Palo Alto Networks: Mastering Server and Authentication Profiles for Robust User-ID
Core Concepts: User-ID, Server Profiles, and Authentication Profiles in PAN-OS
Palo Alto Networks' Next-Generation Firewalls (NGFWs) leverage User-ID™ technology to integrate user identity information into security policies. This allows for granular control and visibility based on users and groups, rather than just IP addresses. To achieve this, PAN-OS relies on two critical configuration components: Server Profiles and Authentication Profiles . These profiles are the bridge between the firewall and your organization's identity infrastructure.
Understanding how to configure and troubleshoot these profiles is fundamental for implementing effective security policies, enabling secure remote access with GlobalProtect, controlling administrative access, and utilizing features like Captive Portal for guest or internal user authentication.
Deep Dive: Server Profiles in Palo Alto Networks
Server Profiles define the connection parameters and communication protocols the Palo Alto Networks firewall uses to interact with external identity and authentication servers. Each profile type is tailored for a specific kind of server. These are configured under
Device > Server Profiles
in the PAN-OS web interface or Panorama.
1. LDAP Server Profile
The LDAP (Lightweight Directory Access Protocol) Server Profile is predominantly used to connect to directory services like Microsoft Active Directory (AD), OpenLDAP, or Novell eDirectory. Its primary functions within PAN-OS are:
- User-ID Group Mapping: Retrieving user and group membership information to populate the User-ID database. This allows policies to be written based on directory group names.
- Authentication: Validating user credentials for various services like GlobalProtect, Captive Portal, and administrative UI access.
Key LDAP Server Profile Configuration Parameters (PAN-OS):
| Parameter | Description | Palo Alto Networks Context & Best Practice |
|---|---|---|
| Profile Name | A descriptive name for the profile. |
Use a name indicating the directory service (e.g.,
AD-Primary-LDAP
).
|
| LDAP Server Type |
Specifies the directory type (e.g.,
active-directory
,
eDirectory
,
sun
,
other
).
|
Selecting the correct type helps PAN-OS optimize queries and attribute mapping. For AD, always select
active-directory
.
|
| Servers Tab: Name, LDAP Server, Port | Defines one or more LDAP server IP addresses or FQDNs and the port. | Standard LDAP port is 389, LDAPS (LDAP over SSL/TLS) is 636. Always prefer LDAPS for security. List multiple domain controllers for redundancy. |
| SSL/TLS Encrypted Connection | Enables LDAPS. |
CRITICAL:
Always enable this. Requires importing the CA certificate (or server certificate if self-signed, not recommended for production) that signed the LDAP server's certificate into the firewall (
Device > Certificate Management > Certificates
).
|
| Verify Server Certificate | When SSL/TLS is enabled, this ensures the firewall validates the LDAP server's certificate against its trusted CAs. | Highly recommended to keep enabled for security. Disable only in trusted lab environments with self-signed certs and after understanding risks. |
| Base DN |
The starting point in the LDAP directory tree for searches (e.g.,
DC=example,DC=com
).
|
Specify as precisely as possible to reduce search scope and improve performance. |
| Bind DN |
The Distinguished Name of a service account used by the firewall to connect and search the LDAP directory (e.g.,
CN=svc-panldap,OU=ServiceAccounts,DC=example,DC=com
).
|
Use a dedicated service account with read-only permissions to the necessary parts of the directory. Do not use an administrator account. |
| Bind Password | The password for the Bind DN account. | Use a strong, unique password. |
| Bind Protection (PAN-OS 10.0+) | Provides options like SASL mechanisms for more secure bind operations. | Consider using if your LDAP environment supports it for enhanced security. |
| User Domain (for AD) |
The NetBIOS domain name. Used if users log in with
DOMAIN\user
format.
|
Automatically populated for AD type usually. |
| Retry Interval / Timelimit | Connection retry and search time limits. | Adjust based on network latency and directory size. Default values are usually fine. |
test ldap-authentication
CLI command is useful for verification.
