Packet Buffer Protection Overview
Packet Buffer Protection defends your firewall and network from single session DoS attacks that can overwhelm the firewall’s packet buffer and cause legitimate traffic to drop. Although you don’t configure Packet Buffer Protection in a Zone Protection profile or in a DoS Protection profile or policy rule, Packet Buffer Protection defends ingress zones.
While zone and DoS protection apply to new sessions (connections) and are granular, Packet Buffer Protection applies to existing sessions and is global in its monitoring, with per-zone enforcement options.
Packet Buffer Protection involves two configuration levels:
-
Global Packet Buffer Protection:
The firewall monitors sessions from
all zones
(regardless of whether Packet Buffer Protection is enabled in a zone) and how those sessions utilize the packet buffer. You must configure Packet Buffer Protection globally (
Device > Setup > Session Settings) to protect the firewall and enable it on individual zones. When packet buffer consumption reaches the configured Activate percentage, the firewall uses Random Early Drop (RED) to drop packets from the offending sessions (the firewall doesn’t drop complete sessions at the global level). -
Per-Zone Packet Buffer Protection:
Enable Packet Buffer Protection on each zone (
Network > Zones) to layer in a second level of protection. When packet buffer consumption crosses the Activate threshold (triggering global RED), the per-zone Block Hold Time timer starts for the offending session(s) in that zone. If the session continues to offend for the duration of the Block Hold Time, the firewall blocks the entire session . The offending session remains blocked until the Block Duration time expires.
You must enable Packet Buffer Protection globally in order for it to be active in zones.
There are two methods to trigger packet buffer protection:
- Packet Buffer Protection Based on Buffer Utilization
- Packet Buffer Protection Based on Latency
Protection Based on Buffer Utilization
Packet Buffer Protection based on buffer utilization is enabled by default. It monitors the percentage of the firewall's packet buffer being used.
Take baseline measurements of firewall packet buffer utilization over a significant period (at least one business week, preferably longer) to understand typical usage. Use the operational CLI command:
show running resource-monitor [day | hour | minute | second | week]
This command provides a snapshot. For continuous monitoring and anomaly detection, consider using an automated script (sample potentially available from Palo Alto Networks, but unsupported).
If baseline measurements consistently show abnormally high packet buffer utilization, the firewall might be undersized. Consider resizing the firewall deployment. Otherwise, carefully tune thresholds to prevent buffer overflow without dropping legitimate traffic.
Overrunning the firewall packet buffer negatively impacts the firewall’s packet forwarding capabilities for all traffic , as no packets can enter the firewall on any interface when buffers are full.
Buffer Utilization Thresholds
Best practices for setting thresholds:
- Alert: Default 50%. When exceeded for >10 seconds, generates a System log every minute. Start with default, adjust based on baseline. If utilization is normally well below 50% (on a correctly sized firewall), this provides an early warning.
- Activate: Default 80%. When reached, the firewall begins RED mitigation on the most abusive sessions (global action). Start with default, adjust based on baseline and capacity.
- Block Hold Time: Default 60 seconds. Per-zone setting. Timer starts when the global Activate threshold is crossed. If the offending session continues for this duration, the entire session is blocked. If buffer usage drops below Activate before the timer expires, it resets. Increasing imposes a greater penalty; decreasing imposes less.
- Block Duration: Default 3600 seconds (1 hour). Per-zone setting. Duration for which an offending session (or IP address, see below) is blocked after the Block Hold Time expires. Adjust if 1 hour is considered too long a penalty.
In addition to blocking individual sessions, Packet Buffer Protection can also block an entire IP address for the configured Block Duration if the firewall detects that source IP rapidly creating many small sessions that wouldn't individually trigger utilization limits but collectively strain the buffer.
Source Network Address Translation (NAT) can make a single external IP address appear responsible for high buffer utilization. If this occurs, consider reducing the Block Hold Time (to block abusive individual sessions faster) and reducing the Block Duration (to avoid penalizing the shared NAT IP for too long).
Protection Based on Latency
As an alternative to buffer utilization, you can trigger packet buffer protection based on packet latency introduced by dataplane buffering, which indicates congestion.
This method mitigates head-of-line blocking and can trigger protection before latency-sensitive protocols or applications (like VoIP or video conferencing) are noticeably affected. Use this method if your network carries significant latency-sensitive traffic.
Latency Thresholds
Packet buffer protection based on latency involves setting these thresholds:
- Latency Alert: Threshold in milliseconds. When average packet latency exceeds this value, the firewall generates an Alert log event.
- Latency Activate: Threshold in milliseconds. When average packet latency exceeds this value, the firewall activates RED on incoming packets and generates an Activate log.
- Latency Max Tolerate: Threshold in milliseconds. When average packet latency exceeds this value, the firewall applies RED with almost 100% drop probability.
The Block Hold Time and Block Duration settings function the same way for latency-based protection as they do for utilization-based protection, determining when and for how long entire sessions are blocked at the zone level after the Latency Activate threshold is crossed.
Configuration Summary
Packet Buffer Protection requires configuration at two levels:
-
Global Configuration:
- Navigate to Device > Setup > Session Settings .
- Under "Packet Buffer Protection", choose either Utilization or Latency as the trigger.
- Configure the corresponding global thresholds ( Alert , Activate for utilization; Latency Alert , Latency Activate , Latency Max Tolerate for latency).
- Ensure the "Enable" checkbox for Packet Buffer Protection is checked globally.
-
Per-Zone Configuration:
- Navigate to Network > Zones .
- Select the zone you want to protect.
- Check the Enable Packet Buffer Protection box for this zone.
- Configure the zone-specific Block Hold Time (seconds).
- Configure the zone-specific Block Duration (seconds).
- Repeat for each ingress zone requiring this protection.
Remember, per-zone settings only take effect if Packet Buffer Protection is also enabled globally.
Start with default values for thresholds, monitor system logs and resource utilization, and tune the settings based on your network's specific baseline and requirements.
Diagrams
Packet Buffer Protection Flow (Utilization Based)
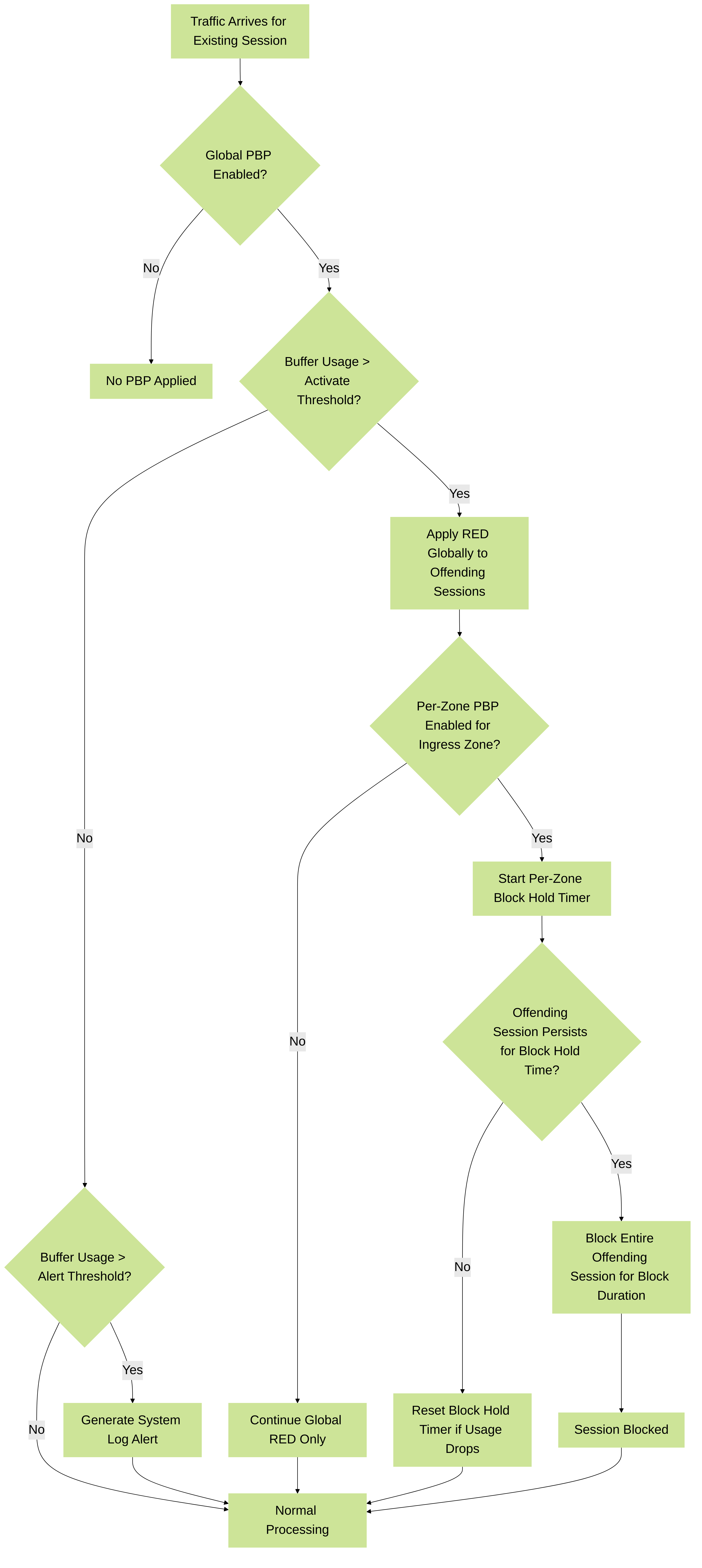
Illustrates the process for Packet Buffer Protection based on buffer utilization, showing global actions (alert, RED) and per-zone actions (block hold, block session).
Packet Buffer Protection Flow (Latency Based)
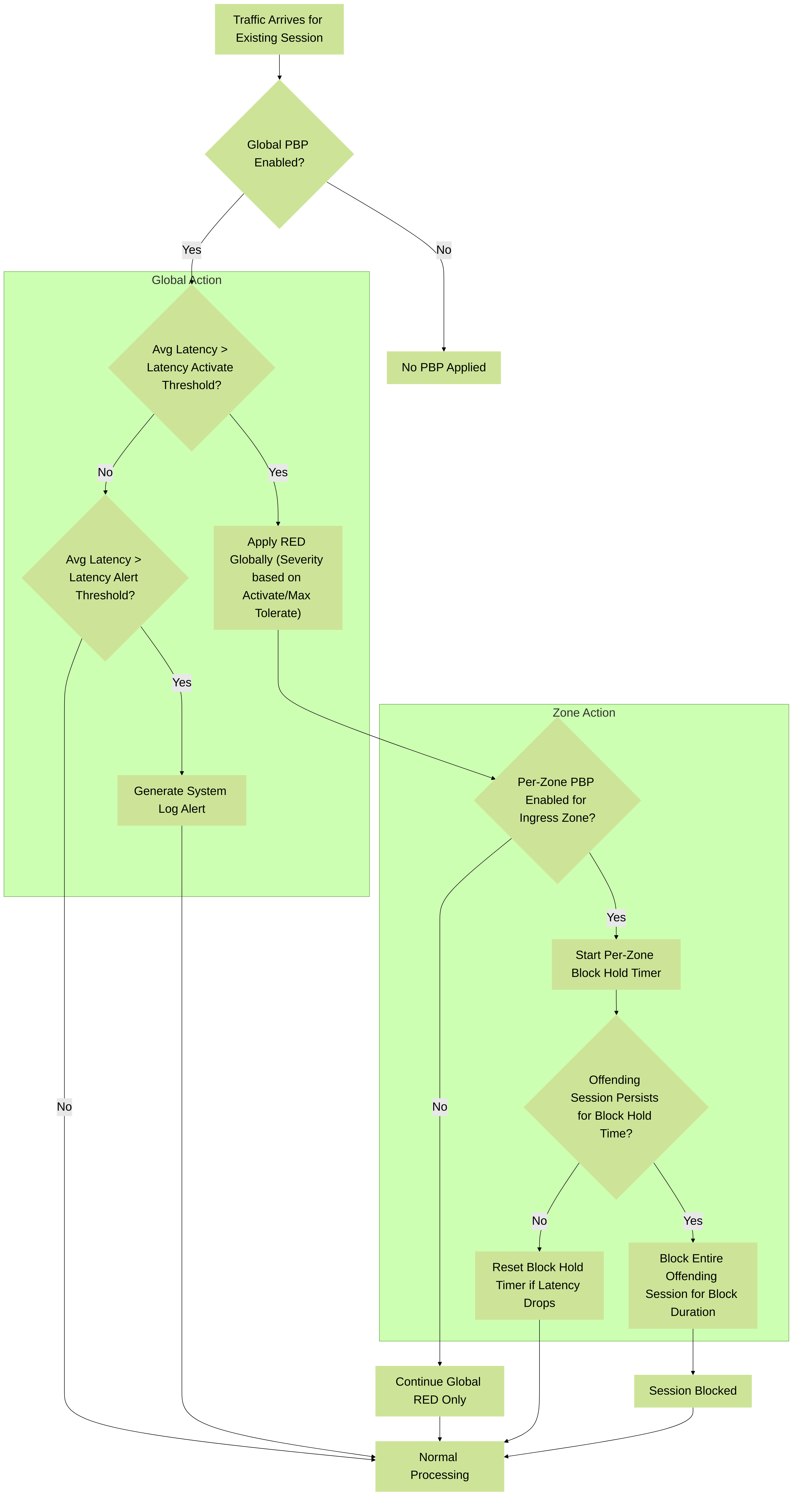
Illustrates the process for Packet Buffer Protection based on packet latency, showing global actions (alert, RED) and per-zone actions (block hold, block session).
Packet Buffer Protection Quiz
Test your understanding of Packet Buffer Protection. Select the best answer for each question.