Controlling LSVPN Satellite Connections with OCSP
Overview
The LSVPN implementation allows administrators to quickly connect VPN sites to the main site. The implementation relies on the usage of certificates to authenticate the satellites to the portal, which allows the administrators control who will be allowed access to the VPN network, and who can be denied if emergency action is needed.
Details
To accomplish full control, there needs to be a Certificate Authority(CA) on the Palo Alto Networks firewall, and OCSP responder for the certificates that we will generate with that CA. The process is very similar to controlling GlobalProtect Remote access VPN connections and similar principles are valid and similar steps should be followed.
Note: For more information reference the following link: Controlling GlobalProtect VPN Access with OCSP
-
Create a CA at the firewall
-
Create a local OCSP responder
-
Create a Certificate Profile that will be used to check the status of the certifications with the given OCSP
-
Create a certificate signed by the CA and include the OCSP responder to be checked for the revocation status of these certificates
-
Verify if the certificates are generated with the correct information when a satellite connects to GlobalProtect (this should include the correct Issuer)
-
Verify that the satellites can connect to the VPN network
-
If needed, revoke the satellite certificate from the gateway and remove this satellite information from portal so that the satellite device will not reconnect to the VPN network.
Steps
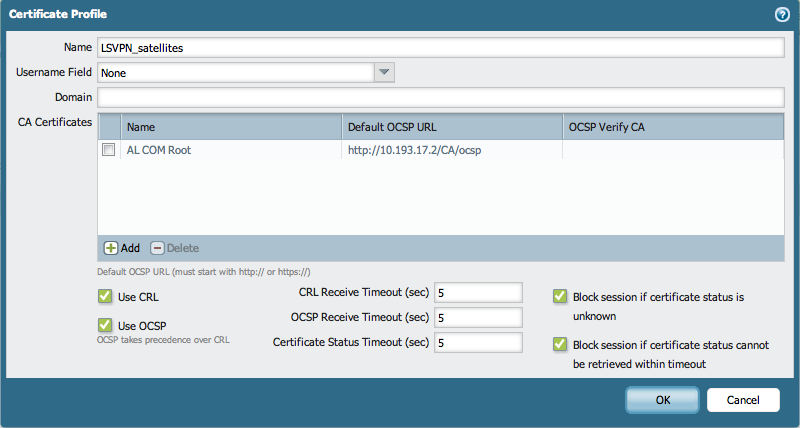
After the CA and the OSCP responder are in place on the firewall, create a Certificate Profile.
Note: Reference the following link for more information on: How to Configure an OCSP Responder
-
To create a Certificate Profile for the LSVPN satellites, which will be verifying the revocation status with the created OCSP, go to Device > Certificate Management > Certificate Profile .
-
GUI: Device > Certificate Management > Certificates and click Generate to create the certificate that will be used to sign the satellite certificates.
While creating the certificate, be sure to use the OCSP responder previously created. If this is an intermediate certificate, make sure to select the root CA that is trusted on the satellite. If the root is not trusted on the satellite, or this is a root certificate that is being creating now, be sure to export the certificate from this firewall and import it on the satellite firewall.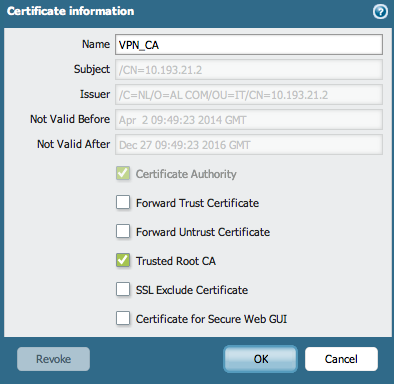
-
At this time, the configuration of the LSVPN needs to be completed. Please reference the Large Scale VPN (LSPV) Deployment Guide to complete the configuration.
While configuring the setup, make sure to use the appropriate certificates and certificate profiles previously created.
Include the trusted root CA and the OCSP responder in the Satellite Configuration under the GlobalProtect Portal, so the certificates are checked for the revocation status.
