Using Panorama as a Hub for User-ID Redistribution
It's important to remember that while Panorama primarily manages your firewalls, using it for User-ID redistribution ties it more closely into your network's operations. Typically, you wouldn't need to worry about Panorama going down because the firewalls can function without Panorama. However, when you start using Panorama for User-ID redistribution, it becomes a crucial part of your network. Fortunately, most setups include a backup Panorama, so downtime shouldn't be a concern. Let’s get started and see how this works in practice.
Please note that this setup doesn't require dedicated 'User-ID Agents' running on separate servers if the firewalls themselves can collect the necessary information (e.g., via DC monitoring or GP).
Diagram and Scenario
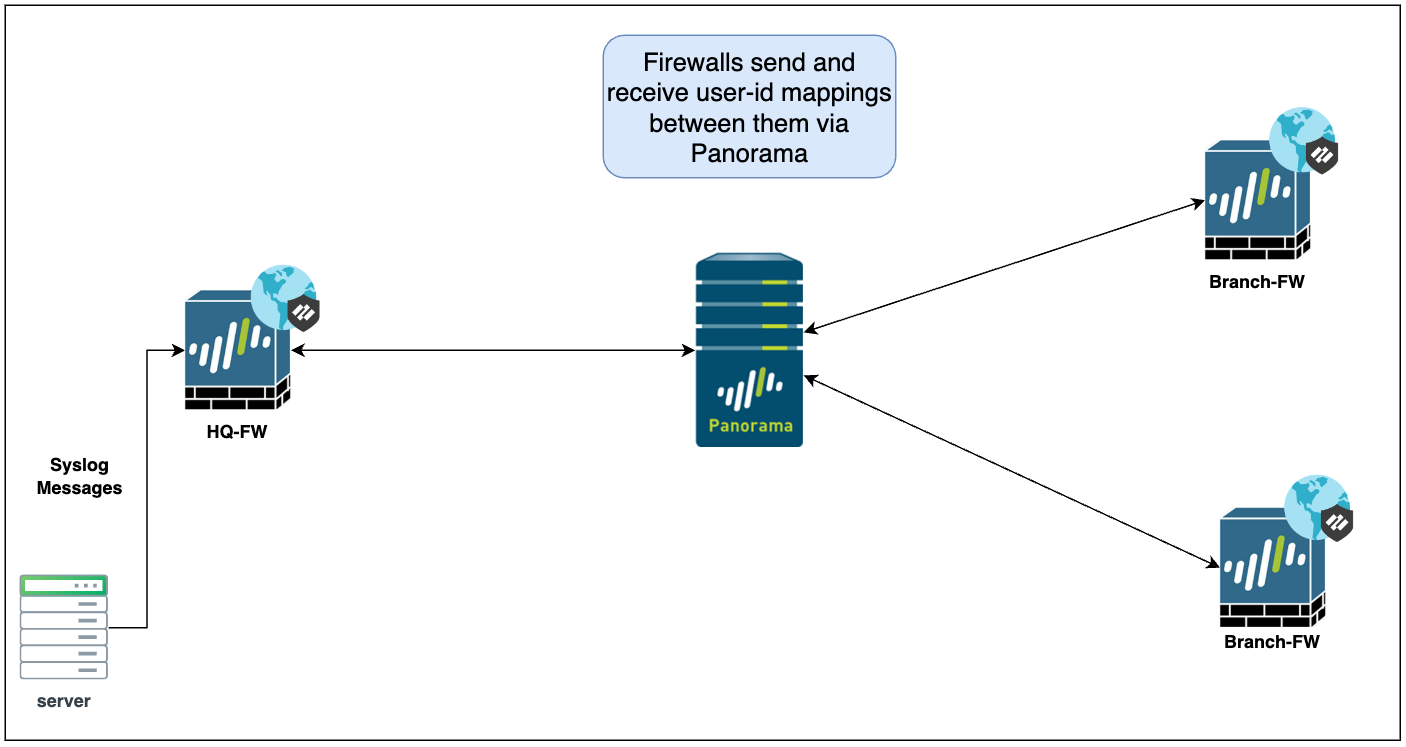
In this example, let's consider a scenario where we have a main headquarters firewall (HQ-FW) that collects User-ID mappings in various ways (e.g., reading directly from the Domain Controller, receiving Syslog messages, or Global Protect VPN connections). We also have users working from branch offices connecting via Global Protect VPN to their respective branch firewalls (Branch-FW).
