PAN-OS Subscriptions: Overview & Licensing
Palo Alto Networks Next-Generation Firewalls (NGFWs) are powerful security platforms, but their full potential is unlocked through various cloud-delivered security subscriptions. These subscriptions provide dynamic updates, advanced threat intelligence, and specialized security services to protect against an ever-evolving threat landscape.
The Role of Subscriptions
Subscriptions transform the NGFW from a stateful firewall into a comprehensive security enforcement point. They enable features like:
- Protection against known and unknown malware, exploits, and phishing attacks.
- Granular control over web and application usage.
- Secure remote access for users.
- Visibility and control over IoT devices and SaaS applications.
- Data loss prevention.
- Proactive operational insights.
Most subscriptions are licensed on a per-firewall basis and require regular updates from the Palo Alto Networks cloud to maintain efficacy. These updates include new threat signatures, URL categorizations, application identifications, and more.
Licensing and Activation
Subscription licenses are typically purchased for a specific term (e.g., 1, 3, or 5 years). Once purchased, they need to be activated and associated with a specific firewall device or, in some cases, a Panorama instance or cloud service account.
- Activation: Licenses are activated through the Palo Alto Networks Customer Support Portal (CSP). An auth code is usually provided, which is then used to register the license to a device serial number.
- Retrieval on Firewall: After activation in the CSP, the firewall must retrieve the license from the licensing server. This can be done via Device > Licenses > Retrieve license keys from license server . Internet connectivity is required for this process.
- Dynamic Updates: Once licensed, the firewall needs to be configured to download and install dynamic content updates for active subscriptions. This is managed under Device > Dynamic Updates . Scheduling regular checks for updates is a best practice.
- Grace Periods: Some subscriptions might offer a grace period after expiration, but relying on this is not recommended. Functionality will be significantly impacted or cease once a license truly expires.
updates.paloaltonetworks.com
and other relevant services.
Subscription Dependencies
Some subscriptions have dependencies on others. For example, DNS Security requires an active Threat Prevention license. Understanding these dependencies is important for proper deployment and functionality.
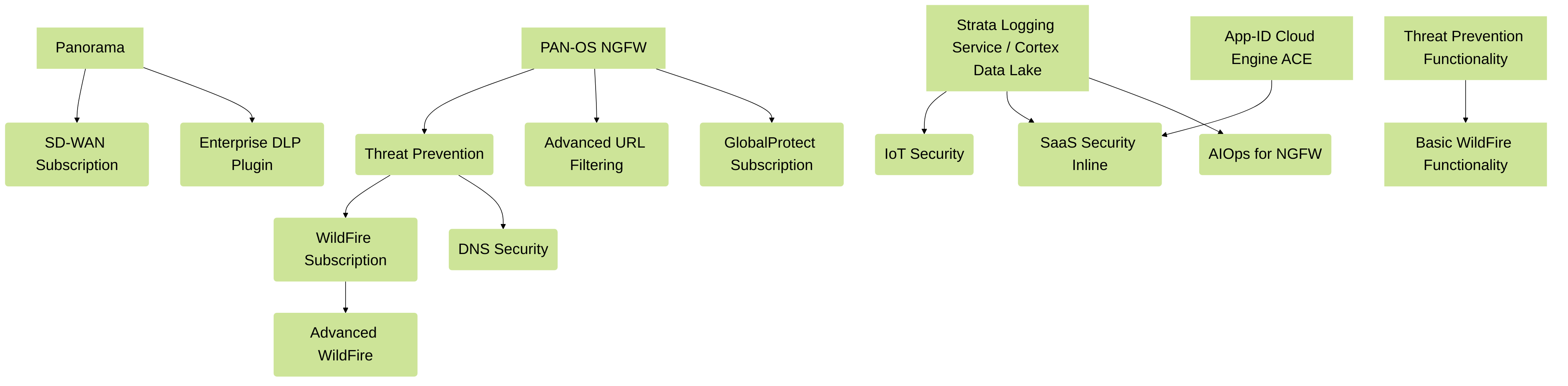
Key interdependencies and management points for PAN-OS subscriptions. Note that basic WildFire functionality is included with Threat Prevention, but a full WildFire subscription offers enhanced features.
Core Security Service: Threat Prevention
The Threat Prevention subscription is foundational for protecting against a wide range of known threats. It bundles several key security engines and capabilities.
Key Features
- Intrusion Prevention System (IPS): Detects and blocks network-based exploits targeting system vulnerabilities. It uses regularly updated signatures to identify malicious traffic patterns.
- Anti-Virus (AV): Scans traffic for known viruses, worms, trojans, and other malware. Signatures are updated frequently to cover new threats.
- Anti-Spyware: Detects and blocks spyware installations and Command-and-Control (C2) communications from already compromised hosts. This includes blocking connections to known malicious C2 servers.
- Vulnerability Protection: Applies profiles to protect against known software vulnerabilities that might be exploited.
- Built-in External Dynamic Lists (EDLs): Provides access to Palo Alto Networks-maintained EDLs of malicious IP addresses and domains that can be used in security policies.
- Basic WildFire Access: Allows forwarding of a limited set of unknown file types to the WildFire cloud for analysis, with standard verdict times (not the 5-minute SLA of the full WildFire subscription). It also provides access to WildFire signatures generated from samples submitted by any WildFire user globally.
- DNS Sinkhole: Can be configured to redirect DNS queries for known malicious domains to an internal "sinkhole" IP, helping identify infected hosts.
How it Works
Threat Prevention profiles (Antivirus, Anti-Spyware, Vulnerability Protection) are attached to Security Policy rules. When traffic matches a rule with an associated Threat Prevention profile, the traffic is inspected against the signatures defined in that profile. Actions like alert, block, reset, or sinkhole can be configured based on threat severity or specific signature triggers.
Core Security Service: WildFire & Advanced WildFire
WildFire is Palo Alto Networks' cloud-based malware analysis service, designed to detect and prevent unknown, zero-day malware and exploits. Advanced WildFire builds upon this with even more sophisticated detection capabilities.
WildFire Subscription
- Protection Against Unknown Threats: Analyzes unknown files and email links submitted by firewalls (and other Palo Alto Networks products) in a secure cloud sandbox environment.
- Analysis Techniques: Uses static analysis, dynamic analysis (executing files in a virtual environment), machine learning, and bare metal analysis to identify malicious behavior.
- Fast Verdict Times: With a full WildFire subscription, verdicts for newly discovered malware are typically available globally within 5 minutes (this is a key differentiator from the basic WildFire included with Threat Prevention).
