Palo Alto Networks User-ID Redistribution: A Comprehensive Guide for PCNSE
Introduction to User-ID Redistribution in the Palo Alto Networks Ecosystem
User-ID™ technology is a cornerstone of Palo Alto Networks' Next-Generation Firewalls (NGFWs), enabling policies based on user and group identities rather than just IP addresses. In distributed network environments, ensuring that all firewalls have consistent and up-to-date user-to-IP address mappings is critical for uniform security policy enforcement and visibility. User-ID redistribution is the Palo Alto Networks mechanism designed to achieve this by allowing User-ID information, along with other identity-related data, to be shared efficiently across multiple PAN-OS devices (firewalls and Panorama) and User-ID agents.
Without redistribution, each firewall would need to independently learn all user mappings, leading to redundant configurations, increased load on authentication sources (like Active Directory domain controllers), and potential inconsistencies. Redistribution centralizes or distributes the collection of User-ID information and then disseminates it to other firewalls that require it for policy enforcement.
Core Concepts and Terminology in Palo Alto Networks User-ID Redistribution
-
User-ID Agent:
This term can refer to several components within the Palo Alto Networks User-ID architecture:
- Windows-based User-ID Agent: Software installed on a Windows server that collects user mapping information from sources like Active Directory domain controller security logs, Exchange Server logs, or Syslog messages, and can also act as a redistribution point.
- PAN-OS Integrated User-ID Agent: Functionality built into PAN-OS devices (firewalls) that allows them to collect user mappings directly (e.g., via port probing, GlobalProtect, Captive Portal, XML API) or receive them from other User-ID agents. A PAN-OS device can act as both a collector and a redistributor.
- Panorama User-ID Agent: Panorama can act as a centralized hub for collecting and redistributing User-ID information from multiple sources to managed firewalls.
- Redistribution Point/Collector: A PAN-OS device (firewall or Panorama) or a Windows-based User-ID agent configured to collect user mapping information from various sources and then make this information available to other devices. This is often referred to as the "server" or "distributor" in a redistribution topology. In PAN-OS, this can be configured under `Device > Data Redistribution > Collector Settings` or `Device > User Identification > User Mapping > Server Monitoring` (for configuring redistribution from other User-ID agents) and `Device > User Identification > Palo Alto Networks User-ID Agent Setup > Redistribution` (for configuring the firewall itself to redistribute its learned mappings).
- Redistribution Client/Subscriber: A PAN-OS firewall configured to receive user mapping information from a redistribution point (collector). This is often referred to as the "client" in a redistribution topology. In PAN-OS, this is configured under `Device > User Identification > User-ID Agents` (when connecting to a Windows agent or another firewall acting as an agent) or `Device > Data Redistribution > Agents` (for the more generic data redistribution framework).
- User Mapping: The association of an IP address with a username. This is the primary piece of information shared via User-ID redistribution.
- Group Mapping: The association of usernames with directory service groups (e.g., Active Directory groups). While group mapping information itself is typically learned by each firewall directly from LDAP servers or Panorama, the redistributed User-ID (IP-to-username) allows the firewall to then apply group-based policies.
- Authentication Timestamps: Timestamps associated with user mappings that indicate when the mapping was last validated. These are also redistributed to ensure mapping freshness.
Supported Data Types for Redistribution
Palo Alto Networks User-ID redistribution is not limited to just IP-to-username mappings. The "Data Redistribution" framework in PAN-OS supports sharing various types of security-related information:
- IP address-to-username mappings (User-ID): This is the fundamental data type for user-based policy enforcement. It allows firewalls to know which user is associated with which IP address. Palo Alto Networks Use Case: Enforcing security policies that allow or deny access to specific applications or URLs based on the user's identity or group membership, regardless of their IP address.
- IP address-to-tag mappings (Dynamic Address Groups - DAGs): Firewalls can tag IP addresses based on various criteria (e.g., learned through User-ID, logs, VM Information Sources, or API calls). These IP-to-tag mappings can be redistributed, allowing other firewalls to use these tags in Dynamic Address Groups for policy enforcement. Palo Alto Networks Use Case: Dynamically including IP addresses of, for example, compromised hosts (tagged as "compromised") into a DAG that is then blocked by security policies across multiple firewalls.