If we want to allow access to resources regardless of where the user is located, creating rules based on User-ID (username/group) is much more flexible than using just IP addresses.
Here's the challenge: if a user connects to a Branch-FW and tries to access a resource at HQ, how will the HQ-FW recognize this user and apply the correct policies? This is where User-ID redistribution becomes essential.
We can configure our firewalls so that all of them send their learned User-ID mappings TO Panorama. Additionally, the firewalls can also be configured to receive User-ID mappings FROM Panorama. This creates a hub-and-spoke topology with Panorama as the central hub, rather than a complex full mesh where every firewall would need direct connections to every other firewall.
This hub-and-spoke approach simplifies the architecture by centralizing the distribution of User-ID information through Panorama.
In summary, the goal is for every firewall to send its learned user-id mappings to Panorama, and also for every firewall to receive the complete set of mappings from Panorama.
Configure Firewalls to Send User-ID Mappings to Panorama
To set up the redistribution of User-ID mappings to Panorama, you’ll need to configure both the individual firewalls and Panorama itself.
Please note that the configuration steps might differ slightly if you are using PanOS version 9.x . This example is based on PanOS 10.x , so keep that in mind when following these instructions. (In 10.x, the relevant menu is generally under "Data Redistribution" instead of "User Identification > User Mapping" for redistribution settings).
Configure Firewalls to Send Mappings to Panorama
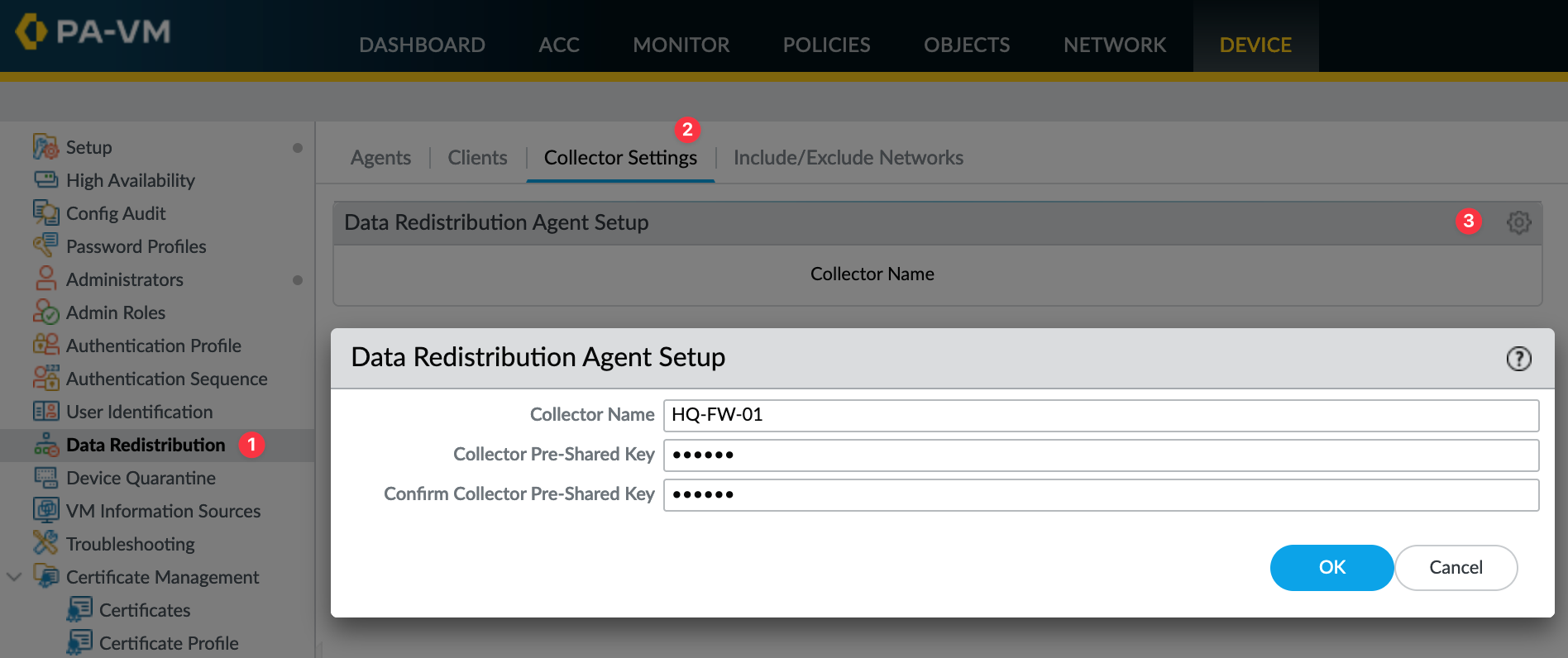
- Navigate to Device > Data Redistribution > Collector Settings on each firewall (HQ-FW, Branch-FWs, etc.).
- Configure Collector Settings by entering a unique Collector Name for that firewall (e.g., `HQ-FW-Collector`) and a secure Pre-Shared Key .
- Remember these details (especially the PSK, which often should be the same for simplicity, and the specific Collector Name for each firewall) as you’ll need them for the Panorama setup. The Collector Name and the PSK must match what you configure on Panorama for that specific firewall agent.
After you have configured all firewalls to send their User-ID mappings, you will need to configure Panorama to receive these mappings.
