Palo Alto Networks: Mastering Virtual Systems (VSYS) and Per-VSYS Service Routes
Understanding Virtual Systems (VSYS) in PAN-OS
Palo Alto Networks Next-Generation Firewalls (NGFWs) running PAN-OS can be partitioned into multiple, independent logical firewalls known as Virtual Systems (VSYS) . This capability, often referred to as multi-VSYS mode, allows a single physical appliance to serve diverse security needs, acting as several distinct firewalls. Each VSYS operates with its own set of resources, policies, and administrative domains, providing robust segmentation and multi-tenancy.
Enabling multi-VSYS mode transforms the firewall from a single logical device (vsys1 by default) into a platform capable of hosting multiple VSYS instances (vsys1, vsys2, ..., vsysN).
Key Benefits and Use Cases of VSYS:
- Multi-Tenancy: Managed Security Service Providers (MSSPs) can offer dedicated logical firewalls to different customers on a shared physical infrastructure. Each tenant VSYS has its own security policies, reporting, and potentially administration.
- Departmental Segmentation: Large enterprises can segment their network by department (e.g., Finance, Engineering, HR), assigning each a VSYS. This allows for tailored security policies and isolates traffic and administration.
- Service Isolation: Different services or applications with unique security requirements can be isolated within their own VSYS.
- Scalability and Resource Optimization: Consolidates multiple physical firewalls into one, reducing hardware footprint and operational overhead while maintaining logical separation.
- Delegated Administration: VSYS-specific administrators can be created, granting them control only over their assigned VSYS, enhancing security and operational efficiency.
VSYS Resource Allocation:
When a VSYS is created, various resources can be dedicated to it or remain shared:
-
Dedicated Resources per VSYS:
- Interfaces: Physical or logical interfaces (subinterfaces, Aggregate Ethernet, VLAN, Tunnel interfaces) are assigned to a specific VSYS.
- Virtual Routers (VRs): Each VSYS typically has its own VR(s) for routing traffic.
- Security Zones: Zones are defined within the context of a VSYS and its assigned interfaces.
- Security Policies: Includes Security, NAT, QoS, Decryption, Application Override, and DoS Protection policies.
- Objects: Address objects, service objects, security profiles (Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, WildFire Analysis, Data Filtering).
- Logs: Traffic, Threat, URL Filtering, WildFire, Data Filtering, and other logs are segregated per VSYS.
- Reporting: Reports can be generated on a per-VSYS basis.
- VSYS Administrators: Role-based access control can define administrators with permissions limited to specific VSYS.
-
Shared Resources (across all VSYS on the device):
- Physical Hardware (CPU, memory, Data Plane, Signature Processors).
- PAN-OS software image.
- Licenses (though some capacity licenses might be allocatable).
- Global system settings (e.g., NTP, Panorama settings, master key) unless overridden by service routes or specific VSYS configurations.
- Management (MGT) Interface (by default, can be changed for some services).
- High Availability (HA) configuration (applies to the physical device).
Device > Setup > Management > General Settings > Multi Virtual System Capability
).
Introduction to Service Routes in PAN-OS
Service Routes in PAN-OS define the network path (source interface, source IP address, and Virtual Router) that the firewall itself uses to initiate connections to various external or internal infrastructure services. These are distinct from security policies that govern transit traffic. Firewall-initiated traffic includes:
- DNS (Domain Name System) resolution: For FQDN objects, URL filtering, etc.
- NTP (Network Time Protocol) synchronization: To maintain accurate time.
- LDAP / RADIUS / TACACS+ / Kerberos: For User-ID, GlobalProtect authentication, and device administration.
- Syslog / NetFlow / SNMP: For sending logs and monitoring data.
-
Palo Alto Networks Services:
- Content & Software Updates (Applications, Threats, Antivirus, WildFire).
- Panorama Connectivity (management, log forwarding).
- WildFire Signature and Sample Forwarding.
- GlobalProtect Services (Portal, Gateway, External Gateways).
- Cortex Data Lake (CDL) log forwarding.
- URL Filtering lookups (PAN-DB Cloud).
- And others like AutoFocus, MineMeld, etc.
- Email Alerts: For notifications.
By default, many of these services use the firewall's Management (MGT) interface as their source. However, this is often not desirable for security or network architecture reasons. Service Routes allow administrators to customize this behavior, forcing specific services to use data plane interfaces, specific source IP addresses, and route via specific Virtual Routers.
Global Service Route Configuration
Global service routes apply to all firewall-initiated traffic for the specified services, unless overridden by a VSYS-specific configuration. They are configured under
Device > Setup > Services > Service Route Configuration
. You can select "Customize" for each service and specify:
- Source Interface: The egress interface on the firewall. This can be a data plane interface or the MGT interface.
-
Source Address:
The IP address to be used as the source for this traffic. This should be an IP address configured on the selected Source Interface or
Use Interface IP.
PAN-OS uses the Virtual Router associated with the chosen Source Interface to route the traffic to the service destination. If "any" is chosen as the interface, the firewall uses its routing table to determine the best path.
Deep Dive: Per-VSYS Service Routes
When a Palo Alto Networks firewall is operating in multi-VSYS mode, the need for granular control over service traffic routing becomes even more critical. Per-VSYS service routes allow administrators to define unique source interfaces and IP addresses for firewall-initiated services on a VSYS-by-VSYS basis.
By default, each VSYS inherits the global service route settings. However, these can be overridden. This is essential for:
- Tenant-Specific Egress: In an MSSP environment, Tenant A's VSYS can use Tenant A's dedicated internet link for its DNS queries or LDAP authentication, while Tenant B's VSYS uses a different path.
- Departmental Autonomy: An Engineering VSYS might need to access specific internal update servers for custom applications, while a Finance VSYS uses centrally managed services.
- Compliance and Security: Ensuring that management traffic from a particular VSYS (e.g., one handling sensitive data) uses a specific, audited network path for services like syslog or NTP.
- Network Segmentation: Directing service traffic through appropriate security zones and inspection points within the VSYS's context before it leaves the firewall.
Configuration of Per-VSYS Service Routes
To configure service routes for a specific VSYS:
-
Switch to the VSYS Context:
- In the PAN-OS GUI (Firewall): At the top right of the web interface, there's a "Virtual System" dropdown menu. Select the desired VSYS (e.g., vsys2). The GUI context will change to that VSYS.
- In Panorama: When configuring in a Template or Template Stack, ensure you are targeting the correct VSYS or that the template is specifically for that VSYS. Panorama might offer a "Target VSYS" selection.
-
In the PAN-OS CLI:
Use the command
set system setting target-vsys <vsys_name_or_id>. For example,set system setting target-vsys vsys2. Then enter configuration mode withconfigure.
-
Navigate to Service Route Settings:
-
GUI:
Once in the VSYS context, go to
Device > Setup > Services. Click on the "Service Route Configuration" tab. -
CLI:
After setting the target VSYS and entering configure mode, use commands like
set deviceconfig system route service <service_name> interface <interface_name> source <ip_address_or_use-interface-ip>. The available interfaces will be those assigned to the current target VSYS.
-
GUI:
Once in the VSYS context, go to
- Customize Routes: For each service (e.g., DNS, LDAP, Palo Alto Networks Updates), select "Customize." The "Source Interface" dropdown will only list interfaces assigned to the current VSYS. Choose the appropriate interface and source IP address.
-
Commit Changes:
After configuration, commit the changes on the firewall or push from Panorama. PAN-OS stores these VSYS-specific settings in a separate configuration file (e.g.,
vsys2.xml).
Service Route Precedence
PAN-OS uses the following order of precedence to determine which service route to use:
- VSYS-Specific Service Route: If a custom service route is configured for a service within the specific VSYS initiating the request, that route is used.
- Global Service Route: If no VSYS-specific route is configured for that service, but a global service route is defined, the global route is used.
- Default Behavior (Usually MGT Interface): If neither a VSYS-specific nor a global service route is configured for the service, PAN-OS falls back to its default behavior, which for many services is to use the MGT interface. Some services may have different defaults or require explicit configuration.
For further details on specific service behaviors and configuration, refer to the official Palo Alto Networks documentation, such as the Customize Service Routes for a Virtual System guide on the TechDocs portal.
