Configure Authorization, Authentication, and Device Access
Overview
Securing administrative access to your Palo Alto Networks firewall or Panorama is paramount. Weak access controls can undermine all other security measures. This involves managing three key aspects:
- Authentication (AuthN): Verifying the identity of the administrator trying to log in (Who are you?).
- Authorization (AuthZ): Determining what actions an authenticated administrator is permitted to perform (What can you do?). This is achieved through Role-Based Access Control (RBAC).
- Device Access Control: Restricting *how* and *from where* administrators can connect to the management interface.
Implementing robust controls across these areas follows the principle of least privilege and significantly enhances the overall security posture of your network infrastructure.
Authorization: Role-Based Access Control (RBAC) - Admin Roles
RBAC allows administrators to enforce the principle of least privilege by assigning specific permissions based on job responsibilities. Instead of granting full superuser access, you define roles that permit access only to the necessary functions and configuration areas.
Admin Role Profiles
The core component of RBAC is the Admin Role Profile ( Device > Admin Roles ).
- Defines granular permissions across various functional areas of the firewall/Panorama GUI and CLI.
- Permissions are typically defined per tab (e.g., Policies, Objects, Network, Device) and sub-sections within tabs.
-
Access levels for each area can be set to:
- Read/Write: Full access to view and modify settings in that area.
- Read Only: Ability to view settings but not make changes.
- None: The functional area might be hidden or inaccessible.
- Disable: (Specific contexts) Explicitly disable access.
- Includes permissions for operational tasks like committing changes, managing software/content updates, running reports, viewing specific log types, and using CLI commands.
Built-in vs. Custom Roles
-
Built-in Roles:
PAN-OS provides several predefined roles, such as:
-
superuser: Full unrestricted access. -
superreader: Read-only access to everything. -
devicereader: Read-only access focused on device status and logs. -
deviceadmin: Broader device management access but potentially restricted policy/object access. - (Others may exist depending on version/platform).
-
-
Custom Roles:
Creating custom roles is highly recommended for implementing least privilege. You can tailor roles precisely to job functions:
- Security Policy Admin: Read/Write access to Policies and Objects, Read Only elsewhere.
- Network Admin: Read/Write access to Network tab, Read Only elsewhere.
- Auditor: Read Only access to relevant logs, reports, and possibly configuration, but no write access.
- Help Desk / Monitoring: Read Only access to dashboard, ACC, logs.
Authorization: RBAC - Access Domains (Panorama/Multi-VSYS)
While Admin Roles define *what* an administrator can do (permissions), Access Domains define *where* they can do it, limiting the scope of their assigned role within Panorama or a multi-VSYS firewall.
Purpose:
- Scope Limitation: Restrict an administrator's access (defined by their Admin Role) to specific Device Groups, Templates/Template Stacks (in Panorama), or Virtual Systems (VSYS) on a firewall.
- Multi-Tenancy / Segmentation: Allows different administrative teams to manage distinct parts of the infrastructure without interfering with or viewing others' configurations (e.g., different departments, customers).
Configuration:
- Access Domains are configured under Panorama > Access Domains or Device > Access Domains (for multi-VSYS firewalls).
- You create an Access Domain and select the specific Device Groups, Templates, or VSYS that administrators assigned to this domain will be able to manage.
- When creating an Administrator account ( Panorama > Administrators or Device > Administrators ), you assign both an Admin Role Profile *and* an Access Domain (if applicable). The default is typically 'All'.
Authentication: Methods (Local/External)
Authentication verifies the identity of an administrator attempting to access the firewall or Panorama. PAN-OS supports multiple methods:
Local Authentication
- User accounts and passwords (hashed) are stored directly on the firewall or Panorama device itself ( Device > Local User Database > Users ).
- Simple to set up for a small number of users.
- Disadvantages: Doesn't scale well, lacks centralized management, password policies might be inconsistent with organizational standards, requires manual account provisioning/deprovisioning on each device.
External Authentication
Leverages centralized authentication servers, providing better scalability, consistency, and management.
-
Supported Protocols:
- LDAP (Lightweight Directory Access Protocol): Integrates with directories like Active Directory, OpenLDAP. Users authenticate with their directory credentials. Group membership can be retrieved for role mapping.
