Comprehensive Guide to Configuring and Managing Certificates in PAN-OS
Digital certificates and the underlying Public Key Infrastructure (PKI) are fundamental components of modern network security, enabling authentication, encryption, and integrity verification. Palo Alto Networks firewalls and Panorama extensively utilize certificates across various features to secure communications and establish trust between network entities.
Proper configuration and diligent management of these certificates are crucial for maintaining a robust security posture. This involves understanding how certificates are obtained, configured, deployed for different use cases, and managed throughout their lifecycle (including renewal and revocation).
This article provides a comprehensive guide to certificate management within PAN-OS, covering key use cases, the management workflow, configuration details, troubleshooting tips, best practices, and PCNSE exam focus areas.
Certificate Use Cases in PAN-OS
Palo Alto Networks devices leverage certificates for various critical functions:
- Administrative Web Interface (HTTPS): Securing access to the firewall/Panorama web UI. A server certificate is presented by the device to administrators' browsers. Using a certificate trusted by the browser (e.g., from an internal CA or public CA) prevents security warnings.
-
SSL/TLS Decryption (Forward Proxy & Inbound Inspection):
- Forward Trust Certificate: Used by the firewall to re-sign server certificates for outbound traffic being decrypted (SSL Forward Proxy). Clients must trust the CA that issued this certificate (or the certificate itself if self-signed).
- Forward Untrust Certificate: Presented to clients when they try to access a site whose original certificate is invalid or untrusted by the firewall. This intentionally generates a browser warning, alerting the user.
- SSL Inbound Inspection: Requires importing the actual server certificate and its private key onto the firewall so it can decrypt traffic destined for internal servers.
-
GlobalProtect (Portal & Gateway):
- Server Certificates: Each Portal and Gateway requires a server certificate to authenticate itself to connecting clients/agents. The client must trust the CA that issued these certificates.
- Client Certificates (Optional): Can be used as an additional factor for authenticating connecting users or devices (machine certificates for pre-logon). Requires a Certificate Profile configured on the Portal/Gateway to validate client certs.
- IPSec VPN (Site-to-Site): Certificates can be used instead of pre-shared keys (PSKs) for IKE authentication between VPN peers, offering stronger authentication and scalability. Requires importing peer certificates or trusting a common CA.
- Authentication Portal & Captive Portal: When using HTTPS for Captive Portal or the Authentication Portal service, a server certificate is required to secure the connection and authenticate the portal to the user's browser.
- User-ID / Terminal Services (TS) Agent Communication: Securing the communication channel between the firewall/Panorama and User-ID agents or TS agents using SSL/TLS.
- External Dynamic List (EDL) Server Validation: When fetching EDLs from an HTTPS server, a Certificate Profile can be used to validate the server's certificate, ensuring the EDL source is authentic.
- Administrative Authentication (Client Certificate): Administrators can be required to present a client certificate (in addition to or instead of a password) for authentication to the web UI or CLI.
Certificate Management Workflow
Effectively managing certificates involves a lifecycle approach:
-
Obtain Certificates:
Acquire the necessary certificates. This can involve:
- Generating a self-signed CA and server/client certificates directly on the firewall/Panorama.
- Generating a Certificate Signing Request (CSR) on the firewall/Panorama and having it signed by an external (public or enterprise) CA.
- Importing existing certificates (including root/intermediate CAs and server/client certs with their private keys, often in formats like PEM or PKCS#12).
-
Configure Certificate Infrastructure:
- Import necessary Root and Intermediate CA certificates to establish trust chains.
- Configure Certificate Profiles to define trust anchors (CAs) and revocation checking methods (CRL/OCSP).
-
Deploy Certificates:
Assign certificates to specific PAN-OS features:
- Assign server certificates via SSL/TLS Service Profiles for Admin UI, GlobalProtect, Captive Portal, etc.
- Assign Forward Trust/Untrust certificates in Decryption Profiles/Policies.
- Reference Certificate Profiles in GlobalProtect Authentication, IPSec Crypto Profiles, etc.
-
Manage Certificate Lifecycles:
- Monitoring: Track certificate validity periods and expiration dates (visible in the Certificates UI).
