Palo Alto Networks: Mastering Multi-VSYS Environments for Enhanced Segmentation and Security
Overview of Multi-VSYS in PAN-OS
A multi-virtual systems (multi-vsys) environment, a cornerstone feature of Palo Alto Networks' PAN-OS, empowers organizations to partition a single physical Next-Generation Firewall (NGFW) or VM-Series firewall into multiple, logically independent virtual firewalls. Each virtual system (vsys) functions as a distinct firewall instance, complete with its own dedicated or shared interfaces, security zones, security policies (including App-ID, Content-ID, and User-ID based rules), routing instances (virtual routers), NAT policies, QoS policies, reporting, and administrative domains.
This powerful capability is indispensable for scenarios requiring strict traffic segmentation and administrative isolation. Common use cases include Managed Security Service Providers (MSSPs) managing multiple tenants, large enterprises segregating departmental or business unit traffic, separating production, development, and testing environments, or meeting stringent compliance mandates (e.g., PCI DSS, HIPAA) that demand logical data separation.
The fundamental principle is that traffic entering an interface assigned to a specific vsys is processed only by the policies and configurations of that vsys. This ensures that the security posture of one vsys does not impact another, providing robust isolation.
Key Features and Benefits of Multi-VSYS
- Logical Segmentation and Isolation: Each vsys operates with its own security policies, routing tables, and administrative credentials. Traffic destined for one vsys is processed independently of others. This prevents security breaches or misconfigurations in one vsys from affecting others.
- Granular Resource Allocation: PAN-OS allows administrators to define resource limits for each vsys, including maximum sessions, security rules, NAT rules, policy-based forwarding (PBF) rules, and virtual router capacity. This prevents a single vsys from consuming all firewall resources.
- Dedicated Administrative Control (Role-Based Access Control - RBAC): Different administrator accounts can be created with permissions scoped to manage only specific vsys instances. This facilitates delegated administration, essential for MSPs or large organizations with multiple IT teams.
- Shared Gateway Functionality: Enables multiple vsys instances to share a common physical interface (and often a single public IP address) for external connectivity, typically to the internet. This conserves IP addresses and simplifies external network configurations.
- Inter-VSYS Traffic Inspection: Traffic can be securely routed and inspected between different vsys instances on the same firewall using features like External Zones or by physically cabling interfaces between vsys if required (though less common and efficient than External Zones).
- User-ID Sharing: A designated vsys (often `vsys1` or a dedicated User-ID hub vsys) can collect User-ID mappings (e.g., from Active Directory, LDAP, GlobalProtect) and redistribute this information to other vsys instances, enabling consistent User-ID based policy enforcement across segments.
- Scalability and Cost-Effectiveness: Leverages a single hardware platform to serve multiple security domains, reducing hardware footprint and associated costs compared to deploying multiple physical firewalls.
- Panorama Management: Multi-VSYS firewalls can be centrally managed by Panorama, Palo Alto Networks' network security management solution. Panorama allows administrators to manage configurations, policies, and software updates for all vsys instances from a single console. Specific Device Group hierarchies and Template Stacks can be applied to individual vsys or groups of vsys.
Enabling Multi-VSYS Mode
By default, Palo Alto Networks firewalls operate in a single vsys mode (implicitly `vsys1`). Enabling multi-vsys mode is a system-level change that requires a reboot of the firewall.
Prerequisites:
- Ensure your Palo Alto Networks firewall model supports multi-vsys. Typically, mid-range (e.g., PA-3200, PA-3400, PA-5200, PA-5400 series) and high-end (e.g., PA-7000 series) physical appliances, as well as most VM-Series virtual firewalls, support this feature. Check the specific model's datasheet for vsys capacity.
- A multi-vsys license might be required depending on the platform and the number of vsys instances you intend to create beyond a certain base number (often `vsys1` + 1 or more included). Consult Palo Alto Networks licensing documentation.
Steps to Enable Multi-VSYS (via GUI):
- Navigate to Device > Setup > Management .
- In the "General Settings" section, click the settings icon (gear) to edit.
- Check the Multi Virtual System Capability checkbox.
- Click OK .
- A warning message will appear indicating a reboot is required and that the current configuration will be moved to `vsys1`. Click Yes to proceed.
- Commit the changes. The firewall will reboot.
Steps to Enable Multi-VSYS (via CLI):
admin@PA-FW> configure
Entering configuration mode
[edit]
admin@PA-FW# set deviceconfig system multi-vsys on
[edit]
admin@PA-FW# commit
After the commit and reboot, the firewall will be in multi-vsys mode. You can verify this in the GUI (Device > Virtual Systems will now be available) or CLI:
admin@PA-FW> show system info
...
multi-vsys: on
...
