Palo Alto Networks Decryption: Mastering Visibility, Risks, and Implications for PCNSE
Enabling SSL/TLS decryption on Palo Alto Networks Next-Generation Firewalls (NGFWs) is paramount for comprehensive security. Without it, critical security services like App-ID™, Content-ID™, Threat Prevention, and WildFire® malware analysis operate with limited visibility into a significant portion of modern network traffic. However, unlocking this visibility introduces several technical, operational, and compliance considerations that network security professionals must meticulously manage. This guide delves into the risks and implications of enabling decryption exclusively within the Palo Alto Networks ecosystem, providing practical insights and PCNSE-relevant details.
Core Palo Alto Networks Decryption Methods
Before diving into risks, it's essential to understand the primary decryption methods available in PAN-OS:
- SSL Forward Proxy: Decrypts outbound SSL/TLS traffic initiated by internal users accessing external resources (e.g., websites, SaaS applications). The firewall acts as a "man-in-the-middle" (MITM), re-signing server certificates with a Forward Trust certificate deployed on client endpoints.
- SSL Inbound Inspection: Decrypts inbound SSL/TLS traffic destined for internal servers (e.g., web servers, application servers). This requires importing the server's certificate and private key onto the Palo Alto Networks firewall.
- SSH Proxy: Decrypts and inspects SSHv2 traffic, enabling visibility into SSH commands and file transfers.
- SSL Decryption Broker: Allows the Palo Alto Networks firewall to decrypt traffic once and then forward copies of the decrypted traffic to multiple security inspection tools (e.g., data loss prevention systems). This is an advanced use case, often for specialized security chains.
Each method has unique configuration requirements and implications, which will be explored in the context of the risks discussed below.
1. Privacy Concerns and Data Handling in Palo Alto Networks Environments
Decrypting traffic inherently means inspecting its contents, which can include sensitive personal, financial, or proprietary information. Organizations must navigate these privacy concerns with care, leveraging Palo Alto Networks features to balance security with privacy obligations.
Palo Alto Networks Mechanisms for Privacy-Aware Decryption:
-
Decryption Exclusions:
PAN-OS provides robust mechanisms to exclude specific traffic from decryption based on various criteria:
-
URL Category:
Exclude categories like "financial-services," "health-and-medicine," or custom URL categories containing sensitive internal sites.
GUI Path (PAN-OS): Objects > Decryption > Decryption Profile > SSL Decryption > SSL Exclusion. - Application: Exclude specific applications identified by App-ID if they are known to handle highly sensitive data or break with decryption (e.g., some banking apps).
- Source/Destination IP Addresses or FQDNs: Exclude traffic to/from specific sensitive servers.
- Service/Port: Exclude specific ports if needed, though URL Category and Application are generally preferred.
-
URL Category:
Exclude categories like "financial-services," "health-and-medicine," or custom URL categories containing sensitive internal sites.
-
Data Filtering Profiles:
Applied
after
decryption, Data Filtering profiles can detect and block specific patterns (e.g., credit card numbers, social security numbers, custom patterns) within the decrypted traffic flow. This acts as a secondary control if sensitive traffic is decrypted.
GUI Path (PAN-OS): Objects > Security Profiles > Data Filtering. - Role-Based Access Control (RBAC): PAN-OS and Panorama allow administrators to define granular roles, limiting who can configure decryption policies, access decryption logs, or view potentially sensitive packet captures. This is crucial for maintaining separation of duties and protecting privacy.
- Logging and Anonymization: While decryption logs are vital for troubleshooting and incident response, consider log retention policies and potential anonymization features if available or integrated with external SIEMs, especially for user-identifiable information. PAN-OS logs decrypted session details, including URLs visited and threats found.
