Interface Management Profiles Overview
An
Interface Management profile
protects the firewall from unauthorized access by defining the protocols, services, and IP addresses that a firewall interface permits for management traffic. For example, you might want to prevent users from accessing the firewall web interface over the
ethernet1/1
interface but allow that interface to receive SNMP queries from your network monitoring system. In this case, you would enable SNMP and disable HTTP/HTTPS in an Interface Management profile and assign the profile to
ethernet1/1
.
You can assign an Interface Management profile to Layer 3 Ethernet interfaces (including subinterfaces) and to logical interfaces (aggregate group, VLAN, loopback, and tunnel interfaces) . If you do not assign an Interface Management profile to an interface, it denies access for all IP addresses, protocols, and services by default.
The management (MGT) interface does not require an Interface Management profile. You restrict protocols, services, and IP addresses for the MGT interface during the initial configuration of the firewall. Allowing management access over another interface (using a profile) provides a backup method in case the MGT interface goes down.
When enabling access to a firewall interface using an Interface Management profile, do not enable management access (HTTP, HTTPS, SSH, or Telnet) from the internet or from other untrusted zones inside your enterprise security boundary. Never enable HTTP or Telnet access because those protocols transmit in cleartext. Follow the Administrative Access Best Practices to ensure proper security.
Configure Interface Management Profile
Steps:
-
Navigate to:
Network > Network Profiles > Interface Mgmtand click Add . -
Name the Profile:
Enter a unique, descriptive name (e.g.,
Mgmt_Profile_L3). -
Enable Administrative Management Services:
- SSH: Enable for secure CLI access.
- HTTPS: Enable for secure web interface access.
- Telnet and HTTP: Do not enable as they transmit data in plaintext.
-
Enable Network Services:
- Ping: Enable to allow ICMP echo requests for connectivity testing.
- SNMP: Enable if SNMP monitoring is required.
- HTTP OCSP: Enable if using the firewall as an OCSP responder.
-
Enable Response Pages:
- Authentication Portal: Enable to serve authentication pages for user identification (Captive Portal). Ports 6081 (transparent) and 6082 (redirect) are used on Layer 3 interfaces.
- URL Admin Override: Enable to allow administrators to override URL filtering blocks.
-
Enable User-ID Services:
- User-ID: Enable to allow redistribution of user mappings.
- User-ID Syslog Listener-SSL: Enable if collecting syslog messages over SSL for User-ID.
- User-ID Syslog Listener-UDP: Enable if collecting syslog messages over UDP for User-ID.
-
Restrict Access by IP Address:
-
In the
Permitted IP Addresses
section, specify the IPv4 or IPv6 addresses or subnets allowed to access the interface (e.g.,
192.168.1.0/24). - If no addresses are specified, access is denied by default. This is a critical security control.
-
In the
Permitted IP Addresses
section, specify the IPv4 or IPv6 addresses or subnets allowed to access the interface (e.g.,
-
Assign the Profile to Interfaces:
-
Navigate to
Network > Interfaces. - Select the desired interface (e.g., Ethernet, VLAN, Loopback, or Tunnel).
- Under the Advanced tab, in the Other Info section, select the newly created Interface Management Profile from the dropdown.
-
Navigate to
- Commit the Configuration: Click Commit to apply the changes. Forgetting to commit is a common mistake.
Configuration Fields Details
The following table details the options available within the Interface Management Profile configuration:
| Field | Description |
|---|---|
| Name | Enter a profile name (up to 31 characters). This name appears in the list of Interface Management profiles when configuring interfaces. The name is case-sensitive and must be unique. Use only letters, numbers, spaces, hyphens, and underscores. |
| Administrative Management Services |
|
| Network Services |
|
| Permitted IP Addresses | Enter the list of IPv4 or IPv6 addresses from which the interface allows access. Crucial for security. If empty, access is denied. |
Remember: Don’t enable HTTP or Telnet because those protocols transmit in cleartext and therefore aren’t secure.
Best Practices for Administrative Interfaces
Administrative interfaces (like the dedicated MGT port or specific Layer 3 interfaces used for management) require careful configuration to prevent unauthorized access.
Key Principles:
- Restrict Access to Trusted IPs: Define specific IP addresses or subnets permitted to access the interface in the "Permitted IP Addresses" list. If no IPs are specified, all access is denied by default. This is the primary security mechanism.
- Enable Only Secure Management Protocols: Activate protocols like HTTPS and SSH for secure access. Avoid enabling HTTP or Telnet , as they transmit data in plaintext.
