Palo Alto Networks: Authentication Policy - Deep Dive and PCNSE Preparation
Introduction to Authentication Policy in PAN-OS
Palo Alto Networks' Authentication Policy, a core feature within PAN-OS, provides a robust mechanism for verifying user identity before granting access to network resources, applications, or specific URL categories. It acts as a critical enforcement point, ensuring that only legitimate, authenticated users can proceed, aligning with Zero Trust security principles. Authentication Policy is evaluated before Security Policy, adding an essential layer of identity-based access control. When a user's traffic matches an Authentication Policy rule requiring authentication, the firewall prompts the user for credentials via an Authentication Portal (often referred to as Captive Portal) or other configured methods. Successful authentication can then populate the User-ID mapping table, allowing for user and group-based Security Policies.
Core Concepts of Palo Alto Networks Authentication Policy
To effectively implement and manage Authentication Policies, a clear understanding of its components and workflow is essential.
- Purpose: To explicitly verify user identity for traffic that would otherwise be unknown or to enforce a higher level of assurance (e.g., MFA) before allowing access to sensitive resources. It's a key tool for implementing identity-aware security.
- Evaluation Order: Authentication Policy rules are evaluated top-down. The first rule that matches the traffic criteria is applied. If no rule matches, authentication is not required by this policy type (though other mechanisms like GlobalProtect might still enforce authentication).
- Relationship with User-ID: Successful authentication via an Authentication Policy is a primary method for the firewall to learn IP-to-user mappings. These mappings are then utilized by User-ID enabled Security Policies, App-ID, Content-ID, and logging/reporting features to provide visibility and control based on user identity rather than just IP addresses.
Key Components of Authentication Policy Configuration
Several objects and settings come together to form a functional Authentication Policy:
-
Authentication Policy Rule:
This is the central piece where you define matching criteria for traffic that will trigger an authentication challenge.
-
Matching Criteria:
- Name: A descriptive name for the rule.
- Source Zone: The zone from which the traffic originates.
- Destination Zone: The zone to which the traffic is destined.
- Source Address: Source IP address(es) or address group(s).
- Destination Address: Destination IP address(es) or address group(s).
- Source User: Crucial for defining who this rule applies to. Options include `any`, `known-user`, `unknown`, or specific users/groups (if already known through other User-ID methods, this can be used for step-up authentication). Typically, for initial authentication, `unknown` or `any` is used.
- Service/Application: The L4 service (e.g., `tcp/80`, `tcp/443`) or specific App-ID application that triggers the policy. Using `application-default` is common.
- URL Category: (Requires a valid URL filtering license) Can trigger authentication for specific web categories.
- HIP Profile: (Requires GlobalProtect license) Can use Host Information Profile data as a match criterion.
- Action: Typically `Authenticate`. This action then invokes an Authentication Enforcement Object. Other actions like `Deny` or `Allow` are less common for this policy type's primary purpose.
-
Matching Criteria:
-
Authentication Enforcement Object:
This object, configured under `Objects > Authentication`, defines
how
the authentication is performed.
- Name: A descriptive name.
-
Authentication Method:
- Web Form: The most common method, redirecting users to an Authentication Portal (Captive Portal) page to enter credentials. This uses an associated Authentication Profile.
- Client Certificate: Prompts the user's browser for a client certificate for authentication. Requires a Certificate Profile.
- Authentication Profile: Specifies the backend authentication service (e.g., LDAP, RADIUS, SAML, Kerberos, TACACS+, Local User Database) to validate the user's credentials. This is linked when using the "Web Form" method.
- Authentication Message: A custom message displayed on the Authentication Portal.
- Redirect Host (Optional): A specific hostname or IP address to redirect users to for authentication. Useful if the firewall itself isn't directly reachable by the user's initial DNS query for the portal.
- Idle Timer / Session Timer: Defines how long an authentication mapping remains valid.
-
Authentication Profile:
Configured under `Device > Authentication Profile`. This object defines the settings for connecting to an authentication server.
- Type: LDAP, RADIUS, Kerberos, SAML, TACACS+, Local User Database.
- Server Profile: For server-based types (LDAP, RADIUS, etc.), this links to a Server Profile object containing server IP/hostname, port, and protocol-specific settings.
- Login Attribute / User Domain / Group Mapping Settings: Specific to the authentication type, e.g., `sAMAccountName` for LDAP.
- Allow List: Specifies which user groups are permitted to authenticate through this profile.
- Authentication Sequence: Configured under `Device > Authentication Sequence`. Allows you to chain multiple Authentication Profiles. The firewall tries them in order until one succeeds or all fail. This provides redundancy or allows for different user populations to authenticate against different backends.
-
Authentication Portal / Captive Portal:
This is the web interface presented to users for credential submission. It's managed under `Device > Authentication Portal`.