- Username-to-tag mappings (Dynamic User Groups - DUGs): Similar to IP-to-tag, but for usernames. A user can be tagged (e.g., "high-risk-user") and this mapping can be redistributed. Firewalls can then use these tags in Dynamic User Groups. Palo Alto Networks Use Case: Applying stricter security profiles to users tagged as "contractor" or "guest" across the network.
- Host Information Profile (HIP) data from GlobalProtect: When GlobalProtect clients connect, they submit HIP reports detailing their security posture (e.g., OS patch level, antivirus status, disk encryption). This HIP data can be redistributed, allowing consistent policy enforcement based on endpoint compliance across different firewalls. Palo Alto Networks Use Case: Ensuring that only endpoints meeting corporate compliance standards (as verified by HIP checks) can access sensitive internal resources, enforced consistently even if users roam between sites protected by different firewalls.
- Device Quarantine Information: Information about devices that have been quarantined (e.g., due to malware detection or HIP policy violation) can be redistributed. This allows other firewalls to enforce quarantine policies consistently. Palo Alto Networks Use Case: Automatically blocking a quarantined device's access network-wide, preventing lateral movement of threats.
- Authentication Timestamps: Used to determine the age of a user mapping and when it should expire or be re-verified.
Palo Alto Networks User-ID Redistribution Architectures
Choosing the right redistribution architecture is crucial for scalability, performance, and manageability. Palo Alto Networks supports several models:
