VM-Series Bootstrapping Explained
Overview: What is Bootstrapping?
Bootstrapping is the process of automating the initial configuration and provisioning of a Palo Alto Networks VM-Series firewall when it is launched for the first time. Instead of manually configuring each new virtual firewall instance, bootstrapping allows the VM-Series to automatically retrieve and apply a baseline configuration, licenses, software updates, and content updates upon its first boot.
Goals of Bootstrapping:
- Automation: Eliminate manual configuration for initial deployment, saving time and reducing errors.
- Scalability: Enable rapid deployment of multiple VM-Series firewalls, essential for dynamic environments like public clouds and virtualized data centers. Supports auto-scaling scenarios where firewalls are launched automatically based on load.
- Consistency: Ensure all deployed firewalls start with a standardized baseline configuration and security posture.
- Day-Zero Readiness: Bring the firewall online quickly with necessary network settings, licenses, content updates, and potentially management connectivity (e.g., registered to Panorama).
Bootstrap Components: The Bootstrap Package
The core of bootstrapping involves providing the VM-Series firewall with a "bootstrap package" during its initial launch. This package is essentially a specific folder structure containing various files that dictate the firewall's initial state.
The standard folder structure looks like this:
/
├── config/
│ ├── init-cfg.txt
│ └── bootstrap.xml (Optional)
├── content/
│ └── panupv2-all-apps-*.tgz
│ └── panupv2-all-threats-*.tgz
│ └── panupv2-all-antivirus-*.tgz
│ └── panupv2-all-wildfire-*.tgz (if applicable)
├── license/
│ └── authcodes (File containing one auth code per line)
│ └── *.key (License key files)
├── software/
│ └── PANOS_vm-*.ova|qcow2|vhdx... (PAN-OS image for upgrade)
└── plugins/
└── vm_series-*.tgz (VM-Series plugin)
└── panorama-*.tgz (Panorama plugin, if needed)
└── other-plugin-*.tgzThe next sections detail the key files and folders within this package.
Bootstrap Components:
init-cfg.txt
The
init-cfg.txt
file, located in the
/config/
folder of the bootstrap package, is arguably the
most critical component
for automated bootstrapping. It contains essential day-zero parameters applied *before* the firewall generates its initial running configuration.
This file allows the firewall to establish basic network connectivity, contact management systems (like Panorama), and identify itself.
Key Parameters in `init-cfg.txt`:
-
Management Interface Settings:
-
type=staticortype=dhcp-client: Defines how the management interface gets its IP. -
ip-address=(if static) -
netmask=(if static) -
default-gateway=(if static)
-
-
Networking:
-
hostname= -
dns-primary=/dns-secondary= -
ntp-primary=/ntp-secondary=
-
-
Panorama Settings (Crucial for Managed Deployments):
-
panorama-server=(Panorama IP or FQDN) -
panorama-server-2=(Secondary Panorama IP/FQDN) -
tpl-stack=(Template Stack name in Panorama) -
device-group=(Device Group name in Panorama) -
vm-auth-key=(VM Authentication Key generated from Panorama - preferred method) -
OR
authkey=(Panorama Auth Key - less common now) -
cgname=(Collector Group name, if applicable)
-
-
Licensing:
-
authcodes=<comma-separated-auth-codes>(Alternative to placing codes in `/license/authcodes` file)
-
-
Operational Settings:
-
op-command-modes=(e.g.,mgmt-interface-swap- rarely used now, `normal` is default) -
vm-mode=(Relevant for specific platforms/plugins, e.g., `vmware`, `aws`) -
op-cmd-dpdk-pkt-io=(DPDK mode enable/disable)
-
-
Plugin Commands:
-
plugin-op-commands=(Used to pass commands to plugins during bootstrap, e.g., AWS S3 bucket details for further config download: `plugin-op-commands=aws-vm-series-plugin:S3BootstrapBucket= bucket-name `)
-
Bootstrap Components:
bootstrap.xml
The
bootstrap.xml
file, also located in the
/config/
folder, is an
optional
file containing a subset of the standard PAN-OS XML configuration.
Purpose and Usage:
- Provides a way to apply a more extensive baseline configuration than `init-cfg.txt` allows (e.g., configuring data interfaces, security zones, basic policy rules, log forwarding profiles).
- It is used as the initial `running-config.xml` only if the VM-Series fails to connect to Panorama during the bootstrap process (or if Panorama is not configured in `init-cfg.txt`).