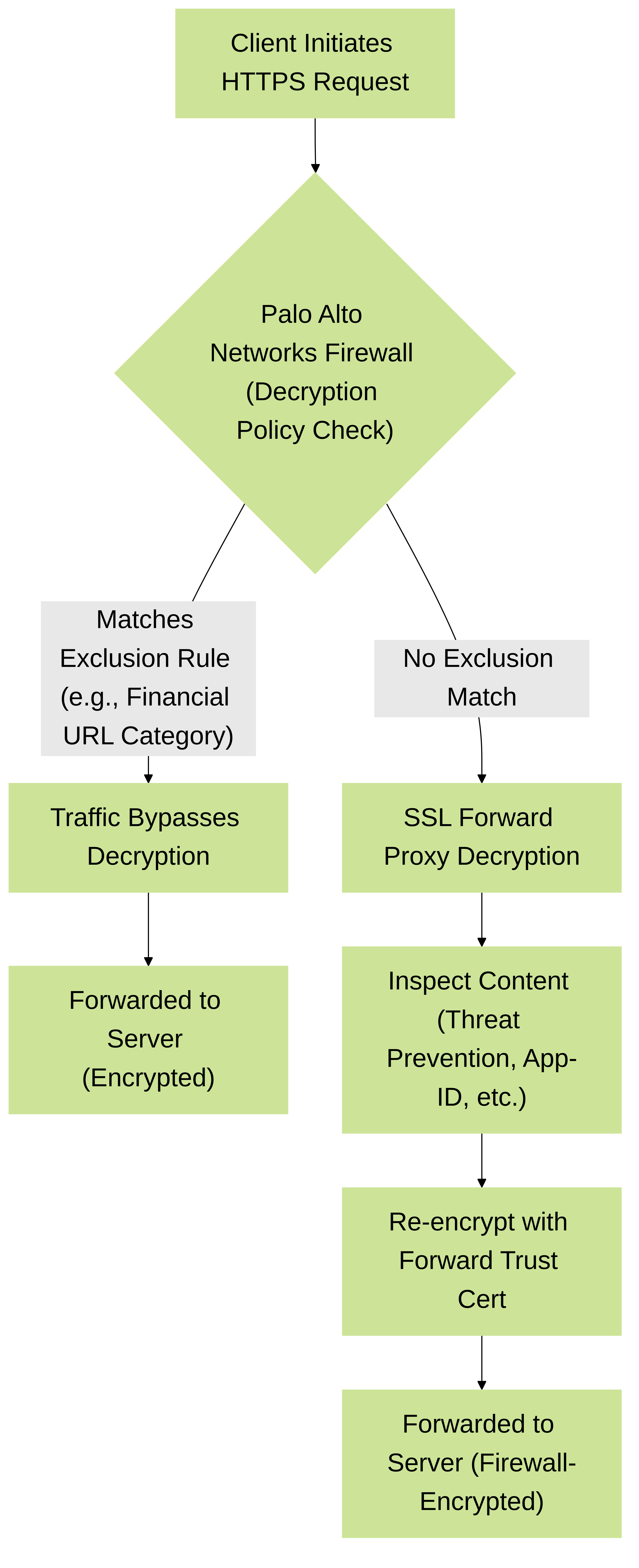
Diagram illustrating the Palo Alto Networks SSL Forward Proxy decision process, highlighting how decryption exclusions for privacy (e.g., financial sites) bypass the decryption engine.
Engage with legal and HR departments to define what constitutes sensitive information within your organization and ensure decryption practices align with corporate policies and legal mandates.
2. Performance Impact of Decryption on Palo Alto Networks Firewalls
Decryption is a computationally intensive process. The cryptographic operations (key exchange, symmetric encryption/decryption) consume significant CPU resources on the firewall's dataplane. Improper sizing or unoptimized decryption policies can lead to performance degradation, increased latency, and reduced overall throughput.
Palo Alto Networks Specific Performance Considerations:
-
Firewall Sizing:
- Consult Palo Alto Networks datasheets for your specific PA-Series, VM-Series, or Prisma Access deployment. Key metrics include "SSL Decryption Throughput," "SSL Decryption Sessions/Sec," and "SSL Decryption Concurrent Sessions." [Source: PA-Series Datasheets]
- These datasheet numbers are often based on ideal conditions and specific cipher suites (e.g., RSA-2048 with AES-256). Real-world performance may vary based on your traffic mix.
- Factor in expected growth in encrypted traffic and decryption adoption.
-
Cipher Suite Impact:
- Elliptic Curve Cryptography (ECC) ciphers are generally more efficient than RSA ciphers for equivalent security strength. PAN-OS allows administrators to control preferred cipher suites in Decryption Profiles.
-
PAN-OS supports a wide range of modern cipher suites. You can view and configure these in:
GUI Path (PAN-OS): Objects > Decryption > Decryption Profile > SSL Protocol Settings > Min/Max Version, Cipher Suites.