1. Hub-and-Spoke Model
In this model, one or more central PAN-OS devices (firewalls or Panorama) or Windows-based User-ID agents act as "hubs" (collectors/redistribution points). These hubs gather User-ID information from various sources (e.g., domain controllers, Syslog, GlobalProtect Gateways) and then redistribute it to multiple "spoke" firewalls (clients/subscribers).
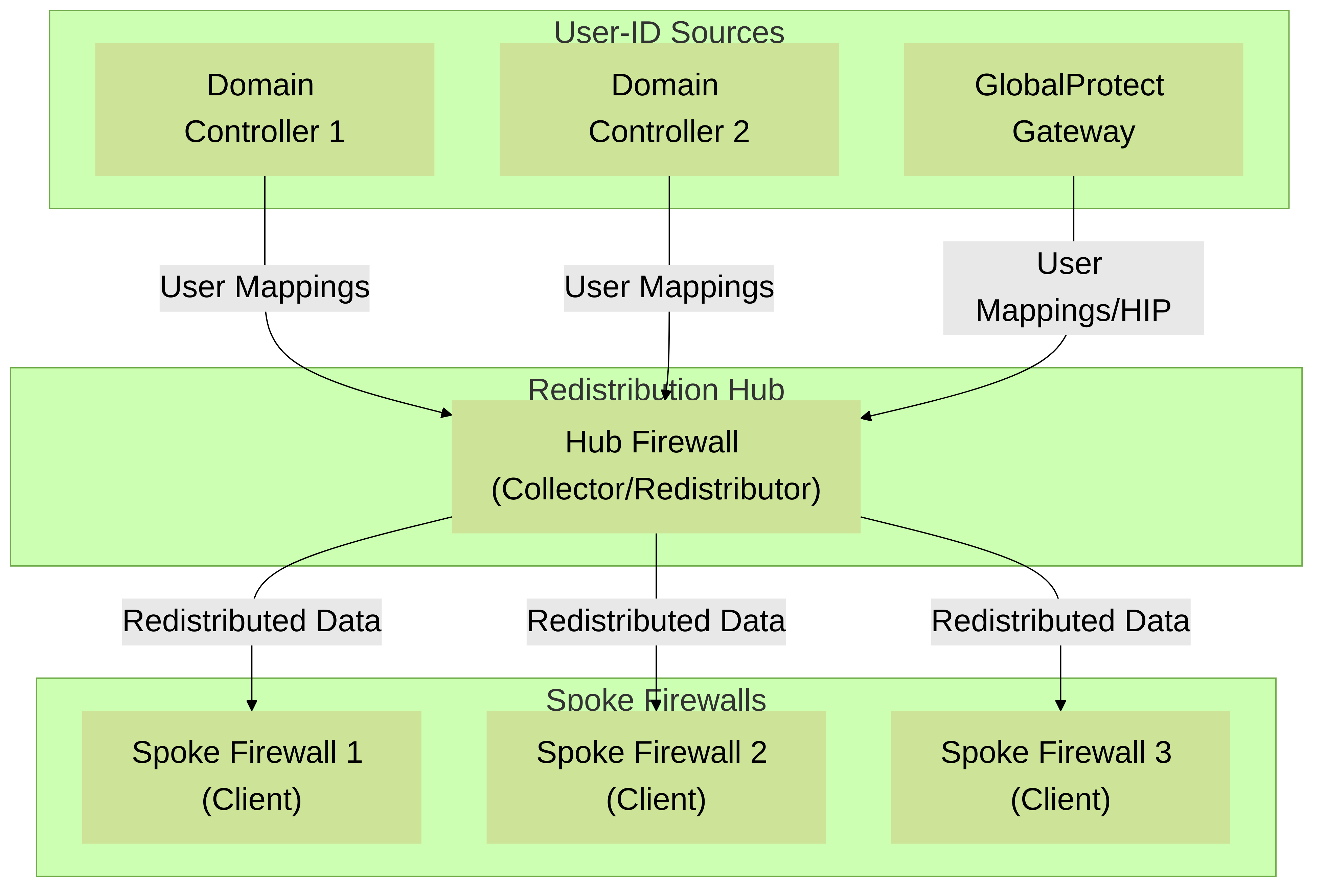
Palo Alto Networks Hub-and-Spoke User-ID Redistribution: A central Hub Firewall collects User-ID and HIP data from various sources and redistributes it to Spoke Firewalls.
Advantages:
- Centralized management of User-ID collection.
- Reduced load on authentication sources as only hubs interact with them directly for primary collection.
- Simpler to configure and troubleshoot for smaller to medium deployments.
Considerations:
- The hub can become a single point of failure if not redundant.
- Latency for spokes depends on their connection to the hub.
- Panorama is often used as the hub in larger deployments for scalability and centralized management.
2. Multi-Hub (Regional Hubs) Model
For larger, geographically dispersed organizations, a multi-hub model can be implemented. Regional hubs (PAN-OS firewalls, Panorama, or Windows User-ID agents) collect User-ID information for their respective regions. These regional hubs can then redistribute information to local spoke firewalls. Optionally, regional hubs can also redistribute information among themselves, creating a more resilient and scalable architecture.
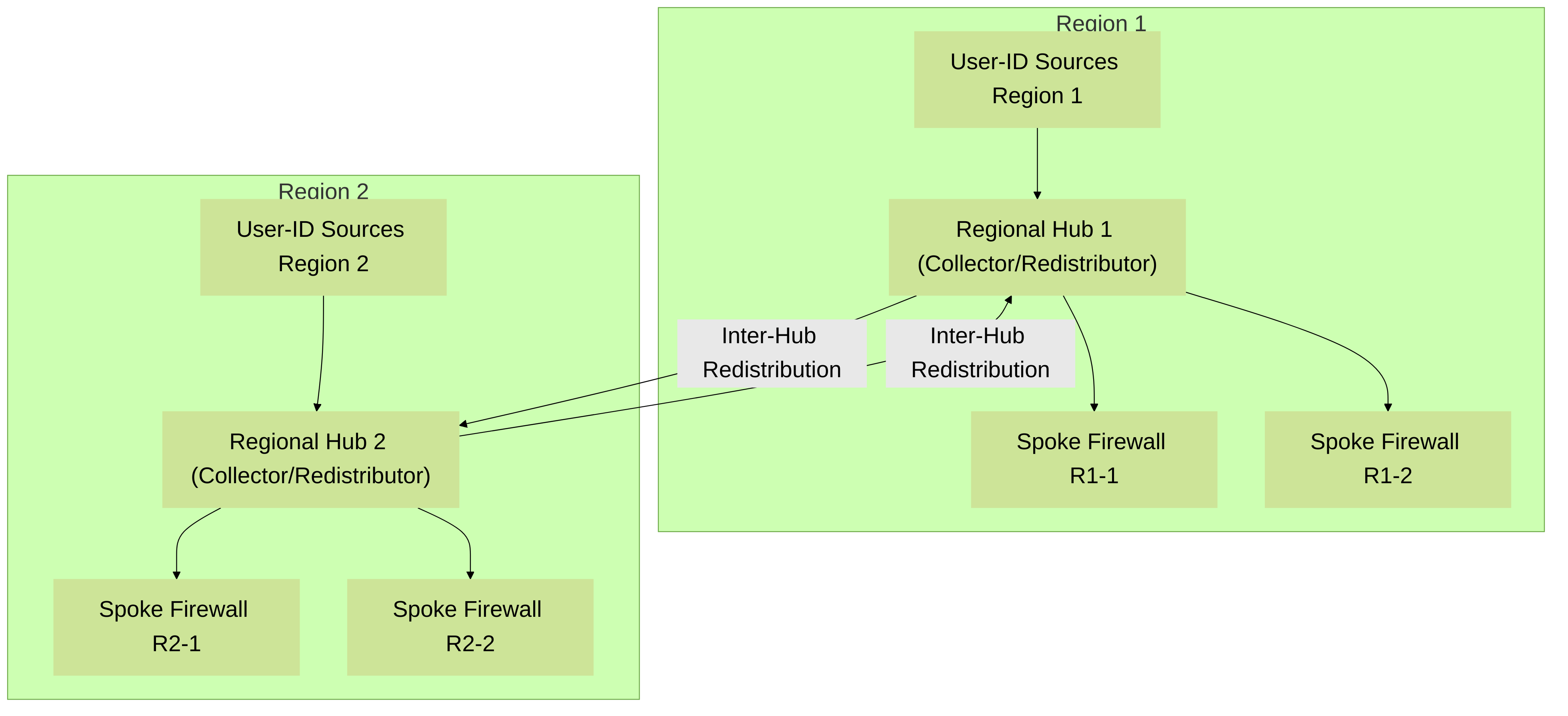