- Renewal: Renew expiring certificates before they expire by generating a new CSR (if applicable) or obtaining a renewed certificate from the CA and importing it (often replacing the existing one with the same name).
- Revocation Checking: Configure CRL (Certificate Revocation List) and/or OCSP (Online Certificate Status Protocol) checking in Certificate Profiles to ensure revoked certificates are not trusted.
- Revocation (if acting as CA): If using the firewall as a CA, revoke certificates for compromised or decommissioned entities.
Obtaining Certificates
PAN-OS provides several ways to get certificates onto the device (
Device > Certificate Management > Certificates
):
-
Generate Self-Signed Certificate:
- Create a certificate signed by itself (no external CA).
- Useful for internal CAs (marking it as 'Certificate Authority'), lab testing, or simple server certs where trust can be manually established (e.g., importing the self-signed cert into clients).
- Requires defining Common Name (CN), cryptographic settings (RSA/ECDSA, key size, digest), validity period, and optional attributes (SANs).
- The private key is generated and stored securely on the device.
-
Generate Certificate Signing Request (CSR):
- Creates a request containing the public key and identity information (CN, attributes) to be sent to an external CA for signing.
- Select 'External Authority (CSR)' as 'Signed By'.
- Specify CN, crypto settings, attributes (including Subject Alternative Names - SANs - if needed for multiple hostnames/IPs).
- Export the generated CSR file (usually PEM format) and submit it to the chosen CA (Enterprise or Public).
- The private key associated with the CSR remains securely on the firewall.
- Once the CA returns the signed certificate, import it back onto the firewall, ensuring the Certificate Name matches the original CSR name. The status changes from 'pending' to 'valid'.
-
Import Certificate:
- Upload existing certificates and optionally their private keys.
- CA Certificates: Import Root and Intermediate CA certificates (usually PEM format, private key not needed/included). Mark Root CAs as 'Trusted Root CA'.
-
Server/Client Certificates (with Key):
Import certificates (e.g., for servers, GlobalProtect clients, device identity) along with their corresponding private key. Common formats:
- PKCS#12 (.pfx, .p12): Contains both certificate and encrypted private key. Requires the import passphrase.
- PEM (Base64): Requires importing the certificate file and the (potentially encrypted) private key file separately.
- Import without Key: Can import certificates without private keys (e.g., CA certs, peer certs for validation).
- HSM Integration: Option to specify that the private key resides on an external Hardware Security Module (HSM) instead of being imported directly. Requires HSM configuration.
Certificate Profiles
Certificate Profiles define how the firewall validates certificates presented to it by clients or servers, and which client certificates it might request or require.
-
Configuration Location:
Device > Certificate Management > Certificate Profile. - Purpose: Used in features requiring certificate validation, such as GlobalProtect Portals/Gateways (for client cert auth), IPSec VPN (certificate-based peer auth), Authentication Portal, and EDL server validation.
-
Key Settings:
- Name: Unique identifier for the profile.
- CA Certificates: List of trusted Root and Intermediate CA certificates used to validate the chain of trust for incoming certificates. The firewall must have these CA certs imported.
- Username Field: For client certificate authentication, specifies which field in the client certificate's Subject or Subject Alternative Name (SAN) contains the username (e.g., Common Name, Email, User Principal Name).
- Domain Name Field: Specifies the attribute containing the domain name, if needed for username construction.
- Block Session if Certificate Status Cannot Be Determined: If revocation checking (OCSP/CRL) fails due to connectivity issues, this option determines whether to block or allow the session. Allowing is less secure but may prevent outages.
-
Certificate Revocation Checking (CRL/OCSP):
- Use CRL: Enables checking against Certificate Revocation Lists. Requires configuring CRL Distribution Points (often extracted from the certificate itself or manually configured).
- Use OCSP: Enables checking against Online Certificate Status Protocol responders. Requires configuring OCSP responder URLs (often extracted from the certificate's Authority Information Access (AIA) extension or manually configured).
- Specify settings for timeouts and behavior if the CRL/OCSP server is unavailable.
- Block Session on Expired Certificate: Ensures certificates past their validity date are rejected.