Panorama Configuration to Receive the Mappings
Now that we’ve set up the firewalls to send their User-ID mappings to Panorama, let’s configure Panorama to receive these mappings.
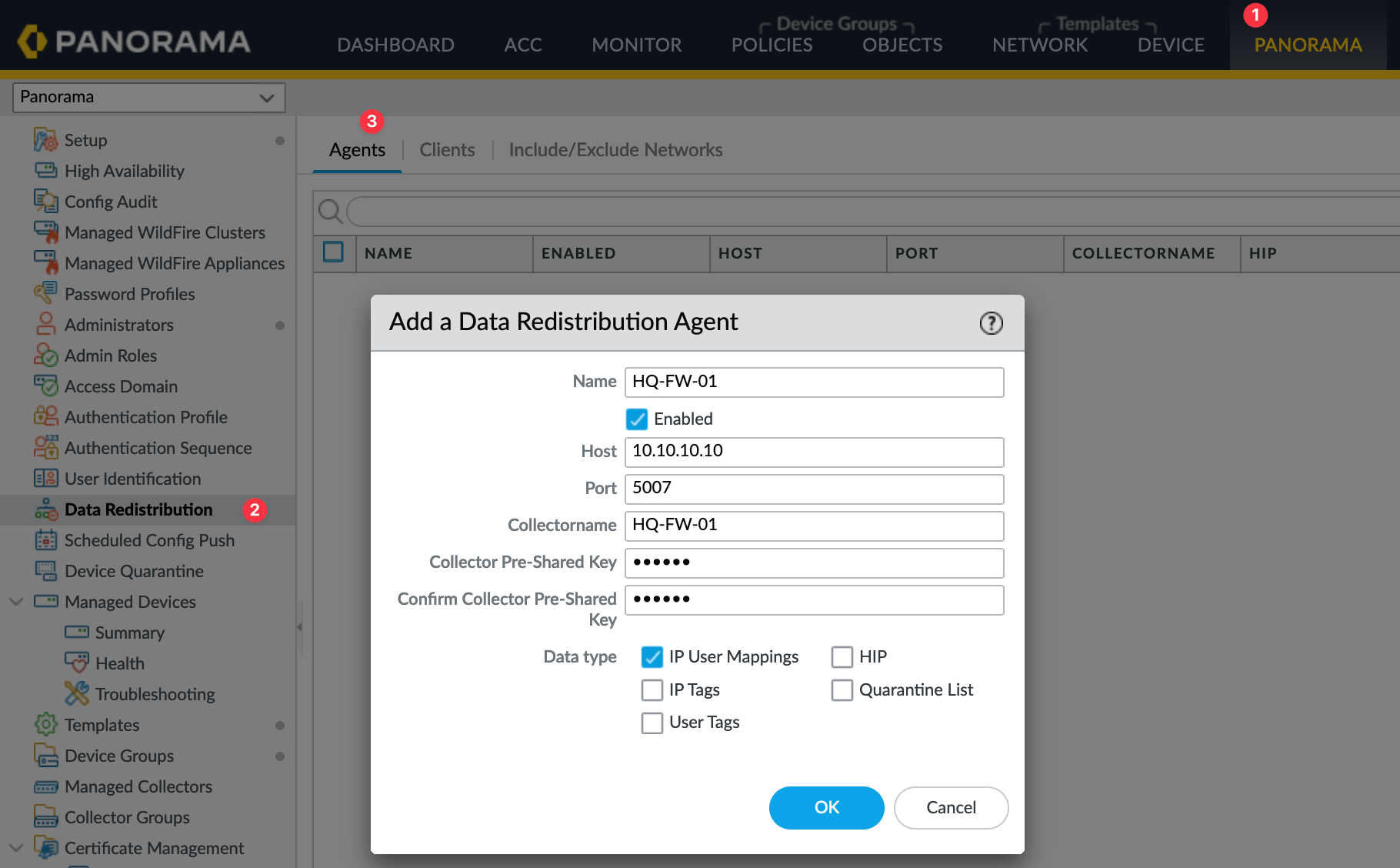
Navigate to Panorama > Data Redistribution > Agents . Here, Add a new agent entry for each firewall that will be sending mappings.
- Enter a Name for the agent (e.g., `Agent-for-HQ-FW`).
- Select the Serial Number of the firewall OR enter its Host IP address (reachable from Panorama).
- Enter the exact Collector Name you configured on that specific firewall (from Step 2 above, e.g., `HQ-FW-Collector`).
- Enter the matching Pre-Shared Key (PSK) you configured on that firewall.
- Select the Data Type(s) you want Panorama to receive (e.g., `IP User Mappings`).
- Click OK .
- Repeat this "Add Agent" step for every firewall (e.g., Branch-FW1, Branch-FW2...).
Once Panorama is configured to receive the mappings from all firewalls, the next step is to configure the firewalls to receive the aggregated User-ID mappings *back* from Panorama. This completes the information sharing loop.