Palo Alto Networks Multi-Hub User-ID Redistribution: Regional Hubs collect local User-ID data and redistribute to local spokes. Hubs can also exchange information for broader visibility.
Advantages:
- Improved scalability and fault tolerance.
- Reduced latency as spokes connect to regional hubs.
- Better distribution of User-ID collection load.
Considerations:
- More complex to design and manage.
- Careful planning is needed to avoid redistribution loops and excessive data transfer between hubs.
- Panorama can play a key role in managing inter-hub redistribution configurations.
3. Hierarchical Model
In a hierarchical model, User-ID information flows upwards through layers of firewalls. For example, branch firewalls might collect local User-ID information and redistribute it to a regional firewall. The regional firewall aggregates this information and may redistribute it further up to a central/data center firewall or Panorama.
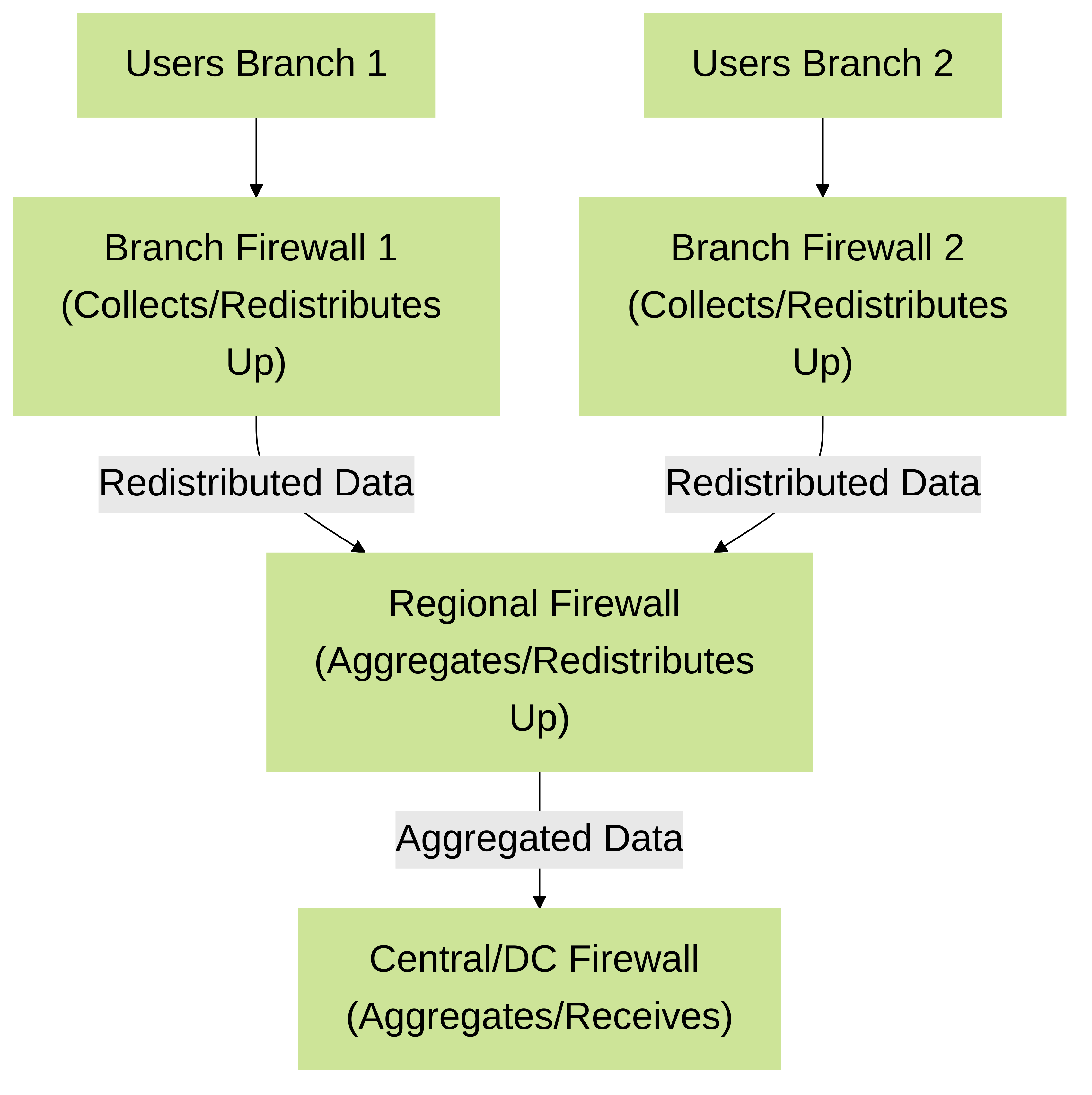
Palo Alto Networks Hierarchical User-ID Redistribution: Branch firewalls send User-ID data to regional firewalls, which then aggregate and send to a central firewall or Panorama.
Advantages:
- Scalable for organizations with many layers of network infrastructure.
- Allows for localized collection and progressive aggregation of User-ID data.
Considerations:
- Potential for increased latency as data traverses multiple hops. PAN-OS has a maximum hop limit for User-ID redistribution (typically 10 hops for user mappings).
- Complexity in managing redistribution paths.
4. Panorama as a Central User-ID Hub