- Settings: You can customize the appearance, timers (idle, timer), and redirect behavior.
- Certificate: A server certificate for the firewall interface serving the portal is essential for HTTPS access to avoid browser warnings.
- Response Pages: Allows customization of various pages (login, success, failure, etc.).
Authentication Policy Workflow
The general workflow when traffic hits an Authentication Policy rule is as follows:
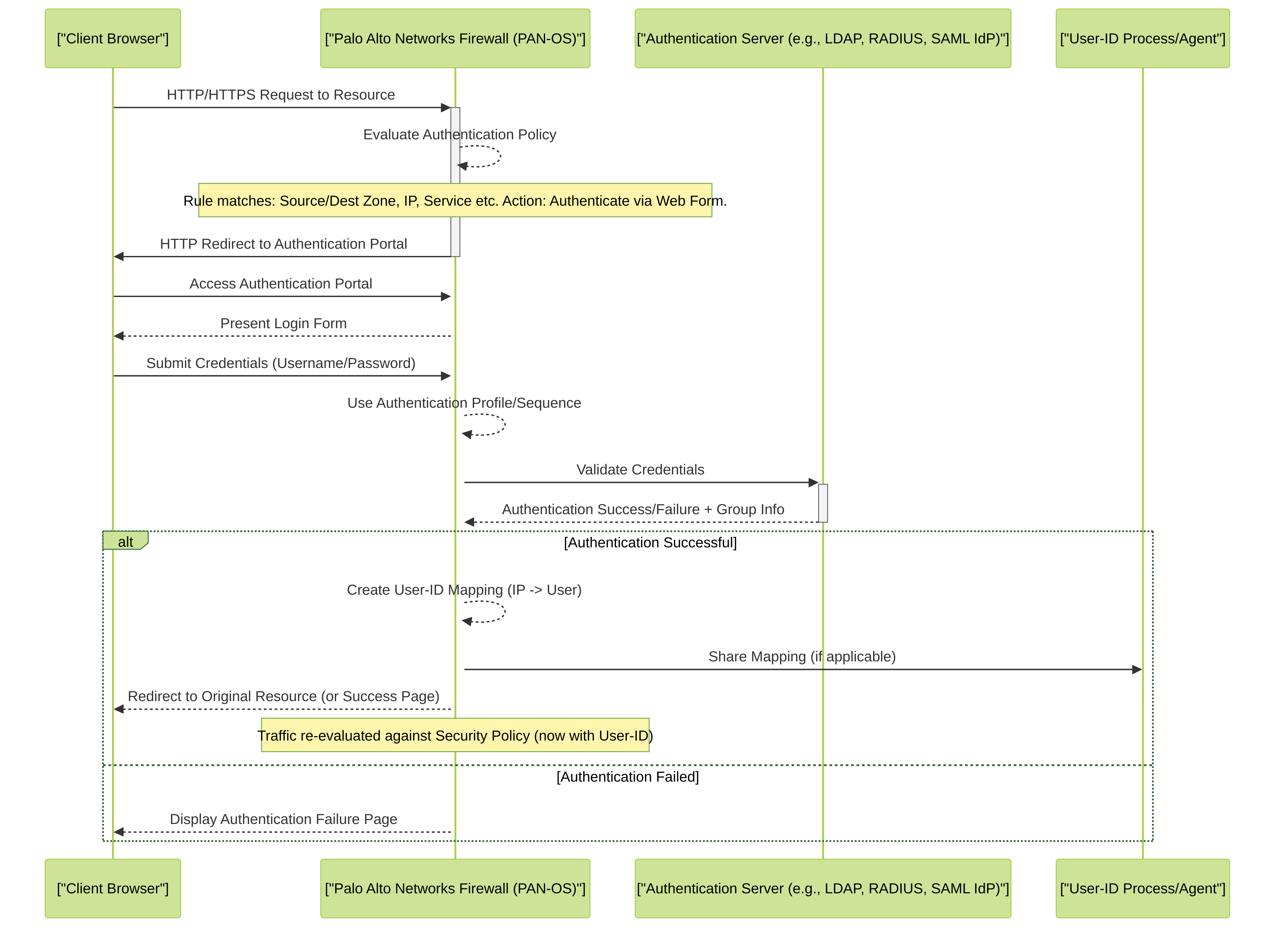
High-level workflow of a user being authenticated via an Authentication Policy rule using a web form and an external authentication server.
Configuring Authentication Policy in PAN-OS
Configuration involves several steps, typically performed via the PAN-OS web interface (Panorama or firewall GUI) or through the CLI/API for automation.
GUI Navigation and Key Steps:
-
Define Authentication Server Profiles (if using external servers):
- Navigate to `Device > Server Profiles`.
- Add LDAP, RADIUS, TACACS+, SAML Identity Provider profiles.
-
Example (LDAP): Server IP, port, Base DN, Bind DN, password, SSL/TLS settings.
