Palo Alto Networks Tap Interfaces: A Deep Dive for PCNSE Certification
Tap interfaces are a crucial aspect of network security monitoring and a key topic for the PCNSE exam. They provide a passive method to monitor network traffic without disrupting the flow of data. This comprehensive guide explores tap interfaces in detail, covering their functionality, configuration, use cases, and PCNSE-relevant considerations.
Understanding Tap Interfaces
A tap interface mirrors traffic from a specific network segment, allowing a Palo Alto Networks firewall to analyze it without being directly in the traffic path. This passive monitoring capability is essential for security analysis, troubleshooting, and compliance auditing. Unlike inline interfaces, tap interfaces do not participate in forwarding traffic, making them ideal for scenarios where network disruption must be avoided.
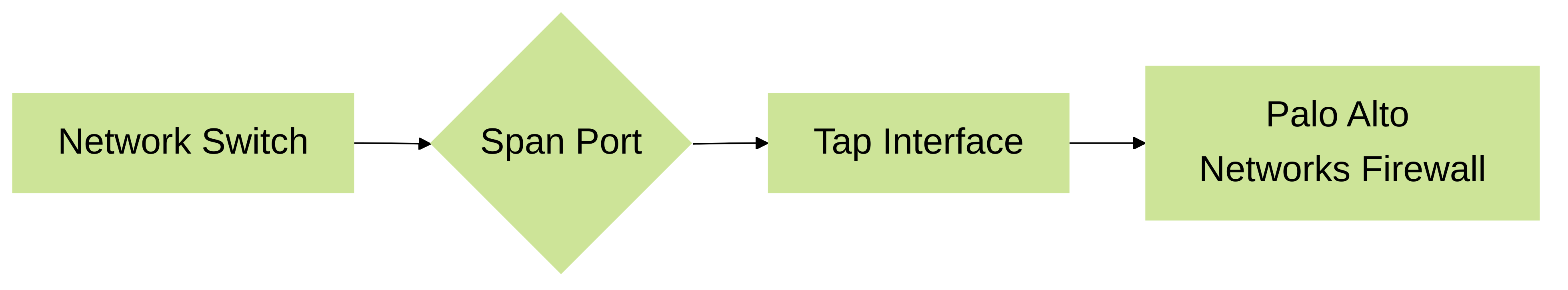
Traffic flow from a switch's SPAN port to a Palo Alto Networks firewall's tap interface.
Configuring Tap Interfaces
Configuring a tap interface on a Palo Alto Networks firewall involves a few key steps:
- Physical Connection: Connect the firewall's physical interface to the SPAN port (or mirrored port) of your network switch.
- Interface Configuration: Navigate to Network > Interfaces in the firewall's web interface. Select the connected physical interface and change its type to Tap .
- Zone Assignment: Assign the tap interface to a dedicated security zone. This isolates the mirrored traffic and prevents interference with other security policies. It's recommended to create a specific 'TapZone' for this purpose.
- Security Profiles: Create or modify security profiles (Antivirus, Anti-spyware, Vulnerability Protection, URL Filtering, WildFire, etc.) with actions set to alert . This allows the firewall to detect threats without actively blocking them.