Panorama can act as a dedicated, centralized User-ID hub, collecting mappings from various sources including Windows User-ID agents, PAN-OS integrated agents on firewalls, and directly from Syslog sources. Panorama then redistributes these mappings to its managed firewalls. This is a highly recommended approach for large-scale deployments.
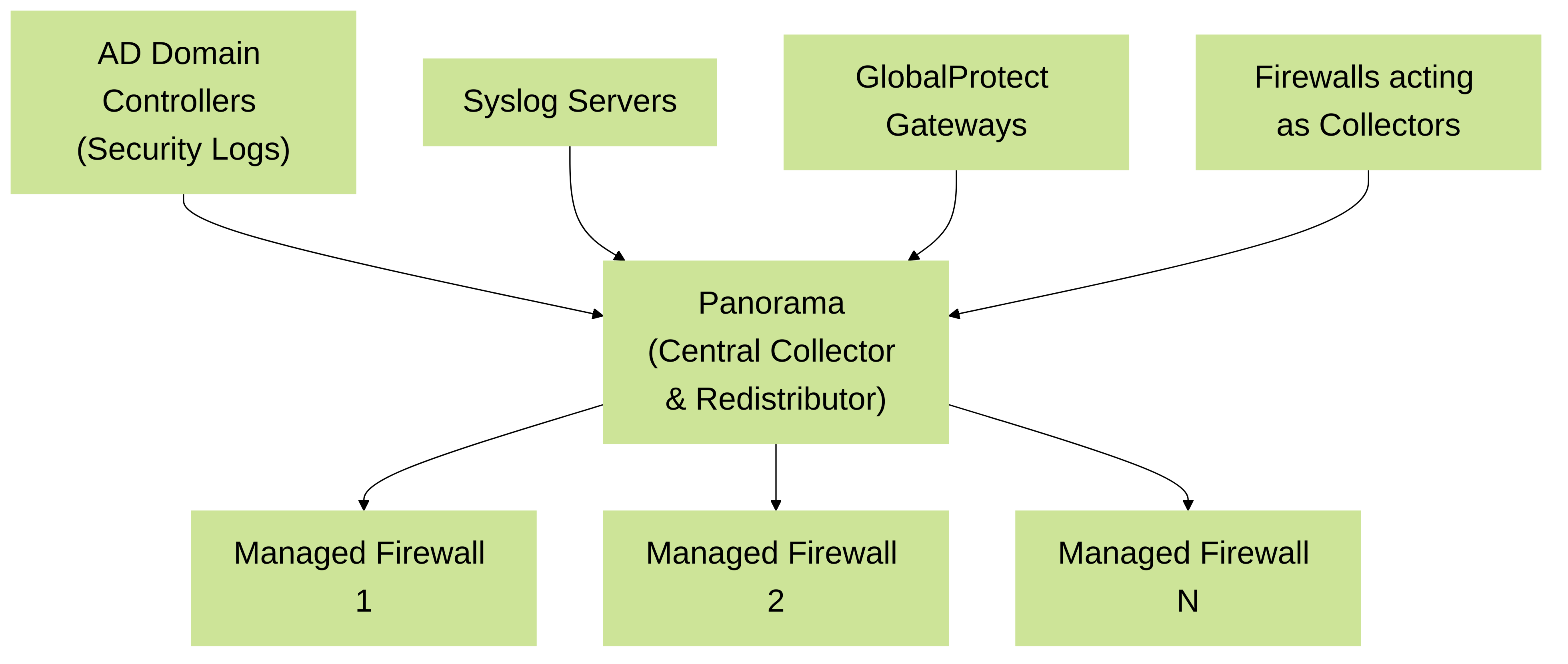
Palo Alto Networks Panorama as a Central User-ID Hub: Panorama collects User-ID information from diverse sources and redistributes it to all managed firewalls, simplifying large-scale User-ID deployments.
Advantages using Panorama:
- Scalability: Panorama is designed to handle a large number of user mappings and redistribute them efficiently to many firewalls.
- Centralized Management: All User-ID source configurations and redistribution policies can be managed from a single Panorama interface.
- Reduced Firewall Load: Offloads the User-ID collection and initial processing tasks from individual firewalls.
- Consistent Data: Ensures all managed firewalls receive the same, consistent set of user mappings.
- Log Collection Point: Panorama also serves as a central log collector, providing a holistic view of user activity across the network.
5. User-ID Redistribution with Prisma Access
Prisma Access, Palo Alto Networks' SASE solution, also relies on User-ID for policy enforcement for remote users and branch offices. User-ID information can be redistributed between on-premises Palo Alto Networks firewalls/Panorama and Prisma Access. This ensures consistent policy application regardless of where the user is connecting from.
- On-prem to Prisma Access: On-premises User-ID agents (Windows-based, PAN-OS integrated, or Panorama) can redistribute learned user mappings to Prisma Access. This is useful for users who might authenticate on-prem but then access resources through Prisma Access.