- Expanded File Type Support: Supports forwarding of a wider range of file types for analysis, including executables (PE, Mach-O, ELF), APKs, PDFs, Microsoft Office documents, Java Applets, and more.
- API Access: Allows programmatic submission of files and queries for verdicts.
- WF-500 Appliance Support: A WildFire subscription is required if forwarding files to an on-premise WF-500 appliance for local analysis (though cloud analysis is generally preferred for broader threat intelligence).
- Prerequisite: Requires an active Threat Prevention license.
Advanced WildFire Subscription
Advanced WildFire enhances the standard WildFire service with additional, more deeply integrated analysis capabilities, particularly targeting evasive malware.
- Intelligent Run-time Memory Analysis: This cloud-based engine complements existing sandboxing by deeply inspecting the memory of a running process. It's designed to detect highly evasive malware that might employ techniques to evade traditional sandbox detection (e.g., sleep timers, environment checks, fileless malware).
- Deeper Visibility: Provides more profound insights into malware behavior during its execution lifecycle.
- Focus on Evasion: Specifically targets threats that attempt to hide their malicious activity until they are in memory or under specific run-time conditions.
- Builds on WildFire: Requires a standard WildFire subscription as a prerequisite.
WildFire Analysis Process
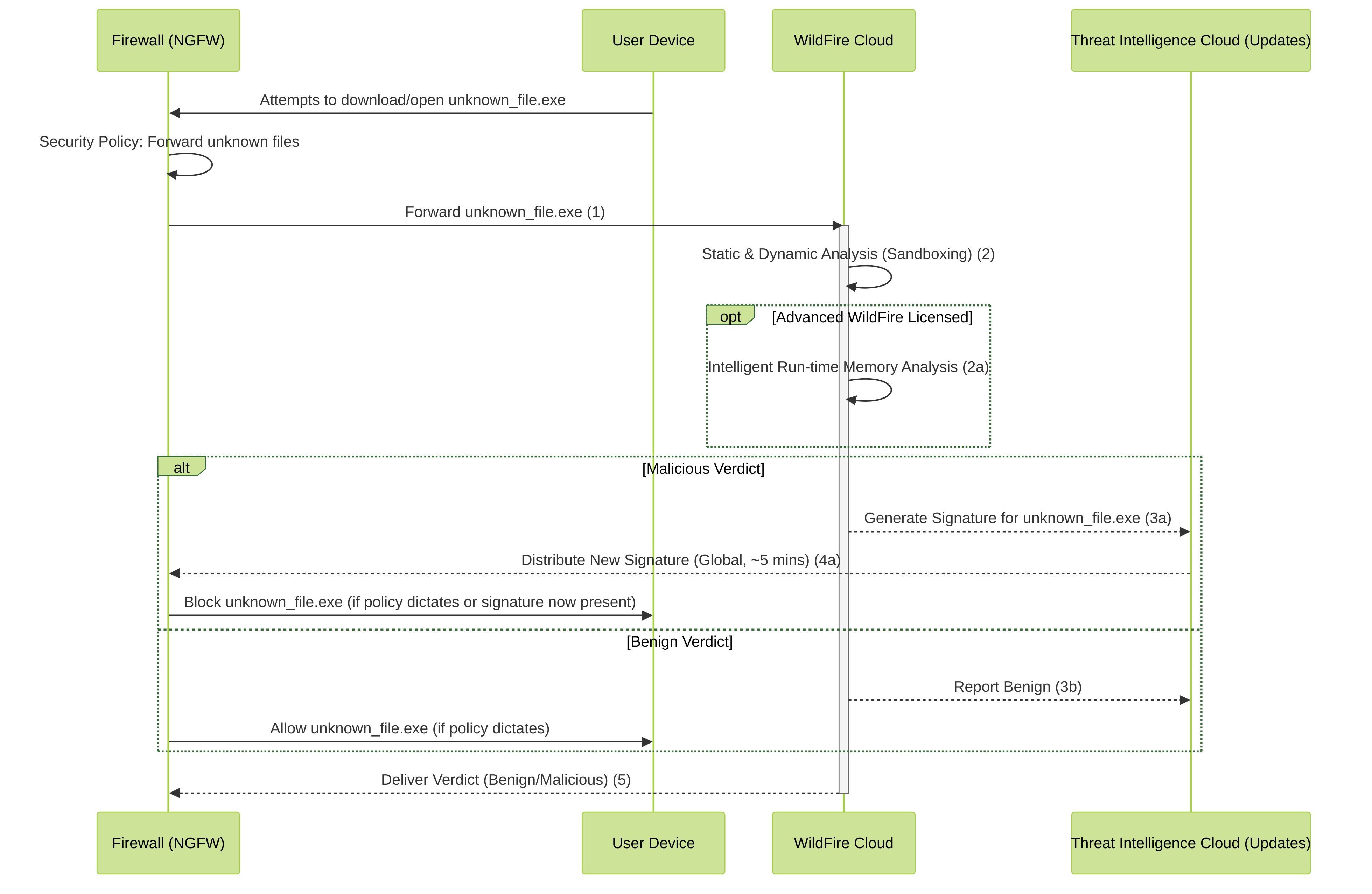
Simplified WildFire and Advanced WildFire analysis process. The firewall forwards unknown files, WildFire cloud analyzes them, and if malicious, generates signatures distributed globally.
Core Security Service: Advanced URL Filtering
Advanced URL Filtering (AUR) provides robust control over web access, leveraging the cloud-based PAN-DB for categorization and inline machine learning for real-time detection of unknown malicious sites.
Key Features
- Comprehensive URL Categorization: Uses PAN-DB, a globally distributed URL database, to categorize websites into numerous categories (e.g., Social Networking, Streaming Media, Malware, Phishing, Adult). Policies can then be set based on these categories.
- Inline Machine Learning (ML): A key differentiator. AUR uses ML directly on the firewall (for some models) and in conjunction with cloud queries to detect and block new malicious and phishing websites in real-time, even if they are not yet in the PAN-DB. This is crucial for zero-day web threats.
- Credential Phishing Prevention: Allows administrators to control where users can submit corporate credentials. It can block submissions to untrusted or unverified sites, or specific URL categories. It supports User-ID integration to identify users and their legitimate corporate domains.
- HTTP Header Insertion: Can insert custom HTTP headers for traffic going to specific URL categories, useful for integration with downstream security or monitoring tools.
- Safe Search Enforcement: Can enforce safe search settings for major search engines.