# Example target for LDAP Server Profile Name: AD-LDAP-Server Type: ldap Server: ldap-server.corp.paloaltonetworks.com Port: 389 (or 636 for LDAPS) Base: dc=corp,dc=paloaltonetworks,dc=com Bind DN: cn=ldapbind,ou=ServiceAccounts,dc=corp,dc=paloaltonetworks,dc=com
-
Define Authentication Profile(s):
- Navigate to `Device > Authentication Profile`.
- Create a new profile, select the type (LDAP, RADIUS, SAML, etc.), and link it to the appropriate Server Profile created in step 1 (or use the Local User Database).
- Configure method-specific settings (e.g., login attribute for LDAP, SAML IdP certificate).
-
Specify an "Allow List" of users/groups permitted to authenticate.
PCNSE/PCNSA Exam Note (Palo Alto Networks): The 'Allow List' in an Authentication Profile is critical. If a user successfully authenticates against the backend server but is not on the Allow List, the firewall will still deny authentication.
-
(Optional) Define Authentication Sequence(s):
- Navigate to `Device > Authentication Sequence`.
- Create a sequence and add Authentication Profiles in the desired order of preference.
- Define an "Allow List" for the sequence itself.
-
Configure Authentication Portal Settings:
- Navigate to `Device > Authentication Portal`.
- Select the interface and certificate for the portal.
- Set Idle Timer and Timer values. These determine how long a user mapping derived from Captive Portal remains active.
-
Customize response pages if needed.
Gotcha! (Palo Alto Networks): Ensure the interface serving the Authentication Portal has an IP address reachable by users and that a valid SSL/TLS certificate is configured if using HTTPS to avoid browser security warnings, which can deter users.
-
Define Authentication Enforcement Object(s):
- Navigate to `Objects > Authentication`.
- Add an Authentication Enforcement object.
- Specify the Authentication Method (e.g., Web Form), the Authentication Profile or Sequence, and any custom messages.
-
Create Authentication Policy Rule(s):
- Navigate to `Policies > Authentication`.
- Click "Add" to create a new rule.
- General Tab: Name the rule.
- Source Tab: Define Source Zone(s) and Source Address(es). For Source User, typically `unknown` or `any` is used for initial challenges.
- Destination Tab: Define Destination Zone(s) and Destination Address(es).
- Service/URL Category Tab: Define the Service (e.g., `service-http`, `service-https`, `any`) or URL Category (if licensed) that triggers authentication.
-
Actions Tab:
- Set Action to `Authenticate`.
- Select the Authentication Enforcement object created in step 5.
-
Ensure the rule is placed correctly in the policy list for proper evaluation.
# Example conceptual PAN-OS CLI structure for an Authentication Policy rule # (Actual configuration is more complex and usually done via GUI/XML API) configure edit Vsys_Name vsys1 # or your specific vsys edit rulebase authentication edit Rule_Name "Auth_for_Internet_Unknown_Users" set from any set to any set source any set destination any set source-user unknown # Key part for initial auth set service any set action authenticate enforcement "Web-Form-Corporate-Auth" # Links to Auth Enforcement Object top # or before/after specific rule exit exit - Commit Changes: Commit the configuration to the firewall.
Expanded Use Cases for Palo Alto Networks Authentication Policy
1. Protecting Sensitive Data Center Resources
By placing Authentication Policy rules in front of access to critical internal resources (e.g., financial systems, development servers, databases), organizations can ensure that only authenticated users can attempt to connect.
- Scenario: Users from the 'Corporate-LAN' zone attempting to access servers in the 'Data-Center' zone over specific applications like SSH or RDP must authenticate.
-
Implementation:
- Source Zone: Corporate-LAN
- Destination Zone: Data-Center
- Destination Address: Address group of sensitive servers.
- Service: `service-ssh`, `service-rdp`, or custom application objects.
- Source User: `unknown` (to capture users not yet identified) or `any` (to re-authenticate if needed).
- Action: `Authenticate` using an Authentication Enforcement object linked to an LDAP or Kerberos profile.
- Benefit: Prevents unverified users/devices from even attempting to exploit vulnerabilities on critical servers. User-ID mappings created are then used in Security Policies for granular access control based on AD groups (e.g., 'Finance-Users' group for financial systems).
2. Enforcing Multi-Factor Authentication (MFA)
Authentication Policy is a key enabler for MFA within the Palo Alto Networks ecosystem, particularly for web-based access or step-up authentication scenarios.
-
Integration Methods:
- SAML 2.0: The firewall acts as a SAML Service Provider (SP). The Authentication Profile is configured for SAML, pointing to an external Identity Provider (IdP) like Okta, Azure AD, Duo. The IdP handles the primary authentication and the MFA challenge. After successful MFA, the IdP sends a SAML assertion back to the firewall.