- Prisma Access to On-prem: Prisma Access can redistribute User-ID information (e.g., from mobile users authenticating via GlobalProtect to Prisma Access) back to on-premises firewalls or Panorama.
This is typically configured using Panorama to manage the redistribution settings for Prisma Access and the on-premises environment.
Configuring User-ID Redistribution in PAN-OS
The configuration involves setting up the "Collector" (the device sending User-ID information) and the "Agent" or "Client" (the device receiving the information). The newer "Data Redistribution" framework is generally preferred for its broader capabilities, but traditional User-ID agent redistribution is also common.
1. Configuring the Redistribution Collector (Source Device)
This device collects User-ID information and redistributes it. This can be a PAN-OS firewall, Panorama, or a Windows-based User-ID agent.
On a PAN-OS Firewall acting as a Collector:-
Navigate to
Device > User Identification. In thePalo Alto Networks User-ID Agent Setupsection, click the gear icon forRedistribution. -
Alternatively, for the broader Data Redistribution framework, navigate to
Device > Data Redistribution > Collector Settings. - Enable Redistribution: Check the box to enable the firewall to act as a redistribution collector.
- Collector Name: Define a unique name for this collector. This name will be used by clients to connect.
- Pre-Shared Key: Configure a strong pre-shared key for secure communication between the collector and its clients. This key must match on the client-side.
