Configure Certificate Profiles
Overview
Certificate Profiles are fundamental components in Palo Alto Networks firewalls used to validate digital certificates presented by clients or devices during authentication or secure communication establishment. They define the parameters the firewall uses to determine if a presented certificate is trustworthy and valid.
Essentially, a Certificate Profile tells the firewall:
- Which Certificate Authorities (CAs) do you trust to sign certificates?
- How should you check if a certificate, even if signed by a trusted CA, has been revoked (cancelled before its expiry date)?
- What specific attributes within the certificate should be used to identify the user or device?
- How should you handle situations where revocation status cannot be determined?
Configuring Certificate Profiles correctly is crucial for securely implementing features that rely on certificate-based authentication.
Common Use Cases
Certificate Profiles are referenced in various features, including:
- Authentication Portal: Validating client certificates for portal access.
- Multi-Factor Authentication (MFA): Often used as one factor or for device posture checking in MFA flows.
- GlobalProtect VPN (Portals and Gateways): Authenticating users and/or devices connecting via GlobalProtect using client certificates.
- Site-to-Site IPSec VPN: Authenticating peer VPN gateways using certificates instead of pre-shared keys.
- SSL Decryption: Validating server certificates during SSL Forward Proxy decryption (though often uses built-in trust). Used more explicitly for client certificate validation in specific scenarios.
- External Dynamic List (EDL) Server Validation: Validating the certificate presented by an EDL server hosting a list over HTTPS.
- Dynamic DNS (DDNS) Secure Updates: Validating DDNS server certificates.
- User-ID Agent / Terminal Server (TS) Agent Communication: Securing communication between the firewall and User-ID agents using certificates.
- Management Access: Configuring certificate-based authentication for administrators accessing the firewall Web UI or CLI.
- Panorama Communication: Securing communication between firewalls and Panorama using certificates.
Configuration: CA Certificates
The foundation of a Certificate Profile is the list of Certificate Authority (CA) certificates that the firewall trusts. A client certificate presented to the firewall will only be considered potentially valid if it chains up to one of the CA certificates listed in the profile.
Obtaining/Managing CA Certificates ( Device > Certificate Management > Certificates )
-
Importing Existing CA Certificates:
- If your organization uses an internal Enterprise CA (e.g., Microsoft AD Certificate Services), export the Root CA certificate (and potentially any Intermediate CA certificates in the chain) in PEM or DER format.
- Import these CA certificates into the firewall's certificate store ( Device > Certificate Management > Certificates > Import ). Ensure you mark them as trusted CA certificates during import.
- You might also need to import public CA certificates if validating external client certificates signed by well-known public CAs, although the firewall has a built-in list of common public CAs.
-
Generating a Self-Signed Root CA:
- The firewall can act as a Root CA itself ( Device > Certificate Management > Certificates > Generate ).
- Select "Self-Signed Root CA".
- Configure parameters like Common Name, cryptographic settings, and validity period.
- This self-signed CA can then be used to issue certificates for other purposes (e.g., firewall management, VPNs), and clients/devices would need to trust this firewall-generated Root CA.
Using a self-signed CA requires distributing the CA certificate to all clients/devices that need to trust certificates issued by it. This is often less manageable than using an established enterprise or public CA.
Once CA certificates are present in the firewall's certificate store, they can be added to a Certificate Profile.
Configuration: Creating the Certificate Profile
Certificate Profiles are configured under Device > Certificate Management > Certificate Profile .
Steps:
- Click Add to create a new profile.
-
Name:
Provide a unique and descriptive name (e.g.,
GlobalProtect_Client_Cert_Check,Admin_UI_Cert_Auth). - Location (Panorama/Multi-VSYS): Select the appropriate VSYS or choose 'Shared' if applicable.
-
CA Certificates Section:
- Click Add in this section.
- Select the CA certificate(s) from the firewall's certificate store that you want this profile to trust. You can add multiple CAs to a single profile.
- Only client certificates signed by one of these selected CAs (or an intermediate CA that chains up to one of them) will pass the initial trust check.
- Configure Verification Settings (detailed next).
- Configure Username Field (detailed later).
- Click OK to save the profile.
Configuration: Certificate Verification Settings
Beyond trusting the CA, the Certificate Profile defines how the firewall checks if a presented certificate, although validly signed, has been revoked (cancelled) by the CA before its natural expiration date. This is crucial for security, as compromised certificates need to be invalidated.