- Supersedes Legacy URL Filtering: Advanced URL Filtering is the current offering and includes all features of the older "URL Filtering (PAN-DB)" subscription, plus the advanced ML capabilities.
How it Works
URL Filtering profiles are attached to Security Policy rules. When a user attempts to access a URL:
- The firewall first checks its local cache for the URL's category.
- If not cached, it queries the PAN-DB cloud service.
- If the URL is uncategorized or potentially suspicious, the inline ML engine analyzes the web page content and other indicators in real time.
- Based on the determined category and the configured policy (allow, alert, block, continue, override), access is managed.
- For credential phishing prevention, the firewall inspects POST requests containing usernames/passwords and checks the destination against allowed categories/domains.

Decision flow for Advanced URL Filtering, highlighting the interplay of local cache, PAN-DB cloud, and inline Machine Learning.
Core Security Service: DNS Security
The DNS Security subscription leverages cloud-based analytics and threat intelligence to protect against threats using the Domain Name System (DNS) for infrastructure, such as C2, malware distribution, and phishing.
Key Features
- Malicious Domain Blocking: Identifies and blocks DNS requests to known malicious domains using a continuously updated cloud-delivered database. This database is powered by predictive analytics, machine learning, and extensive threat research.
- DNS Sinkholing: Allows redirection of DNS requests for malicious or undesirable domains to a specified sinkhole IP address. This helps identify infected hosts on the internal network attempting to contact these domains.
-
Protection Against Advanced Threats:
Effective against various attack vectors including:
- Command and Control (C2) callbacks
- Malware and ransomware distribution sites
- Phishing sites
- Domains generated by Domain Generation Algorithms (DGAs)
- Extensible Cloud Architecture: The service can rapidly incorporate new threat intelligence.
- Prerequisite: Requires an active Threat Prevention license.
How it Works
When a client on the network makes a DNS query that transits the firewall:
- The firewall intercepts the DNS query.
- It checks the requested domain against the DNS Security cloud service's intelligence.
-
If the domain is identified as malicious or matches a policy:
- The firewall can block the query, returning a synthetic response (e.g., NXDOMAIN).
- Alternatively, it can perform DNS sinkholing, returning a pre-configured IP address (the sinkhole IP) instead of the actual malicious IP. Traffic to this sinkhole IP can then be monitored.
- If the domain is benign, the query is allowed to proceed to the legitimate DNS server.
This inspection is applied via Anti-Spyware profiles, which are attached to Security Policy rules.
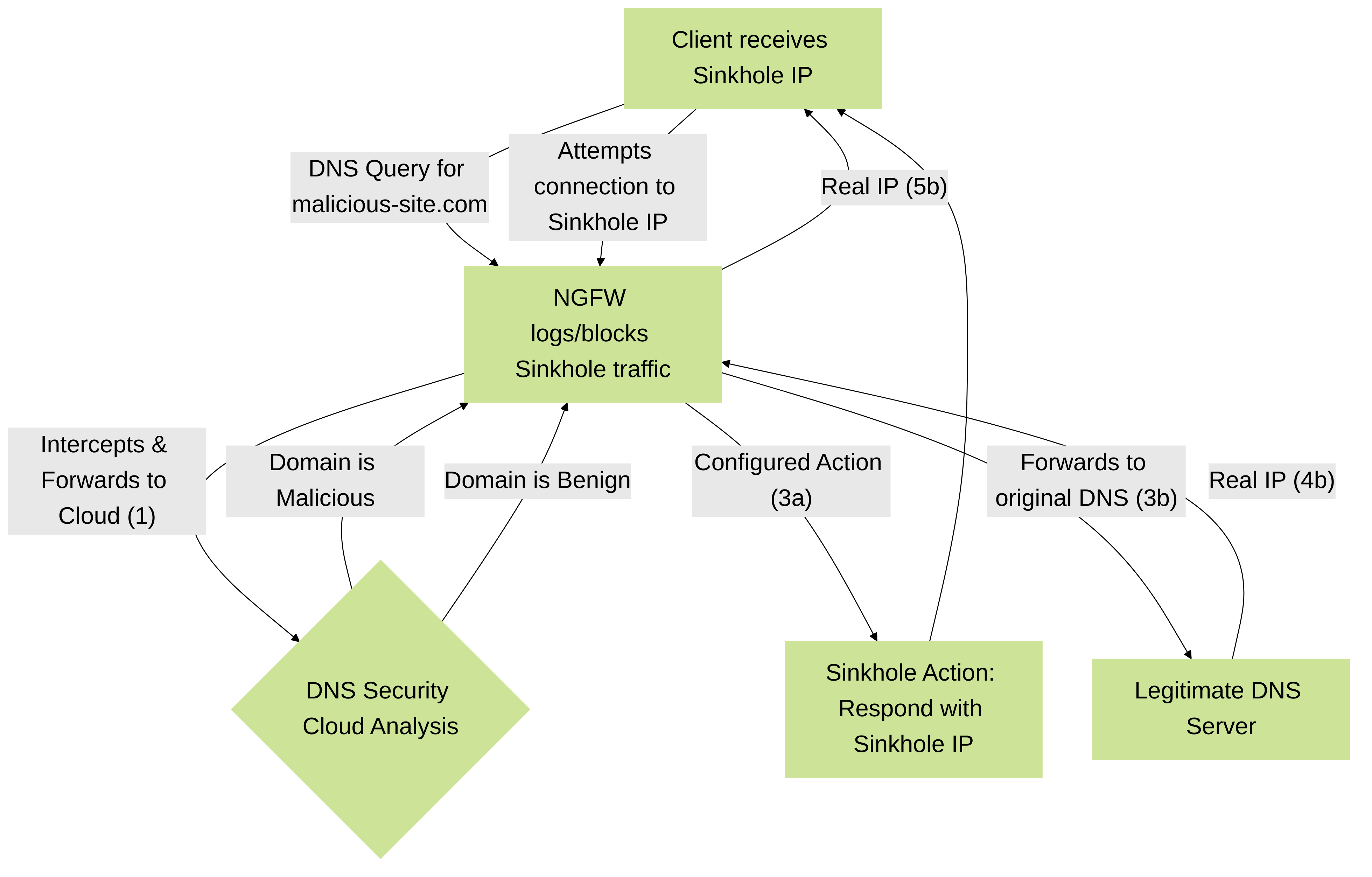
DNS Security workflow: Intercepting DNS queries, checking against cloud intelligence, and applying actions like sinkholing.
Core Security Service: Advanced Threat Prevention
Advanced Threat Prevention (ATP) is an inline, cloud-delivered security service that builds upon the standard Threat Prevention subscription. It introduces signature-less detection capabilities using machine learning directly on the firewall to block unknown and evasive command-and-control (C2) traffic and exploits in real-time.
Key Features
- Inline Deep Learning Models: Leverages custom-built deep learning models on the firewall to analyze network traffic patterns and detect malicious behavior without relying solely on traditional signatures.
- Real-time C2 Detection: Specialized in identifying and blocking unknown C2 communication attempts, even those using novel techniques or encryption. This is crucial for stopping active intrusions and data exfiltration.
- Zero-Day Exploit Prevention: Designed to identify and stop exploit attempts in real-time, even for vulnerabilities that do not yet have specific signatures. It looks for anomalous traffic patterns indicative of exploitation.
- Signature-less Detection: While it complements signature-based detection from standard Threat Prevention, its core strength is identifying threats that have no existing signature. This reduces the window of exposure to new attacks.
- Cloud-Assisted Intelligence: While detection is inline, it benefits from the broader threat landscape visibility and model training occurring in the Palo Alto Networks cloud.
- Builds on Threat Prevention: Requires the standard Threat Prevention subscription as a base.
How it Works
Advanced Threat Prevention inspects traffic inline as it passes through the firewall. It applies machine learning models that have been trained to recognize subtle indicators of malicious activity often missed by signatures alone.
- Traffic flows through the firewall and is subject to standard Threat Prevention (signatures).
- If Advanced Threat Prevention is licensed and enabled, the same traffic is also analyzed by inline ML models.
-
These models look for characteristics of:
- Evasive C2 (e.g., unusual beaconing, non-standard protocols, encrypted channels with suspicious metadata).
- Exploit kits or vulnerability exploitation attempts (e.g., specific sequences of network requests, shellcode-like patterns).
- If the ML models detect a high probability of malicious activity, ATP can block the traffic in real-time, preventing the threat from succeeding.
This capability is typically configured within the Anti-Spyware and Vulnerability Protection profiles, often by setting certain actions for "critical," "high," and "medium" severity cloud-delivered C2 and exploit detections.
Connectivity & Specialized Service: GlobalProtect
GlobalProtect provides secure remote access (VPN) for users, whether they are mobile, at home, or in branch offices. The GlobalProtect subscription unlocks advanced features for endpoint posture assessment and broader client support.
Key Features (Enabled/Enhanced by Subscription)
- Host Information Profile (HIP) Checks: This is a major feature unlocked by the subscription. HIP allows the firewall to collect information about the security posture of connecting endpoints (e.g., OS patch level, antivirus status, disk encryption, presence of specific software). Policies can then be enforced based on HIP data (e.g., grant full access only to compliant devices).
- HIP Notification and Content Updates: The subscription provides regular updates for HIP checks, including new OS versions, antivirus definitions, and other endpoint security software.
- GlobalProtect Mobile App Support: Full support for the GlobalProtect app on mobile platforms (iOS, Android).
- IPv6 Support: Enables GlobalProtect connections over IPv6.
- Clientless VPN: Provides access to specific web applications through a browser-based portal without requiring the full GlobalProtect client. Useful for contractors or unmanaged devices needing limited access.
- Enhanced Scale and Features: While basic portal/gateway functionality might work without a license on some platforms, the subscription is generally required for any production deployment relying on the features listed above and for optimal performance and scale.
Core GlobalProtect Functionality (May have limitations without license)
- Portal: Authenticates users and provides them with the appropriate GlobalProtect agent software and configuration.
- Gateway(s): Terminate VPN tunnels, enforce security policy on remote user traffic, and provide access to internal or cloud resources.
- Connection Methods: Supports various connection methods like "On-demand," "User-logon (Always On)," and "Pre-logon (Always On for device)."
A GlobalProtect Gateway license is typically required for each gateway that will utilize the advanced features. A single portal can serve multiple gateways.
For detailed setup, refer to the GlobalProtect Administrator's Guide .
Connectivity & Specialized Service: SD-WAN
The SD-WAN (Software-Defined Wide Area Network) subscription enables Palo Alto Networks firewalls to provide intelligent path selection, simplified VPN orchestration, and centralized management for distributed enterprise networks.
Key Features
- Dynamic Path Selection: Intelligently steers application traffic across multiple WAN links (e.g., MPLS, internet broadband, LTE) based on real-time path performance (latency, jitter, packet loss) and application requirements (defined in SLAs).
- Application-Aware Routing: Identifies applications using App-ID and makes path decisions tailored to the needs of each application.
- Simplified VPN Orchestration: Automates the creation and maintenance of VPN tunnels between branch firewalls and hub locations, simplifying complex mesh or hub-and-spoke topologies.
- Centralized Management via Panorama: SD-WAN configuration, monitoring, and troubleshooting are managed centrally through Panorama. Panorama is a requirement for SD-WAN.
- Zero Touch Provisioning (ZTP): Simplifies the deployment of new branch firewalls.
- Secure SD-WAN: Combines SD-WAN functionality with the NGFW's security capabilities, ensuring that all traffic, regardless of path, is inspected and secured.
- Monitoring and Reporting: Provides visibility into WAN link performance and application traffic patterns.
How it Works
Palo Alto Networks SD-WAN typically involves:
- Panorama as Controller: Panorama acts as the central SD-WAN controller and management plane. It's used to define SD-WAN policies, device configurations, and monitor the network.
- Branch and Hub Devices: Firewalls at branch locations and central hub sites are configured as part of the SD-WAN fabric. They require the SD-WAN subscription.
- Path Quality Monitoring: Devices continuously monitor the health of available WAN paths using probes.
- Policy-Based Path Selection: Based on configured application SLAs and real-time path metrics, traffic is dynamically routed over the optimal path. For example, critical VoIP traffic might be prioritized on a low-latency link, while bulk data transfer might use a higher-bandwidth internet link.
- Secure Tunnels: VPN tunnels (typically IPsec) are established between devices to secure inter-site traffic.
