Securing Administrative Access to Palo Alto Networks Devices
Securing administrative access to Palo Alto Networks firewalls and Panorama is paramount for maintaining network integrity and preventing unauthorized configuration changes. This involves a combination of verifying who the administrator is ( Authentication ), determining what they are allowed to do ( Authorization via Role-Based Access Control), and controlling how they connect to the device ( Device Access ).
Proper configuration of these three pillars ensures that only legitimate administrators can log in, they only have the permissions necessary for their job function, and access to management interfaces is restricted. This article provides a comprehensive guide to configuring Authentication, Authorization (RBAC), and Device Access, incorporating best practices and focusing on topics relevant to the PCNSE certification.
- Authentication: Who are you? (Verified via Local DB, RADIUS, LDAP, TACACS+, SAML, Kerberos, MFA)
- Authorization: What can you do? (Defined by Admin Roles and potentially limited by Access Domains)
- Accounting: What did you do? (Provided by Audit Logs - Config Log, System Log) - While not explicitly configured here, effective AuthN/AuthZ enables meaningful accounting.
Authentication: Verifying Administrator Identity
Authentication is the process of verifying that an administrator attempting to log in to the firewall or Panorama is who they claim to be. PAN-OS supports multiple methods to achieve this, allowing flexibility in integrating with existing identity management systems.
The core components involved in authentication are:
- Administrator Accounts: User accounts defined either locally on the device or externally in a directory service.
- Authentication Methods: The protocols and services used to validate credentials (e.g., password checks against local DB, RADIUS, LDAP query).
- Authentication Profile: Configures the settings needed to connect to and query an external authentication service (e.g., server IP, port, base DN, secret keys).
- Authentication Sequence: Defines an ordered list of Authentication Profiles to try when authenticating a user, allowing for fallback mechanisms.
Authentication Methods
PAN-OS provides support for a range of authentication methods for administrators:
-
Local Database:
- Usernames and password hashes are stored directly on the firewall or Panorama.
- Simple to configure but does not scale well and lacks central management.
- Often used for initial setup, emergency access (`admin` account), or as a fallback.
-
Requires manual creation of each administrator account under
Device > Administrators.
-
RADIUS (Remote Authentication Dial-In User Service):
- Uses an external RADIUS server (e.g., NPS, FreeRADIUS, ISE) for authentication.
-
Requires configuring a RADIUS Server Profile (
Device > Server Profiles > RADIUS) and an Authentication Profile referencing it. - Can also be used for MFA integration with RADIUS-based MFA providers (e.g., Duo, RSA SecurID).
-
LDAP (Lightweight Directory Access Protocol):
- Authenticates against an external LDAP directory (e.g., Active Directory, OpenLDAP).
-
Requires configuring an LDAP Server Profile (
Device > Server Profiles > LDAP) and an Authentication Profile referencing it. - Allows leveraging existing corporate directory credentials. Can also retrieve group memberships for role mapping.
-
TACACS+ (Terminal Access Controller Access-Control System Plus):
- Uses an external TACACS+ server (e.g., Cisco ISE, FreeTACACS) for Authentication, Authorization, and Accounting (AAA).
-
Requires configuring a TACACS+ Server Profile (
Device > Server Profiles > TACACS+) and an Authentication Profile referencing it. - Can provide granular command authorization, although PAN-OS RBAC is typically used for authorization within the firewall/Panorama context.
-
Kerberos:
- Authenticates against a Kerberos Key Distribution Center (KDC), typically within an Active Directory domain.
-
Requires configuring a Kerberos Server Profile (
Device > Server Profiles > Kerberos).
-
SAML (Security Assertion Markup Language):
- Enables Single Sign-On (SSO) by delegating authentication to an external SAML Identity Provider (IdP) like Azure AD, Okta, Ping Identity.
-
Requires configuring SAML Identity Provider server profiles (
Device > Server Profiles > SAML Identity Provider) and an Authentication Profile. - Often used for implementing MFA enforced by the IdP.
-
Multi-Factor Authentication (MFA):
- Not a standalone method in PAN-OS, but integrated via other protocols.
-
Can be achieved using:
- RADIUS with an MFA server proxying requests.
- SAML where the IdP enforces MFA.
- Potentially TACACS+ depending on the server implementation.
- Requires specific configuration within the corresponding Authentication Profile or external IdP.
Authentication Profiles & Sequence
To use external authentication services, you link them via Authentication Profiles and control the order using an Authentication Sequence.
Authentication Profile
- Purpose: Defines how the firewall/Panorama connects to and interacts with a specific authentication service (either local DB or an external server type).
-
Configuration Location:
Device > Authentication Profile. -
Key Settings:
- Name: A unique identifier for the profile.
- Type: Selects the method (Local Database, RADIUS, LDAP, TACACS+, Kerberos, SAML).
- Server Profile (for external): Links to the pre-configured Server Profile (RADIUS, LDAP, etc.) containing connection details.
- Login Attributes (LDAP/SAML): Specifies the attribute containing the username (e.g., `sAMAccountName` for AD).
- User Domain (Kerberos/SAML): Specifies the domain if needed.
- Allow List: Restricts which users or groups (retrieved from LDAP/RADIUS/SAML/TACACS+) are permitted to authenticate using this profile. If empty, all valid users on the external server are allowed (Authorization still applies).
- Advanced Settings: Timer adjustments, username modifiers, etc.
Authentication Sequence
- Purpose: Defines an ordered list of Authentication Profiles that the firewall/Panorama attempts sequentially when authenticating an administrator.
-
Configuration Location:
Device > Authentication Sequence. -
Operation:
- The firewall tries the first Authentication Profile in the sequence.
- If the user is found and successfully authenticated by that profile's method AND is permitted by the profile's Allow List (if configured), the process stops, and authentication succeeds.
- If the user is *not found* in the first profile (or its associated server), the firewall proceeds to the next profile in the sequence.
- If the user is found but authentication *fails* (e.g., wrong password), the process typically stops, and authentication fails (it doesn't usually try the next profile on a password failure).
- If the end of the sequence is reached without successful authentication, the login fails.
- Use Case: Allows fallback mechanisms. For example, try RADIUS first, and if the RADIUS server is down or the user isn't found there, fall back to checking the Local Database.
-
Assignment:
The Authentication Sequence is assigned globally under
Device > Setup > Management > Authentication Settings, or potentially overridden per administrator account (though less common).
Multi-Factor Authentication (MFA) for Administrators
Implementing MFA significantly enhances the security of administrative access. PAN-OS integrates with external MFA solutions rather than having a built-in MFA server.
Common MFA Integration Methods:
-
RADIUS with MFA Server:
- Configure a RADIUS Server Profile pointing to your MFA server (e.g., Duo Authentication Proxy, RSA Authentication Manager, NPS with Azure MFA extension).
- Configure an Authentication Profile using this RADIUS Server Profile.
- The MFA server handles the second factor challenge (push, OTP, etc.) after validating the primary password (often via LDAP passthrough).
- Adjust RADIUS timeouts in the Server Profile to accommodate MFA delays.
-
SAML with MFA-enabled IdP:
- Configure a SAML Authentication Profile pointing to your SAML IdP (e.g., Okta, Azure AD, PingFederate).
- Configure the IdP itself to require MFA for logins to the Palo Alto Networks application (PAN-OS/Panorama).
- Authentication is fully delegated to the IdP, which enforces MFA.
- This often provides the smoothest user experience (SSO + MFA).
-
TACACS+ with MFA:
- Less common for PAN-OS admin MFA but possible if the TACACS+ server supports MFA challenges/responses. Configuration depends heavily on the TACACS+ server capabilities.
Authorization: Role-Based Access Control (RBAC)
Once an administrator is authenticated, Authorization determines what actions they are permitted to perform. PAN-OS uses Role-Based Access Control (RBAC) to define granular permissions.
RBAC allows administrators to:
- Assign predefined or custom roles to administrators.
- Control access to specific Web UI tabs, CLI commands, and XML API functions based on the assigned role.
- Implement the principle of least privilege, granting users only the access required for their job responsibilities.
- (Panorama Specific) Use Access Domains to limit an administrator's scope to specific Device Groups, Templates, or virtual systems.
RBAC is configured through Administrative Roles and, on Panorama, Access Domains.
RBAC: Administrative Roles
Administrative Roles define the set of permissions granted to an administrator. PAN-OS includes several predefined roles and allows the creation of custom roles for more specific needs.
Predefined Roles (Examples):
- Superuser (read-write): Full access to all configuration and operational aspects of the device/Panorama. Equivalent to root.
- Superuser (read-only): View access to all configuration and operational aspects, but cannot make changes.
- Device Administrator (read-write): Full access to a specific firewall (or virtual system context), but limited access to global Panorama settings.
- Device Administrator (read-only): Read-only access to a specific firewall/vsys.
- Panorama Administrator: Access focused on Panorama management functions, potentially with limited device-level access.
- Virtual System Administrator: Full access within the scope of assigned virtual systems (VSYS) on a firewall.
- Audit Admin: Can view logs and manage reporting features, but generally cannot change configurations.
- (Note: Exact predefined roles may vary slightly by PAN-OS/Panorama version)
Custom Roles:
-
Configuration Location:
Device > Admin Roles(on Firewall) orPanorama > Admin Roles(on Panorama). -
Granularity:
Allows enabling/disabling access to specific:
- Web UI Tabs/Sections: Control visibility of Dashboard, ACC, Monitor, Policies, Objects, Network, Device tabs and their sub-sections.
- XML API / CLI: Grant access to specific configuration paths, operational commands, or disable CLI/API access entirely. Permissions are defined based on the XML structure of the configuration and operational commands.
- Command Line: Allow/disallow specific CLI commands or command hierarchies.
- Use Cases: Create roles for Help Desk (view logs, basic troubleshooting), Network Operations (manage interfaces, routing), Security Policy Editors (manage Security rules), Auditors (read-only access to logs/config).
RBAC: Access Domains (Panorama)
Access Domains are a Panorama-specific feature used to restrict the scope of what a Panorama administrator can see and manage. They are essential for multi-tenant environments or large organizations where different teams manage different sets of firewalls.
- Purpose: To limit an administrator's visibility and control to only specific Device Groups, Templates, Template Stacks, and managed firewalls.
-
Configuration Location:
Panorama > Access Domains. -
Functionality:
- When an administrator logs into Panorama, if they are assigned to an Access Domain, their view is filtered.
- They will only see the Device Groups, Templates, Stacks, and associated firewalls that are included in their assigned Access Domain(s).
- They cannot view or modify configurations outside their assigned domain(s).
-
Assignment:
An Access Domain is assigned to an administrator account within Panorama under
Panorama > Administrators. - 'All' Access Domain: By default, administrators might be assigned to the implicit 'All' domain, giving them visibility into everything (subject to their Admin Role permissions). Creating custom domains restricts this.
Device Access: Administrator Accounts
Creating and managing administrator accounts is the foundation of controlling device access.
Configuration:
-
Location:
Device > Administrators(on Firewall) orPanorama > Administrators(on Panorama). -
Key Fields:
- Name: The username for the administrator account.
- Authentication Profile: Selects the method used to authenticate this user (e.g., Local Database, or a specific RADIUS/LDAP/SAML/TACACS+ profile). Determines where the password/credentials are verified.
- Password/Confirm Password (for Local): Set if using Local Database authentication. Governed by Password Profile settings.
- Administrator Type (Role): Assigns the authorization level. Choose a predefined role (e.g., `superuser`, `deviceadmin`) or a Custom Role.
- Access Domain (Panorama only): Assigns the scope limitation for Panorama administrators.
-
Password Profile (Optional):
Assigns specific complexity, expiration, and reuse policies if not using the default profile. (Configured under
Device > Password Profiles).
Device Access: Securing Management Interfaces
Beyond authenticating and authorizing users, it's crucial to secure the network interfaces used for management access.
Management Interface Settings:
-
Location:
Device > Setup > Management > Management Interface Settings. - IP Configuration: Statically assign or use DHCP for the management interface IP address, netmask, and default gateway.
- Permitted IP Addresses: Critically important security control. Define specific IP addresses or subnets allowed to connect to the management interface. Restricting this to trusted management networks significantly reduces the attack surface. Leaving this as `0.0.0.0/0` (or `any`) is highly discouraged, especially on internet-facing interfaces.
- Permitted Services: Control which management protocols are allowed on the interface (e.g., HTTPS, SSH, SNMP, Ping). Disable unnecessary services.
Interface Management Profiles:
-
Location:
Network > Network Profiles > Interface Mgmt. - Purpose: Applied to *data plane* interfaces (not the dedicated MGT port) to allow management access (HTTPS, SSH, Ping, SNMP, etc.) via those interfaces.
- Configuration: Similar to MGT Interface Settings, allows defining permitted IPs and services specifically for management access via data ports.
-
Application:
Assigned to Layer 3 interfaces under
Network > Interfaces > Ethernet > [Select Interface] > Advanced > Management Profile.
Device Access: Other Related Settings
Additional settings contribute to securing administrative access:
-
Password Profiles:
(
Device > Password Profiles) Define password complexity requirements (length, character types), expiration policies, and reuse prevention for local administrator accounts. -
Session Timeouts:
(
Device > Setup > Management > General Settings) Configure idle timeouts for Web UI and CLI sessions to automatically log out inactive administrators. -
Login Banner / Message of the Day:
(
Device > Setup > Management > General Settings) Configure banners displayed before login (e.g., legal notices, authorized use warnings). -
Certificate for Management Interface:
(
Device > Setup > Management > General Settings) Assign a specific certificate (ideally from a trusted CA or enterprise PKI) for HTTPS management access to avoid browser warnings and ensure identity. -
TLS Service Profile:
(
Device > Setup > Management > Management Interface Settingsor Interface Management Profile) Define the allowed TLS/SSL versions and cipher suites for secure management connections (HTTPS, SSL VPN). -
SSH Service Profile:
(
Device > Setup > Management > Management Interface Settingsor Interface Management Profile) Define allowed SSH algorithms and parameters.
Troubleshooting Administrative Access Issues
Common issues and troubleshooting steps:
-
Login Failure (Incorrect Password/Username):
- Verify username and password case sensitivity.
- Check if the account is locked out (see System Logs or use `show admins` CLI). Reset password if needed (requires another admin).
- Verify the correct Authentication Profile is selected/configured for the account.
- For external auth, check if the user exists and password is correct on the external server.
-
Login Failure (External Server Issues - RADIUS/LDAP/TACACS+):
-
Connectivity:
Can the firewall ping the authentication server IP? (
ping source). Are firewall rules/routing correct?host - Service Ports: Are the correct ports open between firewall and server (e.g., UDP 1812/1813 for RADIUS, TCP/UDP 389/636 for LDAP, TCP 49 for TACACS+)? Check Traffic Logs.
- Server Profile Config: Verify server IP/FQDN, port, shared secret (RADIUS/TACACS+), Base DN/Bind DN/Password (LDAP), certificate validity (LDAPS/SAML).
- Authentication Profile Config: Verify the correct Server Profile is selected. Check the Allow List if configured.
-
Test Command:
Use `test authentication authentication-profile
username password` CLI command to isolate issues. - Server Logs: Check logs on the RADIUS/LDAP/TACACS+ server itself for errors.
- Debugging: Use `debug authentication on debug` and view `less mp-log authmgr.log` (Use with caution, can be verbose).
-
Connectivity:
Can the firewall ping the authentication server IP? (
-
Login Failure (SAML):
- Verify IdP configuration (Entity ID, SSO URL, certificate).
- Verify firewall SAML Auth Profile config (matches IdP settings).
- Check system clock synchronization between firewall/Panorama and IdP.
- Check IdP logs for assertion generation errors.
-
Login Success, but Limited Access (Authorization Failure):
- Admin Role Permissions: Verify the assigned Admin Role (predefined or custom) has the necessary permissions enabled for the desired Web UI tabs, CLI commands, or API functions.
- Access Domain (Panorama): Ensure the administrator is assigned to the correct Access Domain that includes the target Device Group/Template/Device.
- Check System Logs for authorization failure messages.
-
Cannot Connect to Management Interface:
-
Permitted IPs:
Verify your source IP address is included in the allowed list under
Device > Setup > Management > Management Interface Settingsor the relevant Interface Management Profile. - Permitted Services: Ensure the protocol you are using (HTTPS, SSH) is enabled for management access on that interface.
- Network Connectivity: Basic IP reachability, routing, upstream firewall rules.
-
Permitted IPs:
Verify your source IP address is included in the allowed list under
-
MFA Failures:
- Check MFA server/proxy logs (e.g., Duo Auth Proxy).
- Verify RADIUS/SAML configuration details match MFA provider requirements.
- Increase RADIUS timeouts if MFA challenges are timing out.
Best Practices for Administrative Access
- Principle of Least Privilege: Assign administrators Custom Roles with only the permissions absolutely necessary to perform their duties. Avoid using `superuser` unless essential.
- Unique Accounts: Do not share administrator accounts. Create unique accounts for each individual user to ensure accountability via logs.
-
Strong Authentication:
- Use external authentication (RADIUS, LDAP, SAML, TACACS+) integrated with corporate directories whenever possible.
- Implement Multi-Factor Authentication (MFA) for all administrative access.
- Enforce strong password policies using Password Profiles for local accounts.
-
Secure Management Plane:
- Strictly limit access using Permitted IP addresses on the management interface and Interface Management profiles.
- Disable unused management services (e.g., Telnet, HTTP).
- Use a trusted certificate for the HTTPS management interface.
- Consider using a dedicated, out-of-band management network.
- Use Access Domains (Panorama): Effectively segment administrative responsibilities in multi-tenant or large environments using Access Domains.
- Regular Audits: Periodically review administrator accounts, roles, access domains, and authentication settings. Disable or remove accounts for personnel who no longer require access.
- Monitor Audit Logs: Regularly review Configuration Logs (to see who changed what) and System Logs (for login attempts, failures, authorization issues). Forward logs to a central SIEM.
- Authentication Sequence Fallback: Use Authentication Sequences carefully. Consider the security implications of falling back to less secure methods like the local database.
Illustrations: Admin Login Flowchart
This flowchart outlines the authentication and authorization process for an administrator login attempt.
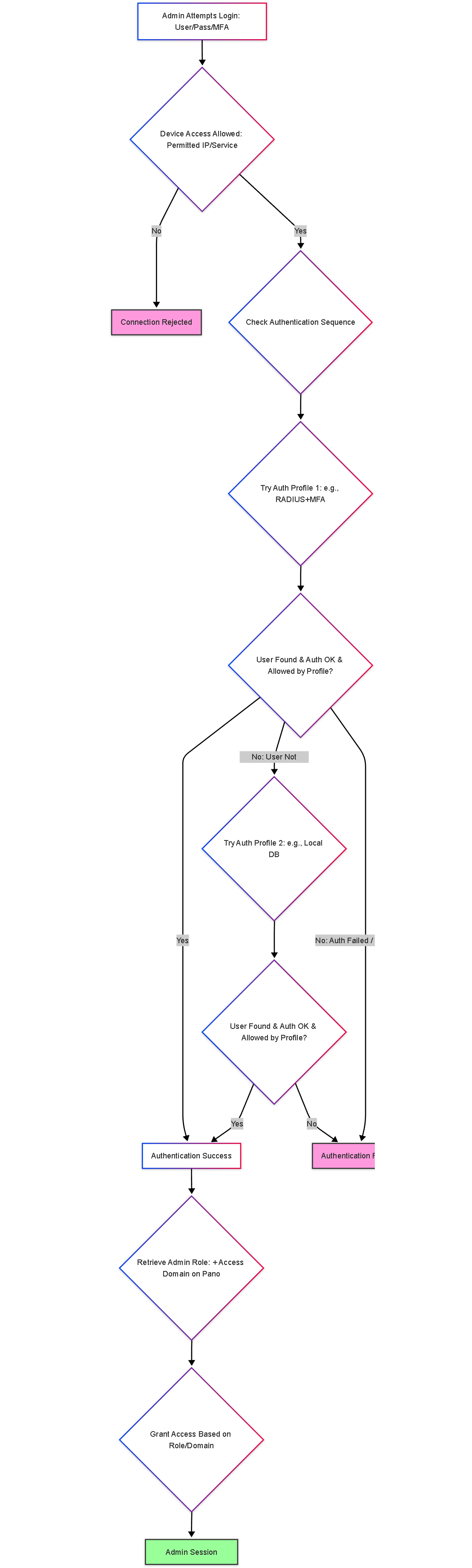
Simplified flowchart of the admin login process, including device access checks, authentication sequence, and role-based authorization.
Illustrations: External Authentication Sequence
This sequence diagram shows an example interaction using RADIUS and then Local DB fallback.
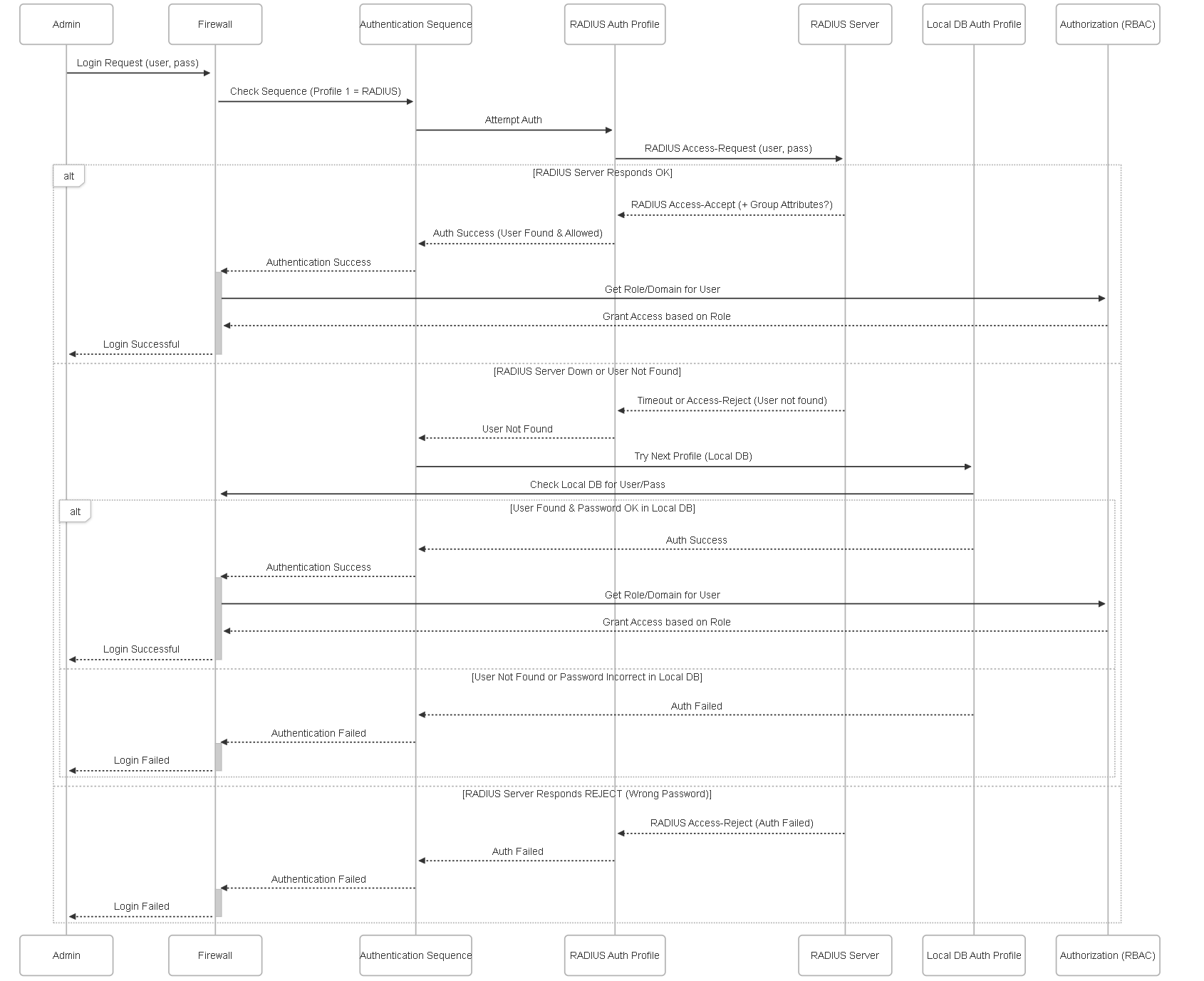
Sequence diagram illustrating the Authentication Sequence trying RADIUS first, then falling back to Local Database if the user is not found on RADIUS.
Illustrations: Configuration Relationship Graph
This graph shows how the different configuration objects relate.
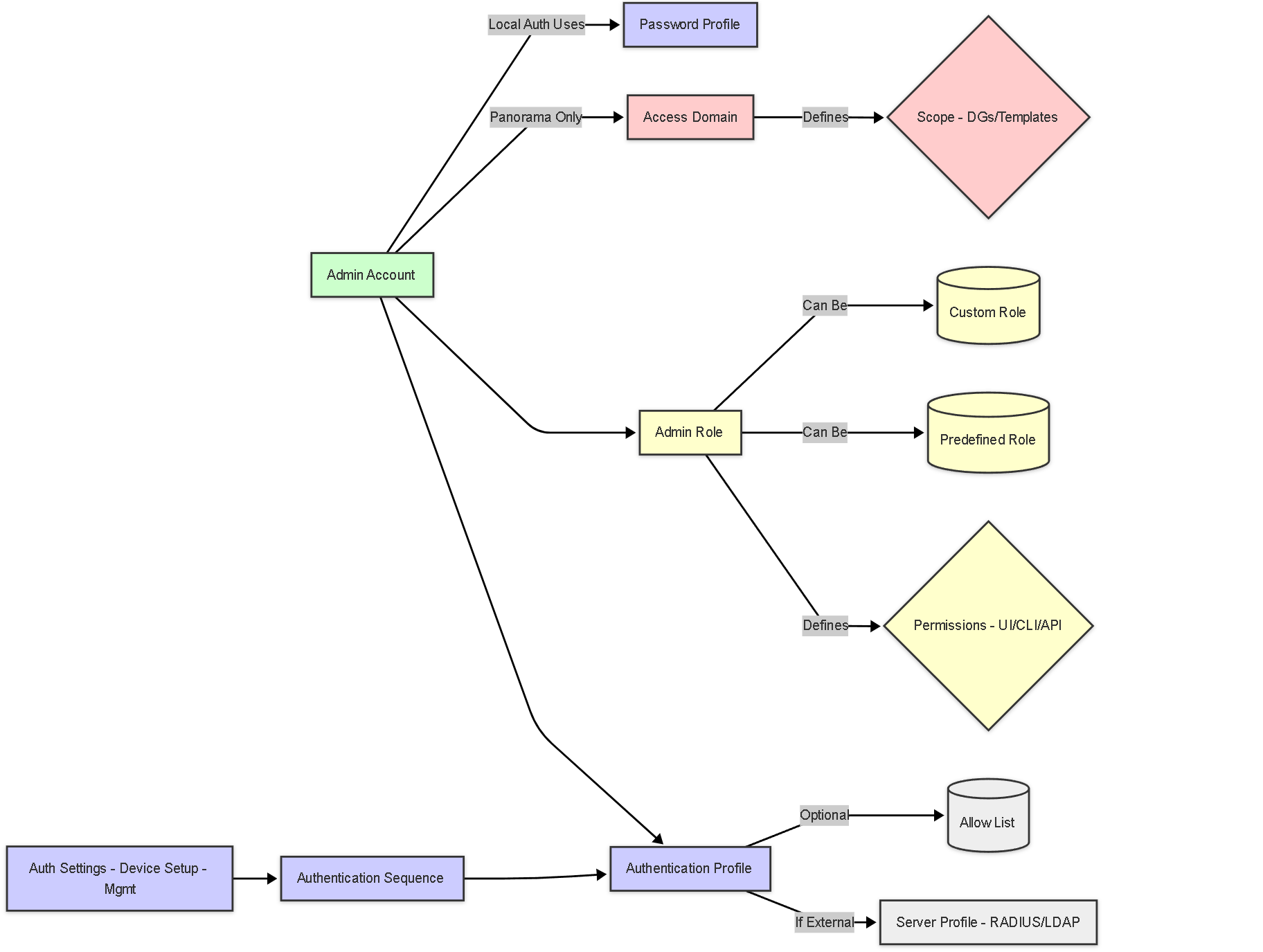
Graph showing relationships: Admin account links Authentication Profile and Role (and Access Domain on Panorama). Authentication Sequence orders profiles. Roles define permissions.
Illustrations: Admin Session State Diagram
This state diagram shows the lifecycle of an administrator's management session.
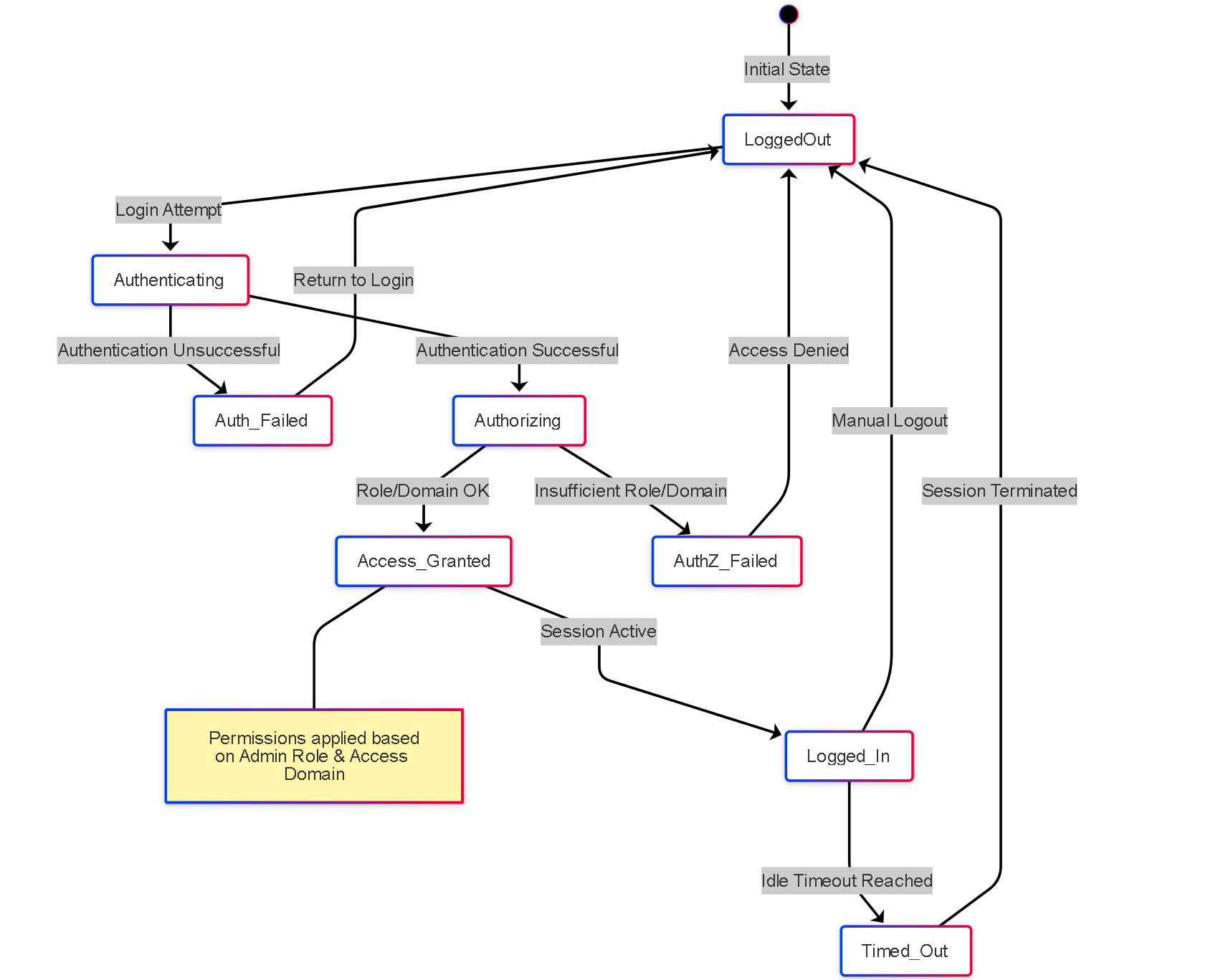
State transitions for an administrative session, from login attempt through authentication, authorization, active session, and termination (logout or timeout).
PCNSE Focus Points
- AAA Components: Understand Authentication (who), Authorization (what), and Accounting (what happened via logs) as applied to administrative access.
- Authentication Methods: Know the available methods (Local, RADIUS, LDAP, TACACS+, SAML, Kerberos) and their use cases.
- Configuration Objects: Differentiate between Server Profiles, Authentication Profiles, and Authentication Sequences and how they work together.
- Authentication Sequence Logic: Understand the order of processing and when the sequence stops or continues.
- MFA Integration: Recognize that MFA relies on RADIUS or SAML integration.
- RBAC Concepts: Understand the purpose of Admin Roles (permissions) and Access Domains (scope on Panorama). Know common predefined roles (Superuser, Device Admin) and the value of custom roles for least privilege.
- Admin Account Configuration: Know the key elements linking authentication and authorization: Authentication Profile, Admin Role, Access Domain (Panorama).
- Management Access Security: Emphasize the importance of restricting access via Permitted IPs on the MGT interface and Interface Management Profiles.
- Troubleshooting: Be familiar with common login failure causes (credentials, server connectivity, config errors, permissions, permitted IPs) and key troubleshooting tools (`test authentication`, logs, config verification).
PCNSE Prep Quiz: Admin Authentication, Authorization & Device Access
Test your knowledge of securing administrative access.