- RADIUS: The firewall's Authentication Profile is configured for RADIUS. The RADIUS server (e.g., Windows NPS, FreeRADIUS) is configured to proxy requests to an MFA provider (e.g., Duo Authentication Proxy, RSA SecurID). The user enters their password, and the MFA provider then typically sends a push notification or requests a one-time password (OTP).
- Scenario: Require MFA for all users accessing a specific internal web application or for administrative access to certain network segments.
-
Implementation:
- Create an Authentication Profile (SAML or RADIUS type) configured for your MFA provider.
- Create an Authentication Enforcement object using this MFA-enabled Authentication Profile.
- Create an Authentication Policy rule matching traffic to the sensitive application/resource, using the MFA Authentication Enforcement object.
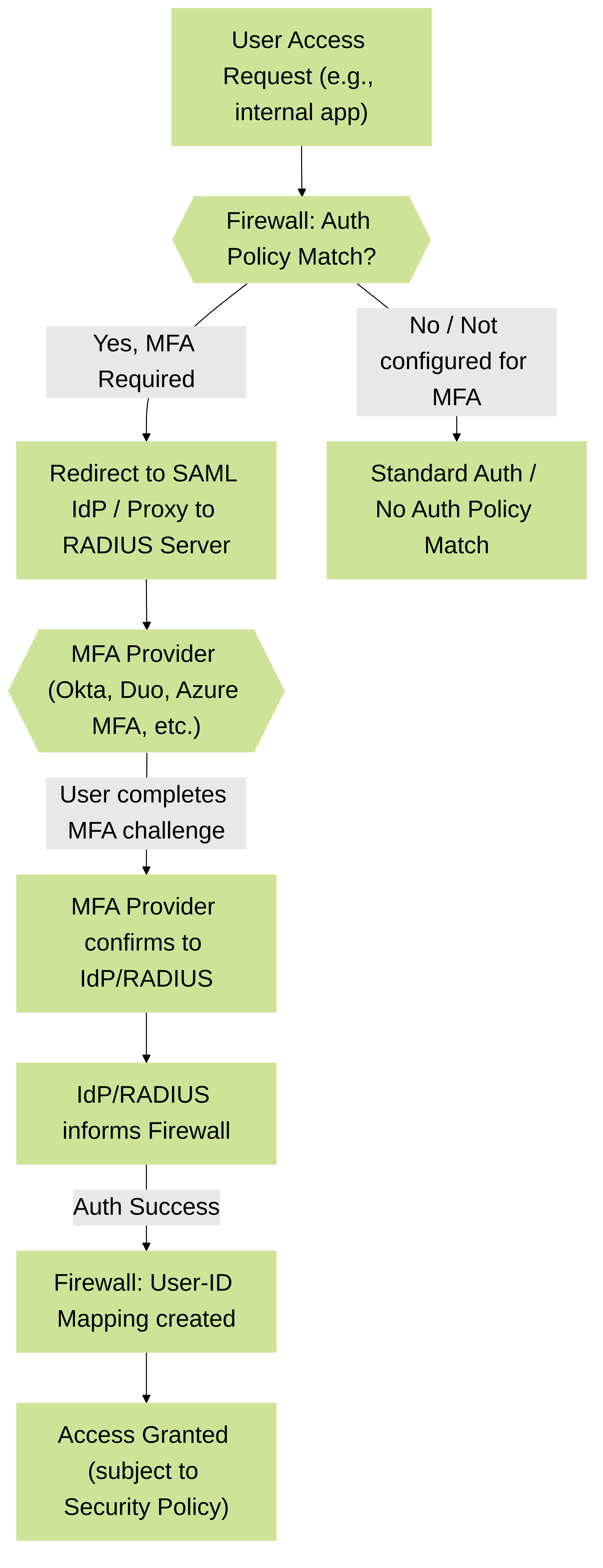
Conceptual flow of MFA enforcement using Authentication Policy integrated with an external MFA provider.
3. Controlling Guest and Third-Party Access
Authentication Policy can be used to provide controlled network access for guests, contractors, or partners.
- Scenario: Guests in a 'Guest-WiFi' zone need to authenticate before accessing the internet. Contractors need to authenticate before accessing specific project servers.
-
Implementation:
-
Guests:
- Authentication Policy rule for Source Zone 'Guest-WiFi', Destination Zone 'Internet', Service 'any'.
- Action: `Authenticate` using an Authentication Enforcement object linked to a Local User Database profile (for simple voucher-based access) or a dedicated guest portal solution integrated via RADIUS/SAML.
- Often, a simpler Authentication Portal page is used for guests.
-
Contractors:
- Dedicated Authentication Profile, possibly pointing to a separate AD domain/OU or a Local User Database.
- Authentication Policy rules specific to contractor source IPs or zones, targeting only the resources they are authorized to access.