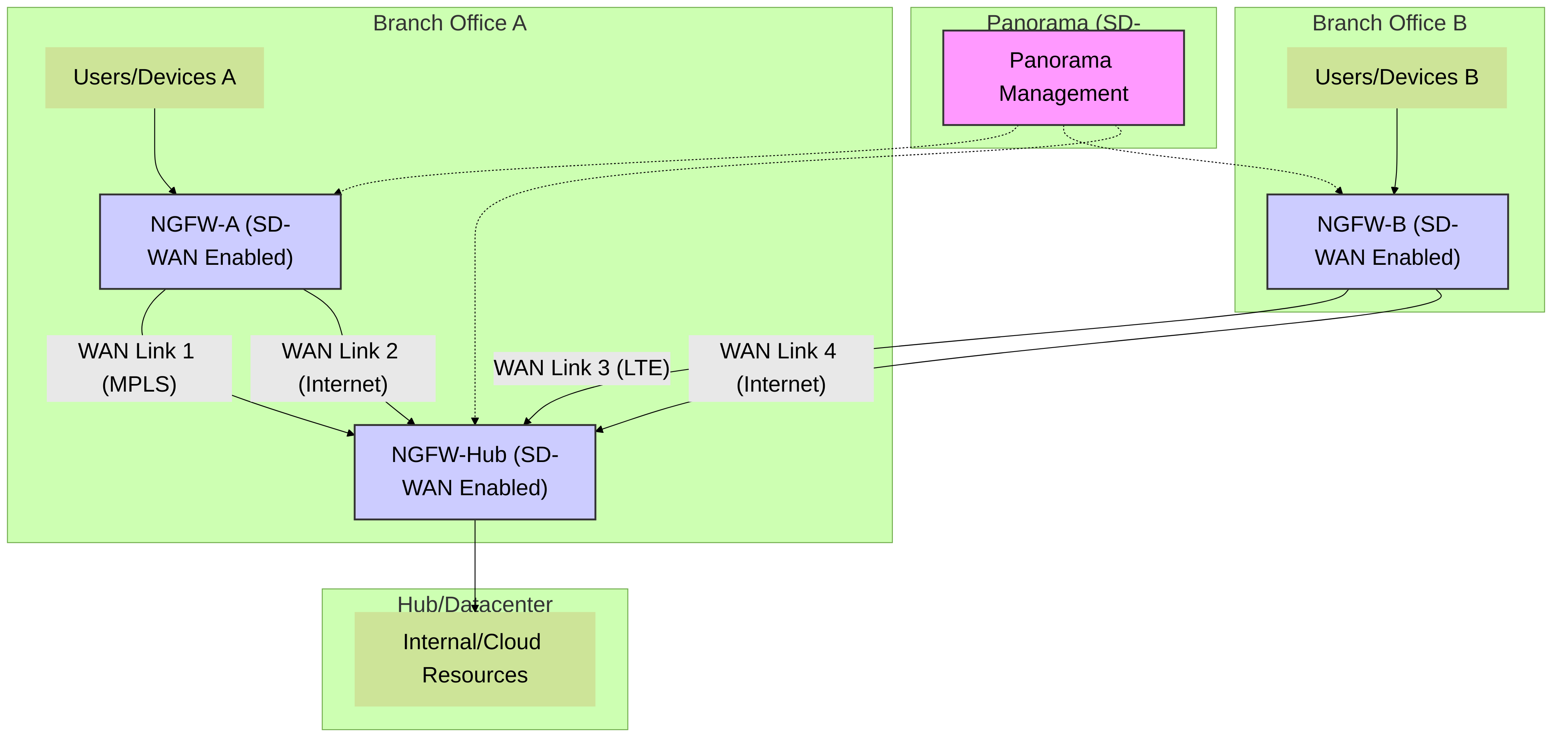
High-level Palo Alto Networks SD-WAN architecture showing Panorama managing branch and hub firewalls with multiple WAN links.
For detailed information, see the SD-WAN Administrator's Guide .
Connectivity & Specialized Service: IoT Security
The Palo Alto Networks IoT Security subscription is a cloud-delivered service designed to provide comprehensive visibility, prevention, and enforcement for Internet of Things (IoT) and Operational Technology (OT) devices.
Key Features
- Device Discovery and Classification: Uses passive network traffic analysis and machine learning to automatically discover and accurately classify all connected IoT/OT devices, even those previously unknown.
- Risk Assessment: Identifies device vulnerabilities, anomalous behaviors, and potential threats associated with discovered IoT devices. Provides a risk score for each device.
- Behavioral Anomaly Detection: Baselines normal device behavior and alerts on deviations that could indicate a compromise or malfunction.
- Policy Recommendations: Generates context-aware security policy recommendations based on device type, risk, and behavior. These recommendations can be easily translated into NGFW policies to segment and secure IoT devices.
- Threat Prevention: Leverages the NGFW's threat prevention capabilities to block known and unknown threats targeting IoT devices.
- Integration with NGFW and Strata Logging Service: IoT Security ingests metadata from NGFWs (via Strata Logging Service, formerly Cortex Data Lake) to analyze device traffic. Policy enforcement occurs on the NGFW.
- IP-Tagging and Device Attributes: Discovered device information (e.g., device type, model, OS) can be used as IP-tags or device attributes in Dynamic Address Groups (DAGs) for policy enforcement.
How it Works
- Data Collection: NGFWs forward traffic metadata (not full packet captures) from segments where IoT devices reside to the Strata Logging Service.
-
Cloud Analysis:
The IoT Security cloud service ingests this metadata and applies advanced analytics, machine learning, and Palo Alto Networks threat intelligence to:
- Discover and identify IoT devices.
- Profile their normal behavior.
- Assess their risk posture.
- Detect anomalies and threats.
- Policy Recommendation & Enforcement: The service provides insights and policy recommendations through its cloud portal. These recommendations (e.g., "Allow camera X to only communicate with NVR Y on port Z") can be used to create granular security policies on the NGFWs, often leveraging Dynamic Address Groups populated by IoT Security.
For more details, refer to the IoT Security Administrator's Guide .
Connectivity & Specialized Service: Enterprise DLP
Palo Alto Networks Enterprise Data Loss Prevention (DLP) is a cloud-delivered service that helps discover, monitor, and protect sensitive data across networks, clouds, and users.
Key Features
- Unified DLP Engine: Provides a consistent DLP engine across Palo Alto Networks products (NGFWs, Prisma Access, Prisma SaaS, Prisma Cloud).
- Comprehensive Data Discovery: Identifies sensitive data in motion (transiting the network via NGFWs or Prisma Access) and at rest (in sanctioned SaaS applications via Prisma SaaS, or cloud storage via Prisma Cloud). This study guide focuses on the NGFW integration.
- Predefined and Custom Data Patterns: Offers a library of predefined data patterns for common sensitive information types (e.g., PII, PCI, PHI, source code). Allows creation of custom patterns using keywords, regular expressions, and document properties.