VSYS Creation and Configuration
Once multi-vsys mode is enabled, `vsys1` exists by default. Additional virtual systems can be created and configured.
Creating a New VSYS (via GUI):
- Navigate to Device > Virtual Systems .
- Click Add at the bottom of the page.
-
General Tab:
- Name: Enter a descriptive name for the vsys (e.g., `vsys-department-A`, `vsys-customer-X`).
- Display Name: (Optional) A more user-friendly name.
- DNS Proxy: (Optional) Configure if this vsys will use DNS Proxy services.
-
Resources Tab:
(Optional but highly recommended for resource control)
- Specify maximum limits for Sessions, Rulebase (Security, NAT, PBF, DoS, Decryption), Virtual Routers, IPSec Tunnels, GlobalProtect Gateway Tunnels, GlobalProtect Portal Concurrent Users . These settings prevent one vsys from exhausting firewall resources.
- If not specified, the vsys shares from the global pool, which can be risky.
-
Interfaces Tab:
- Select physical or aggregate interfaces that will be exclusively assigned to this vsys. An interface can only belong to one vsys at a time (unless it's part of a Shared Gateway configuration).
-
Import Tab:
(Optional)
- Allows importing a configuration from another vsys on the same firewall or from an exported vsys configuration file.
- Click OK and commit the changes.
Assigning Administrators to a VSYS:
You can create administrator accounts that have access only to specific vsys instances:
- Navigate to Device > Admin Roles . Create a new role profile, and under "Virtual Systems," specify the vsys this role can access.
- Navigate to Device > Administrators . Create a new administrator account and assign the role profile created above.
VSYS Context Switching (CLI):
When managing a multi-vsys firewall via CLI, you operate in a global context or a specific vsys context. `vsys1` is the default management vsys.
admin@PA-FW> set system setting target-vsys vsys2 // Switch to vsys2 context
Switched to vsys vsys2
admin@PA-FW(vsys2)> configure
Entering configuration mode
[edit]
admin@PA-FW(vsys2)# // Now configuring vsys2 specific settings
admin@PA-FW(vsys2)> set system setting target-vsys none // Switch back to global context
Switched to vsys none
admin@PA-FW>
Alternatively, you can use `set cli config-output-format set` and prepend commands with `vsys
Mermaid Diagram: Multi-VSYS Architecture with Dedicated Interfaces
This diagram illustrates a Palo Alto Networks firewall in multi-vsys mode. Each VSYS (VSYS1, VSYS2, VSYS3) has its own dedicated physical interface(s), virtual router, and security policies, providing complete logical separation for different network segments or tenants.
Shared Gateway Deep Dive
A Shared Gateway in PAN-OS is a crucial component in multi-vsys deployments, allowing multiple tenant vsys instances to share a common uplink, typically for internet access, without each needing its own public IP address or physical external interface. The Shared Gateway itself is configured as a special, dedicated vsys (often, but not necessarily, `vsys1` or a new vsys specifically for this purpose).
Key Characteristics and Configuration Points:
- Dedicated VSYS: The Shared Gateway functionality resides within a specific vsys. This vsys owns the physical interface(s) connected to the external network (e.g., ISP).
- Interface Configuration: The external-facing interface in the Shared Gateway vsys is configured with an IP address, and it belongs to an "external" zone (e.g., `UNTRUST`).
-
Internal "Shared Gateway" Interface Type:
- For each "tenant" vsys that needs to use the Shared Gateway, you create a Layer 3 interface within that tenant vsys.
- Crucially, in the tenant vsys, this interface is not assigned a physical port. Instead, under Device > Virtual Systems > [Select Tenant VSYS] > Interfaces , when adding/editing the interface, you select the "Shared Gateway" tab.
- Here, you specify the Shared Gateway VSYS (the vsys acting as the gateway) and the Shared Gateway Interface within that vsys (the internal-facing interface of the Shared Gateway vsys that connects to the tenant vsys).
-
Routing:
- Tenant VSYS: A default route (or specific routes) in the tenant vsys's virtual router will point to the IP address of its "Shared Gateway" type interface (which effectively points to the Shared Gateway vsys).
- Shared Gateway VSYS: This vsys has a default route pointing to the actual ISP gateway. It also needs routes back to the tenant vsys networks, typically learned via BGP or configured statically, pointing to the internal interface that connects to the tenants.
-
NAT and Security Policies:
- NAT: Source NAT (typically PAT using the Shared Gateway's external IP) is configured in the Shared Gateway vsys for traffic originating from tenant vsys and going to the internet.
- Security Policies: Security policies to allow/deny traffic from tenant vsys to the internet are configured in the Shared Gateway vsys. Policies controlling traffic within a tenant vsys or between a tenant vsys and other internal networks (not using the Shared Gateway) remain within the tenant vsys.