- Can be combined with Security Policies that reference contractor-specific user groups.
-
Guests:
- Benefit: Segregates and controls access for non-employees, provides an audit trail, and helps enforce time-bound access if user accounts are managed accordingly.
4. Granular Access Based on User Groups and Services/Applications
By leveraging User-ID information (which Authentication Policy helps populate), you can create highly granular access controls.
- Scenario: Only users in the 'Engineering' Active Directory group are allowed to access development tools (identified by App-ID), and they must authenticate first if their User-ID mapping is unknown or has expired.
-
Implementation:
-
Authentication Policy:
- Source Zone: Corporate-LAN, Source User: `unknown` (or `any` for re-auth).
- Application: `github`, `svn`, `jenkins` (or custom App-IDs for internal tools).
- Action: `Authenticate` using a standard corporate Authentication Profile (e.g., LDAP).
-
Security Policy (evaluated
after
successful authentication):
- Source Zone: Corporate-LAN, Source User: 'corp\Engineering' (AD group).
- Application: `github`, `svn`, `jenkins`.
- Action: `Allow`.
-
Authentication Policy:
- Benefit: Ensures that resource access is strictly tied to verified user identity and group membership, adhering to the principle of least privilege.
5. Step-Up Authentication for Sensitive Operations
Even if a user is already known to the firewall (e.g., via GlobalProtect or a previous Captive Portal authentication), you can enforce re-authentication for access to highly sensitive applications or data.
- Scenario: A user is browsing the internet (known user). When they attempt to access the HR portal, they must re-authenticate, potentially with MFA.
-
Implementation:
-
Authentication Policy rule:
- Source User: `known-user` (or `any`, or specific user groups).
- Destination: HR Portal IP/URL.
- Application/Service: HTTP/HTTPS to HR Portal.
- Action: `Authenticate` using an Authentication Enforcement object that specifies a strong authentication method (e.g., SAML with MFA).
- The "Timeout" settings on the Authentication Portal and the "Idle Timer / Session Timer" on the Authentication Enforcement object play a role in how frequently users might be re-challenged if they are already known. Forcing re-authentication for `known-user` makes it explicit.
-
Authentication Policy rule:
Integration with Other Palo Alto Networks Features
- User-ID: Authentication Policy is a key method for populating User-ID mappings. Once a user authenticates, their IP address is mapped to their username, enabling user-based Security Policies, logging, and reporting. Other User-ID sources include User-ID Agents (monitoring Active Directory, Exchange, eDirectory), GlobalProtect, Syslog, and the XML API.
- Security Policy: User-ID information gathered via Authentication Policy allows Security Policies to be defined based on `Source User` (e.g., `corp\john.doe` or `corp\finance-group`) instead of just IP addresses. This is fundamental to Palo Alto Networks' identity-driven security model.
- App-ID and Content-ID: With User-ID, App-ID (application identification) and Content-ID (threat prevention, URL filtering, file blocking) can also be applied on a per-user or per-group basis, providing granular control and visibility.
- Logging and Reporting: Authentication events (successes, failures) are logged in the Authentication Log. These logs are crucial for troubleshooting and auditing. The ACC (Application Command Center) and reporting tools can provide insights into user activity and authentication trends.
- GlobalProtect: While GlobalProtect has its own authentication mechanisms for remote users, Authentication Policy can be used for users already on the internal network or for step-up authentication scenarios even for GlobalProtect users accessing specific resources. They are generally complementary.
Palo Alto Networks Best Practices for Authentication Policy
- Be Specific: Use specific source/destination zones, addresses, and services/applications in your Authentication Policy rules rather than `any`/`any` where possible to limit the scope and impact.
- Leverage User Groups: In conjunction with Security Policies, use directory (e.g., Active Directory) groups for fine-grained access control once users are authenticated.
- Implement MFA: For access to sensitive resources or for privileged users, always integrate MFA using SAML or RADIUS via Authentication Profiles.
-
Regularly Review Logs:
Monitor Authentication Logs for failures, anomalies, or patterns that might indicate misconfiguration or security issues.
# PAN-OS CLI command to view recent authentication logs > show log authentication direction equal backward - Use Authentication Sequences: For redundancy if you have multiple authentication servers (e.g., primary and backup domain controllers).
- Customize Authentication Portal: Provide clear instructions and branding on the Authentication Portal for a better user experience and to reduce helpdesk calls. Ensure it uses HTTPS with a valid certificate.
- Consider Timers: Carefully configure Authentication Portal timers (Idle Timeout, Timer) and Authentication Enforcement timers to balance security with user convenience. Shorter timers increase security but may lead to more frequent re-authentication prompts.
- Rule Order: Pay close attention to the order of Authentication Policy rules, as they are processed top-down. More specific rules should generally precede more general ones.