Use the Server Certificate and the Certificate Profile for the GlobalProtect Gateway, as shown below: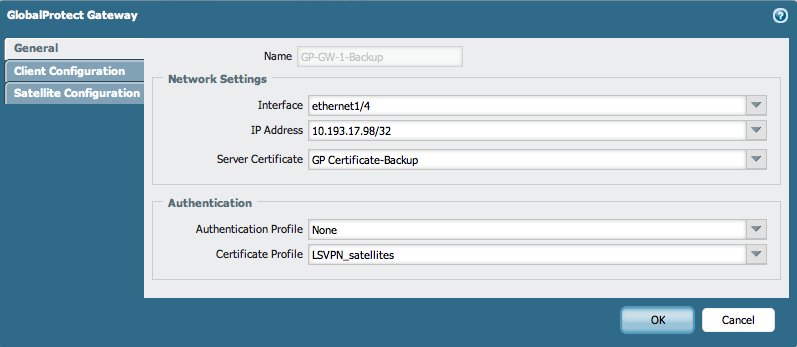
-
After the full LSVPN configuration is complete, verify if connections are establishing from the satellites to GlobalProtect.
Check the connection under Network > GlobalProtect > Portals . Under Info > click on Satellite Information: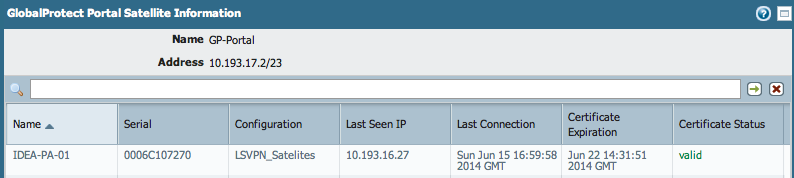
-
GUI: Network > GlobalProtect > Gateways . Under Info > click on Satellite Information to access details about the connection to the needed gateway:
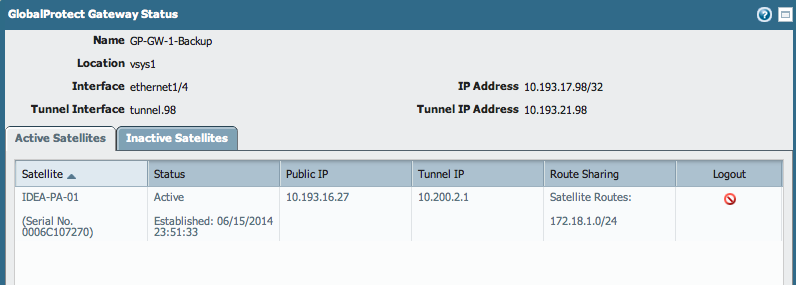
The certificate that is used for this process is actually created for the satellite, from the CA that has been specified in the previous steps. By default, the validity of these certificates is 7 days.
As shown below, see the issued certificate under Device > Certificate Management > Certificates :
-
Revoke this certificate by opening the certificate.
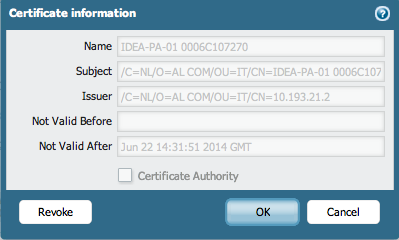
Once the Revoke button is clicked, the certificate is no longer valid and should not be accepted by the portal to establish connections to the VPN network:
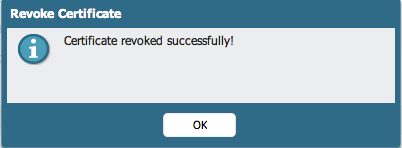
The status immediately changes to revoked:

From this point on, the connections from that satellite will be dropped, because of authentication with an invalid certificate. This can be viewed in the system logs, as shown below:

sslmgr.log displays the certificate revocation.