Configuration Workflow Summary:
- Designate or create a vsys to act as the Shared Gateway (e.g., `vsys-shared-gw`).
- Assign the physical external interface (e.g., `ethernet1/1`) to `vsys-shared-gw`. Configure its IP address and zone (e.g., `UNTRUST`).
- In `vsys-shared-gw`, create an internal-facing interface (e.g., `ethernet1/2`, or a VLAN interface if connecting to multiple tenants via a switch). Assign it an IP address and zone (e.g., `SHARED-TENANT-LINK`). This interface will be the next-hop for tenant vsys.
-
In each tenant vsys (e.g., `vsys-customer-A`):
- Create a new Layer 3 interface (e.g., `ethernet1/10` - name is logical, not tied to physical). Do NOT assign a physical interface.
- Go to the "Shared Gateway" tab for this interface. Select `vsys-shared-gw` as the Shared Gateway VSYS and `ethernet1/2` (the internal interface of `vsys-shared-gw`) as the Shared Gateway Interface.
- Assign an IP address to this interface in `vsys-customer-A` (e.g., an IP in the same subnet as `vsys-shared-gw`'s `ethernet1/2`).
- Configure a default route in `vsys-customer-A` pointing to the IP of `vsys-shared-gw`'s `ethernet1/2`.
- In `vsys-shared-gw`, configure NAT policies for outbound traffic from tenant networks and security policies to control this traffic.
- Ensure `vsys-shared-gw` has routes back to the tenant networks.
For detailed configuration steps, refer to the official documentation on Configuring a Shared Gateway (example using PAN-OS 10.2, adjust version as needed) .
Mermaid Sequence Diagram: Shared Gateway Traffic Flow with NAT
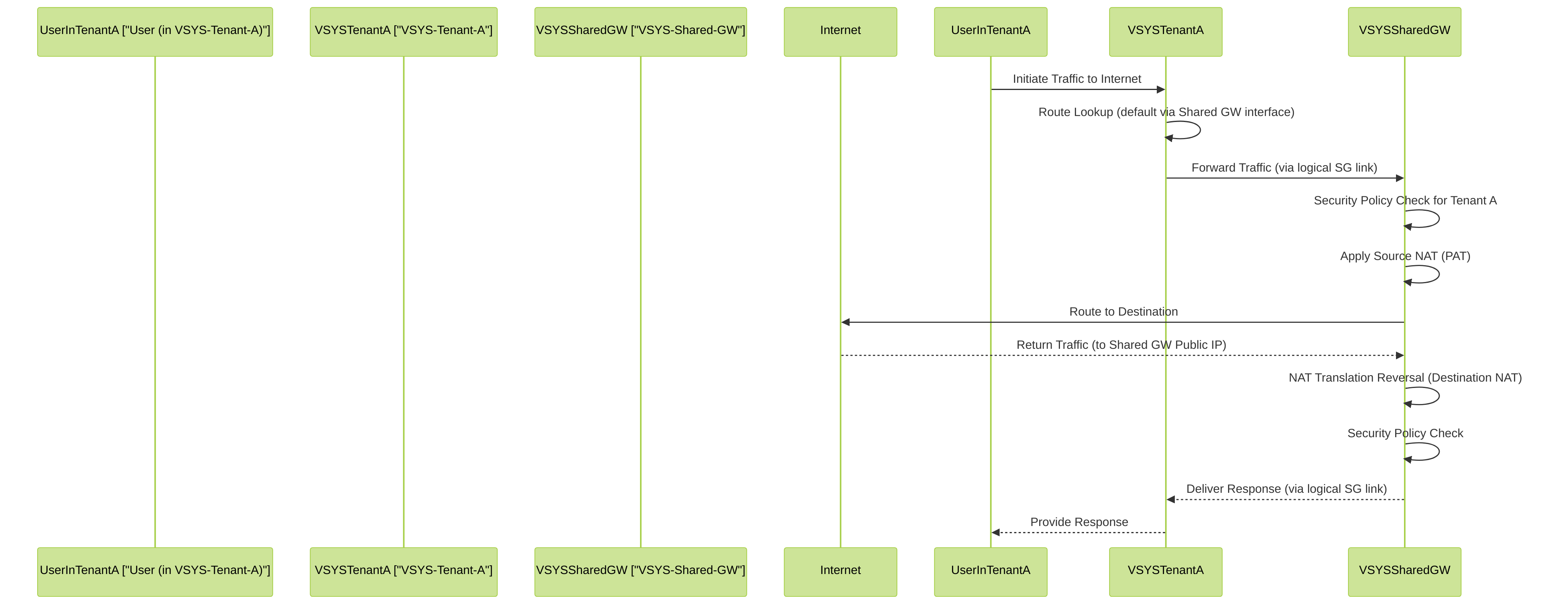
This sequence diagram illustrates the traffic flow from a user in a tenant VSYS through a Shared Gateway VSYS to the internet. It highlights routing within the tenant, policy checks and NAT in the Shared Gateway, and the return path.
External Zone for Inter-VSYS Communication
An External Zone in PAN-OS is a specialized type of security zone designed specifically to enable direct, logical communication between different virtual systems (vsys) residing on the same Palo Alto Networks firewall. This mechanism allows traffic to pass from one vsys to another without needing to physically leave and re-enter the firewall, making inter-vsys communication efficient.
Key Characteristics and Usage:
- Logical Construct: Unlike regular security zones (e.g., Trust, Untrust, DMZ) that are bound to physical or virtual interfaces, an External Zone is not directly associated with an interface. Instead, it acts as a logical representation of "another vsys."
-
One-to-One Mapping (Per VSYS):
Each vsys can have at most
one
External Zone. This External Zone in `vsysA` would be used to represent `vsysB` when `vsysA` needs to send traffic to or receive traffic from `vsysB`. Similarly, `vsysB` would have its own External Zone representing `vsysA`.
Gotcha! (Palo Alto Networks): A common point of confusion is that an External Zone in `vsysA` doesn't represent "all other vsys." It represents *a specific, designated other vsys* that `vsysA` is configured to communicate with through this mechanism. If `vsysA` needs to talk to `vsysB` and `vsysC` via External Zones, this is not directly possible using a single External Zone; alternative routing or multiple inter-vsys links would be needed. However, traffic can transit through intermediate vsys.
-
Inter-VSYS Routing Required:
- To direct traffic towards another vsys via an External Zone, you must configure a static route in the source vsys's virtual router.
- This static route's destination would be the network(s) in the target vsys, and the next-hop would be specified as the target vsys itself (e.g., `next-vsys vsysB`).
-
Security Policies:
As with any traffic traversing zones on a Palo Alto Networks firewall, security policies are mandatory to permit or deny traffic.
- In the source vsys (e.g., `vsysA` sending to `vsysB`): A security policy is needed allowing traffic from an internal zone (e.g., `vsysA-Trust`) to the External Zone (which represents `vsysB`).
- In the destination vsys (e.g., `vsysB` receiving from `vsysA`): A security policy is needed allowing traffic from its External Zone (which represents `vsysA`) to its internal destination zone (e.g., `vsysB-DMZ`).
-
Configuration Steps:
- In `vsysA`: Navigate to Network > Zones . Click Add . For Type , select External . Give it a name (e.g., `EXT-to-VSYSB`). Under the "External" tab, select `vsysB` from the "Select Virtual System" dropdown.
- In `vsysB`: Repeat the process, creating an External Zone (e.g., `EXT-to-VSYSA`) and selecting `vsysA`.
- In `vsysA`: Go to Network > Virtual Routers > [vsysA's_VR] > Static Routes . Add a route for `vsysB`'s network(s) with Next Hop Type as Next VSYS and select `vsysB`.
- In `vsysB`: Add a similar static route for `vsysA`'s network(s) pointing to `next-vsys vsysA`.
- In both `vsysA` and `vsysB`, create the necessary security policies involving their respective External Zones.
External Zones are highly efficient for inter-vsys traffic that needs to remain within the firewall chassis, as they avoid hair-pinning traffic through external interfaces.
For more information, consult the official documentation on Inter-VSYS Traffic (example using PAN-OS 10.2, adjust version as needed) .
Mermaid Diagram: Inter-VSYS Traffic Flow using External Zones
This diagram depicts traffic flow between VSYS-A and VSYS-B using External Zones. Traffic from a user in VSYS-A is routed to its External Zone (representing VSYS-B) based on a "Next VSYS" static route. Security policies are applied in VSYS-A. The traffic then logically transits to VSYS-B's External Zone (representing VSYS-A), where VSYS-B's security policies are applied before the traffic reaches the server in VSYS-B's DMZ.
Resource Management in Multi-VSYS
Effective resource management is critical in a multi-vsys environment to ensure fair usage and prevent resource exhaustion by a single vsys. PAN-OS provides mechanisms to allocate and limit various system resources on a per-vsys basis.
Configurable Resources per VSYS:
- Max Sessions: The maximum number of concurrent sessions a vsys can handle.
- Max Security Rules: The maximum number of security policy rules.
- Max NAT Rules: The maximum number of NAT policy rules.
- Max Policy-Based Forwarding (PBF) Rules: The maximum number of PBF rules.
