinterfaces:
Logical interfaces created on a physical Layer 3 interface. Each subinterface is tagged with an IEEE 802.1Q VLAN ID, allowing a single physical port to connect to multiple VLANs, each with its own IP address, zone, and routing configuration. This is extremely useful for segmenting traffic without requiring multiple physical interfaces.
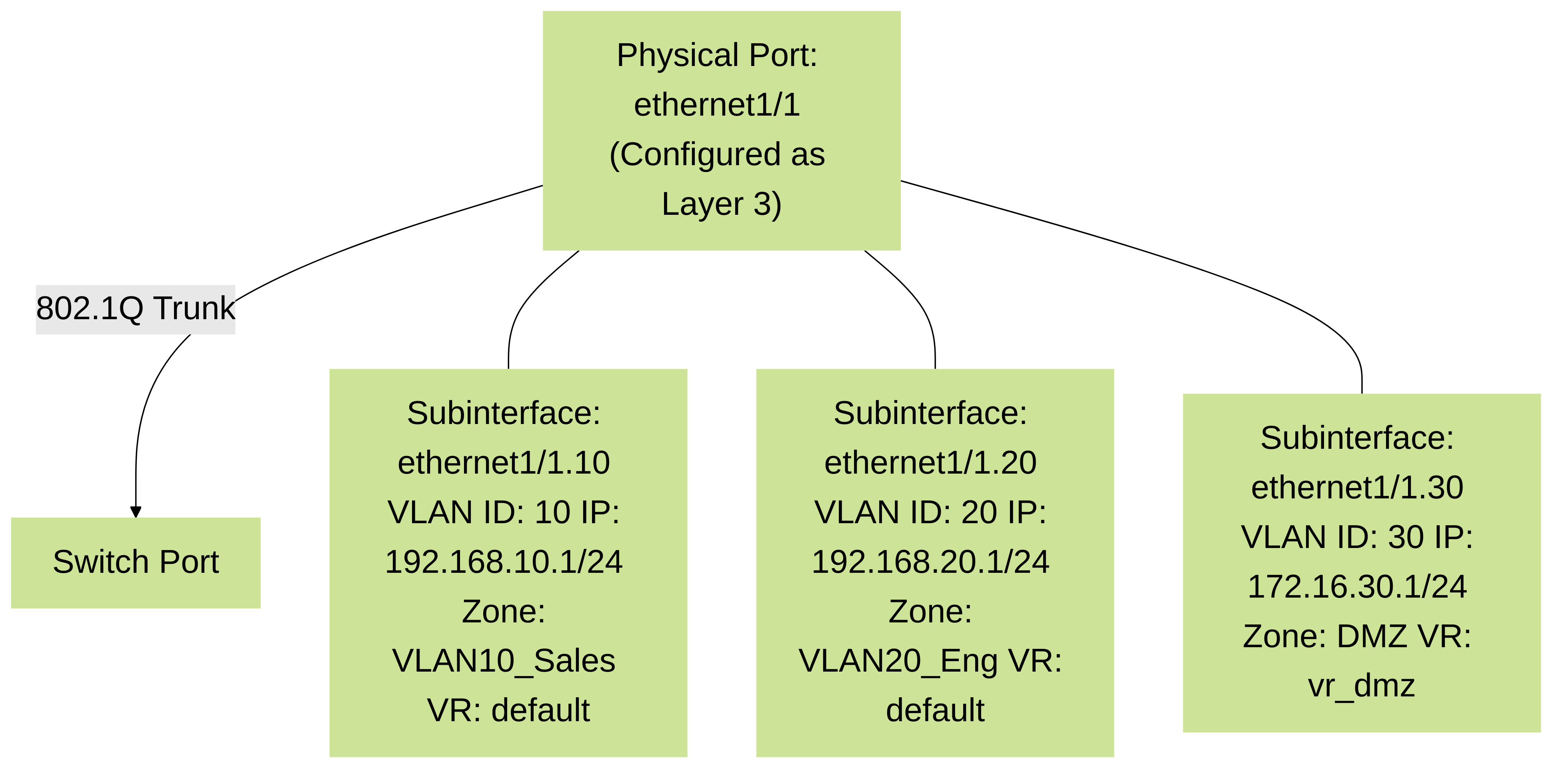
Diagram illustrating Layer 3 subinterfaces on a single physical port, each associated with a VLAN ID, IP configuration, Security Zone, and potentially a different Virtual Router.
- Aggregate Ethernet (AE) Interfaces: Logical interfaces that bundle multiple physical Ethernet interfaces into a single link (Link Aggregation Group - LAG). AE interfaces can be configured as Layer 3 interfaces, providing increased bandwidth and redundancy. LACP (Link Aggregation Control Protocol) is typically used for dynamic bundling.
-
Loopback Interfaces:
Virtual, software-only interfaces that are always up as long as the firewall is powered on and the interface is administratively enabled. They are commonly used for:
- Providing a stable BGP Router ID.
- Termination points for management services or VPNs if a stable, non-physical IP is needed.
- As a source interface for services like SNMP traps or syslog messages originating from the firewall.
- Tunnel Interfaces: Logical interfaces used as endpoints for IPsec VPN tunnels, GRE tunnels, and GlobalProtect VPNs. They are assigned an IP address (often unnumbered for route-based VPNs, or with an IP for GRE/GlobalProtect) and placed in a security zone and virtual router. Traffic routed into a tunnel interface is encrypted (for IPsec) and sent to the remote tunnel peer.
Key Features Supported by PAN-OS Layer 3 Interfaces
Layer 3 interfaces are the conduits through which traffic flows and becomes subject to the rich feature set of PAN-OS:
- Security Policy Enforcement (App-ID, Content-ID, User-ID): Traffic ingressing and egressing Layer 3 interfaces is evaluated against Security Policies. These policies leverage App-ID to identify applications, Content-ID for threat prevention (antivirus, anti-spyware, vulnerability protection, WildFire analysis, URL filtering), and User-ID to identify users and groups, enabling granular control.
- SSL Forward Proxy Decryption: If SSL Decryption policies are configured, traffic passing through Layer 3 interfaces can be decrypted, inspected for threats, and then re-encrypted. The firewall acts as a "man-in-the-middle" for this purpose.
-
NAT (Network Address Translation):
NAT policies in PAN-OS are applied to traffic traversing zones associated with Layer 3 interfaces.
- Source NAT (SNAT): Translates private source IP addresses to a public IP address (or pool) for outbound internet access. Types include Dynamic IP and Port (DIPP), Static IP, and Dynamic IP.
- Destination NAT (DNAT): Translates a public destination IP address to a private IP address for inbound access to internal servers (e.g., web servers, mail servers). Port translation is also possible.
- No NAT: For traffic that should not be translated.
- QoS (Quality of Service): QoS profiles can be applied to Layer 3 interfaces (typically egress interfaces) to manage bandwidth and prioritize traffic. PAN-OS QoS allows for defining traffic classes, setting guaranteed bandwidth, maximum bandwidth, and priority levels.
-
Routing Protocols:
Layer 3 interfaces participate in dynamic routing. PAN-OS supports:
- Static Routes: Manually configured routes.
- OSPF (v2 and v3): Interfaces can be enabled for OSPF, forming adjacencies and exchanging LSAs.
- BGP (MP-BGP for IPv4/IPv6): For complex inter-AS routing or large enterprise networks.
- RIPv2: A simpler distance-vector protocol.
- Policy-Based Forwarding (PBF): Overrides routing table decisions based on defined criteria (source, application, service) to forward traffic to a specific next-hop or interface.
-
IPv6 Functionality:
Beyond basic IPv6 addressing, Layer 3 interfaces support:
- Router Advertisements (RAs): The firewall can send RAs to enable SLAAC (Stateless Address Autoconfiguration) for IPv6 clients on the connected segment.
- DHCPv6 Relay: The firewall can relay DHCPv6 messages between clients and DHCPv6 servers on different network segments.
- Neighbor Discovery Protocol (NDP): Essential for IPv6 link operations.
- High Availability (HA): Layer 3 interfaces play a critical role in HA (Active/Passive and Active/Active). Path monitoring can be configured for Layer 3 interfaces to trigger failover if a monitored link goes down. In Active/Passive HA, floating IP addresses are configured on Layer 3 interfaces and move to the active firewall during a failover.
- GlobalProtect Gateway/Portal: Layer 3 interfaces can be configured as GlobalProtect Gateway interfaces, allowing remote users to connect securely to the corporate network. Loopback interfaces are often used for GlobalProtect Portals.
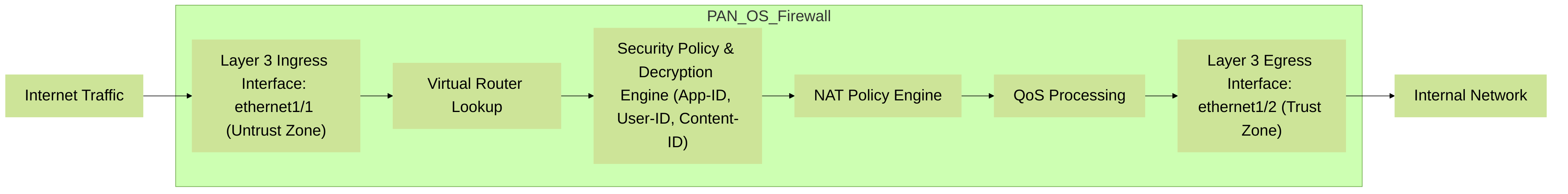
Simplified packet flow through a Palo Alto Networks firewall, highlighting the involvement of Layer 3 interfaces at ingress/egress and the application of various PAN-OS engines.
PAN-OS Layer 3 Interface Configuration Steps
Configuring a Layer 3 interface in PAN-OS (via the WebGUI) involves several key steps:
- Navigate to Network > Interfaces: Select the 'Ethernet' tab (or 'AE Groups', 'Loopback', 'Tunnel' as appropriate). Click on the physical interface name (e.g., `ethernet1/1`) you wish to configure, or click 'Add' to create a new logical interface (like Loopback or Tunnel).
-
Set Interface Type to Layer3:
In the interface configuration window, on the 'Config' tab (default), select `Layer3` from the 'Interface Type' dropdown menu. If configuring a subinterface, click 'Add Subinterface' on a parent Layer 3 physical interface, assign a numeric tag (VLAN ID), and then proceed.
// Example: Viewing interface type in CLI admin@PA-VM> show interface ethernet1/1 ------------------------------------------------------------------------------- Name: ethernet1/1, ID: 6 Operation mode: layer3 Virtual router: default Zone: untrust, Nsx Universal: no ... -
Assign to Virtual Router and Security Zone:
- Config Tab > Virtual Router: Select the appropriate Virtual Router from the dropdown (e.g., `default`). If needed, you can create a new VR from `Network > Virtual Routers` first.
- Config Tab > Security Zone: Select an existing Layer 3 Security Zone from the dropdown or click 'New Zone' to create one. Ensure the new zone is of type 'Layer 3'.
-
Configure IP Address(es):
-
IPv4 Tab:
- Select Type: `Static`, `DHCP Client`, or `PPPoE Client`.
- For `Static`: Click 'Add' and enter the IP address and netmask (e.g., `192.168.1.1/24`). You can add multiple secondary IP addresses if needed.
- For `DHCP Client`: Optionally check 'Automatically create default route pointing to default gateway acquired from server'. You can also set a Client ID.
- For `PPPoE Client`: Enter username, password, and select authentication type.
-
IPv6 Tab:
- Check 'Enable IPv6'.
- Click 'Add' to configure static IPv6 addresses (e.g., `2001:db8:acad:1::1/64`).
- Configure settings for 'Router Advertisement' if the firewall should act as an IPv6 router for clients (e.g., Managed flag, Other Config flag).
- Optionally enable 'DHCPv6 Client'.
-
IPv4 Tab:
-
Apply Interface Management Profile (Optional but Recommended):
Navigate to the 'Advanced' tab. In the 'Other Info' section, select an existing Interface Management Profile from the 'Management Profile' dropdown. This profile must be pre-configured under `Network > Network Profiles > Interface Mgmt`.
Gotcha! (Palo Alto Networks): If you are configuring a new firewall and this is the primary interface for management (other than the MGT port), ensure this profile permits HTTPS/SSH from your management station's IP.
-
Adjust Advanced Settings (as needed):
On the 'Advanced' tab:
- Link Speed / Duplex: Usually 'auto', but can be set manually.
- MTU: Adjust from the default 1500 if necessary.
-
Adjust TCP MSS:
Enable if needed, especially for VPNs.
- IPv4 MSS: Enter a specific MSS value or let PAN-OS calculate.
- IPv6 MSS: Enter a specific MSS value or let PAN-OS calculate.
- LLDP: Select an LLDP Profile if LLDP is required.
- ARP Entries: Add static ARP entries if required.
- NDP Proxy / NDP Configuration (for IPv6): Configure as needed for specific IPv6 scenarios.
- NetFlow Profile: Assign if exporting flow data from this interface.
- Click OK and Commit: Click 'OK' to close the interface configuration window. Then, click 'Commit' in the top-right corner of the WebGUI. Review the changes in the commit preview window and then click 'Commit' again to apply the configuration to the running state of the firewall.
Troubleshooting Layer 3 Interfaces on PAN-OS
Effective troubleshooting is key for maintaining network stability. PAN-OS provides several tools and CLI commands.
Common Issues:
- No Connectivity: Incorrect IP, mask, or gateway. Interface down (cable, SFP, peer device issue). Missing or incorrect security zone assignment. No security policy allowing traffic. Routing issues.
- Intermittent Connectivity: MTU mismatches. Duplex/speed mismatches. Hardware issues. High resource utilization on the firewall.
- Cannot Manage Firewall via Dataplane Interface: Missing or misconfigured Interface Management Profile. Service not enabled (e.g., HTTPS, SSH). Permitted IP list in profile too restrictive. No route to the interface from the management station.
- Routing Protocol Adjacency/Peering Issues: Mismatched parameters (OSPF area, BGP AS). Interface not enabled for the protocol. Network reachability issues between peers.
PAN-OS CLI Commands for Troubleshooting:
// Check interface status, IP, zone, VR admin@PA-FW> show interface ethernet1/1 // Check hardware details and counters for an interface admin@PA-FW> show interface ethernet1/1 hardware // Check ARP table for a specific interface or all admin@PA-FW> show arp ethernet1/1 admin@PA-FW> show arp all // Check MAC address table (useful for L2 troubleshooting leading to L3) admin@PA-FW> show mac all // Check IPv6 neighbor cache admin@PA-FW> show ipv6 neighbors interface ethernet1/1 // Check routing table for a specific VR admin@PA-FW> show routing route virtual-router default // Check forwarding table (FIB) admin@PA-FW> show routing fib virtual-router default // Test reachability from a specific L3 interface source IP admin@PA-FW> ping source <IP_on_L3_interface> host <destination_IP> // Test routing lookup for a destination IP admin@PA-FW> test routing fib-lookup virtual-router default ip <destination_IP> // Show active sessions, can filter by interface, zone, IP admin@PA-FW> show session all filter source <source_IP> destination <dest_IP> admin@PA-FW> show session id <session_ID> // View global counters, can be filtered (e.g., for packet drops on an interface) admin@PA-FW> show counter global filter packet-filter yes delta yes admin@PA-FW> show counter interface ethernet1/1 // (Available on some platforms/versions) // Check traffic logs via CLI (useful in headless scenarios) admin@PA-FW> show log traffic direction equal backward query "(addr.src in 10.1.1.5) and (zone.src eq Trust)"
GUI Troubleshooting Tools:
- Dashboard > ACC (Application Command Center): Provides an overview of traffic, threats, and applications, which can indicate issues related to specific interfaces or zones.
- Monitor > Traffic Log: Essential for checking if traffic is hitting the firewall, what policy it matches (or if it's denied), and details like source/destination zone and interface.
- Monitor > System Log: For interface up/down events, HA events, routing protocol events.
-
Device > Troubleshooting:
- Ping, Traceroute: GUI-based tools for testing connectivity.
- Test Policy Match: Allows you to simulate traffic and see which Security, NAT, QoS, or PBF policy it would match.
- Session Browser: GUI view of active sessions.
- Network > Interfaces > Etherstats/Counters: Some interface statistics are available directly in the interface view.
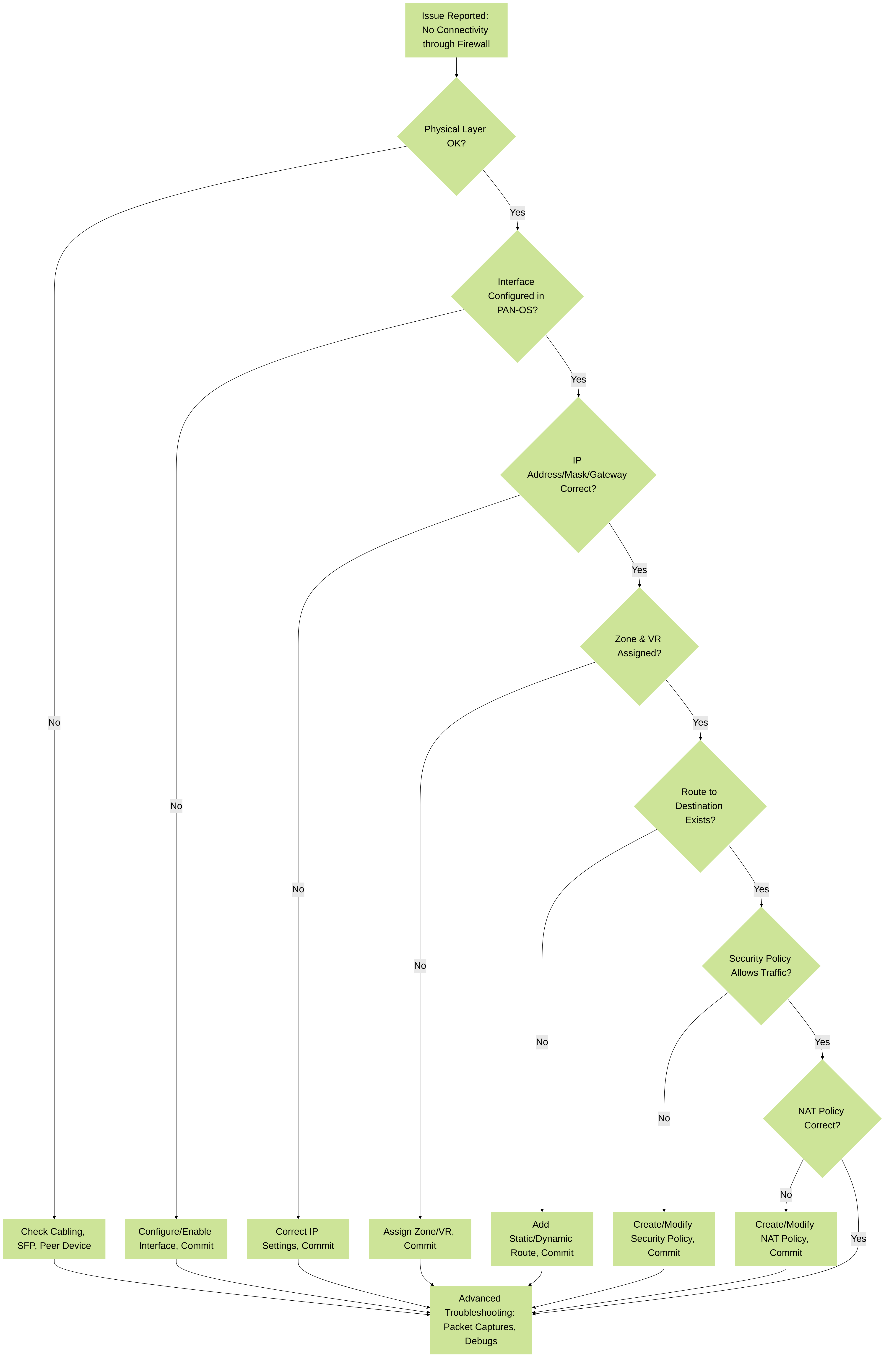
A simplified decision tree for troubleshooting Layer 3 interface connectivity issues on a Palo Alto Networks firewall.
Layer 3 Interfaces in Palo Alto Networks High Availability (HA)
In a Palo Alto Networks HA cluster (Active/Passive or Active/Active), Layer 3 interfaces play a crucial role in maintaining connectivity during failovers.
-
Active/Passive HA:
- Floating IP Addresses: Configured on Layer 3 interfaces (and loopback/tunnel interfaces) that need to provide continuous service. The floating IP address is active only on the currently active firewall. Upon failover, the newly active firewall takes ownership of the floating IP(s) and sends Gratuitous ARP (GARP) packets to update MAC address tables on connected switches.
- Path Monitoring: Layer 3 interfaces can be monitored. If a monitored interface fails on the active firewall, it can trigger an HA failover to the passive firewall (if the passive firewall's corresponding link is healthy). This ensures traffic is routed through a firewall with working paths.
-
Active/Active HA:
- More complex, often involving distinct IP addresses per firewall for directly connected networks, or shared virtual IP addresses using different mechanisms.
- Session ownership and synchronization are key. Layer 3 interfaces handle traffic for sessions owned by their respective firewalls.
- Path monitoring is also critical.
Conclusion
Layer 3 interfaces are indispensable components of any Palo Alto Networks firewall deployment. Their proper configuration is paramount for routing, security policy enforcement, NAT, VPNs, and many other advanced features. For the PCNSE exam, a thorough grasp of their setup, the types available (physical, subinterface, loopback, tunnel, aggregate), associated features, troubleshooting techniques, and HA considerations within the PAN-OS ecosystem is non-negotiable.