Palo Alto Networks: User-ID Hub in Multi-VSYS Environment
Overview of User-ID in Palo Alto Networks
User-ID™ is a cornerstone technology in Palo Alto Networks Next-Generation Firewalls (NGFWs) that enables organizations to integrate user identity information into their security policies. By identifying users rather than just IP addresses, administrators can create more granular and effective security rules, gain better visibility into network activity, and simplify incident response. In environments utilizing multi-virtual systems (multi-vsys) on a single Palo Alto Networks firewall, managing User-ID information across these isolated logical firewalls can become complex.
To address this, PAN-OS® allows for the designation of one virtual system as a User-ID Hub . This hub vsys acts as a centralized repository and distribution point for IP-address-to-username mappings and user-to-group mappings. Other vsys (spoke vsys) on the same physical firewall can then leverage these mappings from the hub, ensuring consistent user identification and policy enforcement across the entire multi-vsys deployment without requiring redundant User-ID configurations on each vsys.
The "Why": Purpose and Benefits of a User-ID Hub
Palo Alto Networks designed the User-ID Hub feature to address specific challenges in multi-vsys environments:
- Scalability: In large deployments with numerous vsys, configuring and managing User-ID sources (like Active Directory server monitoring or User-ID agents) on each individual vsys is inefficient and resource-intensive. The hub model scales by centralizing this effort.
- Consistency: Ensures all vsys have access to the same, up-to-date user mapping information, leading to consistent policy enforcement. If a user's IP changes, the update propagates from the hub to all spokes.
- Administrative Efficiency: Reduces the administrative burden by consolidating User-ID configuration, monitoring, and troubleshooting to a single point (the hub vsys).
- Resource Optimization: Prevents multiple vsys from independently polling the same directory services or communicating with the same User-ID agents, thus reducing redundant network traffic and load on those sources.
- Simplified Policy Management: Allows security policies in spoke vsys to leverage user and group information transparently, without needing direct connectivity to all User-ID sources.
Key Concepts in User-ID Hub Operation
Understanding these Palo Alto Networks-specific concepts is essential for deploying and managing a User-ID Hub:
-
User-ID Agent Types and Roles:
- Windows-based User-ID Agent: Software installed on a Windows server that monitors domain controller security logs, Exchange server logs, or polls client probing to gather IP-to-user mappings. It then forwards these mappings to one or more Palo Alto Networks firewalls, including a User-ID Hub.
- PAN-OS Integrated User-ID Agent: A feature built into PAN-OS that allows the firewall itself (typically the hub vsys) to directly monitor Active Directory domain controllers using WMI or an agentless approach by parsing security event logs sent via syslog from domain controllers.
- Palo Alto Networks GlobalProtect™: Endpoints running GlobalProtect client software report user and device information to the GlobalProtect Gateway/Portal, which can be a significant source of User-ID mappings.
- Palo Alto Networks Cloud Identity Engine (CIE): A cloud-based service that synchronizes user and group information from various identity providers (IdPs) and makes it available to Palo Alto Networks firewalls and other services. The hub can be configured to pull mappings from CIE.
-
Mapping Sources for the Hub:
The User-ID Hub vsys can collect mappings from various sources:
- Server Monitoring (Active Directory, eDirectory, Exchange)
- Windows-based User-ID Agents
- GlobalProtect
- Syslog (parsing specific log formats containing user mapping info)
- XML API (for custom integrations or third-party systems providing IP-user mappings, often referred to as IP-Tagging when tags are involved, but User-ID focuses on user identity)
- Captive Portal
- Authentication Policy
- Cloud Identity Engine (CIE)
-
Mapping Ownership and Precedence:
- Hub Mappings: Mappings learned or configured on the User-ID Hub vsys.
- Local Mappings: Mappings learned or configured directly on a spoke vsys.
- Precedence Rule: If a spoke vsys has a locally learned or configured mapping for a specific IP address, that local mapping takes precedence over any mapping for the same IP address received from the User-ID Hub. This allows for specific overrides if needed on a per-vsys basis.
