Palo Alto Networks User-ID™ Acquisition Methods and Concepts
The Foundation: Understanding Palo Alto Networks User-ID™
User-ID is a cornerstone technology in Palo Alto Networks Next-Generation Firewalls (NGFWs) that enables the identification and control of network traffic based on users and groups, rather than solely on IP addresses. In modern dynamic network environments where users may have multiple devices or IP addresses can change frequently, User-ID provides the crucial link between network activity and actual users. This empowers administrators to create granular security policies, gain deep visibility into user behavior, and generate comprehensive reports for compliance and threat analysis.
- Core Purpose: To map IP addresses to individual usernames, thereby enabling user-based security policies, application visibility (App-ID™), threat prevention (Content-ID™), and detailed logging/reporting within the PAN-OS® environment.
- Enhanced Visibility: With User-ID, logs and reports transition from IP-centric views to user-centric insights. This allows for a clearer understanding of who is accessing which applications, from where, and what potential threats are associated with specific user activities. For example, seeing "John Doe accessed Salesforce" is far more actionable than "10.1.1.5 accessed 34.203.250.5".
- Granular Policy Control: Security policies can be defined based on Active Directory (or other LDAP-compliant directory) usernames and group memberships. This allows for precise control, such as permitting only the "Engineering" group to access internal Git repositories or restricting the "Interns" group from accessing sensitive financial applications protected by App-ID policies.
- Simplified Forensics and Reporting: When a security incident occurs, User-ID helps quickly identify the involved user, significantly speeding up investigation and remediation. User-based reports are also invaluable for demonstrating compliance with regulatory requirements (e.g., PCI DSS, HIPAA) by showing who accessed specific data.
- User Mapping Table: The PAN-OS firewall maintains a dynamic User-ID mapping table that stores the association between IP addresses and usernames. This table is constantly updated by the various acquisition methods. Mappings have a configurable timeout (default typically 45 minutes, but adjustable in `Device > User Identification > User-ID Timeouts`), after which they expire if not refreshed. The table size limit depends on the firewall model.
- Group Mapping: Complementary to IP-to-user mapping, User-ID leverages Group Mapping to retrieve user group information from directory services like LDAP (e.g., Microsoft Active Directory). This allows policies to be based on group membership (e.g., "sales-team", "finance-dept"), simplifying administration and scaling policy management. This is configured under `Device > User Identification > Group Mapping Settings`.
The User-ID technology consists of two main functional components within PAN-OS:
- IP Address-to-User Mapping: The process of discovering which user is associated with which IP address. This is achieved through various acquisition methods detailed in subsequent sections. The PAN-OS management plane process `useridd` is primarily responsible for managing these mappings.
- User-to-Group Mapping: The process of retrieving user group memberships from a directory server (e.g., Active Directory via LDAP) to enable group-based policies. This also involves the `useridd` process interacting with configured LDAP server profiles.
User-ID mappings can be collected by the PAN-OS integrated User-ID agent running directly on the firewall (for methods like Server Monitoring of Domain Controllers, Client Probing, Syslog Listening) or by dedicated Palo Alto Networks User-ID agents (Windows-based or Linux-based). These mappings are then shared with the firewall's dataplane for high-speed policy enforcement. Panorama™ can also play a role in redistributing User-ID information in large-scale deployments.
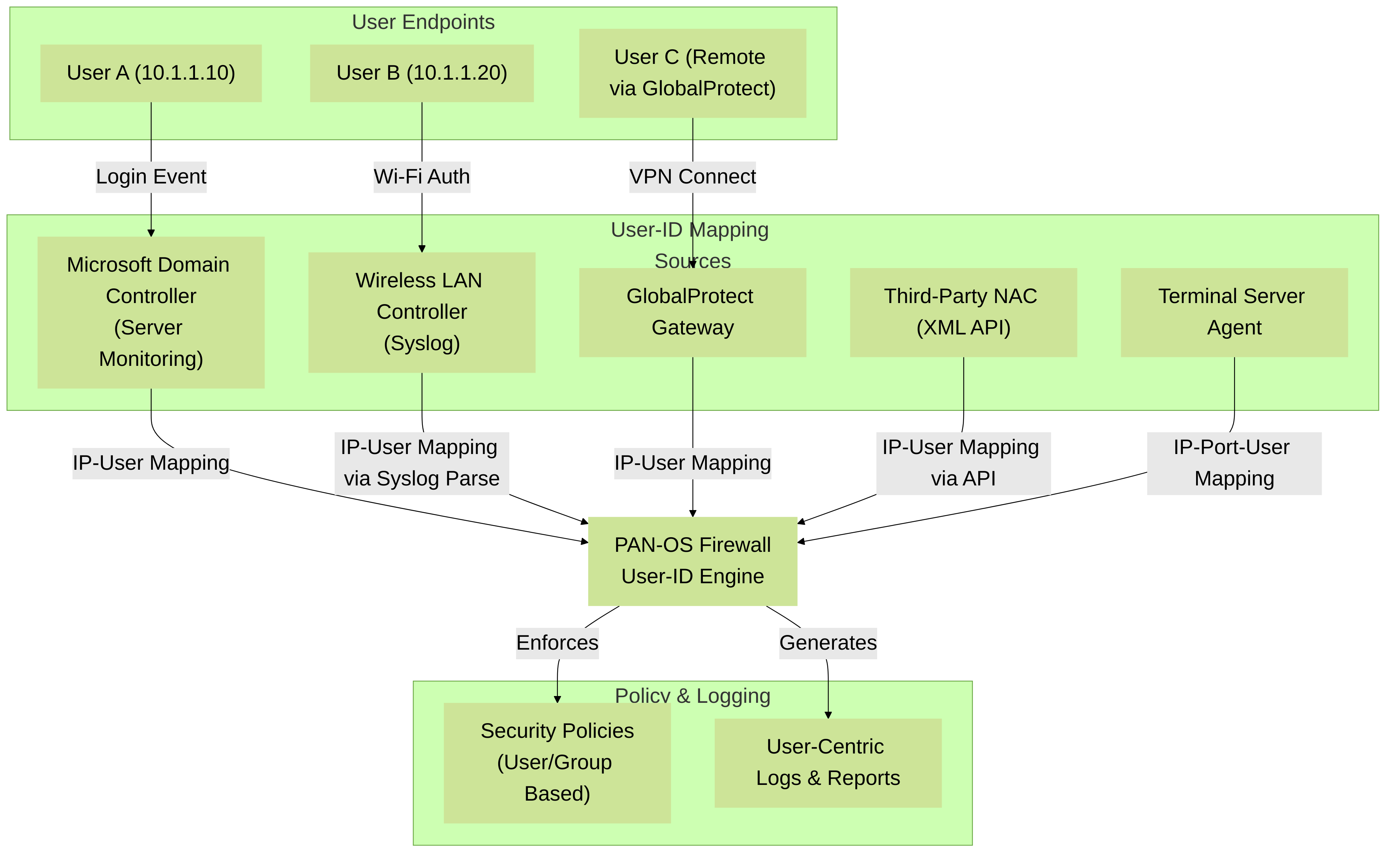
Palo Alto Networks User-ID Ecosystem Overview: Various sources provide IP-to-User mappings to the PAN-OS Firewall, which then enables user-based security policies and detailed logging.
For more detailed information, refer to the official Palo Alto Networks documentation: User-ID Overview - Palo Alto Networks
IP Address-to-User Mapping Acquisition Methods
1. Server Monitoring (Security Log Monitoring)
Server Monitoring is a common and often preferred passive method for obtaining User-ID mappings in environments with Microsoft Windows domain controllers, Microsoft Exchange Servers, or Novell eDirectory servers. The Palo Alto Networks User-ID Agent (a piece of software installed on a Windows member server) or the PAN-OS Integrated User-ID feature (agentless, running directly on the firewall for Windows Domain Controllers) monitors server security event logs for successful user login events.
How it works (Windows User-ID Agent Example):

Palo Alto Networks User-ID Acquisition via Server Monitoring using a Windows User-ID Agent. The agent monitors Domain Controller security logs for login events to map IPs to users.
Key Components and Configuration (PAN-OS):
- User-ID Agent (Windows-based): Installed on a Windows server (typically a member server, not a DC itself for performance and security best practices). Requires a service account with appropriate permissions (e.g., member of "Event Log Readers" and "Distributed COM Users" on DCs, plus permissions to read NetBIOS information if client probing is enabled on the agent). Configuration: `Device > User Identification > User-ID Agents`. Here you define the connection to your User-ID agent(s), specifying its IP and pre-shared key if used.