Troubleshooting Common Authentication Policy Issues
When Authentication Policy isn't behaving as expected, consider these Palo Alto Networks-specific troubleshooting steps:
| Symptom | Potential Palo Alto Networks Cause | Troubleshooting Steps (PAN-OS) |
|---|---|---|
| Users not prompted for authentication |
- No matching Authentication Policy rule.
- Rule is shadowed by a preceding rule. - Incorrect zone, address, or service specified in the rule. - Traffic not hitting the firewall or interface configured for Authentication Portal. - User already authenticated and mapping is still valid. |
- Verify rule order and matching criteria (GUI: `Policies > Authentication`).
- Check session browser (`Monitor > Session Browser`) to see if traffic is hitting the firewall and what policy it matches. - Use `show counter global filter aspect authd` and `show counter global filter delta yes aspect authd` to see if authd counters are incrementing. - Check `show user ip-user-mapping ip |
| Authentication Portal page not loading or shows certificate error |
- Incorrect interface configured for Authentication Portal (`Device > Authentication Portal`).
- No valid SSL/TLS certificate assigned to the portal (for HTTPS). - DNS resolution issue for the portal redirect hostname. - Client browser blocking pop-ups or JavaScript (less common for primary page load). - Firewall management interface not enabled for HTTP/HTTPS service. |
- Verify Authentication Portal settings (`Device > Authentication Portal`).
- Ensure a valid certificate is imported and assigned. - Check Interface Management Profile on the interface serving the portal; it must allow "Response Pages" or "User-ID Agent" (depending on method). - Test DNS resolution from client. |
| Authentication fails with correct credentials |
- Incorrect Authentication Profile settings (server IP, port, Bind DN/password for LDAP, shared secret for RADIUS).
- Communication issue between firewall and authentication server (routing, firewall policies on intermediate devices). - User not in "Allow List" of Authentication Profile or Sequence. - Account locked out or disabled in the backend directory. - Incorrect login attribute (e.g., `sAMAccountName` vs `userPrincipalName` for LDAP). |
- Test Authentication Profile: `Device > Authentication Profile > [Select Profile] > Test Authentication Profile`.
- Check Authentication Logs (`Monitor > Logs > Authentication`) for detailed error messages. - Use CLI: `test authentication authentication-profile - `debug authenticationd on debug` (use with caution in production, generates verbose logs). - Packet captures on firewall for traffic to/from authentication server. |
| User authenticates, but User-ID mapping not created/updated |
- User-ID not enabled on the relevant zones.
- Issues with the User-ID agent process (`userid`) on the firewall. - Group mapping issues (if relying on group membership from auth server). |
- Verify User-ID enabled on zones: `Network > Zones > [Zone Name] > Enable User Identification`.
- Check `show user ip-user-mapping all` or `show user user-id-agent state all` (if agent is involved). - Review User-ID logs: `Monitor > Logs > User-ID`. - Ensure group mapping is correctly configured in Authentication Profile or `Device > User Identification > Group Mapping Settings`. |
| MFA challenges not occurring |
- SAML IdP or RADIUS server not correctly configured for MFA.
- Authentication Profile not using the correct SAML/RADIUS server configured for MFA. - Firewall not properly configured as SAML SP, or RADIUS client configuration mismatch. |
- Verify MFA configuration on the IdP/RADIUS server and MFA provider side.
- Double-check SAML IdP Profile or RADIUS Server Profile on PAN-OS. - Authentication Logs may show if the primary auth succeeded but MFA step was expected by the server. |
Mermaid Diagrams: Visualizing Authentication Policy Concepts
1. Authentication Policy Evaluation Logic
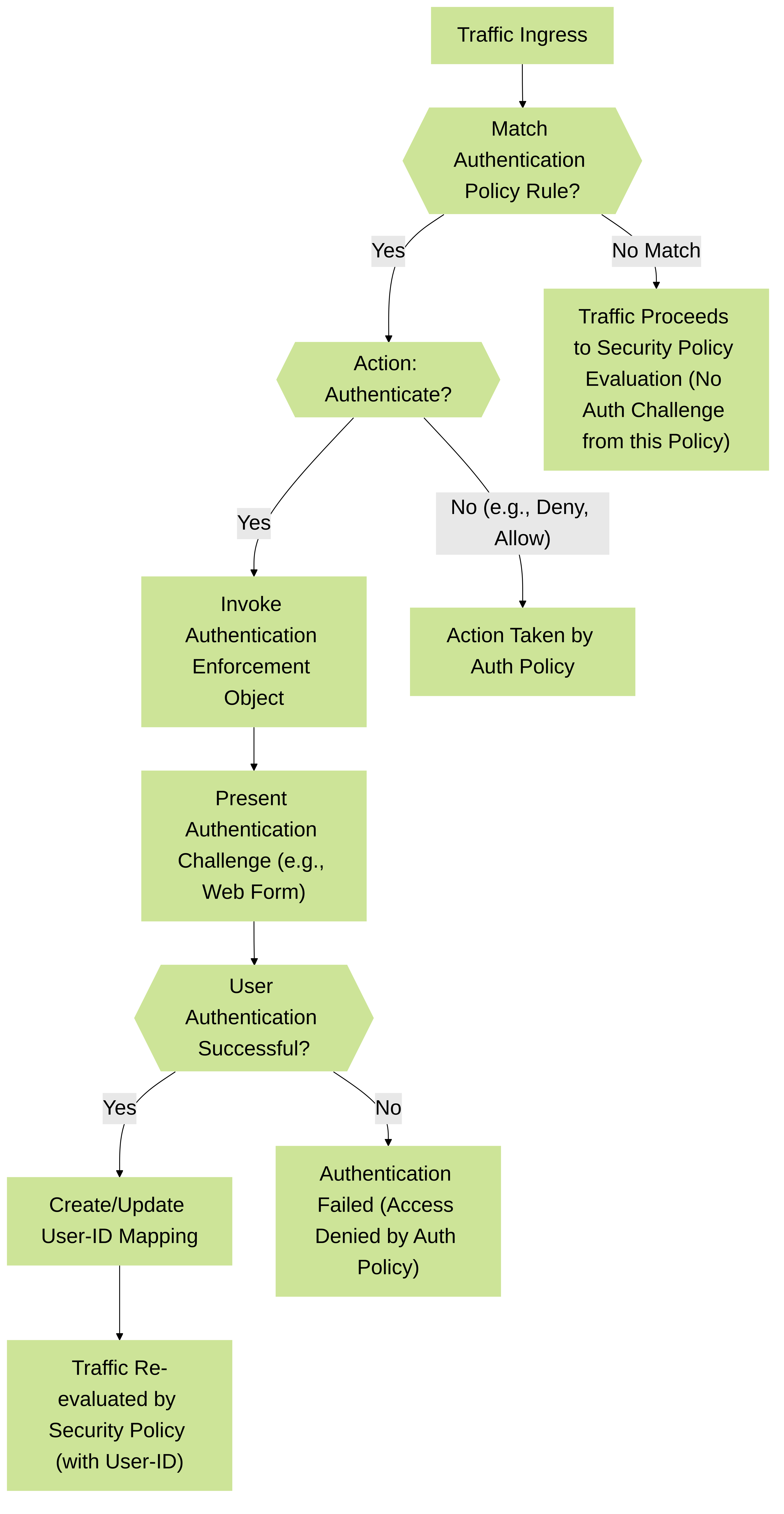
Decision tree illustrating the Palo Alto Networks Authentication Policy evaluation flow when new traffic arrives at the firewall.
2. Components of an Authentication Challenge
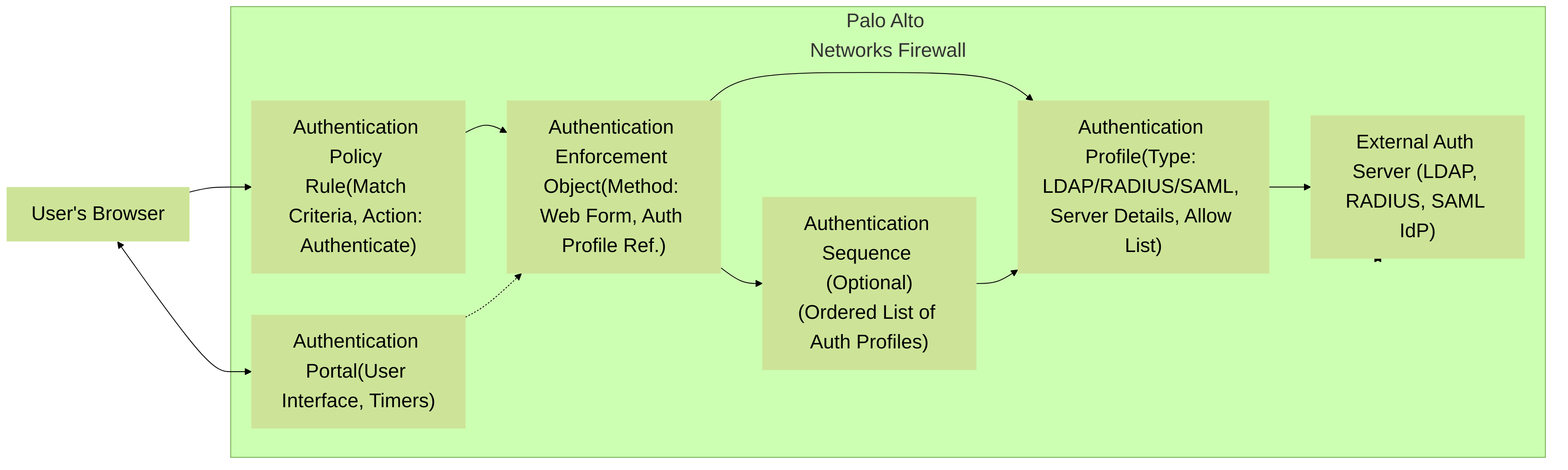
Key Palo Alto Networks objects involved in an Authentication Policy challenge and their relationships. The Authentication Policy Rule triggers the Authentication Enforcement object, which uses an Authentication Profile (or Sequence) to validate credentials against an authentication server, often presenting an Authentication Portal to the user.