Illustrative Diagrams for VSYS and Service Routes
Mermaid Diagram: Multi-VSYS Architecture Overview
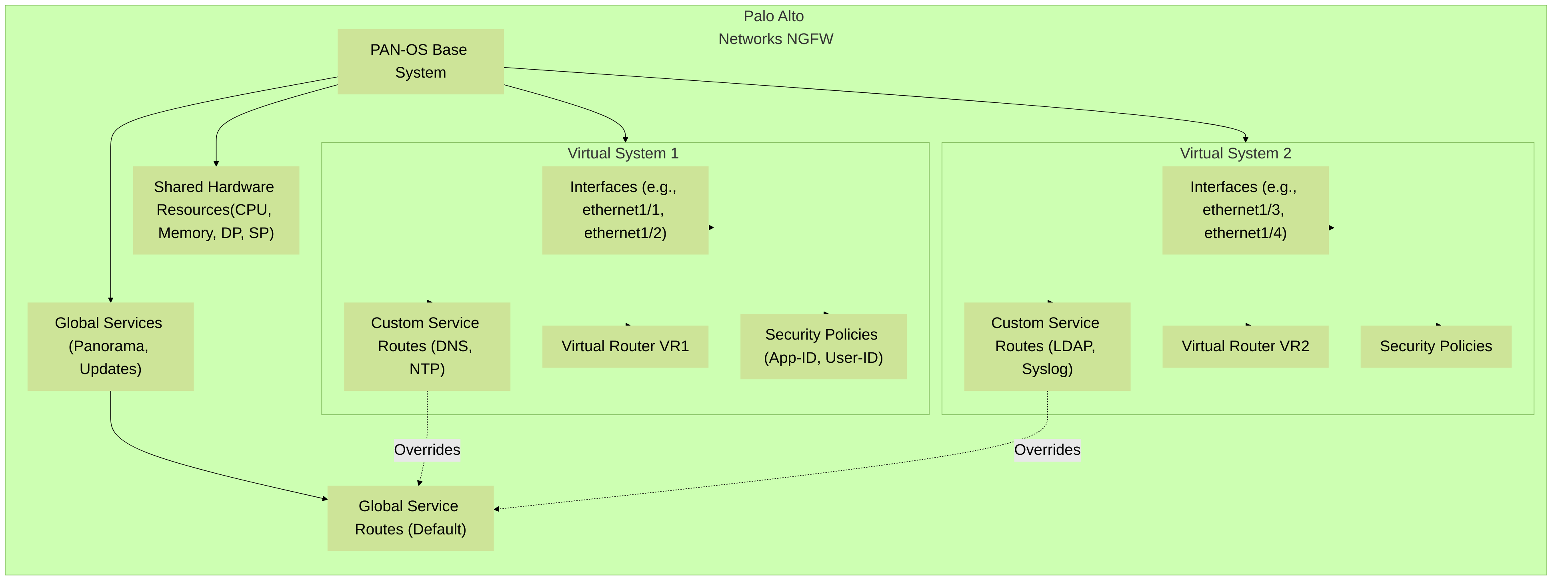
This diagram provides a high-level overview of a Palo Alto Networks Next-Generation Firewall configured with multiple Virtual Systems (VSYS). It highlights shared resources versus resources dedicated or customized per VSYS, including interfaces, virtual routers, and service routes that can override global settings.
Mermaid Diagram: Configuring Per-VSYS Service Routes Workflow
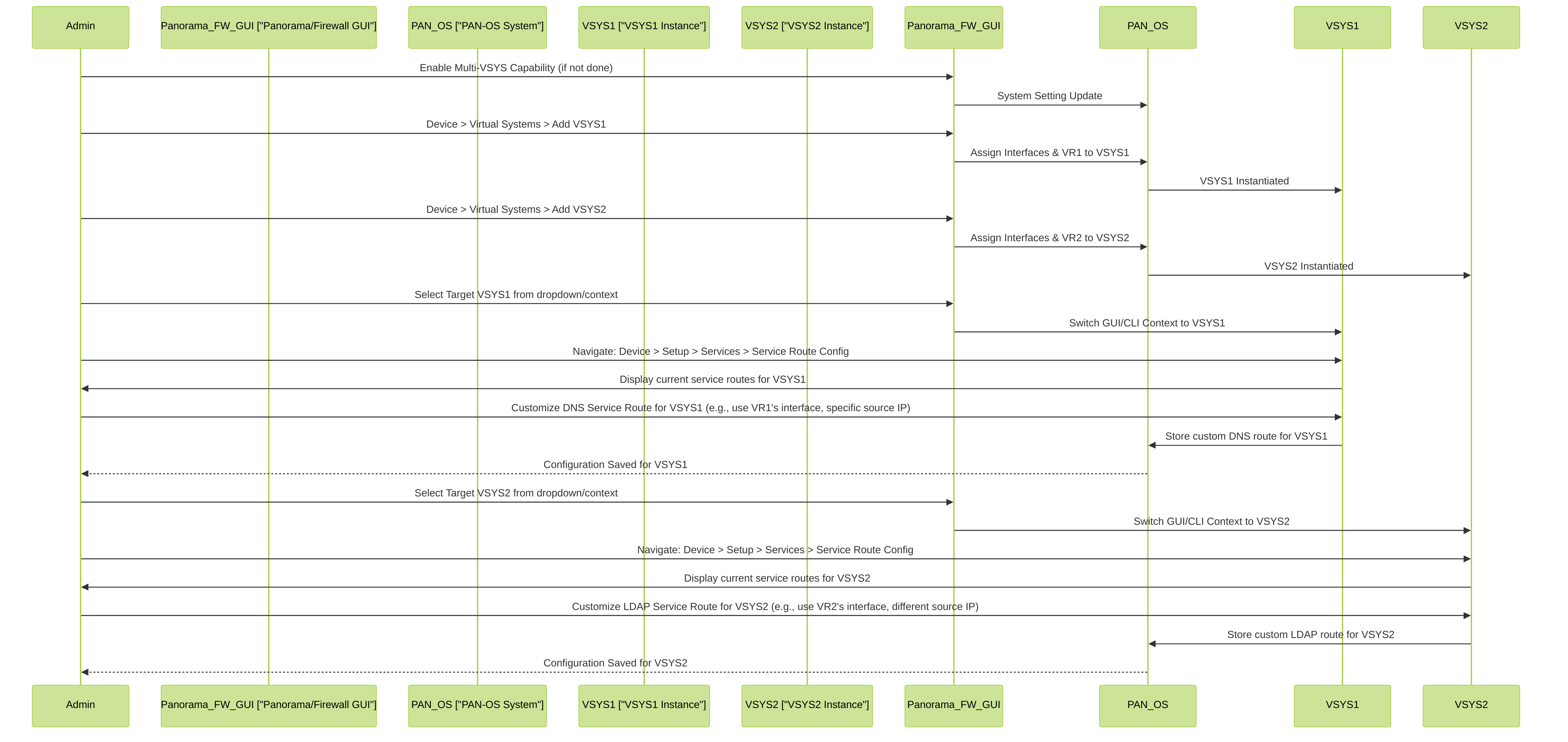
