Configuring Application-Based QoS in Palo Alto Networks Firewalls
1. Introduction to Palo Alto Networks Application-Based QoS
Application-based Quality of Service (QoS) in Palo Alto Networks firewalls is a critical feature for network administrators aiming to ensure predictable performance for essential applications and users. Unlike traditional QoS mechanisms that rely solely on port numbers or IP addresses, Palo Alto Networks leverages its core technologies, primarily App-ID™ and optionally User-ID™ , to provide granular control over bandwidth allocation. This allows for the prioritization of business-critical applications (e.g., SAP, Salesforce, VoIP services) and the limitation of non-critical or bandwidth-intensive applications (e.g., recreational streaming, peer-to-peer file sharing).
By integrating deep application awareness into QoS policies, PAN-OS® enables precise traffic management. This ensures that even if applications use dynamic ports or try to evade detection through encryption (where SSL Forward Proxy decryption is enabled), they can still be accurately identified and subjected to defined QoS treatments. This study guide provides a comprehensive overview of configuring and managing QoS on Palo Alto Networks Next-Generation Firewalls (NGFWs), aligning with PCNSE certification objectives.
2. Core QoS Concepts in PAN-OS
Before diving into configuration, it's essential to understand the key components and concepts that underpin QoS in the Palo Alto Networks ecosystem:
- QoS Profile: A QoS Profile is a template that defines up to eight traffic classes. Each class is assigned a priority (real-time, high, medium, low) and can have configured values for maximum egress bandwidth (Egress Max) and guaranteed egress bandwidth (Egress Guaranteed). These profiles are reusable across different QoS policies and interfaces.
- QoS Classes: PAN-OS supports up to eight distinct QoS classes (Class 1 to Class 8) within a single QoS Profile. These classes are used to segregate traffic based on application, user, or other criteria, each receiving different bandwidth and priority treatment. Class 1 typically has the highest priority, and Class 8 the lowest, though specific priority labels (real-time, etc.) determine actual scheduling behavior.
-
Priority Levels:
Palo Alto Networks firewalls support four priority levels for QoS classes:
- Real-time: Highest priority, suitable for latency-sensitive applications like VoIP and video conferencing.
- High: For business-critical applications that require preferential treatment but are less latency-sensitive than real-time traffic.
- Medium: For general business applications or important web traffic.
- Low: For non-critical applications, bulk data transfers, or recreational traffic that can tolerate delays.
- Egress Max (per class): This setting within a QoS Profile defines the maximum amount of bandwidth a specific QoS class can consume on an interface. This is an absolute cap for that class.
- Egress Guaranteed (per class): This setting within a QoS Profile specifies the minimum amount of bandwidth reserved for a specific QoS class on an interface. This bandwidth is available to the class even if there is congestion. If not fully utilized by the class, it can be borrowed by other classes based on their priority and Egress Max settings.
- QoS Interface Settings: QoS must be enabled on a specific physical egress interface (or subinterface, Aggregate Ethernet interface). Here, you define the total Egress Max bandwidth available for all QoS-managed traffic on that interface and assign a default QoS Profile for clear text and/or tunneled traffic.
- QoS Policy Rules: These rules tie everything together. They define the matching criteria (source/destination zones, addresses, users via User-ID, applications via App-ID, services) and assign traffic matching these criteria to a specific QoS class within a chosen QoS Profile.
- App-ID Integration: The foundation of Palo Alto Networks QoS. App-ID accurately identifies applications regardless of port, protocol, encryption (with decryption), or evasive tactics. This identification is then used in QoS Policy Rules to classify traffic.
- User-ID Integration: Allows QoS policies to be applied based on user identity or group membership, providing even more granular control (e.g., prioritizing traffic for the executive team).
3. Prerequisites for QoS Configuration
-
App-ID and User-ID Enabled and Functional:
Since Palo Alto Networks QoS heavily relies on application and user identification:
- Ensure App-ID is enabled and application signatures are up-to-date (via dynamic updates). Accurate application identification is paramount.
- If user-based QoS is required, User-ID must be configured and correctly mapping IP addresses to users. This involves configuring User-ID agents, Active Directory integration, or other supported mapping methods.
-
Interface Configuration and Egress Path Identification:
Clearly identify the egress interfaces through which the traffic to be managed will exit the firewall. QoS policies are applied based on egress interfaces.
This includes:
- Physical interfaces
- Subinterfaces (e.g., eth1/1.10)
- Aggregate Ethernet (AE) interfaces
- Tunnel interfaces (for QoS on VPN traffic, ensure the tunnel interface is selected)
- VLAN interfaces
- Firewall Model Support and PAN-OS Version: Verify that your specific Palo Alto Networks firewall model and PAN-OS version support QoS on the desired interface types and offer the required scale. While most modern platforms have robust QoS capabilities, there might be differences, especially with older hardware or specific VM-Series deployments. Always consult the official Palo Alto Networks documentation for your model and PAN-OS version. You can refer to the QoS Interface Settings page on the Palo Alto Networks TechDocs site for the most current information.
- Bandwidth Assessment: Have a clear understanding of the total available bandwidth on the egress interfaces where QoS will be applied. This information is critical for setting realistic Egress Max values on interfaces and for classes within QoS Profiles.
4. Detailed Configuration Steps in PAN-OS
Step 1: Create a QoS Profile
A QoS Profile is where you define your traffic classes and their bandwidth/priority characteristics.
- Navigate to Network > Network Profiles > QoS Profile in the PAN-OS web interface.
- Click Add to create a new QoS profile.
- Provide a descriptive Name for the profile (e.g., `Standard_Corp_QoS_Profile`).
-
The profile allows configuration for up to eight classes (Class 1 through Class 8). For each class you intend to use:
- Class Name (Optional but Recommended): You can provide a friendly name for each class (e.g., `VoIP_Traffic`, `Critical_Apps`, `General_Web`). This is not directly configured in the class row but is good for documentation. The QoS Policy rule is what maps traffic to a numbered class.
-
Priority:
Select a priority from the dropdown:
-
real-time: Highest priority, minimal latency. Use for VoIP, video conferencing. -
high: For important business applications (e.g., ERP, CRM). -
medium: For general web browsing and less critical applications. -
low: For bulk transfers, non-essential traffic. (Default for unclassified traffic if a default profile is used).
-
- Egress Max (Mbps or Kbps): Define the absolute maximum bandwidth this class can consume. Traffic exceeding this limit for the class will be dropped or queued according to PAN-OS internal mechanisms if other classes also contend for bandwidth.
- Egress Guaranteed (Mbps or Kbps): Specify the minimum bandwidth that will be available to this class. This bandwidth is reserved. The sum of Egress Guaranteed bandwidth for all classes on an interface should not exceed the interface's Egress Max (or physical capacity).
-
Example:
Class Priority Egress Max (Mbps) Egress Guaranteed (Mbps) Typical Use Case (Conceptual) Class 1 real-time 5 2 VoIP Class 2 high 20 10 SAP, Office 365 Class 3 medium 50 5 General Web Browsing Class 4 low 10 1 Software Updates, Large File Transfers (Non-Urgent) Classes 5-8 can be configured similarly or left at default (low priority, minimal/no guarantee). - Click OK to save the QoS Profile.
Step 2: Enable QoS on Egress Interfaces
QoS must be explicitly enabled on the egress (outgoing) interface(s) where you want to manage traffic bandwidth.
- Go to Network > QoS .
- Click Add to configure QoS on a new interface, or select an existing entry to modify.
-
Select the desired
Interface Name
from the dropdown list (e.g.,
ethernet1/1,ae1,tunnel.1). - Check the box for Turn on QoS feature on this interface .
- Default QoS Profile for Clear Text Traffic: Assign a QoS Profile (created in Step 1) that will be applied to all clear text (non-tunneled) traffic on this interface that is not explicitly matched by a QoS Policy Rule. You can also select the specific Class within this profile to be the default. Often, a 'low' priority class is chosen as the default.
- Default QoS Profile for Tunneled Traffic: (Optional) If the interface handles VPN tunnel traffic (e.g., IPSec, GlobalProtect), you can assign a different default QoS Profile and Class for traffic exiting through tunnels on this interface. This is useful if you want different baseline QoS treatment for VPN traffic.
- Set the Egress Max (Mbps or Kbps) for the interface. This is the total maximum bandwidth available for all QoS-managed traffic egressing this interface. This value should typically be set to the known bandwidth capacity of the link (e.g., your ISP circuit speed).