- Avoid Exposure to Untrusted Networks: Do not enable management access from the internet or untrusted zones within your enterprise. Ensure administrative interfaces are isolated from general user traffic.
-
Implement Role-Based Access Controls (RBAC):
Assign Admin Role Profiles (
Device > Admin Roles) to limit administrative privileges to necessary areas. Create unique accounts for each administrator or service to ensure accountability. -
Configure Session Security Settings:
Set login timeouts (
Device > Setup > Management > Authentication Settings > Idle Timeout) to prevent prolonged idle sessions. Specify the number ofFailed AttemptsandLockout Time(in Authentication Profile or global settings) to mitigate brute-force attacks.
Do not attach an interface management profile that allows Telnet, SSH, HTTP, or HTTPS to an interface where you have configured a GlobalProtect portal or gateway, as this will expose the management interface to the internet.
Best Practices for User-Facing Interfaces
Interfaces handling regular user traffic (typically assigned to security zones like 'Trust' or 'Untrust') should have minimal management services enabled.
Key Principles:
- Limit Management Services: Avoid enabling administrative services (e.g., HTTPS, SSH) on these interfaces. If absolutely necessary for troubleshooting, enable only essential services like Ping temporarily.
-
Enable Necessary User Services:
If using features like Captive Portal or User-ID on this interface, enable the corresponding services in the profile:
- Response Pages for Authentication Portal (Captive Portal).
- User-ID services (User-ID, Syslog Listener-SSL/UDP) if the firewall needs to collect or redistribute User-ID information via this interface.
- Restrict Access to Specific IPs (If Applicable): While generally administrative access is disabled, if specific network services like SNMP *must* be enabled on a user-facing interface, use the Permitted IP Addresses list to restrict access only to authorized monitoring servers or specific subnets.
- Avoid Enabling Insecure Protocols: Never enable HTTP or Telnet on user-facing interfaces.
The goal for user-facing interfaces is to minimize the attack surface by disabling any management protocol or service not explicitly required for user interaction features like Captive Portal or User-ID functions tied to that specific interface.
Detailed Administrative Access Best Practices
This section expands on securing administrative access, drawing from Palo Alto Networks' best practice documentation.
Deploying Administrative Access Best Practices
This involves several key tasks:
- Select the Management Interface (MGT vs. Dataplane)
- Manage Administrator Access (Accounts, Roles, Authentication)
- Isolate the Management Network
- Restrict Access to the Management Interface (Profiles, IPs, Services)
- Replace the Certificate for Inbound Traffic Management
- Keep Content and Software Updates Current
- Scan All Traffic Destined for the Management Interface
Two critical concepts underpin these practices:
-
Principle of Least Privilege:
- Enable access only for those who need it.
- Limit access to required areas/privileges using RBAC (Admin Roles) .
- Isolate the management network and interface.
-
Inspect All Management Traffic:
- Use granular Security Policy rules (IPs, Users, Apps, Zones).
- Apply Threat Prevention profiles (especially Vulnerability Protection).
- Log traffic and forward logs appropriately.
Selecting the Management Interface
You can use the dedicated MGT port or a dedicated in-band dataplane (DP) port . Panorama must use the MGT port.
You cannot apply Security Policy rules directly to traffic ingressing the MGT port . To inspect MGT port traffic, you must route it through a DP port (on the same or another firewall).
- Recommended: Use the MGT port but route inbound traffic via a DP port for inspection (e.g., loopback, another firewall). Do not enable management protocols on the inspecting DP port itself.
- Alternative: If inspection via another DP port isn't feasible, dedicate a DP port as the management interface. This allows direct Security Policy application but consumes a production port.
Inspecting inbound management traffic is crucial to prevent unauthorized access and threats.
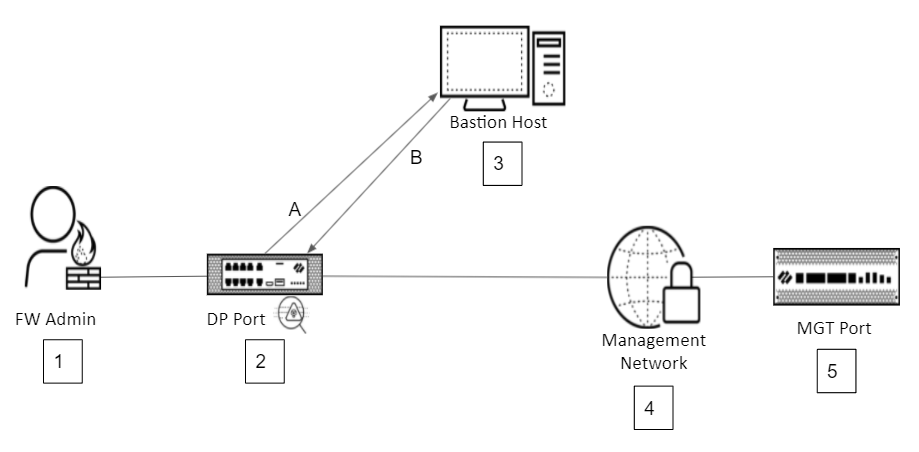
Management Isolation Topologies
Architectures often involve isolating the management network and inspecting traffic before it reaches the managed device's MGT port. Common components include:
- Administrator (often via VPN)
- Bastion Host: Authenticates administrators before granting access to the management network.
- Inspecting Firewall (using a dedicated DP subinterface/VLAN for isolation)
- Isolated Management Network
- Managed Device (Firewall/Panorama)

Managing Administrator Access
Apply the principle of least privilege rigorously.
- Replace the default 'admin' account: Change the password immediately, then create a new local superuser account with a strong password, log in with the new account, and delete the default 'admin' account . Store the new local credentials securely for emergencies.
- Use External Authentication + MFA: For all other administrators (including API users), use an external system (RADIUS, SAML) with Multi-Factor Authentication (MFA). Avoid multiple local accounts.
- Strong Passwords & Keys: Follow NIST guidelines. Use password managers. If using local accounts is unavoidable, use Certificate-Based Authentication for the web UI and SSH Key-Based Authentication for the CLI.
- Change the Master Key: Replace the default master key to protect stored credentials. Back up config first. Ensure HA pairs and Panorama/Log Collectors use the same key. Store the new key securely.
- Secure API Access: Use role-based access for API service accounts. Generate API keys and configure API Key Lifetimes to enforce rotation.
- Secure SNMP: Use SNMPv3 if possible due to its enhanced security (authentication, encryption, granular access). Route SNMP traffic securely (ideally inspected via a DP port).
-
Use Admin Role Profiles (RBAC):
Define roles (
Device > Admin Roles) limiting access to specific functions/areas (CLI/API/UI). Assign roles to unique administrator/service accounts. Do not over-provision privileges. Use Access Domains in Panorama for granular control. -
Configure Session Security:
Set
Idle Timeout,Failed Attempts, andLockout Time(Device > Setup > Management > Authentication SettingsorDevice > Authentication Profile). - Monitor Activity: Configure Administrator Activity Tracking, System Logs, and Log Forwarding to an external server. Use Administrator Login Activity Indicators. Enforce audit comments on policy changes.
Isolating the Management Network
- Use a Bastion Host as a single, hardened entry point with strong authentication (MFA) and screen recording.
- Allow management interface access only from the isolated management network (including the bastion host).
- Require multiple authentication steps (bastion host, then firewall) with MFA.
- Ensure necessary services (like Panorama managing firewalls) are within or have secure, inspected access to the management network.
Restricting Access to the Management Interface
- Allow direct access only from the management network. Route external access via VPN through the bastion host.
-
If using MGT port:
Configure
Device > Setup > Interfaces > Management > Management Interface Settings.- Enable only necessary secure services (HTTPS, SSH, maybe Ping).
- Specify Permitted IP Addresses (ideally just bastion host and essential management network IPs).
- Route traffic via DP port for inspection using Security Policy.
-
If using DP port as Mgmt Interface:
Configure an
Interface Management Profile(Network > Network Profiles > Interface Mgmt).- Enable only necessary secure services.
- Specify Permitted IP Addresses.
- Apply Security Policy rules directly to this interface.
- Use strong TLS/SSH settings: Configure SSL/TLS Service Profiles (Min TLSv1.2) and SSH Service Profiles to restrict weak ciphers/algorithms.
- Secure external service access (DNS, NTP, Updates): Use Service Routes via a DP port for inspection, applying Security Policy with specific App-IDs.
Replace the Certificate for Inbound Traffic Management
Replace the default self-signed certificate used for management access (HTTPS) with one issued by your enterprise CA or a trusted public CA.
Keep Content and Software Updates Current
Regularly apply PAN-OS software updates and Content (Apps/Threats) updates to patch vulnerabilities and get the latest protections.
Scan All Traffic Destined for the Management Interface
Requires routing traffic via a DP port for inspection.
-
Create granular
Security Policy rules
allowing access:
- Source/Destination Zone: Management Zone
- Source IP: Permitted IPs (e.g., Bastion Host, Mgmt Servers)
- Application: Specific required apps (e.g., ssh, ssl, paloalto-logging-service, panos-web-interface)
- User: Specific admin groups/users (if using User-ID)
- Action: Allow
- Apply a Vulnerability Protection profile (cloned from 'strict', modified to scan server-side vulnerabilities only) to these rules.
- Enable Logging and configure Log Forwarding.
- Use Schedules for temporary access.
- Apply SSL Inbound Inspection decryption policy to inspect encrypted management traffic (HTTPS).
Do not configure SSL Forward Proxy to decrypt outbound management traffic from the firewall/Panorama.
Best Practices Summary Table
This table summarizes recommended Interface Management Profile settings for different interface types:
| Setting | Administrative Interfaces | User-Facing Interfaces |
|---|---|---|
| Permitted IP Addresses | Trusted Admin IPs Only | Specific User Subnets (if services enabled) or Deny All (Default) |
| HTTPS/SSH | Enable | Disable |
| HTTP/Telnet | Disable | Disable |
| Ping | Optional (for testing) | Optional (rarely needed) |
| Response Pages (Captive Portal/URL Override) | Usually Disable (unless specific need) | Enable if needed (e.g., Captive Portal) |
| User-ID Services (Redistribution/Syslog Listener) | Optional (if used for mgmt plane User-ID) | Enable if needed (e.g., Syslog Listener on user interface) |
| SNMP | Optional (if monitoring needed, restrict IPs) | Optional (if monitoring needed, restrict IPs) |
| Role-Based Access (Device > Admin Roles) | Implement | Not Applicable (Handled by Device Settings) |
| Session Security Settings (Timeout/Lockout) | Configure | Not Applicable (Handled by Device Settings) |
Diagrams
Configuration Workflow
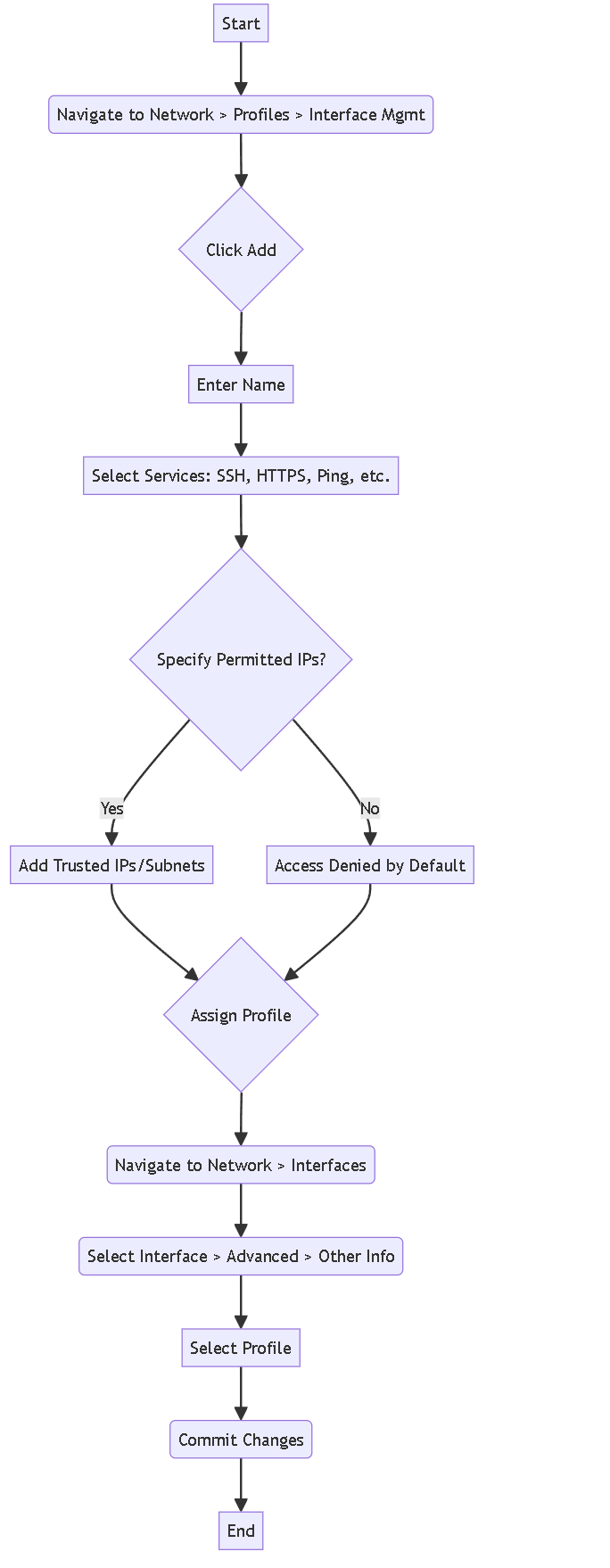
Basic workflow for creating and assigning an Interface Management Profile.
