HTTP Header Insertion with User-ID on Palo Alto Networks
Palo Alto Networks Next-Generation Firewalls (NGFWs) offer a powerful feature allowing the injection of user identity information, specifically the username and domain name derived from the User-ID feature, directly into HTTP headers of web requests passing through the firewall.
This mechanism enables downstream web servers, proxies, or other applications to gain visibility into the identity of the user initiating the request without needing direct integration with the organization's authentication systems or the firewall's User-ID mappings themselves. This article explores the concepts, configuration, use cases, troubleshooting, and security considerations surrounding this feature, tying it directly to objectives relevant for the Palo Alto Networks Certified Network Security Engineer (PCNSE) certification.
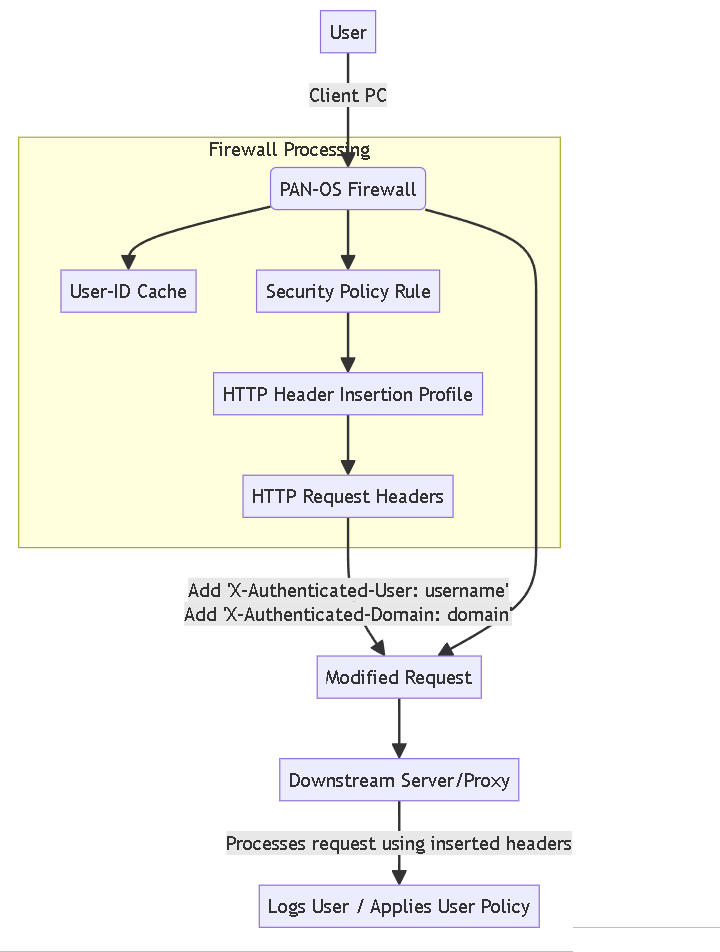
High-level flow of HTTP Header Insertion based on User-ID.
Core Concepts - What is HTTP Header Insertion?
HTTP (Hypertext Transfer Protocol) uses headers within its request and response messages to convey metadata about the transaction. These headers are typically key-value pairs (e.g., `User-Agent: Chrome/120...`).
HTTP Header Insertion on a PAN-OS firewall is the process where the firewall intercepts an outgoing HTTP request that matches a specific Security Policy rule, identifies the user associated with the request's source IP via User-ID, and adds one or more custom HTTP headers containing this user identity information (like username and/or domain) before forwarding the request to its final destination.
Essentially, the firewall acts as an intermediary that enriches the request with context it uniquely possesses.