Certificate Deployment
Once certificates are obtained and profiles configured, they need to be assigned to the features that use them.
-
SSL/TLS Service Profiles:
-
Location:
Device > Certificate Management > SSL/TLS Service Profile. - Purpose: Associates a specific server certificate (and its private key stored on the firewall) with services that need to present a certificate to clients (e.g., Admin Web UI, GlobalProtect Portal/Gateway, Captive Portal over HTTPS).
- Configuration: Select the desired server Certificate from the dropdown. Also allows configuring supported TLS versions (e.g., min TLSv1.2) and allowed cipher suites (though ciphers often best left managed by PAN-OS unless specific compliance needed).
-
Application:
These profiles are selected in the configuration sections of the respective services (e.g.,
Device > Setup > Managementfor Admin UI, GlobalProtect Portal/Gateway configuration, Authentication Portal settings).
-
Location:
-
SSL Decryption:
-
Forward Trust Certificate:
Marked directly on the CA certificate used for signing (
Device > Certificates, check 'Forward Trust Certificate'). Recommended to use a subordinate CA signed by your enterprise CA or a self-signed root CA deployed to clients. -
Forward Untrust Certificate:
Marked directly on a certificate (often self-signed) used for untrusted sites (
Device > Certificates, check 'Forward Untrust Certificate'). - Inbound Inspection: The actual server certificate (with private key) is imported and selected within the Decryption Policy rule (Action: Decrypt, Type: SSL Inbound Inspection).
-
Forward Trust Certificate:
Marked directly on the CA certificate used for signing (
-
GlobalProtect / VPN / Authentication Portal (Client Validation):
- Certificate Profiles (defining trusted CAs and revocation) are assigned within the authentication settings of the GlobalProtect Portal/Gateway, IPSec Crypto Profile, or Authentication Profile used by Captive Portal.
-
EDL Server Validation:
-
A Certificate Profile is selected within the External Dynamic List object configuration (
Objects > External Dynamic Lists) when using an HTTPS source URL.
-
A Certificate Profile is selected within the External Dynamic List object configuration (
Certificate Lifecycle Management
Certificates have a finite lifespan and can become invalid. Managing this lifecycle is crucial.
Monitoring Expiration:
-
The Certificates list (
Device > Certificate Management > Certificates) displays the validity dates (Not Valid Before, Not Valid After). -
Configure System Log forwarding or SNMP traps for certificate expiration warnings (
Device > Log Settings > System). - Utilize Panorama dashboards or external monitoring tools integrated via API/SNMP.
Renewal:
- Self-Signed: Generate a new self-signed certificate before the old one expires and update all configurations referencing it (e.g., SSL/TLS Service Profiles).
-
Externally Signed (via CSR):
- Generate a new CSR for the expiring certificate (can often reuse attributes from the old one).
- Submit the new CSR to the CA.
- Import the newly signed certificate from the CA, ensuring the Certificate Name matches the expiring certificate exactly. This replaces the old certificate while keeping the existing private key.
- Commit the changes. Services using the certificate via profiles should automatically pick up the renewed certificate.
- Imported (e.g., PKCS#12): Obtain the renewed certificate (with its private key) from the CA or source system. Import it using the same Certificate Name as the expiring certificate to replace it.
Revocation Checking:
- Purpose: To ensure that certificates that were compromised or invalidated *before* their expiration date are not trusted.
-
Methods:
- CRL (Certificate Revocation List): The firewall downloads a list of revoked serial numbers from a CRL Distribution Point (CDP) URL (often embedded in the certificate). Requires the firewall to periodically fetch potentially large files.
- OCSP (Online Certificate Status Protocol): The firewall queries an OCSP responder URL (often embedded in the certificate's AIA extension) in real-time for the status of a specific certificate serial number. Generally more efficient than CRLs but requires real-time connectivity to the responder.
-
Configuration:
Enabled within Certificate Profiles (
Device > Certificate Management > Certificate Profile). Specify whether to use CRL, OCSP, or both, and configure timeouts and failure behavior.