Best Practice Decision Flow
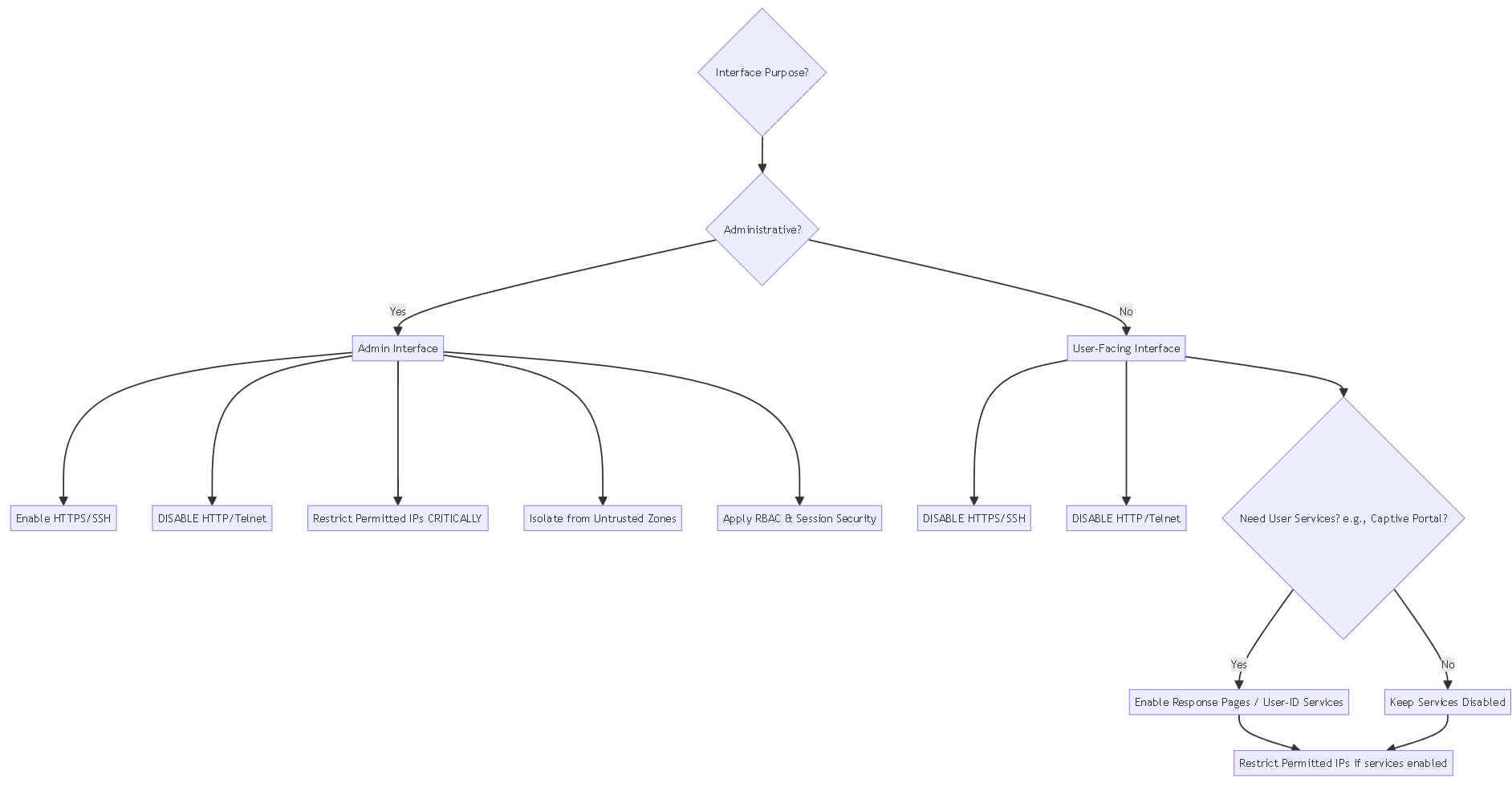
Decision flow for applying best practices based on interface type.
Management Isolation Packet Flow (Simplified Topology 1)
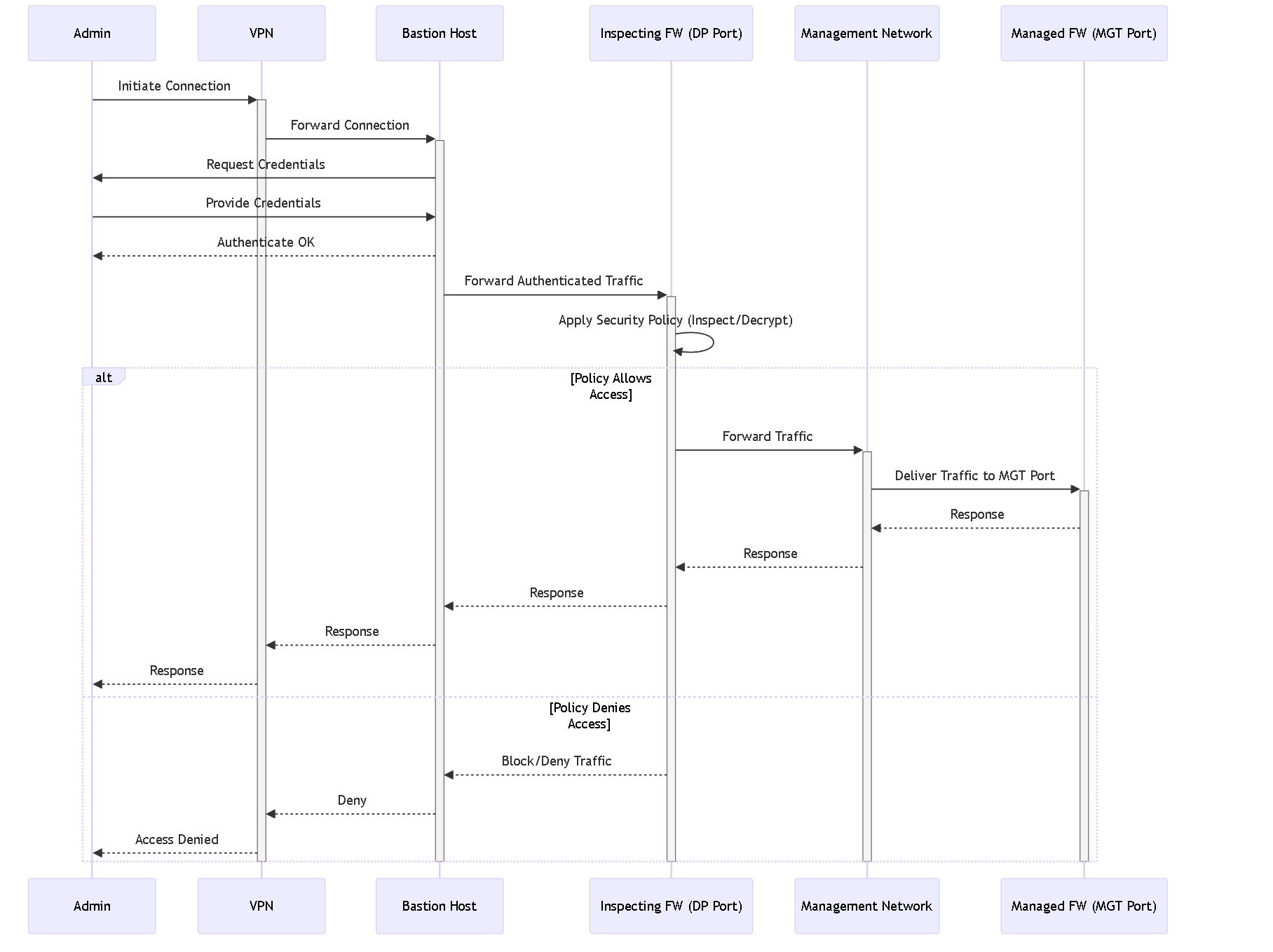
Simplified sequence diagram for traffic flow in Management Isolation Topology 1.
Interface Management Profile Quiz
Test your understanding of Interface Management Profiles and related best practices.