Gotcha! (Palo Alto Networks): A common point of confusion is mapping precedence. If a user is not being identified as expected on a spoke vsys, check if there's a conflicting or stale local mapping on that vsys that is overriding the hub's information. Use CLI commands like `show user ip-user-mapping ip` on the spoke vsys to see the mapping source. -
Group Mapping Centralization:
- PAN-OS offers features to centralize group mapping information. This means the hub vsys can connect to directory services (like Active Directory LDAP servers), retrieve user group memberships, and then share this group information with spoke vsys.
- This reduces the need for each spoke vsys to have its own LDAP server profiles and group mapping configurations.
- Spoke vsys can then use these centrally provided groups in security policies.
Detailed Configuration of User-ID Hub
Configuring a User-ID Hub involves steps on the designated hub vsys and on the spoke vsys that will consume the mappings.
Prerequisites:
- The Palo Alto Networks firewall must be operating in multi-vsys mode .
- Network connectivity must exist between the hub vsys's management interface (or a dedicated service route interface) and any User-ID sources (e.g., domain controllers, User-ID agents).
- Spoke vsys must be able to communicate with the hub vsys internally for mapping synchronization. This is typically handled by the firewall's internal data plane.
1. Configuring the User-ID Hub VSYS:
This vsys will collect and distribute User-ID information.
Using the PAN-OS Web Interface:
-
Navigate to
Device > Virtual Systems. - Select the vsys you want to designate as the hub. Click its name to edit.
- In the vsys properties window, check the User-ID Hub checkbox.
- Click OK .
-
Configure User-ID sources on this hub vsys:
-
Go to
Device > User Identification. -
Under
User Mapping
, configure methods like Server Monitoring (for AD), User-ID Agents, GlobalProtect settings, etc. For example, to add an AD server for monitoring:
- Click Palo Alto Networks User-ID Agent Setup (gear icon).
- Under Server Monitoring , add your LDAP server profile and configure AD domain controllers to monitor.
-
If centralizing group mapping, configure Group Mapping settings under
Device > User Identification > Group Mapping Settingson the hub vsys. Add your LDAP server profiles and define group include lists.
-
Go to
- Commit the changes.
Using the PAN-OS CLI:
admin@PA-VM> configure Entering configuration mode [edit] admin@PA-VM# set vsys <hub_vsys_name> system user-id-hub yes admin@PA-VM# set vsys <hub_vsys_name> user-id-agent <agent_name> server <server_ip_or_name> admin@PA-VM# set vsys <hub_vsys_name> user-id-agent <agent_name> type "active-directory" admin@PA-VM# set vsys <hub_vsys_name> group-mapping <group_mapping_profile_name> group-include-list <list_name> admin@PA-VM# commit
2. Configuring Spoke VSYS:
Spoke vsys are configured to receive mappings from the hub. They should not be configured as User-ID hubs themselves, and generally should not have overlapping User-ID source configurations unless specific local overrides are intended.
Using the PAN-OS Web Interface:
-
Navigate to
Device > Virtual Systems. - Select a spoke vsys. Click its name to edit.
- Ensure the User-ID Hub checkbox is unchecked .
- No specific configuration is typically needed on the spoke vsys to "connect" to the hub for IP-to-user mappings; this is handled automatically once a hub is designated on the chassis.
- For spoke vsys to use centralized group mappings, they might need to be configured to fetch group lists from the hub, depending on the PAN-OS version and specific feature. Refer to "Group Mapping Centralization for Virtual System Hubs" documentation. Typically, the spoke vsys will automatically have access to groups published by the hub.
- Commit the changes if any were made.
Using the PAN-OS CLI:
Ensure the spoke vsys is not a hub:
admin@PA-VM> configure Entering configuration mode [edit] admin@PA-VM# set vsys <spoke_vsys_name> system user-id-hub no admin@PA-VM# commit
3. Verifying Configuration:
After configuration, verify that mappings are being shared:
-
On the hub vsys, check if it's learning mappings:
show user ip-user-mapping all
-
On a spoke vsys, check if it's receiving mappings from the hub:
show user ip-user-mapping all
Look for mappings where the source indicates they came from the hub (e.g., "Hub"). -
Verify group availability on spoke vsys:
show user group list
Groups learned by the hub should be visible here.
Expanded Key Functions of the User-ID Hub
- Centralized Mapping Collection & Aggregation: The User-ID Hub vsys serves as the single point of contact for all configured User-ID sources. It actively polls (e.g., Server Monitoring of Active Directory) or listens (e.g., Syslog, User-ID Agent connections) for user mapping data. This data, typically IP-address-to-username mappings, is compiled into a central table on the hub vsys.
- Efficient Mapping Distribution to Spoke VSYS: Once mappings are collected, the hub vsys efficiently distributes them to all other (spoke) vsys on the same physical Palo Alto Networks firewall. This distribution occurs internally within the firewall's chassis, minimizing network overhead. Spoke vsys automatically receive these mappings without needing individual configurations to fetch them.
-
Mapping Conflict Resolution and Precedence:
PAN-OS has a clear precedence order for User-ID mappings. If a spoke vsys learns an IP-to-user mapping from one of its own locally configured User-ID sources (e.g., a local Captive Portal or a directly connected User-ID agent specific to that vsys), this
local mapping takes precedence
over any mapping for the same IP address received from the User-ID Hub. This allows for granular control and overrides where necessary but generally, for simplicity, it's best to rely on hub mappings.
Gotcha! (Palo Alto Networks): If a spoke vsys is not using the expected user mapping from the hub, verify that there isn't a local, more specific mapping overriding it. Use
show user ip-user-mapping ip <IP_ADDRESS>on the spoke vsys and check the 'Source' or 'Vsys' field for the mapping's origin. - Streamlined Operational Efficiency and Reduced Overhead: By centralizing User-ID source configuration (like AD server monitoring profiles, User-ID agent settings, syslog