- Hardware Acceleration: Many PA-Series firewalls include dedicated hardware for accelerating cryptographic operations. This significantly improves decryption performance. For example, higher-end PA-Series models (e.g., PA-5400 Series, PA-7000 Series) have more powerful crypto acceleration.
- Decryption Mirroring: If using the decryption mirror feature (to send a copy of decrypted traffic to a third-party device), this adds load to the firewall as it has to re-encrypt the mirrored traffic.
- Selective Decryption: Do not attempt to decrypt all traffic. Strategically choose what to decrypt. Start with high-risk URL categories (e.g., unknown, malware, phishing) and gradually expand. Exclude low-risk, high-volume traffic if performance is a concern (e.g., trusted software update services after initial vetting).
Monitoring Performance on PAN-OS:
- Dashboard & ACC (Application Command Center): Monitor CPU utilization, session count, and throughput. The ACC can provide insights into decrypted vs. non-decrypted traffic.
-
CLI Commands:
show session info // General session statistics show system resources // Overall system resource utilization (follow with 'top' or 'mp-top', 'dp-top') debug dataplane pool statistics // Detailed buffer and resource usage on dataplanes show counter global filter aspect ssl // SSL-specific counters, including errors and successes show running resource-monitor // Real-time resource usage graphs
The following table provides a conceptual overview of how different factors can affect decryption performance. Actual impact varies greatly by model and traffic characteristics.
| Factor | Potential Impact on Performance | Palo Alto Networks Mitigation/Consideration |
|---|---|---|
| Firewall Model (CPU/Crypto Hardware) | Major: Determines baseline capacity | Select appropriate model based on sizing guides and expected load. |
| Percentage of Traffic Decrypted | Major: More decrypted traffic = more load | Implement selective decryption policies. Phased rollout. |
| Cipher Suites Used (e.g., RSA vs. ECC) | Moderate: ECC generally more efficient | Configure preferred ciphers in Decryption Profile. PAN-OS generally optimizes. |
| Session Rate (New SSL Sessions/Sec) | High: Key exchange is CPU intensive | Ensure firewall's SSL sessions/sec capacity is not exceeded. |
| Average Session Duration | Moderate: Longer sessions distribute initial handshake cost | Less directly controllable, but influences overall resource use. |
| Number of Decryption Policies/Exclusions | Minor: Policy lookup is generally efficient | Keep policies organized, but focus on traffic volume for performance. |
3. Legal and Compliance Implications with Palo Alto Networks Decryption
Many industries and regions have strict regulations regarding data privacy and inspection. Decrypting traffic, especially if it contains financial (PCI-DSS), healthcare (HIPAA), or personally identifiable information (GDPR, CCPA), requires careful consideration of these legal frameworks.
Palo Alto Networks Features for Aiding Compliance:
-
Granular Decryption Exclusions:
As discussed under Privacy, using URL categories (e.g., "financial-services," "health-and-medicine"), application filters, and custom URL lists is the primary method to prevent decryption of regulated data.
GUI Path (Panorama): Panorama > Objects > Decryption Profile > SSL Decryption > SSL Exclusion. - Geo-IP Based Policies (Indirect): While not a direct decryption exclusion, you can use source/destination region objects in security policies that feed into decryption policies to limit inspection of traffic from/to certain jurisdictions, if required.
-
Audit Logging:
PAN-OS and Panorama maintain detailed audit logs of all configuration changes, including modifications to decryption policies and profiles. These logs are essential for demonstrating compliance and for internal change control.
Access: Monitor > Logs > Configuration (in PAN-OS/Panorama). -
Documented Decryption Strategy:
Maintain a formal document outlining your organization's decryption strategy. This should include:
- The purpose of decryption.
- Scope of traffic to be decrypted.
- Scope of traffic explicitly excluded (and why).
- How user privacy is protected.
- Roles and responsibilities for managing decryption.
- Approval from relevant stakeholders (legal, HR, management).
Regularly review and update your decryption policies and exclusion lists to align with changes in regulations, business applications, and evolving privacy standards.
4. Technical Limitations and Troubleshooting in Palo Alto Networks Decryption
Despite the advanced capabilities of Palo Alto Networks NGFWs, certain technical challenges can prevent successful decryption or break application functionality.
-
Certificate Pinning (HTTP Public Key Pinning - HPKP):
- How it works: Some applications and websites embed (pin) the public keys of their legitimate SSL/TLS certificates (or their issuing CAs) directly into the application or browser. If the certificate presented during the TLS handshake (like the firewall's Forward Trust re-signed certificate) doesn't match one of the pinned keys, the application will refuse to connect, breaking functionality.
-
Palo Alto Networks Approach:
PAN-OS cannot bypass true certificate pinning. The solution is to identify applications/sites using pinning and add them to a decryption exclusion list.
Common Examples: Dropbox client, some Microsoft services (e.g., OneDrive sync client initial setup), many mobile applications. - Identifying Pinned Connections: Decryption logs (Monitor > Logs > Decryption) may show errors like "Policy action 'decrypt' SSL error:ERR_SSL_DECRYPTION_FAILURE_PINNED_CERT". The CLI command `show counter global filter aspect ssl | match pinned` can also indicate detected pinned certificates.
-
Unsupported Cipher Suites or TLS Versions:
- While PAN-OS supports a broad range of modern ciphers and TLS versions (up to TLS 1.3), there might be edge cases with very new, deprecated, or proprietary ciphers/protocols that the firewall cannot negotiate.
-
Configuration:
Decryption Profiles allow setting minimum and maximum TLS versions and selecting supported cipher suites.
GUI Path (PAN-OS): Objects > Decryption > Decryption Profile > SSL Protocol Settings. - Troubleshooting: Decryption logs will typically indicate handshake failures or unsupported parameter errors. Packet captures can reveal the specific ciphers being negotiated.
-
Client Certificate Authentication (Mutual Authentication):
- When a server requires the client to present its own SSL certificate for authentication, SSL Forward Proxy decryption can interfere. The firewall, acting as the client to the server, doesn't possess the user's private key to complete this mutual authentication.
- Palo Alto Networks Recommendation: Exclude sites or applications requiring client certificate authentication from SSL Forward Proxy decryption.
-
Applications with Hardcoded Certificates or Non-Standard TLS Implementations:
- Similar to pinning, some poorly designed or older applications might hardcode specific CA certificates or use non-standard TLS handshakes that break when intercepted.
- Solution: Identify via App-ID and exclude from decryption.
-
QUIC Protocol (HTTP/3):
- QUIC, often used by Google services and other applications, runs over UDP and encrypts its transport headers, bypassing traditional TCP-based SSL/TLS inspection.
-
Palo Alto Networks Options:
- Block QUIC: Create a security policy to deny the "quic" application. This forces applications to fall back to TCP/TLS, which can then be decrypted.
- Allow QUIC: If QUIC traffic is allowed, it will not be decrypted by SSL Forward Proxy. Palo Alto Networks continues to enhance its capabilities; always check the latest PAN-OS release notes for updates on QUIC inspection.
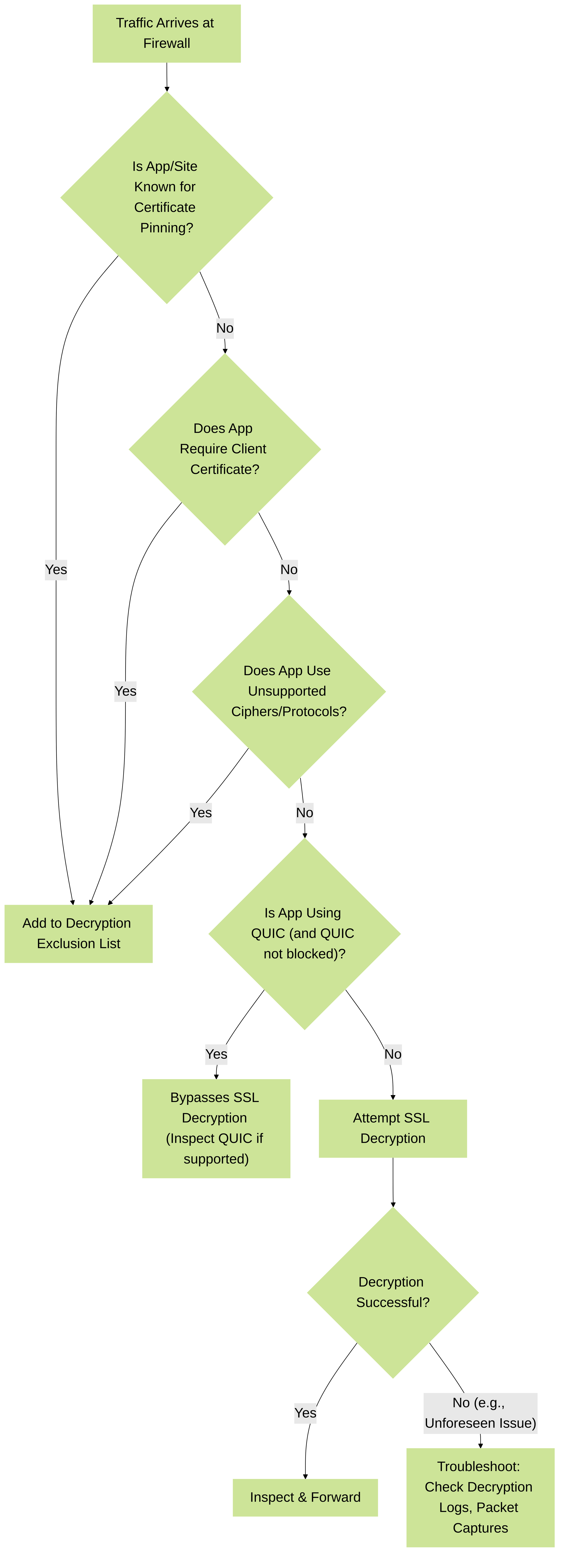
