Palo Alto Networks Loopback Interfaces: A Comprehensive Guide for PCNSE
Introduction to Loopback Interfaces in PAN-OS
In Palo Alto Networks firewalls running PAN-OS, a Loopback Interface is a logical, software-based interface. Unlike physical interfaces (e.g., Ethernet), loopback interfaces are not tied to any specific hardware port. Their primary characteristic is that they are always considered "up" as long as the firewall itself is operational and the interface is administratively enabled. This inherent stability makes them exceptionally valuable for various functions within the Palo Alto Networks security platform.
Loopback interfaces are assigned IP addresses (both IPv4 and IPv6 are supported) and behave like any other Layer 3 interface in terms of routing and policy enforcement. They must be assigned to a Virtual Router and a Security Zone, allowing them to participate in routing decisions and be subject to Security Policy rules.
Core Characteristics and Benefits
- Always Up: A loopback interface remains operational as long as the firewall is running, regardless of the state of any physical interfaces. This provides a stable IP address for critical services.
- Logical Nature: Being software-defined, they are not dependent on physical cabling or hardware link status.
-
IP Addressability: They are assigned static IPv4 and/or IPv6 addresses. For IPv4, a
/32subnet mask is used, and for IPv6, a/128subnet mask is used, signifying a host address. - Routing Participation: They can be included in routing processes (static and dynamic) and their networks can be advertised.
- Zone Membership: Like other interfaces, they must belong to a Security Zone, allowing for granular policy control over traffic to or from the loopback IP.
- Management & Service Stability: Provides a consistent source or destination IP for management access, firewall-initiated services (like DNS, NTP, updates), and VPN termination points.
/32 (for IPv4) or /128 (for IPv6) subnet mask. This indicates that the IP address is a specific host endpoint on the firewall.
PAN-OS Configuration of Loopback Interfaces
Configuring a loopback interface in PAN-OS is straightforward and can be done via the web interface (GUI) or the Command Line Interface (CLI).
GUI Configuration Steps:
- Navigate to Network > Interfaces > Loopback.
- Click Add at the bottom of the page.
-
In the Loopback Interface dialog box:
- Interface Name: The suffix number is automatically assigned (e.g., loopback.1, loopback.2). You can add a descriptive comment.
- Comment: (Optional but recommended) Describe the purpose of the loopback (e.g., "Management Loopback", "BGP Peering IP").
-
Config Tab:
- Virtual Router: Select the Virtual Router this loopback interface will belong to (e.g., 'default'). This is essential for routing.
- Security Zone: Select an existing Security Zone or create a new one (e.g., 'MGMT_Zone', 'Loopback_Zone'). This controls policy application.
-
IPv4 Tab:
- Click Add.
-
Enter the IPv4 address followed by
/32(e.g.,192.168.254.1/32). Multiple IPv4 addresses can be added to a single loopback interface if needed.
-
IPv6 Tab: (Optional)
- Check Enable IPv6 Interface.
-
Click Add and enter the IPv6 address followed by
/128(e.g.,2001:db8:0:254::1/128).
-
Advanced Tab:
- Management Profile: If this loopback interface will be used for management access (HTTPS, SSH, SNMP, Ping) or certain services (User-ID, NetFlow), select or create an Interface Management Profile that permits these services.
- MTU: Typically left at the default (1500).
- Click OK.
- Commit the changes to the firewall.
CLI Configuration Example:
Here's how to configure a loopback interface (loopback.10) with an IPv4 address, assign it to a virtual router and zone, and apply a management profile using the PAN-OS CLI:
configure set network interface loopback units loopback.10 set network interface loopback units loopback.10 comment "Primary Management Loopback" set network interface loopback units loopback.10 ip 10.255.0.1/32 set network interface loopback units loopback.10 interface-management-profile Allow_Management_Services set network virtual-router VR-Main interface loopback.10 set zone Untrust-L3 network layer3 loopback.10 commit
/32 for IPv4 or /128 for IPv6.
Key Use Cases for Loopback Interfaces in Palo Alto Networks
Loopback interfaces are versatile and serve several critical functions in a Palo Alto Networks environment.
1. Stable Management Access
Using a loopback interface IP address for managing the firewall (HTTPS, SSH, Panorama connectivity) provides a stable endpoint. If a physical management interface goes down, but other routed paths to the loopback IP exist, management access remains possible.
- An Interface Management Profile must be applied to the loopback interface, permitting services like HTTPS, SSH, SNMP, and Ping.
- Security policies must allow traffic from the management source to the loopback IP in its designated zone.
_used_for_stable_manag_May_19_2025_04-15PM.png)
Diagram 1: Loopback interface (10.255.0.1) used for stable management access to a Palo Alto Networks firewall, reachable via multiple physical paths.
2. Dynamic Routing Protocol Stability
Loopback interfaces play a vital role in ensuring stability and predictability in dynamic routing protocols like BGP and OSPF.
OSPF (Open Shortest Path First)
- Router ID: The highest loopback IP address is often automatically chosen as the OSPF Router ID if not manually configured. A stable Router ID is crucial for OSPF operations. Using a loopback ensures the Router ID doesn't change if a physical interface IP changes or goes down.
- Stub Network Advertisement: Loopback interface networks (as /32 host routes) can be advertised into OSPF, providing reachable endpoints for various services.
- Redistribution: The loopback IP itself, as a connected route, needs to be redistributed into OSPF if it's to be learned by other OSPF routers. This is done under Network > Virtual Routers > [Your VR] > OSPF > Export Rules.
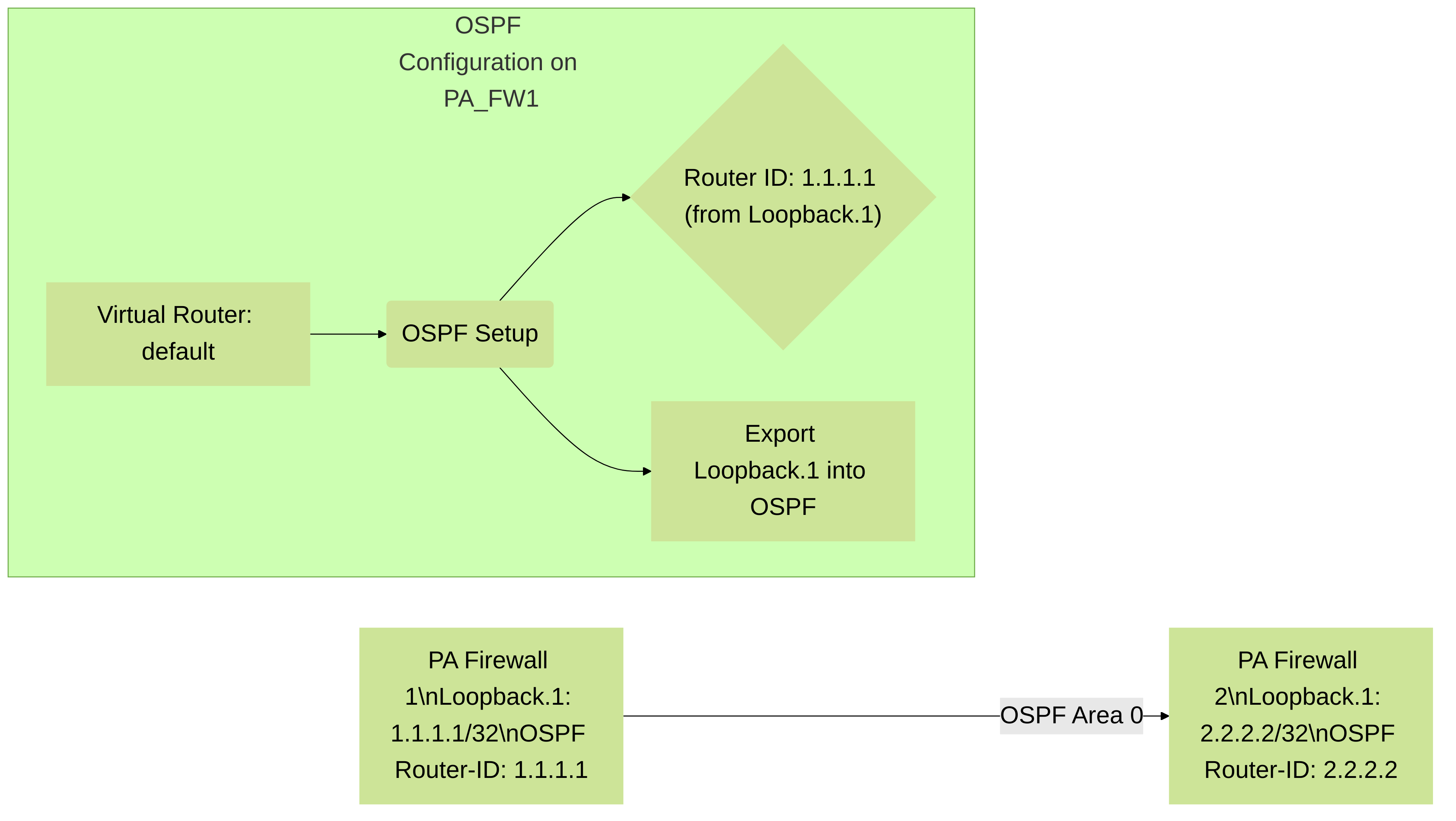
Diagram 2: Palo Alto Networks firewalls using loopback interface IPs as stable OSPF Router IDs and advertising these loopbacks into the OSPF domain.
BGP (Border Gateway Protocol)
-
Update Source: For eBGP and iBGP peerings, a loopback interface is commonly used as the
update-source. This ensures that BGP peering remains up as long as there is any route to the peer's loopback IP, even if the direct physical link between peers fails and an alternate path exists.set network virtual-router <VR_NAME> protocol bgp peer-group <PEER_GROUP_NAME> peer <PEER_NAME> local-interface loopback.X set network virtual-router <VR_NAME> protocol bgp peer-group <PEER_GROUP_NAME> peer <PEER_NAME> local-interface-ip <LOOPBACK_IP>
- Router ID: Similar to OSPF, BGP uses a Router ID, and a loopback IP provides a stable and predictable choice.
- Next-Hop-Self (iBGP): While not directly loopback, understanding how loopbacks interact with iBGP (e.g., ensuring loopbacks are reachable for next-hop resolution) is important.
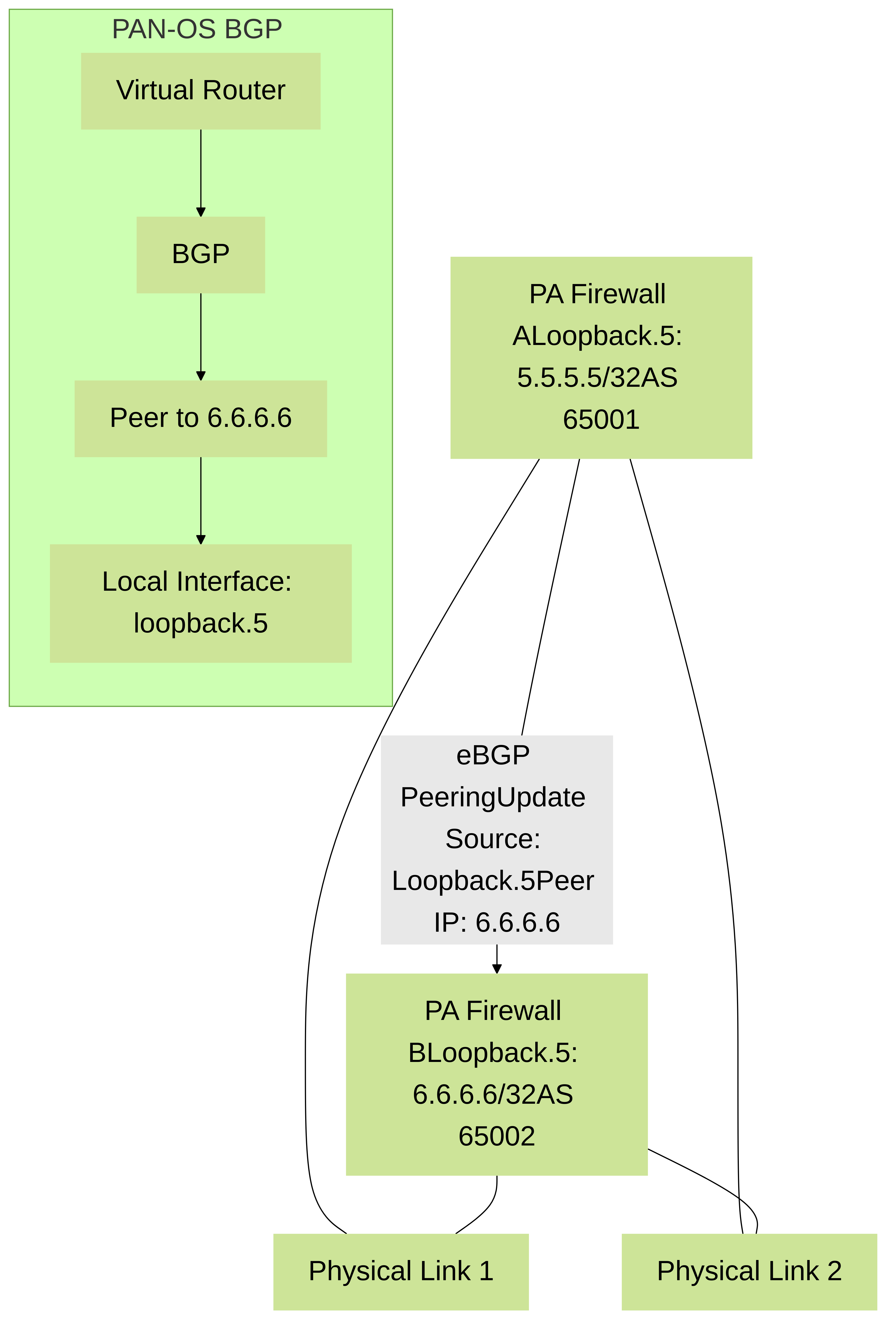
Diagram 3: Palo Alto Networks firewalls using loopback interfaces as the update source for eBGP peering, enhancing resiliency across multiple physical paths.
3. VPN Termination
Loopback interfaces offer a stable IP address for terminating VPN tunnels, such as IPSec and GlobalProtect.
IPSec Tunnels
- IKE Gateway Local IP Address: A loopback IP can be configured as the local IP address for an IKE Gateway. This is beneficial if the firewall has multiple ISP connections or if physical interface IPs might change. The remote VPN peer always points to this stable loopback IP.
- Requires appropriate routing for the loopback IP to be reachable from the internet (or relevant network) and security policies to allow IKE (UDP 500/4500) and ESP (protocol 50) traffic.
GlobalProtect
- Portal Address: A loopback interface IP can be used as the address for the GlobalProtect Portal. Users' GlobalProtect clients connect to this stable IP.
- Gateway Address: Similarly, GlobalProtect Gateways can be configured to use a loopback interface IP. This provides a consistent connection point for VPN clients.
- Benefits include easier DNS configuration (a single A record for the portal/gateway) and independence from physical interface IP addresses.
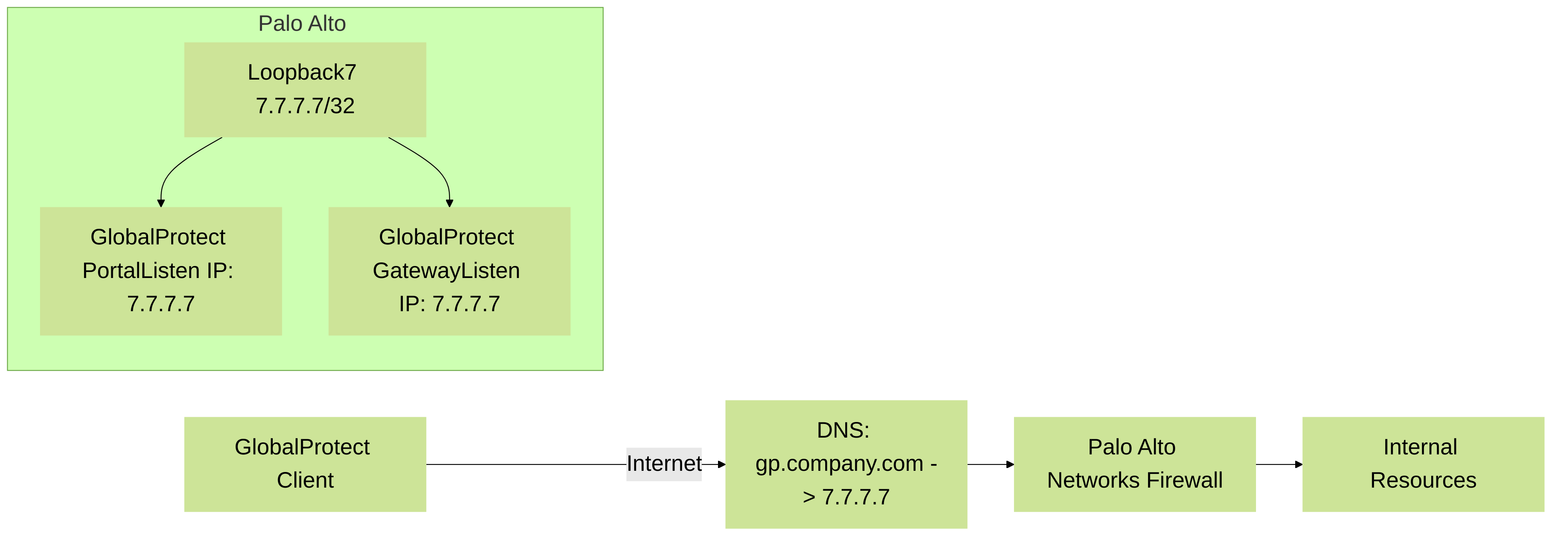
Diagram 4: GlobalProtect Portal and Gateway on a Palo Alto Networks firewall using a loopback interface IP (7.7.7.7) for stable client connectivity.
4. Source for Firewall-Initiated Services (Service Routes)
Palo Alto Networks firewalls can be configured to use a specific source IP address for services initiated by the firewall itself. This is configured under Device > Setup > Services > Service Route Configuration.
Using a loopback interface IP as the source for these services ensures consistent communication, even if the default management interface IP changes or the interface goes down (assuming the loopback is reachable via other routes).
Services that can leverage a loopback IP as a source via Service Routes include:
- DNS queries
- NTP server communication
- Palo Alto Networks Updates (Applications & Threats, Antivirus, WildFire, etc.)
- Syslog
- SNMP Traps
- Panorama communication
- User-ID Agent communication
- External Dynamic List (EDL) fetching
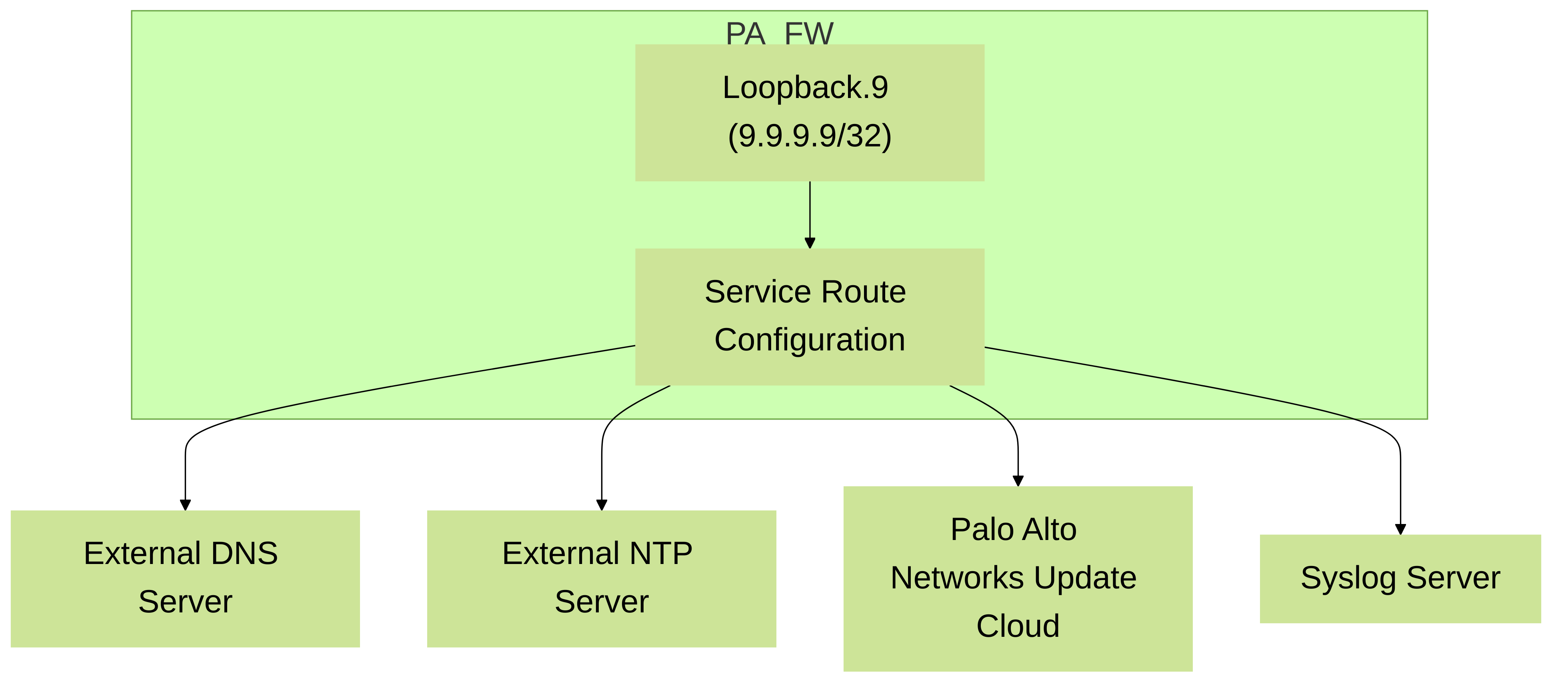
Diagram 5: Palo Alto Networks firewall using a loopback interface IP (9.9.9.9) as the source for various firewall-initiated services via Service Route Configuration.
5. Other Niche Use Cases
-
Source IP for Traffic Generation: When initiating pings or traceroutes from the firewall CLI, you can specify a loopback IP as the source.
ping source <loopback_ip_address> host <destination_ip_address>
- High Availability (HA): While HA has dedicated HA links, management reachability to individual firewalls in an HA pair or to a virtual IP representing the cluster can sometimes involve loopback IPs, especially if routing is complex. However, primary HA functions (sync, heartbeats) use dedicated HA interfaces.