parsing profiles) on the hub vsys, administrators avoid duplicating these configurations across potentially dozens of spoke vsys. This significantly reduces administrative overhead, simplifies troubleshooting, and minimizes the load on external systems like domain controllers.
- Centralized Group Mapping Distribution: Beyond individual user mappings, the User-ID Hub can also centralize the retrieval and distribution of user group information. The hub vsys connects to directory services (e.g., Active Directory via LDAP), retrieves group memberships, and makes these groups available to all spoke vsys. This allows security policies on spoke vsys to reference user groups without each spoke needing its own LDAP server profile and group mapping configuration.
Mermaid Diagram: User-ID Hub Architecture and Mapping Flow
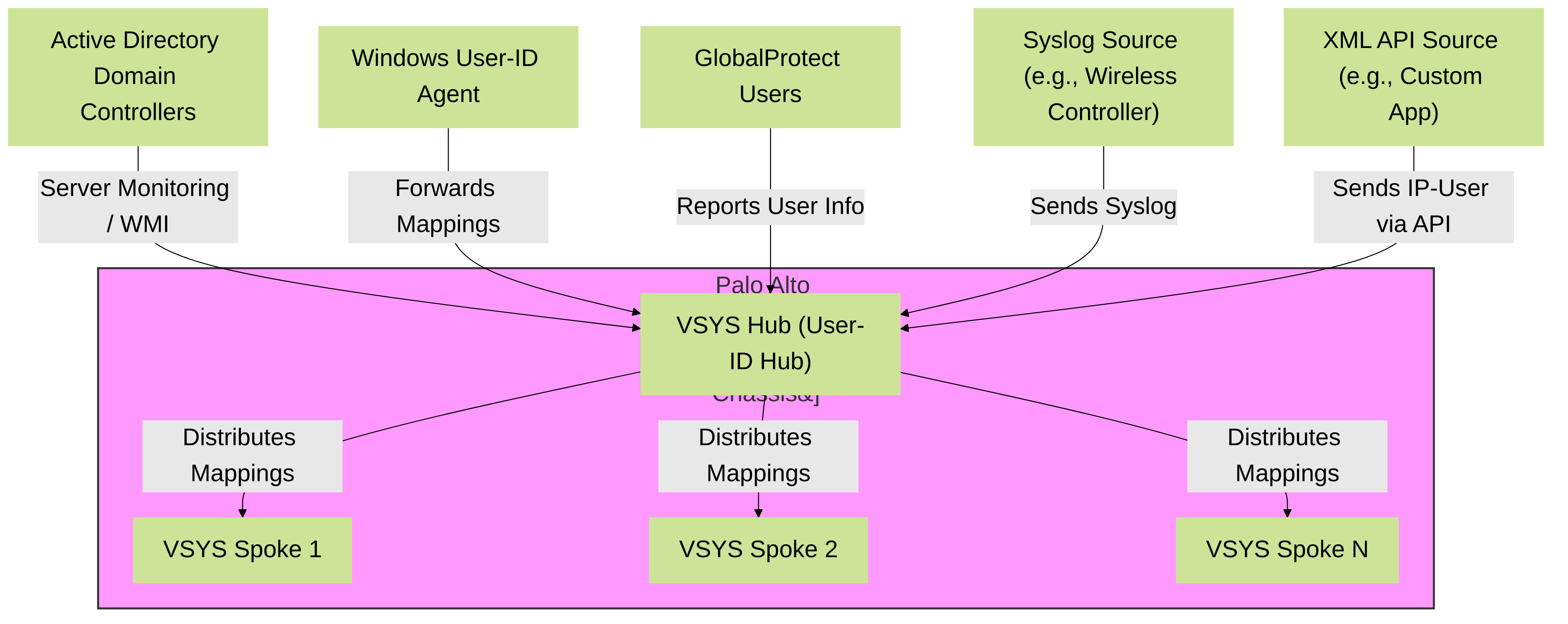
This diagram illustrates a Palo Alto Networks firewall in multi-vsys mode. The VSYS Hub is designated as the User-ID Hub. It collects IP-to-user mappings from various sources like Active Directory (via direct server monitoring or a Windows User-ID Agent), GlobalProtect VPN users, Syslog sources, and XML API feeds. The User-ID Hub then distributes these consolidated mappings to all spoke vsys (VSYS Spoke 1, 2, N) within the same firewall chassis.
Mermaid Sequence Diagram: User-ID Mapping Source Aggregation on Hub
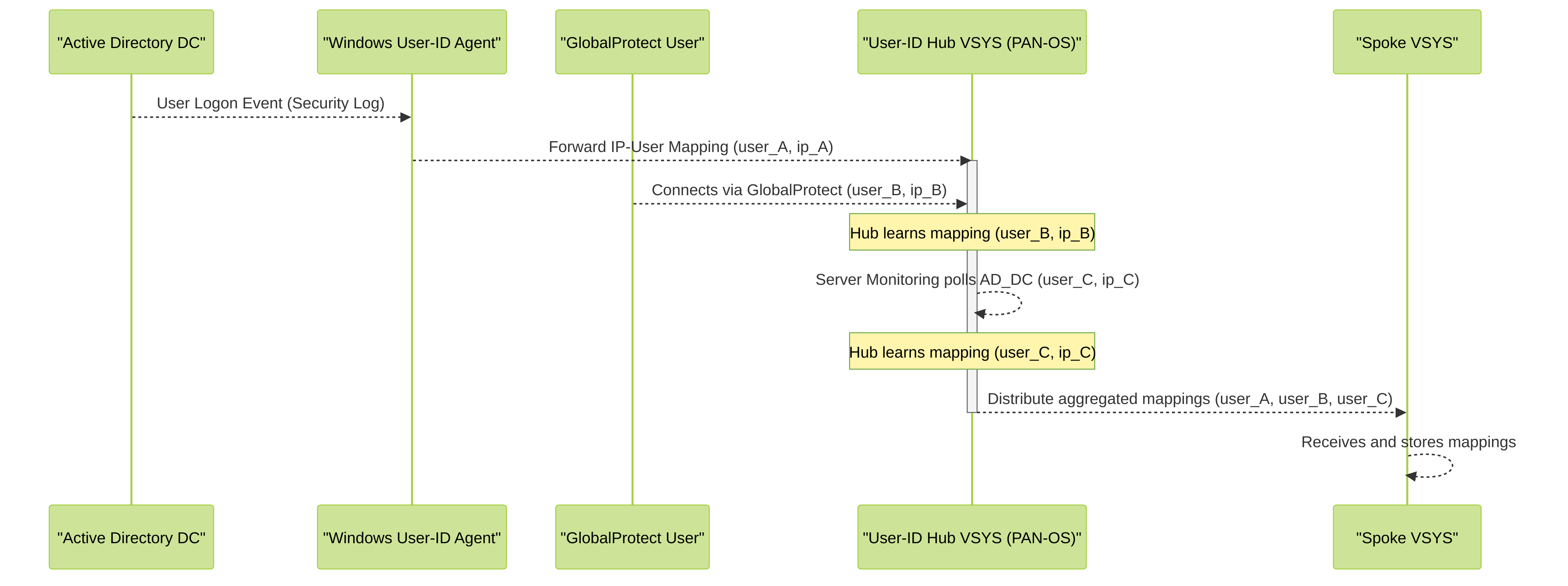
This sequence diagram shows how the User-ID Hub VSYS on a Palo Alto Networks firewall aggregates mappings from different sources. A Windows User-ID Agent forwards a mapping from an AD DC. A GlobalProtect user connection provides another mapping directly. The Hub VSYS itself might also use Server Monitoring to learn mappings. All these collected mappings are then distributed to spoke vsys.
Mermaid Diagram: Traffic Flow & Mapping Lookup with User-ID Hub
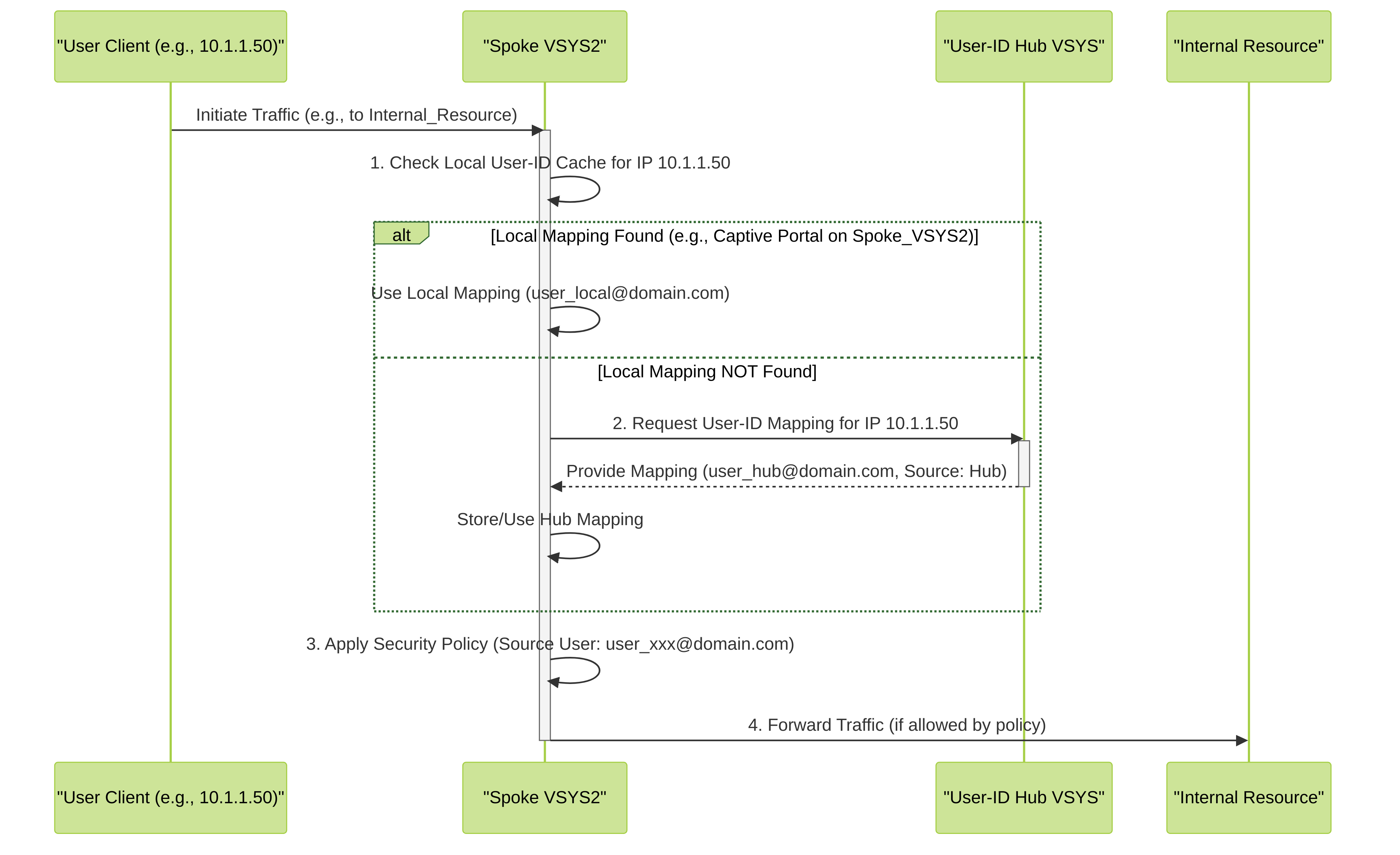
This diagram illustrates the traffic flow when a user initiates traffic through a spoke vsys (VSYS2) in an environment with a User-ID Hub. 1. VSYS2 first checks its local User-ID cache for a mapping associated with the source IP address. 2. If a local mapping exists (e.g., learned via a Captive Portal directly on VSYS2), it takes precedence. 3. If no local mapping is found, VSYS2 queries the User-ID Hub VSYS for the mapping. The hub provides the mapping if available. 4. VSYS2 then uses the identified user in its security policy evaluation before forwarding traffic to the resource.
Monitoring and Troubleshooting User-ID Hub
Effective monitoring and troubleshooting are key to maintaining a healthy User-ID Hub deployment.
PAN-OS Web Interface Monitoring:
-
Hub VSYS:
-
Monitor > User-ID: Shows current IP-to-user mappings, group mappings, and server monitoring status. -
Monitor > Logs > User-ID: Displays User-ID related events, such as users logging in/out, agent connections, and errors. -
Device > User Identification > User Mapping > Palo Alto Networks User-ID Agent Setup (gear icon): Check connectivity status for Server Monitoring and connected User-ID Agents.
-
-
Spoke VSYS:
-
Monitor > User-ID: View mappings. Pay attention to the "Source" or "Vsys" column to distinguish hub-provided mappings from local ones. -
Monitor > Logs > User-ID: Can show events related to receiving mappings or local User-ID activities.
-
PAN-OS CLI Commands:
These commands are invaluable for troubleshooting. Remember to execute them in the correct vsys context (