- Machine Learning-Based Classification: Uses ML for accurate data classification, reducing false positives.
- Data Profiling: Scan for collective types of data using Boolean logic (e.g., detect if a document contains a credit card number AND a name AND an address).
- Policy Enforcement: Enables policies on NGFWs (and other enforcement points) to monitor, alert, or block the exfiltration of sensitive data.
- Integration with Panorama: The Enterprise DLP plugin on Panorama is used to configure DLP policies and profiles, which are then pushed to managed NGFWs.
- Incident Management: Provides reporting and analytics on DLP incidents.
How it Works (NGFW Context)
- Configuration: DLP data patterns, profiles, and policies are configured using the Enterprise DLP plugin on Panorama.
- Policy Deployment: These configurations are pushed from Panorama to the managed NGFWs.
- Traffic Inspection: NGFWs inspect traffic matching relevant security policies that have DLP profiles attached. SSL/TLS decryption is critical for inspecting encrypted traffic.
-
Data Analysis:
When traffic is inspected:
- The NGFW can perform initial matching against simpler patterns.
- For more complex analysis or confirmation, snippets or metadata might be sent to the Enterprise DLP cloud service.
- Enforcement: Based on the DLP policy, the NGFW can alert, block the data transfer, or take other configured actions if sensitive data is detected.
- Logging and Reporting: DLP events are logged on the firewall and can be forwarded to Panorama and SIEM systems.
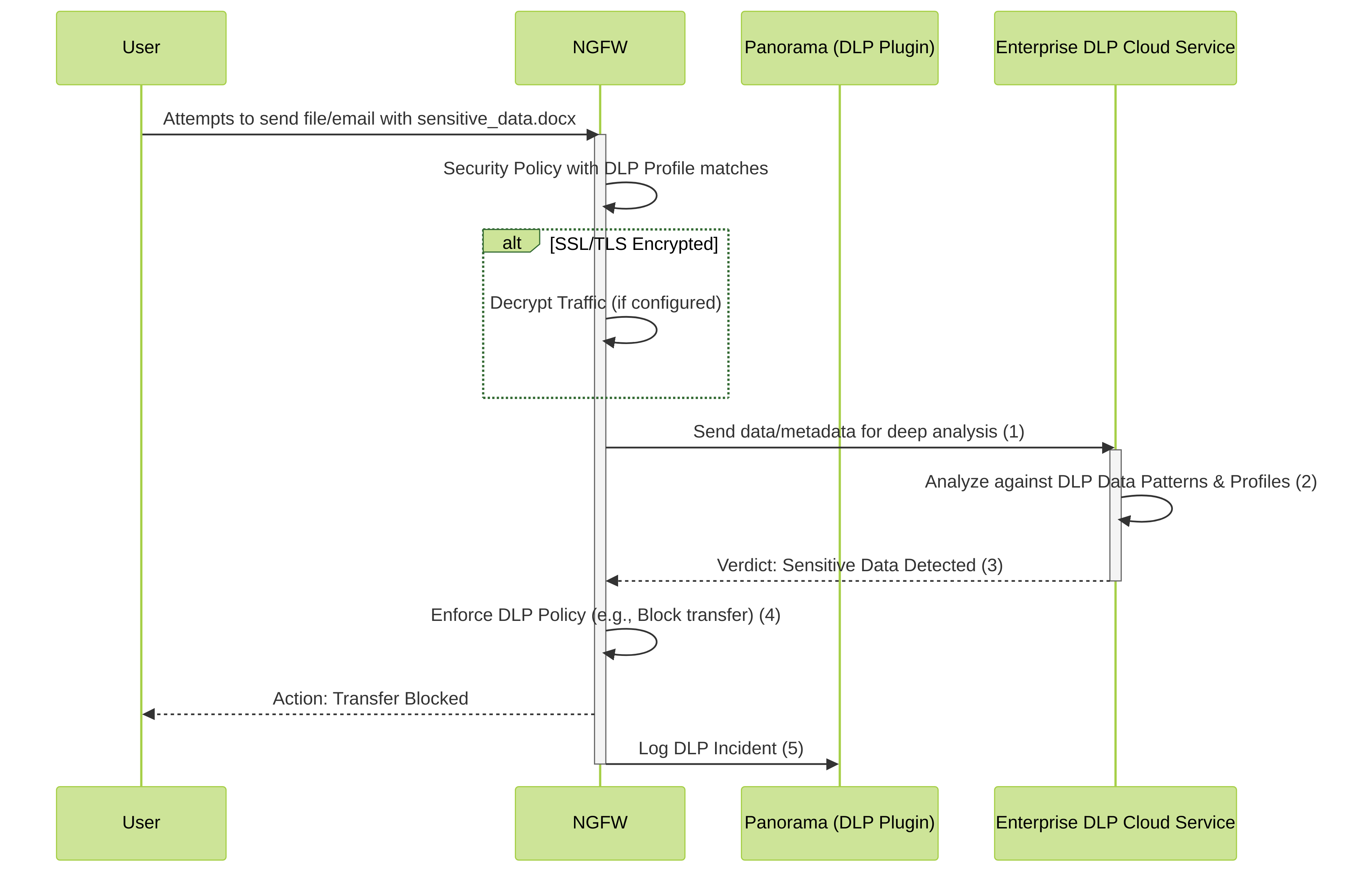
Simplified flow of data inspection with Enterprise DLP for NGFWs. Panorama manages configuration, and the DLP cloud service assists with analysis.
For more details, consult the Enterprise DLP Administration Guide .
Connectivity & Specialized Service: SaaS Security Inline
SaaS Security Inline, in conjunction with the App-ID Cloud Engine (ACE), provides enhanced visibility and granular control over Software-as-a-Service (SaaS) application usage directly on the NGFW.
Key Features
- Enhanced SaaS App Discovery: Leverages the App-ID Cloud Engine (ACE) to rapidly identify new, emerging, and evasive SaaS applications that might not be covered by standard App-ID updates. ACE is updated frequently (multiple times per day).
- Granular Control: Allows for policy enforcement not just on the SaaS application itself (e.g., Box, Slack) but also on specific functions or activities within those applications (e.g., block file uploads to personal Box accounts, allow chat but block file sharing in Slack for certain users).
- Shadow IT Discovery: Helps identify unsanctioned SaaS applications being used within the organization by analyzing traffic patterns.
- User and Usage Details: Provides insights into who is using which SaaS apps and for what purposes.
- Policy Recommendations: Can generate policy recommendations for controlling SaaS usage.
