Palo Alto Networks: Mastering Shared Gateways and External Zones for Multi-VSYS Internet Access
In complex network environments managed by Palo Alto Networks firewalls, particularly those leveraging multiple Virtual Systems (vsys), providing efficient and manageable internet access for each vsys is crucial. Shared Gateways, in conjunction with External Zones, offer a streamlined solution for this, especially in scenarios with limited public IP addresses or when reducing administrative overhead is a priority. This guide delves deep into the architecture, configuration, traffic flow, and best practices for using Shared Gateways within the Palo Alto Networks ecosystem, with a strong focus on PCNSE certification readiness.
Understanding Shared Gateways in PAN-OS
A Shared Gateway (SG) on a Palo Alto Networks firewall is a specialized mechanism that allows multiple virtual systems (vsys) to share a common physical interface (or set of interfaces, like an Aggregate Ethernet group) for external communication, typically to the internet. Each participating virtual system requires an External Zone . This External Zone acts as a logical conduit within the vsys, enabling it to direct traffic towards the Shared Gateway. Security policies are configured within each vsys to control traffic flowing from its internal zones to this External Zone.
The primary motivations for using a Shared Gateway include:
- IP Address Conservation: When an Internet Service Provider (ISP) allocates only a single public IP address (or a small block) to an organization that needs to provide internet access for multiple distinct logical firewalls (vsys). The Shared Gateway uses this single IP (or IPs from the block) for all outbound traffic from the participating vsys.
- Reduced Administrative Overhead: Configuring NAT and Policy-Based Forwarding (PBF) can be centralized on the Shared Gateway rather than being duplicated across multiple vsys.
- Performance Optimization (for this specific path): Unlike inter-vsys traffic that transits between two full virtual systems (which typically undergoes full App-ID and Security Policy inspection at each vsys hop), traffic passing from a vsys to a Shared Gateway for internet breakout does not undergo a second round of App-ID and Security Policy evaluation by the Shared Gateway itself. The inspection is performed by the originating vsys before the traffic is handed off. This makes the Shared Gateway a more lightweight option for simple internet egress compared to creating another full vsys solely for internet transit.
A Shared Gateway utilizes a single, dedicated Virtual Router (VR) to manage routing for all the virtual systems it serves. This VR contains the necessary routes (e.g., a default route) to the external network (e.g., the ISP). While interfaces within the individual virtual systems can use private, non-routable IP addresses, the Shared Gateway's external-facing interface will have a globally routable IP address.
Shared Gateways are always visible to all virtual systems on the firewall, simplifying connectivity. In the PAN-OS web interface, a Shared Gateway is identified with an ID like
sg<ID>
(e.g.,
sg1
). It's a recommended practice to incorporate this ID into the descriptive name you assign to the Shared Gateway (e.g., "Internet-Shared-Gateway-sg1"). When you assign objects like interfaces or zones to a Shared Gateway, it appears in the vsys selection dropdowns, similar to a regular vsys, but with its distinct `sgX` identifier.
Architectural Overview: Shared Gateway and Vsys Interaction
The diagram below illustrates a common scenario where multiple virtual systems (representing different tenants or departments) share a single internet connection via a Shared Gateway on a Palo Alto Networks firewall.
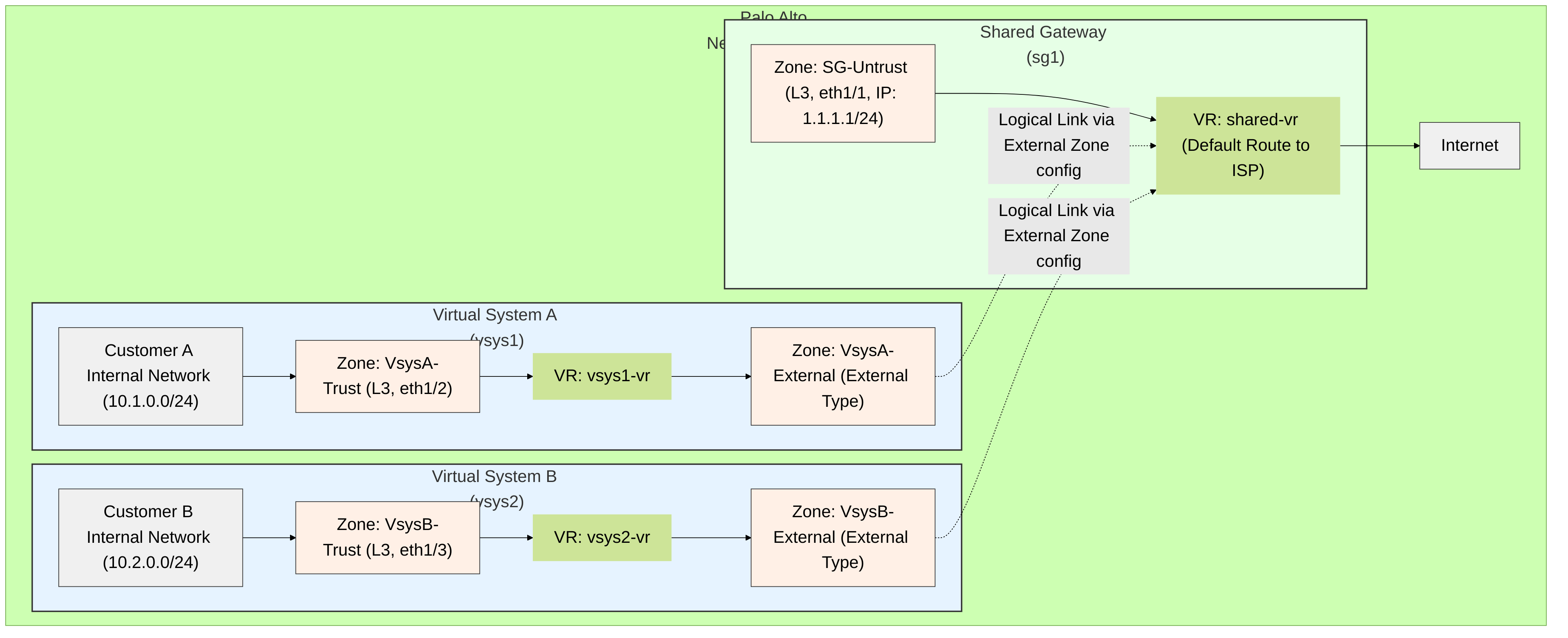
Architectural overview of multiple virtual systems (vsys1, vsys2) on a Palo Alto Networks firewall using a common Shared Gateway (sg1) for internet access. Each vsys has its internal trust zone and an "External Zone" that logically connects to the Shared Gateway's virtual router (shared-vr). The Shared Gateway manages the physical connection (eth1/1) to the internet and performs NAT.
Key components in this architecture:
- Virtual Systems (vsys): Independent, logical firewall instances (e.g., vsys1, vsys2). Each has its own zones, interfaces (logical or dedicated physical), virtual router, policies, and administrators (if delegated).
- Shared Gateway (sg1): A global entity that "owns" the physical interface(s) connected to the external network (e.g., `ethernet1/1`). It has its own virtual router (`shared-vr`).
- Vsys Internal Zones: Standard zones within each vsys containing internal user networks (e.g., `VsysA-Trust`).
- Vsys External Zones: Special zones configured within each vsys (e.g., `VsysA-External`). These are of type "External" and are pointed towards the Shared Gateway. They act as the next-hop logical interface for traffic from the vsys destined for the internet via the Shared Gateway.
- Shared Gateway Zone: A zone within the Shared Gateway that contains the physical external interface (e.g., `SG-Untrust`).
-
Virtual Routers:
- Each vsys has its own VR (e.g., `vsys1-vr`) which routes internal traffic and traffic destined for the Shared Gateway (typically via a default route pointing to its External Zone).
- The Shared Gateway has its own VR (`shared-vr`) which has routes to the internet (e.g., a default route to the ISP router).
Configuration Steps for Shared Gateways in PAN-OS
Configuring a Shared Gateway involves steps on the firewall globally (for the SG itself) and within each vsys that will use it.
-
Enable Multiple Virtual Systems:
This is a prerequisite. If not already enabled, this is done under
Device > Setup > Management > General Settings. A reboot is typically required after enabling multi-vsys mode.PCNSE/PCNSA Exam Note (Palo Alto Networks): Enabling multi-vsys mode fundamentally changes how the firewall operates and allocates resources. Understand its implications. -
Create the Shared Gateway:
-
GUI:
Navigate to
Network > Virtual Systems. Click "Shared Gateway" at the bottom of the vsys list, then click "Add". - Provide a Name (e.g., "SG1-Internet"). The system will assign an ID like `sg1`.
- Assign Interfaces: Add the physical interface(s) that will connect to the external network (e.g., internet) to this Shared Gateway.