set system session vsys <vsys_name>
if not in the global context or using a vsys-specific CLI prompt).
On the User-ID Hub VSYS:
-
show user ip-user-mapping all: Displays all learned IP-to-user mappings. -
show user ip-user-mapping ip <ip_address>: Shows mapping for a specific IP. -
show user group list: Lists all known groups. -
show user group name <group_name>: Shows users in a specific group. -
show user server-monitor statistics: Status of AD server monitoring. -
show user user-id-agent statistics: Status of connected User-ID agents. -
show system setting user-id-agent user-id-hub: Verifies if the vsys is configured as a hub. -
debug user-id dump {ip-user-map | group-map | server-monitor-state | user-id-agent-state}: Dumps detailed internal User-ID information. Use with caution. -
less mp-log useridd.log: View the User-ID daemon logs for detailed troubleshooting. -
less mp-log gpsrv.log: View GlobalProtect service logs if GP is a mapping source.
show user ...
commands for verifying User-ID operations. Knowing where to find logs (
useridd.log
) is also important for deeper troubleshooting.
On a Spoke VSYS:
-
show user ip-user-mapping all: View mappings. Check source to ensure hub mappings are present. -
show user ip-user-mapping ip <ip_address>: Check a specific mapping and its source. -
show user group list: Verify groups from the hub are available.
Common Issues and Resolutions:
-
Mappings not appearing on Spoke VSYS:
- Verify the Hub VSYS is correctly designated and has learned mappings.
- Ensure no network connectivity issues are preventing internal communication (rare, as it's chassis-internal).
- Check for PAN-OS software bugs (consult release notes).