! Example PAN-OS CLI command to test an LDAP server profile connection (run from operational mode): > test ldap-authentication server-profile "AD-Primary-LDAP" host ldap.example.com port 636 encryption ssl user-dn "CN=svc-panldap,OU=ServiceAccounts,DC=example,DC=com" password
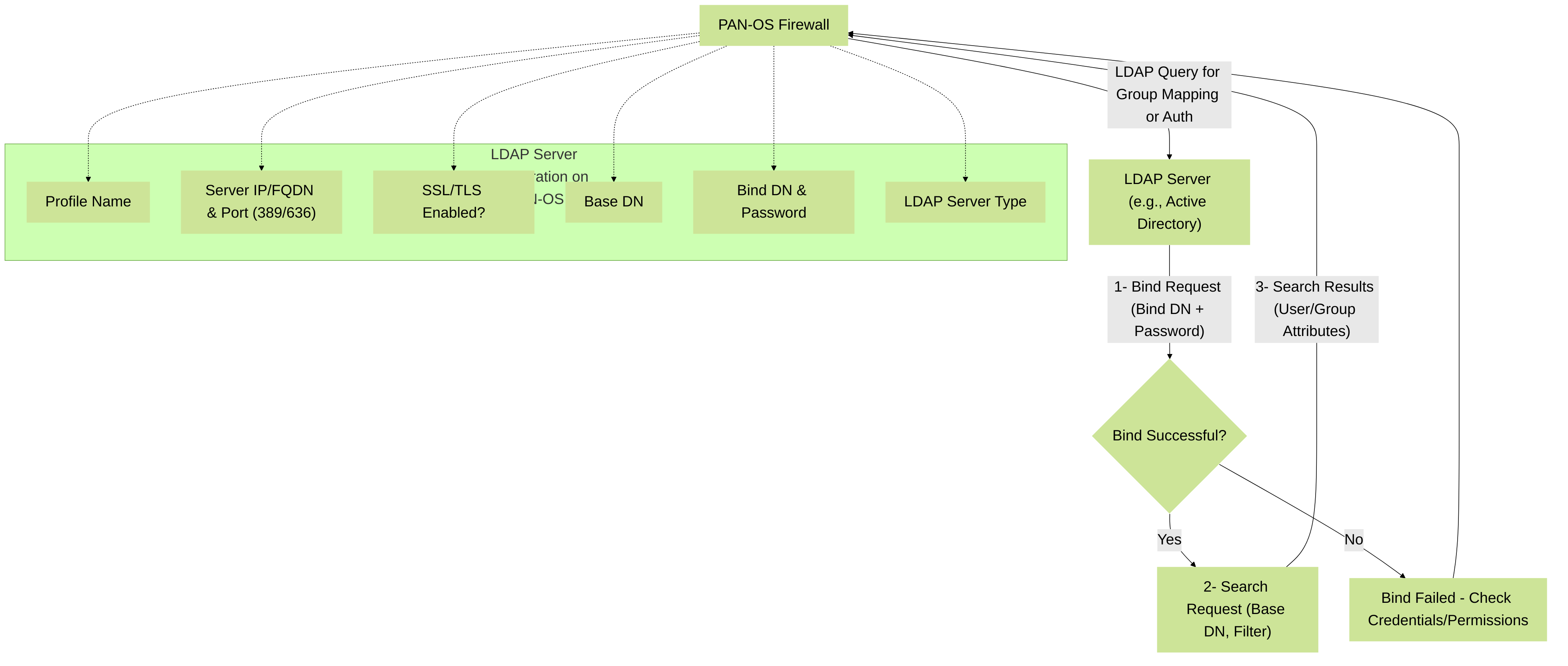
Figure 1: Simplified LDAP interaction flow with key PAN-OS configuration components. The PAN-OS firewall uses the configured Bind DN to authenticate to the LDAP server and then issues search queries starting from the Base DN to retrieve user/group information or validate credentials.
2. RADIUS Server Profile
RADIUS (Remote Authentication Dial-In User Service) is a client/server protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management. In Palo Alto Networks firewalls, RADIUS Server Profiles are commonly used for:
- Multi-Factor Authentication (MFA): Integrating with MFA providers like Duo, Okta, Azure MFA (via NPS), RSA SecurID. The firewall acts as a RADIUS client to the MFA server.
- GlobalProtect Authentication: Authenticating remote users.
- Captive Portal Authentication: Authenticating users on guest or internal networks.
- Administrative UI Access: Authenticating administrators to the firewall.
- User-ID Group Mapping (less common for primary source): RADIUS accounting messages or specific vendor attributes can sometimes be used for group information, though LDAP is more typical for this.
Key RADIUS Server Profile Configuration Parameters (PAN-OS):
-
Profile Name:
A descriptive name (e.g.,
MFA-RADIUS-Duo). - Servers Tab: Name, RADIUS Server, Secret, Port: IP/FQDN of the RADIUS server, the shared secret (must match on both ends), and port (typically 1812 for authentication, 1813 for accounting).
- Timeout / Retries: How long to wait for a response and how many times to retry.
- Protocol: PAP, CHAP, MS-CHAPv2. The chosen protocol must be supported by the RADIUS server. PAP is least secure; MS-CHAPv2 is generally preferred if available.
3. TACACS+ Server Profile
TACACS+ (Terminal Access Controller Access-Control System Plus) is another AAA protocol. While RADIUS combines Authentication and Authorization, TACACS+ separates these functions, offering more granularity, particularly for device administration.
In Palo Alto Networks firewalls, TACACS+ Server Profiles are almost exclusively used for:
- Administrative UI/CLI Access: Authenticating administrators and authorizing specific command sets or GUI views based on TACACS+ profiles.
It's less common to use TACACS+ for end-user authentication (like GlobalProtect or Captive Portal) as LDAP or RADIUS/SAML are better suited for those purposes.
Key TACACS+ Server Profile Configuration Parameters (PAN-OS):
-
Profile Name:
(e.g.,
Admin-TACACS-Primary). - Servers Tab: Name, TACACS+ Server, Secret, Port: IP/FQDN of the TACACS+ server, shared secret, and port (typically TCP 49).
- Protocol: PAP or CHAP.
- Timeout / Retries.
4. Kerberos Server Profile
Kerberos is a network authentication protocol designed to provide strong authentication for client/server applications by using secret-key cryptography. A Kerberos Server Profile on PAN-OS enables the firewall to:
- Authenticate administrators to the PAN-OS UI/CLI using Kerberos.
- Provide Kerberos-based authentication for GlobalProtect users.
- Perform transparent authentication for web access via Captive Portal (using Kerberos single sign-on if browser is configured).
Key Kerberos Server Profile Configuration Parameters (PAN-OS):
-
Profile Name:
(e.g.,
Domain-Kerberos). -
Server Tab: Server Name, Realm:
Name for the server entry, and the Kerberos realm (usually your AD domain name in uppercase, e.g.,
EXAMPLE.COM). -
Keytab File:
Upload a keytab file generated from your Key Distribution Center (KDC, typically a domain controller). This file contains the service principal name (SPN) and encrypted key for the firewall service. The SPN typically looks like
HTTP/firewall.example.com@EXAMPLE.COM.
5. SAML Identity Provider (IdP) Profile
SAML (Security Assertion Markup Language) is an XML-based open standard for exchanging authentication and authorization data between an Identity Provider (IdP) and a Service Provider (SP).
In this context, the Palo Alto Networks firewall acts as a Service Provider (SP) . The SAML IdP Profile configures the firewall to trust and consume assertions from an external SAML IdP (e.g., Okta, Azure AD, Ping Identity, ADFS). This enables Single Sign-On (SSO) for:
- GlobalProtect (Portal and Gateway)
- Captive Portal
- Administrative UI/CLI access
- Prisma Access
Key SAML IdP Profile Configuration Parameters (PAN-OS):
-
Profile Name:
(e.g.,
SAML-Okta-IdP). - Identity Provider Metadata: Typically, you import the IdP's metadata XML file. This file contains the IdP's SSO URL, entity ID, and signing certificate.
- Validate Identity Provider Certificate: Ensures the IdP's signing certificate is trusted.
- Service Provider (SP) Configuration: PAN-OS automatically generates its SP metadata, which needs to be provided to the IdP. Key parts include the Assertion Consumer Service (ACS) URL and Entity ID of the firewall.
-
Username Attribute / Group Attribute:
Specifies which SAML attributes from the assertion will be used for the username and group membership information. Common username attributes are
username,email, orNameID.
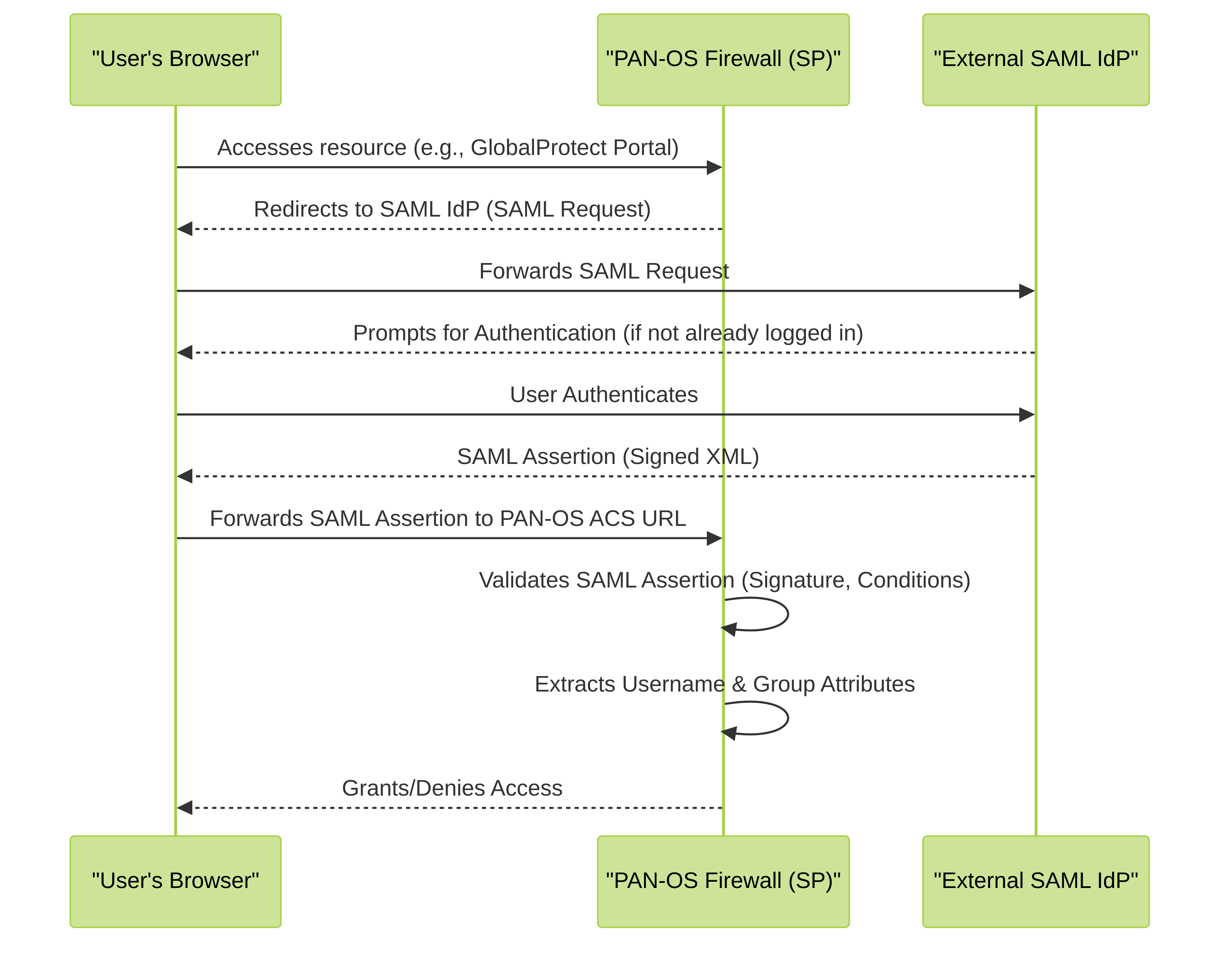
Figure 2: SAML Authentication Flow where PAN-OS acts as a Service Provider (SP). The user is redirected to the external IdP for authentication, and the IdP sends a SAML assertion back to PAN-OS.
Deep Dive: Authentication Profiles in Palo Alto Networks
An Authentication Profile on a Palo Alto Networks firewall ties together a Server Profile (defining
how
to connect to an authentication server) with specific authentication settings and user/group restrictions. It defines
who
can authenticate and
what
credentials or attributes are expected. Authentication Profiles are configured under
Device > Authentication Profile
.
They are referenced in various PAN-OS features that require user authentication:
- Administrator authentication to the firewall (Management UI/CLI).
- GlobalProtect Portal and Gateway authentication.
- Captive Portal policies.
- VPN (IKE/IPSec) user authentication.
- Explicit Proxy authentication.
Key Authentication Profile Configuration Parameters (PAN-OS):
| Parameter | Description | Palo Alto Networks Context & Best Practice |
|---|---|---|
| Name | A descriptive name for the profile. |
Use a name reflecting its purpose and method (e.g.,
Auth-GP-SAML-Okta
,
Auth-Admin-LDAP
).
|
| Type |
Specifies the authentication method (e.g.,
LDAP
,
RADIUS
,
TACACS+
,
SAML
,
Kerberos
,
Local Database
).
|
This selection dictates which type of Server Profile can be associated. |
| Server Profile | Selects the pre-configured Server Profile that this Authentication Profile will use. | This links the "who" and "what" (Authentication Profile) to the "how" (Server Profile). |
| Login Attribute (for LDAP type) |
The LDAP attribute used to identify the user during login (e.g.,
sAMAccountName
,
userPrincipalName
,
mail
,
uid
).
|
Must match what users will enter as their username.
sAMAccountName
is common for AD.
userPrincipalName
(UPN) is often used for multi-domain environments.
|
| Username Modifier |
Modifies the username format before sending it to the authentication server. Options:
|
Crucial for ensuring the username format matches what the authentication server expects (e.g., AD UPN format vs. pre-Windows 2000). |
| Allow List |
Specifies which users or groups are permitted to authenticate using this profile. Can be
all
or a selection of groups (from User-ID group mapping) or individual users.
|
CRITICAL:
Best practice is to define a specific allow list rather than using
all
. This restricts authentication attempts to only authorized personnel. For group-based allow lists, ensure group mapping is working correctly.
|
| Multi-Factor Authentication Tab (if applicable) | Allows chaining an MFA server profile (typically RADIUS) for second-factor authentication after primary authentication succeeds. | Enables robust MFA for various services. |
| Advanced Tab: Lockout Settings | Configure failed attempt lockouts (Failed Attempts, Lockout Time). | Helps prevent brute-force attacks. |
| Advanced Tab: Timers | Cache authentication results for a period (Authentication Cache Timeout). | Can improve performance by reducing redundant authentications for the same user. |
show user group name
on the CLI.
! Example PAN-OS CLI command to test an authentication profile:
> test authentication authentication-profile "Auth-GP-LDAP" username "jdoe" password
Enter password:
Target vsys: vsys1
Authentication type: ldap
Server profile: AD-Primary-LDAP
Authentication server: ldap.example.com
Username for authentication: EXAMPLE\jdoe
Trying to find user 'jdoe' in group 'all'...
User 'jdoe' is a member of the following group(s) :
cn=globalprotect_users,ou=groups,dc=example,dc=com
cn=domain users,ou=users,dc=example,dc=com
Authentication successful for user 'jdoe'
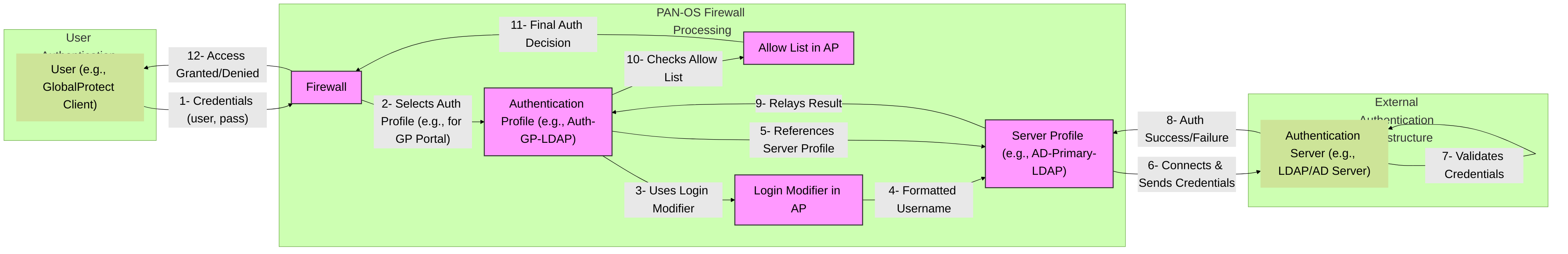
Figure 3: Interaction between Authentication Profile, Server Profile, and external Authentication Server during a user authentication attempt on a Palo Alto Networks firewall. The Authentication Profile orchestrates the process, applying modifiers and checking allow lists.
Authentication Sequences
Authentication Sequences (configured under
Device > Authentication Sequence
) allow you to list multiple Authentication Profiles in an ordered sequence. When an authentication event occurs that uses an Authentication Sequence, the firewall attempts to authenticate the user against each profile in the list, one by one, until authentication succeeds or all profiles have been tried.
Key Features and Use Cases:
- Failover/Redundancy: If the primary authentication method (e.g., LDAP) is unavailable, the sequence can automatically try a secondary method (e.g., RADIUS or local user database).
- Multiple Identity Stores: Authenticate users against different identity stores. For example, try corporate AD first, then a partner AD.
- Profile Selection Criteria (Use Profile From): Can specify criteria (e.g., username contains "@partner.com") to select a specific profile from the sequence, rather than trying all in order.
Configuration:
- Name: A descriptive name for the sequence.
- Authentication Profiles: An ordered list of existing Authentication Profiles.
- Use Profile From: (Optional) Criteria to directly select a profile from the list based on username or domain.

Figure 4: Logic flow of an Authentication Sequence in PAN-OS. The firewall attempts authentication against each profile in the defined order until success or exhaustion of profiles.
User-ID: The Big Picture with Authentication
Server Profiles and Authentication Profiles are not just for authenticating users accessing firewall services; they are integral to the broader User-ID functionality. User-ID's goal is to map IP addresses to usernames. While methods like User-ID Agents (Windows-based, PAN-OS integrated), Syslog, and API integrations provide many mappings passively, active authentication methods are also key:
- Captive Portal: When traffic from an unknown IP address matches a policy with Captive Portal enabled, the user is redirected to a web page to authenticate. This authentication typically uses an Authentication Profile (e.g., LDAP, RADIUS, SAML). Upon successful authentication, PAN-OS creates an IP-to-user mapping.
- GlobalProtect: When users connect via GlobalProtect, their authentication (using an Authentication Profile) provides a direct IP-to-user mapping for their VPN session IP.
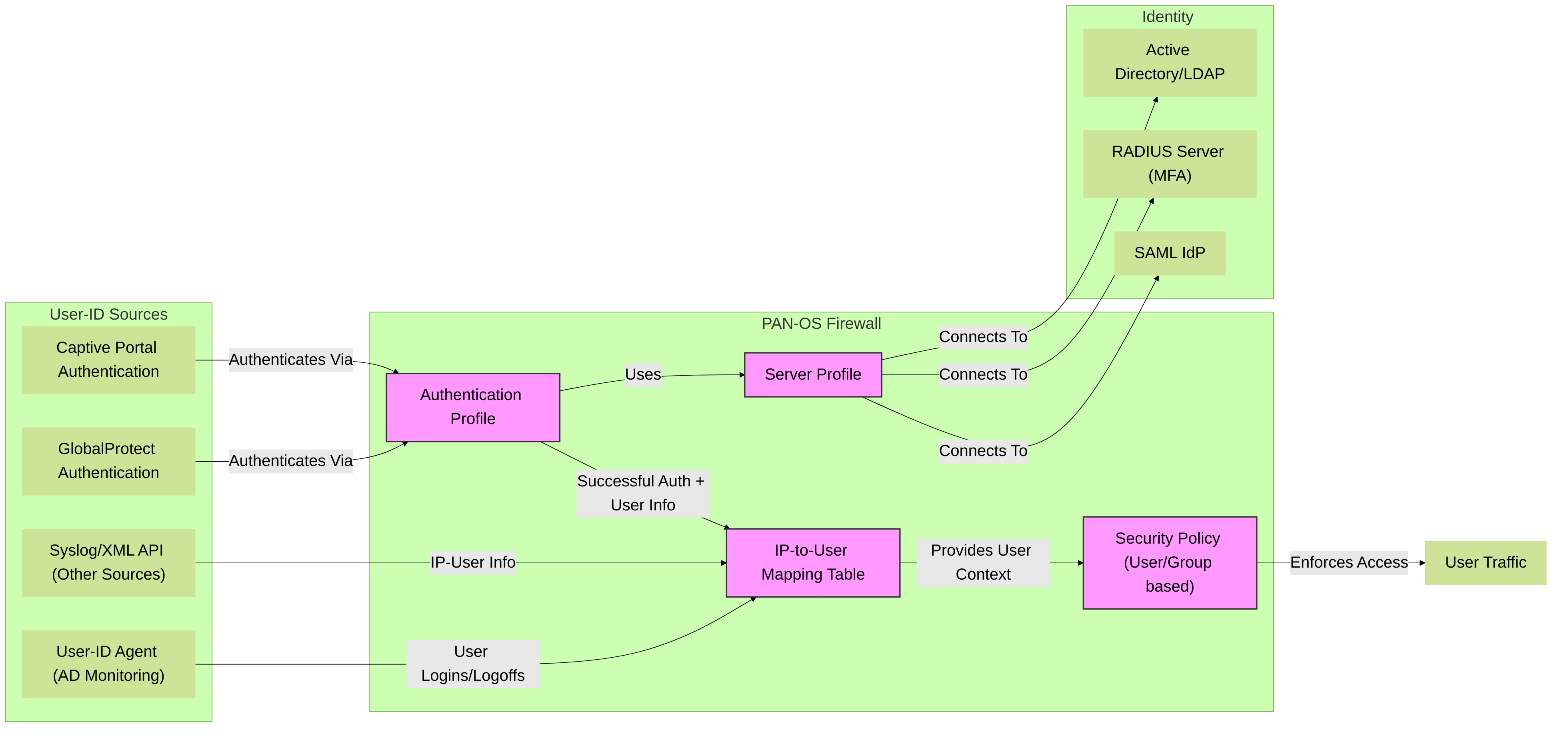
Figure 5: Integration of User-ID sources, Authentication Profiles, and Server Profiles in Palo Alto Networks. Authentication events from GlobalProtect and Captive Portal directly contribute to the IP-to-User mapping table, enabling user-based policy enforcement.
Troubleshooting Server and Authentication Profiles in PAN-OS
Effective troubleshooting involves a systematic approach:
-
Verify Network Connectivity:
-
Can the firewall reach the authentication server on the required port(s)? (e.g., LDAP 389/636, RADIUS UDP 1812/1813, TACACS+ TCP 49). Use
pingandshow arp all(for L2 reachability). - Are there any intermediate firewalls or ACLs blocking traffic? Check traffic logs on PAN-OS and other devices.
-
For Server Profiles, the firewall typically sources traffic from its management interface. Ensure this interface has proper routing. For GlobalProtect/Captive Portal using data plane interfaces as source for RADIUS/LDAP, ensure service routes are configured if necessary (
Device > Setup > Services > Service Route Configuration).
-
Can the firewall reach the authentication server on the required port(s)? (e.g., LDAP 389/636, RADIUS UDP 1812/1813, TACACS+ TCP 49). Use
-
Test Server Profile:
-
LDAP:
Use
test ldap-authentication server-profile <profile_name> ...ortest authentication server-profile <profile_name> ...in PAN-OS 10.x+. Checkshow user server-monitor state name <profile_name>to see server status. -
RADIUS/TACACS+:
No direct "test" command for the server profile itself, but testing an Authentication Profile using it will validate connectivity. Check server status with
show user server-monitor state name <profile_name>. -
Kerberos:
Verify keytab is loaded, realm is correct, and time is synchronized (
show clock). - SAML: Check IdP metadata validity, certificate trust, and attribute mapping. Developer tools in browsers can show SAML requests/responses.
-
LDAP:
Use
-
Test Authentication Profile:
-
Use the CLI command:
test authentication authentication-profile <profile_name> username <username> password. This provides detailed output on which server was tried, username modification, and group checks.
-
Use the CLI command:
-
Check Firewall Logs:
-
System Logs (
Monitor > Logs > System): Look for general errors related to server connectivity or profile misconfigurations. -
Authentication Logs (
Monitor > Logs > Authentication): Shows authentication attempts, successes, and failures with reasons. Crucial for diagnosing login issues. Filter by username or auth profile. -
User-ID Logs (
Monitor > Logs > User-ID): Shows User-ID agent activity, IP-user mapping updates, and group mapping refreshes. Check for errors related to LDAP group mapping (useridd.log). -
Traffic Logs (
Monitor > Logs > Traffic): If policies are not behaving as expected, ensure User-ID is correctly identifying the user for the session.
-
System Logs (
-
Examine Daemon Logs (CLI - Advanced):
-
less mp-log authd.log: Authentication daemon logs. Very detailed, useful for deep troubleshooting of RADIUS, LDAP, Kerberos, SAML authentication processes. -
less mp-log useridd.log: User-ID daemon logs. Useful for User-ID agent issues, group mapping problems. -
less mp-log ikemgr.log(for VPN) /less mp-log gpsvc.log(for GlobalProtect).
-
-
Packet Captures (CLI/GUI):
-
If connectivity issues are suspected, take packet captures on the firewall filtered for the authentication server's IP and port. This can reveal TLS handshake failures, incorrect RADIUS secrets, or other network-level problems.
! Example: Capture LDAP traffic on management interface > debug dataplane packet-diag set capture stage firewall file ldap_capture.pcap interface management host
port 636 > debug dataplane packet-diag set capture on ... (reproduce issue) ... > debug dataplane packet-diag set capture off ! Then view or export the pcap file.
-
If connectivity issues are suspected, take packet captures on the firewall filtered for the authentication server's IP and port. This can reveal TLS handshake failures, incorrect RADIUS secrets, or other network-level problems.
memberOf
or primary group) and group objects across the relevant Base DN. Also, check the Group Include List and User Group Mapping settings under
Device > User Identification > Group Mapping Settings
. The command
show user group list
and
show user group name "
"
are invaluable.
Palo Alto Networks Best Practices for Server and Authentication Profiles
- Secure Protocols: Always use secure protocols like LDAPS (LDAP over SSL/TLS), SAML over HTTPS, and ensure RADIUS/TACACS+ secrets are strong and unique.
- Least Privilege: For LDAP Bind DN accounts, grant only the necessary read permissions to the required directory attributes and OUs. Avoid using domain administrator accounts.
- Redundancy: Configure multiple servers in Server Profiles (e.g., multiple Domain Controllers for LDAP) for high availability.
- Specific Allow Lists: In Authentication Profiles, always use specific Allow Lists (groups or users) rather than "all" to restrict who can attempt authentication.
- Authentication Sequences: Use Authentication Sequences for failover to secondary methods or local databases to enhance resilience.
- Regular Testing: Periodically test your Authentication Profiles and Server Profile connectivity, especially after changes in your identity infrastructure.
- Monitor Logs: Regularly review Authentication, System, and User-ID logs for any errors or unusual activity. Set up log forwarding to a SIEM.
- Certificate Management: Keep certificates (for LDAPS, SAML IdP validation) up to date and monitor their expiration dates.
- PAN-OS Updates: Keep your PAN-OS software updated to the latest preferred release to benefit from security patches and feature enhancements.
-
Username Modifiers:
Understand and correctly configure Username Modifiers in Authentication Profiles to match the format expected by your authentication servers (e.g.,
DOMAIN\uservsuser@domain.com).