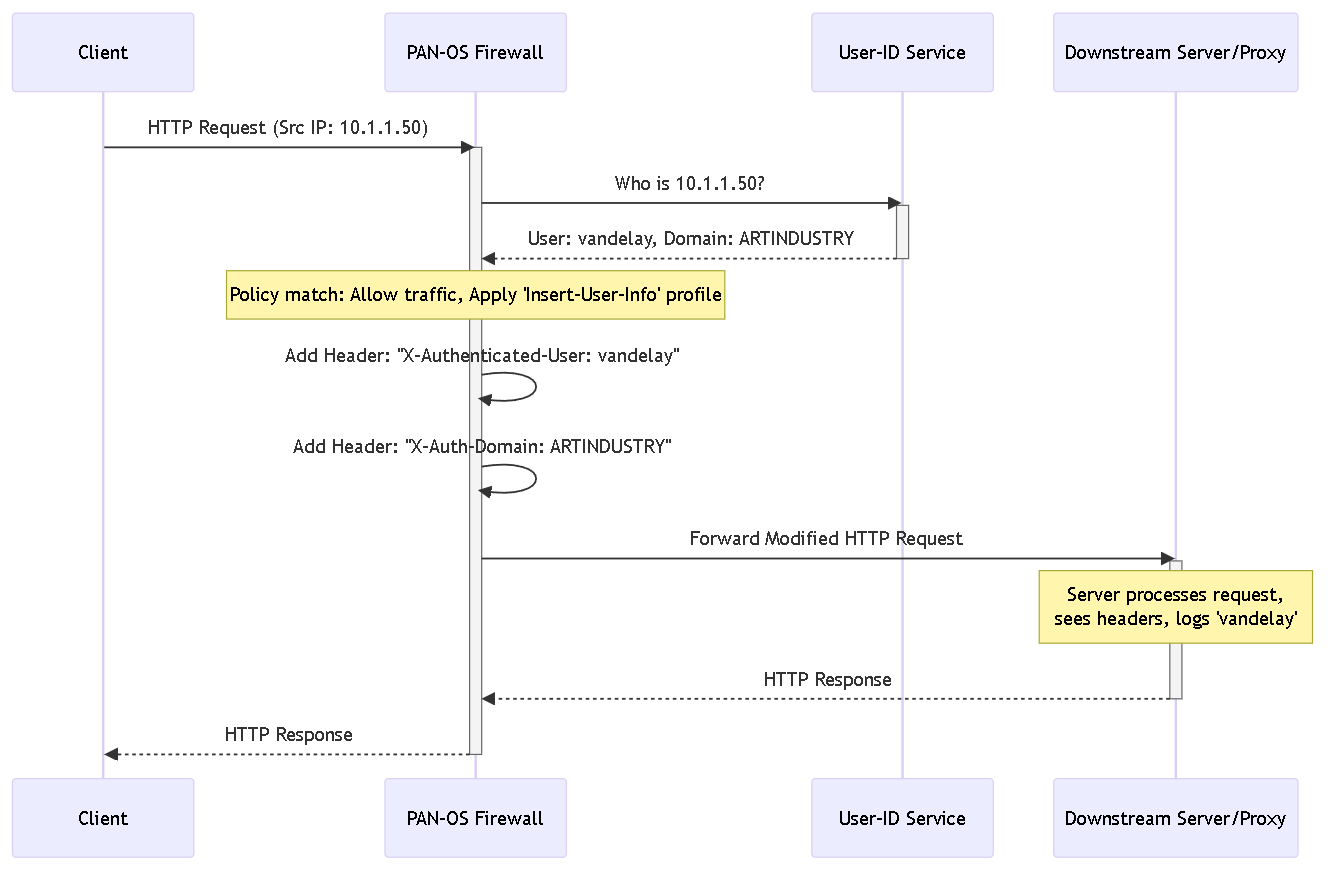
Sequence diagram showing firewall intercepting, looking up User-ID, and inserting headers.
Core Concepts - Why Use HTTP Header Insertion? (Use Cases)
This feature bridges the gap between the firewall's user awareness and the needs of downstream systems:
- Enhanced Logging: Web servers or proxies can log the actual username alongside the source IP, providing much clearer audit trails than IP addresses alone.
- User-Based Policy on Downstream Devices: Enables upstream proxies (like cloud-based web filters) or internal applications to enforce user-specific or group-specific policies, even if they cannot perform User-ID lookups themselves. The PAN-OS firewall essentially delegates the user identification part.
- Application Personalization/Context: Internal web applications can read the inserted headers to tailor content or functionality based on the identified user without implementing their own complex authentication integration.
- Integration with Content Filters: Allows third-party content filtering solutions (especially cloud services where traffic is forwarded from PAN-OS) to apply policies based on the username provided by the firewall.
- Simplified Reporting: Consolidates user information into logs generated by various systems (firewall, proxy, web server), simplifying reporting and analysis.
Scenario Example
A company uses a cloud-based web security service. Users' web traffic goes through the internal PAN-OS firewall, which identifies users via User-ID, and then forwards the traffic to the cloud service. By configuring HTTP Header Insertion on the PAN-OS firewall to add the `X-Authenticated-User` header, the cloud service can read this header and apply specific web filtering rules based on the user's department or role, information it wouldn't otherwise have easily.
Core Concepts - The Role of User-ID
HTTP Header Insertion for username and domain is **entirely dependent** on a functional Palo Alto Networks User-ID deployment. User-ID is the mechanism by which the firewall maps dynamic IP addresses to static user identities.
How User-ID Feeds Header Insertion:
- Mapping Collection: The firewall gathers IP-to-User mappings from various sources (Domain Controller monitoring via Agent/Agentless, Captive Portal, GlobalProtect, Syslog, API, etc.).
- Mapping Storage: These mappings (IP <-> User, Domain, Groups) are stored locally on the firewall's dataplane.
- Lookup on Traffic: When an HTTP request hits the firewall, it checks the source IP against its User-ID cache.
- Data Retrieval: If a match is found, it retrieves the associated username and domain.
- Conditional Insertion: If the Security Policy rule matching the traffic has an HTTP Header Insertion profile configured for user/domain, the firewall uses the retrieved data to populate and insert the headers.
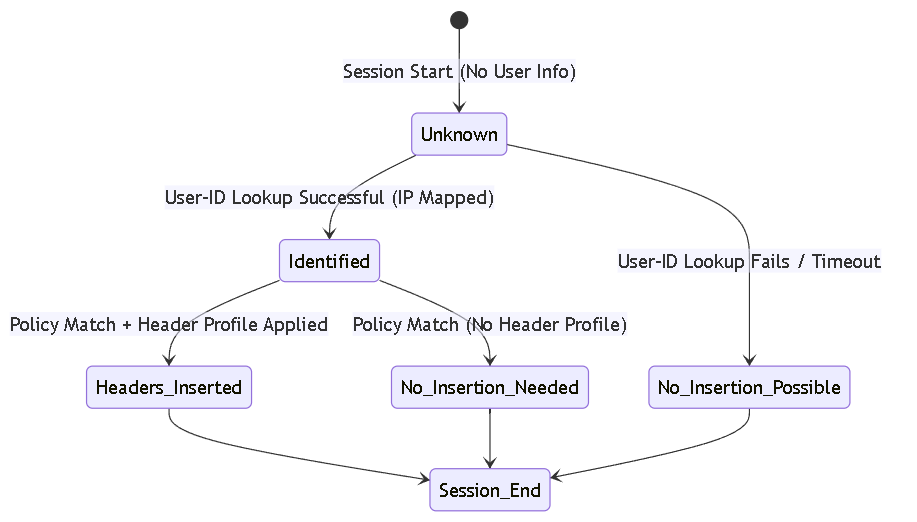
State diagram illustrating the dependency on User-ID identification for header insertion.
Configuration - Prerequisites
Before configuring HTTP Header Insertion for username and domain, ensure these are in place:
-
Functional User-ID:
- User-ID configured and successfully mapping IPs to users for the relevant subnets.
-
Verify using CLI (`show user ip-user-mapping all` or `show user ip-user-mapping ip
`) or GUI (Monitor > Logs > User-ID / Monitor > User-ID Monitoring). - Crucial: No User-ID mapping = No header insertion.
- Relevant Traffic Flow: The HTTP/HTTPS traffic must transit the PAN-OS firewall where User-ID is active and the policy will be applied.
- Matching Security Policy Rule: An existing or new Security Policy rule must match the intended traffic (based on source zone, destination zone, address, user, application, service). This rule will have the header insertion profile attached.
-
SSL Forward Proxy Decryption (for HTTPS):
- If you need to insert headers into HTTPS traffic, decryption is **mandatory**.
- The firewall cannot modify encrypted traffic without decrypting it first.
- Ensure an appropriate Decryption Policy rule or profile is configured and applied to decrypt the relevant HTTPS sessions.
- Gotcha! Forgetting decryption is the #1 reason header insertion fails for HTTPS sites.