- Integration with Strata Logging Service: Requires Strata Logging Service (formerly Cortex Data Lake) to send traffic logs and metadata to the cloud for analysis by ACE and the SaaS Security service.
- Inline Enforcement: Unlike CASB solutions that might be API-based, SaaS Security Inline provides real-time, inline policy enforcement on the NGFW.
How it Works
- Traffic Forwarding: The NGFW sends relevant traffic logs and metadata (particularly for unidentified or broadly categorized web traffic) to the Strata Logging Service.
- App-ID Cloud Engine (ACE) Analysis: ACE, a cloud service, analyzes this data to identify specific SaaS applications, including new and evasive ones.
- App-ID Updates: The NGFW receives frequent updates from ACE, effectively expanding its App-ID database with these new SaaS application signatures.
-
Policy Enforcement:
With the SaaS Security Inline subscription and updated App-IDs from ACE, administrators can create granular Security Policy rules:
- Using the newly identified SaaS App-IDs.
- Specifying application functions (e.g., `slack-file-transfer`, `dropbox-upload`) if available through App-ID.
- Applying actions like allow, block, alert, or QoS.
- Visibility: The SaaS Security portal (integrated within the Palo Alto Networks hub/Cortex Gateway) provides dashboards and reports on discovered SaaS usage.
For more information, refer to the SaaS Security Inline documentation .
Operational & Platform Service: AIOps for NGFW
AIOps (Artificial Intelligence for IT Operations) for NGFW is a cloud-based service that provides proactive insights, predictive analytics, and best practice recommendations to optimize the health, performance, and security posture of Palo Alto Networks firewalls.
Key Features
- Proactive Issue Detection: Identifies potential problems, misconfigurations, and security gaps before they impact operations or lead to breaches.
- Predictive Analytics: Forecasts potential issues like resource exhaustion (CPU, memory, session capacity) based on trends.
- Best Practice Adherence: Compares firewall configurations against Palo Alto Networks best practices and security hardening guidelines, highlighting deviations.
- Remediation Recommendations: Offers actionable recommendations to address identified issues and align with best practices.
- Security Posture Insights: Helps improve overall security posture by identifying areas for improvement in policy configuration, subscription utilization, and feature adoption.
- Health and Performance Monitoring: Provides dashboards and metrics on firewall health, performance, and capacity utilization.
- Integration with Strata Logging Service: Requires firewalls to forward telemetry and logs to Strata Logging Service (Cortex Data Lake) for analysis by the AIOps service.
- Free and Premium Tiers: Offers a free tier with basic insights and a premium tier (licensed) with more advanced analytics, predictions, and longer data retention.
How it Works
- Data Collection: Firewalls (NGFWs and Panorama-managed firewalls) send telemetry data, configuration information, and logs to the Strata Logging Service.
- Cloud-Based Analysis: The AIOps cloud service processes this data using AI/ML algorithms and Palo Alto Networks expertise.
- Insight Generation: It identifies anomalies, predicts potential issues, compares configurations to best practices, and assesses security posture.
- Dashboard and Reporting: Insights, alerts, and recommendations are presented through a dedicated AIOps portal (accessible via the Palo Alto Networks hub/Cortex Gateway).
AIOps aims to reduce manual effort in troubleshooting, optimize resource utilization, and improve the overall effectiveness of the firewall deployment.
For more information on features, including the differences between Free and Premium, see the AIOps Free and Premium Features documentation .
Operational & Platform Service: Strata Logging Service
Strata Logging Service (formerly known as Cortex Data Lake) is a cloud-based, centralized log storage and aggregation solution. It's a foundational service that enables many other Palo Alto Networks cloud-delivered security services and applications.
Key Features
- Centralized Log Collection: Collects logs from Palo Alto Networks NGFWs, Prisma Access, Cortex XDR, and other sources into a single, scalable cloud repository.
- Long-Term Storage: Provides scalable and cost-effective long-term storage for security and network logs, essential for compliance, forensics, and historical analysis.
- Data Normalization: Normalizes log data from various sources into a common format, simplifying analysis and correlation.
-
Foundation for Cloud Services:
Serves as the data backbone for numerous Palo Alto Networks cloud services, including:
- Cortex XDR (for endpoint, network, and cloud data analysis)
- IoT Security
- AIOps for NGFW
- SaaS Security Inline (via App-ID Cloud Engine integration)
- Prisma Access insights
- Scalability and Performance: Designed to handle large volumes of log data from distributed environments.
- Regional Data Storage: Allows customers to choose the geographic region for log storage to help meet data sovereignty and compliance requirements.
How it Works
- Log Forwarding Configuration: Administrators configure NGFWs, Panorama, Prisma Access, etc., to forward logs to their dedicated Strata Logging Service instance in the cloud.
- Secure Data Ingestion: Logs are securely transmitted and ingested into the service.
- Storage and Indexing: Data is stored, indexed, and normalized for efficient querying and analysis.
- Data Access by Cloud Services: Other licensed Palo Alto Networks cloud services (e.g., Cortex XDR, AIOps) access the relevant log data from Strata Logging Service to perform their specialized analytics and functions.
- Direct Query (Limited): While primarily a backend for other services, some direct query capabilities may be available through tools like Cortex XSOAR or APIs for specific use cases.
For more details, refer to the Strata Logging Service (Cortex Data Lake) Getting Started Guide .
Operational & Platform Service: AutoFocus
AutoFocus is a cloud-based contextual threat intelligence service. It provides security analysts with deep insights into attack campaigns, threat actors, and malware by correlating threat data from Palo Alto Networks' global threat intelligence network, third-party sources, and an organization's own network logs.
Key Features
- Contextual Threat Intelligence: Goes beyond individual threat indicators (like a malicious IP or hash) to provide context about related campaigns, malware families, threat actors, and tactics, techniques, and procedures (TTPs).
- Correlation of Global and Local Data: Correlates threat data from Palo Alto Networks' Unit 42 threat research team, WildFire, third-party feeds, and (optionally) an organization's own firewall logs if integrated.
- Threat Actor Profiling: Provides information on known threat actors, their common targets, and modus operandi.
- Malware Family Analysis: Details on malware families, their behaviors, and variants.
- Graphical Analysis: Offers visualization tools to explore relationships between threats, campaigns, and indicators.
- Search and Pivoting: Allows analysts to search for specific indicators (IPs, domains, hashes, CVEs) and pivot to related threat intelligence.
- API Access: Enables integration with SIEM, SOAR, and other security tools for automated enrichment and response.