Decision tree illustrating common technical reasons for excluding traffic from Palo Alto Networks SSL decryption or for decryption failure troubleshooting.
Palo Alto Networks Troubleshooting Tools for Decryption:
- Decryption Logs: Monitor > Logs > Decryption . Provides details on decrypted sessions, errors, and reasons for non-decryption. Filter by "Action: decrypt" and look for sessions with "Error" status.
-
CLI Commands:
test ssl-decryption server-name <fqdn> // Simulates a handshake to a server show counter global filter aspect ssl // Key SSL processing counters show counter global filter delta yes aspect ssl // Shows changes in SSL counters debug dataplane packet-diag set filter match session <session_id> // For deep packet inspection debug dataplane packet-diag set filter on // Enable packet diagnostics debug dataplane packet-diag show setting // View current filter - Packet Captures (PCAPs): Configure on the firewall (Monitor > Packet Capture) to capture traffic pre-decryption (on client-side interface) and post-decryption (on server-side interface, if traffic is routed) to analyze the TLS handshake and identify issues.
5. User Experience Considerations with Palo Alto Networks Decryption
If not implemented carefully, decryption can negatively impact user experience, leading to helpdesk calls and reduced productivity.
-
Certificate Errors in Browsers/Applications:
- Cause: This is the most common issue. If the Palo Alto Networks Forward Trust certificate (used by SSL Forward Proxy to re-sign server certificates) is not installed in the trusted root CA store of client devices, users will see "Untrusted CA" or similar certificate warnings.
-
Palo Alto Networks Solution:
-
Generate/Import a Forward Trust Certificate:
This can be a self-signed certificate generated on the firewall or, preferably, an intermediate CA certificate signed by an existing internal (enterprise) Root CA. Using an intermediate CA signed by an already trusted internal Root CA often simplifies deployment.
GUI Path (PAN-OS): Device > Certificate Management > Certificates. Mark a certificate for "Forward Trust." - Distribute the Forward Trust CA Certificate: Deploy this certificate to all client endpoints via Group Policy (GPO) for Windows, MDM solutions for mobile devices, or manual installation for unmanaged devices.
- Forward Untrust Certificate: The firewall uses the Forward Untrust certificate to present to clients when it encounters a server with an invalid certificate (e.g., expired, self-signed, untrusted). This ensures users still see a browser warning, but it's from the firewall, indicating the original site was untrustworthy.
-
Generate/Import a Forward Trust Certificate:
This can be a self-signed certificate generated on the firewall or, preferably, an intermediate CA certificate signed by an existing internal (enterprise) Root CA. Using an intermediate CA signed by an already trusted internal Root CA often simplifies deployment.
-
Broken Websites/Applications:
- Cause: Usually due to certificate pinning, client certificate requirements, or non-standard TLS implementations, as discussed earlier.
- Solution: Proactive identification and exclusion of problematic applications/sites. Establish a clear process for users to report broken sites/apps post-decryption enablement, allowing for quick investigation and addition to exclusion lists if necessary.
-
Latency and Slow Performance:
- Cause: Firewall undersized for decryption load, inefficient decryption policies (decrypting too much), or network path issues exacerbated by decryption processing.
- Solution: Proper sizing, optimized decryption policies, and performance monitoring.
-
Communication and Transparency:
- Inform users about the implementation of SSL/TLS decryption. Explain why it's being done (enhanced security) and what they might observe (e.g., if they inspect the certificate, they'll see the firewall's CA).
- Provide clear instructions for reporting issues.
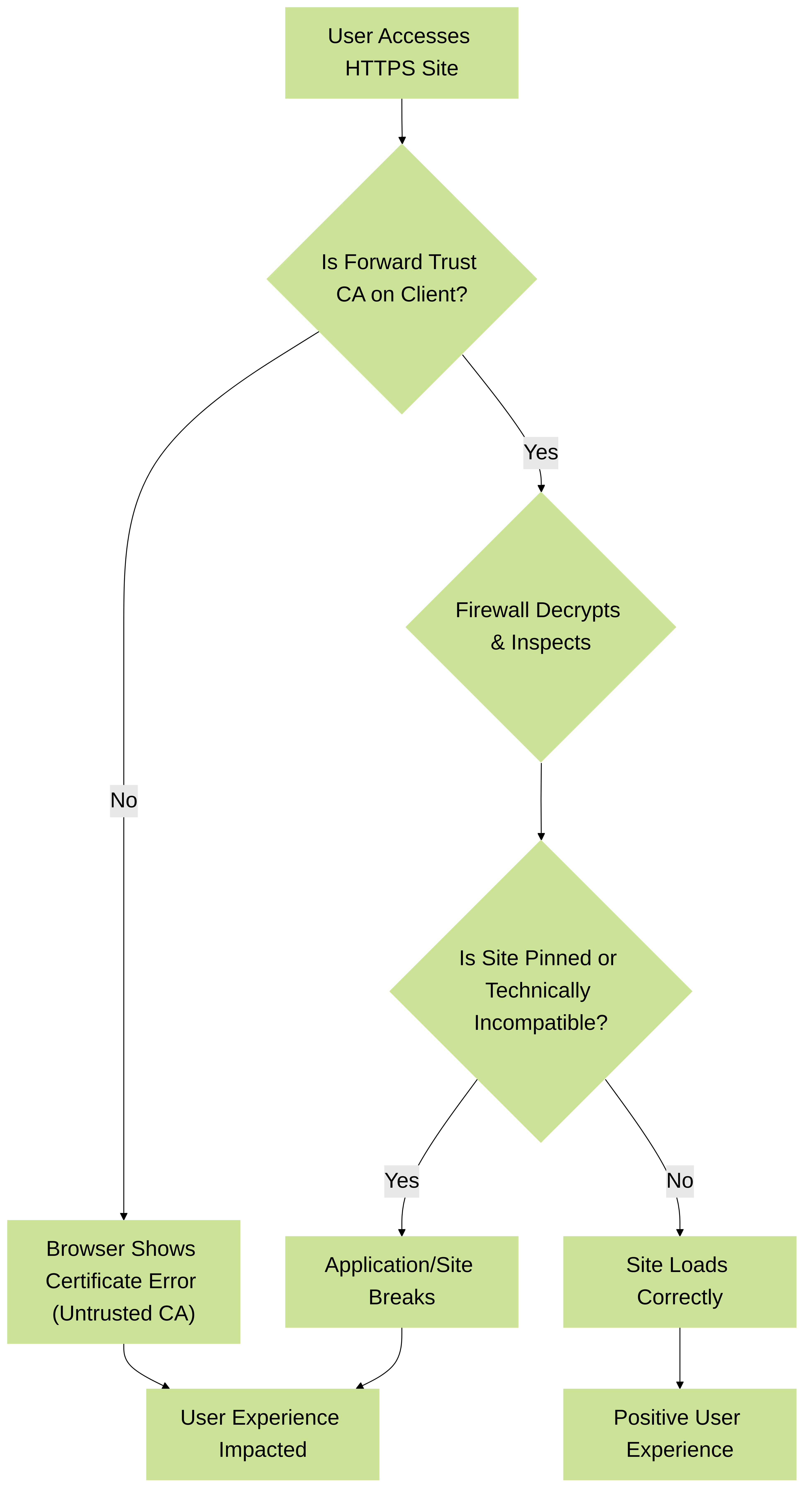
Flowchart showing how proper Palo Alto Networks Forward Trust CA deployment and handling of incompatible sites are critical for a positive user experience during SSL decryption.