Two primary mechanisms are used:
Certificate Revocation List (CRL)
- Concept: The CA periodically publishes a signed list (CRL) containing the serial numbers of all revoked certificates it has issued.
- Firewall Action: When Use CRL is enabled, the firewall needs to periodically download the CRL from a distribution point (usually an HTTP or LDAP URL specified in the client certificate or the CA certificate). It then checks the serial number of the presented certificate against this downloaded list.
- Configuration: Requires the firewall to have network connectivity to the CRL Distribution Point (CDP) URL. You configure the CRL Receive Timeout .
- Pros/Cons: Simpler protocol, but lists can become large, and there's latency between revocation and publication/download.
Online Certificate Status Protocol (OCSP)
- Concept: Provides a real-time method for checking revocation status.
- Firewall Action: When Use OCSP is enabled, the firewall contacts an OCSP Responder server (usually specified in the certificate's Authority Information Access - AIA extension) for the specific certificate being validated. The OCSP responder provides a signed response indicating the certificate's status (good, revoked, or unknown).
- Configuration: Requires the firewall to have network connectivity to the OCSP responder URL. You configure the OCSP Receive Timeout .
- Pros/Cons: Provides more up-to-date status, less download overhead than large CRLs, but relies on the availability and responsiveness of the OCSP responder. Requires more complex request/response handling.
Profile Settings for Verification:
- Use CRL: Enable checkbox to perform CRL checking.
- Use OCSP: Enable checkbox to perform OCSP checking.
- CRL Receive Timeout (seconds): Max time to wait for CRL download.
- OCSP Receive Timeout (seconds): Max time to wait for OCSP response.
- Certificate Status Timeout (seconds): How long the firewall caches a verified status (good or revoked) before re-checking.
- Block session if certificate status is unknown: (Security Enhancement) If checked, sessions are blocked if neither OCSP nor CRL provides a definitive 'good' or 'revoked' status (e.g., both checks fail or time out). If unchecked, an unknown status might be treated as 'good' (less secure).
- Block sessions if certificate status cannot be retrieved within timeout: (Security Enhancement) Explicitly block if the CRL/OCSP checks time out based on their respective timeout settings.
- Block sessions if the certificate was not issued to the authenticating device (GlobalProtect only): Specific check for GlobalProtect client certificates.
Configuration: Username Field and Domain
When using client certificates for user authentication (e.g., GlobalProtect, Admin UI, Authentication Portal), the Certificate Profile needs to know which field within the certificate contains the user's identity (username).
Username Field Options:
-
Subject - Common Name (CN):
Extracts the username from the Common Name (CN) field within the certificate's Subject distinguished name (DN).
-
Example Subject:
CN=johndoe, OU=Users, DC=corp, DC=com-> Username =johndoe
-
Example Subject:
-
Subject Alternative Name (SAN) - Email:
Extracts the username from the RFC822 Name (Email address) field within the certificate's Subject Alternative Name (SAN) extension.
-
Example SAN:
Email=john.doe@corp.com-> Username =john.doe@corp.com
-
Example SAN:
-
Subject Alternative Name (SAN) - Principal Name:
Extracts the username from the User Principal Name (UPN) field within the certificate's SAN extension. Common in Active Directory environments.
-
Example SAN:
UPN=johndoe@corp.com-> Username =johndoe@corp.com
-
Example SAN:
- None: Do not extract a username from the certificate. This is typically used when the certificate is used purely for device identification or pre-logon authentication, not primary user authentication.
Domain
- Purpose: Optionally specify a domain name (e.g., NetBIOS domain name like `CORP`) to associate with the username extracted from the certificate.
- Use Case: Helps User-ID map the certificate-derived username (which might lack a domain) to a fully qualified domain user (e.g., `CORP\johndoe`) for policy enforcement based on directory group membership.
- Configuration: Enter the domain name in the `Domain` field.
Best Practices for Certificate Profiles
- Enable Revocation Checking: Always enable both OCSP and CRL checking for robust validation, unless there's a specific, documented reason not to. Prioritize OCSP for timeliness but keep CRL as a fallback.
- Configure Blocking for Unknown Status: For higher security, enable "Block session if certificate status is unknown" and "Block sessions if certificate status cannot be retrieved within timeout" . This prevents potentially revoked certificates from being used if revocation checking fails. Be aware this can cause outages if CRL/OCSP responders are unavailable. Monitor closely after enabling.
- Tune Timeouts Carefully: Set CRL/OCSP Receive Timeouts appropriately based on network latency to responders. Too short may cause false failures; too long can delay user connections. Default (often 5 seconds) is usually reasonable, but monitor.
- Use Correct Username Field: Ensure the selected Username Field (CN, SAN-Email, SAN-Principal Name) accurately matches where the user identity is stored in your issued client certificates.
- Maintain CA Trust Store: Regularly review and update the CA certificates included in the profile and stored on the firewall. Remove expired or untrusted CAs.
- Use Descriptive Names: Name Certificate Profiles clearly based on their intended use case (e.g., `GP_User_Cert_Profile`, `Admin_UI_CAC_Profile`).
- Verify Network Connectivity: Ensure the firewall has network routes and policy rules allowing it to reach the necessary CRL Distribution Points (CDPs) and OCSP Responders (typically over HTTP/80). Use source NAT if necessary.
Diagrams: Certificate Profile Concepts
Sequence Diagram: Client Certificate Validation
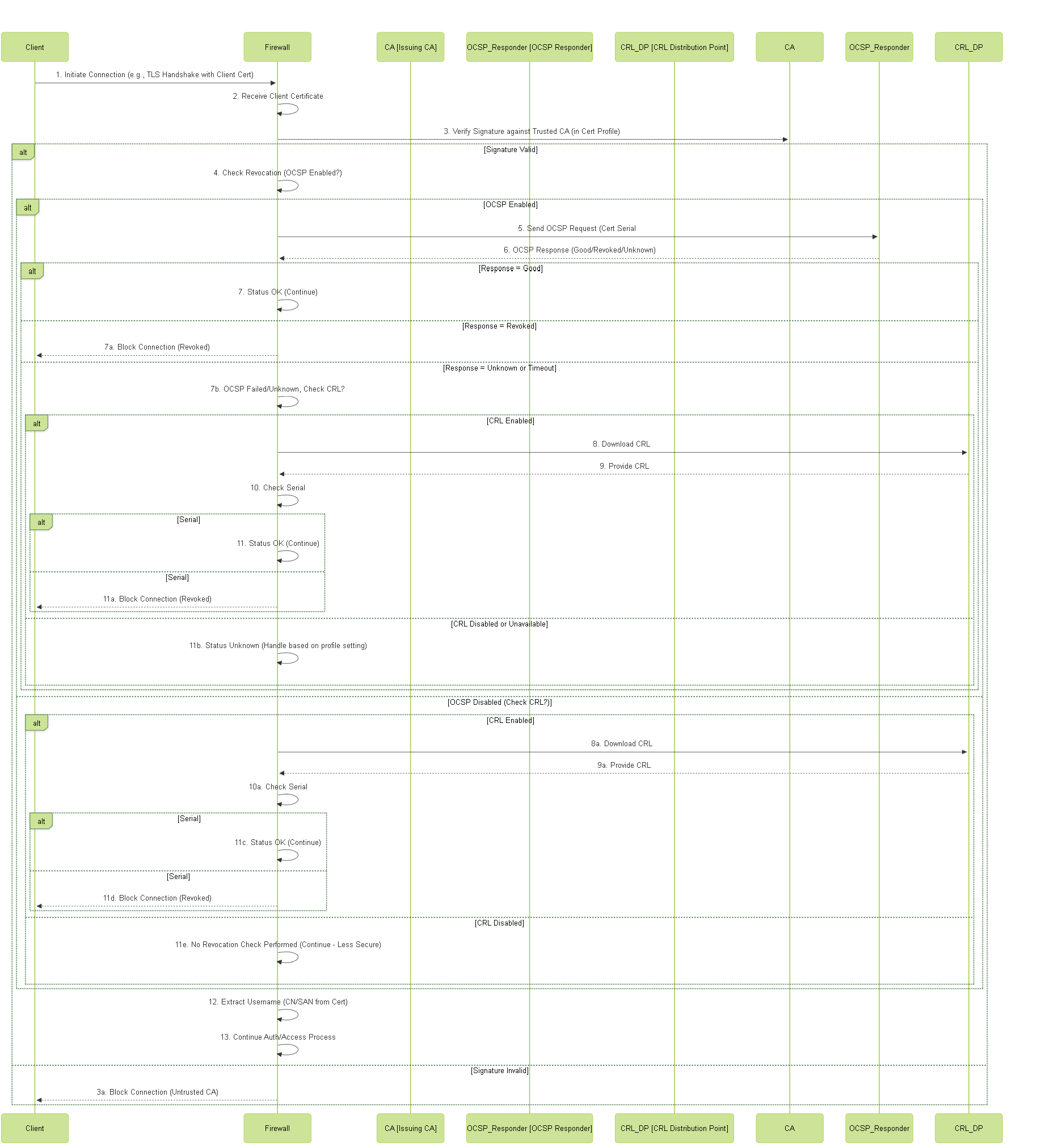
Sequence diagram illustrating the steps firewall takes to validate a client certificate using a Certificate Profile, including OCSP and CRL checks.
Flowchart: Certificate Profile Decision Logic
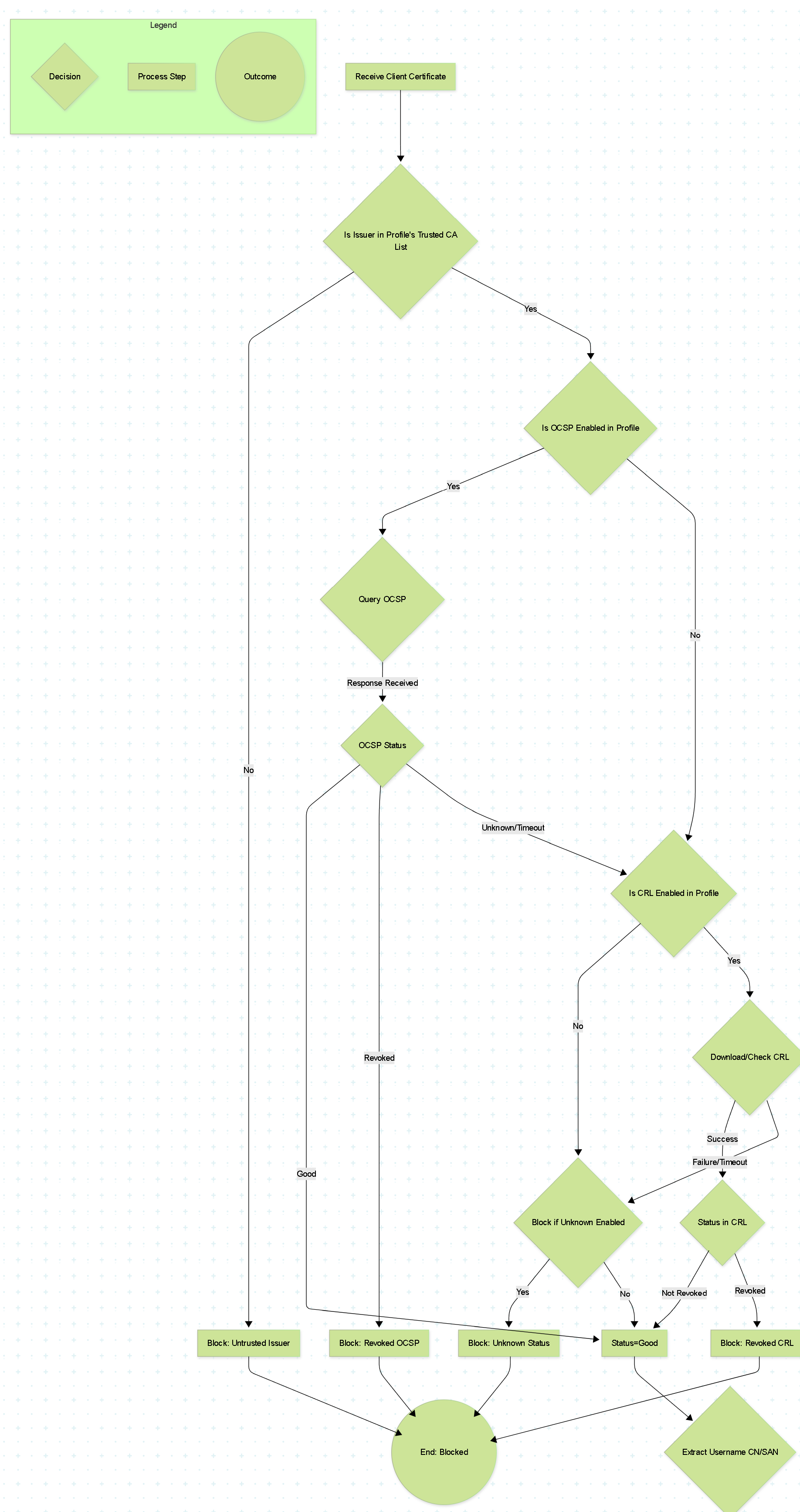
Flowchart showing the decision logic for certificate validation based on Certificate Profile settings.
Graph: Certificate Profile Ecosystem
Graph showing relationships between Certificate Profiles, CAs, revocation services, and firewall features that utilize them.
State Diagram: Certificate Validation Status
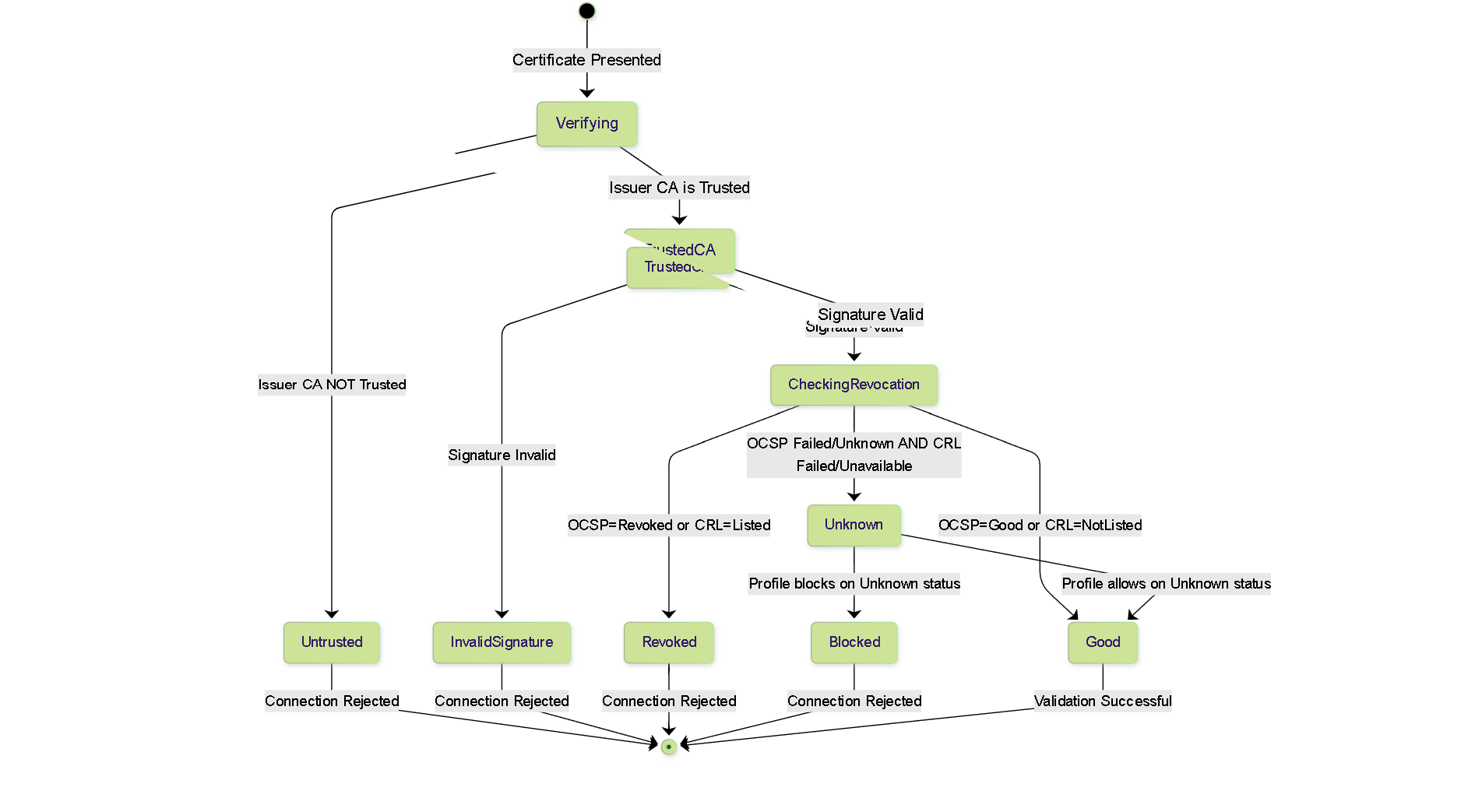
State diagram showing the possible outcomes of the certificate validation process based on trust and revocation checks.
Troubleshooting Certificate Profile Issues
Failures related to Certificate Profiles often manifest as failed authentications (GlobalProtect, Admin UI, etc.) or failed secure connections (IPSec, EDL).