- NAT Policy: While less common, a loopback IP could technically be used as an address in a NAT pool if it's routed appropriately within the network. Typically, dedicated IP ranges on physical interfaces are used for NAT.
Troubleshooting Loopback Interfaces
Since loopback interfaces are always "up," troubleshooting typically revolves around IP reachability and service configuration.
-
IP Reachability:
- Verify the loopback IP is correctly configured with a /32 (IPv4) or /128 (IPv6) mask.
- Ensure the loopback interface is assigned to the correct Virtual Router.
- Check routing tables on the firewall and intermediary devices to ensure paths to the loopback IP exist.
show routing route interface loopback.<id>
- If advertised via dynamic routing, ensure redistribution or network statements are correct in BGP/OSPF.
show routing protocol bgp rib-out show routing protocol ospf lsdb
-
Security Policy:
- Confirm the loopback interface is in the intended Security Zone.
- Verify Security Policy rules allow the required traffic to/from the loopback IP and its zone (e.g., for management access, VPNs). Check traffic logs for denials.
-
Interface Management Profile:
- If used for management or specific services (User-ID, etc.), ensure an appropriate Interface Management Profile is applied to the loopback and permits the necessary services (HTTPS, SSH, Ping, SNMP, Response Pages, User-ID service).
-
Service Route Configuration:
- If a service (DNS, NTP, Updates) is not working as expected and is configured to use a loopback as a source, verify the Service Route Configuration (Device > Setup > Services) is correct and that the loopback IP has reachability to the service destination.
-
Application Override/Security Policy for VPNs:
- For GlobalProtect or IPSec, ensure applications like `ssl`, `ike`, `ipsec-esp`, `panos-globalprotect` are allowed by security policies targeting the zone where the loopback resides.