Configure Firewalls to Receive User-ID Mappings From Panorama
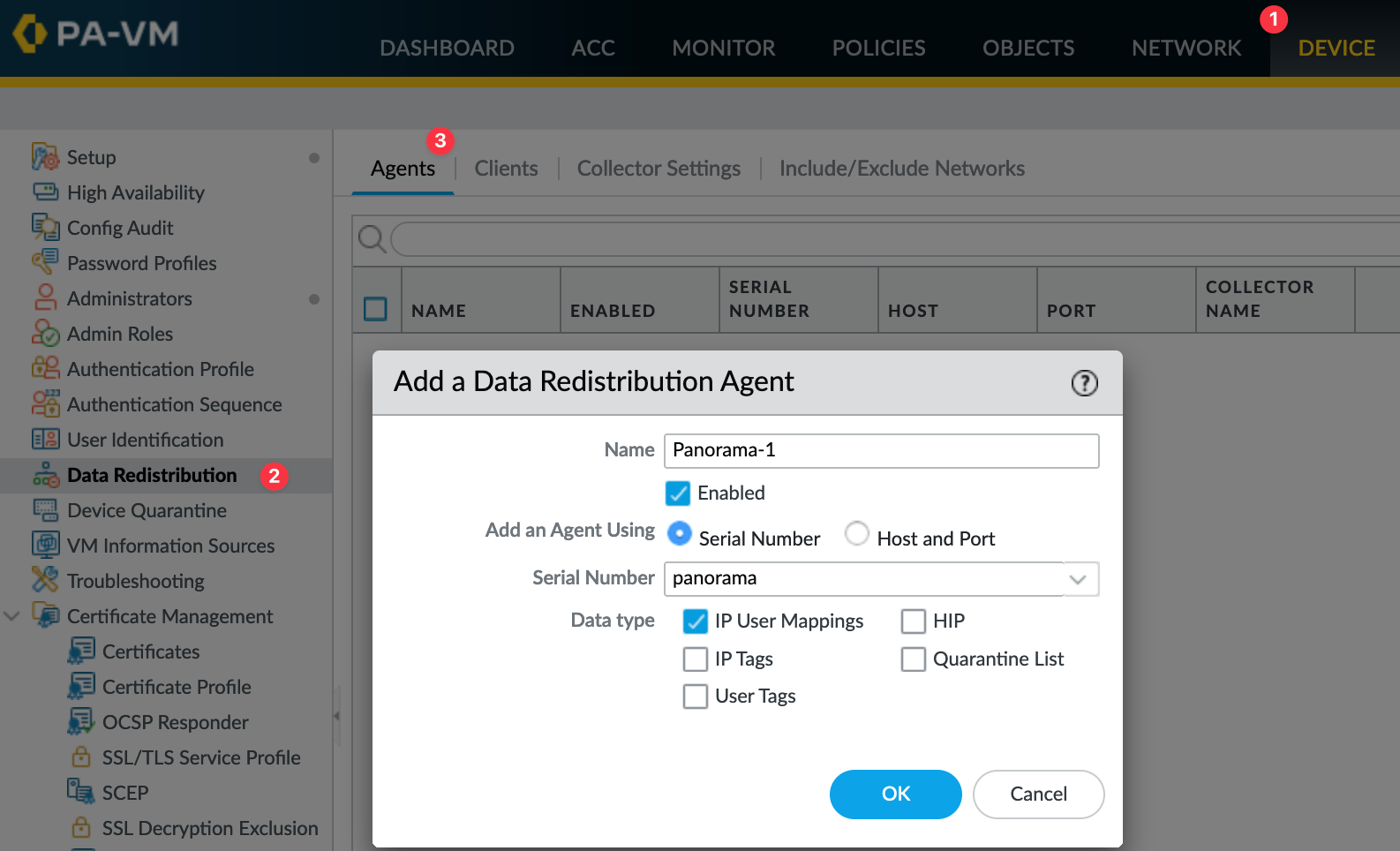
For the final step in setting up User-ID redistribution, go to each firewall (HQ-FW, Branch-FWs...) and navigate to Device > Data Redistribution > Agents .
- Here, Add Panorama as a new agent.
- Enter a Name (e.g., `Panorama-Hub`).
- Enter the Host IP address of your Panorama management server.
- Enter the appropriate Port (default is usually 5007).
- Select the required Data Type(s) to receive (e.g., `IP User Mappings`).
- Click OK .
- If your setup includes two Panoramas in an High Availability (HA) active/passive configuration, make sure to repeat this process adding the secondary Panorama as another agent source.
Closing Up
That wraps up configuring User-ID redistribution with Panorama as a central hub across multiple firewalls. Now, when a user connects to Global Protect VPN through a branch firewall, their User-IP mapping is sent to Panorama. Panorama then redistributes this mapping (along with mappings from HQ and other branches) back to all connected firewalls. All firewalls will eventually have a consistent view of User-IP mappings across the network. This same process applies to mappings learned via Active Directory monitoring or Syslog.