Common Issues & Checks:
-
Untrusted Issuer:
- Symptom: Connection fails, logs might indicate "Certificate issuer is not trusted".
- Cause: The CA certificate that signed the client/server certificate (or an intermediate CA in the chain) is not included in the 'CA Certificates' list of the applied Certificate Profile, or is not marked as trusted in the firewall's certificate store.
- Fix: Import the necessary Root CA and Intermediate CA certificates, ensure they are marked as trusted, and add them to the Certificate Profile.
-
Revocation Check Failure (CRL/OCSP):
- Symptom: Connection fails, logs might indicate "Certificate revoked", "Unable to get certificate CRL", "Unable to get OCSP response", "Certificate status unknown".
- Cause (CRL): Firewall cannot reach the CDP URL (network connectivity, routing, policy block, DNS failure), CRL is expired, CRL signature is invalid, CRL download timed out.
- Cause (OCSP): Firewall cannot reach the OCSP Responder URL, OCSP responder is down or slow, OCSP response signature is invalid, OCSP response indicates 'revoked' or 'unknown', OCSP request timed out.
-
Fix:
- Verify network connectivity (ping, traceroute from firewall CLI to CDP/OCSP URLs). Use appropriate source interface if needed.
- Check Security Policy rules to ensure traffic (HTTP/80 typically) to CDP/OCSP URLs is allowed.
- Verify DNS resolution for CDP/OCSP hostnames.
- Check validity of the CRL/OCSP responder certificate itself.
- Adjust CRL/OCSP timeouts in the Certificate Profile if necessary due to latency, but investigate underlying cause first.
- Check the CA's infrastructure if CRL/OCSP is consistently unavailable.
- Temporarily disable "Block session if certificate status is unknown" for testing, but re-enable for security.
-
Troubleshooting Commands:
debug pki validation enable yes level 9(Use cautiously, generates lots of output)tail follow yes mp-log pki.logshow certificate <cert-name> crl-statusshow certificate <cert-name> ocsp-statustest certificate-status crl url <url>test certificate-status ocsp url <url> certificate <cert-name>
-
Username Extraction Failure:
- Symptom: Certificate validation might pass, but authentication fails, often with generic "Authentication failed" messages. User-ID mapping might fail.
- Cause: The "Username Field" setting in the Certificate Profile (CN, SAN-Email, SAN-Principal) does not match the field where the actual username is located within the presented client certificate.
- Fix: Inspect a sample client certificate to confirm where the username is stored (Subject CN, SAN Email, SAN UPN). Adjust the Certificate Profile's "Username Field" setting accordingly.
- Expired Certificates: Ensure the client certificate, intermediate CA certificates, and root CA certificates are all within their validity periods. Check system time/NTP on the firewall.
PCNSE Exam Focus Points
Key areas related to Certificate Profiles for the PCNSE exam:
- Purpose: Understand that Certificate Profiles define parameters for validating client/peer certificates, primarily focusing on issuer trust and revocation status checking .
- Configuration Location: Know that Certificate Profiles are configured under Device > Certificate Management > Certificate Profile .
- CA Certificates: Recognize that profiles rely on CA certificates already imported into the firewall ( Device > Certificate Management > Certificates ) and marked as trusted.
-
Revocation Checking Methods:
- CRL (Certificate Revocation List): Know it's a downloaded list of revoked serial numbers. Understand the need for CDP reachability.
- OCSP (Online Certificate Status Protocol): Know it's a real-time query to an OCSP responder. Understand the need for responder reachability.
- Check Order: Remember that if both are enabled, OCSP is checked first , and CRL is used as a fallback if OCSP fails or returns 'unknown'.
- Key Verification Settings: Understand the implications of enabling/disabling CRL/OCSP, setting timeouts, and especially the security impact of the "Block session if certificate status is unknown" option.
- Username Extraction: Know the options for the Username Field ( Subject - Common Name , Subject Alternative Name - Email , Subject Alternative Name - Principal Name , None) and their purpose in identifying the user from the certificate for features like GlobalProtect authentication or Admin UI login.
- Common Use Cases: Be familiar with scenarios where Certificate Profiles are essential, such as GlobalProtect (Portal/Gateway), certificate-based IPSec VPNs, certificate-based Admin UI authentication, and Authentication Portal.
- Troubleshooting Basics: Recognize common failure points like untrusted CAs, CRL/OCSP connectivity issues, and incorrect username field selection.
Certificate Profiles Knowledge Check (PCNSE Style)
Test your understanding of Certificate Profiles.