- If the firewall successfully connects to Panorama and is assigned to a Template Stack and Device Group, the configuration pushed from Panorama overrides and replaces the contents of `bootstrap.xml`. The `bootstrap.xml` is effectively ignored in this scenario.
Creating `bootstrap.xml`:
- Typically created by configuring a firewall (physical or VM) with the desired baseline settings.
- Exporting the configuration (`Device > Setup > Operations > Export named configuration snapshot`).
- Editing the exported XML file to remove sections that are not needed or are dynamically assigned (like management IP if using DHCP, interface MAC addresses, etc.).
- Saving the relevant XML structure as `bootstrap.xml`.
Bootstrap Components: Content Folders
The bootstrap package structure includes several folders used to preload licenses, content updates, software images, and plugins.
/license
Folder
- Purpose: Holds license information needed to activate features on the VM-Series.
-
Contents:
-
authcodes(File): A simple text file containing one license authorization code per line. The firewall will attempt to contact the Palo Alto Networks license server to activate these codes during bootstrap. Requires internet connectivity. -
*.key(Files): Pre-generated license key files obtained from the Palo Alto Networks support portal for the specific VM-Series UUID (or generic keys for certain licenses). These can be applied directly without needing internet access to the license server during bootstrap (though updates might still require it later). - Note: Auth codes can also be provided directly within `init-cfg.txt` using the `authcodes=` parameter.
-
/content
Folder
- Purpose: Preloads dynamic content update files, allowing the firewall to have up-to-date threat intelligence and application signatures immediately after bootstrapping, without needing to download them separately.
-
Contents:
Standard PAN-OS content files, typically including:
-
Application and Threat definitions (e.g.,
panupv2-all-apps-*.tgz,panupv2-all-threats-*.tgz) -
Antivirus definitions (e.g.,
panupv2-all-antivirus-*.tgz) -
WildFire definitions (e.g.,
panupv2-all-wildfire-*.tgz)
-
Application and Threat definitions (e.g.,
/software
Folder
- Purpose: Allows the VM-Series to automatically upgrade (or downgrade) its PAN-OS version during the bootstrap process.
-
Contents:
The target PAN-OS software image file (e.g.,
PANOS_vm-10.1.5.ovaorPANOS_vm-10.1.5.qcow2, depending on the hypervisor/platform). - Note: The firewall will only perform the upgrade if the image version in this folder is different from the version it initially booted with.
/plugins
Folder
- Purpose: Installs specific software plugins required for integration with certain environments or features.
-
Contents:
Plugin software package files (`.tgz`), such as:
- VM-Series plugin (often required for cloud integration features)
- Panorama plugin
- Other specific plugins (e.g., for CN-Series, specific cloud integrations)
- Note: Plugin installation often requires specific commands or parameters in `init-cfg.txt` via the `plugin-op-commands` setting.
The Bootstrap Process: Step-by-Step
When a VM-Series firewall boots for the very first time and detects a bootstrap instruction (e.g., attached ISO, user-data script), it follows a specific sequence:
- Detect Bootstrap Source: The VM identifies the presence of bootstrap instructions/package (e.g., detects attached ISO/vmdk, reads user-data/customData/metadata).
- Process `init-cfg.txt`: If found in `/config`, the firewall parses and applies the parameters within `init-cfg.txt`. This sets the initial management IP, DNS, hostname, Panorama details, etc. This happens before the main configuration daemon starts.
- Panorama Connection Attempt: If Panorama server details are provided in `init-cfg.txt`, the firewall attempts to connect and register with Panorama using the specified VM Auth Key or auth key.
-
Configuration Load Decision:
- Panorama Connection Successful: The firewall signals Panorama it's ready for configuration. Panorama pushes the appropriate configuration based on the assigned Template Stack and Device Group. The local `/config/bootstrap.xml` file, if present, is ignored.
-
Panorama Connection Fails (or Not Configured):
The firewall looks for `/config/bootstrap.xml`.
- If `bootstrap.xml` exists, it is loaded as the initial running configuration.
- If `bootstrap.xml` does *not* exist, the firewall loads the factory default configuration.
- License Application: The firewall attempts to install license keys from the `/license` folder or activate licenses using auth codes provided in `/license/authcodes` or `init-cfg.txt` (requires connectivity to license server).
- Content Installation: Installs dynamic content update files found in the `/content` folder.
- Software Upgrade/Downgrade: If a PAN-OS image file is present in the `/software` folder and its version differs from the current image, the firewall attempts to install it and will reboot to complete the process.
- Plugin Installation: Installs plugin packages found in the `/plugins` folder, potentially using parameters from `init-cfg.txt`.
- Final Commit: The firewall performs a commit operation to save the applied configuration (either from Panorama or `bootstrap.xml`/factory default plus `init-cfg.txt` settings).
- Ready: The firewall completes the boot process and becomes operational with the bootstrapped configuration.
Bootstrap Methods: Delivering the Package
How the bootstrap package (the folder structure and files) is made available to the VM-Series instance depends on the deployment environment.
Hypervisor Environments (VMware ESXi, KVM, Hyper-V)
- ISO Image: Create an ISO file containing the standard bootstrap folder structure (`/config`, `/license`, etc.). Attach this ISO file as a CD/DVD drive to the VM *before* its first power-on. The VM-Series OS automatically detects and mounts the ISO to retrieve the bootstrap files.
- Virtual Disk (vmdk, qcow2, vhd/vhdx): Create a small virtual hard disk, format it (e.g., ext3, fat32), copy the bootstrap folder structure onto it, and attach it as a secondary disk to the VM before first power-on. Similar detection logic applies.
Public Cloud Environments (AWS, Azure, GCP)
Cloud environments typically use metadata services and scripting capabilities:
-
User Data (AWS) / Custom Data (Azure) / Startup Script (GCP):
- Provide configuration parameters directly within the user-data/customData field during instance launch. This often includes the contents of `init-cfg.txt`.
-
More commonly, use a script (e.g., bash, powershell) within user-data/customData. This script typically:
- Retrieves the full bootstrap package (usually zipped) from cloud storage (AWS S3, Azure Blob Storage, Google Cloud Storage).
- Unzips the package into a temporary location on the firewall's filesystem (often `/var/tmp/` or similar).
-
Executes a PAN-OS command like
request bootstrap file stage path <path-to-unzipped-folder>to copy the files into the expected bootstrap locations. - Alternatively, the script might manually copy files into the standard mount point used for bootstrapping (e.g., `/mnt/bootstrap`).
- Cloud Storage (S3, Blob, GCS): Store the complete bootstrap package (usually as a `.zip` file) in a cloud storage bucket. Grant the VM-Series instance appropriate permissions (e.g., IAM Role in AWS, Managed Identity in Azure) to access the bucket. The user-data script handles downloading and extracting the package.
- External Web Server: Store the bootstrap package on an accessible HTTP/HTTPS server. The user-data script uses tools like `curl` or `wget` to download it.
Bootstrap Integration with Panorama
A primary goal of bootstrapping VM-Series firewalls, especially in large or automated deployments, is to have them automatically register with Panorama for centralized management and configuration.
Key Steps & Parameters:
-
Panorama Configuration:
- Ensure Panorama is reachable from the network where the VM-Series management interface will reside after bootstrapping.
- Configure appropriate Template(s) and Template Stack(s) containing network settings, zones, base policies, etc.
- Configure appropriate Device Group(s) containing security policies, objects, etc.
- (Recommended) Generate a VM Authentication Key ( Panorama > Managed Devices > VM Auth Keys ). This key is used by the VM-Series to securely authenticate and register itself with Panorama during bootstrap.
-
`init-cfg.txt` Configuration:
-
Specify the Panorama server IP address or FQDN:
panorama-server=192.168.1.100 -
Specify the secondary Panorama server (if applicable):
panorama-server-2=192.168.1.101 -
Provide the VM Authentication Key:
vm-auth-key= GeneratedKeyString -
(Optional) Specify target Template Stack and Device Group:
tpl-stack=MyVMTemplateStack
device-group=MyVMDeviceGroup
(If not specified, Panorama might place it based on serial number pre-provisioning or defaults). - Ensure DNS settings (`dns-primary`, `dns-secondary`) are configured in `init-cfg.txt` if using an FQDN for `panorama-server`.
-
Specify the Panorama server IP address or FQDN:
-
Bootstrap Process:
- The VM-Series uses the `init-cfg.txt` parameters to connect to Panorama.
- It authenticates using the VM Auth Key.
- Panorama recognizes the key, registers the device (associating its serial number), and potentially assigns it to the specified (or default) Device Group and Template Stack.
- Panorama pushes the relevant configuration bundle down to the VM-Series.
- The firewall commits the Panorama configuration.
Bootstrapping and Licensing
Bootstrapping can also automate the initial licensing of the VM-Series firewall.
Methods:
-
Authorization Codes (Requires Internet Access):
-
Place license authorization codes (obtained from the Palo Alto Networks support portal after purchasing licenses) into a file named
authcodeswithin the/licensefolder of the bootstrap package (one code per line). -
Alternatively, provide the codes directly in
init-cfg.txtusing the comma-separated `authcodes=` parameter. - During bootstrap, the firewall uses its configured DNS and gateway settings (from `init-cfg.txt`) to connect to the Palo Alto Networks license activation server over the internet.
- It submits the auth codes to retrieve and install the corresponding license key files.
This method requires the firewall to have internet connectivity (via its management interface) *during* the bootstrap process to reach the license activation servers. Ensure DNS resolution and routing work correctly based on `init-cfg.txt`. -
Place license authorization codes (obtained from the Palo Alto Networks support portal after purchasing licenses) into a file named
-
License Key Files (Offline/Direct):
- Manually activate the licenses on the Palo Alto Networks support portal using the VM-Series UUID (obtained after initial launch or via specific commands).
- Download the generated license key files (`*.key`).
-
Place these `.key` files directly into the
/licensefolder of the bootstrap package. - During bootstrap, the firewall directly installs these keys without needing to contact the external license server.
-
Panorama-Managed Licenses (VM-Series Subscriptions / ELA):
- For capacity licenses or Enterprise License Agreements (ELA) managed through Panorama or the Customer Support Portal (CSP), bootstrapping often focuses on just registering the device to Panorama.
- Panorama, once managing the device, can automatically allocate and push the appropriate subscription licenses to the VM-Series based on its inventory and license pools.
- This often simplifies the bootstrap package as explicit auth codes or key files might not be needed within it, relying instead on the Panorama connection established via `init-cfg.txt`.
Troubleshooting Bootstrapping Issues
When bootstrapping doesn't work as expected, systematic troubleshooting is required.
Common Issues & Checks:
-
Bootstrap Package Not Found/Readable:
- ISO/vDisk: Verify the virtual CD/DVD drive or secondary disk containing the bootstrap files is correctly attached to the VM *before* the first power-on. Check VM settings in the hypervisor.
- Cloud Storage: Verify the storage bucket/container name and region are correct. Check that the VM instance has the necessary IAM/Managed Identity permissions to read from the bucket. Ensure the user-data script correctly downloads and extracts the package. Check script logs if possible (e.g., cloud-init logs).
- Web Server: Verify network reachability from the VM's initial management IP to the web server. Check web server logs.
- Incorrect Folder Structure/Filenames: Ensure the exact folder names (`config`, `license`, `content`, `software`, `plugins`) and key filenames (`init-cfg.txt`, `bootstrap.xml`, `authcodes`) are used, respecting case sensitivity where applicable (especially in scripts).
- Syntax Errors in `init-cfg.txt`: Even minor typos (e.g., misspelled parameter names, missing equals signs, incorrect IP formats) can cause `init-cfg.txt` processing to fail. Double-check syntax carefully against documentation examples.
-
Network Connectivity Issues:
- Verify the management IP, netmask, gateway, and DNS settings provided in `init-cfg.txt` are correct and allow the firewall to reach necessary resources (Panorama, license server, content update server, storage bucket).
- Check security groups, network ACLs, or routing in the virtual/cloud environment that might be blocking the firewall's initial outbound connections.
-
Panorama Registration Failure:
- Verify Panorama IP/FQDN and VM Auth Key/Auth Key in `init-cfg.txt` are correct.
- Ensure Panorama is reachable from the firewall's management IP.
- Check Panorama system logs for registration attempts or errors.
- Ensure the VM Auth Key hasn't expired or already been used (they are typically single-use).
-
Licensing Failure:
- If using auth codes, verify codes are correct and firewall has internet connectivity + DNS resolution.
- If using key files, ensure they are for the correct UUID (if applicable) and are not corrupted.
- Content/Software/Plugin Issues: Verify files are correctly placed in respective folders and are not corrupted. Ensure firewall has connectivity if downloading content directly.
Key Log Files (via Console or SSH after basic connectivity):
Check logs within
/var/log/pan/
:
-
bootstrap.log: Records the overall bootstrap process, including detection of media, file copying, and stage completion. (Primary log for bootstrap process itself) -
devsrvr.log: Logs management server processes, including processing of `init-cfg.txt` and initial configuration loading. Errors applying `init-cfg.txt` often appear here. -
ms.log: Management server core logs, can show details about commits, Panorama connection attempts, licensing interactions. -
cloud_init*.log(Cloud environments): Check logs related to the cloud-init or equivalent process that runs user-data/customData scripts.
Diagrams: Bootstrapping Concepts
Flowchart: VM-Series Bootstrap Process Logic
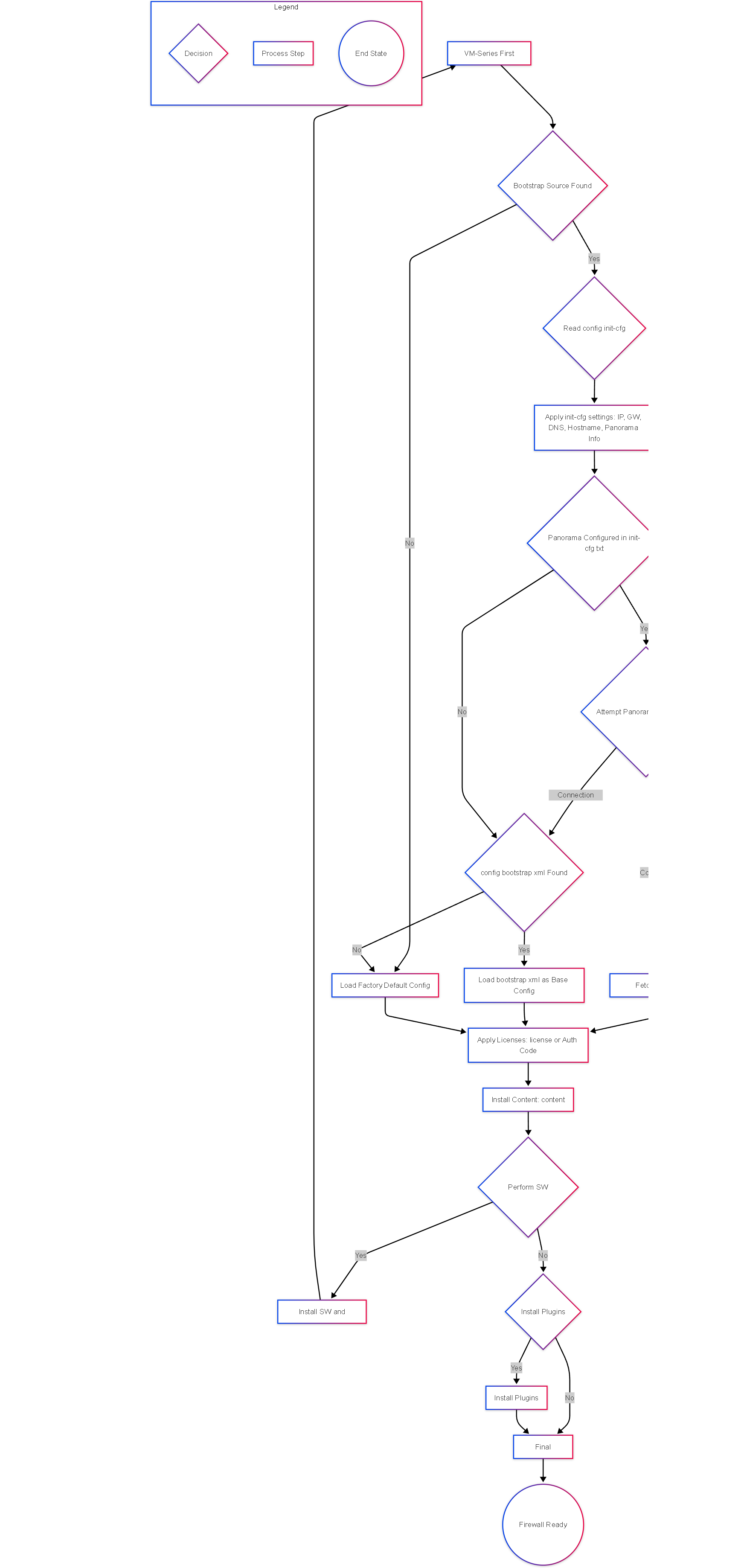
Flowchart illustrating the decision logic and sequence of the VM-Series bootstrap process.
Sequence Diagram: Bootstrap with Panorama
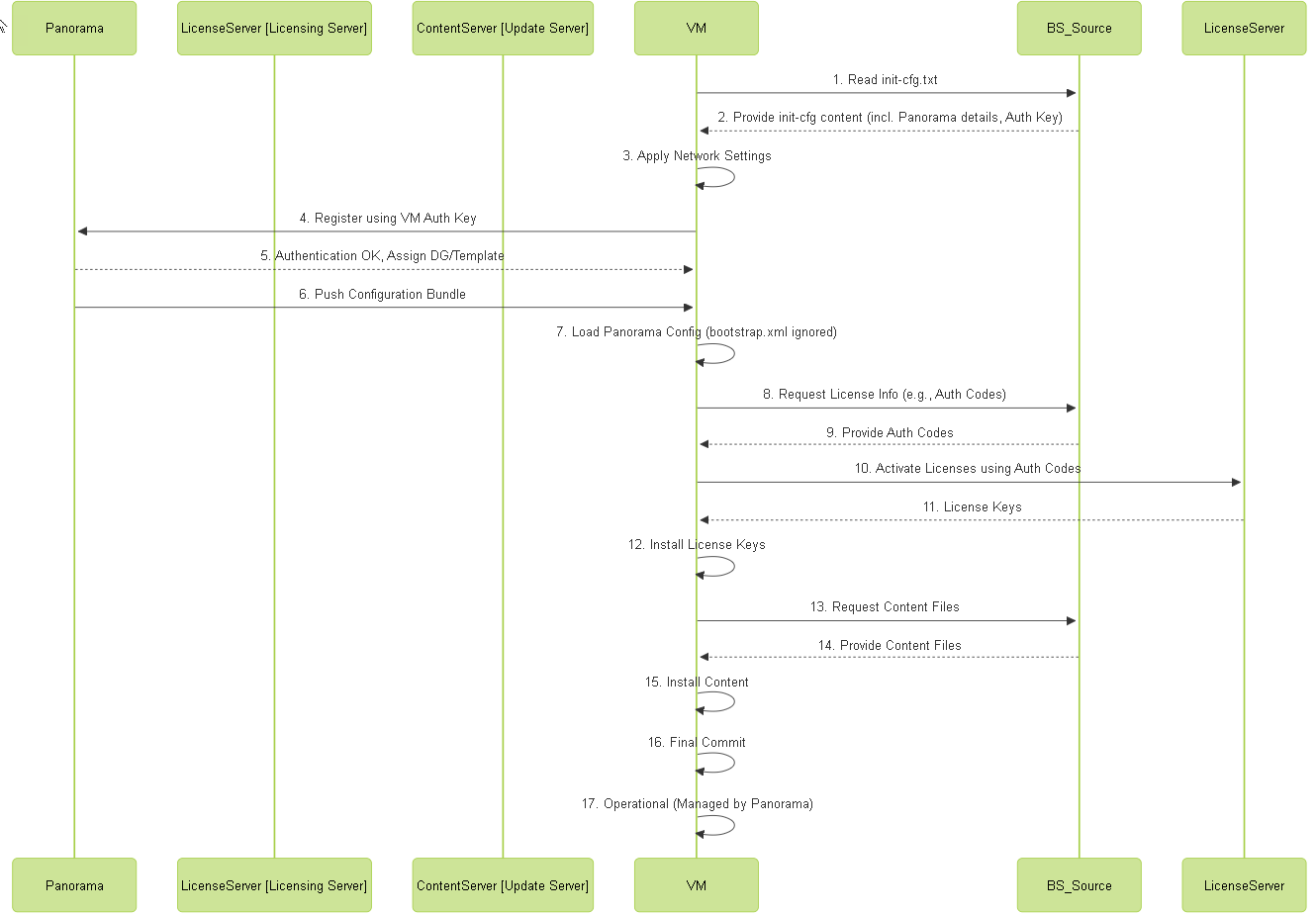
Sequence diagram showing a typical bootstrap process involving successful Panorama registration.
Graph: Bootstrap Ecosystem Components
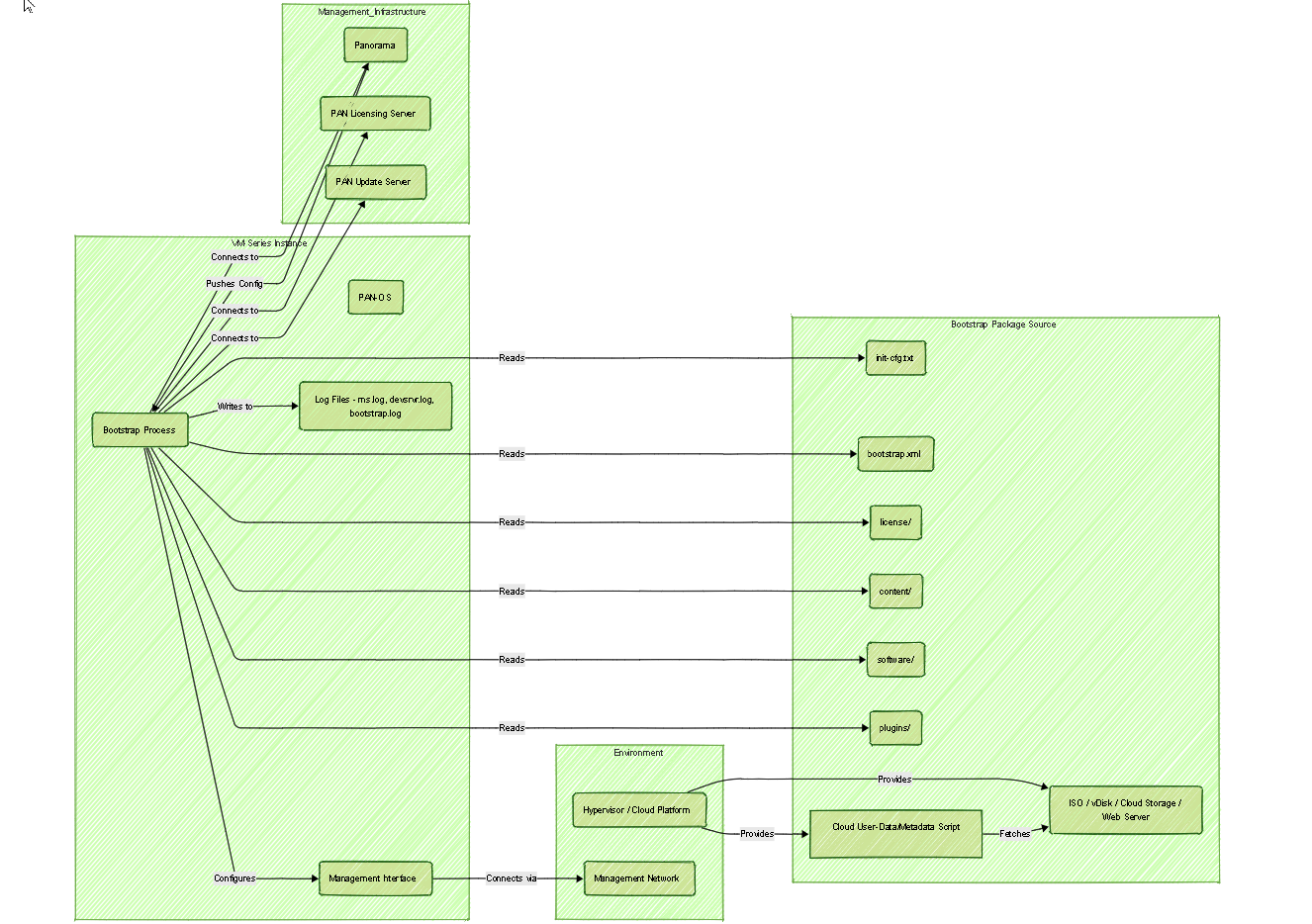
Graph showing the key components and interactions involved in the VM-Series bootstrapping ecosystem.
State Diagram: VM-Series Bootstrap States
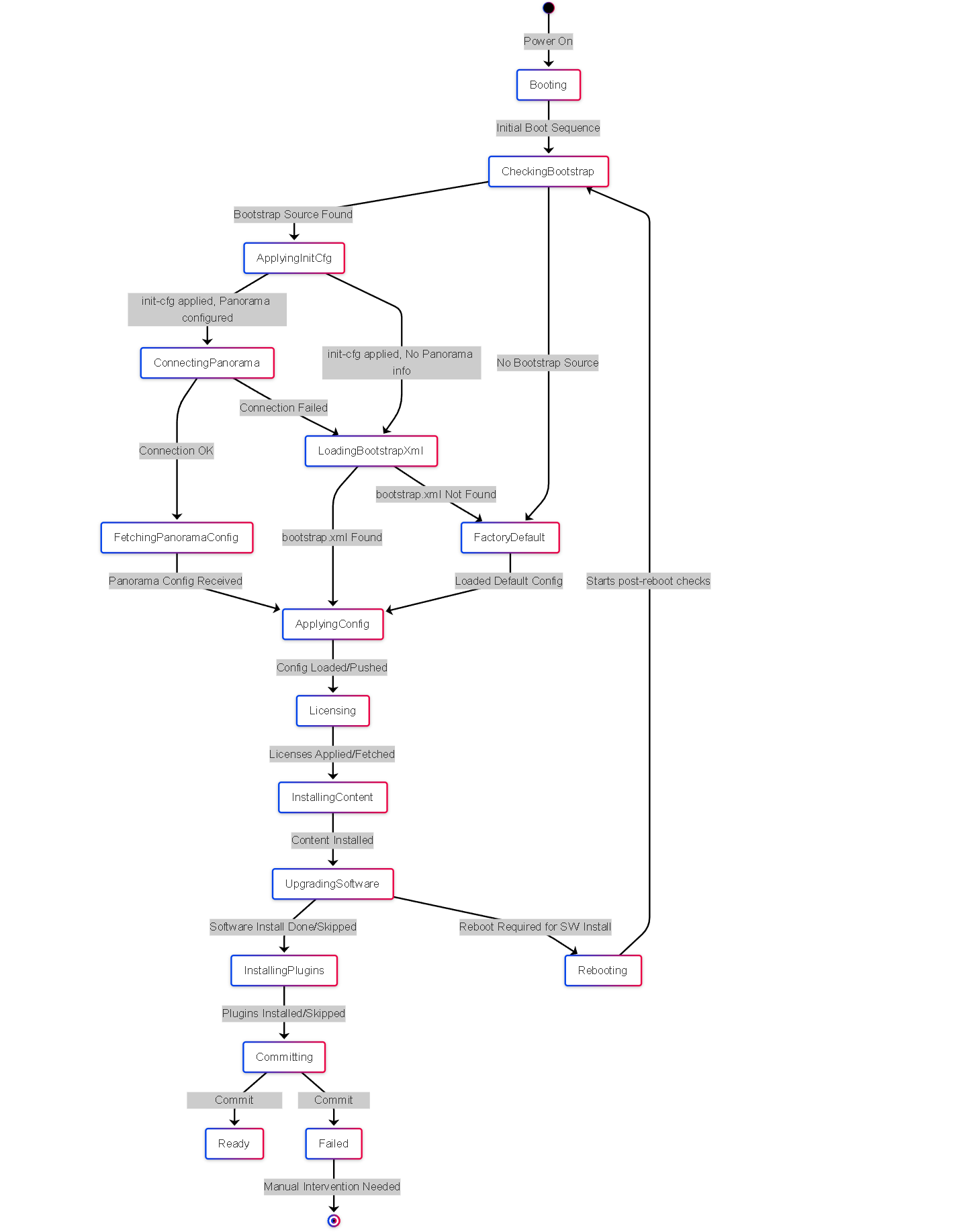
State diagram showing the possible states and transitions of a VM-Series firewall during the bootstrapping process.
PCNSE Exam Focus Points
Key VM-Series Bootstrapping concepts for the PCNSE exam:
- Purpose: Understand bootstrapping automates initial configuration for scalability and consistency, especially in virtual/cloud environments.
- Bootstrap Package: Know the standard folder structure (`/config`, `/license`, `/content`, `/software`, `/plugins`) and the purpose of each folder.
-
Key Files:
- `init-cfg.txt` : Mandatory for automation. Contains day-zero network, hostname, Panorama, license settings. Applied *before* main config load.
- `bootstrap.xml` : Optional. Contains PAN-OS XML config snippets. Used *only if* Panorama connection fails or isn't configured. Overridden by Panorama push.
- Process Order: Know the sequence: `init-cfg.txt` -> Panorama Attempt -> Panorama Config OR `bootstrap.xml` OR Factory Default -> License -> Content -> Software -> Plugins -> Commit.
- Delivery Methods: Be familiar with methods for different platforms: ISO/vDisk (Hypervisor), User-Data/CustomData + Cloud Storage (AWS, Azure, GCP).
- Panorama Integration: Understand how `init-cfg.txt` facilitates registration using Panorama IP/FQDN and VM Auth Key/Auth Key. Know that Panorama config takes precedence over `bootstrap.xml`.
- Licensing during Bootstrap: Know the methods: auth codes (in `/license/authcodes` or `init-cfg.txt`, requires internet) vs. license key files (in `/license`, offline capable). Panorama-managed licensing is also common.
- Troubleshooting: Recognize common failure points (package access, syntax errors, network connectivity, Panorama registration). Know key log files: `bootstrap.log`, `devsrvr.log`, `ms.log`.
- Use Cases: Auto Scaling Groups, rapid deployment, consistent baseline configurations.
VM-Series Bootstrapping Knowledge Check (PCNSE Style)
Test your understanding of VM-Series bootstrapping.