3. Simplified Packet Flow with Authentication Policy
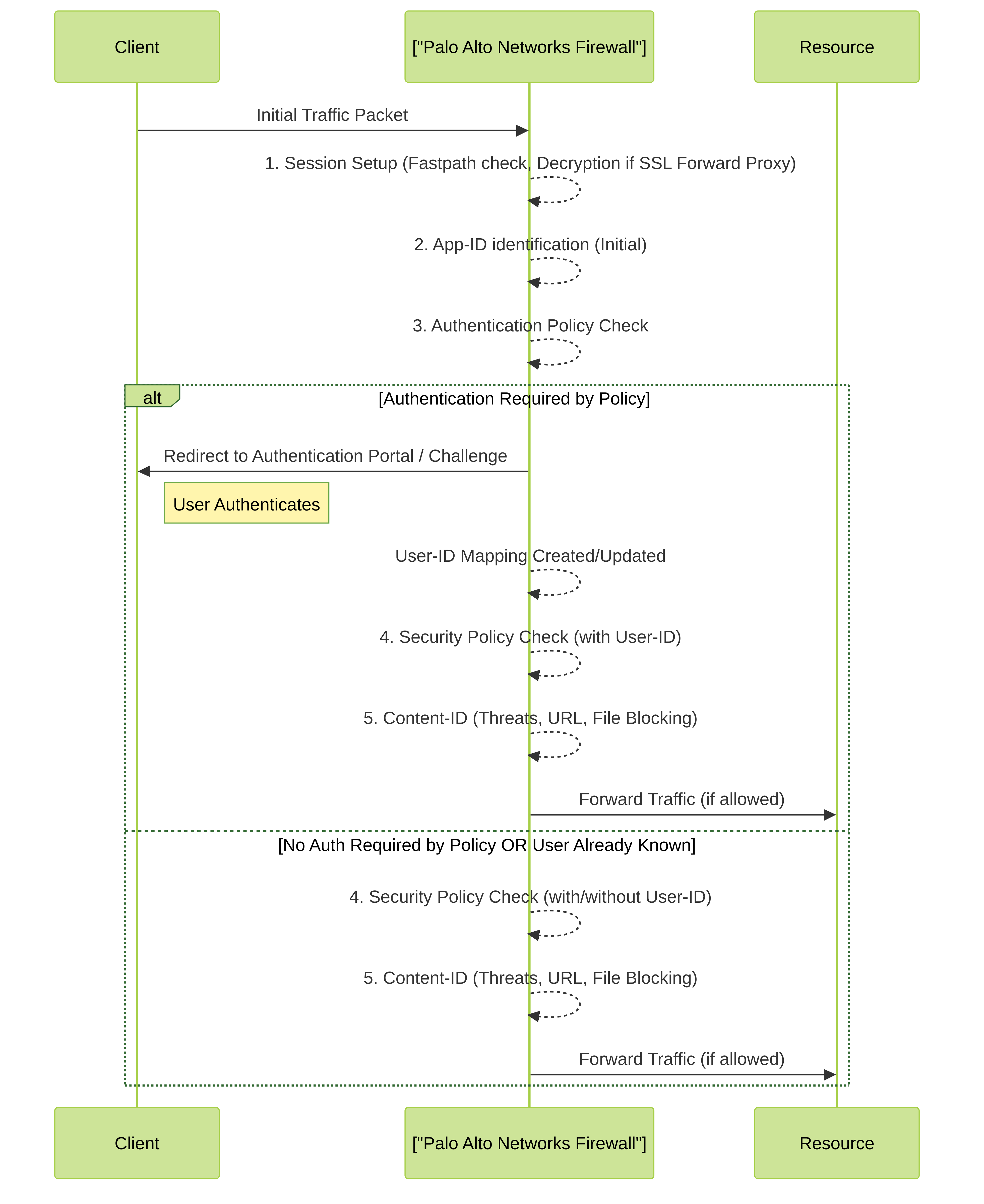
Simplified packet flow within a Palo Alto Networks firewall highlighting the stage where Authentication Policy is evaluated, relative to Security Policy and other processing stages. Successful authentication can provide User-ID context for subsequent Security Policy evaluation.
Note: The original base HTML sequence diagram remains relevant for the basic user interaction workflow.