- PAN-OS Integrated User-ID (Agentless for Domain Controllers): The firewall itself can directly monitor Windows Domain Controller security logs using WMI or WinRM. This reduces the need for a separate Windows User-ID agent for this specific function. Requires a service account with permissions to read security event logs on the DCs. Configuration: `Device > User Identification > User Mapping`, then click the gear icon for "Palo Alto Networks User-ID Agent Setup" and navigate to "Server Monitoring". Add your DCs here.
- Supported Servers: Microsoft Domain Controllers (most common), Microsoft Exchange Servers (for Outlook Web Access, ActiveSync logins, using Event ID 1310 for IIS successful auth on Client Access Servers), and Novell eDirectory.
- Permissions: The service account used by the User-ID agent or integrated User-ID needs specific permissions to read security event logs (e.g., Windows Event ID 4624 for successful logons, 4768/4769 for Kerberos TGT/Service Ticket requests, 4634 for logoff).
-
Monitored Event IDs (Windows):
- Successful Logon: 4624 (Windows Vista/2008 and later), 672 (Windows 2003/XP Kerberos AS_REQ), 528/540 (Windows 2003/XP NTLM).
- Successful Logoff: 4634, 4647.
- Kerberos Ticket Events: 4768 (AS_REQ), 4769 (TGS_REQ), 4770 (Renew), 4771 (Kerberos Pre-Authentication failed - can indicate issues).
- Exchange CAS logs (IIS logs): Event ID 1310 (MSExchange Autodiscover) or specific IIS log fields.
CLI Commands for Troubleshooting (PAN-OS):
> show user server-monitor state all // For PAN-OS Integrated Server Monitoring status
> show user user-id-agent state all // For Windows User-ID Agent connection status
> show user ip-user-mapping ip 192.168.1.100 // To check a specific IP mapping
> debug user-id dumpన్యాయserver-monitorన్యాయstatistics // Detailed stats for integrated server monitor
> less mp-log useridd.log // Check for errors related to server monitoring
2. Syslog Integration (Syslog Listener & Parser)
Many network devices and applications generate syslog messages containing username and IP address information upon user authentication or activity. The Palo Alto Networks firewall can be configured as a syslog listener. It then uses configurable parsing profiles (Syslog Parse Profiles) with regular expressions (regex) to extract this information and create User-ID mappings. The firewall's management plane process `useridd` handles the listening and parsing.
Common Use Cases:
- Wireless LAN Controllers (WLCs) authenticating Wi-Fi users (e.g., Cisco WLC, Aruba).
- VPN concentrators (non-GlobalProtect Palo Alto Networks solutions).
- Network Access Control (NAC) solutions (e.g., Aruba ClearPass, Cisco ISE sending syslog upon successful authentication).
- Proxy servers that log username and client IP.
- Custom applications that log user sessions via syslog.
- Linux/UNIX servers using `sshd` or `login` that log to syslog.
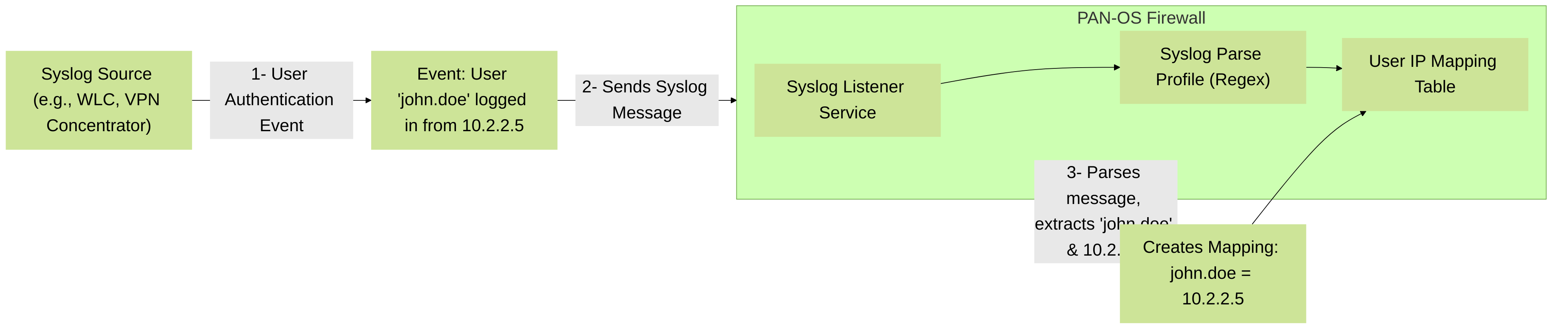
Palo Alto Networks User-ID Acquisition via Syslog Integration. The firewall parses syslog messages from other devices to extract user and IP information.
Configuration (PAN-OS):
- Configure a Syslog Server Profile for Listening: `Device > Server Profiles > Syslog`. Add a new profile. This profile itself doesn't define parsing, just that the firewall is listening. Ensure the firewall's management interface or a service-route enabled dataplane interface is reachable by the syslog source on the chosen port (typically UDP 514).
-
Create a User-ID Syslog Filter Profile:
`Device > User Identification > User Mapping` (click gear icon for "Palo Alto Networks User-ID Agent Setup") `> Syslog Filters`. Click "Add".
- Provide a Profile Name.
- Select the Syslog Server Profile created in step 1.
- Event Regex: A regex pattern to match the entire syslog line that contains the user login event. Example: `.*User (\S+) logged in from IP (\d+\.\d+\.\d+\.\d+).*`
- Username Regex: A regex pattern to extract the username from the matched line. This often uses a capture group from the Event Regex. Example: `User (\S+)` (where `\S+` captures non-space characters, representing the username). Specify the capture group number if needed.
- Address Regex: A regex pattern to extract the IP address. Example: `IP (\d+\.\d+\.\d+\.\d+)` (where `\d+\.\d+\.\d+\.\d+` captures an IP address). Specify the capture group number.
- Strip Domain: Optionally strip domain prefixes/suffixes from usernames.
- Configure the Sending Device: Ensure the external device (e.g., WLC) is configured to send syslog messages containing the necessary user authentication information to the firewall's listening interface IP and port.
CLI Commands for Troubleshooting (PAN-OS):
> show user ip-user-mapping all type SYSLOG
> less mp-log useridd.log // Check for syslog processing messages, parsing errors
> test user-id syslog-parse filter <profile_name> syslog-message "<sample_log_line_from_source_device>" // Test regex parsing
> show counter global filter delta yes aspect useridd // Look for syslog_event_received, syslog_event_parsed, syslog_mapping_added counters
3. Authentication Portal (Captive Portal)
The Authentication Portal, commonly known as Captive Portal, is an active authentication method within PAN-OS. When traffic from an unknown IP address (i.e., an IP address not yet mapped to a user) attempts to access resources and matches an Authentication Policy rule, the firewall can redirect the user's web browser to a login page hosted on the firewall. The user must then provide valid credentials (validated against an Authentication Profile) to gain access, and upon successful authentication, a User-ID mapping is created.
Common Use Cases:
- Guest user access for internet or specific resources.
- Authenticating users on non-domain-joined devices or BYOD devices.
- Fallback authentication method when passive methods (like Server Monitoring) fail or are not available for certain user segments.
- Enforcing Multi-Factor Authentication (MFA) for certain traffic by integrating the Authentication Profile with an MFA server (e.g., RADIUS with Duo, Okta, Azure MFA; SAML).
- Identifying users before allowing access to specific sensitive applications.
_wo_May_19_2025_07-02PM.png)
Palo Alto Networks Authentication Portal (Captive Portal) workflow. Users are redirected to a login page to establish User-ID mappings.
Configuration (PAN-OS):
- Configure an Authentication Profile: `Device > Authentication Profile`. Defines how users are authenticated (e.g., LDAP for Active Directory, RADIUS, SAML for SSO, Kerberos, local user database). Specify server details, bind accounts, etc. For MFA, this profile would point to an MFA provider like a RADIUS server integrated with Duo/Okta, or a SAML IdP.
- Configure an Authentication Sequence (Optional): `Device > Authentication Sequence`. Allows chaining multiple authentication profiles. The firewall tries them in order until one succeeds.
-
Configure Captive Portal Settings:
`Device > User Identification > Captive Portal Settings`.
- Specify the Authentication Profile (or Sequence) to use.
-
Mode:
- Transparent: The firewall attempts to inject JavaScript into HTTP traffic to prompt for credentials without a full redirect. Less reliable, often problematic with HTTPS.
- Redirect: The firewall redirects the user's browser to a specific IP address and port on one of its interfaces (the Captive Portal page). This is the most common and reliable mode. Requires an interface to be configured for Captive Portal redirection.