- Tagging System: Uses tags to categorize and search for threats based on various attributes (e.g., malware family, exploit kit, target industry).
How it's Used
Security operations teams and threat analysts typically use AutoFocus to:
- Investigate Alerts: When a firewall or other security tool generates an alert for a suspicious event, analysts can use AutoFocus to look up the indicators (e.g., IP address, file hash) and gain more context.
- Proactive Threat Hunting: Search for threats relevant to their industry or specific TTPs used by known adversaries.
- Enrich Incident Data: Augment data from SIEMs or incident response platforms with detailed threat intelligence from AutoFocus.
- Understand Attack Campaigns: Piece together disparate alerts or indicators to understand the scope and nature of a broader attack campaign.
With an active AutoFocus license, firewall logs (if forwarded to Strata Logging Service and integrated) can be correlated with AutoFocus intelligence, allowing analysts to see if global threats have been observed on their own network.
For more information, visit the AutoFocus Documentation .
Operational & Platform Service: Virtual Systems (VSYS)
Virtual Systems (VSYS) is a licensing feature that allows a single physical Palo Alto Networks firewall to be partitioned into multiple independent, logical firewall instances. Each VSYS operates as a separate firewall with its own policies, interfaces, routing tables, and administrative domains.
Key Features & Concepts
- Firewall Virtualization: Enables logical separation of network security functions on a single hardware device.
- Independent Administration: Each VSYS can have its own administrators with distinct access rights and visibility limited to their assigned VSYS.
- Resource Allocation: System resources (like sessions, security processing) can be allocated or shared among VSYS instances.
- Dedicated or Shared Interfaces: Physical interfaces can be dedicated to a single VSYS or shared among multiple VSYS instances using subinterfaces or VLANs.
-
Use Cases:
- Multi-tenancy: Service providers can offer distinct virtual firewalls to different customers.
- Departmental Separation: Large enterprises can segment networks for different departments (e.g., HR, Finance, Engineering) with separate security policies and administration.
- Network Function Consolidation: Consolidate multiple physical firewalls onto fewer, more powerful platforms.
- Lab/Test Environments: Create isolated VSYS instances for testing policies without impacting production environments.
-
Platform Dependent:
VSYS capability and the number of supported VSYS instances vary by firewall model.
- Not supported on PA-220, PA-400 Series, PA-800 Series, and most VM-Series models (some higher-end VM-Series might have limited VSYS capacity with specific licensing).
- PA-3200 Series, PA-5200 Series, PA-5450, and PA-7000 Series firewalls support VSYS.
-
Licensing:
- A base number of VSYS instances might be included by default on some high-end platforms (e.g., PA-5200, PA-7000 Series).
- To enable VSYS on platforms like the PA-3200 Series, or to increase the number of VSYS instances beyond the base capacity on other supported platforms, a Virtual Systems license must be purchased. This is typically a perpetual license for a certain number of additional VSYS.
Considerations
- Resource Management: Careful planning is needed for allocating resources (CPU, memory, sessions, security processing capacity) to each VSYS to ensure performance.
- Inter-VSYS Routing: By default, traffic between different VSYS instances on the same firewall must exit the physical firewall and re-enter (hairpinning) through an external router or switch, or by using dedicated inter-VSYS Layer 3 interfaces if configured.
- Shared Services: Some services (like Panorama management, User-ID agent connectivity) might be configured globally or per-VSYS depending on the deployment.
For detailed guidance, refer to the Virtual Systems Administrator's Guide (select your PAN-OS version).
Operational & Platform Service: Subscription Reference Table
The following table, sourced from Palo Alto Networks documentation, provides a summary of many available subscriptions. For the most current and detailed information, always refer to the official Palo Alto Networks documentation website.
|
Palo Alto Networks Firewall Subscriptions Summary |
|
|
IoT Security |
Discovers and classifies IoT devices using AI/ML, provides risk assessment, and generates policy recommendations for NGFW enforcement. Requires Strata Logging Service. |
|
SD-WAN |
Enables intelligent dynamic path selection, simplified VPN orchestration, and centralized configuration/monitoring for WAN links. Requires Panorama. |
|
Threat Prevention |
Provides IPS, Antivirus, Anti-Spyware (C2 protection), vulnerability protection, built-in EDLs, and basic WildFire access. Foundational for many other security services. |
|
Advanced Threat Prevention |
Inline, signature-less detection using ML on the firewall to block unknown C2 and exploits in real-time. Builds on standard Threat Prevention. |
|
DNS Security |
Blocks access to malicious domains using predictive analytics and ML-driven threat intelligence; provides DNS sinkholing. Requires Threat Prevention. |
|
Advanced URL Filtering |
Controls web access using PAN-DB categories, prevents credential phishing, and uses inline ML to detect and block unknown malicious/phishing sites in real-time. Supersedes legacy URL Filtering. |
|
WildFire |
Cloud-based advanced malware analysis (sandboxing) for unknown threats. Provides fast (~5 min) signature updates, supports more file types, and API access. Requires Threat Prevention. |
|
Advanced WildFire |
Adds Intelligent Run-time Memory Analysis to WildFire, enhancing detection of highly evasive malware. Requires WildFire subscription. |
|
AutoFocus |
Cloud-based contextual threat intelligence service. Provides graphical analysis of firewall logs (if integrated) and correlates with global threat data. |
|
Strata Logging Service (Cortex Data Lake) |
Cloud-based centralized log storage and aggregation. Required or recommended for Cortex XDR, IoT Security, AIOps, Prisma Access, etc. |
|
GlobalProtect |
Subscription enables advanced VPN features: Host Information Profile (HIP) checks, mobile app support, IPv6, Clientless VPN. Required per gateway. |
|
Virtual Systems |
Perpetual license to enable multiple logical firewall instances (VSYS) on supported hardware platforms, or increase VSYS capacity beyond base. |
|
Enterprise DLP |
Cloud-delivered service for discovering and protecting sensitive data using predefined/custom patterns and ML. Requires Panorama DLP plugin for NGFW integration. |
|
SaaS Security Inline |
Provides visibility and granular control over SaaS apps using App-ID Cloud Engine (ACE) for rapid identification. Requires Strata Logging Service. |
|
AIOps for NGFW |
Cloud service providing proactive insights, predictive analytics, and best practice recommendations for NGFW health, performance, and configuration. Comes in Free and Premium (licensed) tiers. Requires Strata Logging Service. |
General References & Further Reading
These links provide broader overviews and details on managing subscriptions: