Understanding Certificate Chains in Palo Alto Networks Firewalls
Overview
In public key infrastructure (PKI), trust is not inherent; it must be established. Certificate chains are the mechanism used in SSL/TLS and other protocols to establish trust in an end-entity's certificate (like a web server's SSL certificate or a user's client certificate). Palo Alto Networks firewalls rely heavily on certificate chain validation for features like SSL Decryption, GlobalProtect, IPSec VPNs using certificates, administrative access, and more.
Understanding how the firewall builds and validates these chains is crucial for configuring these features correctly and troubleshooting related issues.
Chain Concepts: What is a Certificate Chain?
A certificate chain (also known as a chain of trust or certification path) is an ordered sequence of digital certificates:
- End-Entity Certificate (Leaf Certificate): This is the certificate being presented for validation (e.g., the web server's certificate, a user's client certificate). It identifies the subject (server FQDN, username). It is signed by an Intermediate CA or sometimes directly by a Root CA.
- Intermediate CA Certificate(s): One or more certificates that act as links between the end-entity certificate and the Root CA. Each Intermediate CA certificate is signed by the *next* certificate higher up in the chain (either another Intermediate CA or the Root CA). They delegate signing authority from the Root CA.
- Root CA Certificate: The top-level certificate in the chain. It is self-signed (meaning it signs itself) and acts as the ultimate trust anchor. The Root CA certificate must be explicitly trusted by the validating entity (in this case, the Palo Alto Networks firewall).
The validation process works by verifying the signature of each certificate in the chain using the public key contained in the *next* certificate up the chain, until the trusted Root CA is reached.
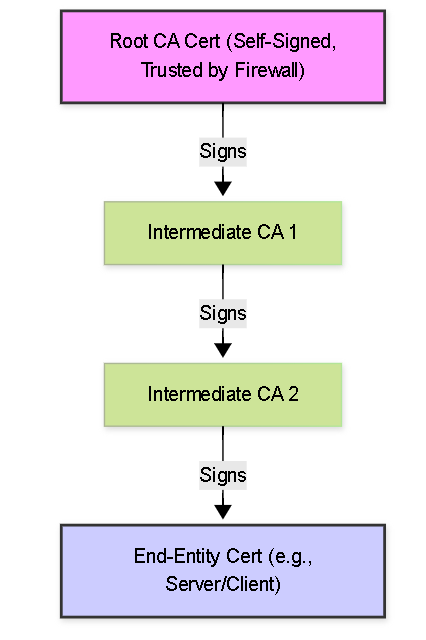 Visual representation of a typical certificate chain structure.
Visual representation of a typical certificate chain structure.
Chain Concepts: How Certificate Chains Work (Validation Process)
When a Palo Alto Networks firewall receives a certificate during a TLS handshake or for authentication (e.g., from a GlobalProtect client), it performs several validation steps to establish trust:
- Chain Building: The firewall receives the end-entity certificate and typically receives the intermediate certificates from the presenting entity (e.g., the web server usually sends its cert plus intermediates). The firewall attempts to build a complete path from the end-entity certificate up to a Root CA certificate that exists in its own trusted CA certificate store.
- Signature Verification: For each certificate in the constructed chain (starting from the end-entity cert), the firewall verifies its digital signature using the public key contained in the *issuer's* certificate (the next one up the chain). This process repeats until the Root CA is reached. The Root CA's signature is verified using its own public key (as it's self-signed).
- Trust Anchor Check: The Root CA certificate at the top of the validated chain must be present in the firewall's list of trusted Root CAs (either the default list or manually imported trusted CAs).
- Validity Period Check: The firewall checks the "Not Before" and "Not After" dates for *every* certificate in the chain (end-entity, intermediates, root) to ensure none have expired or are not yet valid.
- Revocation Check: If configured in the applicable Certificate Profile, the firewall checks if any certificate in the chain (usually the end-entity and potentially intermediates) has been revoked using CRL or OCSP.
- Other Checks: Additional checks like Key Usage, Basic Constraints (verifying CAs are marked as CAs), and Name Constraints might also be performed.
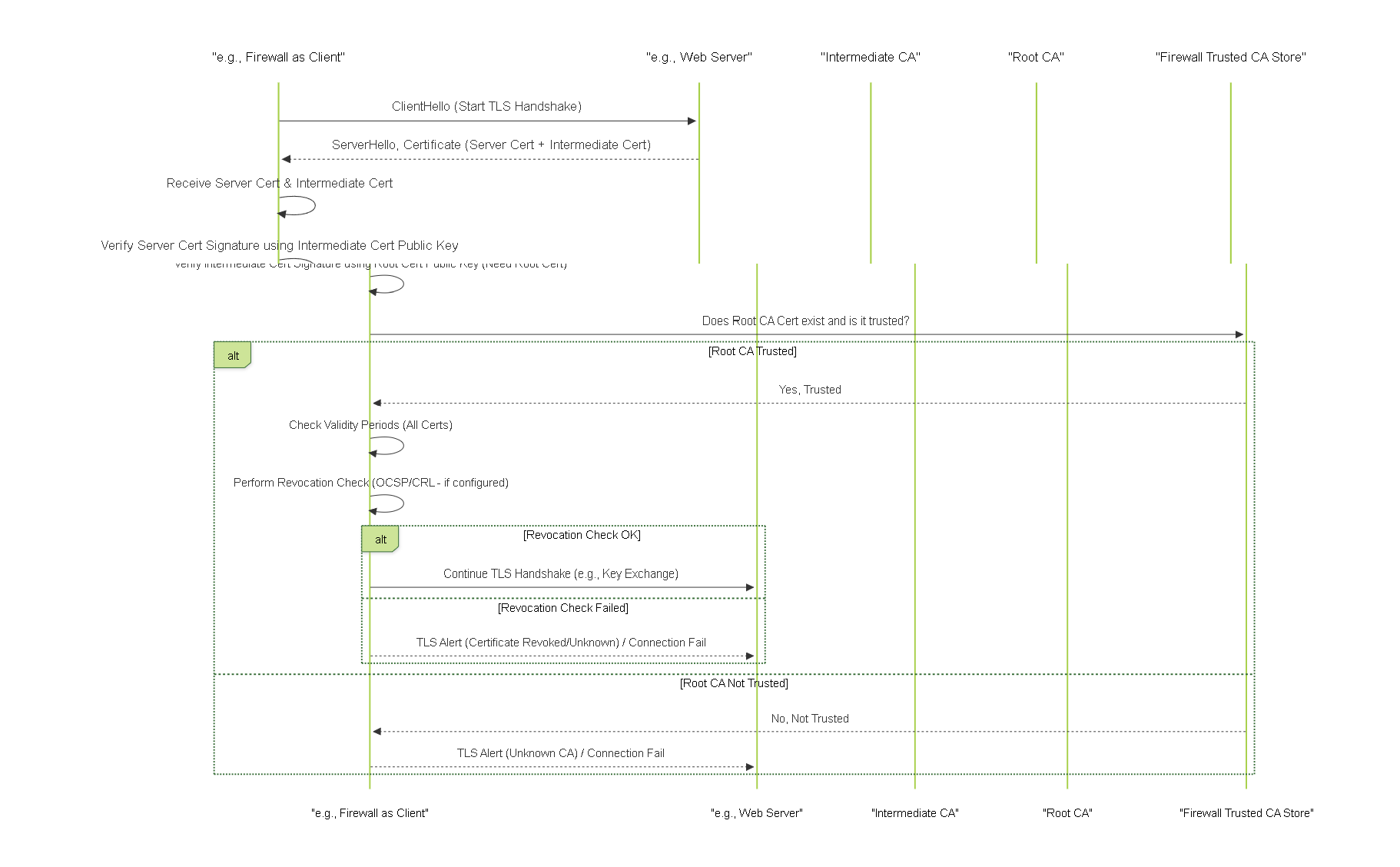
Simplified sequence of TLS handshake focusing on certificate chain validation by the client (firewall).
Trust Management: Default Trusted Certificate Authorities
Palo Alto Networks firewalls ship with a pre-installed list of commonly trusted public Root CA certificates. This list forms the default trust basis for validating certificates presented by external entities, such as public web servers during SSL/TLS decryption (Forward Proxy) or external VPN peers.
Managing Default Trusted CAs:
- Location: Device > Certificate Management > Certificates > Default Trusted Certificate Authorities .
-
Actions:
- View: Browse the list of included Root CAs.
- Enable/Disable: While generally not recommended unless you have a specific reason, you can technically disable trust for a specific default CA.
- Export: Export a default CA certificate if needed elsewhere.
- Updates: This default trust list is updated periodically via PAN-OS content updates. Keeping content current helps maintain trust in newly established public CAs and potentially removes distrusted ones.
Trust Management: Adding a Certificate That Is Not Trusted
If the firewall encounters a certificate issued by a CA that is *not* in its default trusted list (e.g., an internal enterprise CA, a less common public CA, or a self-signed certificate), validation will fail unless trust is manually established.
Process for Adding Trust:
- Obtain the CA Certificate(s): You need the certificate file(s) for the Root CA and any Intermediate CAs in the chain that issued the end-entity certificate. These are usually obtained from the CA administrator or downloaded from the CA's website. Common formats are PEM (.crt, .cer, .pem) or DER (.der, .cer).
-
Import into Firewall Certificate Store:
- Navigate to Device > Certificate Management > Certificates .
- Click Import .
- Provide a unique Certificate Name .
- Browse to and select the CA certificate file.
- Select the correct File Format (PEM or DER).
- Crucially, check the box labeled "Certificate Authority (CA)". This marks the imported certificate as a potential CA.
- Click OK .
- Repeat the import process for all required Intermediate CAs and the Root CA in the chain.
Forgetting to check the "Certificate Authority (CA)" box during import is a common mistake. If unchecked, the firewall will treat it as an end-entity certificate and won't be able to use it to validate other certificates. -
Add CA to Certificate Profile (or rely on global trust):
- For specific use cases (Recommended): Edit the relevant Certificate Profile ( Device > Certificate Management > Certificate Profile ) used by the feature (e.g., GlobalProtect, IPSec) and add the newly imported Root CA (and potentially intermediates if needed for specific checks) to the profile's 'CA Certificates' list. This limits trust for that specific CA to only the features using that profile.
- For global trust (Use with caution): While possible to mark an imported CA as globally trusted (similar to the default list), it's generally better practice to manage trust granularly via Certificate Profiles unless the CA needs to be trusted for nearly all functions (like an internal enterprise Root CA often is).
- Commit Changes.
Troubleshooting: Common Causes of Certificate Validation Failure
When certificate validation fails, connections are typically dropped or rejected. Understanding common causes helps in diagnosing the issue:
- Missing Intermediate Certificates: (Very Common) The server or client presenting its certificate fails to include the necessary Intermediate CA certificate(s) needed to link its certificate back to a Root CA trusted by the firewall. The firewall cannot complete the chain.
- Untrusted Root CA: The Root CA at the top of the presented chain is not present in the firewall's trusted CA list (either default or manually added).
- Expired Certificate: Any certificate in the chain (end-entity, intermediate, or root) has passed its "Not After" validity date. Firewall system time must be accurate (use NTP).
- Certificate Not Yet Valid: Any certificate in the chain has a "Not Before" date that is in the future relative to the firewall's system time.
- Revoked Certificate: A certificate in the chain has been revoked by its issuing CA, and the firewall successfully confirmed this via OCSP or CRL check (requires revocation checking to be enabled in the Certificate Profile).
- Revocation Check Unavailable / Unknown Status: The firewall cannot reach the CRL DP or OCSP Responder, or the check times out, AND the Certificate Profile is configured to block sessions when status is unknown.
- Incorrect Certificate Order: While less common with modern systems, sometimes certificates in the chain are presented in the wrong order, confusing the validation process.
- Signature Verification Failure: The digital signature of a certificate in the chain does not validate correctly using the public key of its stated issuer, indicating potential tampering or corruption.
- Name Mismatch: For server certificates (e.g., in SSL Decryption), the hostname the client is trying to reach does not match the Common Name (CN) or any Subject Alternative Name (SAN) listed in the server's certificate.
Troubleshooting: Tips and Techniques
When facing certificate validation errors:
-
Check Firewall Logs:
- System Log: Look for PKI-related errors, especially around certificate expiration or loading issues.
- Decryption Log (for SSL Decryption): Provides specific error messages related to certificate validation failures during decryption (e.g., "Untrusted issuer", "Unable to get local issuer certificate", "Certificate has expired", "Certificate revoked").
- GlobalProtect Logs (System Log / GP Logs): Check for certificate-related errors during client connection attempts.
- IPSec System Logs: Look for errors related to peer certificate validation in Site-to-Site VPNs.
- PKI Debug Log (CLI): Use `debug pki validation enable yes level 9` and `tail follow yes mp-log pki.log` for highly detailed, real-time validation steps and errors. (Use cautiously, very verbose).
-
Verify the Chain Externally:
- Use online SSL checker tools (for public web servers) to view the chain presented by the server and check for completeness and trust issues against public CAs.
-
Use OpenSSL commands from a separate machine to connect and view the presented chain:
openssl s_client -connect <server_ip_or_fqdn>:<port> -showcerts
- Check Server/Client Configuration: Ensure the server or client system is configured to send the complete certificate chain , including all necessary intermediate certificates. This is a common server-side misconfiguration.
-
Verify Firewall Trust Store:
- Confirm the Root CA certificate for the chain exists under Device > Certificate Management > Certificates .
- Ensure the Root CA is marked as a "Certificate Authority (CA)".
- Verify the Root CA is included in the correct Certificate Profile's 'CA Certificates' list if not relying on default trust.
- Import any necessary Intermediate CA certificates and ensure they are also marked as "Certificate Authority (CA)". While intermediates don't strictly *need* to be in the profile's CA list (trust flows from the root), importing them can sometimes help the firewall build the chain if the server fails to send them.
- Check Certificate Validity: Manually inspect the validity dates ("Not Before", "Not After") of all certificates in the chain (End-entity, Intermediates, Root). Ensure the firewall's system time is accurate ( Device > Setup > Services > NTP ).
-
Test Revocation Connectivity:
Use firewall CLI commands to test connectivity to CRL/OCSP URLs identified from the certificates:
test certificate-status crl url <url>test certificate-status ocsp url <url> certificate <name_of_cert_on_fw>Also use basic `ping` and `traceroute` (potentially specifying source interface/IP). Check firewall policies allow traffic to these destinations.
Diagrams: Certificate Chain Validation
Diagram: Certificate Chain Structure
 Visual representation of a typical certificate chain structure.
Visual representation of a typical certificate chain structure.
Diagram: TLS Handshake & Chain Validation Sequence
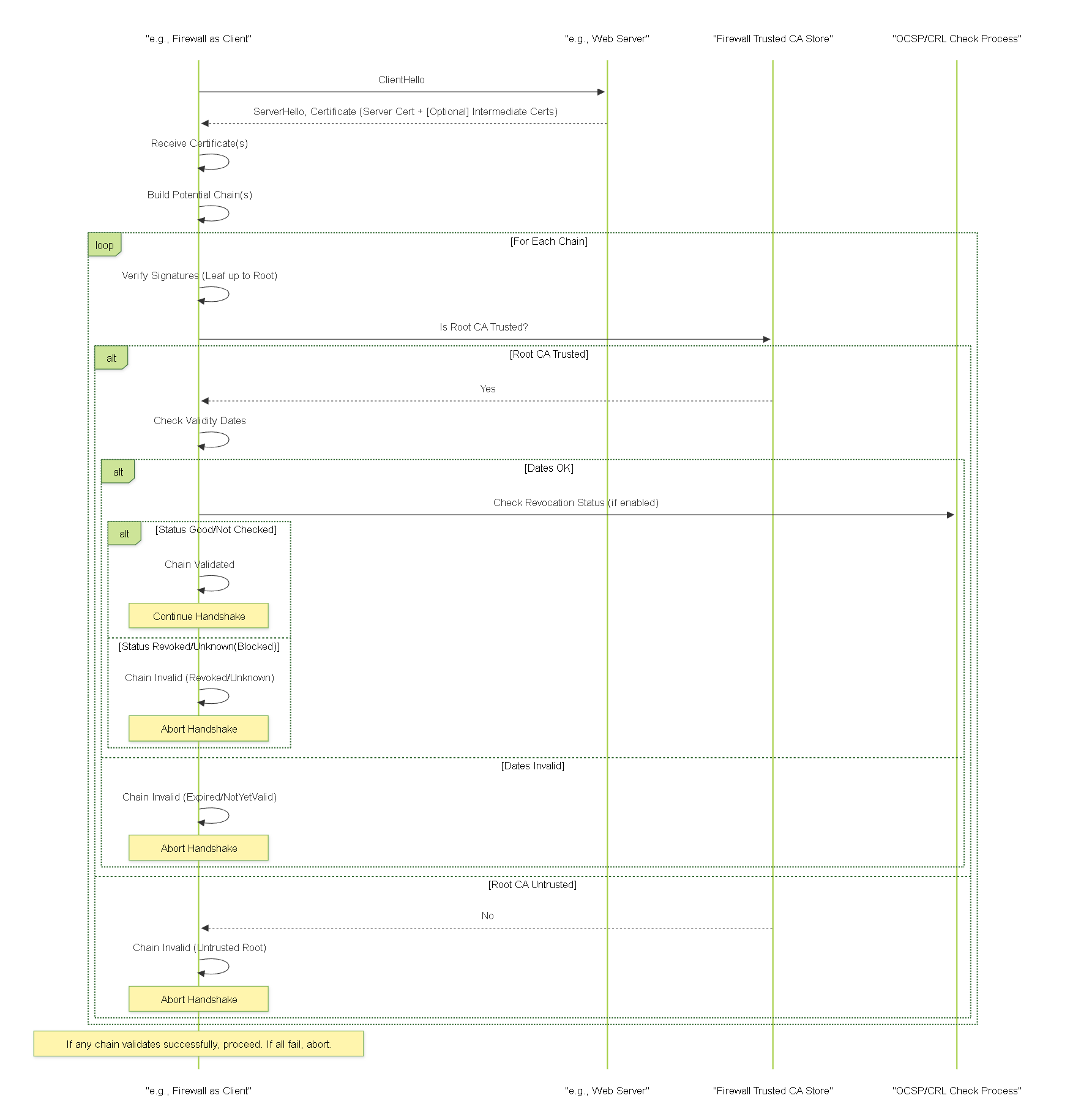
Sequence diagram showing TLS certificate exchange and the validation steps performed by the firewall.
Flowchart: Certificate Validation Decision
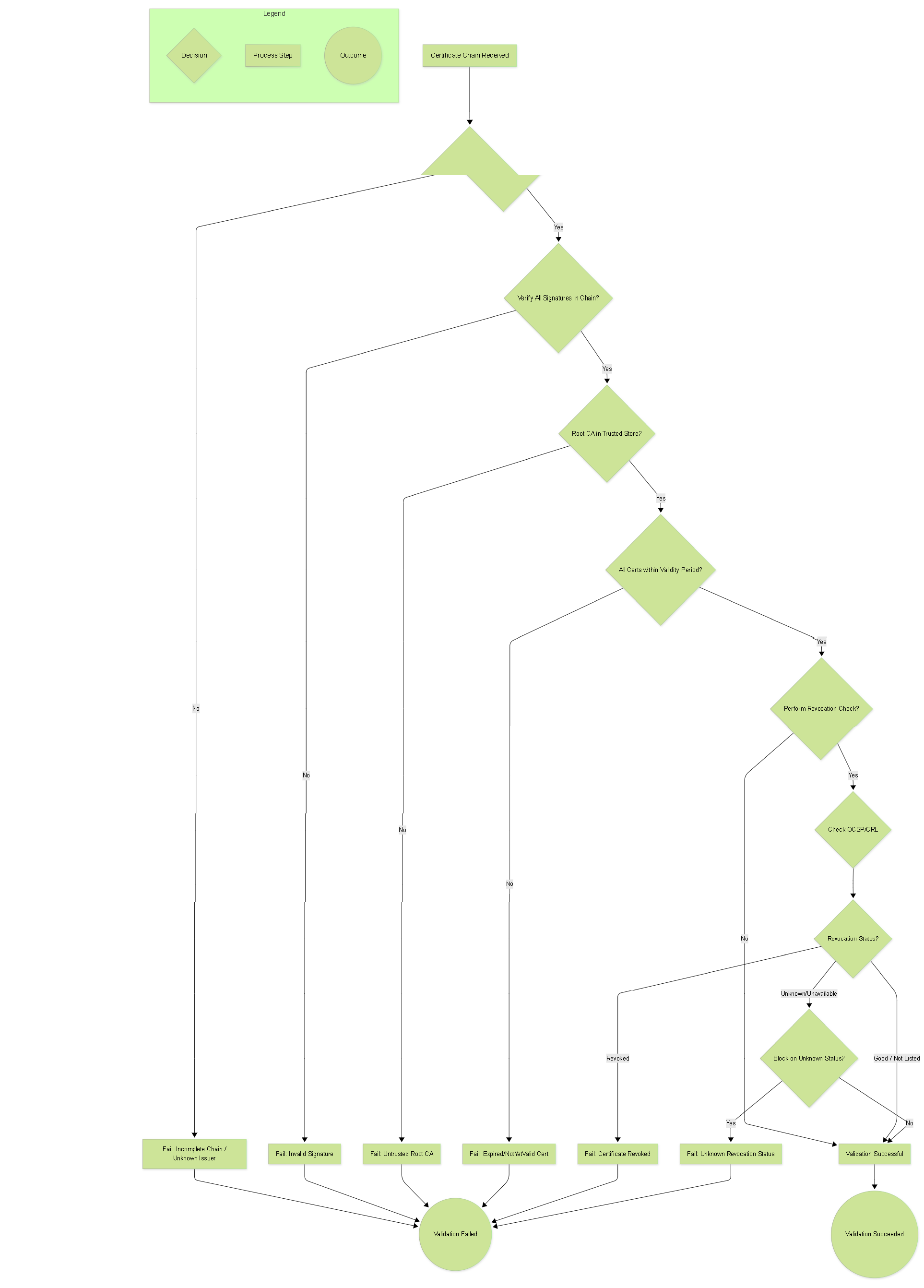
Decision flowchart for the firewall's certificate chain validation process.
State Diagram: Certificate Trust/Validity State
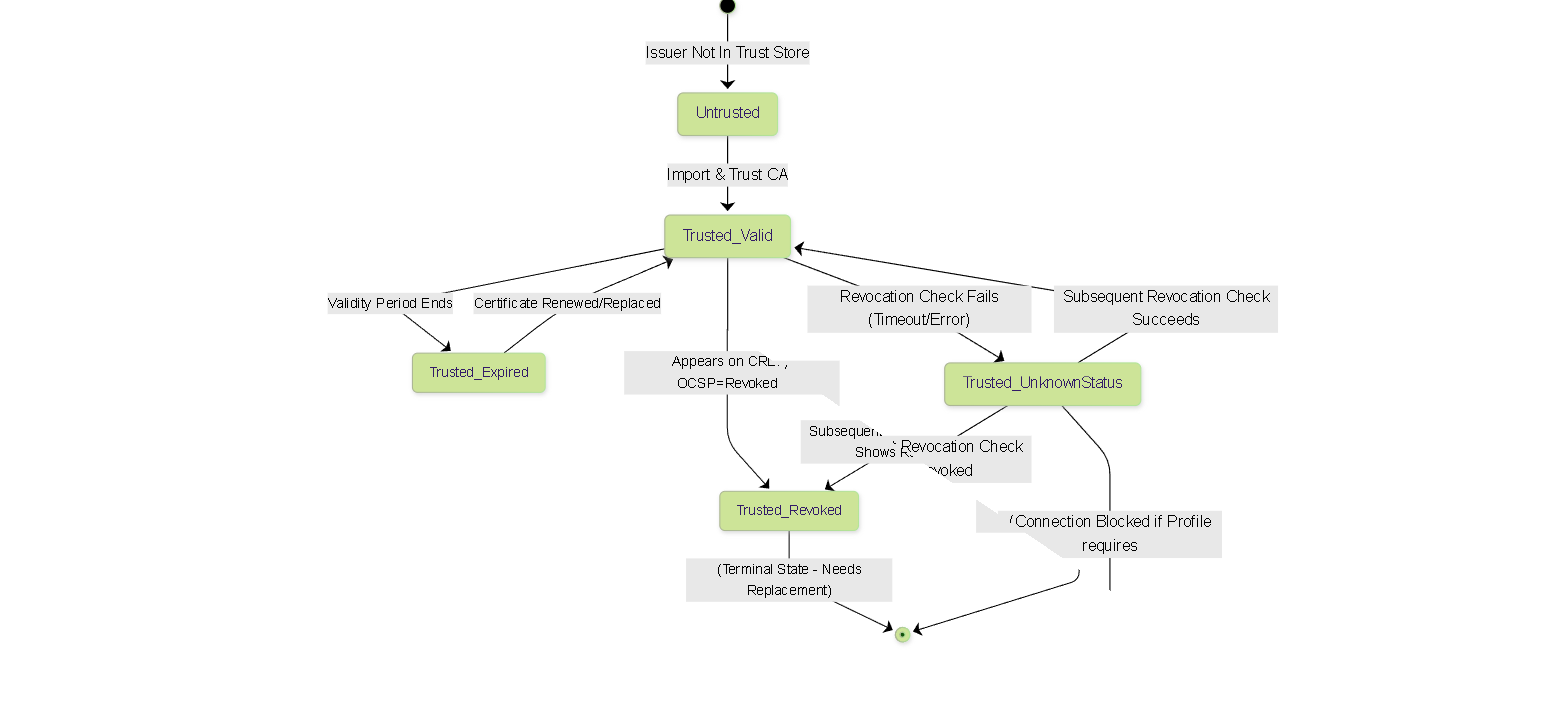
Simplified state diagram showing possible trust and validity states for a certificate from the firewall's perspective.
PCNSE Exam Focus Points
Key concepts related to Certificate Chains for the PCNSE exam:
- Chain Structure: Understand the hierarchy: End-Entity (Leaf) -> Intermediate CA(s) -> Root CA. Know that each signs the one below it.
- Trust Anchor: Recognize that the validation process must chain back to a Root CA certificate that is explicitly trusted by the firewall (either default or manually imported).
- Intermediate Certificates: Understand their role in linking the end-entity cert to the root. Know that the server/client presenting the certificate is typically responsible for sending the necessary intermediate certificates along with the end-entity certificate. A common failure is when intermediates are missing.
- Validation Steps: Be familiar with the sequence: Signature Checks -> Trust Anchor Check -> Validity Period Check -> Revocation Check (if enabled).
- Default Trusted CAs: Know where to find this list ( Device > Certificate Management > Certificates ) and that it contains common public Root CAs, updated via content updates, but generally not intermediates.
- Importing CAs: Understand the process of importing Root/Intermediate CAs and the critical importance of checking the "Certificate Authority (CA)" box during import.
- Certificate Profiles: Know that Certificate Profiles are where you reference the trusted CAs and configure revocation checking (CRL/OCSP) settings for specific features (like GlobalProtect, IPSec VPNs).
- Revocation Checking: Understand the basics of CRL (list) vs. OCSP (real-time query) and the firewall's check order (OCSP first, then CRL fallback). Know the importance of the "Block on Unknown" setting.
- Troubleshooting: Recognize common failure reasons (missing intermediates, untrusted root, expired certs, revocation failures). Know that decryption logs are useful for SSL/TLS issues, and general system/feature logs (GP, IPSec) may indicate certificate problems. Basic connectivity tests (ping, traceroute) to CDP/OCSP URLs are relevant.
Certificate Chains Knowledge Check (PCNSE Style)
Test your understanding of certificate chains and validation.