-
Incorrect user identified on Spoke VSYS:
-
Check for a local mapping on the spoke vsys that is overriding the hub mapping. Use
show user ip-user-mapping ip <ip_address>on the spoke. - Investigate the source of the incorrect mapping on the hub or the local spoke.
-
Check for a local mapping on the spoke vsys that is overriding the hub mapping. Use
-
Hub VSYS not learning mappings from a source (e.g., AD):
- Check connectivity from hub vsys to the source (e.g., ping, LDAP connectivity to DC).
- Verify credentials and permissions for Server Monitoring or User-ID Agent.
-
Examine
useridd.logon the hub for errors related to that source.
-
Groups not available on Spoke VSYS:
- Ensure Group Mapping is configured correctly on the Hub VSYS and it can connect to the LDAP server.
- Verify the "Group Mapping Centralization for Virtual System Hubs" feature behavior for your PAN-OS version.
Benefits of Using a User-ID Hub
- Simplified Management: Centralizes configuration of User-ID sources, reducing administrative effort compared to managing each vsys individually.
- Consistent Policy Enforcement: Ensures all vsys utilize the same user identity information, leading to uniform security policy application.
- Improved Scalability: Ideal for large deployments with many vsys, as it avoids redundant polling and agent connections from each vsys.
- Reduced Load on Directory Services: Only the hub vsys queries directory services (like Active Directory), lessening the impact on these critical infrastructure components.
- Enhanced Visibility: Provides a consolidated view of user activity across the multi-vsys environment through the hub's User-ID logs and monitoring tools.
- Resource Optimization: Optimizes firewall resource usage by preventing redundant User-ID processes across multiple vsys.
Limitations and Considerations
- Single Point of Failure (for User-ID data): If the User-ID Hub vsys experiences issues with its User-ID process (useridd), it can affect user identification across all spoke vsys relying on it. However, the underlying vsys itself remains operational. High Availability (HA) for the firewall chassis is recommended for overall resilience.
- Mapping Precedence: While providing flexibility, the local mapping precedence on spokes can sometimes lead to unexpected behavior if not managed carefully. Documentation and clear operational procedures are important.
- Inter-VSYS Traffic for User-ID Data: Although internal, there is some processing overhead for distributing mappings. This is generally minimal but should be considered in extremely high-scale scenarios.
- PAN-OS Version Dependencies: Specific features, like the extent of group mapping centralization, can vary slightly between PAN-OS versions. Always consult the documentation for your specific PAN-OS release.
- Complexity in Mixed Environments: If some vsys need highly customized or independent User-ID setups, integrating them with a hub model requires careful planning.
- Not a Replacement for Panorama User-ID Redistribution: The User-ID Hub is for sharing mappings *within* a single multi-vsys firewall. For sharing User-ID information *between different firewalls* (physical or virtual), Panorama's User-ID redistribution features or inter-firewall User-ID agent configurations are used.
PCNSE Exam Focus: User-ID Hub
For the PCNSE certification, a thorough understanding of the User-ID Hub is essential. Key areas include:
- Purpose and Use Cases: Why and when to implement a User-ID Hub in a multi-vsys environment.
-
Configuration:
- Designating a vsys as a User-ID Hub (GUI and CLI).
- Configuring User-ID sources (Server Monitoring, User-ID Agents, GlobalProtect, etc.) on the hub.
- Understanding spoke vsys configuration (or lack thereof for receiving mappings).
- Group Mapping centralization concepts.
-
Operation:
- How mappings are collected, aggregated, and distributed.
- The concept of mapping ownership and precedence (local vs. hub).
-
Monitoring and Troubleshooting:
-
Key CLI commands (
show user ip-user-mapping,show user group list,show user server-monitor statistics, etc.) on both hub and spoke vsys. - Interpreting User-ID logs.
- Common troubleshooting scenarios and how to approach them.
-
Key CLI commands (
- Comparison/Distinction: Differentiating User-ID Hub (intra-firewall) from Panorama User-ID redistribution or inter-firewall User-ID agent setups (inter-firewall).
Expect scenario-based questions where you need to identify the correct configuration, troubleshoot a User-ID problem involving a hub, or explain the flow of User-ID information.