6. Configuration and Management Overhead in Palo Alto Networks
While immensely beneficial, decryption adds a layer of configuration and ongoing management to your Palo Alto Networks firewall deployment.
-
Certificate Management:
- Forward Trust & Forward Untrust Certificates: Regular monitoring of expiry dates. Procedures for renewal and redistribution if necessary.
-
SSL Inbound Inspection Certificates:
Managing imported server certificates and private keys. Ensuring they are updated when server certificates are renewed. Securely handling private keys is paramount.
GUI Path (PAN-OS): Device > Certificate Management > Certificates. -
Certificate Revocation Checks:
PAN-OS can perform OCSP and/or CRL checks to validate the revocation status of certificates it encounters. Configure this in Decryption Profiles. Ensure the firewall has connectivity to OCSP responders and CRL distribution points.
GUI Path (PAN-OS): Objects > Decryption > Decryption Profile > SSL Decryption > SSL Protocol Settings > Certificate Revocation Checking.
-
Policy and Profile Management:
- Creating and maintaining Decryption policies (defining what traffic is subject to decryption) and Decryption Profiles (defining how decryption is performed – ciphers, protocol versions, exclusions).
- Regularly reviewing and updating decryption exclusion lists for new applications, URL categories, or specific sites. This is an ongoing task.
- Understanding the interaction between Decryption policies, Security policies, and other security profiles (e.g., Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, WildFire). Decryption enables these profiles to inspect encrypted traffic.
-
Logging and Monitoring:
- Decryption generates additional log data. Ensure adequate log storage capacity on the firewall or Panorama, and for any external SIEM.
- Regularly monitor decryption logs for errors, trends in blocked traffic, and successfully decrypted traffic volumes. Use Panorama for centralized logging and reporting.
- Troubleshooting Complexity: When issues arise, troubleshooting can involve analyzing client behavior, firewall configurations (decryption policies, profiles, certificates), decryption logs, and packet captures. This requires a good understanding of TLS/SSL handshakes and PAN-OS decryption processes.
Palo Alto Networks Best Practices for Implementing Decryption
To maximize the benefits of decryption while minimizing risks and operational friction, follow these Palo Alto Networks recommended best practices:
- Develop a Comprehensive Decryption Strategy: Before enabling decryption, work with stakeholders (IT, security, legal, HR, business units) to define goals, scope, exclusions, and responsibilities. [Source]
-
Start with a Phased Rollout:
- Begin by decrypting traffic for a pilot group of users or specific high-risk URL categories (e.g., "malware," "phishing," "unknown-sites," "parked").
- Monitor performance and user impact closely.
- Gradually expand the scope of decryption as you gain confidence and address any issues.
- Prioritize User Communication: Inform users about the decryption initiative, its benefits for security, and how to report any access issues. Transparency builds trust.
-
Robust Certificate Management:
- Use an Intermediate CA signed by your internal Enterprise Root CA as the Forward Trust certificate for easier deployment and trust management.
- Establish a clear process for deploying and renewing Forward Trust certificates.
- Securely manage private keys for SSL Inbound Inspection.
- Maintain Diligent Exclusion Lists: Regularly review and update decryption exclusions for privacy, compliance, and technical compatibility (especially for applications using certificate pinning).
- Monitor Performance Continuously: Keep a close eye on firewall CPU, memory, session rates, and decryption throughput. Adjust policies or consider hardware upgrades if performance bottlenecks arise.
- Leverage Panorama: For multi-firewall deployments, use Panorama for centralized management of decryption policies, profiles, certificates, and logs.
- Stay Updated: Keep PAN-OS software, applications, and threat content updated to the latest recommended versions for new features, bug fixes, and improved security efficacy related to decryption.
- Regularly Review and Audit: Periodically review your decryption policies, exclusion lists, and overall strategy to ensure they remain effective and aligned with business and security requirements.