Comprehensive Guide to PAN-OS IPSec VPN Components
IPSec (Internet Protocol Security) is a suite of protocols used to secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session. Palo Alto Networks firewalls implement robust IPSec VPN capabilities, primarily using a route-based approach. This guide details the essential components configured in PAN-OS to establish and manage IPSec VPN tunnels.
Understanding these components is crucial for building secure site-to-site or remote access connections and is a core topic for the PCNSE certification.
IPSec VPN Fundamentals: Two Phases
An IPSec VPN connection is established in two distinct phases:
- Phase 1 (IKE - Internet Key Exchange): Establishes a secure, authenticated channel between the two VPN peers (gateways). Its main purpose is to negotiate security parameters and generate shared secret keys for protecting the Phase 2 negotiation. This is often called the IKE Security Association (IKE SA) or Management Connection.
- Phase 2 (IPSec): Uses the secure channel created in Phase 1 to negotiate parameters specifically for encrypting and authenticating the actual user data that will flow through the VPN tunnel. Multiple Phase 2 SAs (IPSec SAs) can exist under a single Phase 1 SA, typically one pair (inbound/outbound) for each defined network pair (Proxy ID).
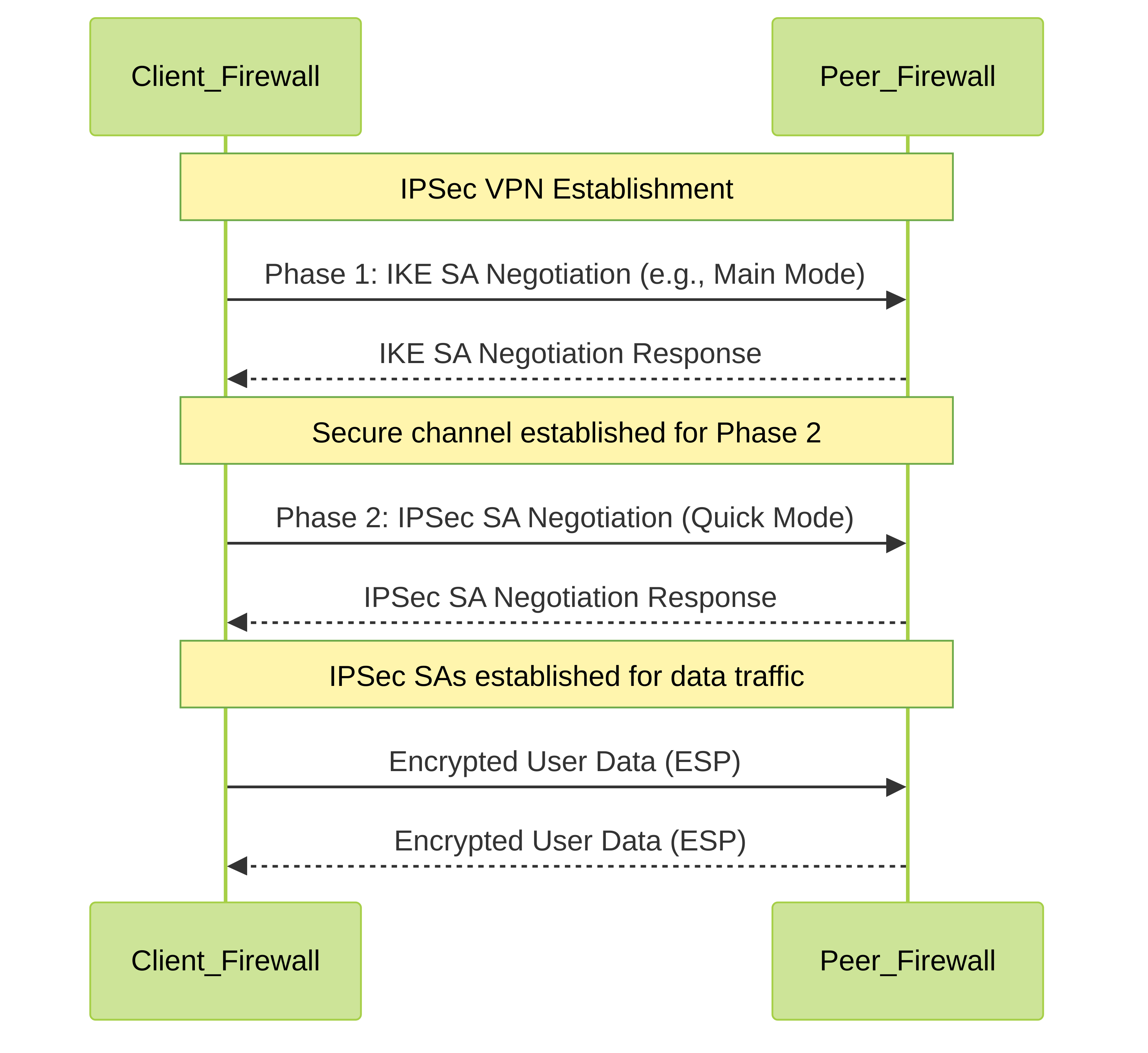
High-level overview of IPSec VPN Phase 1 and Phase 2 establishment.
Phase 1 (IKE) Components: IKE Gateway
The IKE Gateway object defines the parameters for establishing the Phase 1 connection with the remote peer firewall.
Key Configuration Settings:
- Name: A unique identifier for the gateway object.
-
Version:
-
IKEv1: Older version, still widely used. -
IKEv2: Preferred due to improved security, reliability (built-in keepalives/liveness check), and efficiency (fewer messages). -
IKEv2 preferred mode: Attempts IKEv2 first, falls back to IKEv1 if the peer doesn't support IKEv2.
IKEv2 offers several advantages over IKEv1, including built-in NAT traversal, support for EAP authentication, and greater resilience to network changes (MOBIKE). -
- Address Type: IPv4 or IPv6.
- Interface: The external-facing physical or logical interface on the firewall where VPN traffic originates/terminates.
- Local IP Address: The specific IP address on the selected interface to use for IKE negotiation. This is typically the public IP of the firewall.
-
Peer IP Address Type:
StaticorDynamic(for peers with unknown/changing IP addresses). - Peer Address: The public IP address of the remote VPN gateway.
-
Authentication:
-
Pre-Shared Key (PSK): A secret string known only to the two peers. Simple but less scalable/secure than certificates. Keys must match exactly on both peers. -
Certificate: Uses digital certificates for authentication. More secure and scalable, requires a PKI (Public Key Infrastructure) setup.
-
-
Local Identification & Peer Identification:
How the firewall identifies itself and expects the peer to identify itself. Options include IP address, FQDN (domain name), User FQDN (email format), or Key ID (ASN.1 DN for certificates).
These *must match* or be acceptable to the peer's configuration on both sides. Mismatches are a common cause of Phase 1 failures. If left as 'None', the IP address of the local/peer gateway is typically used.
IKEv1 Specific Settings:
-
Exchange Mode:
-
Main Mode: (6 messages) Protects identities but is slower. -
Aggressive Mode: (3 messages) Faster but exposes identities; generally less secure. Sometimes needed for dynamic peers or specific clients. -
Auto: Typically defaults to Main Mode. Palo Alto Networks recommends Main Mode.
-
IKEv2 Specific Settings:
- Liveness Check (DPD): Enable Dead Peer Detection (DPD) to detect if the peer is unresponsive. Configure interval and retry values. IKEv2 has this built-in (often just called Liveness Check).
-
NAT Traversal:
Enable if a NAT device exists between the VPN peers. This encapsulates IKE/ESP traffic within UDP port 4500.
NAT Traversal should be enabled when either VPN peer is behind a device performing NAT. This changes the port for IKE from UDP 500 to UDP 4500 after initial contact.
- Enable Passive Mode: Forces the firewall to only respond to IKE connections and never initiate them.
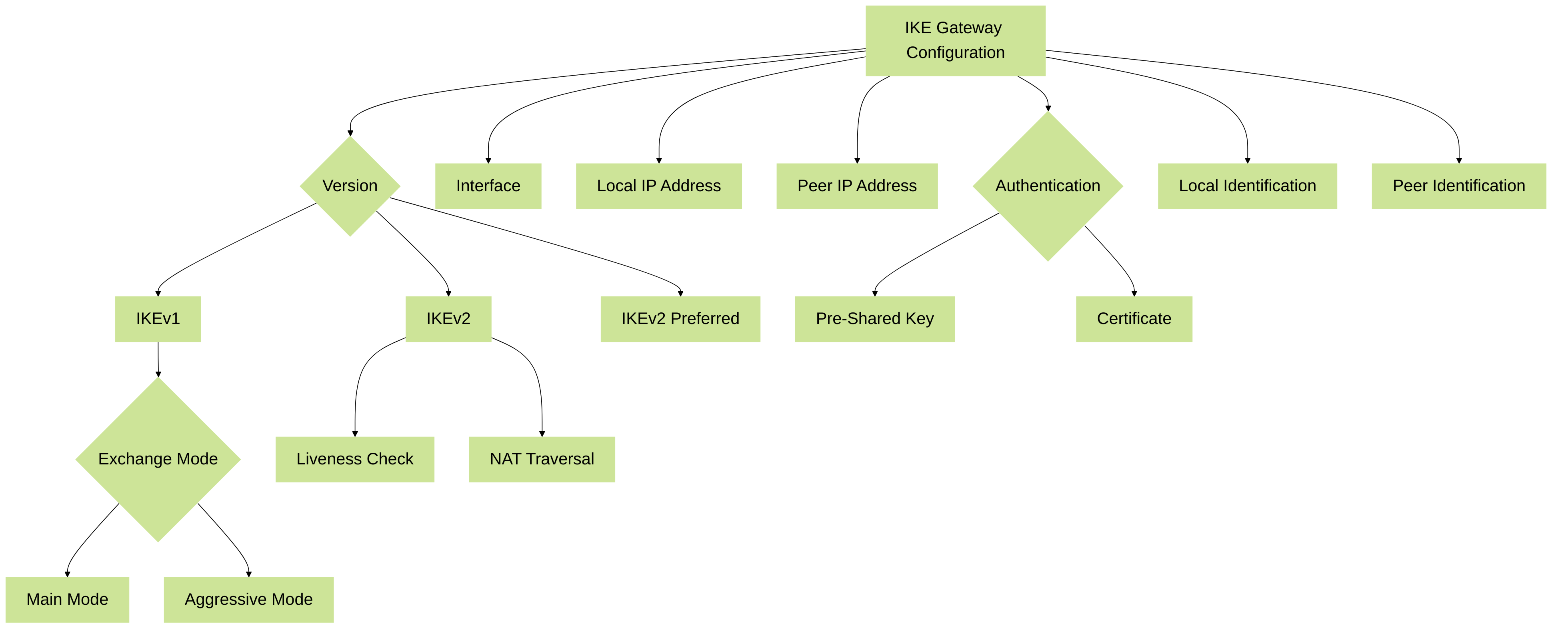
Key parameters for IKE Gateway configuration.
Phase 1 (IKE) Components: IKE Crypto Profile
This profile defines the cryptographic algorithms used to secure the Phase 1 (IKE SA) negotiation itself.
Key Configuration Settings:
- Name: A unique identifier for the profile.
- DH Group (Diffie-Hellman): Specifies the strength of the key exchange process. Higher groups (e.g., group 14, 19, 20, 21) are more secure. Both peers must support and agree on at least one common group. Multiple can be selected for negotiation.
- Authentication: Hashing algorithm used for message integrity (e.g., SHA1, SHA256, SHA384, SHA512). Stronger algorithms like SHA256 or higher are recommended.
- Encryption: Algorithm used to encrypt the Phase 1 negotiation (e.g., DES, 3DES, AES-128-CBC, AES-192-CBC, AES-256-CBC, AES-128-GCM, AES-256-GCM). AES (especially GCM variants which combine encryption and authentication) is strongly recommended.
- Lifetime: How long the Phase 1 SA remains valid before it must be renegotiated (e.g., 8 hours, 24 hours). Shorter lifetimes increase security but also overhead. Common default is 28800 seconds (8 hours).
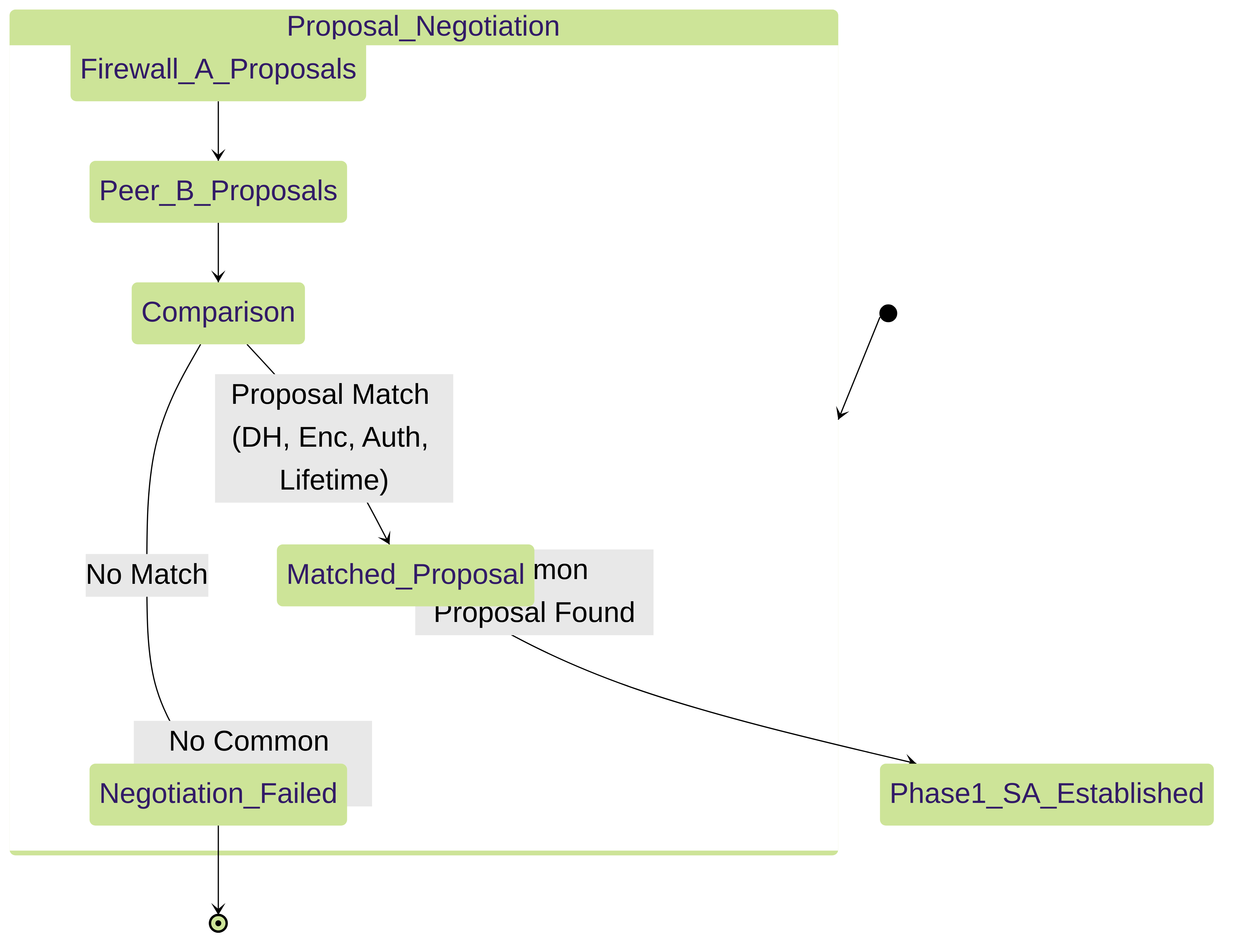
IKE Crypto Profile proposal negotiation leading to Phase 1 SA.
Phase 2 (IPSec) Components: IPSec Crypto Profile
This profile defines the cryptographic algorithms used to secure the actual user data (Phase 2 / IPSec SA).
Key Configuration Settings:
- Name: A unique identifier for the profile.
-
IPSec Protocol:
-
ESP (Encapsulating Security Payload): Provides confidentiality (encryption) and authentication. Most common. -
AH (Authentication Header): Provides authentication only, no encryption. Rarely used. AH authenticates the entire IP packet, including parts of the IP header, which makes it incompatible with NAT. ESP authentication typically covers the IP datagram.
ESP is overwhelmingly preferred as it provides both encryption and authentication. AH is generally not used because it doesn't offer encryption and is incompatible with NAT. -
-
Encryption:
Algorithm used to encrypt user data (e.g., DES, 3DES, AES-128-CBC, AES-192-CBC, AES-256-CBC, AES-128-GCM, AES-256-GCM). A
nulloption provides authentication without encryption if needed (uncommon with ESP). AES (especially GCM) is strongly recommended. - Authentication: Hashing algorithm for data integrity (e.g., MD5, SHA1, SHA256, SHA384, SHA512). SHA256 or higher recommended.
-
DH Group (PFS - Perfect Forward Secrecy):
Optional but
highly recommended
. If enabled, forces a new Diffie-Hellman exchange for each Phase 2 rekey. This ensures that if a Phase 2 key is compromised, it cannot be used to decrypt previously captured traffic (even if the Phase 1 key was also compromised). Select a strong group (e.g., group14, 19, 20, 21).
If PFS is enabled on one peer, it must be enabled on the other, and they must agree on a DH group. Mismatched PFS settings will cause Phase 2 to fail.
- Lifetime: How long the Phase 2 SA remains valid before rekeying (e.g., 1 hour / 3600 seconds). Typically shorter than Phase 1 lifetime. Can also be specified in KBytes.
Phase 2 (IPSec) Components: Tunnel Interface
In PAN-OS's route-based VPN approach, a logical Tunnel Interface is created to represent the VPN connection endpoint on the firewall.
Key Configuration Settings:
- Interface Name: Logical name (e.g., tunnel.1, tunnel.10). Must be unique.
- Virtual Router: Assign the tunnel interface to a Virtual Router (e.g., default). This allows the firewall to route traffic towards the tunnel.
- Security Zone: Assign the tunnel interface to a Security Zone (e.g., VPN-Zone, Trust-VPN). This is crucial for Security Policy enforcement.
- IPv4/IPv6 Address (Optional): Assigning an IP address is often done for routing protocol peering (like BGP/OSPF) over the tunnel or for tunnel monitoring, but it's not strictly required for the tunnel to function if static routes are used and tunnel monitoring pings a remote IP.
-
MTU (Maximum Transmission Unit):
Can be adjusted if needed due to IPSec overhead, but default usually works. Palo Alto Networks may recommend specific MTU values like 1427 for some configurations.
IPSec adds overhead (ESP/AH headers, new IP header in tunnel mode). If the resulting packet exceeds the MTU of any link in the path, fragmentation can occur, or packets might be dropped if DF (Don't Fragment) bit is set. Adjusting TCP MSS (Maximum Segment Size) on the firewall can help prevent issues.
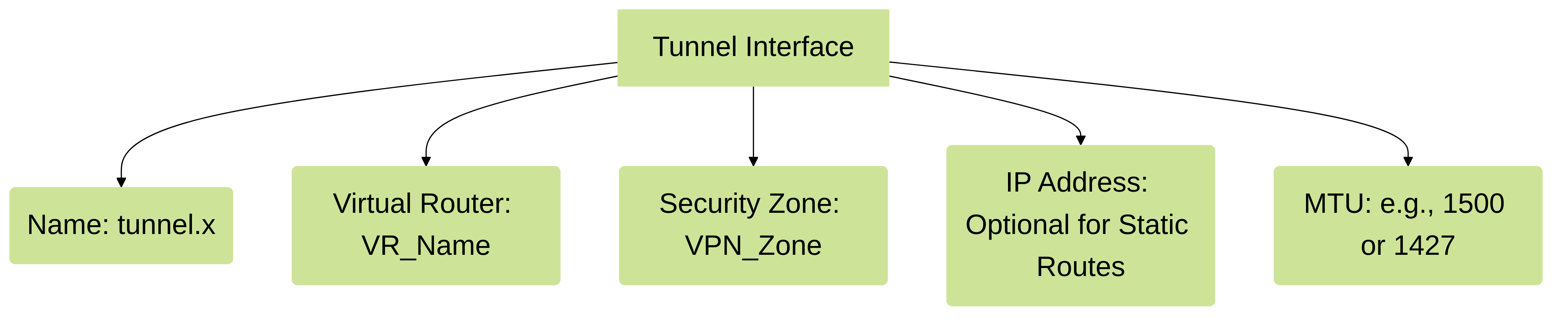
Key attributes of a Tunnel Interface.
Phase 2 (IPSec) Components: IPSec Tunnel (Proxy ID / Traffic Selector Configuration)
The IPSec Tunnel object ties together the IKE Gateway, IPSec Crypto Profile, and the logical Tunnel Interface. It also defines which traffic is allowed through the tunnel using Proxy IDs (also known as Traffic Selectors).
Key Configuration Settings:
- Name: A unique identifier for the IPSec tunnel configuration.
- Tunnel Interface: Select the logical tunnel interface created earlier (e.g., tunnel.1).
-
Type:
Auto Key(uses IKE) is standard. Manual Key is highly discouraged and generally not used. - IKE Gateway: Select the IKE Gateway object configured for the peer.
- IPSec Crypto Profile: Select the IPSec Crypto profile defining Phase 2 parameters.
-
Proxy IDs (Traffic Selectors):
This defines the specific local and remote networks that this IPSec SA will protect.
- Local Network(s): The source IP subnet(s) behind the Palo Alto Networks firewall.
- Remote Network(s): The destination IP subnet(s) behind the remote peer firewall.
- Protocol/Port (Optional): Can further restrict the SA to specific protocols/ports (rarely used in route-based VPNs unless connecting to specific policy-based peers).
PAN-OS Route-Based Default: Often configured with Local:0.0.0.0/0and Remote:0.0.0.0/0. In this case, the routing table and security policies determine what *actually* goes over the tunnel. This is typical for PAN-to-PAN or PAN-to-route-based peer configurations.Policy-Based VPN / Specific Needs: If connecting to a peer that requires specific network pairs (like a traditional policy-based VPN device) or if you need multiple SAs for different traffic types, you *must* configure specific, matching Proxy IDs on both ends.
Proxy IDs must be a "mirror image" on both peers. For example, if Firewall A has Local: 192.168.1.0/24 and Remote: 10.0.0.0/24, then Firewall B must have Local: 10.0.0.0/24 and Remote: 192.168.1.0/24.
Mismatched Proxy IDs are a very common cause of Phase 2 failures, often indicated by " IKE phase-2 negotiation failed when processing Proxy ID " messages in logs.PCNSE Exam Tip: Proxy IDs are critical. For route-based VPNs (PAN-OS default), 0.0.0.0/0 for local and remote is common. When connecting to a policy-based VPN peer, proxy IDs must be specific and be a mirror image of the peer's configuration. If traffic is NATed before entering the VPN, the Proxy ID should reflect the post-NAT IP addresses. - Tunnel Monitor (Optional): Allows the firewall to ping an IP address (typically the peer's tunnel interface IP or an internal IP behind the peer) across the tunnel to verify connectivity. Can trigger failover actions if the destination becomes unreachable.
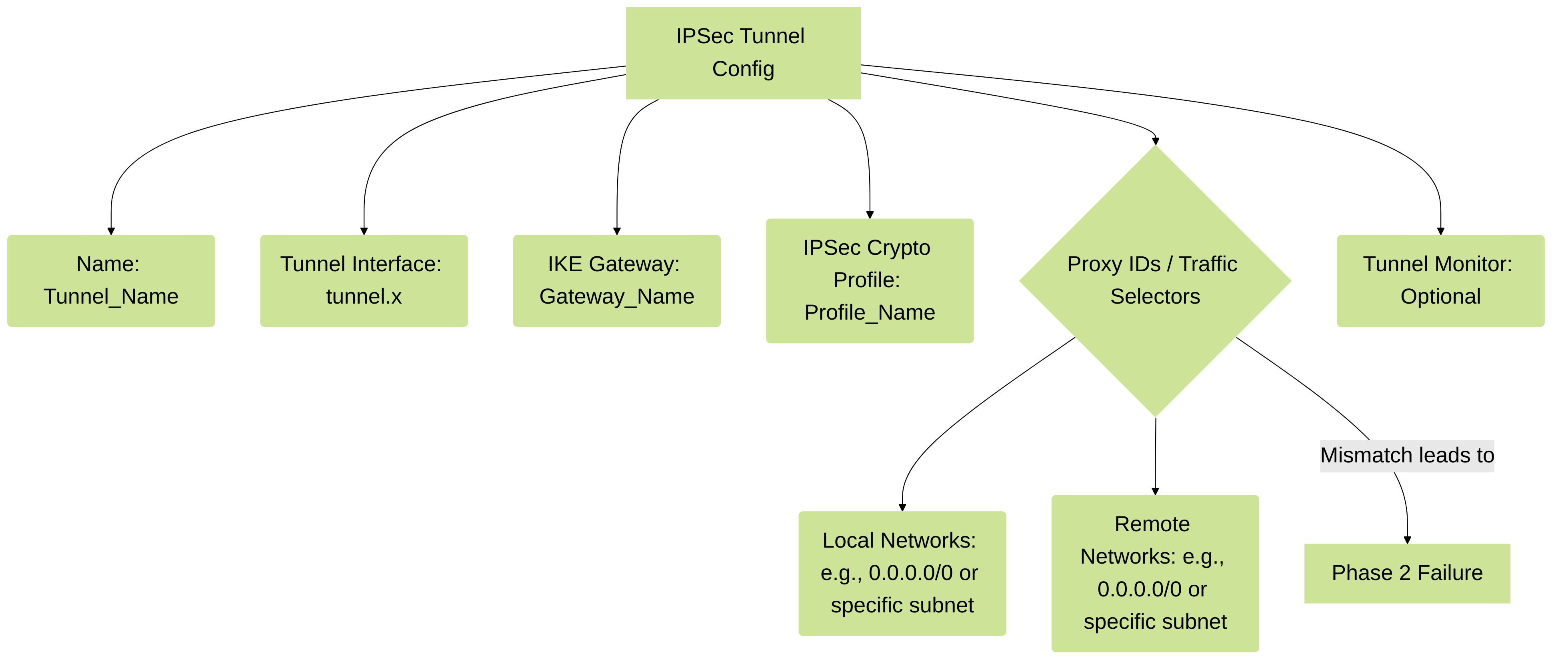
IPSec Tunnel configuration elements and the critical role of Proxy IDs.
Supporting Configuration: Routing
Since PAN-OS uses route-based VPNs, the firewall needs routes to direct traffic destined for the remote network(s) *towards* the logical Tunnel Interface.
Static Routes:
Manually configure routes in the Virtual Router pointing the remote subnet(s) to the appropriate Tunnel Interface. For example: Destination:
10.20.0.0/16
, Interface:
tunnel.1
, Next Hop: typically
None
for a tunnel interface (as the interface itself is the path).
Dynamic Routing (BGP/OSPF):
Configure a dynamic routing protocol to peer with the remote gateway *over* the tunnel interface. This allows for automatic learning and updating of routes. Often requires IP addresses on the tunnel interfaces to establish peering.
Routing decision flow for VPN traffic.
Supporting Configuration: Security Policies
IPSec tunnels terminate in Security Zones. You need Security Policies to explicitly allow traffic to flow between your internal zones and the VPN zone associated with the tunnel interface.
Example Policies:
-
Outbound Policy:
-
From Zone: e.g.,
Trust -
To Zone: e.g.,
VPN-Zone(the zone your tunnel interface is in) - Source Address: Local-Subnets
- Destination Address: Remote-VPN-Subnets
-
Application:
any(or specific) -
Service:
any(or specific, e.g.,application-default) -
Action:
Allow
-
From Zone: e.g.,
-
Inbound Policy:
-
From Zone: e.g.,
VPN-Zone -
To Zone: e.g.,
Trust - Source Address: Remote-VPN-Subnets
- Destination Address: Local-Subnets
-
Application:
any(or specific) -
Service:
any(or specific, e.g.,application-default) -
Action:
Allow
-
From Zone: e.g.,
Supporting Configuration: NAT Considerations
NAT Traversal (NAT-T):
Handled by enabling the option in the IKE Gateway settings. This allows IPSec packets (which are normally IP protocol 50 for ESP) to be encapsulated in UDP (typically port 4500 after initial IKE on UDP 500) so they can pass through NAT devices. No specific NAT policy is needed for NAT-T itself to function, but the IKE Gateway must be configured for it if a NAT device is between peers.
No-NAT for VPN Traffic:
Often, you do *not* want to perform NAT on traffic going over the VPN tunnel because you want internal IPs to communicate directly with remote internal IPs. You may need explicit "No NAT" rules in your NAT Policy list *before* any broader outbound NAT rules.
These No-NAT rules would typically match traffic:
-
Original Packet:
-
Source Zone: e.g.,
Trust -
Destination Zone: e.g.,
VPN-Zone(or the zone of the tunnel interface) -
Destination Interface: The tunnel interface (e.g.,
tunnel.1) - Source Address: Local internal subnets
- Destination Address: Remote VPN subnets
-
Source Zone: e.g.,
-
Translated Packet:
-
Source Address Translation:
None -
Destination Address Translation:
None
-
Source Address Translation:
IPSec Flow Diagrams
Visualizing the IPSec process can help in understanding and troubleshooting.
Simplified IKEv2 Negotiation Flow
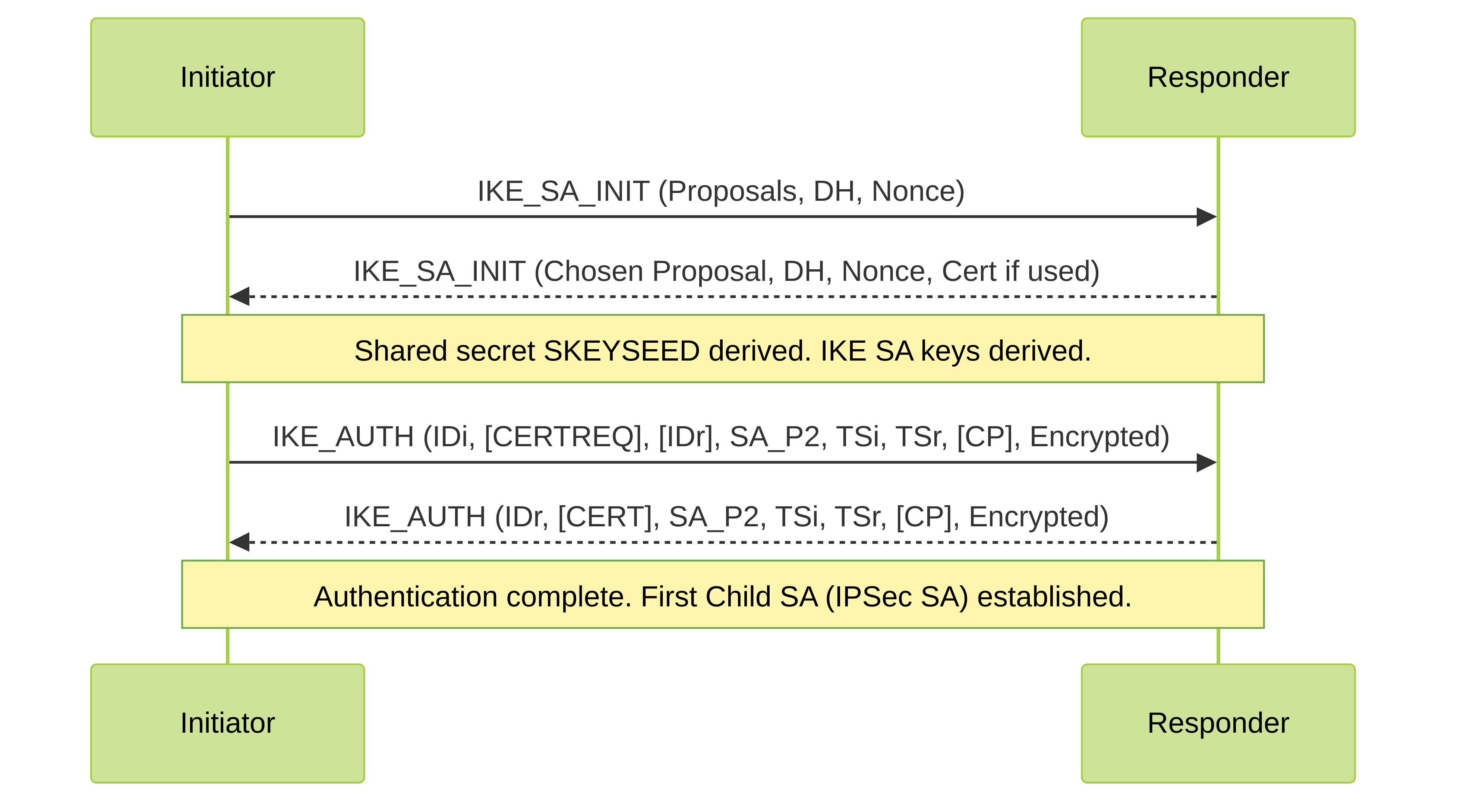
Simplified IKEv2 4-message exchange for initial IKE SA and first Child (IPSec) SA. IKEv2 is more efficient than IKEv1.
PAN-OS Route-Based VPN Traffic Processing

Simplified traffic flow for outbound traffic through a route-based VPN on PAN-OS.
Proxy ID Matching Logic
_matching_is_critical_for_Phase_2_May_20_2025_12-16PM.png)
Proxy ID (Traffic Selector) matching is critical for Phase 2 success.
PCNSE Prep: IPSec VPN Quiz
Test your knowledge of PAN-OS IPSec VPN configurations.