-
Create Zones:
Within the Shared Gateway context (select `sg1` from the vsys dropdown in the top right of the web interface, or use `set system setting target-vsys sg1` in CLI):
- Create a zone (e.g., "SG-UNTRUST") and assign the external-facing interface(s) to it. This zone will typically be a Layer 3 zone.
-
Configure Shared Gateway's Virtual Router:
- Create a Virtual Router within the Shared Gateway (e.g., "SG-VR-Internet").
- Add the Shared Gateway's external interface (from the SG-UNTRUST zone) to this VR. Configure its IP address (the public IP).
-
Add a static default route (
0.0.0.0/0) pointing to the ISP's gateway.admin@PA-FW(sg1)> configure Entering configuration mode [edit] admin@PA-FW(sg1)# set network virtual-router SG-VR-Internet interface ethernet1/1 admin@PA-FW(sg1)# set network virtual-router SG-VR-Internet routing-table ip static-route default destination 0.0.0.0/0 nexthop ip-address <ISP_GATEWAY_IP> admin@PA-FW(sg1)# commit
-
GUI:
Navigate to
-
Configure Each Virtual System to Use the Shared Gateway:
For each vsys (e.g., vsys1) that needs to use the Shared Gateway:
- Import Shared Gateway Interfaces (if needed for visibility, typically not directly assigned to vsys): This step is more about awareness; interfaces are owned by the SG.
-
Create an External Zone in the Vsys:
-
GUI: Navigate to
Network > Zones(ensure you are in the context of the specific vsys, e.g., `vsys1`). - Click "Add" and create a zone (e.g., "vsys1-External-to-SG1").
- Set the "Type" to External .
- In the "Shared Gateway" dropdown, select the Shared Gateway you created (e.g., `sg1`).
Gotcha! (Palo Alto Networks): Forgetting to set the zone type to "External" and linking it to the correct Shared Gateway is a common misconfiguration. This link is what enables the vsys to forward traffic to the SG. -
GUI: Navigate to
-
Configure Vsys Virtual Router:
-
In the vsys's VR (e.g., `vsys1-vr`), add a static route (often a default route
0.0.0.0/0) that directs traffic destined for the internet to the External Zone you just created. No next-hop IP is specified for routes pointing to an External Zone; the zone itself acts as the target.admin@PA-FW(vsys1)> configure Entering configuration mode [edit] admin@PA-FW(vsys1)# set network virtual-router vsys1-vr routing-table ip static-route internet-out destination 0.0.0.0/0 next-hop next-vr SG-VR-Internet ; This is incorrect for external zone admin@PA-FW(vsys1)# set network virtual-router vsys1-vr routing-table ip static-route internet-out destination 0.0.0.0/0 interface ??? ; This is also tricky. Correct approach for vsys VR to use External Zone: The route in the vsys VR should point to a next-hop *interface* that is part of the External Zone, OR it might be simpler that the External Zone itself is the "gateway". Let's re-verify. PAN-OS Admin Guide for 10.1: "For the vsys, configure a static route in its virtual router that lists the External zone as the destination for traffic that the vsys forwards to the shared gateway." This means you do not specify a next-hop IP or a physical interface in the typical sense for this route. The "External Zone" acts as the logical next hop. When configuring the static route in the vsys VR: Destination: 0.0.0.0/0 Interface: (Leave Blank if 'External Zone' is the target) - this is where it gets tricky. You typically pick an interface. Next Hop: Select "None", and the External Zone itself implicitly handles the forwarding to the SG. Actually, it's more like: you create a virtual interface (like a tunnel interface, but not quite) or the zone becomes a routing target. Let's use the official doc style: "Select the External zone as the path monitoring destination for the static route that forwards traffic from the vsys to the shared gateway." In PAN-OS, when you create a static route, you specify a destination, and then either an interface and next-hop IP, or just an interface (for directly connected networks), or a next-hop virtual router. For External Zones, you essentially define a route in the vsys's VR that says "traffic for 0.0.0.0/0 goes towards 'vsys1-External-to-SG1'". PAN-OS handles the internal plumbing. Upon reviewing TechDocs again: When you configure a static route in a vsys to send traffic to a Shared Gateway, you typically don't specify a next-hop IP within the vsys's VR for that route. Instead, the External Zone effectively becomes the target. The firewall knows traffic sent to this External Zone is destined for the linked Shared Gateway. If `vsys1-External-to-SG1` is the name of the External Zone, you would typically have an interface within `vsys1` that's associated with this zone for routing purposes, even if it's a logical construct. Or, the routing decision directs traffic *to* the zone. A common way is to create a Layer 3 subinterface or a dummy/loopback interface in the vsys, assign it to the External Zone, and then route to that interface. However, the "External" zone type simplifies this. The route points "towards" the SG via this External Zone. The key is that the vsys's forwarding plane knows that traffic matching this route needs to be passed to the SG specified in the External Zone's definition. Let's assume the vsys has a logical interface (e.g. loopback or nullif, though not strictly needed as the External Zone itself is the gateway) that is notionally part of the external zone for routing purposes. More accurately, the route in vsys1 would simply be: `set network virtual-router vsys1-vr routing-table ip static-route default-to-sg destination 0.0.0.0/0 interface
` - This is not quite right. The External Zone itself acts as the gateway. So the route in vsys1's VR: Destination: 0.0.0.0/0 Next Hop: (Type) -> select the External Zone, or it's implicit by policy. The most common way is that policy (from vsys-trust to vsys-External-to-SG1) allows it, and the default route in vsys1-vr points to an IP address within the Shared Gateway's network *IF* there was a direct L3 link. But here it's an External Zone. The Palo Alto Networks documentation often shows the external zone configured, and then security policy allows traffic to it. The routing decision is: if destination is external zone, send to linked SG. The default route in the vsys should simply point to the Shared Gateway as the next hop. The "External Zone" facilitates this. Official PAN-OS Admin Guide ("Configure a Static Route from the Virtual System to the Shared Gateway"): 1. Select Network > Virtual Routers > vsys-internet-vr. 2. Select Static Routes > IPv4 > Add. 3. Name: default-route-to-SG 4. Destination: 0.0.0.0/0 5. Interface: (select an interface in the vsys that is part of the external zone if you created one; otherwise, this can be tricky. If the external zone is purely logical, the forwarding relies on the zone link). 6. Next Hop: IP Address. **This is where it clarifies.** You use an IP address that is on the Shared Gateway's internal-facing network, if the SG had such an interface accessible by the vsys. But with an "External Zone" type, the mechanism is more abstract. Let's use the "less overhead" model: The external zone is the target. A vsys routes traffic to an External Zone. The External Zone is linked to an SG. The SG handles it from there. The vsys VR: `set network virtual-router routing-table ip static-route destination 0.0.0.0/0 path-monitor-destination-type external-zone ` (this is more for path monitoring). The key is the *forwarding lookup* in the vsys. If a route exists that matches the destination, and the next-hop for that route implies egress through the External Zone, the traffic goes there. So, a simple default route in the vsys VR: `set network virtual-router vsys1-vr routing-table ip static-route default-to-internet destination 0.0.0.0/0 nexthop ?` It will effectively be the Shared Gateway. The selection of the External Zone in Security Policy is key. Let's simplify the vsys routing part: The vsys needs a route that directs internet-bound traffic towards the logical construct representing the connection to the Shared Gateway. This is achieved by having a default route in the vsys's VR where the next-hop effectively becomes the Shared Gateway. The 'External Zone' is the mechanism. Often, you will configure the default route in the vsys VR to point to an IP address that resides on an interface within the Shared Gateway, IF the Shared Gateway were to expose such an interface directly to the vsys (e.g. using inter-vsys routing interfaces). However, for the "External Zone" type, it's simpler: traffic is routed to the External Zone, which then forwards to the SG. The VR needs a default route that will eventually match and forward to that external zone. A more practical way: 1. Vsys VR default route: `set network virtual-router vsys1-vr routing-table ip static-route default-to-sg destination 0.0.0.0/0 nexthop next-vr shared-vr` This command assumes `shared-vr` is directly routable or known. This is more for direct inter-VR routing. For External Zones, the link is more implicit. The most straightforward explanation: Configure a default static route in the vsys's virtual router. The 'next hop' part of this route should logically resolve to the Shared Gateway. For an External Zone, you don't specify a next-hop IP in the typical sense. The firewall resolves this through the External Zone configuration. Security policy then allows traffic from internal zone to this External Zone. The external zone itself is not an interface you pick in the static route. What you do is: In the vsys VR: `set network virtual-router vsys1-vr routing-table ip static-route default-to-internet destination 0.0.0.0/0` And then you must specify a next hop. If the SG is `sg1`, you would typically provide a next-hop IP *on the sg1 network* or specify `next-vr sg1_vr_name`. The External Zone is a policy construct. Let's re-check the base HTML: "The default route for the virtual systems should point to the shared gateway." This implies the SG has some addressable point or the vsys VR can target the SG's VR. Yes, when you link an External Zone to an SG, the vsys's VR can then have a static route whose next-hop is the VR of the Shared Gateway. Example from Palo Alto Networks documentation (slightly adapted for clarity): `set network virtual-router [vsys_router_name] routing-table ip static-route [route_name] destination 0.0.0.0/0 nexthop next-vr [shared_gateway_router_name]` This makes the most sense. The External Zone establishes the *permission* and *path*, and the route uses it. admin@PA-FW(vsys1)> configure [edit] admin@PA-FW(vsys1)# set network virtual-router vsys1-vr routing-table ip static-route default-to-sg destination 0.0.0.0/0 nexthop next-vr SG-VR-Internet admin@PA-FW(vsys1)# commit
-
In the vsys's VR (e.g., `vsys1-vr`), add a static route (often a default route
-
Configure Security Policies in the Vsys:
- Create a policy allowing traffic from the vsys's internal zone(s) (e.g., `VsysA-Trust`) to the External Zone created in the previous step (e.g., `vsys1-External-to-SG1`).
- Apply necessary Security Profiles (Antivirus, Anti-Spyware, etc.) to this policy, as this is where inspection occurs.
admin@PA-FW(vsys1)> configure [edit] admin@PA-FW(vsys1)# set rulebase security rules Allow-To-Internet from VsysA-Trust to vsys1-External-to-SG1 source any destination any application any service any action allow profile-setting group
admin@PA-FW(vsys1)# commit
-
Configure NAT Policies (Typically in Shared Gateway):
- As per best practice for SGs, configure Source NAT in the Shared Gateway context (`sg1`).
-
Create a NAT policy that translates the source IP addresses of traffic coming from the vsys's internal subnets to the Shared Gateway's external (public) IP address.
admin@PA-FW(sg1)> configure [edit] admin@PA-FW(sg1)# set rulebase nat rules VsysA-Outbound-NAT from VsysA-Trust source 10.1.0.0/24 to SG-UNTRUST destination any service any admin@PA-FW(sg1)# set rulebase nat rules VsysA-Outbound-NAT source-translation dynamic-ip-and-port interface-address interface ethernet1/1 admin@PA-FW(sg1)# commit
(Note: In the NAT rule `from` clause, you'd select the zone from which the SG *receives* traffic from the vsys. This is implicitly handled by the external zone linking. The key is the source IP matching the vsys's internal network.) A more robust NAT rule on the SG: Original Packet: Source Zone (any, as traffic arrives from vsys), Dest Zone (SG-UNTRUST), Source IP (vsys internal IPs).admin@PA-FW(sg1)> configure [edit] admin@PA-FW(sg1)# set rulebase nat rules SG-Source-NAT description "NAT for vsys traffic to Internet" from any to SG-UNTRUST source [10.1.0.0/24, 10.2.0.0/24] destination any service any source-translation dynamic-ip-and-port interface-address interface ethernet1/1 admin@PA-FW(sg1)# commit
Traffic Flow with a Shared Gateway
Understanding the packet lifecycle is crucial for troubleshooting and design.
Outbound Traffic (e.g., Host in VsysA to Internet):
- Origination: A host in VsysA's internal network (e.g., 10.1.0.100) sends a packet to an internet destination (e.g., 8.8.8.8).
-
VsysA Ingress & Forwarding Lookup:
- Packet arrives on VsysA's internal interface (e.g., `ethernet1/2`), source zone `VsysA-Trust`.
- VsysA's Virtual Router (`vsys1-vr`) performs a route lookup. The default route `0.0.0.0/0 next-vr SG-VR-Internet` matches. This indicates the packet needs to go towards the Shared Gateway via the External Zone `vsys1-External-to-SG1`.
-
VsysA Security Policy Evaluation:
- VsysA checks its Security Policy rules. A rule matching `from VsysA-Trust to vsys1-External-to-SG1` for the specific application/service must exist and permit the traffic.
- If allowed, App-ID, Content-ID (Antivirus, Anti-Spyware, etc.), and other configured security profiles are applied by VsysA.
-
Hand-off to Shared Gateway:
The packet, now processed by VsysA's security engine, is logically passed to the Shared Gateway (`sg1`).
CRITICAL (Palo Alto Networks): At this hand-off point, the Shared Gateway does not re-evaluate the traffic against its own (non-existent for this path) Security Policies or App-ID. It trusts the originating vsys's decision.
-
Shared Gateway Processing:
- PBF Check (Optional): If PBF rules are configured on `sg1`, they are evaluated.
- NAT Policy Lookup: `sg1` checks its NAT rules. The rule matching source `10.1.0.0/24` (VsysA's internal network) to destination zone `SG-UNTRUST` will translate the source IP (10.1.0.100) to `sg1`'s public IP on `ethernet1/1` (e.g., 1.1.1.1) and assign a port.
-
Forwarding Lookup (SG_VR):
`sg1`'s Virtual Router (`SG-VR-Internet`) performs a route lookup. The default route `0.0.0.0/0 nexthop
` matches.
- Egress: The NAT-ed packet exits `sg1`'s external interface (`ethernet1/1`) towards the internet.
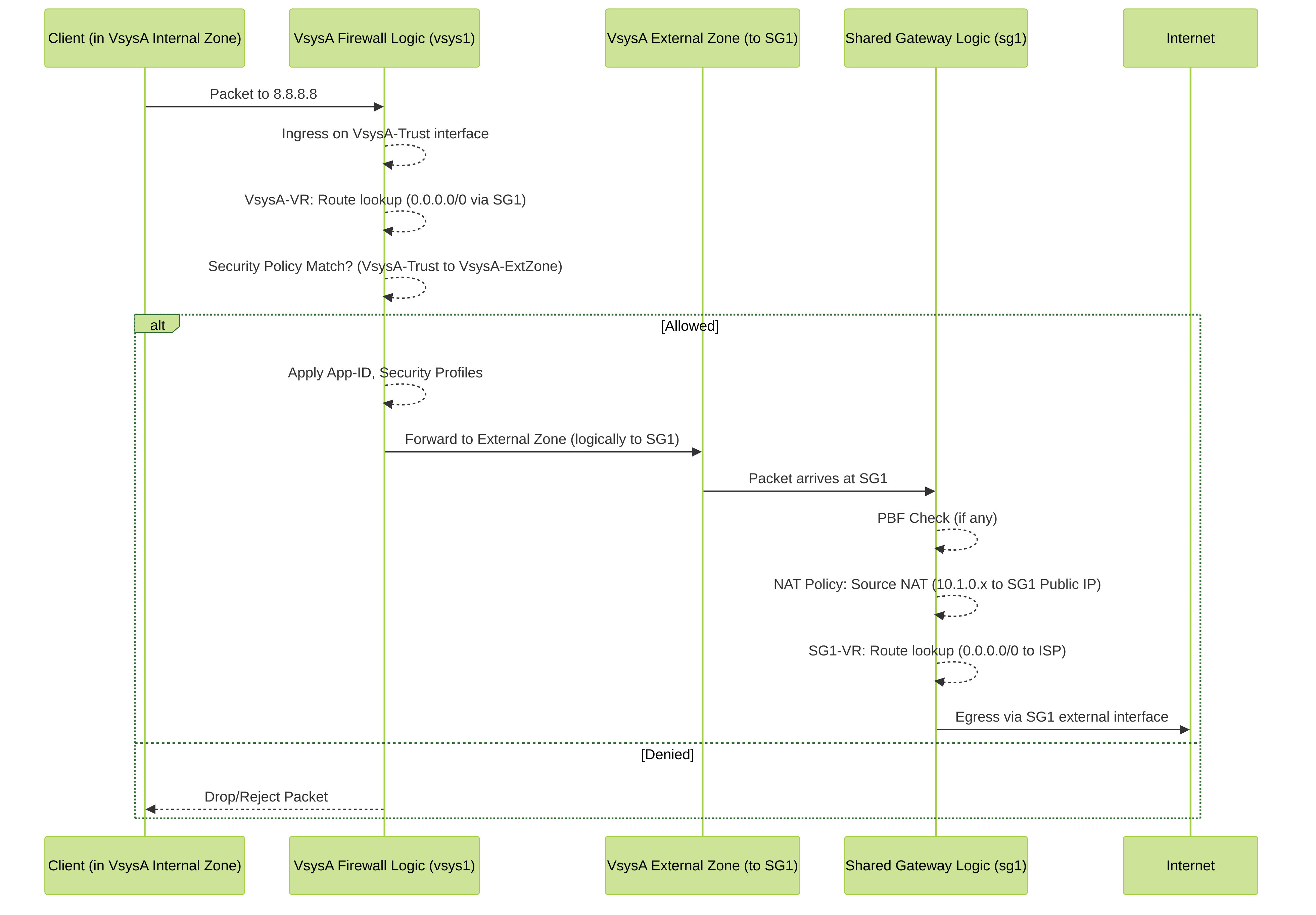
Sequence diagram illustrating outbound packet flow from a client in VsysA, through VsysA's security processing, to the Shared Gateway (SG1) for NAT and routing to the Internet. Note that security inspection happens in VsysA.
Networking Considerations and Advantages
The base HTML provided several important considerations, which are expanded here:
- Source NAT: As highlighted, if the IP addresses of the virtual systems' internal networks are private (RFC1918), configure Source NAT on the Shared Gateway to translate these to its globally routable IP address. This is crucial for internet connectivity.
- Centralized Virtual Router: The Shared Gateway's virtual router is the single point of routing for all external traffic from participating vsys. Ensure its routing table (especially the default route to the ISP) is correct.
-
Vsys Default Route:
Each vsys using the Shared Gateway must have its default route (or relevant internet-bound routes) pointing towards the Shared Gateway's virtual router (e.g., via `nexthop next-vr
`). - Vsys Security Policies: Critical! Security policies within each vsys must explicitly allow traffic from their internal zones to their respective External Zones (which link to the Shared Gateway). This is where all threat prevention and access control for outbound traffic from a vsys is enforced.
- Administrative Control: The firewall super-administrator (or an admin with global permissions) should control the Shared Gateway's configuration (interfaces, zones, VR, NAT, PBF). Individual vsys administrators typically do not have rights to modify the Shared Gateway, ensuring stability for all tenants.
Advantages of Centralizing Configuration on Shared Gateway:
- Simplified NAT Management: Instead of configuring and managing potentially numerous Source NAT rules across multiple vsys (if each vsys were to handle its own NAT before reaching a shared transit point), you can configure a more consolidated set of NAT rules on the Shared Gateway. This is especially beneficial for dynamic IP and port NAT using the SG's interface IP.
- Centralized Policy-Based Forwarding (PBF): If specific types of traffic from any of the participating vsys need to be routed via a different next-hop (e.g., a secondary ISP link or a specific security service), PBF rules can be configured once on the Shared Gateway, applying to all relevant traffic passing through it.
When to Use a Shared Gateway: A Decision Guide
Choosing between a Shared Gateway and other multi-vsys internet access methods (like a dedicated transit vsys) depends on specific requirements.
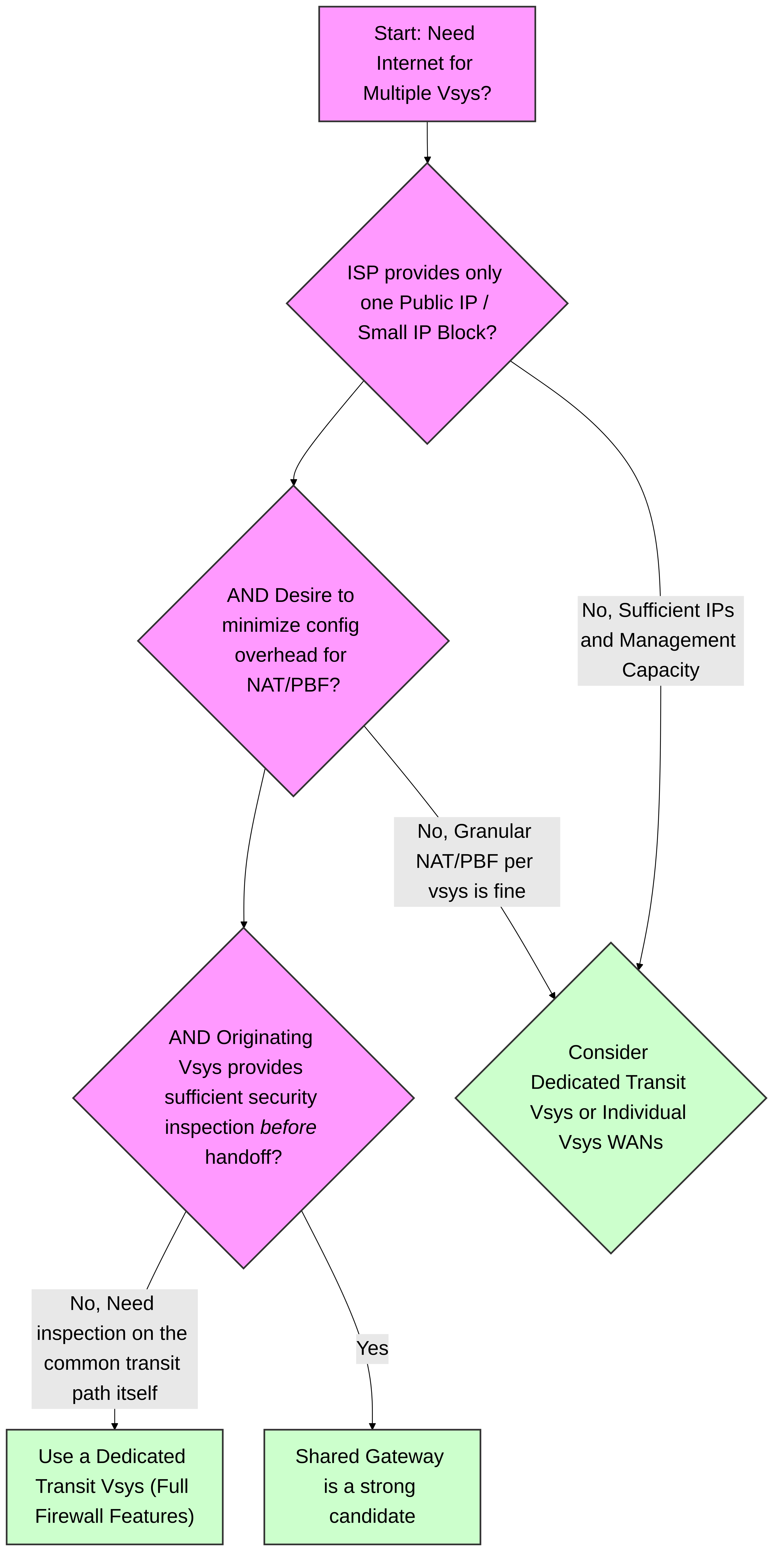
Decision tree to help determine if a Shared Gateway is the appropriate Palo Alto Networks solution for providing internet access to multiple virtual systems.
Consider a Shared Gateway when:
- You have a limited number of public IP addresses from your ISP.
- You want to centralize NAT and PBF for multiple vsys.
- The security inspection performed by the originating vsys (before traffic reaches the External Zone) is sufficient, and you don't require an additional layer of inspection on the common transit path itself.
- Reducing the processing overhead associated with a full transit vsys is desirable.
Consider a dedicated transit vsys (a full vsys acting as an internet gateway for other vsys) when:
- You need to apply full security inspection (Threat Prevention, WildFire, Decryption, etc.) on the aggregated traffic from multiple vsys at the common internet gateway point.
- Each vsys requires highly customized routing or NAT policies that are better managed within a full vsys context before reaching the actual internet exit.
- The limitations of a Shared Gateway (no Security Policies, QoS, etc., on the SG itself) are not acceptable for the shared path.
Shared Gateway Limitations Recap
It's crucial to remember the inherent limitations of a Shared Gateway, as these define its appropriate use cases:
- No Security Policy Evaluation: For traffic passing from a vsys, through its External Zone, to the Shared Gateway, the SG itself does not perform Security Policy evaluation (including App-ID, User-ID based policy decisions). All such policy enforcement must occur in the originating vsys.
- No Threat Prevention Profiles: Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, and WildFire analysis are not applied by the Shared Gateway on traffic transiting from vsys. These must be applied by the originating vsys.
- No DoS Protection Policies: Zone Protection Profiles and DoS Protection Policies configured on the Shared Gateway will protect the SG's own interfaces and IP addresses, but they do not apply to the traffic streams transiting from individual vsys.
- No QoS (Quality of Service): QoS policies cannot be applied on the Shared Gateway to prioritize or shape traffic coming from different vsys. QoS must be handled within each vsys or by upstream/downstream devices if needed on the aggregate link.
- No SSL Decryption: The Shared Gateway cannot perform SSL Forward Proxy or Inbound Inspection decryption for traffic transiting from vsys. Decryption must be handled by the originating vsys.
- No Application Override: Application Override policies are not effective on the Shared Gateway for vsys-originated traffic.
- No Authentication Policies: Captive Portal or other authentication mechanisms cannot be enforced by the Shared Gateway for traffic originating from vsys users.