Configuration - Creating the HTTP Header Insertion Profile
The profile defines *what* headers to insert and *which* destination domains should trigger the insertion.
Steps (GUI):
- Navigate to Objects > Security Profiles > HTTP Header Insertion .
- Click Add .
- Name: Enter a descriptive name (e.g., `Profile-Insert-UserDomain`).
-
Select the
User-Agent
tab.
Gotcha! Yes, Username/Domain insertion is configured under the 'User-Agent' tab, not a more intuitively named one. Remember this!
-
Domains:
Define for which destination domains headers should be inserted.
- Add `*` (wildcard) to insert for **any** domain (common for general proxy/filter integration).
- Add specific domains (e.g., `myapp.internal.corp`) to limit insertion to requests for those hosts only.
- Click Add for each entry.
-
Headers:
Click
Add
in the Headers section to define each header to insert.
- Name: The name of the HTTP header (e.g., `X-Authenticated-User`, `X-User-Domain`, `PANW-Identity`). Use names the downstream system expects. The `X-` prefix is a common convention.
-
Type:
Select the data source/format:
- `Username`: Inserts the bare username (e.g., `vandelay`).
- `Domain`: Inserts the domain name (e.g., `ARTINDUSTRY`).
- `User@Domain`: Inserts `username@domain` format (e.g., `vandelay@artindustry.com`).
- `Domain\User`: Inserts `DOMAIN\username` format (e.g., `ARTINDUSTRY\vandelay`).
- Repeat adding headers as needed (e.g., one for Username, one for Domain).
- Click OK .
Configuration - Applying the Profile to a Security Policy Rule
A profile does nothing until applied to traffic via a Security Policy rule.
Steps (GUI):
- Navigate to Policies > Security .
- Locate or create the rule matching the traffic needing header insertion (e.g., `Trust` zone users going to `Untrust` zone web servers).
- Click the rule name to edit it.
- Go to the Actions tab.
-
Under
Profile Setting
:
- Ensure Type is `Profiles`.
- In the HTTP Header Insertion dropdown, select the profile you created (e.g., `Profile-Insert-UserDomain`).
- (If HTTPS) Decryption Setting: Ensure the rule's Action is `Allow` and `Decrypt`, OR ensure a separate Decryption policy rule matches and decrypts this traffic. If the session is not decrypted, insertion for HTTPS fails.
- Click OK .
- Commit the changes to the firewall.
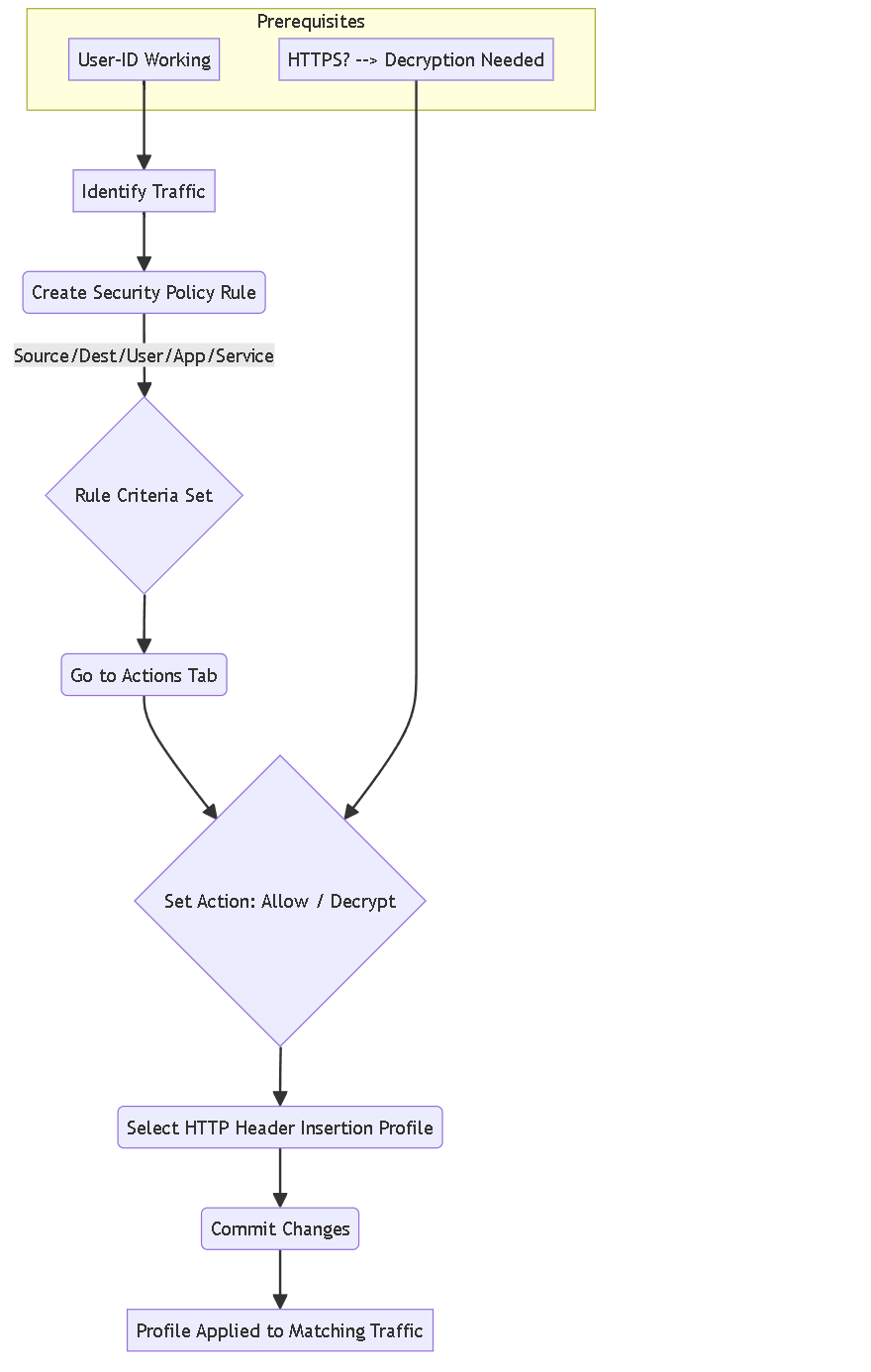
Flowchart applying the profile to a Security Policy rule.
Configuration - Verification
Always verify the configuration works as expected.
Methods:
-
Downstream Server/Proxy Logs:
**(Most Common & Reliable)**
- Check the access logs on the web server or proxy receiving the traffic.
- Configure the server/proxy logging format to include the custom headers (e.g., `%req{X-Authenticated-User}i` in Apache).
- Confirm the username/domain appears in logs for requests from identified users.
-
Packet Captures (Firewall):
**(Definitive Firewall Check)**
- Monitor > Packet Capture.
- Capture on the **egress** interface (`transmit` stage) for the traffic.
- Filter by source/destination IP and port (80/443).
- Analyze the capture in Wireshark. Inspect the HTTP request headers for the custom headers. (Requires decryption for HTTPS).
-
Packet Captures (Server-Side):
- Run Wireshark/tcpdump on the destination server.
- Check incoming HTTP requests for the headers. Confirms they traverse the network.
-
Firewall Logs (Indirect Confirmation):
- Check Traffic logs: Ensure the session hits the correct rule, action is Allow/Decrypt, and User-ID is correctly identified.
- Check Decryption logs (if HTTPS): Ensure successful decryption.
- These logs don't show the headers themselves but confirm prerequisites.
- Browser Developer Tools: Generally **not** useful for verifying *firewall-inserted* headers, as the browser sends the request *before* the firewall modifies it. Only useful if the server echoes headers back, which is rare.
Advanced Topics & PCNSE - Header Naming & Formats
Flexibility exists, but coordination is key.
Header Names:
- Standard Practice: Using the `X-` prefix (e.g., `X-Authenticated-User`, `X-Client-Username`) is common for custom headers to avoid conflict with standard HTTP headers, although RFC 6648 deprecated the "experimental" meaning of `X-`. It remains widely used and understood for this purpose.
- Custom Names: You can use names without `X-` (e.g., `MyAppUser`), but ensure they don't clash with standard headers (`Host`, `Authorization`, etc.).
- Coordination: **Crucially, the header name configured on the PAN-OS firewall MUST match what the downstream system is configured to read.** Consult the downstream system's documentation.
Data Formats (Recap):
Choose the 'Type' in the profile based on downstream needs:
-
Username:vandelay -
Domain:ARTINDUSTRY -
User@Domain:vandelay@artindustry.com(UPN format) -
Domain\User:ARTINDUSTRY\vandelay(NetBIOS format)
Advanced Topics & PCNSE - Security Implications
Inserting user identity information requires careful consideration:
- Information Disclosure: Sending internal usernames/domains, especially to external destinations (internet), leaks internal directory structure information. Attackers could potentially harvest this via sniffing (if not HTTPS) or compromising the downstream system.
- Scope: Applying insertion broadly (to all domains via `*`, on general internet rules) increases risk exposure significantly.
- Trust: You are inherently trusting the downstream system to handle the provided identity information securely.
Mitigation Strategies:
- Limit Scope: Apply header insertion profiles **only** to rules governing traffic to specific, trusted downstream systems that require it. Use specific destination IPs/FQDNs or Custom URL Categories in policies.
- Use Specific Domains: In the profile's 'Domains' list, specify only the FQDNs of the trusted downstream systems instead of `*`.
- Mandate HTTPS & Decryption: Protect data in transit. Ensure end-to-end encryption by using SSL Forward Proxy Decryption on the firewall.
- Least Privilege: Only insert the specific information needed (e.g., just username if domain isn't required).
- Audit Regularly: Review policies using header insertion periodically.
Advanced Topics & PCNSE - Compatibility Issues
Ensure downstream systems can handle the inserted headers:
- Header Recognition: The downstream application/proxy MUST be configured to read and understand the specific custom header names you are inserting.
- Format Expectation: The format (`username`, `user@domain`, etc.) must match what the downstream system expects to parse.
- Intermediate Devices: Other proxies or load balancers between the firewall and the final destination might strip or modify custom headers. Ensure they are configured for pass-through if necessary.
- Header Size/Limits: Extremely long usernames/domains combined with many other headers could theoretically hit server/proxy limits, though this is rare.
- Case Sensitivity: While header names are case-insensitive, values might be treated as case-sensitive by the application. User-ID usually preserves case from the directory.
Advanced Topics & PCNSE - Troubleshooting
Systematically check potential points of failure:
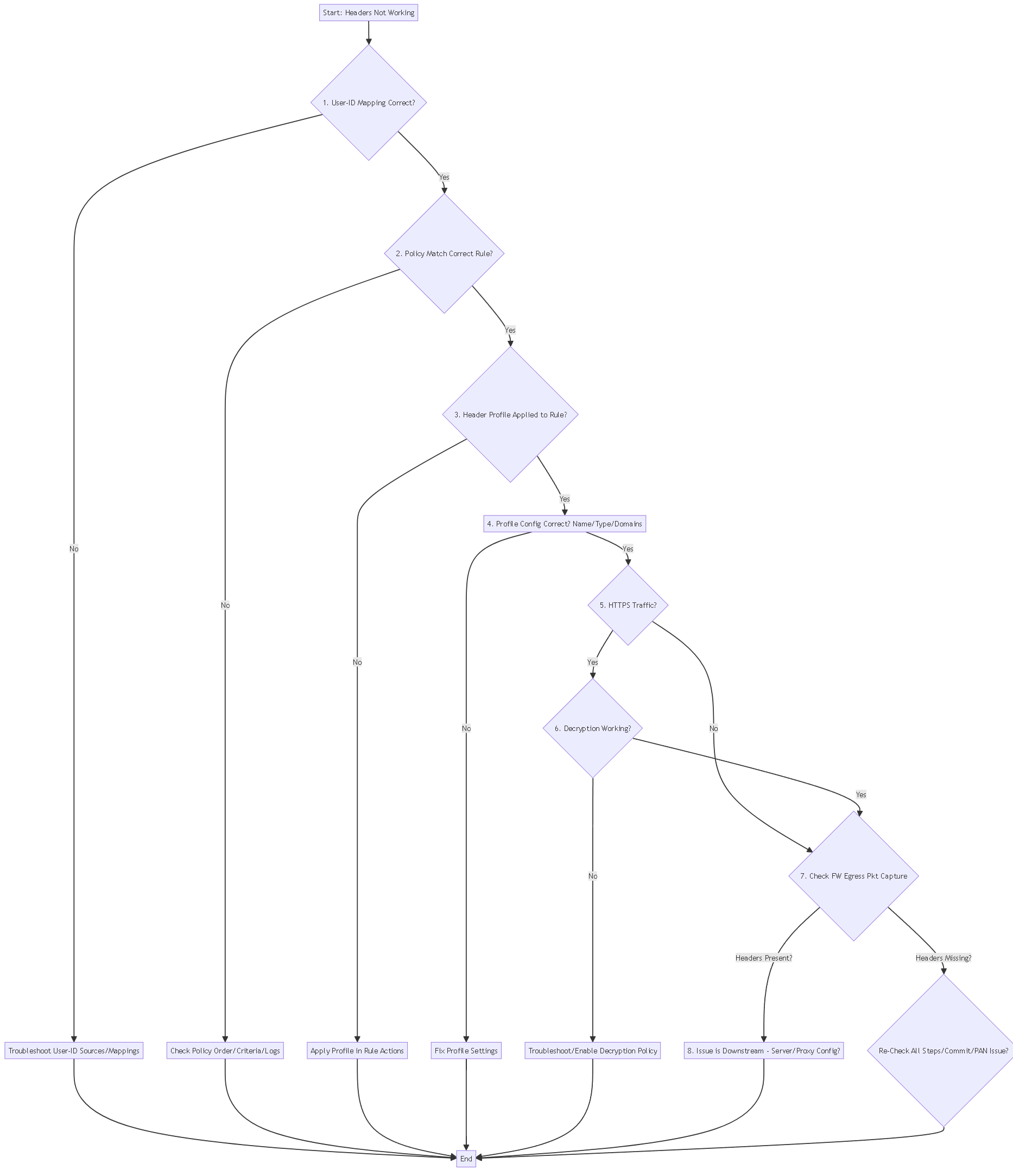
Troubleshooting flowchart for HTTP Header Insertion.
Key Checks:
-
User-ID:
`show user ip-user-mapping ip
`, Monitor logs. Is the user mapped *at the time of the request*? - Policy Match: Traffic logs. Correct rule hit? User-ID shown in log? Action Allow/Decrypt?
- Profile Application: Edit the Security rule -> Actions tab. Is the profile selected?
- Profile Configuration: Objects > Security Profiles > HTTP Header Insertion. Correct Names/Types? Correct Domains (or `*`)?
- HTTPS Decryption: Decryption logs. Is the session decrypted successfully? If not, insertion fails for HTTPS.
- Packet Captures: Firewall egress (`transmit` stage) or Server ingress. Definitive check.
- Downstream System: Is the server/proxy configured to read the *exact* header name? Check its logs/config.
- Commit: Were changes committed?
Advanced Topics & PCNSE - PCNSE Exam Relevance Summary
Understanding HTTP Header Insertion touches upon several key PCNSE domains:
- Core Concepts & Policies: Understanding Security Policy rules, Security Profiles, policy evaluation logic, and how profiles like HTTP Header Insertion are applied (Actions tab).
- User-ID: Deep understanding of User-ID sources (Agent, Agentless, CP, GP, etc.), mapping verification (`show user ip-user-mapping`), timeouts, and troubleshooting is essential due to the feature's direct dependency.
- SSL Decryption: Recognizing the mandatory requirement for decryption for HTTPS traffic links this to SSL Forward Proxy configuration, Decryption policies, certificate management, and troubleshooting decryption failures (common exam topics).
- Troubleshooting: The entire process of diagnosing failures (checking User-ID, policy hits, profile config, decryption, using logs, CLI commands, packet captures) aligns directly with the PCNSE troubleshooting domain.
- Security Best Practices: Evaluating the security implications (information disclosure) and applying mitigation strategies (limiting scope, using HTTPS) relates to designing secure solutions.
- Integration Scenarios: Understanding use cases, like integrating with upstream proxies or cloud filters, demonstrates practical application knowledge.
Quiz: HTTP Header Insertion with User-ID
Test your understanding of Palo Alto Networks HTTP Header Insertion.