-
Network Settings:
- Specify the Listening IP Address/Interface on which the collector will listen for connections from clients. This is typically a management interface or a dedicated interface for User-ID traffic.
- The default Port for User-ID redistribution is TCP/5007. Ensure this port is allowed through any intermediate firewalls.
- Data to Redistribute: Select the types of data you want to redistribute (e.g., IP-User Mappings, IP-Tag Mappings, User-Tag Mappings, HIP reports).
-
Include/Exclude Networks:
Specify which network ranges' User-ID information should be included or excluded from redistribution. This helps optimize bandwidth and ensures only relevant information is shared.
Example: Include 192.168.1.0/24, Exclude 10.0.0.0/8 - Commit the changes.
- Open the Palo Alto Networks User-ID Agent configuration utility.
-
Go to the
Redistributiontab. - Check "Enable Redistribution".
- Define a "Collector Name" and "Pre-Shared Key".
- Specify the "Listening IP" and "Port" (default TCP/5007).
- Configure "Include/Exclude Networks".
- Save the configuration.
2. Configuring the Redistribution Client (Receiving Device)
This PAN-OS firewall receives User-ID information from a collector.
-
Navigate to
Device > User Identification. In theUser-ID Agentstab, clickAdd. (This path is typically used when connecting to a Windows User-ID Agent or another PAN-OS firewall configured for User-ID agent redistribution). -
Alternatively, for the broader Data Redistribution framework, navigate to
Device > Data Redistribution > Agentsand clickAdd. - Name: Give a name to this agent configuration entry.
- Host/IP Address: Enter the IP address of the redistribution collector.
- Port: Enter the port number the collector is listening on (default TCP/5007).
- Collector Name: Enter the exact Collector Name configured on the redistribution collector.
- Pre-Shared Key: Enter the exact Pre-Shared Key configured on the redistribution collector.
- Enable: Ensure the agent configuration is enabled.
- Data to Receive: Select the types of data you expect to receive.
- Commit the changes.
3. Service Route Configuration
For User-ID redistribution traffic to be correctly sourced from the firewall and routed, especially if the redistribution collector/client communication uses a data plane interface instead of the management interface, a service route might be necessary.
-
Navigate to
Device > Setup > Services > Service Route Configuration. - Customize the service route for "User-ID" (or "Palo Alto Networks Services" more broadly).
- Select the source interface that the firewall should use for initiating or receiving User-ID redistribution connections.
4. Security Policy and Interface Management Profile
- Security Policies: Ensure that security policies on the collector, client, and any intermediate firewalls permit traffic on the User-ID redistribution port (default TCP/5007) between the involved IP addresses. The application `paloalto-userid-agent` can be used in policies.
-
Interface Management Profile:
If User-ID redistribution traffic is expected on a data plane interface, ensure that an Interface Management Profile permitting "User-ID Service" (or "Response Pages" if also using Captive Portal on that interface) is assigned to that interface. This allows the interface to respond to User-ID related communications. (Path:
Network > Network Profiles > Interface Mgmt).
5. Verifying Redistribution
On the PAN-OS CLI:
-
On the client firewall:
show user user-id-agent state all show user ip-user-mapping all type UIA // Shows mappings learned via User-ID Agent show user ip-tag-mapping all // Shows IP-to-tag mappings show user user-tag-mapping all // Shows user-to-tag mappings show high-availability data-forwarding statistics // If HA Data Link is used for redistribution sync -
On the collector firewall:
show user user-id-agent statistics // Shows connected clients and mapping counts show data-redistribution collector statistics // For Data Redistribution framework -
Packet captures (
tcpdumpor via GUIMonitor > Packet Capture) can be used to verify traffic flow on port 5007. -
System logs (
Monitor > Logs > System) will show events related to User-ID agent connections and disconnections. Filter for `( subtype eq user-id )`.
Best Practices for Palo Alto Networks User-ID Redistribution
- Use Panorama or Dedicated Hubs: In large environments, leverage Panorama or dedicated VM-Series firewalls as central redistribution hubs. This centralizes control and reduces the load on individual firewalls.
- Limit Hops: Adhere to the maximum of 10 redistribution hops for user mappings to prevent stale or missing information. Design flatter redistribution hierarchies where possible.
-
Redundancy:
Implement redundancy for redistribution hubs. This can be achieved by:
- Configuring multiple User-ID agents (collectors) on clients.