- Max Decryption Rules: The maximum number of SSL/TLS decryption policy rules.
- Max DoS Protection Rules: The maximum number of Denial of Service protection policy rules.
- Max Virtual Routers: The number of virtual routers that can be configured within the vsys.
- Max IPSec Tunnels: The maximum number of active IPSec VPN tunnels.
- Max GlobalProtect Gateway Tunnels: Maximum concurrent GlobalProtect VPN tunnels for a gateway configured in this vsys.
- Max GlobalProtect Portal Concurrent Users: Maximum concurrent users for a GlobalProtect portal configured in this vsys.
These limits are configured under Device > Virtual Systems > [select vsys] > Resources tab .
CPU Resource Allocation:
While direct per-vsys CPU percentage allocation isn't typically granularly configured like individual rule counts, the overall firewall's CPU resources are shared among vsys. The session limits and processing demands of each vsys indirectly influence CPU load. On some higher-end platforms (like the PA-7000 series with multiple Network Processing Cards - NPCs), there can be more sophisticated partitioning of hardware resources, but for most platforms, CPU is a globally shared resource managed by PAN-OS. Ensuring that session and rule limits are appropriately set helps manage CPU utilization indirectly.
Monitoring Resource Usage:
- GUI: The Dashboard (ACC, GlobalProtect, etc.) can often be filtered by vsys. Specific statistics for vsys resources can be found under Device > Virtual Systems > [select vsys] > Resource Usage tab .
-
CLI:
admin@PA-FW> show running resource-monitor virtual-system vsys2
Panorama and Multi-VSYS Management
Palo Alto Networks Panorama provides centralized management for multiple firewalls, including those configured in multi-vsys mode. Panorama simplifies administration, policy deployment, and monitoring across numerous vsys instances.
Key Panorama Capabilities for Multi-VSYS:
-
Device Groups and Templates:
- Device Groups: You can create Device Groups in Panorama that specifically target individual vsys instances on a firewall. For example, `DG-CustomerA-VSYS2` could manage policies for `vsys2` on firewall `FW-01`. This allows for vsys-specific policy management.
- Templates/Template Stacks: Network and device settings (interfaces, zones, server profiles, virtual routers) can be pushed to specific vsys instances using Templates and Template Stacks. Panorama variables can be used within templates to customize settings for each targeted vsys.
- Context Switching: Within the Panorama GUI, when managing a multi-vsys firewall, you can switch context to a specific vsys to view and manage its dedicated configuration (policies, objects, network settings relevant to that vsys).
- Role-Based Access Control (RBAC): Panorama's RBAC can be extended to control administrative access to specific vsys within managed firewalls, ensuring that administrators only see and manage the vsys instances they are authorized for.
- Centralized Logging and Reporting: Logs from all vsys instances can be forwarded to Panorama (or dedicated Log Collectors managed by Panorama / Cortex Data Lake). Panorama provides aggregated views and reporting, with the ability to filter by vsys.
-
Configuration Deployment:
Panorama allows administrators to create and validate configurations for individual vsys and then push these configurations to the managed firewalls.
Gotcha! (Palo Alto Networks): When using Panorama, it's crucial to understand the hierarchy. Some objects might be "shared" globally in Panorama and available to all Device Groups/Templates, while others might be specific to a Device Group (and thus a vsys or group of vsys). Careful planning of the object scope and Device Group/Template structure is essential.
- Software Updates: Panorama can manage PAN-OS software updates for firewalls, which applies to the entire device, including all its vsys instances.
Managing multi-vsys firewalls via Panorama offers significant operational efficiency, consistency, and scalability compared to managing each vsys or firewall individually.
Mermaid Diagram: Panorama Managing Multi-VSYS Firewall
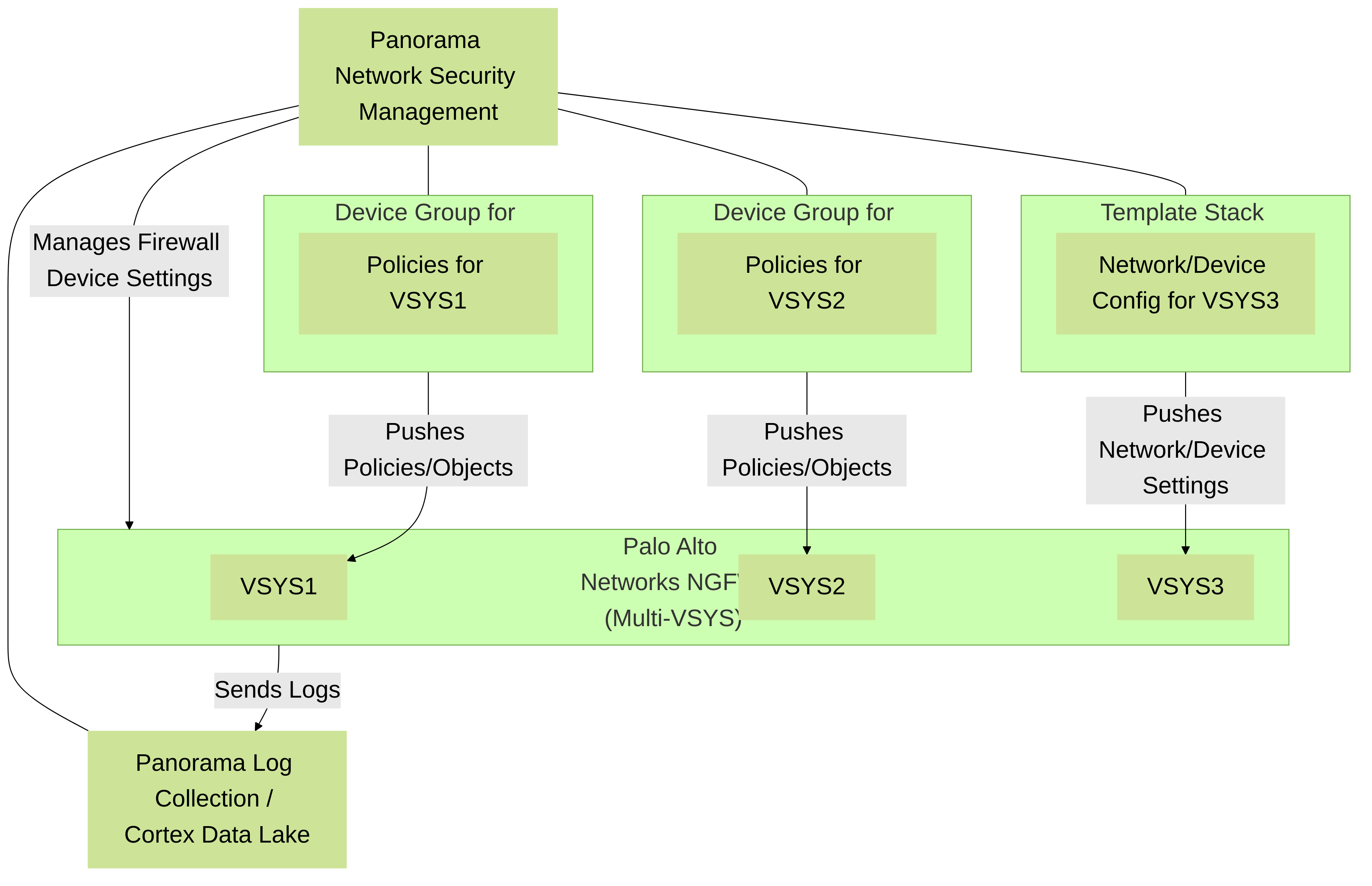
This diagram shows Panorama managing a multi-vsys firewall. Panorama uses Device Groups to apply specific policies to individual VSYS instances (VSYS1, VSYS2) and Template Stacks to push network and device configurations (e.g., to VSYS3). Logs from all VSYS are sent to Panorama for centralized monitoring and reporting.
User-ID Sharing in Multi-VSYS Environments
User-ID technology allows policies to be based on user and group identity rather than just IP addresses. In a multi-vsys environment, sharing User-ID information across vsys instances is often necessary for consistent policy enforcement.
User-ID Hub Concept:
- A designated vsys, often `vsys1` or a dedicated "User-ID hub" vsys, is configured to be the central point for User-ID information collection.
- This hub vsys connects to User-ID agents, domain controllers (for Windows monitoring), syslog sources, GlobalProtect, or other sources of user mapping information.
- Other "tenant" or "spoke" vsys instances can then be configured to receive User-ID mappings from this hub vsys.
Configuration (General Steps):
-
In the Hub VSYS (e.g., `vsys1`):
- Configure User-ID Agents, Server Monitoring, etc., as per standard User-ID setup ( Device > User Identification ).
- Enable User-ID redistribution. Navigate to Device > User Identification > User-ID Agents > [Agent Name] > Client Configuration (this terminology varies slightly across PAN-OS versions, look for redistribution or multi-vsys sharing settings). Alternatively, for system-wide redistribution (newer PAN-OS versions), configure under Device > Setup > Services > Service Route Configuration to ensure User-ID service is reachable, and then configure redistribution under Device > User Identification > Setup > Multi-VSYS Sharing .
-
In the Spoke/Tenant VSYS (e.g., `vsys2`):
- Navigate to Device > User Identification > Setup > Multi-VSYS Sharing (or similar path depending on PAN-OS version).
- Configure the spoke vsys to receive mappings from the hub vsys. You'll typically specify the hub vsys name.
- Ensure network connectivity allows the spoke vsys to communicate with the hub vsys for User-ID updates (often over the management plane or via inter-vsys routing if necessary).
This allows each vsys to enforce User-ID based security policies using a consistent and centrally managed set of user-to-IP mappings, without each vsys needing to independently collect all User-ID information.
Logging and Reporting in Multi-VSYS
Each vsys in a multi-vsys environment generates its own logs (Traffic, Threat, URL Filtering, WildFire, etc.). It's crucial to manage and access these logs effectively.
-
Local Logging:
By default, logs are stored locally on the firewall, partitioned by vsys. Accessing logs via the firewall's GUI or CLI will be context-specific to the selected vsys.
- GUI: When you switch vsys context (top-right dropdown), the Monitor tab will show logs for that selected vsys.
-
CLI:
Use `set system setting target-vsys
` then `show log `. Or, filter directly: `show log traffic filter "vsys eq "`.
-
Log Forwarding:
Best practice is to forward logs to a centralized logging solution:
- Panorama: Each vsys can have its Log Forwarding Profiles configured to send logs to Panorama (or its associated Log Collectors). Panorama then aggregates these logs and allows filtering by vsys.
- Cortex Data Lake (CDL): Similar to Panorama, logs can be forwarded to CDL for centralized storage, analysis, and integration with other Palo Alto Networks cloud services.
- Syslog/SNMP: Log Forwarding Profiles can also send logs to external Syslog servers or generate SNMP traps. This can be configured per vsys.
-
Reporting:
- On-box reports: Can be generated per vsys.
- Panorama/CDL reports: Offer comprehensive, aggregated reporting capabilities with filtering by vsys, providing a consolidated view across the entire multi-vsys deployment.
Common Use Cases for Multi-VSYS
| Use Case | Description | Key Multi-VSYS Benefits Utilized |
|---|---|---|
| Managed Security Service Providers (MSSPs) | Hosting multiple customers (tenants) on a single physical firewall. | Isolation, dedicated administration, resource allocation, Shared Gateway for internet, User-ID sharing. |
| Large Enterprises (Departmental/BU Segmentation) | Isolating network traffic and security policies for different departments (e.g., Finance, HR, Engineering). | Isolation, dedicated administration (optional), granular policy control, inter-vsys communication via External Zones. |
| Dev/Test/Prod Environments | Separating development, testing, and production networks with distinct security policies and risk profiles. | Isolation, distinct policy sets, resource control. |
| Compliance Requirements (e.g., PCI DSS) | Isolating specific network segments (e.g., Cardholder Data Environment) to meet regulatory compliance. | Strict isolation, auditable policy boundaries, dedicated logging. |
| Business Partner Extranets | Providing controlled network access to business partners, isolated from internal corporate networks. | Isolation, specific security policies for partner access. |
| Firewall Consolidation | Reducing the number of physical firewalls by consolidating multiple security domains onto fewer, more powerful platforms. | Cost savings, reduced hardware footprint, centralized management (especially with Panorama). |
Limitations and Considerations
- Platform Support and VSYS Limits: Not all Palo Alto Networks firewall models support multi-vsys, and those that do have a maximum number of supported vsys. Always check the platform datasheet. VM-Series also has specific licensing for vsys capacity.
- Reboot Requirement: Enabling multi-vsys mode requires a firewall reboot. Disabling multi-vsys (reverting to single vsys mode) requires a factory reset of the firewall.
- System-Level Settings: Some settings are global to the firewall and cannot be configured independently per vsys. Examples include PAN-OS version, High Availability (HA) configuration (though HA path monitoring can be vsys-specific), management interface IP, and some global counters.
- GlobalProtect: While GlobalProtect can be configured in a multi-vsys environment, careful planning is needed. Often, a dedicated vsys is used for GlobalProtect Portal and Gateways, or specific configurations are required if gateways are distributed across multiple vsys. User-ID sharing becomes very important here.
- SD-WAN: Integrating SD-WAN features in a multi-vsys environment can have complexities, particularly around how VPN tunnels and path selection interact with vsys boundaries. This typically requires careful design.
- Performance Overhead: While generally efficient, running multiple vsys instances can introduce some performance overhead compared to a single vsys configuration on the same hardware, due to context switching and resource management. This is usually minimal on appropriately sized platforms.
- Complexity: Managing a multi-vsys environment, especially with inter-vsys routing and shared services, can be more complex than managing a single-vsys firewall. Panorama significantly helps mitigate this complexity.
- Shared Objects Scope: When not using Panorama, objects (addresses, services, etc.) are typically local to each vsys. Panorama allows for shared object scopes across vsys, which simplifies management but requires careful planning.
- Licensing: Some platforms may require specific licenses to enable multi-vsys or to increase the number of supported vsys beyond a base count. Subscription services (Threat Prevention, URL Filtering, WildFire, etc.) are generally licensed for the entire device and their benefits apply to traffic processed by any vsys, subject to policy.
Troubleshooting Common Multi-VSYS Issues
-
No Traffic Flowing Through a VSYS:
- Verify interface assignments: Is the correct physical interface assigned to the vsys? Is the interface up/up?
- Zone configuration: Are interfaces in the correct zones within the vsys?
- Security Policies: Are there "allow" policies in the vsys for the traffic in question? Check policy order.
- Routing: Does the vsys's virtual router have correct routes for source and destination?
- NAT Policies: If NAT is expected, are policies correctly configured in the vsys?
-
Inter-VSYS Communication Failure (External Zones):
- External Zone configuration: Is the External Zone in each vsys correctly pointing to the other vsys?
- Static Routes: Does each vsys have a static route with "Next VSYS" pointing to the other vsys for the relevant networks?
- Security Policies: Are there policies in both vsys allowing traffic (Source VSYS: InternalZone to ExternalZone; Destination VSYS: ExternalZone to InternalZone)?
- Log analysis: Check traffic logs in both vsys to see where the traffic is being dropped.
-
Shared Gateway Issues:
- Tenant VSYS Routing: Does the tenant vsys have a default route pointing to the Shared Gateway vsys's internal interface IP?
-
Shared Gateway VSYS Configuration:
- Are NAT policies correctly configured for tenant traffic?
- Are security policies in the Shared Gateway vsys allowing tenant traffic to the internet?
- Does the Shared Gateway vsys have a correct default route to the ISP?
- Are there routes back to tenant networks in the Shared Gateway vsys?
- Interface types: Verify the tenant vsys interface connecting to the Shared Gateway is correctly configured using the "Shared Gateway" tab.
-
Resource Exhaustion:
-
Use `show running resource-monitor virtual-system
` or GUI to check resource usage against configured limits. - If a vsys is hitting limits, investigate the cause (e.g., high session count due to an attack, too many rules) or consider increasing limits if legitimate.
-
Use `show running resource-monitor virtual-system
-
User-ID Not Propagating:
- Hub VSYS: Is it correctly collecting User-ID info? Are redistribution settings enabled?
- Spoke VSYS: Is it configured to receive from the correct hub vsys?
- Connectivity: Can the spoke vsys communicate with the hub vsys (check service routes, inter-vsys routing if needed)?
- Check `show user user-id-agent state all` (on hub) and `show user ip-user-mapping all` (on hub and spoke, filtering by vsys).
General Troubleshooting Commands (use `set system setting target-vsys
show session all filter// Check active sessions show counter global filter packet-filter yes delta yes // Real-time packet processing counters show log traffic // Check traffic logs show log threat // Check threat logs debug dataplane packet-diag set filter ... // Advanced packet diagnostics test routing fib-lookup virtual-router ip // Check routing table
PCNSE Exam Focus for Multi-VSYS
For the PCNSE exam, a solid understanding of multi-vsys is essential. Expect questions covering:
- Core Concepts: Purpose of multi-vsys, benefits (isolation, resource management), when to use it.
- Enabling Multi-VSYS: Process, CLI command, reboot requirement, impact on existing config (`vsys1`).
- VSYS Configuration: Creating vsys, assigning interfaces, resource allocation (max sessions, rules, etc.).
-
Inter-VSYS Communication:
- External Zones: Configuration, how they work, static routing with "Next VSYS," security policy requirements in both vsys.
- Limitations (one External Zone per vsys).
-
Shared Gateway:
- Purpose and architecture.
- Role of the Shared Gateway vsys vs. tenant vsys.
- Interface configuration in tenant vsys (Shared Gateway tab).
- Where NAT and security policies for internet traffic are applied (in Shared Gateway vsys).
- Resource Management: Importance of setting limits, types of resources that can be limited.
- Panorama Management: How Panorama handles multi-vsys (Device Groups, Templates for vsys).
- User-ID Sharing: Concept of a User-ID hub and spoke vsys, general configuration idea.
- Logging: How logs are segregated, forwarding to Panorama/CDL.
- Troubleshooting: Common issues and how to approach them (e.g., checking policies/routes in the correct vsys).
-
CLI Commands:
`set deviceconfig system multi-vsys on`, `set system setting target-vsys
`, `show running resource-monitor virtual-system `.