- RADIUS (Remote Authentication Dial-In User Service): Common protocol used by various authentication servers and MFA solutions.
- TACACS+ (Terminal Access Controller Access-Control System Plus): Cisco-developed protocol often used for network device administration, providing separate Authentication, Authorization, and Accounting (AAA).
- Kerberos: Network authentication protocol often used in Windows environments (Active Directory).
- SAML (Security Assertion Markup Language): An XML-based standard for exchanging authentication and authorization data between an Identity Provider (IdP) and a Service Provider (SP - the firewall/Panorama). Enables Single Sign-On (SSO) and integration with modern cloud IdPs (Okta, Azure AD, etc.). Often used for MFA integration.
- Configuration: Requires creating Server Profiles for each external server type ( Device > Server Profiles ) and an Authentication Profile ( Device > Authentication Profile ) that references the Server Profile(s).
- Advantages: Centralized user management, consistent password policies, easier onboarding/offboarding, potential for MFA integration.
Authentication: Authentication Profiles
An Authentication Profile ( Device > Authentication Profile ) acts as a bridge, defining *how* the firewall should authenticate users using specific methods and linking those methods to user attributes or group memberships for authorization.
Configuration Steps:
- Navigate to Device > Authentication Profile .
- Click Add to create a new profile.
- Name: Provide a descriptive name (e.g., `LDAP_Admin_Auth`, `RADIUS_MFA_Auth`).
- Type: Select the authentication type (LDAP, RADIUS, TACACS+, Kerberos, SAML, Local Database).
- Server Profile: Select the corresponding Server Profile (created under Device > Server Profiles ) that contains the connection details for the external server (e.g., IP address, port, base DN, secret). Not needed for 'Local Database' type.
- Login Attributes / User Domain: Specify the attribute used for the username during login (e.g., `sAMAccountName` for LDAP, often left default for RADIUS/TACACS+). Optionally define a User Domain.
-
Advanced Tab (Crucial Settings):
- Allow List: Specify which users or, more commonly, groups from the external server are permitted to authenticate using this profile. This is a critical security control – only allow authorized administrative groups!
- (LDAP Specific) Group Mapping Settings: Configure how to retrieve group membership from the directory.
- (SAML Specific) Configure IdP details, certificate validation, attribute mapping for username and roles.
- (RADIUS Specific) Configure timeouts, retries, protocol (PAP, CHAP, MS-CHAPv2).
- Click OK .
Authentication: Authentication Sequence
An Authentication Sequence ( Device > Authentication Sequence ) allows you to define an ordered list of Authentication Profiles to be tried sequentially when an administrator logs in. This enables fallback authentication and integration of multiple sources.
Use Cases:
- Redundancy/Fallback: Try authenticating against a primary external server (e.g., LDAP), and if it's unavailable or the user isn't found, fall back to a secondary server or the local database.
- Hybrid Environments: Authenticate certain administrators via one method (e.g., SAML for SSO users) and others via a different method (e.g., local DB for emergency access).
- Phased Migration: Gradually migrate users from one authentication system to another.
Configuration:
- Navigate to Device > Authentication Sequence .
- Click Add .
- Name: Give the sequence a descriptive name (e.g., `Admin_Auth_Sequence`).
- Authentication Profiles List: Add previously configured Authentication Profiles to the list in the desired order of execution. The firewall attempts authentication using the profiles from top to bottom.
- Use Profile From Authentication Profile: Select which profile's 'Allow List' should be used to authorize the user *after* successful authentication by any profile in the sequence. Often, this is set to the primary profile, but could be a dedicated authorization profile.
- Click OK .
Authentication: Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) significantly enhances security by requiring administrators to provide multiple forms of verification before granting access. PAN-OS typically integrates with external MFA solutions rather than having a built-in MFA server.
Common Integration Methods:
- RADIUS: Many MFA providers (Duo, RSA SecurID, Okta RADIUS Agent, etc.) offer RADIUS interfaces. Configure a RADIUS Server Profile pointing to the MFA server and an Authentication Profile using RADIUS. The firewall forwards the username and password/OTP to the RADIUS server, which performs the MFA check.
- SAML 2.0: Modern Identity Providers (IdPs) like Okta, Azure AD, Ping Identity often act as SAML IdPs that can enforce MFA policies centrally. Configure a SAML Authentication Profile on the firewall pointing to the IdP. When an admin logs in, they are redirected to the IdP for authentication (including MFA), and the IdP sends a SAML assertion back to the firewall upon success.
- LDAP (with MFA overlays): Some solutions might integrate MFA checks during the LDAP bind process, though RADIUS and SAML are more common for dedicated MFA integration.
- TACACS+: Can also be used with MFA solutions that support it.
Configuration Steps (General - Example using RADIUS):
- Configure your MFA provider (e.g., Duo, RSA) to accept RADIUS requests from the firewall's management IP address. Note the shared secret.
- On the firewall, create a RADIUS Server Profile ( Device > Server Profiles > RADIUS ) pointing to your MFA server's IP, port, and using the shared secret.
- Create an Authentication Profile ( Device > Authentication Profile ) of type RADIUS, referencing the Server Profile created above. Configure the Allow List as needed.
- Assign this Authentication Profile (or an Authentication Sequence containing it) to your administrator accounts ( Device > Administrators ).
Secure Access: Administrator Accounts
Configuring administrator accounts links user identities to their authentication methods and authorization levels (roles).
Configuration Steps:
- Navigate to Device > Administrators .
- Click Add .
- Name: Enter the username the administrator will use to log in. This must match the username expected by the Authentication Profile/Sequence (e.g., sAMAccountName for AD, local username, SAML NameID).
- Authentication Profile: Select the Authentication Profile or Authentication Sequence that will be used to verify this user's credentials. Select 'None' if using local password authentication only.
- Password / Confirm Password: Set a password *only* if using local authentication (i.e., Authentication Profile is set to 'None' or a sequence including the Local DB is used, and this user is intended to use local). Otherwise, leave blank as authentication occurs externally.
-
Administrator Type:
-
Dynamic:
Assigns roles based on attributes returned from the external authentication server (e.g., group membership from LDAP/SAML/RADIUS). Requires configuration within the Authentication Profile (e.g., SAML attribute mapping, RADIUS vendor-specific attributes).
- Select the Admin Role Profile or Access Domain Profile that maps external attributes/groups to firewall roles/domains.
-
Role Based:
Manually assign a specific role to this administrator account.
- Profile: Select the desired Admin Role Profile (e.g., Network Admin, Security Admin, Superreader).
- Access Domain (Panorama/Multi-VSYS): Select the Access Domain to restrict the scope, or 'All'.
- Superuser / Superuser (read only): Grants full access or full read-only access, bypassing specific Admin Role profiles. Avoid using Superuser unless absolutely essential.
-
Dynamic:
Assigns roles based on attributes returned from the external authentication server (e.g., group membership from LDAP/SAML/RADIUS). Requires configuration within the Authentication Profile (e.g., SAML attribute mapping, RADIUS vendor-specific attributes).
- Click OK .
Secure Access: Management Profiles & Permitted IPs
Securing device access involves controlling *how* and *from where* administrators can connect to the firewall's management interfaces.
Interface Management Profiles
An Interface Management Profile defines which management services are allowed on a specific interface (typically the dedicated Management interface, but can also be applied to data plane interfaces if management access is permitted there).
- Configuration: Network > Network Profiles > Interface Mgmt .
-
Services Allowed:
Check boxes to enable desired services:
- HTTPS: For Web UI access (Essential).
- SSH: For Command Line Interface (CLI) access (Essential).
- SNMP: For network monitoring systems.
- Ping: Allows ICMP echo requests to the interface IP (useful for reachability testing).
- Telnet: Should always be disabled (insecure).
- HTTP: Should always be disabled (insecure). Redirects to HTTPS if enabled, but better to disable outright.
- User-ID, User-ID Syslog Listener, etc.: For specific feature integrations.
-
Permitted IP Addresses:
Crucially,
define a list of specific source IP addresses or subnets that are allowed to connect to the management services enabled on the interface. This drastically reduces the attack surface. Use dedicated management subnets or bastion host IPs here. Avoid using
0.0.0.0/0(Any). - Application: Apply the created Interface Management Profile to the relevant network interface under Network > Interfaces > [Select Interface] > Advanced > Management Profile .
Secure Access: Management Network Isolation
Physically or logically isolating the network segment used for firewall management provides a significant security enhancement.
Best Practices:
- Dedicated Management Network: Use a separate VLAN or network segment exclusively for management traffic (firewall management interfaces, Panorama, AAA servers, monitoring tools, admin workstations).
- Out-of-Band Management: Whenever possible, use the dedicated Management (MGT) port for management access and keep it separate from data plane traffic paths.
- Restrict Access: Implement strict firewall policies (on the Palo Alto Networks firewall itself or upstream devices) to control traffic entering and leaving the management network. Only allow necessary protocols (HTTPS, SSH, SNMP, NTP, DNS, AAA protocols, Panorama traffic) from authorized sources (admin workstations, specific servers).
- Bastion Hosts / Jump Servers: Require administrators to connect first to a hardened bastion host or jump server within the management network before accessing the firewall interfaces. This provides a single point of control and auditing.
- Permitted IPs: Configure Permitted IP addresses on the Interface Management profile to only allow connections from the designated bastion hosts or specific administrative subnets.
Secure Access: Logging & Auditing
Tracking administrator activity is crucial for accountability, troubleshooting, and incident investigation.
Key Log Types:
- System Logs ( Monitor > Logs > System ): Records administrative login successes, failures, logout events, password changes, and other system-level events related to administration.
- Configuration Logs ( Monitor > Logs > Configuration ): Provides a detailed audit trail of *all* configuration changes made by administrators. It shows who changed what, when, and the specific configuration elements modified (both GUI and CLI changes are logged).
- Command Logs (CLI): When enabled ( Device > Setup > Management > Logging and Reporting Settings > Log Settings > System Log Settings > CLI Command Logging ), logs the actual commands executed by administrators via the CLI in the System Log.
- Audit Comment Archive: When committing changes, administrators can (and should) be required to enter comments describing the change. These comments are stored with the configuration version ( Device > Setup > Operations > Config Audit ).
Best Practices:
- Ensure adequate log retention settings.
- Forward relevant logs (System, Configuration, potentially Command) to a centralized SIEM (Security Information and Event Management) system for long-term storage, correlation, and analysis.
- Regularly review Configuration Logs to ensure changes are authorized and expected.
- Investigate failed login attempts recorded in the System Log.
Secure Access: Updates and Patching
Maintaining up-to-date software is a fundamental security practice for any network device, including firewalls.
Best Practices:
- Stay Informed: Subscribe to Palo Alto Networks security advisories and release notes to be aware of vulnerabilities and bug fixes.
- Regular PAN-OS Updates: Plan and execute regular updates to the latest preferred PAN-OS release for your platform. Patches often contain critical security fixes.
- Content Updates: Ensure dynamic content (Applications, Threats, Antivirus, WildFire) is updated frequently (often daily or hourly) to maintain protection against the latest threats.
- Test Before Deploying: Whenever possible, test PAN-OS updates in a non-production lab environment that mimics your production setup before deploying them widely.
- Follow Release Guidance: Pay attention to recommended/preferred releases indicated in the release notes.
Diagrams: Authentication & Authorization Concepts
Flowchart: Authentication Sequence Logic
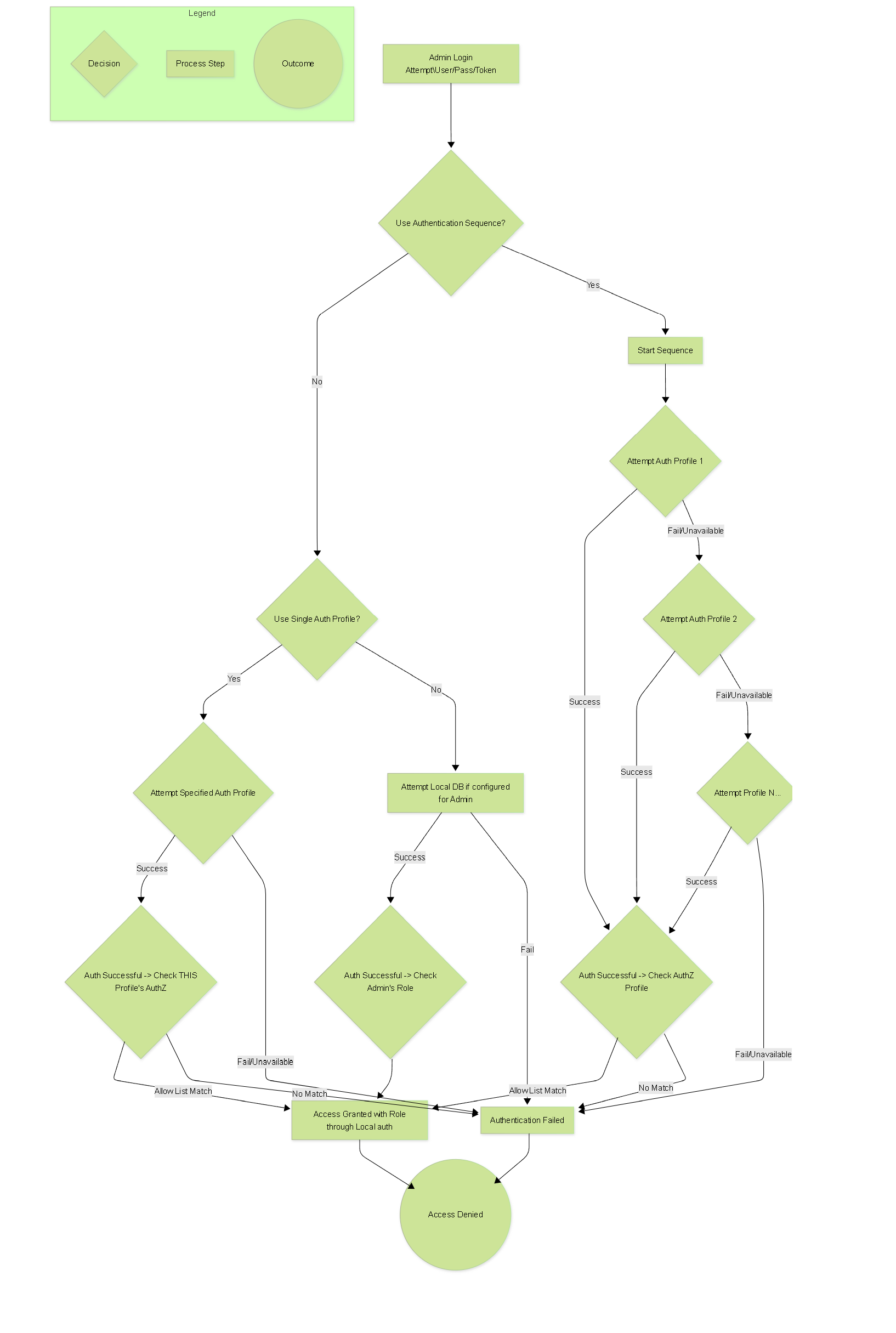
Flowchart illustrating the logic of an Authentication Sequence with fallback and final authorization check.
Graph: Admin Access Components Relationship
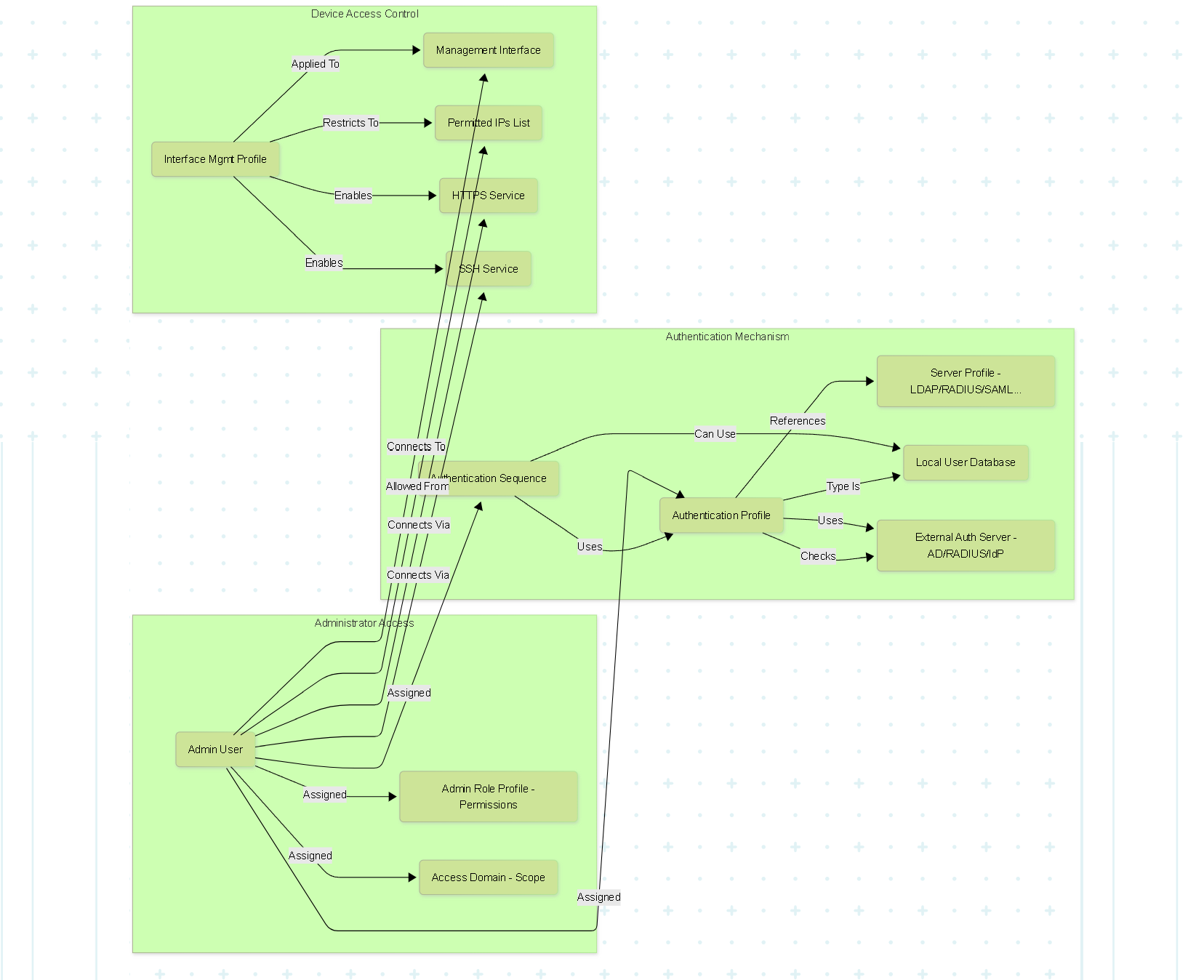
Graph showing the relationships between Administrators, Roles, Authentication components, and Interface Access controls.
Sequence Diagram: External Authentication (LDAP Example)
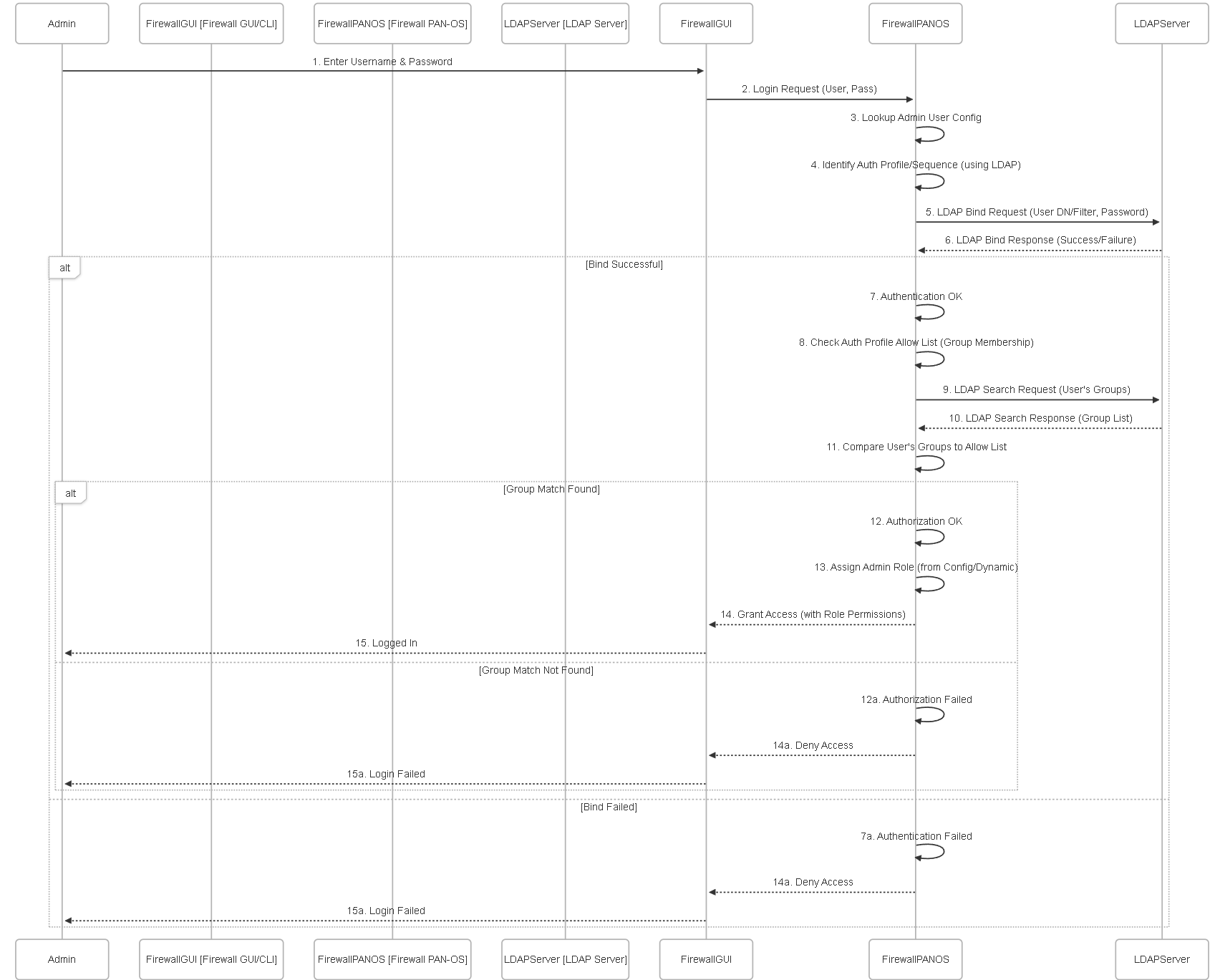
Sequence diagram illustrating an administrator login using an LDAP Authentication Profile.
State Diagram: Admin Access States
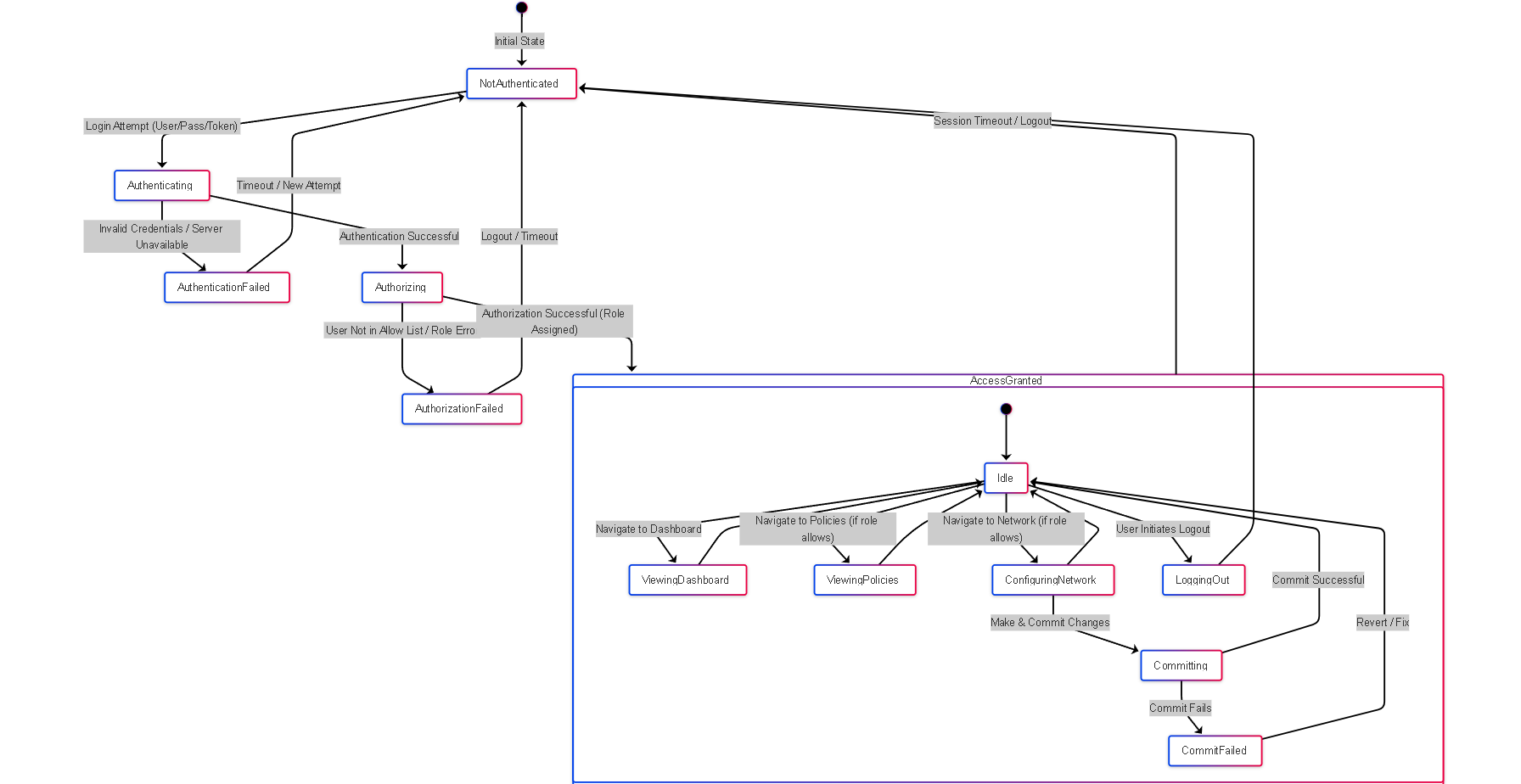 Simplified state diagram showing transitions between authentication, authorization, and activity states for an administrator.
Simplified state diagram showing transitions between authentication, authorization, and activity states for an administrator.
PCNSE Exam Focus Points
Key areas related to Authentication, Authorization, and Device Access for the PCNSE exam:
- Authentication vs. Authorization: Clearly distinguish between verifying identity (AuthN) and determining permissions (AuthZ - via RBAC).
-
RBAC Components:
- Admin Role Profiles: Understand their purpose (define granular permissions), configuration location ( Device > Admin Roles ), and common permission levels (Read/Write, Read Only, None). Know the difference between built-in (superuser, superreader) and custom roles.
- Access Domains: Know their purpose (limit scope of roles in Panorama/multi-VSYS), configuration location, and how they combine with Admin Roles.
-
Authentication Methods:
- Know the supported methods: Local, LDAP, RADIUS, TACACS+, Kerberos, SAML.
- Understand the pros/cons of Local vs. External (centralization, scalability, MFA).
-
Authentication Configuration Objects:
- Server Profiles: Define connection parameters for external servers (LDAP, RADIUS, etc.).
- Authentication Profile: Links a Server Profile (or Local DB) to an authentication method type and, critically, contains the Allow List for authorization.
- Authentication Sequence: Defines ordered fallback between multiple Authentication Profiles. Know the role of the "Use Profile From Authentication Profile" setting for final authorization.
- Administrator Configuration: Know where Admins are configured ( Device > Administrators ) and how they link a username to an Authentication Profile/Sequence and an Admin Role/Access Domain. Understand Dynamic vs. Role Based types.
-
Securing Management Access:
- Interface Management Profiles: Know they control allowed services (HTTPS, SSH - disable HTTP/Telnet) and Permitted IP Addresses on specific interfaces.
- Best Practices: Emphasize using HTTPS/SSH, dedicated management network, and restricting access via Permitted IPs.
- Logging and Auditing: Know which logs track specific admin actions: System Log (login/logout), Configuration Log (config changes), Command Log (CLI commands, if enabled).
- MFA Integration: Understand MFA enhances security and is typically implemented via RADIUS or SAML integration with external MFA providers.
Admin Access, AuthN & AuthZ Knowledge Check (PCNSE Style)
Test your understanding of configuring secure administrative access.