Configure BGP in a GRE over IPSec
Objective
Configure BGP in a GRE over IPSec to establish peering between endpoints
Environment
-
Palo Alto Firewalls
-
PANOS- 9.1 and above
-
BGP configuration
-
GRE over IPSEC tunnel using loopback
Procedure
-
Configure GRE over IPsec using loopback
-
Configure IP address to GRE tunnel interface, in our example we are assigning IP address 172.16.2.1 for the local firewall and 172.16.2.2 for the remote side.
-
Navigate to Network > Interfaces > Tunnel
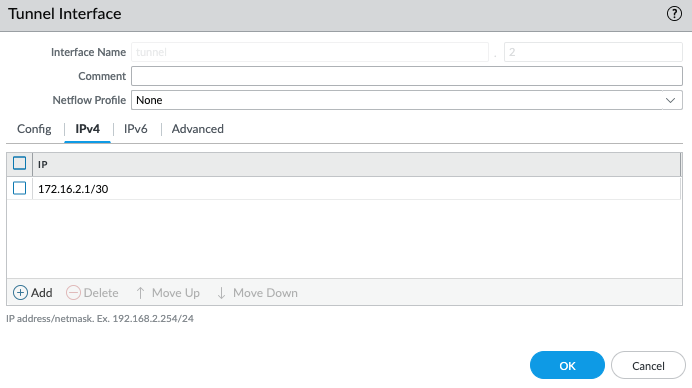
-
Configure BGP on a firewall by using GRE interface for BGP neighborship, navigate to Network > Virtual Routers > Default > BGP >
-
Enable BGP, set the AS number (using AS as 65201 and remote as 65200), and provide router ID
-
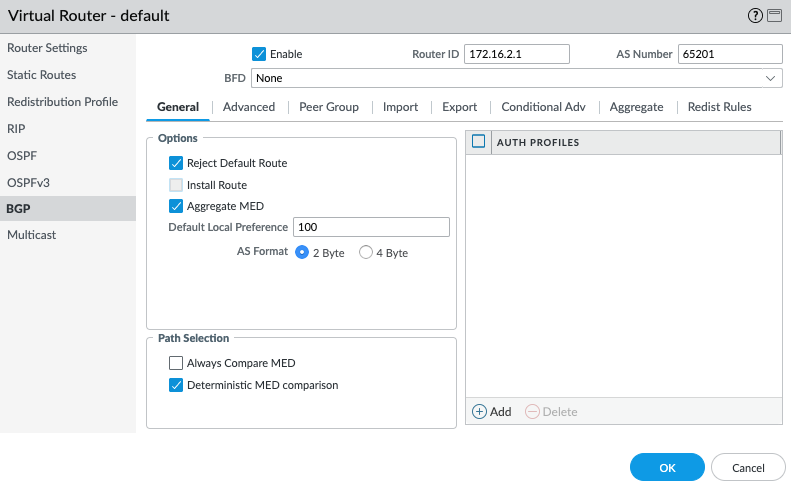
-
Navigate to Peer Group > Add > Provide name and click add, give it a name, and select Peer AS 65200 and local address Interface as GRE tunnel interface which is a tunnel.2
-
In this example, select GRE interface IP as IP and enter remote peer IP address then click OK and commit.
-
Configure the other side accordingly.
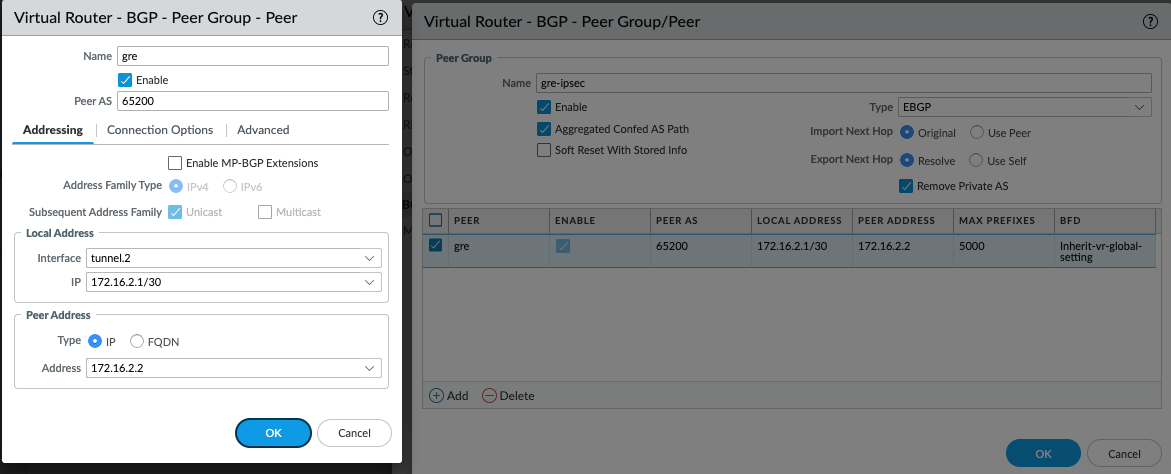
-
Verify BGP peering status by running command "show routing protocol bgp peer peer-name <name>"
adminn@PA-FW1> show routing protocol bgp peer peer-name gre
==========
Peer: gre (id 1)
virtual router: default
Peer router id: 172.16.2.2
Remote AS: 65200
Peer group: gre-ipsec (id 1)
Peer status: Established, for 2246 seconds
Password set: no
Passive: no
Multi-hop TTL: 1
Remote Address: 172.16.2.2:179
Local Address: 172.16.2.1:45127