Troubleshooting Certificate Issues
Certificate problems can manifest in various ways (e.g., browser warnings, GlobalProtect connection failures, decryption errors). Common issues include:
-
Untrusted Certificate Errors (Browser Warnings):
- Cause: The certificate presented by the service (e.g., Admin UI, GP Portal, decrypted site) is self-signed or signed by a CA that the client browser/OS does not trust.
- Troubleshooting: Verify the certificate chain. Is the Root CA certificate installed in the client's trusted store? If using an Enterprise CA, ensure the full chain (Root, Intermediates) is correctly imported onto the firewall and potentially served to the client. Check if the correct certificate is assigned via the SSL/TLS Service Profile.
-
Certificate Name Mismatch Errors:
- Cause: The Common Name (CN) or a Subject Alternative Name (SAN) in the certificate does not match the hostname or IP address the client is using to access the service.
- Troubleshooting: Ensure the certificate's CN/SANs include all FQDNs and IP addresses used to access the service. Regenerate CSR/certificate if necessary. Use FQDNs consistently.
-
Expired Certificate Errors:
- Cause: The certificate's validity period has ended.
-
Troubleshooting:
Check the 'Not Valid After' date in
Device > Certificates. Renew the certificate and import/replace the expiring one. Ensure system clocks on firewall and clients are synchronized.
-
Revoked Certificate Errors:
- Cause: The certificate has been revoked by the issuing CA, but revocation checking (CRL/OCSP) is functioning correctly.
- Troubleshooting: Obtain a new, valid certificate. Investigate why the certificate was revoked.
-
Revocation Check Failures (CRL/OCSP):
- Cause: Firewall cannot reach the CDP or OCSP responder URL due to network connectivity issues (routing, firewall rules upstream), DNS failures, or the responder being offline. The Certificate Profile might be configured to block sessions if status cannot be obtained.
- Troubleshooting: Verify firewall connectivity to CRL/OCSP URLs (ping, curl via CLI). Check DNS resolution. Review Certificate Profile settings for CRL/OCSP (URLs, timeouts, failure handling). Check Traffic and System logs for connection errors.
-
Private Key Missing / Mismatch:
- Cause: Importing a certificate without its corresponding private key when the key is required (e.g., for a server certificate used in an SSL/TLS Service Profile). Importing a renewed certificate with a name that doesn't match the CSR generated on the firewall (key mismatch).
-
Troubleshooting:
Ensure the private key is present (Key column checked in
Device > Certificates). Re-import using the correct format (e.g., PKCS#12) or import the key separately if using PEM. Ensure the certificate name matches the original CSR exactly when importing a signed certificate.
-
Incorrect Certificate Chain Order:
- Cause: When importing PEM certificates containing a chain, the order (End-entity -> Intermediate(s) -> Root) might be incorrect, or intermediates might be missing.
- Troubleshooting: Export the certificate, inspect the PEM file contents, reorder if necessary, ensure all needed intermediates are included (or imported separately), and re-import.
Certificate Management Best Practices
- Use Trusted CAs: Whenever possible, use certificates signed by a well-known public CA or a trusted internal Enterprise CA, especially for user/client-facing services (Admin UI, GlobalProtect, Captive Portal, SSL Decryption Forward Trust). This minimizes trust issues on client devices. Self-signed certificates are generally acceptable only for lab/testing or specific internal uses where trust can be manually deployed.
- Implement Revocation Checking: Configure OCSP and/or CRL checking in Certificate Profiles used for validating client/peer certificates to ensure revoked certificates are promptly rejected.
- Proactive Lifecycle Management: Monitor certificate expiration dates diligently. Establish processes for renewing certificates well before they expire to prevent service disruptions. Automate renewal and deployment where possible using tools or APIs.
-
Secure Private Keys:
Protect private keys associated with certificates.
- Avoid exporting private keys from the firewall unless absolutely necessary and transfer them securely.
- Use strong passphrases if exporting in formats like PKCS#12.
- Consider using Hardware Security Modules (HSMs) for storing critical private keys (e.g., Forward Trust CA, inbound inspection keys) if supported and required by security policy.
- When getting CSRs signed by an Enterprise CA, block private key export if the CA generates the key pair.
- Use SANs: Utilize Subject Alternative Names (SANs) in certificates to cover multiple FQDNs or IP addresses with a single certificate, rather than relying solely on the Common Name (CN).
- Appropriate Key Lengths & Algorithms: Use industry-standard key lengths (e.g., RSA 2048-bit or higher, ECDSA P-256 or higher) and secure signature algorithms (e.g., SHA-256 or higher).
- Separate Certificates for Functions: While SANs are useful, consider using distinct certificates for logically separate functions (e.g., one for Admin UI, one for GlobalProtect Portal, one for SSL Decryption Forward Trust) for better isolation and easier management/revocation if needed. Avoid using the same certificate for HA peers' management interfaces.
- Regular Audits: Periodically review all configured certificates, their usage, expiration dates, and associated profiles. Remove unused or expired certificates.
Illustrations: Certificate Lifecycle Flowchart
This flowchart outlines the typical lifecycle of a certificate used on PAN-OS.
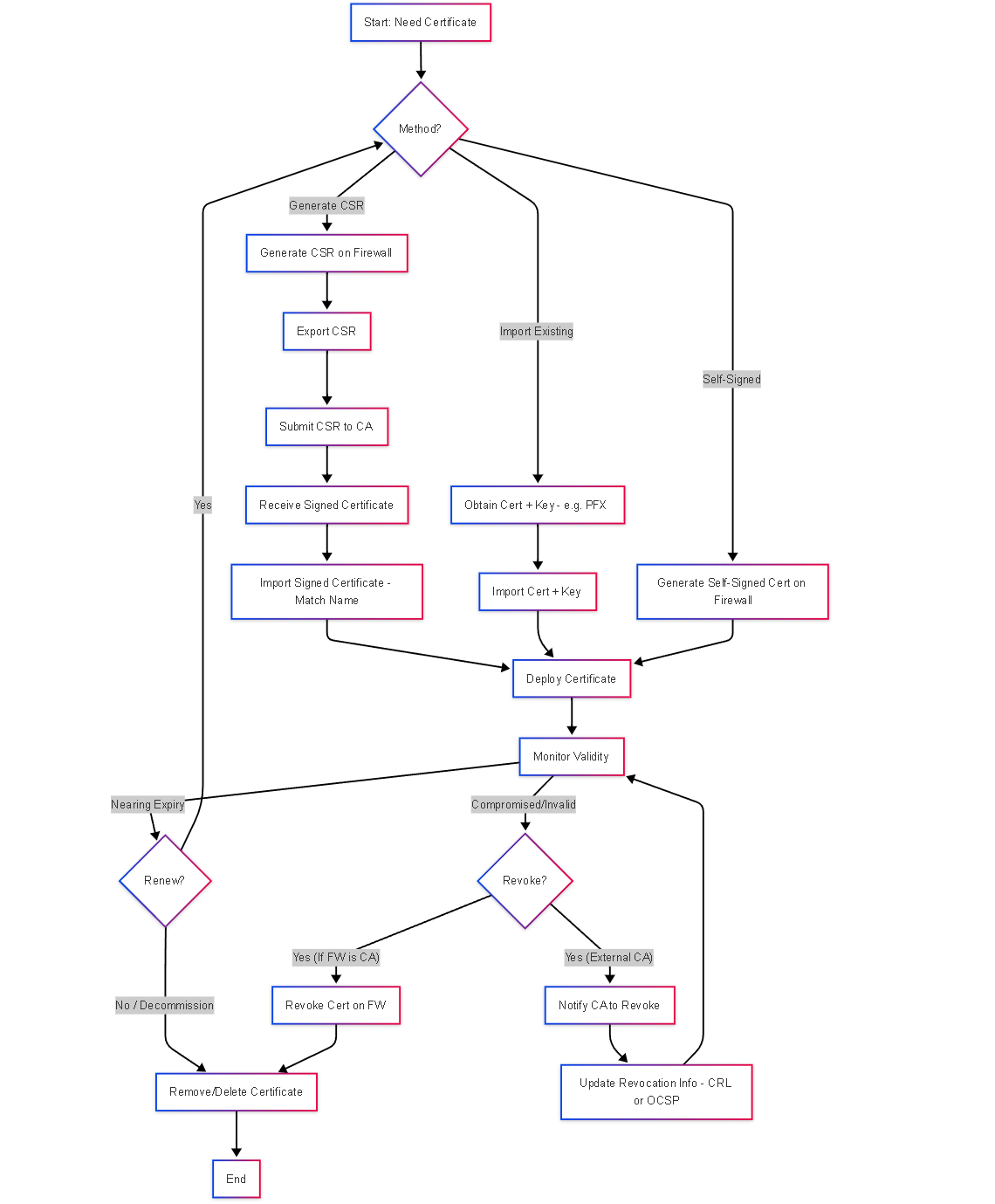
Simplified flowchart illustrating the certificate lifecycle stages from obtaining to deployment, monitoring, renewal, and revocation/removal.
Illustrations: Simplified TLS Handshake Sequence (Server Auth)
This sequence shows a client connecting to a service secured by a certificate on the firewall.
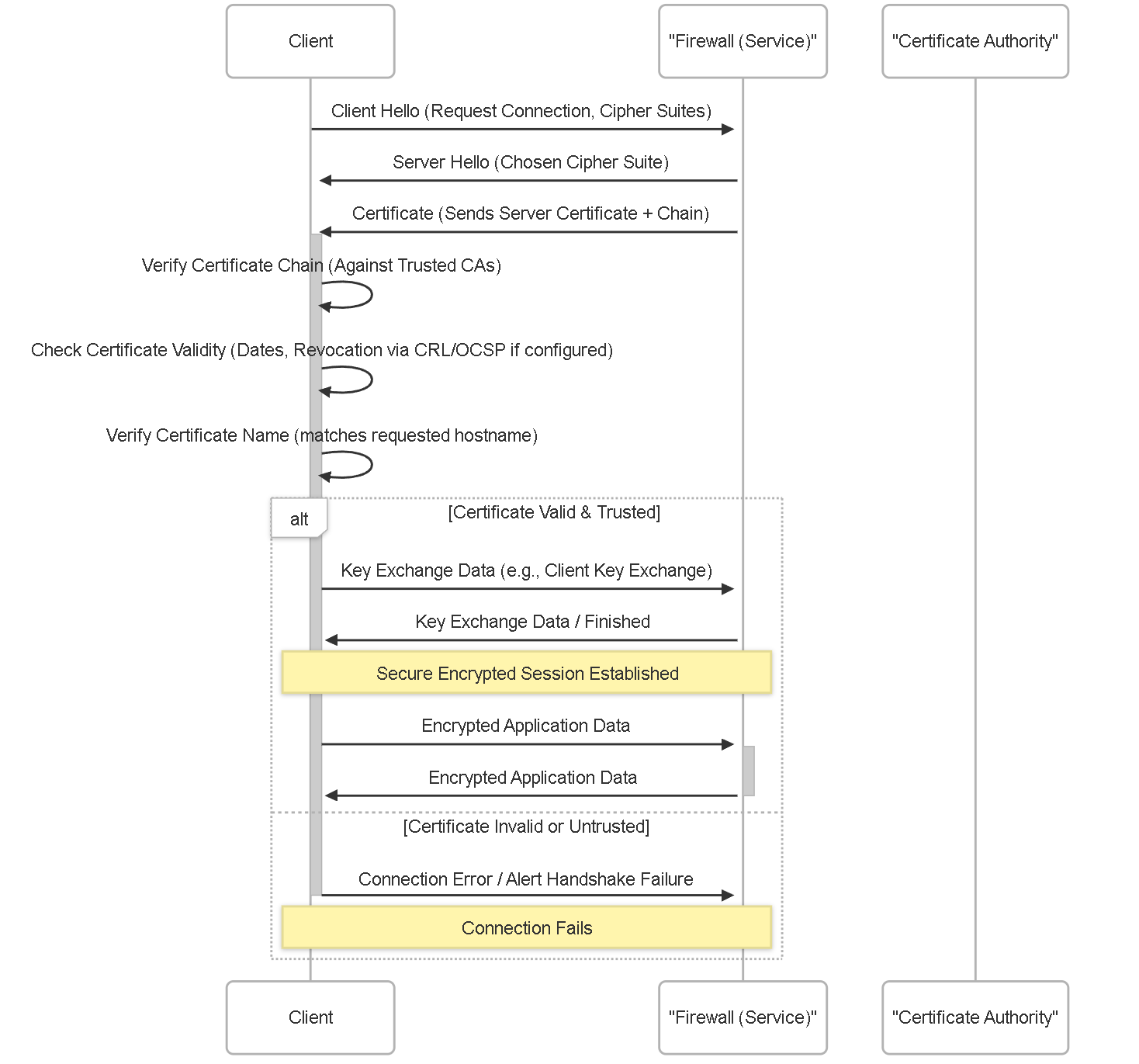 Simplified TLS handshake focusing on the server certificate validation steps performed by the client.
Simplified TLS handshake focusing on the server certificate validation steps performed by the client.
Illustrations: Configuration Relationship Graph
This graph shows how certificate-related objects interconnect.
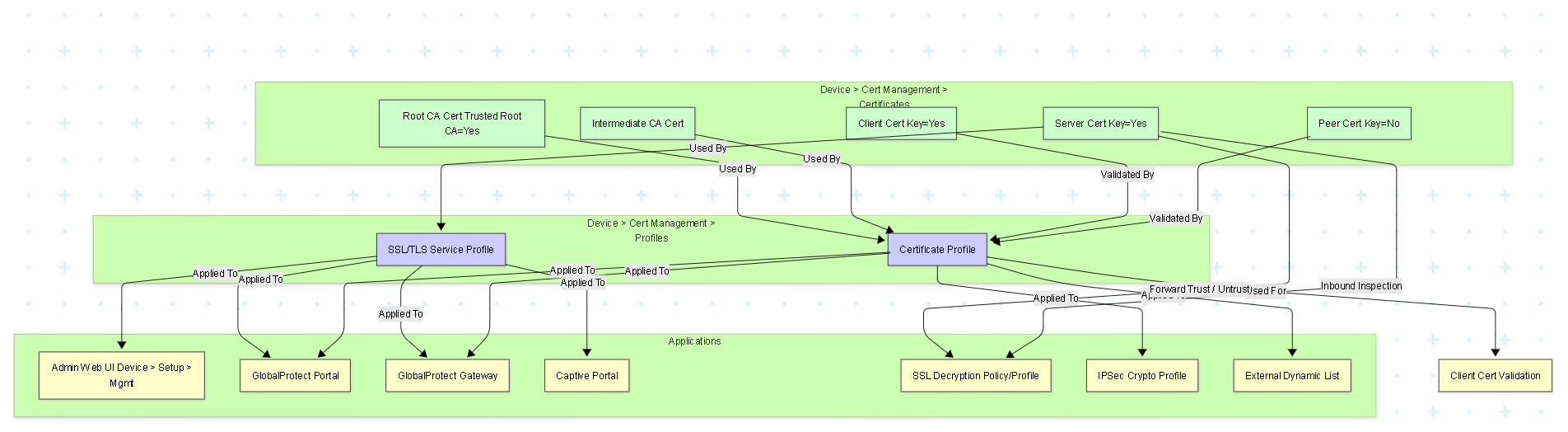
Graph showing how certificates are used by profiles (Certificate Profile, SSL/TLS Service Profile), which are then applied to various firewall applications/features.
Illustrations: Certificate State Diagram
This diagram shows the possible validity states of a certificate.
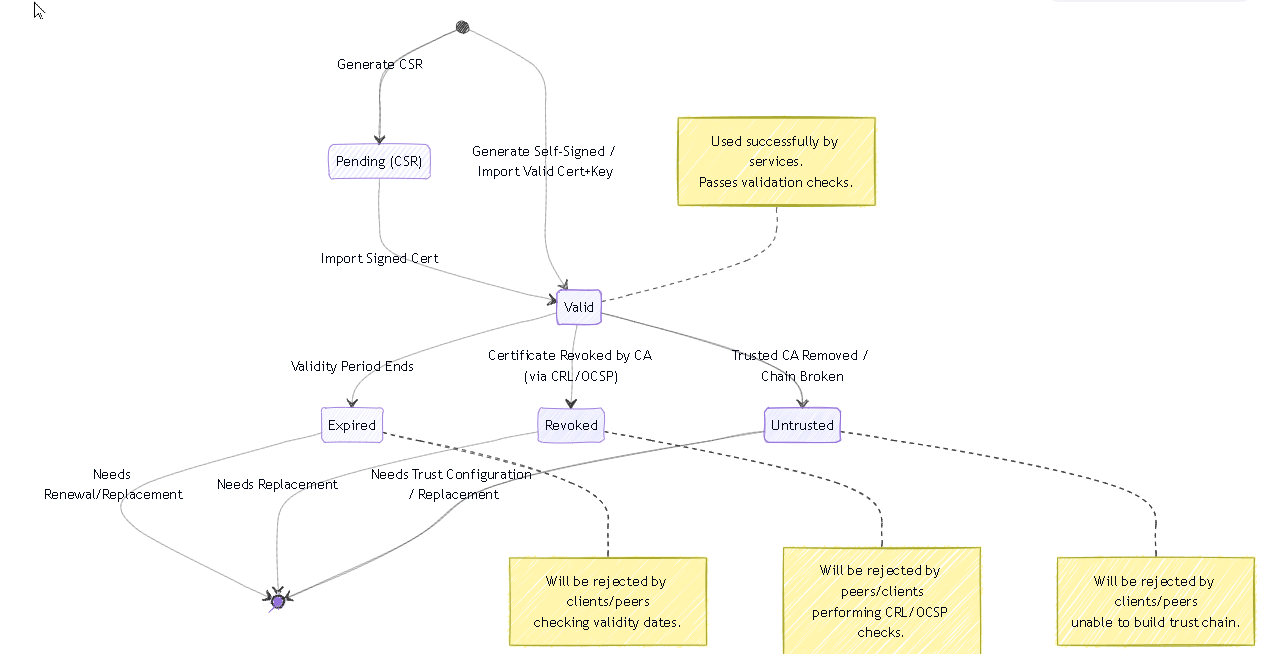
Simplified state diagram showing the transitions between certificate states based on signing, expiration, revocation, and trust configuration.
PCNSE Focus Points
- Certificate Types & Purpose: Differentiate between Root CA, Intermediate CA, Server Certificates, and Client Certificates and where each is typically used (e.g., Server cert for Admin UI/GP, CA certs in Certificate Profiles).
- Obtaining Certificates: Understand the three methods: Generate Self-Signed, Generate CSR & Import Signed, Import Existing (PEM, PKCS#12). Know when a private key is needed.
- Certificate Profiles: Know their purpose (validating incoming certs), key settings (CA list, Username Field, CRL/OCSP), and where they are applied (GP Auth, IPSec, EDL, Auth Portal).
- SSL/TLS Service Profiles: Know their purpose (assigning a *server* certificate to a firewall service), key settings (Certificate selection, TLS versions), and where they are applied (Admin UI, GP Portal/Gateway, Captive Portal).
- SSL Decryption Certificates: Understand Forward Trust (signing outbound) and Forward Untrust (blocking untrusted) concepts. Know that the Forward Trust CA (or self-signed root) needs to be trusted by clients. Know that Inbound Inspection requires the server's actual cert and private key.
- GlobalProtect Certificates: Know that Portal/Gateway require Server Certificates (via SSL/TLS Service Profile) and optionally use Certificate Profiles for client certificate validation.
- Revocation Checking: Understand the difference between CRL and OCSP and that they are configured in Certificate Profiles.
- Troubleshooting Concepts: Recognize common failure points: untrusted CA, name mismatch, expiration, revocation check failure, missing private key, incorrect chain order.
- Best Practices: Emphasize using Trusted CAs, implementing revocation checking, managing expirations, and securing private keys.
PCNSE Prep Quiz: Certificate Configuration and Management
Test your knowledge of PAN-OS certificate management.