- Using HA (High Availability) pairs for hub firewalls.
- Leveraging Panorama's inherent redundancy if deployed in an HA configuration.
- Secure Communication: Always use a strong, unique Pre-Shared Key for each collector-client relationship.
- Optimize with Include/Exclude Lists: Use Include/Exclude network lists on collectors to ensure only relevant User-ID information is redistributed. This reduces bandwidth consumption and processing load on clients. For instance, don't redistribute mappings for server subnets if users don't typically originate from there.
- Monitor Regularly: Continuously monitor the status of redistribution links and mapping counts. Use Panorama dashboards, ACC, and CLI commands. Set up log forwarding for critical User-ID events.
- Consistent PAN-OS Versions: While not always strictly necessary for basic redistribution, keeping PAN-OS versions reasonably consistent across redistributing devices can prevent unexpected issues with newer features or data types.
- Dedicated Management/Service Interface: If possible, use a dedicated network interface or subnet for User-ID redistribution traffic, especially in high-volume environments. Configure appropriate service routes.
- Understand Data Flow: Clearly map out how User-ID data will flow through your network. Document your redistribution architecture.
- Time Synchronization: Ensure all devices participating in User-ID (sources, collectors, clients) are synchronized to a reliable NTP (Network Time Protocol) server. Timestamps are critical for mapping validity and expiration.
Advanced Considerations and Troubleshooting
Interaction with High Availability (HA)
In an HA pair, User-ID mappings and other redistributed data are synchronized between the active and passive firewalls.
- Active-Passive: The active firewall manages all User-ID agent connections and redistribution. Mappings are synchronized to the passive firewall over the HA link (typically HA1 for control link, but some data like IP-tag can sync over HA3/data link if configured). Upon failover, the newly active firewall takes over existing connections or re-establishes them.
- Active-Active: User-ID session ownership and mapping might be more complex. Generally, the firewall owning the session (based on session owner/setup) handles the User-ID aspects for that session. Redistribution configuration should be identical on both peers.
Ensure HA link health and sufficient bandwidth for synchronization.
Redistribution Filtering and Performance
Filtering (Include/Exclude lists) is crucial for performance. Redistributing unnecessary mappings consumes bandwidth, CPU, and memory on both collector and client firewalls.
- Collector-side Filtering: Define what networks' mappings the collector will send. This is the most efficient place to filter.
- Client-side Considerations: While clients don't directly filter what they receive beyond what the collector sends, they process all received mappings. If a client firewall only protects a specific segment, it might receive many irrelevant mappings if the collector is not filtering properly.
The number of user mappings a firewall can store depends on the model. Exceeding these limits can lead to performance degradation or loss of older mappings.
Troubleshooting Common Issues
-
No Mappings Received by Client:
- Verify Collector Name and Pre-Shared Key (case-sensitive).
-
Check network connectivity between client and collector on the configured port (default TCP/5007). Use
ping,traceroute, and packet captures. - Ensure Security Policies allow `paloalto-userid-agent` application or TCP/5007.
- Verify Service Route configuration on both devices.
-
Check system logs on both devices for connection errors. On client:
less mp-log useridd.log. On collector:less mp-log useridmc.log(for User-ID Main Collector process). - Ensure the collector is actually learning mappings to redistribute.
-
Intermittent Connectivity:
- Look for network instability (flapping links, high latency, packet loss).
-
Check for resource exhaustion on the collector or client (CPU, memory). CLI:
show system resources. - Conflicting User-ID agent configurations (e.g., multiple entries for the same collector).
-
Stale or Incorrect Mappings:
- Verify NTP synchronization across all devices.
- Check User-ID timeouts on the original source (e.g., Windows User-ID Agent timeout, firewall User-ID timeout).
- Ensure redistribution hops are within limits (max 10).
-
High CPU on User-ID Processes (useridd, useridmc):
- Too many mappings being processed or redistributed. Optimize with Include/Exclude lists.
- Rapidly changing mappings (e.g., in a VDI environment without proper configuration).
- Consider upgrading hardware or offloading to Panorama/dedicated User-ID hubs.
// Example debug commands (use with caution and under guidance of Palo Alto Networks support)
debug user-id set tracecuts on
debug user-id dump entry ip <IP_address>
debug user-id on demand-poll server <server_name> ip <ip_address>