- The Egress Guaranteed field for the interface is typically not directly configurable here but is an aggregation of the guaranteed bandwidth of all classes active on the interface. It is important that the sum of Egress Guaranteed from your QoS Profiles classes does not exceed the physical capability or the Egress Max of the interface.
- Click OK to apply the settings. Repeat for all necessary egress interfaces.
Step 3: Define QoS Policy Rules
QoS Policy Rules determine which traffic gets assigned to which QoS Class within a QoS Profile.
- Navigate to Policies > QoS .
- Click Add to create a new QoS policy rule.
-
General Tab:
- Provide a descriptive Name for the rule (e.g., `Prioritize_VoIP`, `Limit_Guest_Streaming`).
- Optionally, add Tags and a Description.
-
Source Tab:
-
Source Zone:
Add source zones (e.g.,
trust,guest-wifi). - Source Address: Specify source IP addresses, address groups, or regions.
-
Source User:
If User-ID is configured, specify source users or groups (e.g.,
domain\sales_users,any).
-
Source Zone:
Add source zones (e.g.,
-
Destination Tab:
-
Destination Zone:
Add destination zones (e.g.,
untrust,dmz). - Destination Address: Specify destination IP addresses or address groups.
-
Destination Zone:
Add destination zones (e.g.,
-
Application Tab:
-
This is where App-ID integration shines. Click
Add
and select specific applications (e.g.,
skype,salesforce,youtube), application filters, or application groups that this rule will apply to. - For example, to prioritize all VoIP traffic, you might select an Application Filter for `subcategory voice-and-video`.
-
This is where App-ID integration shines. Click
Add
and select specific applications (e.g.,
-
Service/URL Category Tab:
-
Service:
Typically leave as
application-defaultto let App-ID handle service identification. Can be used to specify TCP/UDP ports if needed, but App-ID is preferred. - URL Category: (Requires a URL Filtering license) Optionally, you can refine the rule by URL categories.
-
Service:
Typically leave as
-
Action Tab:
- Action: This is implicitly "Allow" as QoS policies only classify traffic that is already permitted by Security Policies.
- Policy Type: Ensure this is set to `QoS`.
- QoS Profile: Select the QoS Profile you created in Step 1.
- Class: From the dropdown, choose the specific QoS Class (1-8) within the selected QoS Profile to which matching traffic will be assigned. For example, traffic matching this rule for VoIP applications would be assigned to 'Class 1' (which you configured with 'real-time' priority in the QoS Profile).
-
Marking:
(Optional) Configure Differentiated Services Code Point (DSCP) or IP Precedence marking if you want the firewall to re-mark packets. You can choose to preserve existing markings, clear them, or apply a new DSCP/IP Precedence value (e.g.,
DSCP EFfor VoIP). This is useful for interoperability with downstream QoS-aware devices.- None: No marking action is taken by this rule. Existing DSCP values are preserved.
- Clear ToS: Clears any existing ToS/DSCP markings (sets to 0).
- DSCP: Allows you to specify a DSCP codepoint to mark matching packets. Common values include EF (Expedited Forwarding - 46), AF classes (Assured Forwarding).
- IP Precedence: Allows you to specify an IP Precedence value (0-7).
- Click OK to save the policy rule.
- Rule Order: QoS policy rules are evaluated top-down, similar to Security Policy rules. The first rule that matches the traffic is applied. Ensure your rules are ordered logically (e.g., more specific rules before more general ones).
Step 4: Commit the Configuration
After configuring the QoS profiles, enabling QoS on interfaces, and defining QoS policy rules, you must commit the changes for them to take effect on the firewall.
- Click Commit at the top right of the PAN-OS web interface.
- Review the changes if desired, then click Commit again to apply.
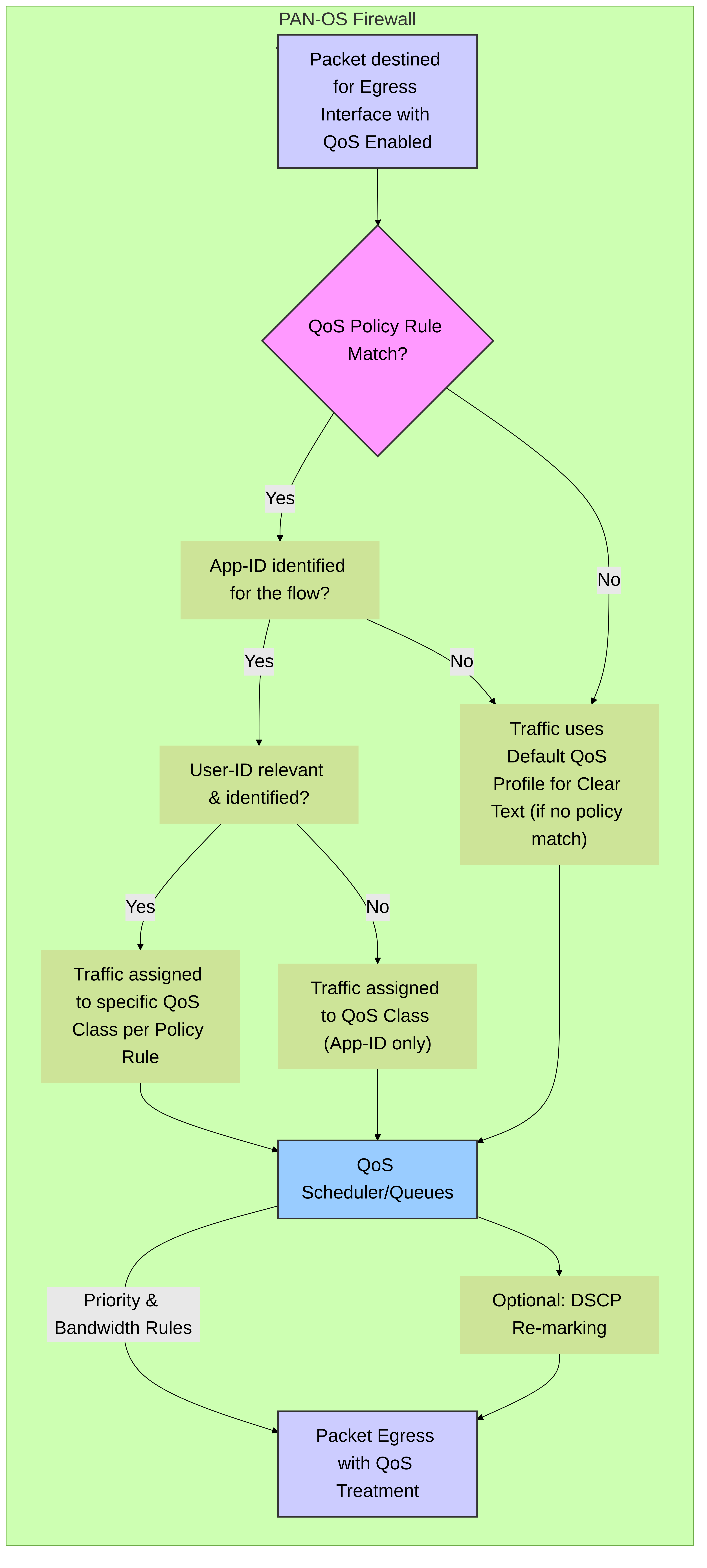
Simplified packet flow focusing on QoS decision points at the egress interface within a Palo Alto Networks firewall. It shows how App-ID, User-ID, and QoS Policy Rules contribute to class assignment, leading to the QoS scheduler for prioritized egress.
5. Verification and Monitoring
After committing your QoS configuration, it's crucial to verify that it's working as expected and to monitor its ongoing effectiveness. PAN-OS provides several tools for this:
GUI Verification:
-
Network > QoS > Statistics:
- Select the interface where QoS is enabled from the list.
- Click on Statistics (often a tab or button associated with the selected interface in the QoS interface list).
-
This view shows real-time statistics for each QoS class on that interface, including:
- Tx Bytes/Packets: Number of bytes/packets transmitted per class.
- Dropped Bytes/Packets: Number of bytes/packets dropped per class (indicates congestion and QoS shaping in action).
- Bandwidth Utilization: Current bandwidth usage per class.
- Active sessions per class.
- These statistics are invaluable for understanding how bandwidth is being distributed and if classes are hitting their Egress Max limits.
-
Monitor > Traffic Logs:
- Traffic logs can show the QoS class applied to specific sessions.
- Add the "QoS Rule" and "QoS Class" columns to your log view (if not already visible by default) by clicking the small down arrow on any column header and selecting them from the "Columns" submenu.
- Filter logs by application, user, or IP to verify that specific traffic types are being classified into the correct QoS class as per your QoS policy rules.
-
Application Command Center (ACC):
- The ACC can provide insights into bandwidth consumption by application. While not a direct QoS monitor, it helps identify top bandwidth consumers, which can inform QoS policy adjustments.
- You can filter ACC views by QoS rule if your PAN-OS version supports such detailed filtering in ACC, or use the information to correlate with QoS statistics.
CLI Verification:
The PAN-OS CLI offers powerful commands for checking QoS status and statistics:
admin@PA-FW> show qos interface <interface_name> statistics
Example:
show qos interface ethernet1/1 statistics
This command provides detailed per-class statistics for the specified interface, similar to the GUI view, including packets, bytes, drops, and current bandwidth utilization for each of the 8 classes.
admin@PA-FW> show running qos-policy-rule
This command displays the configured QoS policy rules, allowing you to verify their parameters and order.
admin@PA-FW> show session id <session_id>
For a specific session, this command can show if QoS is applied and which class it's assigned to (look for QoS-related fields in the output).
admin@PA-FW> show counter global filter aspect qos
This command can show various global counters related to QoS processing, useful for advanced troubleshooting to see if packets are being dropped at different stages of QoS pipeline or for specific reasons.
6. Palo Alto Networks QoS Best Practices
- Identify and Prioritize Critical Applications: Use App-ID to accurately identify business-critical applications (VoIP, video conferencing, ERP, CRM) and assign them to higher priority QoS classes with appropriate guaranteed bandwidth.
- Limit Non-Essential Traffic: Identify non-critical, high-bandwidth applications (recreational streaming, P2P, large downloads) and assign them to lower priority classes with limited Egress Max bandwidth and minimal or no guaranteed bandwidth.
- Start Conservatively with Guaranteed Bandwidth: The sum of Egress Guaranteed bandwidth for all classes on an interface should not exceed ~70-80% of the interface's Egress Max or actual link capacity. This leaves room for overhead and burst traffic. Over-subscribing guaranteed bandwidth can lead to inefficiencies.
- Use Realistic Egress Max on Interfaces: Set the Egress Max on the QoS-enabled interface to match the actual available bandwidth of the link (e.g., ISP circuit speed). Setting it too high makes shaping ineffective; too low unnecessarily restricts bandwidth.
-
Monitor and Adjust:
QoS is not a "set and forget" feature. Regularly monitor QoS statistics (
Network > QoS > Statistics, CLI commands) and traffic logs to ensure policies are working as intended and to make adjustments based on observed traffic patterns and business needs. - Leverage User-ID for Granular Control: Where appropriate, use User-ID to apply specific QoS policies to different user groups (e.g., providing higher priority for executives or specific departments).
- Test Thoroughly: After implementing or modifying QoS policies, test critical applications to confirm they are receiving the desired performance.
- DSCP Marking for End-to-End QoS: If your network includes other QoS-aware devices (switches, routers), consider using DSCP marking in your QoS policy rules on the Palo Alto Networks firewall. This allows downstream devices to honor the prioritization set by the firewall. Ensure consistency in DSCP policies across the network.
- Be Mindful of Performance Impact: While QoS is highly optimized, extensive QoS processing on very high-throughput firewalls can consume some CPU resources. Monitor firewall resource utilization after implementing complex QoS policies, especially on lower-end models. Refer to the Palo Alto Networks performance datasheets for guidance.
- Document Your QoS Strategy: Maintain clear documentation of your QoS profiles, classes, application mappings, and policy goals. This is invaluable for troubleshooting and future modifications.
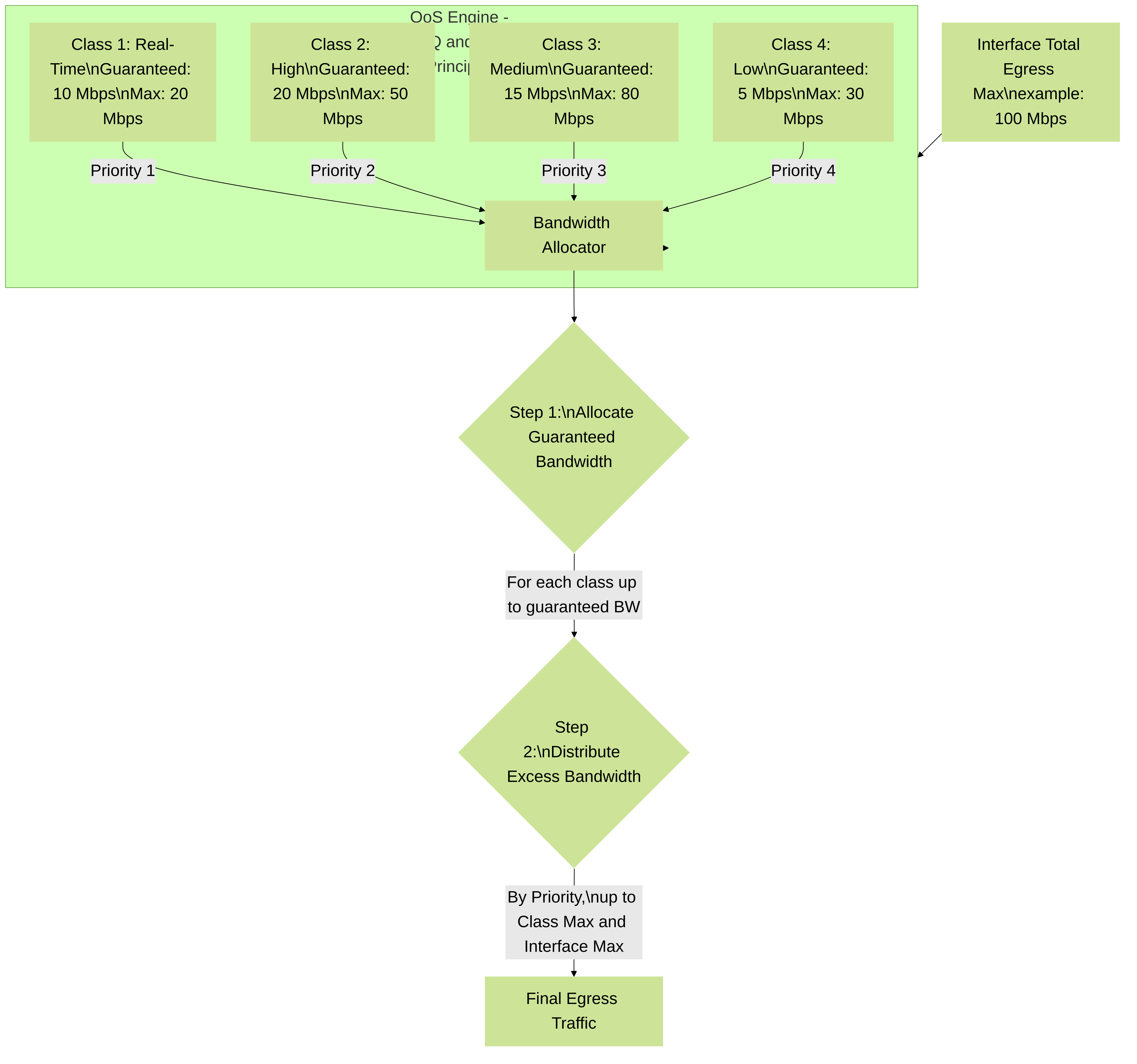
Conceptual diagram of bandwidth allocation within the Palo Alto Networks QoS engine. It shows how an interface's total Egress Max is distributed among different QoS classes based on their configured 'Egress Guaranteed', 'Egress Max', and 'Priority' levels, reflecting principles similar to Class Based Queuing (CBQ) or Hierarchical QoS Frameworks (HQF).
7. Troubleshooting Common QoS Issues on Palo Alto Networks Firewalls
-
Traffic Not Matching Expected QoS Class:
-
App-ID Misidentification:
Verify App-ID is correctly identifying the application in
Monitor > Trafficlogs. Ensure App-ID signatures are up-to-date. Consider if SSL decryption is needed for accurate identification. - QoS Policy Rule Order: Rules are processed top-down. A more general rule above a specific one might match first. Re-order rules as needed.
- Incorrect Source/Destination/User Criteria: Double-check zones, IP addresses, and User-ID mappings in the QoS policy rule.
- Security Policy Blocking Traffic: QoS policies only apply to traffic permitted by Security Policy rules. If traffic is blocked, QoS is irrelevant.
-
App-ID Misidentification:
Verify App-ID is correctly identifying the application in
-
Bandwidth Limits Not Enforced as Expected:
-
Interface Egress Max Too High:
If the interface Egress Max in QoS settings (
Network > QoS) is set higher than the actual physical link speed, the firewall won't be the bottleneck, and shaping might not occur as expected. - Incorrect Egress Max/Guaranteed in QoS Profile: Review class settings in the QoS Profile. Ensure Egress Max per class is not overly generous if you intend to limit it.
- QoS Not Enabled on Correct Egress Interface: Verify QoS is enabled on the actual egress interface for the traffic flow in question.
- Licensed Bandwidth Exceeded (VM-Series): For VM-Series firewalls, ensure QoS bandwidth settings do not exceed the licensed throughput of the virtual firewall.
-
Interface Egress Max Too High:
If the interface Egress Max in QoS settings (
-
High Latency for Prioritized Traffic:
- Insufficient Guaranteed Bandwidth: The 'real-time' or 'high' priority class may not have enough 'Egress Guaranteed' bandwidth, especially during congestion.
- Overall Interface Saturation: If the entire link is saturated beyond its Egress Max, even prioritized traffic will suffer. QoS manages contention on the link; it cannot create more bandwidth.
- Upstream/Downstream Bottlenecks: The latency might be introduced by other devices in the path, not the Palo Alto Networks firewall.
-
Dropped Packets in High Priority Classes:
- Egress Max for Class Reached: Even high-priority classes have an Egress Max. If they try to exceed it consistently, packets will be dropped.
- Overall Interface Egress Max Reached: If the total interface Egress Max is hit, drops can occur across classes depending on the queuing mechanisms.
-
Use
show qos interface <name> statisticsto check drop counters for each class.
-
Verifying QoS Operation with Packet Captures:
-
Take packet captures on ingress and egress interfaces (
Monitor > Packet Capture). - On egress, if DSCP marking is configured, check the ToS/DSCP field in the IP header to verify if packets are being marked correctly.
- Analyzing timing and packet loss in captures can help diagnose QoS effectiveness.
-
Take packet captures on ingress and egress interfaces (
8. QoS in Palo Alto Networks SD-WAN
Palo Alto Networks SD-WAN (Software-Defined Wide Area Network) functionality, integrated into PAN-OS, also leverages QoS principles to optimize application performance across multiple WAN links.
- Path Quality Monitoring and QoS: SD-WAN continuously monitors the quality (latency, jitter, packet loss) of available paths. QoS policies help prioritize applications. When SD-WAN path selection occurs, it can consider the QoS requirements of an application. For example, real-time voice traffic (identified by App-ID and mapped to a high-priority QoS class) can be steered over the path with the best latency and jitter.
- Application-Based Path Selection: QoS policies define the importance of applications. SD-WAN policies use this application awareness (via App-ID) along with path health to make intelligent forwarding decisions. A critical application might be assigned to a QoS class with high priority and guaranteed bandwidth, and the SD-WAN policy will ensure it uses the best available link that can meet these requirements.
- Traffic Shaping on SD-WAN Links: QoS shaping (Egress Max, Egress Guaranteed) is applied on each individual SD-WAN member interface. This ensures that even if multiple applications are directed over a single link, the prioritization defined in QoS policies is enforced.
- Integration: QoS Profiles and Policies are configured as described in previous sections. SD-WAN policies then reference applications or services. The underlying QoS mechanism ensures that traffic routed by SD-WAN decisions receives the appropriate bandwidth and priority treatment on the chosen egress link.
-
Configuration Example Scenario:
- Define a QoS Profile with classes for VoIP (real-time), Critical SaaS (high), and General Internet (medium).
- Apply this QoS Profile and enable QoS on all physical interfaces participating in the SD-WAN (e.g., MPLS, Internet broadband). Set appropriate Interface Egress Max for each link.
- Create QoS Policy Rules to map VoIP applications to the 'real-time' class, SaaS apps to 'high', etc.
- Configure SD-WAN Link Management and Traffic Distribution profiles to define how different applications should be treated regarding path selection (e.g., VoIP prefers lowest latency link, SaaS prefers a link with low packet loss).