- Redirect Host: The FQDN or IP address of the firewall interface hosting the portal.
- Idle Timer / Timer: How long the mapping stays active.
- Customize the portal page appearance (response pages, logos - optional). `Device > Response Pages`.
- Assign an SSL/TLS Service Profile for HTTPS portal access (highly recommended). `Device > Certificate Management > SSL/TLS Service Profiles`. Ensure the certificate is trusted by client browsers.
-
Create an Authentication Policy:
`Policies > Authentication`.
- Define source/destination zones, addresses, users (can be "unknown" or "any" to trigger for unmapped users), and services (typically HTTP/HTTPS).
- Action: Set to the configured Captive Portal method (e.g., "Browser Challenge" which uses the global settings, or specify a redirect if multiple portal configs exist via Authentication Enforcement objects).
- Specify the Authentication Profile/Sequence if not using the global Captive Portal setting.
- Timeout Settings: Override global User-ID timeouts if needed for Captive Portal users specifically.
4. Windows User-ID Agent for Terminal Services / Multi-User Citrix Environments
In environments like Microsoft Remote Desktop Services (RDS), Citrix XenApp/XenDesktop (Virtual Apps and Desktops), Azure Virtual Desktop (AVD), or other multi-user shared host environments, multiple users connect to a single server and therefore share the same IP address from the firewall's perspective. Standard User-ID methods would map this shared IP to only one user (typically the first or last to log in), leading to incorrect policy enforcement and logging for subsequent users.
To address this, the Palo Alto Networks Windows User-ID Agent can be installed directly on these multi-user servers (Terminal Servers, Citrix worker hosts, AVD session hosts). The agent is configured in "Terminal Server" mode to allocate a unique range of source TCP/UDP ports for each user session. It then reports user-to-IP- and-port mappings to the PAN-OS firewall.
How it works:
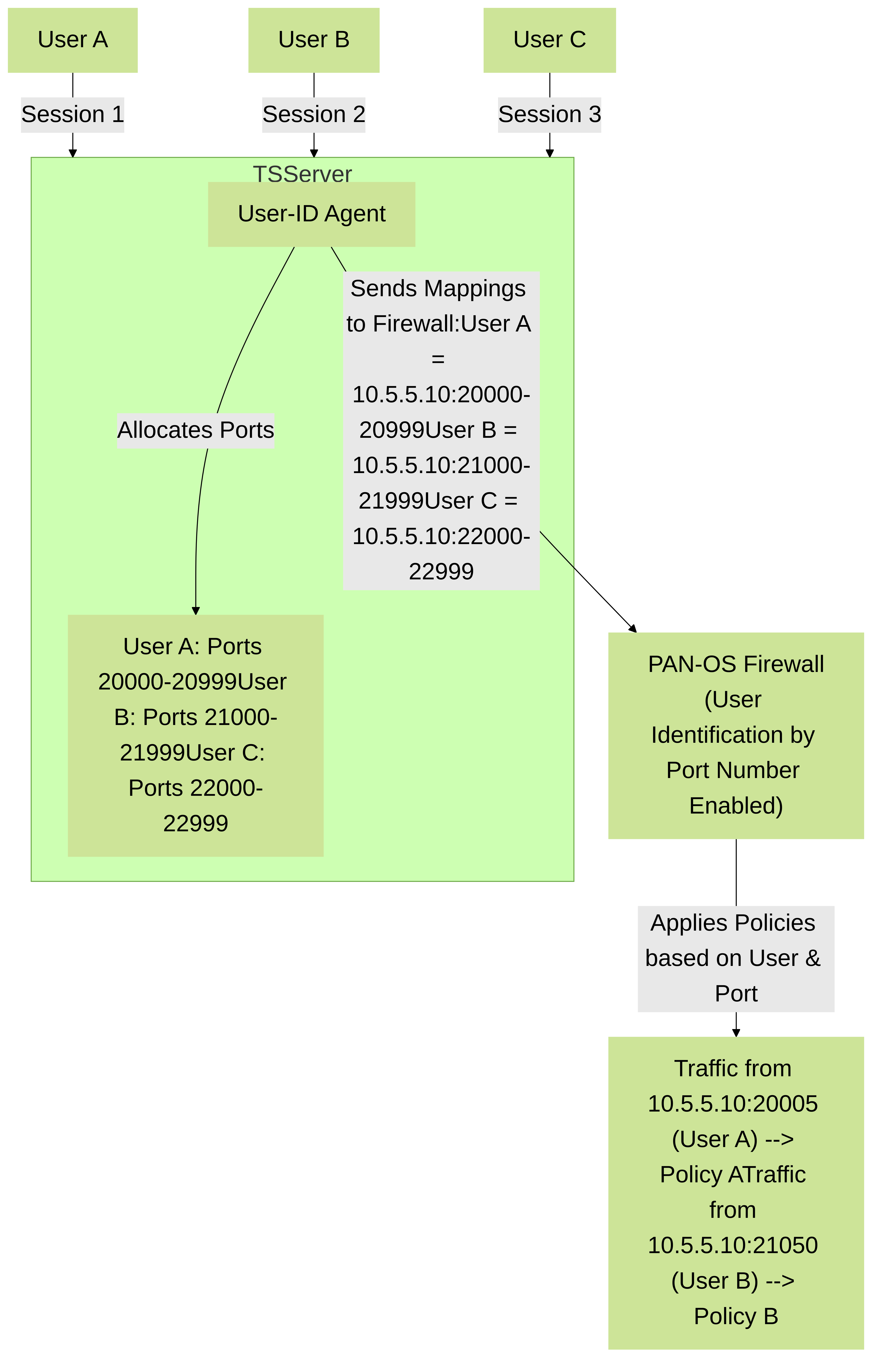
Palo Alto Networks User-ID Agent for Terminal Services. The agent assigns unique source port ranges to differentiate users sharing a single IP address on a multi-user host.
Configuration (PAN-OS and TS Agent):
-
On the Terminal Server / Citrix Host:
- Install the Palo Alto Networks Windows User-ID Agent software.
- During agent configuration (or by editing its `UserIDAgentConfig.xml` or via the agent GUI), enable the "Terminal Server" option (or "Citrix" option, functionality is similar).
- Define the Starting Port Number (e.g., 20000) and the Number of Ports per User (e.g., 1000 or 2000). The agent will dynamically assign blocks of these ports to user sessions. Ensure this port range doesn't conflict with well-known ports or other applications on the server. The total range available is typically up to port 65535.
- Configure the agent to send mappings to the IP address(es) of the PAN-OS firewall(s) or Panorama.
-
On the PAN-OS Firewall:
-
Enable User Identification by Port Number:
`Device > Setup > Session > Session Settings > Enable User Identification by Port Number`.
Check this box.
CRITICAL (Palo Alto Networks): This setting is global and absolutely essential for the firewall to utilize port-based User-ID mappings from the TS Agent. Without it, the port information in the mappings will be ignored. This is a common point of failure in TS User-ID deployments if missed.
- Configure the firewall to receive mappings from this User-ID agent: `Device > User Identification > User-ID Agents`. Add the Terminal Server agent as a source by specifying its IP address. The firewall must be able to reach the agent on its listening port (default TCP 5007).
-
Enable User Identification by Port Number:
`Device > Setup > Session > Session Settings > Enable User Identification by Port Number`.
Check this box.
5. GlobalProtect™
GlobalProtect is Palo Alto Networks' comprehensive solution for securing remote and mobile users, providing VPN access, endpoint security posture checking (HIP), and consistent policy enforcement. When users connect to the corporate network via the GlobalProtect client (agent) or clientless VPN, User-ID mappings are automatically and reliably created on the PAN-OS firewall acting as the GlobalProtect Gateway.
- GlobalProtect Agent (Client VPN): When a user establishes a VPN tunnel using the GlobalProtect agent, the agent authenticates the user against an Authentication Profile configured on the GlobalProtect Portal and/or Gateway. Upon successful authentication, the GlobalProtect Gateway on the firewall receives the username and the inner (tunnel) IP address assigned to the client from its IP pool. The firewall then creates a User-ID mapping for this user and their VPN IP. This is a very reliable source of User-ID.
- Clientless VPN (Portal-based Access): For browser-based access to specific internal web applications, users authenticate through the GlobalProtect Portal. Upon successful authentication, a User-ID mapping is established for the duration of their session, using their public source IP address (the IP address from which they are accessing the portal).
- Internal Gateways: GlobalProtect can also be used with internal gateways for on-network users. When users authenticate to an internal gateway (often for HIP checks or to enforce consistent policy for internal users), User-ID mappings are created using their internal LAN IP address.