- Security Policy: Create a security policy rule that allows traffic from the tap zone to itself (TapZone to TapZone). Apply the configured security profiles to this rule. This ensures all mirrored traffic is inspected.
- Commit: Commit the changes to apply the configuration.
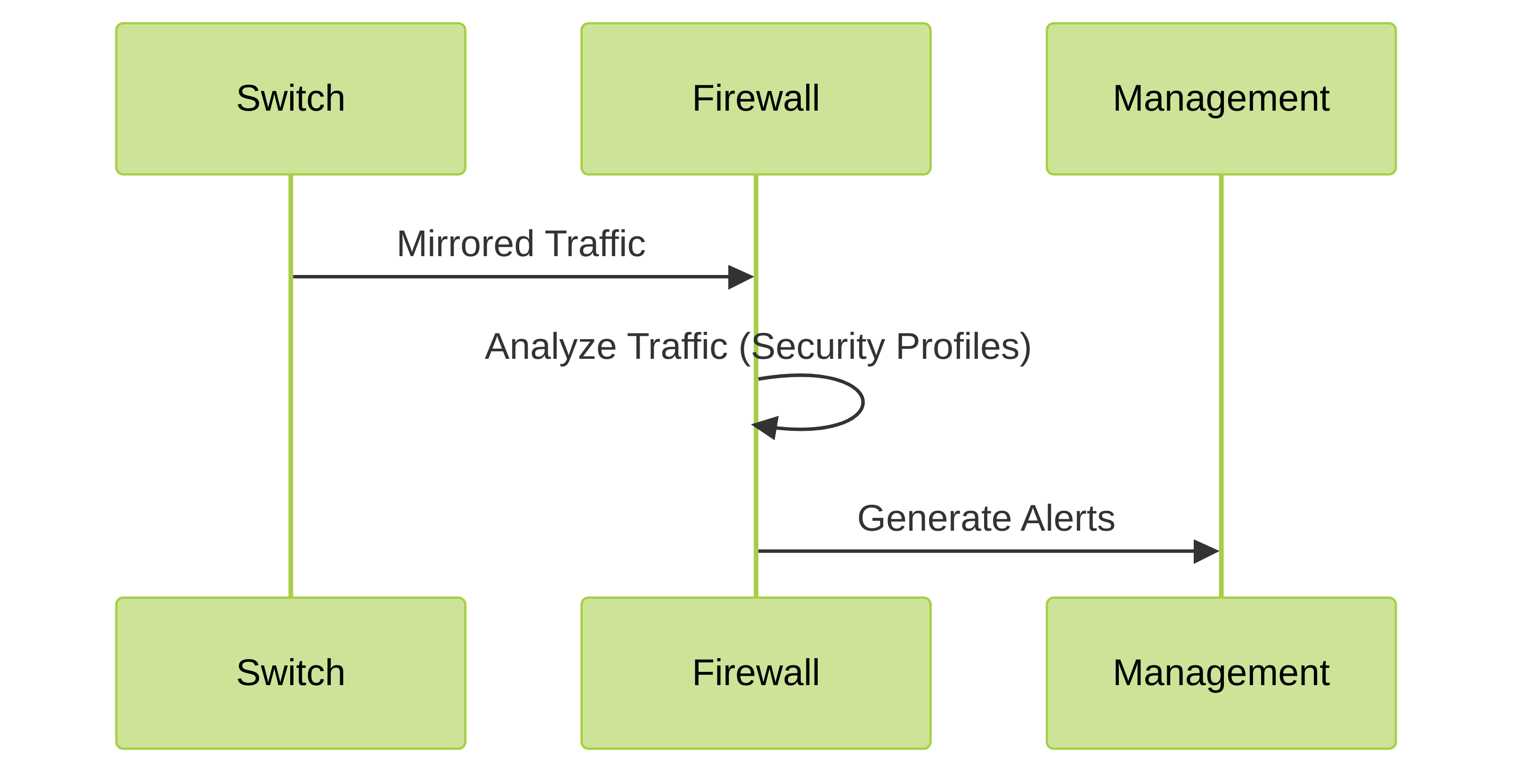
Sequence diagram illustrating the flow of mirrored traffic and alert generation.
Benefits of Tap Interfaces
- Passive Monitoring: Tap interfaces provide visibility without impacting network performance or availability.
- Simplified Deployment: Implementing tap mode requires minimal changes to the existing network infrastructure.
- Security Analysis: Gain valuable insights into network traffic patterns, identify potential threats, and monitor security policy effectiveness.
- Troubleshooting: Tap interfaces aid in troubleshooting network issues by providing access to raw traffic data.
- Compliance: Monitor and log network activity for compliance with regulatory requirements.
Use Cases and Practical Examples
Here are some real-world examples of how tap interfaces can be utilized:
- Monitoring DMZ Traffic: Analyze traffic entering and leaving the DMZ to identify malicious activity or policy violations.
- Monitoring Database Server Traffic: Capture database traffic for auditing and security analysis without affecting database performance.
- Troubleshooting Intermittent Connectivity Issues: Use a tap interface to capture traffic during intermittent outages to pinpoint the root cause.
- Validating Security Policies: Monitor traffic and alerts generated by the tap interface to verify the effectiveness of existing security policies.
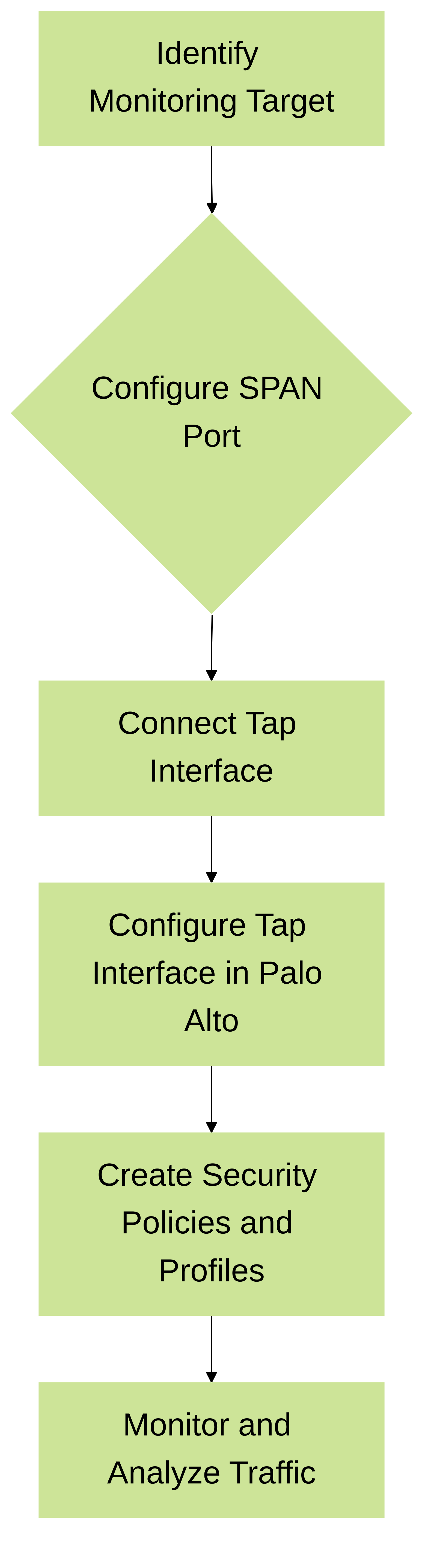
Flowchart depicting the process of setting up and utilizing a tap interface.
Troubleshooting Tap Interfaces
Common issues and troubleshooting steps:
- No Traffic Captured: Verify SPAN port configuration on the switch, ensure correct cabling, and check the interface status on the firewall.
- Excessive Resource Consumption: Consider using a dedicated management interface for monitoring or using a separate firewall for tap mode deployments in high-traffic environments.
- Incorrect Alerts: Review security profile configurations and ensure they are appropriately tuned for tap mode (actions set to 'alert').
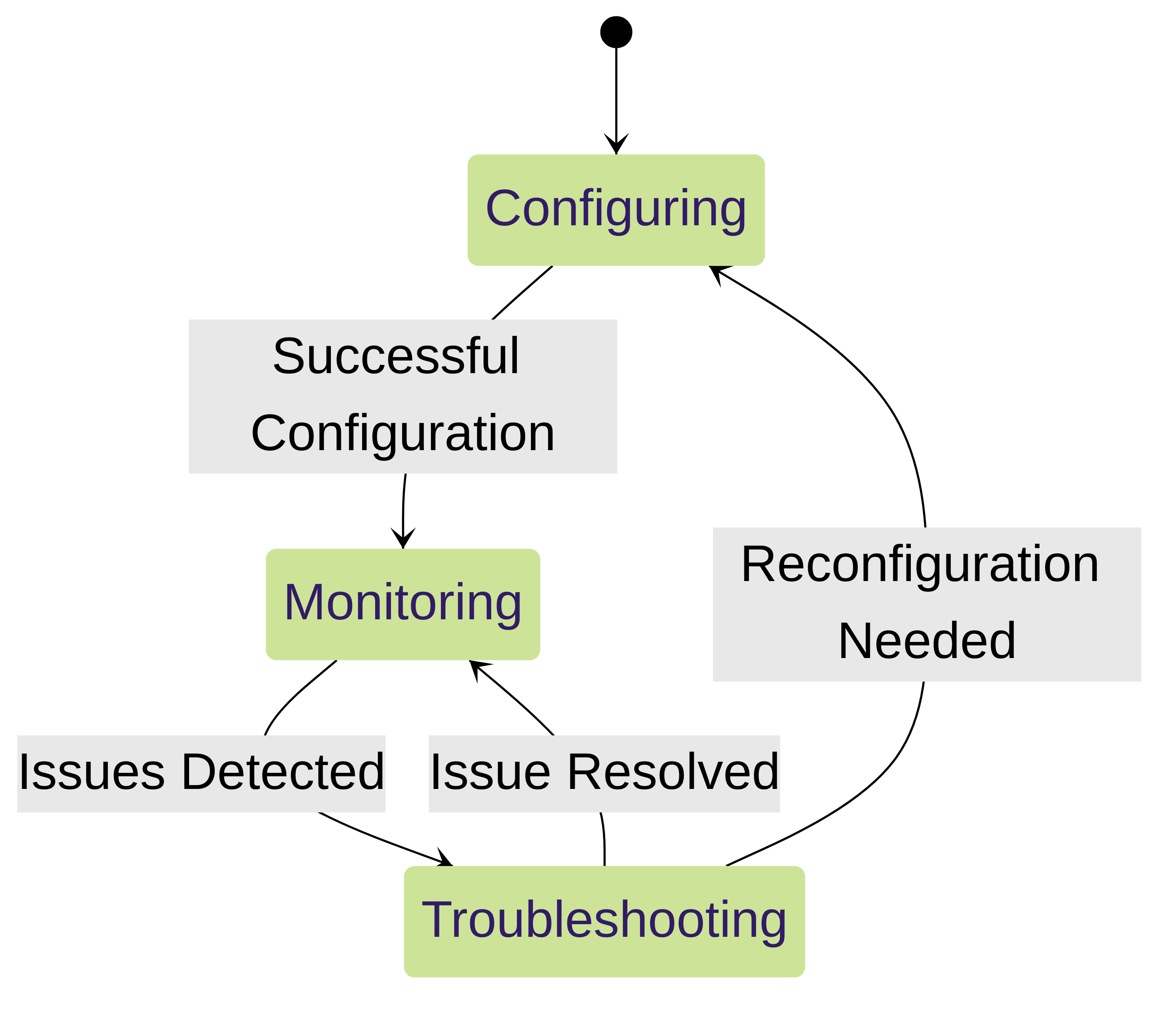
State diagram showing the lifecycle of a tap interface configuration.