This diagram illustrates the administrative workflow for configuring distinct service routes for different Virtual Systems (VSYS1 and VSYS2) on a Palo Alto Networks firewall. It shows the context switching and specific customization for services like DNS and LDAP within each VSYS.
Mermaid Diagram: Traffic Flow with Customized Per-VSYS Service Routes
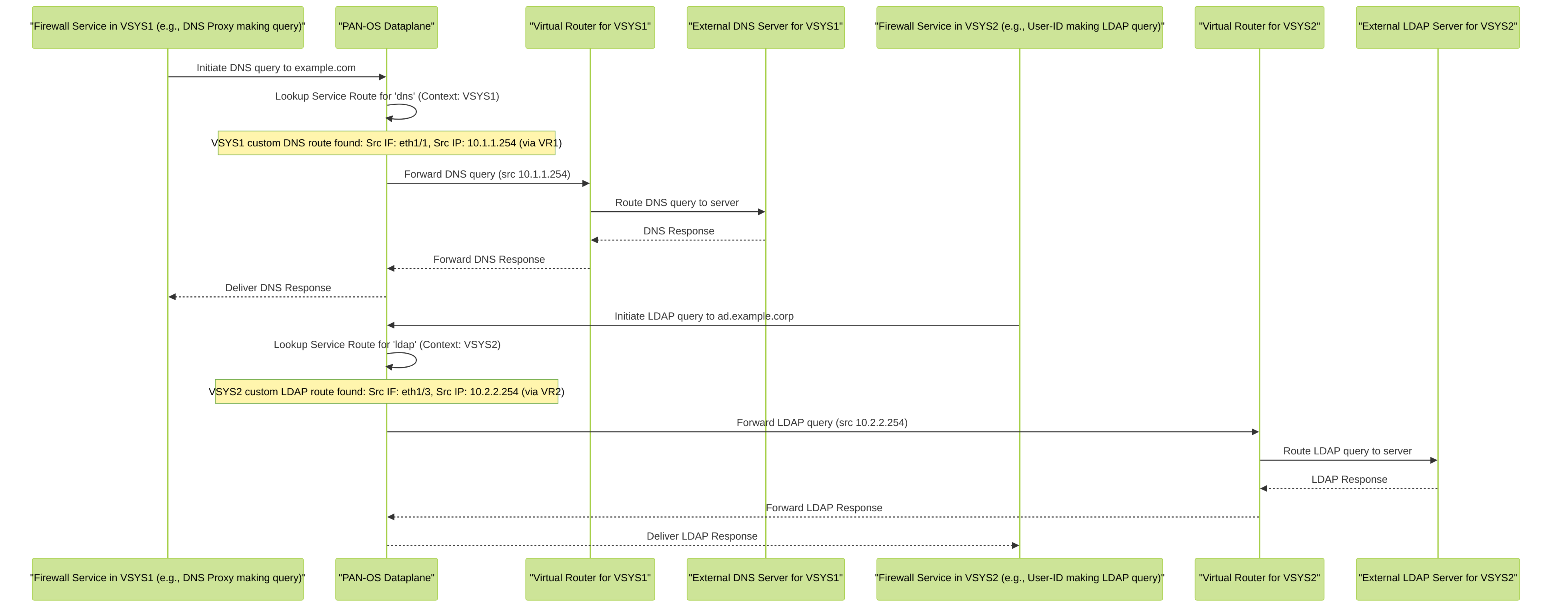
This diagram depicts how a Palo Alto Networks firewall, with per-VSYS service routes, handles self-originated traffic. DNS traffic from VSYS1 uses its dedicated service route via VR1, while LDAP traffic from VSYS2 uses its own distinct service route via VR2, demonstrating traffic isolation and customized egress paths.
Mermaid Diagram: PAN-OS Service Route Selection Logic
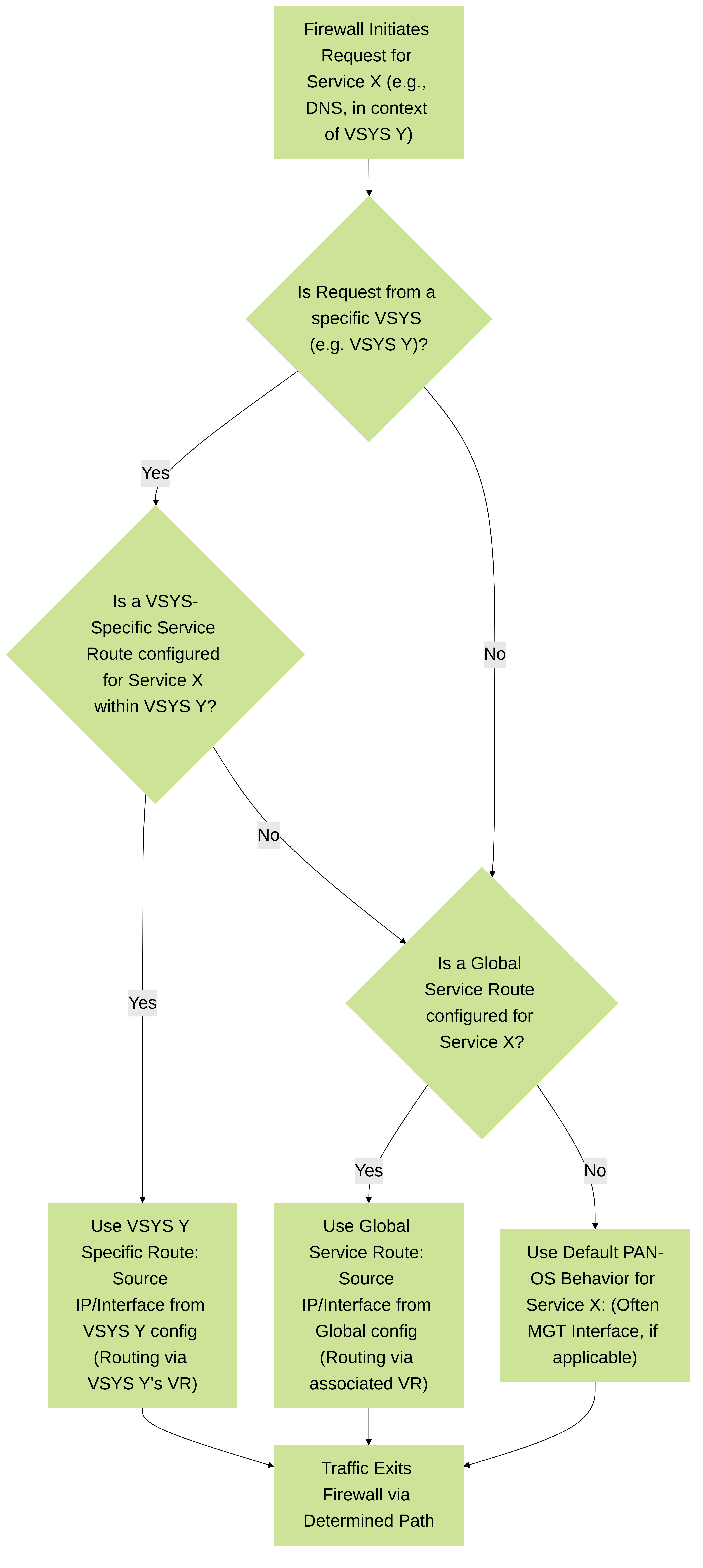
This flowchart illustrates the decision-making process PAN-OS follows to select a service route when a firewall service needs to communicate externally, especially in a multi-VSYS environment. It prioritizes VSYS-specific routes, then global routes, and finally falls back to default PAN-OS behavior for that service.