GlobalProtect also provides Host Information Profile (HIP) data (e.g., OS patch level, antivirus status, disk encryption). This HIP data can be used in conjunction with User-ID in Security policy rules for more granular policy control based on endpoint security posture (e.g., allow access only if user is 'JohnDoe' AND their endpoint has 'AV-Installed-And-Updated').
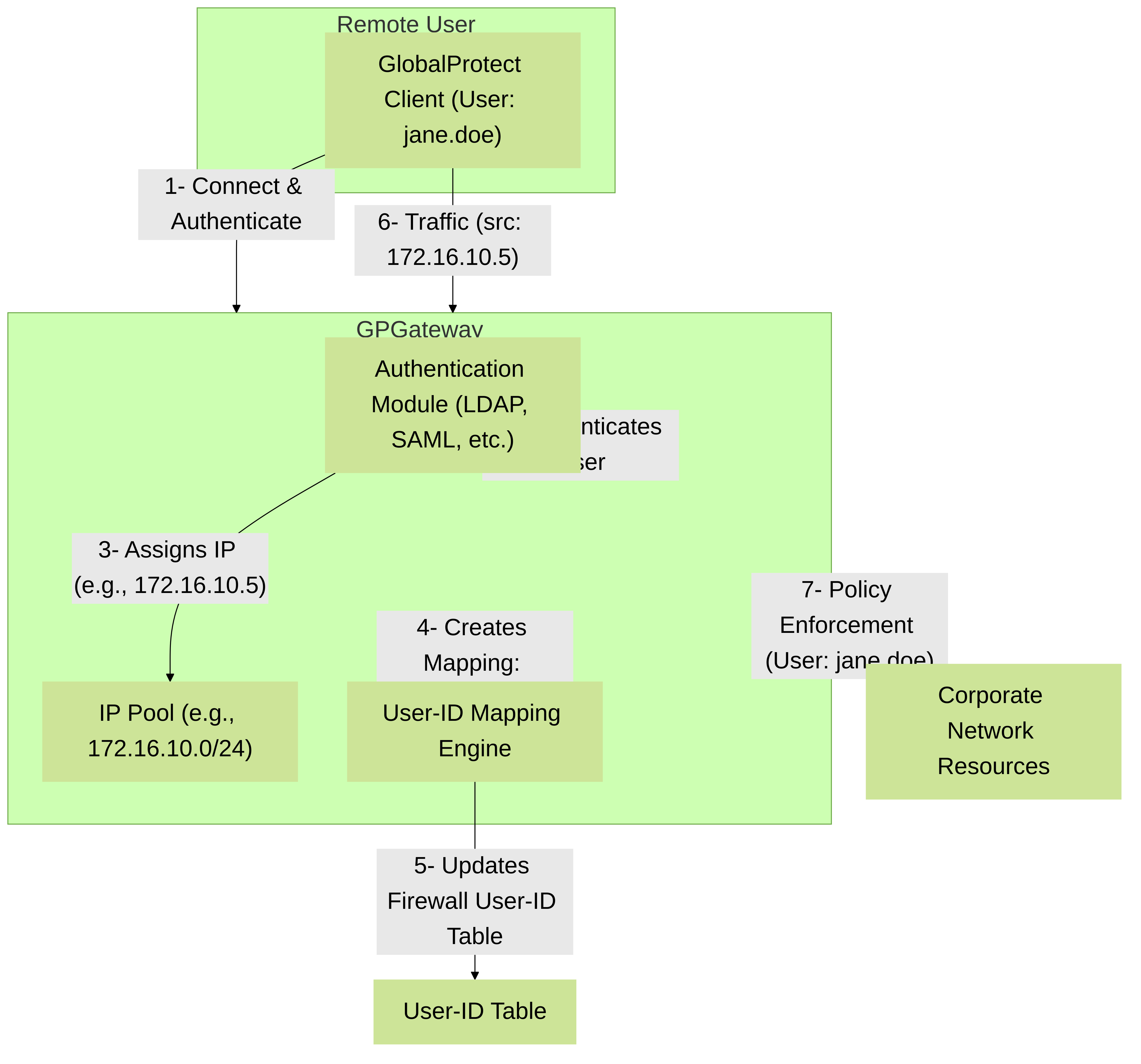
Palo Alto Networks GlobalProtect User-ID Mapping Flow. User authentication via GlobalProtect automatically generates User-ID mappings on the Gateway.
Configuration (PAN-OS):
- GlobalProtect Portal and Gateway configurations are set up under `Network > GlobalProtect > Portals` and `Network > GlobalProtect > Gateways` .
- Authentication Profiles (e.g., LDAP, SAML, RADIUS, Kerberos) are associated with the Portal and Gateway configurations to authenticate users. These are configured under `Device > Authentication Profile` .
- User-ID is inherently integrated; no separate User-ID specific configuration is typically needed for GlobalProtect to provide mappings beyond the standard GlobalProtect setup. The firewall automatically creates mappings upon successful GP authentication.
- HIP Objects and Profiles can be configured under `Objects > GlobalProtect > HIP Objects` and `Objects > GlobalProtect > HIP Profiles` to be used in policy.
6. XML API for User-ID
The Palo Alto Networks PAN-OS XML API provides a programmatic and flexible way to send User-ID mappings to the firewall. This is particularly useful for integrating with third-party authentication systems, custom applications, NAC solutions that don't use syslog, or for scripting User-ID updates based on various triggers.
An external system (e.g., a NAC server, a custom script, a Wi-Fi authentication system, even another User-ID Agent redistributing mappings) can send an XML message to the firewall containing username, IP address, and type (login or logout).
XML Message Structure Example (Login):
<uid-message>
<version>2.0</version>
<type>update</type>
<payload>
<login>
<entry name="CORP\user.name" ip="192.168.1.50" timeout="3600" />
<entry name="another.user@example.com" ip="10.10.20.30" vlan_id="100" timeout="7200" />
<!-- Multiple entries can be included -->
</login>
</payload>
</uid-message>
For logout:
<uid-message>
<version>2.0</version>
<type>update</type>
<payload>
<logout>
<entry name="CORP\user.name" ip="192.168.1.50" />
</logout>
</payload>
</uid-message>
Sending the Mapping:
The XML payload is typically sent via an HTTP POST request to the firewall's API endpoint. The URL is usually `https://
Example using `curl`:
curl -k -X POST "https://firewall.example.com/api/?type=user-id&action=set&key=YOUR_API_KEY&cmd=<uid-message>...</uid-message>"
Configuration (PAN-OS):
- Ensure API access is enabled on the firewall's management interface or a dedicated service interface. `Device > Setup > Management > Management Interface Settings > HTTPS` (ensure enabled).
- Create an administrator role with specific XML API permissions. For User-ID, the minimum privilege is usually under `XML API > User-ID Agent`. `Device > Admin Roles`.
- Create an administrator account and assign this role to it. `Device > Administrators`.
-
Generate an API key for this administrator account. This can be done via the CLI (`request api-key generate username
`) or by the admin logging into the GUI and generating it themselves if permissions allow. The key can also be retrieved via API request `type=keygen`. - Configure permitted IP addresses for API access for enhanced security: `Device > Setup > Management > Management Interface Settings > Permitted IP Addresses`. Add the IP of the system sending API requests.
For detailed API documentation, refer to the PAN-OS XML API Guide on the Palo Alto Networks TechDocs site. Send User Mappings to User-ID Using the XML API - Palo Alto Networks
7. Client Probing (WMI and NetBIOS)
Client Probing is an agentless method where the PAN-OS firewall (via its integrated User-ID component) or a Windows User-ID Agent actively queries Windows client machines to determine the currently logged-in user. This is an "active" method as the firewall/agent initiates the connection to the client.
- Windows Management Instrumentation (WMI) Probing: The preferred method for probing modern Windows clients. It queries for user login session information (e.g., `Win32_ComputerSystem` for username, or enumerating explorer.exe process owner). Requires administrative credentials on the client and specific firewall exceptions.
-
NetBIOS Probing:
A legacy method used for older Windows clients or as a fallback. It queries for NetBIOS session information (e.g., `nbtstat -A
`). Less reliable and provides less detailed information.
Client Probing is typically used as a secondary or tertiary method for subnets where Server Monitoring might not be effective (e.g., workgroup environments, or to catch users missed by security log monitoring due to log rollover or if DCs are unavailable). It can also be used to verify mappings from other sources.
How it works:
- The firewall or User-ID Agent identifies an unmapped IP address initiating traffic, or an existing mapping that needs verification.
- It sends a WMI query (or NetBIOS probe) to that client's IP address.
- The Windows client responds with information about the logged-in user(s) if the query is successful and permitted.
- A User-ID mapping is created or updated.
Configuration (PAN-OS for Integrated User-ID or on Windows User-ID Agent):
- Enable Client Probing: On the Windows User-ID Agent: Configure under the "Client Probing" tab. On PAN-OS Integrated User-ID: `Device > User Identification > User Mapping` (click gear icon for "Palo Alto Networks User-ID Agent Setup") `> Client Probing`. Select WMI and/or NetBIOS.
- Service Account: A domain account with administrative privileges on the client workstations (or at least permissions to perform remote WMI queries and NetBIOS lookups) is required. This account is configured in the User-ID Agent settings or the PAN-OS integrated User-ID configuration that defines WMI credentials.
-
Client-Side Requirements:
- Windows Firewall on clients must allow incoming WMI (TCP port 135 for RPC Endpoint Mapper, and a dynamic range of high TCP ports for DCOM/WMI itself) and/or NetBIOS (UDP 137, 138, TCP 139) traffic from the firewall/User-ID agent. Group Policy can be used to configure these exceptions.
- Remote Procedure Call (RPC) service and WMI service must be running on clients.
- File and Printer Sharing (for NetBIOS) should be enabled if using NetBIOS probing.
- User Account Control (UAC) can interfere with remote WMI unless specific GPO settings are applied (e.g., `LocalAccountTokenFilterPolicy=1` for non-domain admin accounts, though using a domain admin for the service account is more common).
- Include/Exclude Networks: Specify which subnets should be probed. It's crucial to limit probing to only necessary subnets to reduce network load and potential security exposure.
8. X-Forwarded-For (XFF) Headers
When user traffic passes through an internal explicit proxy server before reaching the Palo Alto Networks firewall, the source IP address seen by the firewall in the packet header will be that of the proxy server, not the original client. This effectively hides the true client IP and breaks standard User-ID mapping, as all users behind the proxy would appear to come from the proxy's IP.
If the proxy server is configured to insert the original client's IP address into an HTTP header, typically the
X-Forwarded-For
(XFF) header, the PAN-OS firewall can be configured to extract and use this XFF IP address for User-ID mapping lookup and for policy enforcement.
Important Distinction: XFF itself doesn't provide the username . It provides the original client IP . This original client IP, once extracted from the XFF header, then needs to be mapped to a username using one of the other User-ID acquisition methods (e.g., Server Monitoring for that client IP, GlobalProtect if it was a GP user, etc.). The firewall will use the XFF IP to query its User-ID mapping table.
Configuration (PAN-OS):
- Enable XFF Processing for User-ID: `Device > Setup > Content-ID > Content-ID Settings` (tab) `> User Identification`. Check "Use X-Forwarded-For Header in User-ID".
- Enable XFF in Security Policy (for logging/visibility): In Security Policy rules, you can also specify to use XFF as the source IP. When a rule is configured with "Source User" and traffic arrives via a proxy, this setting ensures the correct client IP is used for the User-ID mapping lookup for that policy. The logging will also reflect the XFF IP as the source. This is generally controlled by enabling the option above. For logging, `Log Setting` profiles can be configured to log XFF if present.
- Specify Trusted Proxy IPs (Optional but Highly Recommended): Still under `Device > Setup > Content-ID > Content-ID Settings > User Identification`, you can specify "X-Forwarded-For Trusted Source Addresses". Add the IP addresses of your trusted internal proxy servers. This is a security measure to ensure the firewall only trusts and uses XFF headers originating from these known proxies, preventing malicious users from spoofing XFF headers. If this list is empty, the firewall may trust XFF from any source, which is a security risk.
- Custom HTTP Header (Optional): If your proxy uses a different header than XFF (e.g., `True-Client-IP`), you can specify this custom header name in the same configuration area.
X-Forwarded-For: client1_ip, proxy1_ip, proxy2_ip
). By default, PAN-OS uses the
first (leftmost)
IP address in the list as the original client IP. Ensure your proxy configuration and firewall expectations align. If the "Use X-Forwarded-For Header in User-ID" setting is not enabled, User-ID will always use the layer 3 source IP from the packet, which would be the proxy IP.
9. VM Information Sources (Indirect User-ID Context)
In virtualized environments, PAN-OS can integrate with various orchestration and virtualization platforms to learn about virtual machine attributes. These platforms include VMware (NSX-T, NSX-V, vCenter/ESXi), Cisco ACI, OpenStack, AWS, Azure, GCP, and Kubernetes.
While not a direct IP-to-username mapping method in the traditional User-ID sense (i.e., it doesn't typically provide
DOMAIN\username
), these integrations allow the firewall to gather rich metadata about VMs, including tags, VM names, OS type, and other attributes defined in the virtualization platform.
This information is primarily used for creating Dynamic Address Groups (DAGs) . DAGs are address groups whose membership is dynamically updated based on this VM metadata (e.g., tags like "App=WebServer-Prod", "OS=Linux", "Department=Finance-VMs"). Security policies can then use these DAGs as source or destination, allowing for automated policy updates as VMs are created, destroyed, or their attributes change.
Indirect User-ID Context: If VM tags are consistently applied based on user roles, primary users, or departmental ownership (e.g., a tag "Owner=JohnDoe" or "Team=Engineering"), these tags, when pulled into DAGs, can indirectly contribute to user-aware policies. For instance, a policy could allow traffic from a DAG representing "Engineering-Team-VMs". However, to identify the specific user logged *into* such a VM, traditional User-ID methods (like Server Monitoring within the VM's OS, or GlobalProtect if the user connects via GP to access the VM console) would still be necessary.
Configuration (PAN-OS):
- Connections to these platforms are configured under `Device > VM Information Sources` (for VMware, AWS, Azure, GCP, etc.) or through specific plugins like the one for Kubernetes, often configured under `Device > User Identification > User Mapping` (for the Kubernetes plugin specifically, it's more about monitoring service/pod IPs and labels).
- For each source, you provide connection details and credentials.
- The firewall then polls the source periodically to retrieve VM information.
- DAGs are created under `Objects > Address Groups` , where you specify matching criteria based on the learned tags/attributes.
10. HTTP Header Insertion (Using User-ID Information)
This is not a User-ID acquisition method, but rather a way to utilize existing User-ID mappings for downstream systems. Once the Palo Alto Networks firewall has successfully identified a user for a specific IP address (through any of the acquisition methods), it can be configured to insert the username (and optionally other attributes like group memberships or client OS) into HTTP headers of traffic destined for downstream web servers or other applications.
This allows these downstream applications to leverage the user identity information, already ascertained by the firewall, for their own logging, personalization, access control, or auditing purposes, without needing to perform their own separate authentication for already authenticated users.
Common Headers Used:
-
X-Authenticated-User: Often used for the username. -
X-Authenticated-Groups: For group memberships (can be a custom name). - Other custom header names can be defined.
Configuration (PAN-OS):
- This feature is configured within an Authentication Profile . `Device > Authentication Profile > Select_Your_Profile > Advanced` tab.
-
Under the "HTTP Header Insertion" section:
- Enable "Generate identity information in HTTP headers for authenticated users".
-
Specify the header name for "Username Header" (e.g.,
X-Authenticated-User). - Optionally, specify the header name for "Group Header" and "Client OS Header".
- Choose which attributes to include (e.g., Username, Domain, Groups, Client OS).
- You can specify a "Header Separator" if multiple groups are inserted into a single header.
- This Authentication Profile must then be referenced in an Authentication Policy rule . The rule should match the traffic for which you want headers inserted. `Policies > Authentication`. The Authentication Policy rule's action doesn't necessarily need to be a challenge (like Captive Portal); it can be "default" if the user is already known via other means, and the header insertion will still occur if the referenced Authentication Profile is configured for it. However, it's often used in conjunction with an Authentication Enforcement object that specifies the profile.
Palo Alto Networks User-ID Agents: A Closer Look
Palo Alto Networks provides different types of User-ID "agents" or mechanisms that facilitate the collection of IP-to-user mappings. The term "agent" can refer to dedicated software or integrated PAN-OS functionality.
| Feature/Agent Type | Description | Deployment | Primary Use Cases | Key Considerations (Palo Alto Networks Specific) |
|---|---|---|---|---|
| Windows User-ID Agent | Software installed on a Windows member server. Can monitor multiple Domain Controllers, Exchange Servers, perform client probing (WMI/NetBIOS), act as a syslog listener (for specific syslog formats it understands), and redistribute mappings. Also used on Terminal Servers/Citrix hosts for port-based user mapping. | Installed on a dedicated Windows Server (recommended for performance and stability) or a member server. Not typically on a DC itself. | Server Monitoring (DCs, Exchange), Client Probing, Terminal Server/Citrix multi-user identification, Syslog Listener (limited, PAN-OS integrated syslog is more flexible), User-ID redistribution to firewalls or Panorama. | Requires a Windows host. Service account with appropriate permissions needed (e.g., Event Log Readers, admin on clients for probing). Can centralize collection for multiple firewalls. Agent version should be compatible with PAN-OS. Listens on TCP port 5007 by default for firewall connections. |
| PAN-OS Integrated User-ID | Functionality built directly into PAN-OS on the firewall. No separate agent software installation needed for these specific functions. The `useridd` process on the management plane handles these tasks. | Runs on the PAN-OS firewall itself. | Server Monitoring (directly queries Windows DCs via WMI/WinRM), Client Probing (WMI/NetBIOS directly from firewall), Syslog Listener (firewall acts as syslog server with configurable parsers), Captive Portal. | Simplifies deployment for certain scenarios by eliminating a separate server. Firewall management plane resources are used, so consider firewall model and load. May have scale limitations compared to a dedicated Windows agent for very large environments (e.g., number of DCs monitored). |
| Linux User-ID Agent | Software installed on a Linux server. Can act as a syslog listener and parse custom log files using regex to extract user mappings. It then forwards these mappings via XML API to the PAN-OS firewall(s). | Installed on a Linux server. Often distributed as a script or package. | Syslog collection from various non-Windows sources (e.g., custom apps, RADIUS accounting logs), custom log file parsing, environments preferring Linux-based tools. | Offers flexibility for non-Windows environments or custom integrations. Uses the PAN-OS XML API to send mappings to the firewall, requiring an API key with User-ID permissions. Regex configuration is key. |
| Panorama User-ID Redistribution | Panorama™ network security management platform can collect User-ID mappings (e.g., from Windows User-ID Agents, firewalls acting as agents, or firewalls learning mappings locally via GlobalProtect) and redistribute them to its managed firewalls. | Configured on Panorama and managed firewalls. Firewalls/agents are configured to send mappings to Panorama; Panorama then pushes them to other selected firewalls. | Centralized User-ID management and distribution in large-scale deployments with Panorama. Ensures consistent User-ID information across many firewalls. Reduces direct connections from agents to all firewalls. | Requires Panorama. Efficient for consistent User-ID information across many firewalls in different device groups or locations. Panorama acts as a "User-ID hub". Configure User-ID Redistribution settings on Panorama. |
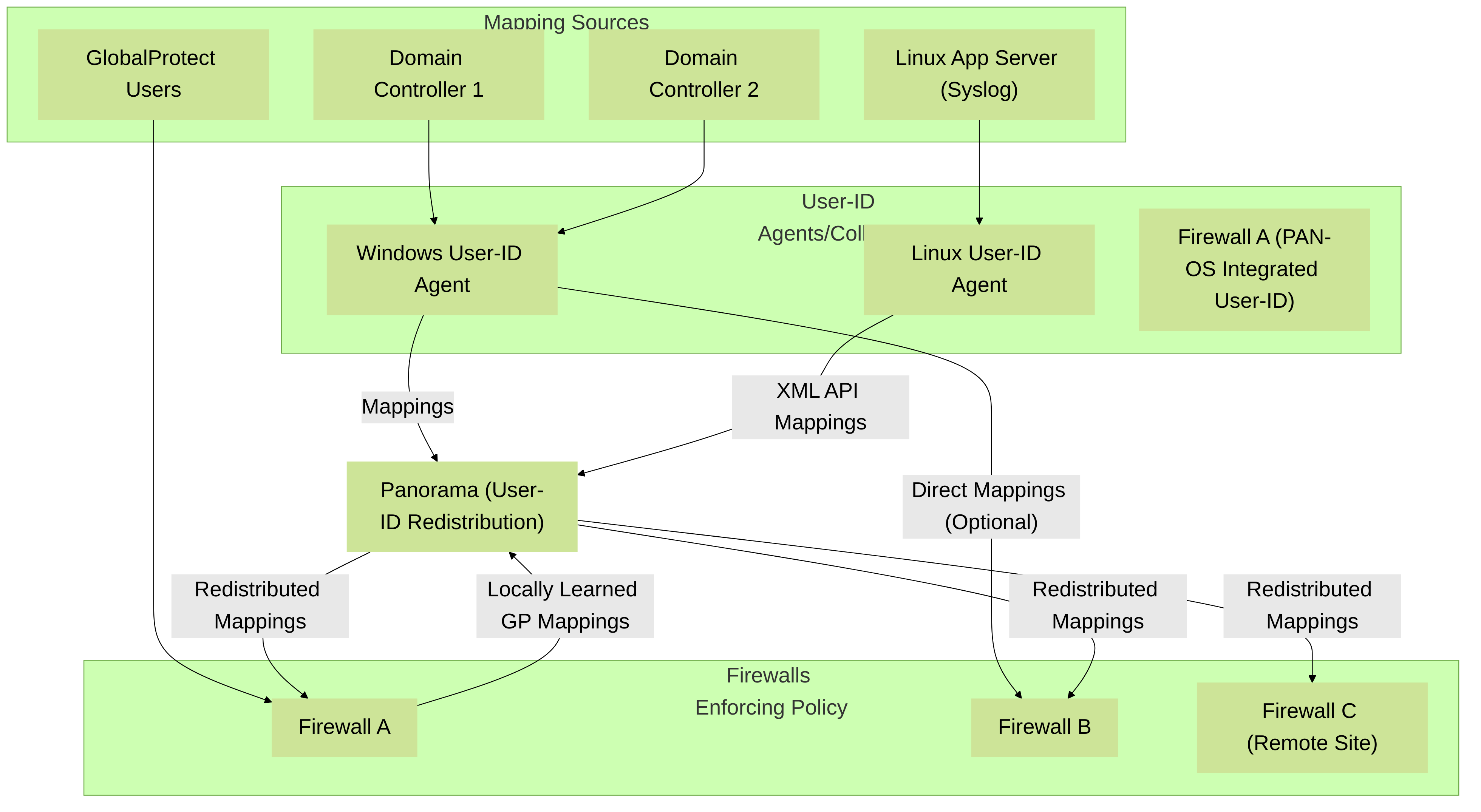
Palo Alto Networks User-ID Collection and Redistribution Architecture example, highlighting roles of different agents (Windows, Linux, PAN-OS Integrated on Firewall A) and Panorama for centralized redistribution to multiple firewalls.
User-ID Mapping Table and Timeouts
The PAN-OS firewall maintains a User-ID mapping table that stores the discovered IP address-to-username associations. Each entry in this table has a timeout value, and the table itself has a maximum capacity depending on the firewall model.
-
Mapping Table Viewing:
You can view the current mappings using PAN-OS CLI commands or in the GUI.
- GUI: `Monitor > Logs > User-ID` (shows recent mapping events) or for current state, often checked via CLI or by looking at traffic logs where username is populated. Some PAN-OS versions might have a direct table view under `Monitor > User-ID` .
-
CLI:
> show user ip-user-mapping all // Shows all mappings > show user ip-user-mapping ip 10.1.1.50 // Shows mapping for a specific IP > show user ip-user-mapping user CORP\\jsmith // Shows mappings for a specific user > show user ip-user-mapping count yes // Shows count of current mappings by type
- User-ID Timeout (Mapping Timeout): This is the duration for which an IP-to-user mapping remains active in the firewall's table if it's not refreshed by a new event from a User-ID source. If a user logs off and a logoff event is detected, the mapping is removed. If no logoff event is detected and no refresh occurs, the mapping expires after this timeout. Configuration: `Device > User Identification > User-ID Timeouts`. Here you can set the "User Identification Timeout (minutes)". The default is often 45 minutes but can be adjusted.
- User-ID Agent Cache Timeout: The Windows User-ID Agent also has its own cache and timeout settings. These should generally align with or be understood in relation to the firewall's User-ID timeout.
- Idle Timeout vs. User-ID Timeout: It's important to distinguish between session idle timeouts (configured in `Device > Setup > Session > Session Settings`, determining how long a TCP/UDP session can be idle before being closed by the firewall) and User-ID mapping timeouts (how long an IP-to-user mapping is considered valid in the User-ID table). They are independent settings. A user's mapping can expire even if they have active sessions, potentially leading to those sessions losing user context if not handled carefully.
- Mapping Refresh: Active User-ID methods (like Server Monitoring detecting ongoing Kerberos ticket renewals from a DC, or GlobalProtect agent heartbeats/rekeys) will refresh mappings, extending their lifetime in the table before the timeout is reached. For passive methods like syslog, a new syslog message for the same user@IP would refresh it.
- Mapping Table Capacity: Each firewall platform has a maximum number of IP-to-user mappings it can store. This can be found in the Palo Alto Networks product datasheets. Exceeding this can lead to older mappings being overwritten or new mappings not being stored. CLI: `show system state | match uid.max_mapping` (approximate, consult official docs for exact model limits)
Group Mapping for Policy Enforcement
While IP-to-user mapping identifies the individual user (e.g., "CORP\john.doe"), Group Mapping allows the Palo Alto Networks firewall to retrieve that user's group membership information from directory services, primarily Microsoft Active Directory (via LDAP) or other LDAP-compliant servers. This is crucial for creating scalable and manageable security policies based on user roles and responsibilities (e.g., allow "Engineering" group to access dev servers, deny "Sales" group access to financial systems).
How it works:
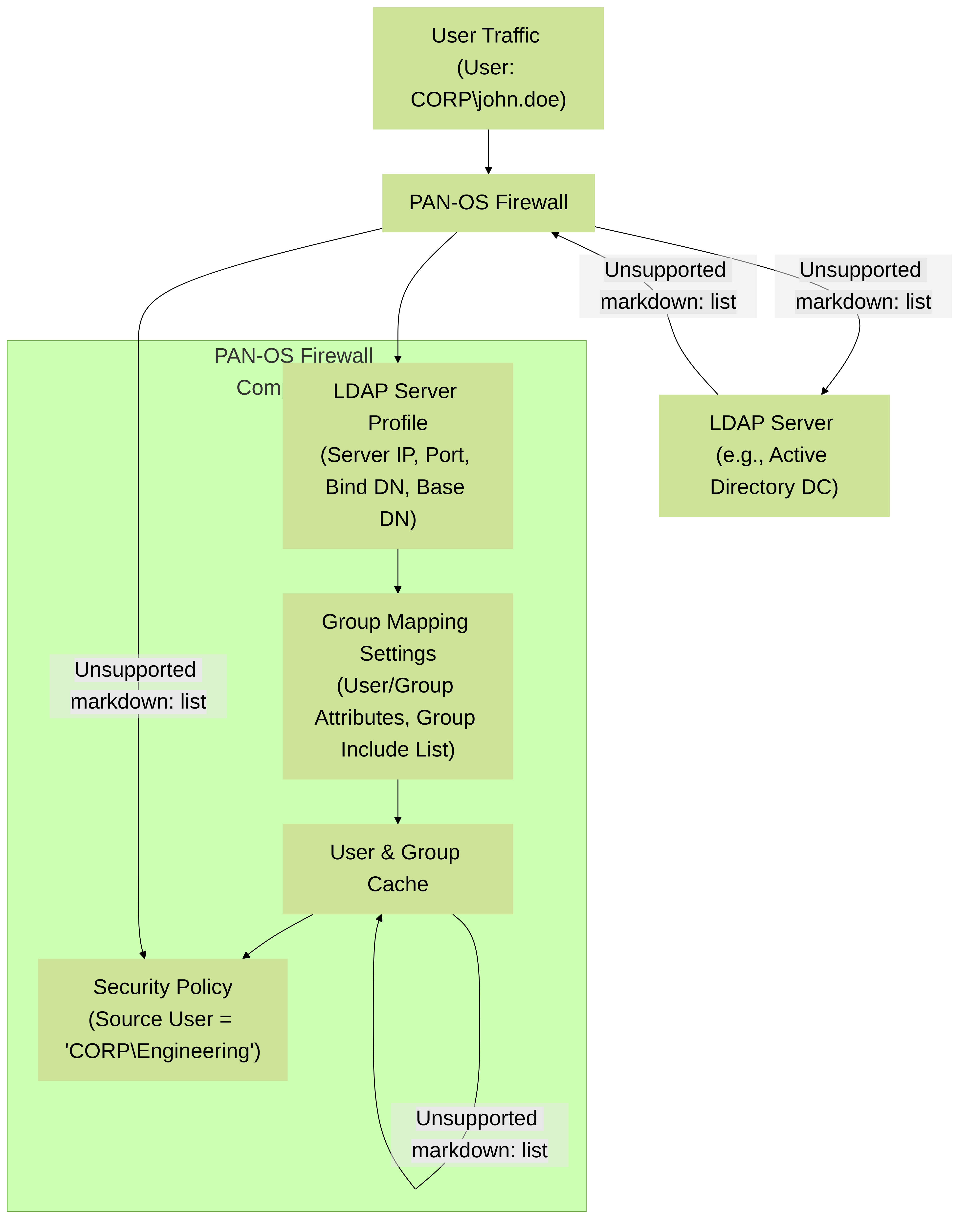
Palo Alto Networks Group Mapping Flow: The firewall queries an LDAP server to fetch user group memberships, stores them, and uses them for policy enforcement.
-
Configure an LDAP Server Profile:
`Device > Server Profiles > LDAP`.
This profile contains all necessary details for the firewall to connect to and query your directory server.
- Servers: IP address or FQDN of LDAP server(s) (e.g., Domain Controllers).
- Port: Typically 389 (LDAP) or 636 (LDAPS - recommended for encrypted communication).
- Type: `active-directory` for AD, or other options for different LDAP vendors.
- Base DN: The starting point in the LDAP tree for searches (e.g., `DC=corp,DC=example,DC=com`).
- Bind DN: The distinguished name of a service account used to bind (authenticate) to LDAP with permissions to read user and group attributes (e.g., `CN=svc-panldap,OU=ServiceAccounts,DC=corp,DC=example,DC=com`).
- Bind Password: Password for the service account.
- SSL/TLS Encryption: Recommended to use LDAPS or Start TLS. Requires importing the CA certificate that signed the LDAP server's certificate into the firewall's trust store if it's an internal CA.
- Verify Server Certificate (for LDAPS/Start TLS): Ensure this is checked for security.
-
Configure Group Mapping Settings:
`Device > User Identification > Group Mapping Settings`.
Create a new group mapping configuration.
- Name: A descriptive name for this mapping.
- Server Profile: Select the LDAP Server Profile created in step 1.
- User Domain: The NetBIOS domain name for users (e.g., `CORP`).
-
User Attributes:
- User Object Class: Typically `user`.
- User Name Attribute: The LDAP attribute for username (e.g., `sAMAccountName` - common for AD, or `uid`).
- Primary Username: Choose which AD attribute to use as the primary identifier for users in PAN-OS logs and policies (e.g., `sAMAccountName` or `userPrincipalName`). This choice is important for consistency.
-
Group Attributes:
- Group Object Class: Typically `group`.
- Group Name Attribute: The LDAP attribute for group name (e.g., `cn` or `sAMAccountName`).
- Group Member Attribute: The attribute in a group object that lists its members (e.g., `member`).
- User's Group Identifier Attribute: The attribute in a user object that lists its group memberships (e.g., `memberOf` - common for AD, or `primaryGroupID` combined with other lookups). For AD, `memberOf` is typical.
- Group Include List: Critically important for performance in large AD environments. Restrict which groups are retrieved by the firewall. You can list specific groups (e.g., `CN=Engineering,OU=UserGroups,DC=corp,DC=example,DC=com`) or use LDAP filters. If left empty, the firewall might try to fetch all groups, which can be resource-intensive.
- Custom Groups (Optional): Define custom groups based on LDAP filters for attributes other than standard group membership (e.g., create a group of users whose 'department' attribute is 'Marketing').
- Update Interval: How often the firewall queries the LDAP server to refresh group membership information (default typically 3600 seconds / 1 hour).
CLI Commands for Troubleshooting (PAN-OS):
> show user group list // Lists all groups known to the firewall from group mapping > show user group name "CORP\Engineering" // Shows members of a specific group as known by firewall > test user-id ldap-server-profile <LDAP_profile_name> username <DOMAIN\user_to_test> password // Test LDAP bind and user lookup > test user-id group-mapping state <group_mapping_profile_name> // Test group mapping sync status > debug user-id dumpన్యాయgroup-mappingన్యాయname// Dumps detailed state of group mapping > less mp-log useridd.log // Check for LDAP or group mapping related errors
For more detailed information, refer to the official documentation: Group Mapping - Palo Alto Networks
Troubleshooting User-ID
Effective User-ID troubleshooting in Palo Alto Networks environments involves a systematic approach, checking connectivity, configurations, and logs on the PAN-OS firewall, User-ID agents (if used), source systems (like Domain Controllers, syslog sources), and client machines.
Common PAN-OS CLI Commands for User-ID:
-
Mapping Verification:
-
show user ip-user-mapping all: Displays all current IP-to-user mappings. -
show user ip-user-mapping ip <ip_address>: Shows mapping for a specific IP. -
show user ip-user-mapping user <DOMAIN\user_or_UPN>: Shows mappings for a specific user. -
show user ip-user-mapping type <GP|CP|SYSLOG|AGENT|XMLAPI|TSAGENT>: Filter by mapping source. -
show user ip-user-mapping count yes: Displays counts of mappings by type.
-
-
Agent/Server Monitor Status:
-
show user server-monitor state all: Status of PAN-OS integrated server monitoring for DCs/Exchange. -
show user user-id-agent state all: Status of connected Windows User-ID Agents (or TS Agents). -
show user user-id-agent statistics name <agent_name>: Detailed stats for a specific agent connection.
-
-
Group Mapping:
-
show user group list: Lists all groups known from group mapping. -
show user group name "<DOMAIN\GroupName>": Shows members of a specific group. -
test user-id ldap-server-profile <profile> username <user> password: Test LDAP connectivity and credentials. -
test user-id group-mapping state <profile>: Check status of group mapping sync.
-
-
Syslog Parsing Test:
-
test user-id syslog-parse filter <filter_profile_name> syslog-message "<sample_log_line>"
-
-
Counters and Statistics:
-
show user counter: Displays various statistics related to User-ID mappings, sources, etc. -
show counter global filter delta yes aspect useridd: Real-time counters for the useridd process.
-
-
Debugging (Use with caution, preferably under TAC guidance):
-
debug user-id set level debug component <component_name>(e.g., server-monitor, agent, syslog) -
debug user-id dumpన్యాయmappingన్యాయip <ip_address>: Dumps detailed mapping info for an IP. -
debug user-id dumpన్యాయgroupన్యాయname "<DOMAIN\GroupName>": Dumps group info. - To clear debugs: `debug user-id set level info component all` or `debug user-id reset`
-
-
Clearing Mappings (for testing):
-
clear user-id all: Clears all User-ID mappings. -
clear user-id ip <ip_address>: Clears mapping for a specific IP. -
clear user-id user <DOMAIN\user>: Clears mappings for a specific user.
-
Key Log Files (PAN-OS):
- useridd.log: Main log for the User-ID daemon (`useridd`) on the management plane. Contains information about mapping acquisition, agent communication, timeouts, group mapping, syslog parsing, API updates, etc. CLI: `less mp-log useridd.log`
- authd.log: Authentication daemon log, relevant for Captive Portal, GlobalProtect authentication, and other authentication-related events. CLI: `less mp-log authd.log`
- Syslog (System Log): General system events, including API access attempts, User-ID agent connections/disconnections. GUI: `Monitor > Logs > System`. Filter for `( subtype eq 'user-id' )`.
- Traffic Logs: Check if usernames are being populated correctly in traffic logs for sessions. GUI: `Monitor > Logs > Traffic`.
General Troubleshooting Steps (Palo Alto Networks Context):
- Define the Scope: Is it one user, a group of users, a specific mapping method, or all User-ID?
-
Verify Connectivity:
- Firewall to Domain Controllers (for Server Monitoring: WMI/WinRM ports, LDAP/LDAPS ports).
- Firewall to User-ID Agent (TCP 5007 for Windows Agent).
- Firewall to Syslog sources (configured syslog port, typically UDP 514).
- Firewall/Agent to Clients (for Client Probing: WMI/NetBIOS ports).
- Firewall to LDAP server (for Group Mapping: LDAP/LDAPS ports).
- Use `ping` and `show arp` from firewall CLI, check `netstat` on agent/DC.
- Check Service Accounts: Confirm service accounts used for Server Monitoring, Client Probing, LDAP Bind have correct permissions, are not locked out, and passwords are not expired.
- Review Configurations: Double-check User-ID Agent settings, Server Monitoring config, Syslog Parse Profiles (especially regex), Captive Portal settings (Authentication Policy, Auth Profile), Group Mapping settings (LDAP attributes, Base DNs, Group Include List), User-ID Timeouts on the PAN-OS firewall.
-
Inspect Source System Logs:
- Domain Controller: Security Event Logs (ensure audit policies are enabled and relevant events like 4624, 4768, 4769 are being generated).
- Syslog Source: Verify it's sending messages in the expected format to the correct firewall IP/port.
- Windows User-ID Agent logs (on the agent server).
- Test Individual Components: Use PAN-OS CLI `test` commands for LDAP, group mapping, syslog parsing.
-
Isolate the Issue:
If multiple methods are used, try to determine which one is failing or providing incorrect information. Use `show user ip-user-mapping ip
` to see the `Type` of mapping. -
Packet Captures (Advanced):
On the firewall, capture traffic to/from DCs, agents, or syslog sources to see the raw communication.
GUI: `Monitor > Packet Capture`. CLI: `debug dataplane packet-diag set capture file
.pcap ...`
Best Practices for Palo Alto Networks User-ID Deployment
-
Use Multiple Methods Layered Appropriately:
Deploy a combination of User-ID acquisition methods for comprehensive coverage and resilience. For example:
- Primary: Server Monitoring (Domain Controllers for on-prem users), GlobalProtect (for remote/mobile users).
- Secondary: Syslog integration from WLCs or NAC. Authentication Portal for guests or unmapped BYOD.
- Tertiary/Specific Use: Terminal Server Agent for multi-user hosts. XML API for custom integrations. Client Probing only for specific, hard-to-map segments if necessary and with caution.
- Prefer Passive Methods: Prioritize passive methods like Server Monitoring (DC/Exchange logs), GlobalProtect, and Syslog Integration over active methods like Client Probing. Passive methods generally have less impact on network performance and client endpoints, and fewer client-side dependencies (like firewall rules).
-
Secure User-ID Agents and API Access:
- If using Windows User-ID Agents, install them on secured member servers (not DCs). Keep the agent software updated.
- Restrict PAN-OS XML API access to known, trusted IP addresses using "Permitted IP Addresses" under management settings. Use strong, unique API keys with least privilege (dedicated admin role for API). Regenerate API keys if compromised. Use HTTPS for API communication.
- Service Account Security (Least Privilege): Use dedicated service accounts for User-ID functions (Server Monitoring, Client Probing, LDAP Bind for Group Mapping). Grant only the minimum necessary permissions (e.g., "Event Log Readers" for Server Monitoring, specific WMI/DCOM rights for Client Probing, read-only LDAP access). Regularly audit these accounts and change passwords according to policy.
-
Optimize Group Mapping:
- Use the Group Include List in Group Mapping settings to fetch only necessary groups from LDAP, especially in large Active Directory environments. This significantly improves performance of the `useridd` process on the firewall and reduces memory consumption.
- Use LDAPS (LDAP over SSL/TLS on port 636) or Start TLS for secure communication with LDAP servers. Ensure the firewall trusts the CA that signed the LDAP server's certificate.
- Choose a consistent "Primary Username" format (`sAMAccountName` or `userPrincipalName`) and ensure mapping sources provide usernames in this format where possible.
-
Regularly Review Mappings, Timeouts, and Logs:
- Periodically check the User-ID mapping table (`show user ip-user-mapping all`) and User-ID logs (`Monitor > Logs > User-ID`, `less mp-log useridd.log`) for anomalies or unexpected behavior.
- Adjust User-ID Timeouts (`Device > User Identification > User-ID Timeouts`) as needed to balance accuracy with resource utilization, based on your environment's user dynamics.
- Keep Software Updated: Ensure PAN-OS on firewalls/Panorama, Windows User-ID Agent software, and GlobalProtect clients are on currently supported and recommended versions to benefit from bug fixes, security updates, and new features.
-
Plan for Scale and Redundancy:
- In large environments, consider dedicated Windows User-ID Agents (potentially multiple for redundancy or geographic distribution).
- Utilize Panorama for User-ID redistribution to simplify management and ensure consistency across many firewalls.
- Understand the User-ID mapping capacity of your firewall platforms.
- For HA firewalls, ensure User-ID configuration is synchronized and consider how agent connections/syslog sources will behave during failover.
- Time Synchronization: Ensure consistent time across all components involved in User-ID (Firewalls, Panorama, Domain Controllers, User-ID Agents, client machines) using NTP. This is critical for accurate log correlation and Kerberos-based authentication events.
- Test Thoroughly: Before full deployment or making significant changes, test User-ID configurations in a lab or pilot environment to ensure correct functionality and identify potential issues.
- Documentation: Document your User-ID architecture, configurations (including regex for syslog, service accounts used, port numbers), and troubleshooting procedures. This is invaluable for ongoing maintenance and issue resolution.