> less mp-log sslmgr.log Jun 16 00:51:58 pan_store_portal_cfg_assigned(pan_store_satellite_info.c:1854): find assigned serialno 0006C107270 Jun 16 00:51:58 pan_store_satellite_info_response_print(pan_store_satellite_info.c:106): {satellite info success; vsys id(1); vsys name(vsys1); portal name(GP-Portal);serialno(0006C107270); hostname(IDEA-PA-01); config(LSVPN_Satelites); pin(static); derived from(); last seen ip(10.193.16.27); } Jun 16 00:51:58 pan_store_certificate_info_find_expired_cert(pan_store_certificate_info.c:964): certificate(539DAE57002715) is revoked, don't cleanup Jun 16 00:51:58 pan_store_certificate_info_find_expired_cert(pan_store_certificate_info.c:973): certificate expiration date(Jun 22 22:51:01 2014 GMT) Jun 16 00:51:58 pan_store_certificate_info_find_expired_cert(pan_store_certificate_info.c:979): current date (Jun 15 22:51:58 2014 GMT) Jun 16 00:51:58 pan_store_certificate_info_find_expired_cert(pan_store_certificate_info.c:981): expdate(140622225101Z) curdate(140615225158Z) Jun 16 00:51:58 pan_store_certificate_info_find_expired_cert(pan_store_certificate_info.c:984): exp date(3183271629) curwarmingdate(3176271686) Jun 16 00:51:58 pan_store_is_cert_expired(pan_store_certificate_info.c:70): certificate expiration date(Jun 22 22:51:01 2014 GMT)(140622225101Z) Jun 16 00:51:58 pan_store_is_cert_expired(pan_store_certificate_info.c:77): current date plus warming days (Jun 18 22:51:58 2014 GMT)(140618225158Z) Jun 16 00:51:58 sslmgr_sysd_store_cert_gen(sslmgr_sysd.c:469): certificate is still valid Jun 16 00:51:58 pan_store_satellite_info_request_print(pan_store_satellite_info.c:75): {satellite info find; vsys id(1); vsys name(vsys1); portal name(GP-Portal); seria lno(0006C107270); hostname(); config(); pin(); derived from(); last seen ip(); } Jun 16 00:51:58 pan_store_portal_cfg_assigned(pan_store_satellite_info.c:1854): find assigned serialno 0006C107270 Jun 16 00:51:58 pan_store_satellite_info_response_print(pan_store_satellite_info.c:106): {satellite info success; vsys id(1); vsys name(vsys1); portal name(GP-Portal);serialno(0006C107270); hostname(IDEA-PA-01); config(LSVPN_Satelites); pin(static); derived from(); last seen ip(10.193.16.27); } Jun 16 00:52:14 [OCSP] URL (null) serialno: 539E235500032C Jun 16 00:52:14 Send cookie:4 session:0 status:2 to DPAfter revocation, a connection can not be established any more:
> show global-protect-gateway current-satellite GlobalProtect Gateway: GP-GW-1 (0 satellites) Tunnel Name : GP-GW-1-S GlobalProtect Gateway: GP-GW-1-Backup (0 satellites) Tunnel Name : GP-GW-1-Backup-S > show global-protect-gateway previous-satellite GlobalProtect Gateway: GP-GW-1 (0 satellites) Tunnel Name : GP-GW-1-S GlobalProtect Gateway: GP-GW-1-Backup (0 satellites) Tunnel Name : GP-GW-1-Backup-S Satellite : 0006C107270 Satellite Hostname : IDEA-PA-01 Private IP : 10.200.2.1 Public IP : 10.193.16.27 Satellite Tunnel IPs : Login Time : Jun.15 23:51:33 Logout Time : Jun.16 00:51:34 Reason : Tunnel Lifetime expired Satellite Published Routes: 172.18.1.0/24 Satellite Denied Routes : Satellite Duplicate Routes: Tunnel Monitor Enabled : Yes Tunnel Monitor Interval : 3 seconds Tunnel Monitor Action : fail-over Tunnel Monitor Threshold : 5 attempts Tunnel Monitor Source : 10.193.21.98 Tunnel Monitor Destination: 10.200.2.1 Tunnel Monitor Status : No data available -
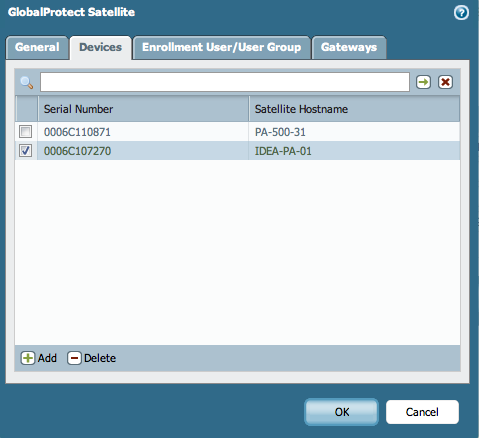
The satellite must be permanently removed from the GlobalProtect Portal Satellite configuration. This means the portal does not have to try to validate the certificate.
To delete, GUI: Network > GlobalProtect > Portals > Satellite Configuration , select the satellite, and delete it from the list: