IPSec & Stability: Introduction to IPSec
IPSec (Internet Protocol Security) is a suite of protocols used to secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session. It operates at the network layer (Layer 3) of the OSI model, providing security for all traffic passing through it, regardless of the application.
IPSec provides two main security services:
- Authentication Header (AH): Provides connectionless integrity, data origin authentication, and an optional anti-replay service. It authenticates the entire packet, including the IP header (except for mutable fields).
- Encapsulating Security Payload (ESP): Provides confidentiality (encryption), and can also provide connectionless integrity, data origin authentication, and an anti-replay service. ESP encrypts the payload of the IP packet.
IPSec can be used in two modes:
- Transport Mode: Only the payload of the IP packet is encrypted and/or authenticated. The original IP header is left intact. This mode is typically used for end-to-end communication between two hosts.
- Tunnel Mode: The entire original IP packet (including the header and payload) is encrypted and/or authenticated. It is then encapsulated into a new IP packet with a new IP header. This mode is commonly used for site-to-site VPNs, where gateways protect traffic between different networks.
The Internet Key Exchange (IKE) protocol is a fundamental part of IPSec. IKE is used to negotiate security associations (SAs) and to authenticate the peers involved in the communication. An SA is a simplex (one-way) connection that defines how two devices will securely communicate. For a bidirectional IPSec tunnel, two SAs are typically established (one for inbound and one for outbound traffic for Phase 2).
IKE typically operates in two phases:
- Phase 1 (IKE SA): Establishes a secure, authenticated channel between the two IKE peers. The peers authenticate each other (using pre-shared keys or digital certificates) and negotiate cryptographic parameters for the IKE SA itself. This phase results in a shared secret key that is used to protect Phase 2 negotiations.
- Phase 2 (IPSec SA or Child SA): Uses the secure channel established in Phase 1 to negotiate the SAs for IPSec (the actual data tunnel). These SAs define the specific security protocols (AH or ESP), encryption algorithms, and keys to be used for protecting the user data.
Key Takeaway: IPSec provides a robust framework for securing IP communications. Understanding its components like AH, ESP, transport/tunnel modes, and the role of IKE (Phase 1 and Phase 2) is crucial for configuring and troubleshooting VPNs.
IPSec & Stability: Importance of Tunnel Stability
IPSec VPN tunnels are often critical for business operations, connecting remote offices, mobile users, or cloud resources to the corporate network. Therefore, ensuring the stability and reliability of these tunnels is paramount. An unstable VPN tunnel can lead to:
- Service Disruptions: Intermittent connectivity loss can disrupt applications, file access, and communication, leading to productivity losses.
- Data Loss: While IPSec protects data in transit, abrupt tunnel failures can interrupt data transfers, potentially leading to incomplete or corrupted data.
- Increased IT Overhead: Frequent tunnel drops require manual intervention for troubleshooting and re-establishment, consuming valuable IT resources.
- User Frustration: Unreliable VPN connections lead to a poor user experience and can hinder remote work effectiveness.
Several factors can affect tunnel stability:
- Network Issues: Problems in the underlying physical network, such as ISP outages, high latency, packet loss, or MTU mismatches, can directly impact VPN stability.
- Misconfigurations: Incorrectly configured IPSec parameters (e.g., mismatched crypto profiles, lifetimes, or peer IDs) are a common cause of tunnel instability or failure to establish.
- Resource Exhaustion: Firewalls or VPN gateways might run out of resources (CPU, memory, session capacity) under heavy load, affecting tunnel performance and stability.
- Peer Unavailability: If the remote peer becomes unresponsive due to a reboot, crash, or network issue, the tunnel will go down.
- Security Association (SA) Expiry: SAs have defined lifetimes. If re-keying fails before expiry, the tunnel will drop.
Mechanisms like Dead Peer Detection (DPD) and Tunnel Monitoring are designed to detect and react to these issues, enhancing overall tunnel stability and resilience. Monitoring helps in quickly identifying when a tunnel is down, allowing for faster remediation, whether it's manual intervention or automated failover to a backup path.
For the PCNSE exam, understanding the factors that impact VPN stability and the tools available to maintain it (like DPD and Tunnel Monitoring) is critical. You should be able to differentiate between these tools and know when to use each.
IPSec & Stability: Dead Peer Detection (DPD)
Dead Peer Detection (DPD), as defined in RFC 3706, is a mechanism used in IPSec to detect if an IKE (Internet Key Exchange) peer is still alive and reachable. Its primary purpose is to identify when a VPN peer has gone down without properly terminating the IKE SA (Security Association), allowing the local device to clean up stale SAs and potentially trigger failover or re-establishment attempts.
DPD works by sending "R-U-THERE" messages to the peer and expecting "R-U-THERE-ACK" acknowledgments in return. If no acknowledgments are received after a certain number of retries, the peer is considered dead, and the IKE SA is torn down.
DPD Modes of Operation (General Concept, vendor implementations may vary):
- On-demand/Optimized: DPD messages are sent only if there has been no traffic from the peer for a specific interval and there is outbound traffic to be sent to the peer. This is often the default and most efficient mode.
- Periodic/Probe Idle Tunnel: DPD messages are sent at regular intervals if there's no traffic (either incoming or outgoing) on the tunnel.
DPD on Palo Alto Networks Firewalls:
On Palo Alto Networks firewalls, DPD checks the liveness of the IKE peer. Key points about DPD on Palo Alto Networks firewalls:
- DPD is configured within the IKE Gateway settings.
- It sends R-U-THERE messages to verify IKE peer responsiveness.
- If the peer fails to respond, DPD will tear down the IKE SA.
- Important Caveat: On Palo Alto Networks firewalls, DPD is described as "not persistent" and is primarily triggered by events like a Phase 2 rekey attempt when there's traffic. This means if Phase 2 is up and stable, the firewall might not actively send DPD probes to check if the IKE SA is still active unless there's a trigger like an impending Phase 2 SA expiration. To ensure more active validation of the Phase 1 IKE SA, enabling Tunnel Monitoring is often recommended in conjunction with DPD.
- DPD must be consistently configured (either enabled or disabled) on both sides of the tunnel to avoid reliability issues.
Gotcha! DPD primarily checks the health of the IKE (Phase 1) peer, not necessarily the data path through the tunnel. A peer might be responsive to IKE messages but still unable to pass actual data traffic due to routing or other network issues. This is where Tunnel Monitoring provides additional value.
DPD helps in:
- Faster Failure Detection: Identifies unresponsive peers more quickly than relying solely on SA lifetime expirations.
- Resource Cleanup: Removes stale SAs, freeing up resources on the firewall.
- Improved Failover: By detecting a dead peer, DPD can help trigger failover to a backup tunnel or connection more promptly.
For the PCNSE exam, understand that DPD is about IKE peer liveness. Be aware of the Palo Alto Networks specific behavior where DPD might not be persistent and is often triggered by Phase 2 rekey events, making Tunnel Monitoring a complementary feature for comprehensive tunnel health assessment.
IPSec & Stability: IPSec Timers (IKEv1 & IKEv2)
IPSec SAs (Security Associations) are not permanent; they have lifetimes to enhance security. Regular re-keying limits the amount of data encrypted with a single key and ensures that if a key is compromised, its usefulness to an attacker is time-bound. Both IKE (Phase 1) and IPSec (Phase 2) SAs have lifetimes.
Phase 1 (IKE SA) Timers:
- Purpose: Defines how long the IKE SA (the secure channel for control plane messages) remains valid before it must be re-negotiated.
- Default Lifetime (Common): Often 24 hours (86400 seconds) for IKEv1 and IKEv2. Palo Alto Networks default for IKEv2 is 8 hours.
- Negotiation (IKEv1): In IKEv1, the lifetime is negotiated between peers, and typically the shorter of the two proposed lifetimes is chosen.
- Negotiation (IKEv2): In IKEv2, SA lifetimes are not directly negotiated . Each end is responsible for enforcing its own lifetime policy on the SA and initiating re-keying when necessary. If the two ends have different lifetime policies, the end with the shorter lifetime will typically initiate the re-keying. However, for compatibility and predictable behavior, it's best practice to configure matching lifetimes.
- IKEv2 Re-authentication: IKEv2 introduces a re-authentication mechanism, which is distinct from re-keying. Re-authentication forces a new IKE_AUTH exchange to verify peer credentials, which is not part of a standard re-key. Palo Alto Networks allows configuring an "IKEv2 Authentication Multiple" which, when multiplied by the Key Lifetime, determines the re-authentication interval. A value of 0 disables re-authentication.
Palo Alto Networks default IKE Crypto profile lifetime for IKEv1 is 8 hours. For IKEv2, the default Key Lifetime is also 8 hours, and the IKEv2 Authentication Multiple defaults to 0 (disabled).
Phase 2 (IPSec SA / Child SA) Timers:
- Purpose: Defines how long the IPSec SA (the SA that protects actual data traffic) remains valid. These lifetimes are generally shorter than Phase 1 lifetimes.
-
Types of Lifetimes:
- Time-based: SA expires after a certain amount of time (e.g., 1 hour or 3600 seconds). This is the most common.
- Traffic-based (Kilobytes/Packets): SA expires after a certain amount of data has been processed or a certain number of packets have been sent. This is less common but provides an additional layer of security. Palo Alto Networks firewalls support both time and traffic-based lifetimes for Phase 2.
- Default Lifetime (Common): Often 1 hour (3600 seconds) or 8 hours (28800 seconds). Palo Alto Networks default IPSec Crypto profile lifetime is 1 hour.
- Negotiation (IKEv1): During Quick Mode in IKEv1, lifetime proposals are exchanged. Similar to Phase 1, the peers usually agree on the shorter lifetime if values differ. Some vendors might have implementations where the initiator's lifetime must be the same or shorter. For best results, configure P2 lifetimes to be the same at both peers.
- Negotiation (IKEv2): As with IKEv2 Phase 1 SAs, the Child SA (Phase 2) lifetimes are also generally not negotiated in the same way as IKEv1. Each peer enforces its own policy. The peer with the shorter lifetime will initiate the re-key. Consistent configuration is highly recommended.
- Perfect Forward Secrecy (PFS): If PFS is enabled for Phase 2, a new Diffie-Hellman exchange is performed for each Phase 2 re-key. This ensures that compromising the Phase 1 keying material doesn't compromise Phase 2 keys. While more secure, it adds overhead to the re-key process.
General Rule for Lifetimes: The Phase 1 (IKE SA) lifetime should generally be longer than the Phase 2 (IPSec SA) lifetime. This allows multiple Phase 2 SAs to be re-keyed under the protection of a single, established Phase 1 SA, reducing the overhead of frequent Phase 1 re-negotiations which are more computationally intensive.
Rekeying Process:
Before an SA's lifetime expires, the peers should initiate a re-keying process to establish a new SA to replace the expiring one. This is done to prevent service interruption.
- IKEv1: Phase 1 re-key involves a new Main Mode or Aggressive Mode exchange. Phase 2 re-key involves a new Quick Mode exchange.
-
IKEv2:
IKEv2 offers more efficient re-keying.
- IKE SA Rekeying: Can be done using a CREATE_CHILD_SA exchange specifically to rekey the IKE SA itself, or through re-authentication (a new IKE_SA_INIT and IKE_AUTH). Make-before-break is a common strategy to avoid interruption.
- Child SA (IPSec SA) Rekeying: Done via a CREATE_CHILD_SA exchange within the existing IKE SA.
Mismatched Timers: While some negotiation occurs, significantly mismatched timers (especially if one side has a much shorter lifetime than the other expects) can lead to one side tearing down the SA while the other still considers it valid. This can cause intermittent tunnel drops and re-negotiations. It's always a best practice to configure identical or very similar lifetime values on both peers for predictable behavior.
Soft Lifetimes: Some systems use "soft lifetimes" which are slightly shorter than the "hard lifetimes". When the soft lifetime is reached, the system initiates re-keying, aiming to have the new SA ready before the hard lifetime expires and the old SA is torn down. IKEv2 often uses a soft lifetime calculated as a percentage of the hard lifetime plus a random value to avoid simultaneous re-key attempts.
For the PCNSE exam, know the default lifetimes for Palo Alto Networks (IKEv1: 8hrs P1, 1hr P2; IKEv2: 8hrs P1 Key Lifetime, 1hr P2). Understand the concept of re-keying and why P1 lifetimes are typically longer than P2. Be aware of the differences in lifetime negotiation between IKEv1 and IKEv2. Also, remember that IKEv2 has distinct re-keying and re-authentication mechanisms.
Palo Alto Tunnel Monitoring: Overview
IPSec tunnel monitoring on Palo Alto Networks firewalls is a feature designed to ensure the reliability and availability of VPN connections by actively verifying the tunnel's health. Unlike Dead Peer Detection (DPD) which primarily checks the liveness of the IKE peer, tunnel monitoring typically focuses on verifying the actual data path through the tunnel.
This feature uses ICMP (ping) probes sent from the local tunnel interface to a destination IP address on the remote side of the tunnel (usually the IP address of the remote tunnel interface). If these probes fail to receive responses after a configured number of attempts, the firewall can take a predefined action, such as logging the event, attempting to re-negotiate the tunnel, or failing over to a backup path.
By configuring tunnel monitoring, administrators can:
- Proactively Detect Tunnel Failures: Identify issues even if the IKE SA is still up but traffic cannot pass.
- Automate Failover Processes: In configurations with redundant tunnels, tunnel monitoring can trigger an automatic switch to a backup tunnel, minimizing downtime.
- Accelerate Recovery: When a failure is detected, the firewall can be configured to renegotiate IPSec keys to speed up tunnel recovery.
- Improve Network Resilience: Enhance overall network uptime and reliability for services dependent on VPN connectivity.
Tunnel monitoring provides a more comprehensive check of VPN health than DPD alone because it tests the actual ability to pass traffic through the tunnel, not just IKE peer responsiveness.
For the PCNSE exam, it's critical to understand that Tunnel Monitoring on Palo Alto Networks firewalls uses ICMP probes to verify data path connectivity through the tunnel. Know the configurable actions (Wait Recover, Fail Over) and that it works in conjunction with a Monitor Profile.
Palo Alto Tunnel Monitoring: 1. Assign an IP Address to the Tunnel Interface
To enable tunnel monitoring, the tunnel interface on the Palo Alto Networks firewall must have an IP address assigned to it. This IP address serves as the source IP for the ICMP probes used by the monitoring feature.
Steps:
- Navigate to Network > Interfaces > Tunnel .
-
Select the tunnel interface you want to configure (e.g.,
tunnel.1). - In the interface configuration window, go to the IPv4 tab (or IPv6 if applicable).
-
Click
Add
and assign an IP address and netmask to the tunnel interface.
-
For point-to-point links, it's common practice to use a /30 subnet (e.g.,
169.254.1.1/30on one end and169.254.1.2/30on the other). A /31 subnet can also be used. - These IP addresses are typically private and used only for the tunnel endpoints' communication and monitoring. They do not need to be routable over the public internet but must be unique and not overlap with other subnets in your network or the peer's network.
-
For point-to-point links, it's common practice to use a /30 subnet (e.g.,
- Assign the tunnel interface to a Virtual Router and a Security Zone (e.g., a dedicated VPN zone or a trusted zone). This is standard practice for tunnel interfaces.
Uniqueness of IPs:
Ensure that the IP addresses assigned to the tunnel interfaces at both ends of the VPN are unique and do not overlap with any existing subnets within either organization's network. Using addresses from the link-local block
169.254.0.0/16
(specifically choosing non-APIPA ranges like
169.254.x.x/30
where x is not 0 or 255 for the third octet for APIPA reserved ranges) is a common practice for these "management" IPs, but any non-overlapping private IP range can be used.
PCNSE Exam Focus: Remember that a tunnel interface must have an IP address for tunnel monitoring to function. This IP is the source for the ICMP probes. Be familiar with the common practice of using /30 or /31 subnets for this purpose.
Palo Alto Tunnel Monitoring: 2. Create a Tunnel Monitoring Profile
A Monitor Profile defines the parameters for the tunnel monitoring process, including the probing interval, the failure threshold, and the action to take if the tunnel is deemed unreachable.
Steps:
- Navigate to Network > Network Profiles > Monitor .
- Click Add at the bottom of the page to create a new monitor profile.
-
Enter a descriptive
Name
for the profile (e.g.,
Std-VPN-Monitor). -
Set the
Action
to take if the tunnel becomes unreachable:
- Wait Recover: The firewall will log the failure and continue to send probes, waiting for the tunnel to recover on its own. It will attempt to renegotiate IPSec keys to accelerate recovery. No routing changes are made by the firewall itself with this action. This is suitable when you want to be alerted but handle failover manually or through other means.
- Fail Over: The firewall will log the failure, attempt to renegotiate IPSec keys, and critically, it will disable the tunnel interface . Disabling the interface effectively removes it from routing consideration, allowing traffic to reroute through alternative paths (e.g., a backup VPN tunnel with a higher metric static route, or a Policy Based Forwarding rule with a backup path). This is the action used for automatic failover.
- Specify the Interval (in seconds): This is the time between ICMP probes sent to the monitored destination IP. The default is typically 3 seconds. The range is 2 to 10 seconds.
- Specify the Threshold (number of missed probes): This is the number of consecutive probes that must fail before the configured Action is taken. The default is typically 5 missed probes. The range is 2 to 100.
- Click OK to save the profile.
Calculation: The tunnel will be marked down after (Interval * Threshold) seconds of continuous probe failures. For example, with an Interval of 3 seconds and a Threshold of 5, the tunnel will be marked down after 15 seconds of unresponsiveness.
PCNSE Exam Focus: Know the two actions: Wait Recover and Fail Over , and understand their implications. "Fail Over" disables the tunnel interface, which is key for route changes. Remember the default interval (3s) and threshold (5).
Palo Alto Tunnel Monitoring: 3. Apply the Monitoring Profile to the IPSec Tunnel
Once the tunnel interface has an IP address and a monitor profile is created, you apply this profile to the specific IPSec tunnel configuration.
Steps:
- Navigate to Network > IPSec Tunnels .
- Select the IPSec tunnel you wish to monitor and click on its name to edit it, or click Add to create a new one.
-
In the IPSec Tunnel configuration window, on the
General
tab:
- Ensure the Tunnel Interface selected is the one you assigned an IP address to in Step 1.
- Check the box for Enable Tunnel Monitor . This will reveal additional options.
- For Destination IP , enter the IP address that the firewall will ping to monitor the tunnel's health. This is typically the IP address assigned to the remote peer's tunnel interface (the IP address you configured on the other end of the VPN, corresponding to your local tunnel IP).
-
From the
Monitor Profile
dropdown, select the profile you created in Step 2 (e.g.,
Std-VPN-Monitor).
- Review other IPSec tunnel settings (IKE Gateway, Crypto Profile, Proxy IDs if applicable) to ensure they are correct.
- Click OK to save the IPSec tunnel configuration.
- Commit the changes to the firewall.
ICMP Reachability: Ensure that the remote tunnel interface IP (the Destination IP for monitoring) is configured to respond to ICMP requests. Firewalls or security policies on the remote end must permit these ICMP probes from your local tunnel interface IP. If ICMP is blocked, tunnel monitoring will incorrectly report the tunnel as down.
Proxy ID Consideration (Policy-Based VPNs): If you are using policy-based VPNs (where Proxy IDs define interesting traffic), ensure that the Proxy ID configuration includes the subnet or specific IPs of the tunnel interfaces themselves, allowing the ICMP monitoring traffic to be encrypted and sent through the tunnel. For route-based VPNs (more common on Palo Alto Networks), this is less of a concern as long as routes direct the monitoring traffic into the tunnel.
PCNSE Exam Focus: The "Enable Tunnel Monitor" checkbox is on the General tab of the IPSec Tunnel configuration. The "Destination IP" is crucial – it's what you are pinging on the other side. The selected "Monitor Profile" dictates the monitoring behavior.
Palo Alto Tunnel Monitoring: Monitoring Actions
When configuring a Monitor Profile on a Palo Alto Networks firewall for IPSec tunnel monitoring, you have two primary actions to choose from if the monitored destination IP becomes unreachable: Wait Recover and Fail Over .
1. Wait Recover
-
Behavior:
If the ICMP probes to the destination IP fail for the configured threshold, the firewall:
- Generates a system log alerting about the tunnel failure.
- Attempts to renegotiate the IPSec keys to accelerate recovery.
- The tunnel interface itself remains administratively up .
- The firewall continues to send probes, waiting for the tunnel to become responsive again.
-
Use Case:
This option is suitable when:
- You want to be notified of tunnel issues but prefer to handle failover manually.
- Failover is managed by external systems or dynamic routing protocols that might react to the loss of connectivity without needing the interface to go down.
- You only have a single VPN tunnel and no backup path, so "failing over" isn't an option, but you still want active monitoring and alerts.
PCNSE Exam Note: With "Wait Recover," the firewall actively tries to bring the tunnel back up by renegotiating keys, but it does NOT change routing by bringing the interface down.
2. Fail Over
-
Behavior:
If the ICMP probes to the destination IP fail for the configured threshold, the firewall:
- Generates a system log alerting about the tunnel failure.
- Attempts to renegotiate the IPSec keys to accelerate recovery.
- Critically, the firewall administratively disables (brings down) the tunnel interface .
-
Impact of Interface Down:
When the tunnel interface goes down:
- Any static routes pointing out this tunnel interface will be removed from the active routing table (FIB).
- If Policy-Based Forwarding (PBF) rules use this tunnel interface as a primary path, PBF may switch to a backup path if configured.
- Dynamic routing protocols (like OSPF or BGP) running over the tunnel will see the interface go down, and adjacencies will drop, leading to route recalculation.
-
Use Case:
This option is essential for:
- Automated failover to a backup VPN tunnel. Typically, you would have two tunnels to the same destination, with static routes for the backup tunnel having a higher (less preferred) metric. When the primary tunnel interface goes down due to monitoring failure, its route is removed, and the backup route becomes active.
- Automated failover in PBF scenarios.
- Recovery: When the monitored destination IP becomes responsive again (ICMP probes succeed), the firewall will bring the tunnel interface back up, and traffic can revert to the primary path (depending on routing configuration, potentially preemptive).
PCNSE Exam Note: The key differentiator for "Fail Over" is that it brings the tunnel interface down . This is what enables automatic route changes for failover scenarios. Understand how this interacts with static routes (metrics) and PBF.
Choosing the correct action depends on your network design and redundancy strategy. For automatic failover, "Fail Over" is the required action. Ensure that your routing (static routes with metrics, PBF, or dynamic routing) is correctly configured to utilize the backup path when the primary tunnel interface goes down.
Palo Alto Tunnel Monitoring: Interaction with DPD
Dead Peer Detection (DPD) and Tunnel Monitoring are two distinct but complementary features on Palo Alto Networks firewalls for maintaining IPSec VPN reliability. Understanding their individual roles and how they can interact is important for robust VPN design.
Recap of Roles:
-
Dead Peer Detection (DPD):
- Focuses on the liveness of the IKE (Phase 1) peer .
- Sends IKE R-U-THERE messages and expects R-U-THERE-ACK responses.
- If the peer is deemed unresponsive, DPD tears down the IKE SA (and consequently associated IPSec SAs).
- On Palo Alto Networks, DPD is described as "not persistent" and often triggered by events like Phase 2 rekey attempts.
-
Tunnel Monitoring:
- Focuses on the liveness of the data path through the established IPSec tunnel.
- Sends ICMP (ping) probes from the local tunnel interface IP to a destination IP on the remote side (typically the remote tunnel interface IP).
- If probes fail, it can trigger actions like "Wait Recover" or "Fail Over" (which brings the tunnel interface down).
- Tunnel monitoring does not require DPD to be enabled, but they can work together.
How They Complement Each Other:
-
Scenario 1: IKE Peer Down (e.g., remote firewall reboots abruptly)
- DPD's Role: If DPD is active and triggered (e.g., by an outgoing packet trying to initiate a Phase 2 rekey, or if configured for more aggressive probing by some vendors), it will eventually detect the IKE peer is unresponsive and tear down the IKE SA. This cleans up state on the local firewall.
- Tunnel Monitoring's Role: ICMP probes from Tunnel Monitoring will also fail. If configured for "Fail Over," it will bring the tunnel interface down, triggering route failover. Tunnel Monitoring might detect the path failure faster or more consistently than DPD if DPD is only triggered by rekey events.
-
Scenario 2: IKE Peer Up, but Data Path Broken (e.g., intermediate routing issue, or remote firewall policy blocking ICMP/data but not IKE)
- DPD's Role: DPD messages might still succeed because the IKE process on the remote peer is responsive. DPD alone would not detect this type of failure.
- Tunnel Monitoring's Role: ICMP probes from Tunnel Monitoring will fail because the data path is broken or ICMP is blocked. This is where Tunnel Monitoring shines. It will detect the failure and can trigger the configured action (e.g., "Fail Over").
-
Scenario 3: Tunnel Monitoring Triggers P1 Rekey via DPD (Palo Alto Specifics)
- As noted in some documentation, on Palo Alto Networks firewalls, enabling tunnel monitoring can effectively make DPD more active. If tunnel monitoring detects a problem and tries to recover the tunnel (even with "Wait Recover"), this can trigger IPSec key renegotiation. An attempt to re-establish Phase 2 may, in turn, trigger DPD to validate the Phase 1 IKE SA if it hasn't been checked recently.
Key Interaction Point: Tunnel Monitoring is generally considered more comprehensive for data path verification. DPD is good for cleaning up stale IKE SAs when a peer truly disappears. Using both provides a more robust solution. Tunnel monitoring can detect issues that DPD might miss.
PCNSE Exam Focus: Understand the distinct roles: DPD for IKE peer liveness, Tunnel Monitoring for data path liveness. Recognize that Tunnel Monitoring can detect failures even if DPD shows the peer as up. Be aware of the Palo Alto specific note that Tunnel Monitoring can help trigger DPD to validate Phase 1, especially given DPD's "not persistent" nature.
Palo Alto Tunnel Monitoring: Best Practices & Considerations
While IPSec Tunnel Monitoring is a valuable feature, proper configuration and understanding of its behavior are key to its effectiveness. Here are some best practices and considerations:
-
Use a Stable Monitoring Target:
- The Destination IP for monitoring should be a highly available IP address on the remote side, typically the IP address of the remote tunnel interface itself. Avoid monitoring IPs that might become unresponsive for reasons unrelated to tunnel health (e.g., a specific server that could be rebooted).
-
Ensure ICMP is Permitted:
- The ICMP probes used by tunnel monitoring must be allowed by any security policies or ACLs on both the local and remote firewalls, as well as any intermediate devices within the tunnel path if applicable (though typically probes are just between tunnel interface IPs).
- If ICMP is blocked, tunnel monitoring will always report the tunnel as down.
-
Tune Interval and Threshold:
- The default Interval (3 seconds) and Threshold (5 retries) result in a ~15-second detection time. Adjust these based on your sensitivity to downtime and tolerance for false positives.
- Aggressive settings (low interval/threshold) can detect failures faster but might lead to premature failovers due to transient network blips.
- Conservative settings are more resilient to transient issues but result in slower failure detection.
-
Coordinate with Peer Administrator:
- If the remote end is managed by a different entity, coordinate the use of tunnel interface IPs and ensure they understand ICMP probes will be sent.
-
Configure Redundant Tunnels for "Fail Over":
-
The "Fail Over" action is most effective when a backup VPN tunnel is configured. This typically involves:
- Two IPSec tunnels to the same remote site (ideally over different ISPs or paths if possible).
- Static routes for traffic destined for the remote network, with the primary tunnel's route having a lower (more preferred) metric than the backup tunnel's route.
- When the primary tunnel's monitor profile triggers "Fail Over", its interface goes down, the primary route is removed, and the backup route becomes active.
-
The "Fail Over" action is most effective when a backup VPN tunnel is configured. This typically involves:
-
Policy-Based Forwarding (PBF) for Failover:
- PBF can also be used to manage failover. A PBF rule can direct traffic to the primary tunnel, and if tunnel monitoring brings that interface down, PBF can then redirect traffic to a backup path (another tunnel or interface).
-
Logging and Alerting:
- Ensure system logs for tunnel events (up, down, renegotiation) are monitored. Configure alerts (e.g., email, SNMP traps, syslog to a SIEM) for tunnel failures so administrators are promptly notified.
-
DPD and Tunnel Monitoring Coexistence:
- It's generally recommended to use both DPD and Tunnel Monitoring. DPD handles IKE peer liveness, while Tunnel Monitoring handles data path verification. On Palo Alto Networks, tunnel monitoring can help make DPD checks more frequent.
-
Proxy ID Considerations (Policy-Based VPNs):
- If using policy-based VPNs, ensure the proxy IDs (traffic selectors) include the IP addresses of the tunnel interfaces themselves. This ensures the ICMP monitoring traffic is encrypted and sent through the tunnel. For route-based VPNs (common with Palo Alto Networks tunnel interfaces), ensure routing directs the monitor traffic into the tunnel.
-
Test Failover Scenarios:
- Regularly test your failover configuration to ensure it works as expected. This can involve manually shutting down the primary tunnel interface or simulating a network failure.
-
Path Monitoring vs. Tunnel Monitoring:
- Palo Alto Networks also offers "Path Monitoring" for static routes. This is different from IPSec Tunnel Monitoring. Path monitoring pings a target to determine if a static route should be active. While it can be used to monitor reachability to the other end of a tunnel, IPSec Tunnel Monitoring is specifically tied to the IPSec tunnel state and can trigger actions like renegotiation or interface down. In some scenarios, using Static Route Path Monitoring to ping the remote tunnel interface IP can be an alternative or complement to IPSec Tunnel Monitoring, especially if you need more granular control over routing decisions independent of the IPSec tunnel object itself. However, IPSec Tunnel Monitoring provides direct actions on the tunnel object.
PCNSE Exam Focus: Understand the interplay between Tunnel Monitoring and routing (static route metrics, PBF). Know that ICMP must be allowed. Be clear on the difference and potential combined use of DPD and Tunnel Monitoring. The consideration for Proxy IDs in policy-based VPNs is also a relevant detail.
Visualizing IPSec: IPSec Key Exchange (Simplified)
The Internet Key Exchange (IKE) protocol is used to set up Security Associations (SAs) for IPSec. This involves authenticating peers and negotiating cryptographic keys and algorithms. Here's a simplified view.
IKEv1 Exchange
IKEv1 typically involves two phases: Phase 1 (Main Mode or Aggressive Mode) and Phase 2 (Quick Mode).
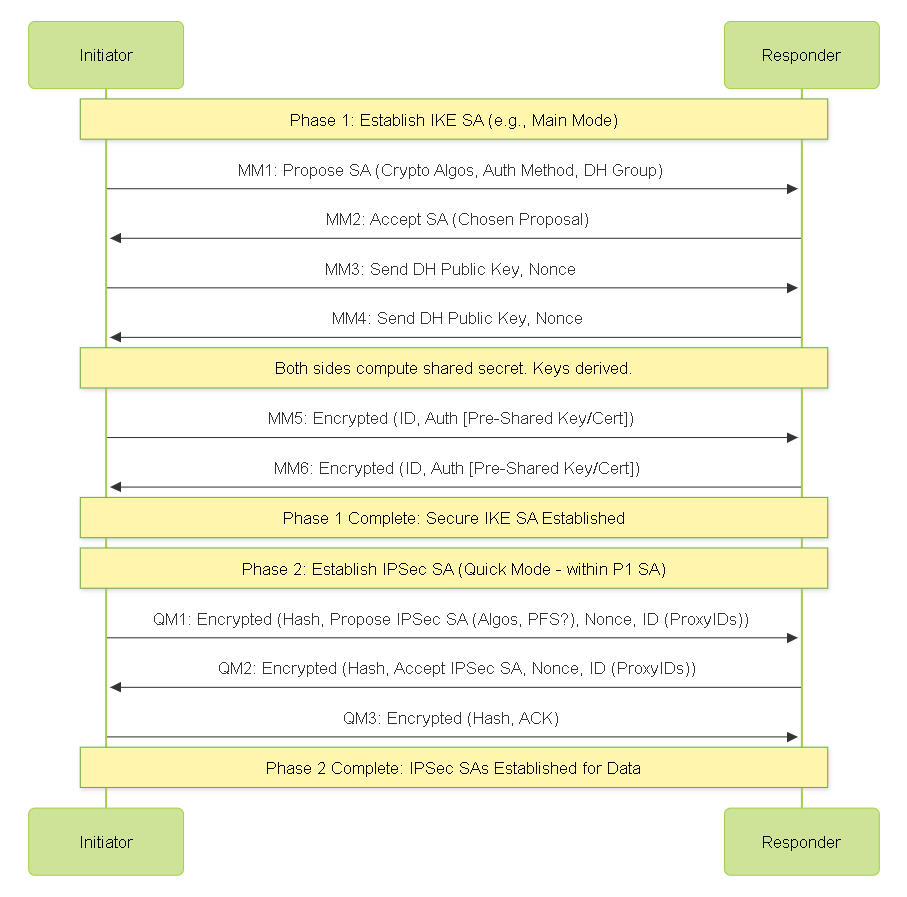
Simplified IKEv1 Main Mode and Quick Mode Exchange.
IKEv2 Exchange
IKEv2 streamlines the process, typically using fewer messages. It combines initial SA negotiation, DH exchange, and authentication into fewer exchanges.
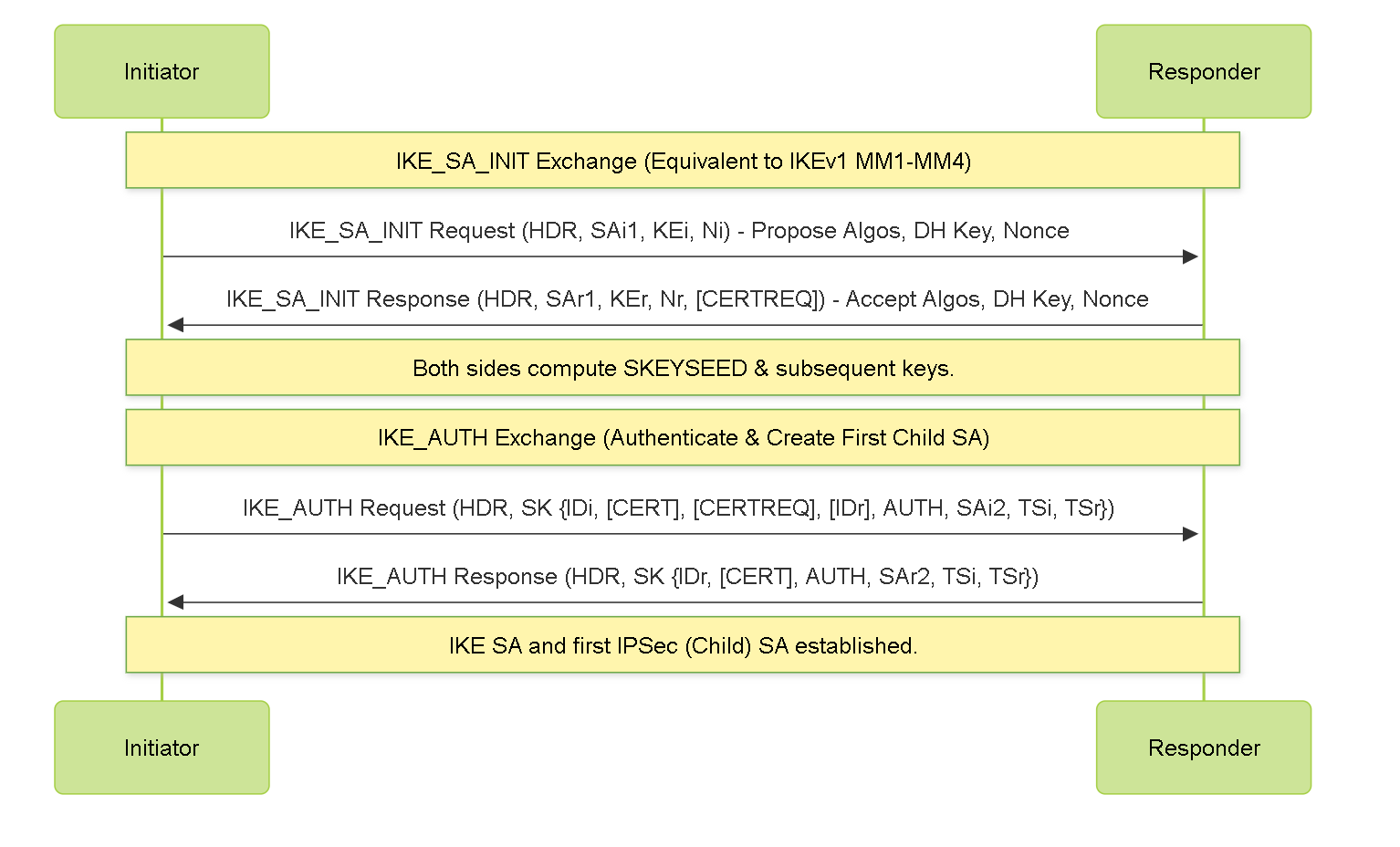
Simplified IKEv2 Exchange.
- IKE_SA_INIT: Negotiates cryptographic algorithms, exchanges nonces, and performs a Diffie-Hellman exchange.
- IKE_AUTH: Authenticates the previous messages, exchanges identities and certificates (if used), and establishes the IKE SA and the first Child SA (IPSec SA).
IKEv2 is generally more efficient, robust (e.g., better NAT traversal, EAP support), and secure than IKEv1.
Visualizing IPSec: Tunnel Monitoring Logic (Palo Alto Networks)
This flowchart illustrates the basic decision-making process of IPSec Tunnel Monitoring on a Palo Alto Networks firewall when it's enabled for an IPSec tunnel.
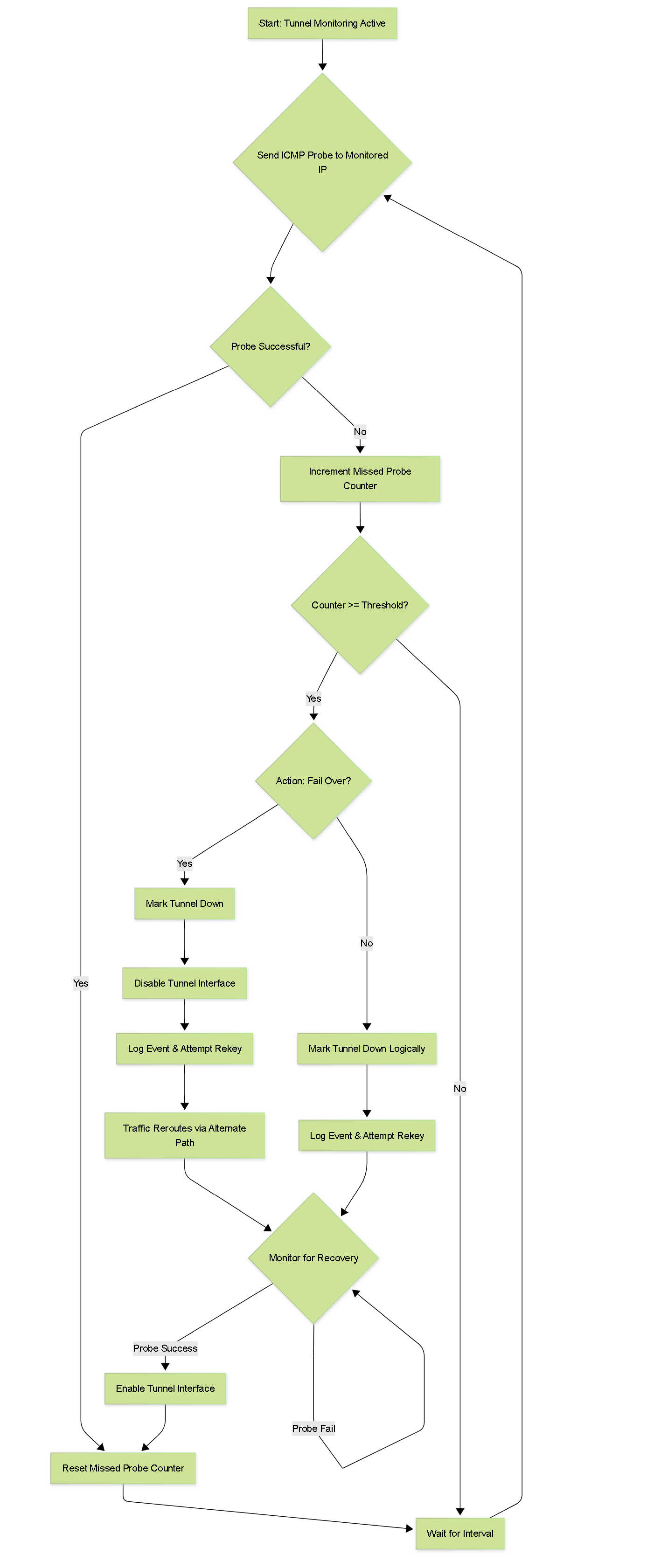
Explanation:
- Monitoring Active: The process starts when tunnel monitoring is enabled for an IPSec tunnel with a valid monitor profile.
- Send ICMP Probe: The firewall sends an ICMP echo request (ping) from its tunnel interface IP to the configured Destination IP on the remote side of the tunnel.
- Probe Successful?: If an ICMP echo reply is received, the probe is successful.
- Reset Counter & Wait: The missed probe counter is reset, and the firewall waits for the configured 'Interval' before sending the next probe.
- Probe Failed: If no reply is received (or an error like "host unreachable" comes back), the probe is considered failed.
- Increment Counter: The missed probe counter is incremented.
- Threshold Check: The firewall checks if the missed probe counter has reached the configured 'Threshold'.
- Threshold Not Reached: If the threshold is not met, it waits for the next interval and sends another probe.
-
Threshold Reached - Action Check:
If the threshold is met, the firewall checks the configured 'Action' in the monitor profile.
- Fail Over: The tunnel is marked down, the tunnel interface is administratively disabled (this is key for routing changes), an event is logged, and the firewall attempts to rekey/recover the tunnel.
- Wait Recover: The tunnel is marked as logically down, an event is logged, and the firewall attempts to rekey/recover.
Visualizing IPSec: DPD vs. Tunnel Monitoring
Dead Peer Detection (DPD) and Tunnel Monitoring serve different but complementary purposes in ensuring VPN reliability. This diagram highlights their distinct focus areas.
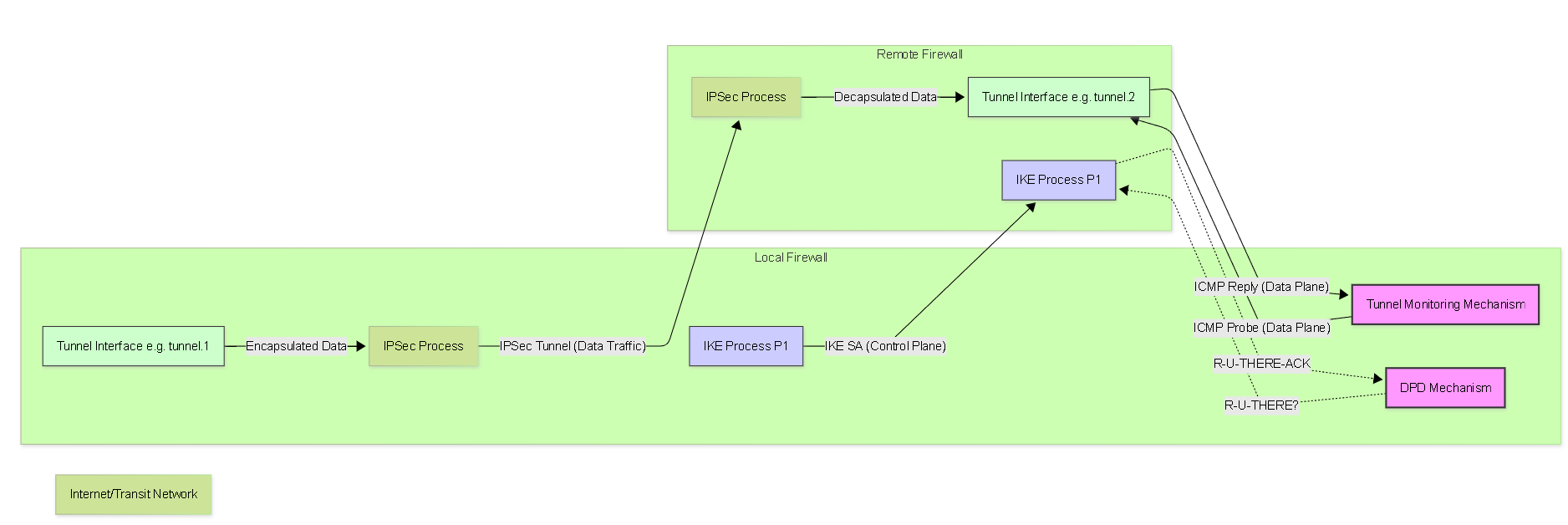
DPD checks IKE Peer Liveness; Tunnel Monitoring checks Data Path Liveness.
Key Differences Illustrated:
-
DPD (Dead Peer Detection):
- Operates at the IKE (Phase 1) level.
- Sends control plane messages (R-U-THERE) to the IKE process on the remote peer.
- Verifies if the remote IKE peer is responsive and capable of participating in IKE negotiations.
- Concern: Is the control plane for key management alive?
-
Tunnel Monitoring (Palo Alto Networks):
- Operates by sending data plane traffic (ICMP probes) through the established IPSec tunnel.
- Sends probes from the local tunnel interface IP to the remote tunnel interface IP (or another designated IP across the tunnel).
- Verifies if actual data can traverse the encrypted tunnel.
- Concern: Is the data path through the tunnel functional?
A scenario where DPD might show the peer as "up" but Tunnel Monitoring shows "down": The remote firewall's IKE process is running and responding to DPD checks, but a routing issue, an ACL, or a problem with the IPSec process on the remote side prevents the ICMP probes (or any data) from passing through the tunnel. In this case, Tunnel Monitoring provides a more accurate reflection of the tunnel's usability for data traffic.
PCNSE Exam Focus: Key Concepts
For the Palo Alto Networks Certified Network Security Engineer (PCNSE) exam, a solid understanding of IPSec VPNs, including their stability and monitoring mechanisms, is crucial. Here are key concepts to master:
Core IPSec & IKE:
- IKEv1 vs. IKEv2: Know the differences in negotiation (phases/exchanges), efficiency, security features (e.g., EAP support in IKEv2), and DPD behavior. IKEv2 is generally preferred.
-
Phases:
- Phase 1 (IKE SA): Purpose is to establish a secure channel for IKE messages. Key negotiation (Diffie-Hellman), authentication (pre-shared key, certificates).
- Phase 2 (IPSec SA / Child SA): Purpose is to negotiate SAs for actual data traffic, protected by the Phase 1 SA. Defines ESP/AH, encryption/auth algorithms, and traffic selectors (Proxy IDs).
-
Lifetimes:
- Phase 1 lifetime is typically longer than Phase 2. (PA Default: P1-8hr, P2-1hr for IKEv1; P1-8hr Key Lifetime, P2-1hr for IKEv2).
- Understand re-keying and how mismatched timers can cause issues (though negotiation attempts to use the shorter).
- IKEv2 specific: Key Lifetime vs. Re-authentication Interval.
-
Proxy IDs (Traffic Selectors):
- Critical for policy-based VPNs. Defines what traffic is considered "interesting" and should be encrypted.
- Must match (often mirrored) on both peers. Mismatches are a common cause of Phase 2 failures.
- For route-based VPNs (using tunnel interfaces), Proxy IDs are often set to 0.0.0.0/0 (any) for local and remote, as routing controls traffic.
- Authentication Methods: Pre-shared keys (PSKs) vs. Certificates. Understand the scalability and security implications.
Tunnel Stability & Monitoring:
-
Dead Peer Detection (DPD):
- Purpose: Detects unresponsive IKE peers.
- Mechanism: R-U-THERE / R-U-THERE-ACK messages.
- Palo Alto Specifics: "Not persistent," often triggered by Phase 2 rekey. Tunnel monitoring can make it more active. Must be configured consistently on both sides.
-
IPSec Tunnel Monitoring (Palo Alto Networks):
- Purpose: Verifies data path liveness through the tunnel using ICMP probes.
- Configuration: Requires IP on tunnel interface, Monitor Profile, and applied to IPSec Tunnel config.
- Monitored IP: Typically the remote tunnel interface IP.
- Actions: Wait Recover (logs, rekeys, interface stays up) vs. Fail Over (logs, rekeys, interface goes down ).
- Interval & Threshold: Defaults are 3s interval, 5 retries.
-
Failover Scenarios:
- Understand how "Fail Over" action in Tunnel Monitoring facilitates automatic failover by bringing the interface down.
- Requires redundant tunnels and appropriate routing (e.g., static routes with different metrics, PBF).
Troubleshooting:
- Common issues: Mismatched P1/P2 parameters, incorrect Proxy IDs, routing problems, NAT traversal issues, DPD/Tunnel Monitoring misconfigurations.
-
Key CLI commands for VPN status and troubleshooting (e.g.,
show vpn ike-sa,show vpn ipsec-sa,show vpn flow, packet captures, system logs).
Focus on the why behind configurations, not just the how . Why is DPD used? Why is Tunnel Monitoring used? How do they differ and complement each other? Why are lifetimes important?
PCNSE Exam Focus: Common Pitfalls & Gotchas
When configuring and troubleshooting IPSec VPNs, especially with features like Tunnel Monitoring, certain misunderstandings or misconfigurations can lead to problems. Being aware of these common pitfalls is essential for the PCNSE exam and real-world deployments.
-
DPD vs. Tunnel Monitoring Confusion:
- Pitfall: Believing DPD alone is sufficient for ensuring tunnel path liveness.
- Gotcha: DPD checks IKE peer responsiveness, not necessarily if data can pass through the tunnel. Tunnel Monitoring addresses data path liveness by sending ICMP probes through the tunnel. A peer can be DPD-alive but the tunnel path broken.
-
Tunnel Monitoring "Fail Over" Action Misunderstanding:
- Pitfall: Expecting "Fail Over" to magically reroute traffic without proper underlying routing configuration.
- Gotcha: The "Fail Over" action disables the tunnel interface . This removal of the interface from an active state is what allows routing protocols or static route metrics / PBF rules to choose an alternative path. Without a configured backup path and routing logic, failover won't occur automatically.
-
ICMP Blocking Affecting Tunnel Monitoring:
- Pitfall: Enabling Tunnel Monitoring but having ICMP blocked by a security policy on either firewall or by the remote host itself.
- Gotcha: If the ICMP probes (pings) from the local tunnel interface to the remote monitored IP are blocked, Tunnel Monitoring will incorrectly assume the tunnel is down and take the configured action. Ensure ICMP is permitted for the monitoring source/destination IPs.
-
Mismatched Proxy IDs (Policy-Based VPNs):
- Pitfall: Incorrectly configured or mismatched Proxy IDs (traffic selectors).
- Gotcha: For policy-based VPNs, Proxy IDs define what traffic is encrypted. They must be an exact mirror image on both sides. If they don't match, Phase 2 negotiation will fail, often with errors indicating "Proxy ID mismatch" or "No proposal chosen". This is a very common issue. For Tunnel Monitoring to work with policy-based VPNs, the tunnel interface IPs must be included in the Proxy IDs.
-
Incorrect Monitored Destination IP:
- Pitfall: Setting the Tunnel Monitoring Destination IP to an unreliable host or an IP not reachable directly through the tunnel.
- Gotcha: The monitored IP should ideally be the IP address of the remote firewall's tunnel interface . Monitoring a less stable server behind the remote firewall can lead to false positives if that server goes down but the tunnel itself is fine.
-
Lifetime Mismatches:
- Pitfall: Configuring drastically different IKE or IPSec lifetimes on peers.
- Gotcha: While negotiation typically results in the shorter lifetime being used, very different settings can sometimes lead to one side expiring SAs prematurely from the other's perspective, causing renegotiation flaps. Best practice is to keep lifetimes identical or very similar. Also, ensure P1 lifetime > P2 lifetime.
-
Palo Alto DPD "Not Persistent" Nuance:
- Pitfall: Assuming DPD on Palo Alto firewalls is constantly probing like some other vendor implementations.
- Gotcha: DPD is often triggered by events like Phase 2 rekey attempts. If a tunnel is idle and no rekeys are imminent, DPD might not actively check. Enabling Tunnel Monitoring can make DPD checks more frequent when the tunnel monitor attempts recovery.
-
Route-Based vs. Policy-Based VPN Logic:
- Pitfall: Applying policy-based VPN thinking (heavy reliance on Proxy IDs for routing) to route-based VPNs, or vice-versa.
- Gotcha: Palo Alto Networks primarily uses route-based VPNs with tunnel interfaces. Traffic is directed into the tunnel via routing (static or dynamic). Proxy IDs in this setup are often set to 0.0.0.0/0 any/any, as routing handles specificity. Tunnel monitoring ICMP traffic also follows these routes.
-
Forgetting to Commit:
- Pitfall: Making changes to VPN configurations, DPD, or Tunnel Monitoring settings and forgetting to commit them on the firewall.
- Gotcha: Changes are not active until committed. This simple oversight can lead to much wasted troubleshooting time.
Many PCNSE questions will test your understanding of these nuanced differences and common issues. Pay attention to wording that hints at DPD vs. Tunnel Monitoring roles, the effect of "Fail Over," and Proxy ID matching.
PCNSE Exam Focus: Troubleshooting Scenarios
Troubleshooting IPSec VPNs and their monitoring mechanisms is a key skill for a PCNSE. Here are common scenarios and approaches:
Scenario 1: Tunnel is Down, DPD is Enabled, Tunnel Monitoring is Enabled (Action: Fail Over)
Symptoms: Users report no connectivity. System logs show tunnel monitoring threshold reached, interface disabled. Backup tunnel (if configured) may or may not be active.
Troubleshooting Steps:
-
Check System Logs:
- Look for messages related to Tunnel Monitor (e.g., "Tunnel xxx is down", "Tunnel monitor: destination y.y.y.y is not reachable").
- Look for IKE and IPSec logs (e.g., "Phase 1 negotiation failed", "Phase 2 negotiation failed", DPD failure messages). This can indicate if the issue is P1, P2, or path related.
-
Verify Tunnel Monitoring Status:
- GUI: Network > IPSec Tunnels (check status icon and hover for details).
-
CLI:
show vpn tunnel name <tunnel_name>- check monitor status.
- Check Physical Connectivity: Ensure WAN interfaces are up on both ends.
-
Verify ICMP Reachability to Monitored IP (manually):
-
From the firewall CLI, try to ping the Tunnel Monitoring Destination IP
sourcing from the local tunnel interface IP
:
ping source <local_tunnel_ip> host <remote_monitored_ip> - If this fails, the issue is likely with the data path or ICMP being blocked. Check security policies on both ends for the tunnel interface IPs and ICMP. Check routing.
-
From the firewall CLI, try to ping the Tunnel Monitoring Destination IP
sourcing from the local tunnel interface IP
:
- Check IKE Gateway and IPSec Crypto Profiles: Ensure parameters (encryption, auth, DH group, lifetimes) match on both peers.
- Check Proxy IDs (if policy-based): Ensure they are exact mirrors.
-
Check DPD Status (CLI):
show vpn ike-sa detail name <ike_gw_name>(look for DPD status). -
If Failover to Backup Tunnel Expected:
-
Verify the primary tunnel interface is indeed down (
show interface <tunnel_interface_name>). -
Check routing table (
show routing route) to see if backup route is active. - Verify backup tunnel configuration and status.
-
Verify the primary tunnel interface is indeed down (
Scenario 2: Tunnel Flapping (Goes Up and Down Intermittently)
Symptoms: Connectivity is unstable. Logs show tunnel going down and coming back up frequently.
Troubleshooting Steps:
- Check Lifetimes: Mismatched or very short lifetimes can cause frequent re-negotiations. Ensure P1 lifetime > P2 lifetime.
- Check DPD Settings: Aggressive DPD timers or inconsistent DPD configuration (enabled on one side, disabled on other) can cause flaps.
- Check Tunnel Monitoring Settings: Aggressive Interval/Threshold might cause failovers on transient network issues.
- Network Instability: Investigate underlying WAN for packet loss or high latency that might cause DPD or Tunnel Monitoring to trigger.
- Resource Issues: Check firewall CPU/memory. High load can impact VPN stability.
- NAT Traversal Issues: If NAT-T is involved, ensure it's working correctly. Sometimes re-negotiations can struggle with NAT mappings.
- Peer Device Issues: The remote peer might be unstable or misconfigured.
Scenario 3: Tunnel Monitoring Shows Tunnel Down, but DPD is Up / Basic Connectivity Seems OK
Symptoms: Tunnel Monitoring action (e.g., Fail Over) triggers. DPD for the IKE gateway might still show connected, or pings to public IPs work.
Troubleshooting Steps:
-
Focus on ICMP:
This strongly points to an issue with the ICMP probes for Tunnel Monitoring.
- Verify the correct Destination IP is configured in Tunnel Monitoring settings.
- Confirm ICMP is permitted by security policies on BOTH firewalls for traffic between the local tunnel interface IP and the remote tunnel interface IP.
- Ensure the remote tunnel interface itself is configured to respond to ICMP.
- Check for any intermediate network devices (if any within the private network path post-decryption) that might block ICMP.
- Routing for Monitor Traffic: Ensure that routes on the local firewall correctly direct traffic destined for the monitored IP through the tunnel interface being monitored. For route-based VPNs, this is usually straightforward. For policy-based VPNs, ensure the tunnel interface IPs are covered by the proxy IDs.
Key CLI Commands for VPN Troubleshooting:
-
System Logs:
less mp-log ikemgr.log,less mp-log vpnmgr.log(or via GUI Monitor tab) -
IKE SA Status:
show vpn ike-sa [detail] [name <gateway_name>] -
IPSec SA Status:
show vpn ipsec-sa [detail] [tunnel <tunnel_name>] -
Tunnel Flow/Stats:
show vpn flow name <tunnel_name>(shows encap/decap counters, errors) -
Clear SAs (use with caution, will drop tunnel):
clear vpn ike-sa name <gateway_name>,clear vpn ipsec-sa tunnel <tunnel_name> -
Packet Capture:
tcpdumpor GUI packet capture filtered for tunnel traffic or IKE (UDP 500/4500). -
Global Counters:
show counter global | match vpn(or more specific filters)
For the PCNSE, be prepared to interpret symptoms and select appropriate troubleshooting steps or CLI commands. Understanding how Tunnel Monitoring interacts with routing and policies is key.
IPSec & Tunnel Monitoring: PCNSE Style Quiz
Test your knowledge on IPSec and Tunnel Monitoring concepts relevant to the PCNSE exam.