Troubleshooting Per-VSYS Service Routes
When firewall-initiated services fail in a multi-VSYS environment, systematic troubleshooting is key:
- Verify VSYS Context: Ensure you are troubleshooting from the perspective of the correct VSYS. Firewall logs for service traffic will be tagged with the source VSYS.
-
Check Service Route Configuration:
-
In the GUI (for the specific VSYS) or CLI (after setting
target-vsys), confirm the service route for the failing service (e.g., DNS, LDAP, Panorama). Note the source interface and IP. - Ensure the chosen source interface is operationally UP and assigned to this VSYS.
- Verify the source IP is correct and bound to that interface or is a loopback/secondary IP routable via that interface's VR.
-
In the GUI (for the specific VSYS) or CLI (after setting
-
Validate Routing:
- Identify the Virtual Router (VR) associated with the service route's source interface (for that VSYS).
-
Check the VR's routing table:
show routing route virtual-router <vsys_vr_name>. Ensure there's a route to the destination service IP address. -
Test reachability from the firewall CLI using the VR and source IP:
ping virtual-router <vsys_vr_name> source <source_ip_from_service_route> host <destination_service_ip>.
-
Examine Traffic Logs:
- Filter traffic logs for traffic originating from the firewall itself (use the source IP configured in the service route) destined for the service IP/port.
- Ensure an "allow" security policy exists if the service route uses a data plane interface that traverses zones within the VSYS. While service route traffic doesn't typically hit dataplane policies if it sources from the firewall directly to an external service *unless* it has to traverse internal zones first, this can be a point of confusion. Generally, traffic sourced by the firewall for its own services doesn't match regular security policies unless it's hair-pinning through other zones.
-
Packet Captures (PCAPs):
- Configure packet captures on the source interface defined in the service route.
- Filter for the destination service IP and port. This can show if traffic is leaving the firewall as expected.
- Global vs. VSYS Specific: If a VSYS is expected to use a global service route (because no VSYS-specific one is set), verify the global service route configuration as well.
-
Service-Specific Debugs:
PAN-OS offers service-specific debug commands (e.g., for User-ID, DNS proxy) that can provide more detailed error messages. Consult Palo Alto Networks documentation for these commands.
Example:
debug device-server reset service-route effective-config vsys <vsys-id>can show effective service routes for a vsys.show system PBF-service-route vsys <vsys-id> service <service-name>might also be useful, though PBF usually refers to Policy Based Forwarding. The CLI command `show system setting PBF-service-route` can be helpful to view details.
# Example CLI commands for troubleshooting (replace placeholders)
# Set target VSYS for CLI context
set system setting target-vsys vsys2
# View routing table for a VR within the VSYS context
configure
show routing route virtual-router vsys2-vr
# Test connectivity from the VSYS context using a specific source IP and VR
ping virtual-router vsys2-vr source 192.168.2.10 host 8.8.8.8
# View configured service routes (after setting target-vsys and entering configure mode)
show deviceconfig system route service all
# To see the effective service route configuration for a specific vsys (often more direct)
# This command might vary slightly by PAN-OS version, check exact syntax if needed
show system setting service-route effective-config vsys vsys2 service dns