Destination NAT on Palo Alto Networks Next-Generation Firewalls: A Comprehensive Guide
Welcome to this in-depth guide on Destination Network Address Translation (DNAT) as implemented on Palo Alto Networks Next-Generation Firewalls (NGFWs). This document is designed for network security engineers, administrators, and PCNSE aspirants seeking a thorough understanding of DNAT concepts, configuration, and troubleshooting within the PAN-OS ecosystem.1. Core Concept and Purpose of Destination NAT
In the context of Palo Alto Networks firewalls, **Destination NAT (DNAT)** is a mechanism that modifies the destination IP address and/or port of incoming packets as they pass through the firewall. It allows external (typically public) IP addresses and ports to be translated to internal (typically private) IP addresses and ports, enabling external users to access services hosted on internal servers.Primary Purpose:
- Exposing Internal Services: The most common use is to make internal servers (e.g., web servers, mail servers, RDP servers) accessible from the internet using a public IP address. These internal servers usually have private IP addresses that are not routable on the internet.
- Port Redirection: DNAT can translate not only the destination IP address but also the destination port. This allows, for example, an external request on port 8080 to be directed to an internal server on port 80.
- IP Address Conservation/Management: While less of a primary goal for DNAT compared to SNAT, it allows multiple internal services to be mapped to different ports on a single public IP address.
- Server Relocation Transparency: If an internal server's IP address changes, only the NAT rule needs to be updated, not any external DNS records or client configurations that point to the public IP.
Differentiation from Source NAT (SNAT):
- Destination NAT (DNAT): Modifies the destination IP address (and optionally port) of incoming packets. It's primarily used for inbound connections to internal resources. Think "who you are going to ".
- Source NAT (SNAT): Modifies the source IP address (and optionally port) of outgoing packets. It's primarily used for outbound connections from internal networks to external networks (e.g., internet), allowing multiple internal devices to share a single public IP address. Think "who you are from ".
Typical Traffic Flow with Destination NAT:
-
An external client initiates a connection to a public IP address and port (e.g.,
203.0.113.10:80) that is managed by the Palo Alto Networks firewall. - The packet arrives at the firewall's external-facing interface (e.g., in the "Untrust" zone).
- The firewall's packet processing engine evaluates NAT policies before Security policies for new sessions.
-
If a matching DNAT rule is found:
-
The destination IP address in the packet header is changed from the public IP (
203.0.113.10) to the private IP of the internal server (e.g.,192.168.1.100). -
Optionally, the destination port can also be changed (e.g., from public port
80to internal port8080).
-
The destination IP address in the packet header is changed from the public IP (
- The packet, now with its modified destination, is then evaluated by Security policies. The Security policy must allow traffic to the original (public) destination IP but use the post-NAT destination zone (the zone where the internal server resides, e.g., "DMZ" or "Trust").
- If allowed by the Security policy, the packet is forwarded to the internal server.
- Return traffic from the internal server back to the external client automatically undergoes the reverse NAT translation (private IP to public IP for the source address of the return packet) because the firewall maintains a session table entry for the translation.
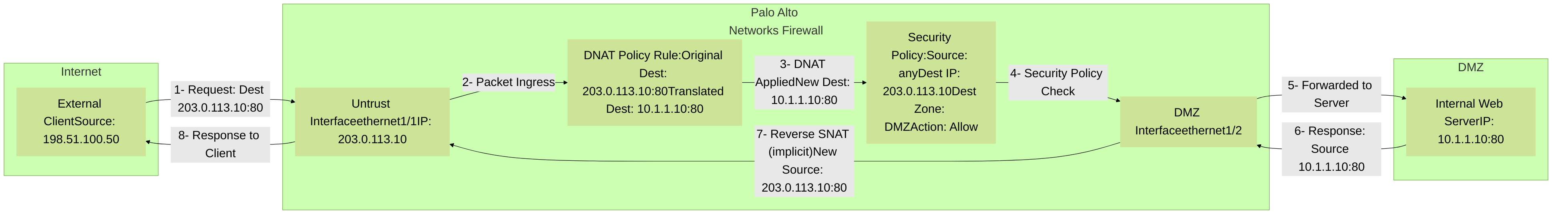
Diagram illustrating a typical Destination NAT traffic flow for accessing an internal web server through a Palo Alto Networks firewall. Note the NAT policy application before the Security policy check, and how the Security policy uses the original destination IP but the post-NAT destination zone.
2. Common Use Cases for Destination NAT
Destination NAT is a cornerstone for enabling secure access to internal resources. Here are some common use cases:-
Exposing an Internal Web Server to the Internet:
-
Scenario:
Your company hosts its public website on an internal web server (e.g., Apache or IIS) with a private IP address (e.g.,
192.168.10.50) in your DMZ zone. You want to make this website accessible via your company's public IP address (e.g.,203.0.113.20) on standard HTTP (port 80) and HTTPS (port 443) ports. -
How DNAT Solves It:
A DNAT rule is configured on the Palo Alto Networks firewall.
-
When an external user browses to
http://203.0.113.20, the firewall receives the packet. -
The DNAT rule matches on destination IP
203.0.113.20and destination port80. -
It translates the destination IP to
192.168.10.50and keeps the port as80(or translates it if needed). -
A corresponding Security policy allows this traffic from the "Untrust" zone to the "DMZ" zone, destined for
203.0.113.20on port80.
-
When an external user browses to
-
Original Destination:
IP
203.0.113.20, Port80(or443for HTTPS) -
Translated Destination:
IP
192.168.10.50, Port80(or443)
-
Scenario:
Your company hosts its public website on an internal web server (e.g., Apache or IIS) with a private IP address (e.g.,
-
Providing Remote Desktop (RDP) Access to an Internal Server:
-
Scenario:
An administrator needs to access an internal Windows server (e.g.,
10.0.5.15) via RDP (TCP port 3389) from their home office. For security, you might want to expose RDP on a non-standard public port (e.g., TCP 33389) while the internal server listens on the standard 3389. -
How DNAT Solves It:
-
A DNAT rule translates incoming connections on public IP
203.0.113.25and port33389to the internal server's IP10.0.5.15and port3389. - This involves both IP address translation and port translation (Port Address Translation - PAT, a form of DNAT).
-
A DNAT rule translates incoming connections on public IP
-
Original Destination:
IP
203.0.113.25, Port33389 -
Translated Destination:
IP
10.0.5.15, Port3389
Gotcha! (Palo Alto Networks): When exposing services like RDP, always ensure your Security Policies are as restrictive as possible (e.g., limit source IPs if feasible, apply strong authentication, and use Threat Prevention profiles). Exposing RDP directly to the internet, even with DNAT, is a significant security risk if not properly secured. -
Scenario:
An administrator needs to access an internal Windows server (e.g.,
-
Mapping Different Public Ports to Different Internal Servers/Services on the Same Public IP:
-
Scenario:
You have only one public IP address (e.g.,
203.0.113.30) but need to host multiple services. For example, a web server on port 80, an FTP server on port 21, and a custom application on port 9000. -
How DNAT Solves It:
Multiple DNAT rules are created, each mapping a specific public port on the shared public IP to a different internal server or service.
-
Rule 1:
203.0.113.30:80(public) ->192.168.1.10:80(internal web server) -
Rule 2:
203.0.113.30:21(public) ->192.168.1.11:21(internal FTP server) -
Rule 3:
203.0.113.30:9000(public) ->192.168.1.12:8080(internal custom app, with port translation)
-
Rule 1:
-
Original Destination:
IP
203.0.113.30, Ports80, 21, 9000(handled by separate rules) -
Translated Destination:
IPs
192.168.1.10, 192.168.1.11, 192.168.1.12, Ports80, 21, 8080respectively
-
Scenario:
You have only one public IP address (e.g.,
-
Basic Load Distribution to Multiple Internal Servers (Static Round Robin-like behavior with Dynamic IP Translation):
-
Scenario:
You have two identical web servers (
10.1.1.100and10.1.1.101) and want to distribute incoming web traffic from public IP203.0.113.40to them. While Palo Alto Networks offers more advanced load balancing features, a simple form of distribution can be achieved with DNAT. -
How DNAT Solves It:
A DNAT rule is configured using "Dynamic IP" as the translated address type, with a pool containing the IPs of the internal servers.
- When "Dynamic IP" is used in DNAT, PAN-OS can distribute new sessions across the IPs in the pool. Note: This is not true session-based load balancing with health checks. It's a simpler distribution. For robust load balancing, dedicated solutions or the firewall's more advanced features should be considered.
-
Original Destination:
IP
203.0.113.40, Port80/443 -
Translated Destination:
Pool containing
10.1.1.100and10.1.1.101, Port80/443. New sessions are assigned to an IP from the pool.
PCNSE/PCNSA Exam Note (Palo Alto Networks): While DNAT can use a pool of translated addresses (Dynamic IP), this is less common for typical DNAT scenarios compared to "Static IP" translation. Be clear on when "Static IP" vs. "Dynamic IP" translated types are used in NAT policies. DIPP is almost exclusively for Source NAT. -
Scenario:
You have two identical web servers (
-
U-Turn NAT: Accessing an Internal Server using its Public IP from the Internal Network
-
Scenario:
Internal users (e.g., in the "Trust" zone) need to access an internal server (e.g., in the "DMZ" zone) using its public FQDN or IP address (e.g.,
www.example.comwhich resolves to203.0.113.50). Without U-Turn NAT, this traffic might be hairpinned by an upstream router or blocked if internal routing doesn't allow it. -
How DNAT Solves It (in conjunction with SNAT):
U-Turn NAT is a combination of DNAT and SNAT.
-
An internal client (
192.168.1.50) tries to connect to203.0.113.50. -
A DNAT rule translates the destination
203.0.113.50to the server's private IP (e.g.,10.10.10.5). -
Crucially, a
second NAT rule (SNAT)
is needed to translate the source IP of the internal client (
192.168.1.50) to an IP address on the firewall (often the firewall's interface IP in the server's zone, e.g.,10.10.10.1). This ensures the server sends return traffic back to the firewall, which can then perform the reverse NAT and send it to the client. Without this SNAT, the server would see the original internal client IP and might try to respond directly, bypassing the firewall for the return path and breaking the session.
-
An internal client (
-
Original Client Request:
Source
192.168.1.50, Destination203.0.113.50 -
After DNAT:
Source
192.168.1.50, Destination10.10.10.5 -
After SNAT (U-Turn):
Source
10.10.10.1(firewall IP), Destination10.10.10.5
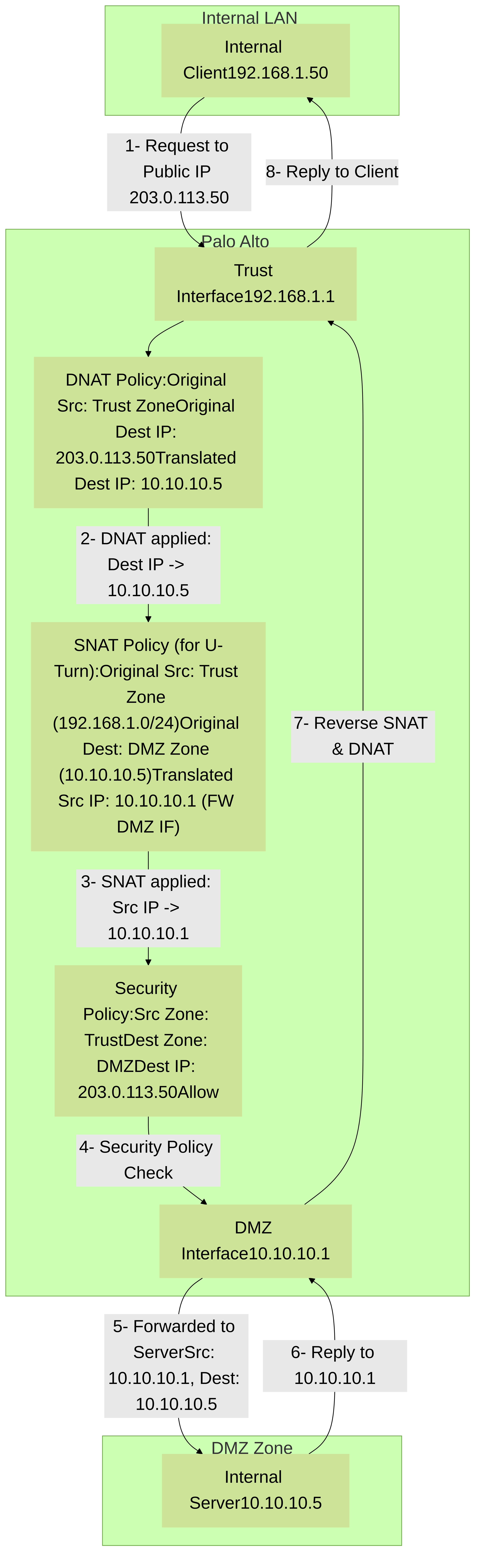
Simplified U-Turn NAT flow. An internal client accesses an internal server using its public IP. Both DNAT and SNAT are required for the session to establish correctly through the firewall.
-
Scenario:
Internal users (e.g., in the "Trust" zone) need to access an internal server (e.g., in the "DMZ" zone) using its public FQDN or IP address (e.g.,
3. Configuration Details and Steps (GUI & CLI)
Configuring Destination NAT on a Palo Alto Networks firewall is primarily done through NAT Policy rules.NAT Policy Configuration (GUI Focus)
Navigate to **Policies > NAT** in the PAN-OS GUI. NAT rules are evaluated top-down, like Security policies.Steps to Configure a Destination NAT Policy:
- Click **"Add"** at the bottom of the NAT Policy page.
- The NAT Policy Rule window opens. Configure the following tabs:
A. General Tab:
-
Name:
Assign a descriptive name (e.g.,
DNAT_WebServer_Public_to_DMZ). - Description: (Optional) Add more details about the rule's purpose.
-
NAT Type:
For DNAT, this is typically
ipv4(ornat64/ipv6if dealing with IPv6 transitions). - Tags: (Optional) For organization and filtering.
B. Original Packet Tab: This tab defines the characteristics of the incoming packet that will trigger this NAT rule.
- Source Zone: The zone from which the traffic originates. For internet-facing services, this is typically your "Untrust" zone (or any zone representing external networks). You can select "any" but being specific is better.
-
Destination Zone:
This is the zone the packet is
initially
destined for, based on the firewall's routing table lookup for the
original
destination IP address. For DNAT, this is typically the zone of the external interface receiving the traffic (e.g., "Untrust" if the public IP is on an Untrust interface).
PCNSE/PCNSA Exam Note (Palo Alto Networks): The Destination Zone in the NAT policy's Original Packet tab is critical. It's the zone where the original destination IP address (public IP) resides or would be routed to before NAT. This differs from the Destination Zone in the Security Policy for the same traffic.
-
Destination Interface:
The physical or logical interface on which the packet arrives. You can specify a particular interface (e.g.,
ethernet1/1) or leave it as "any". Specifying the interface can be more secure and precise. -
Service:
The original L4 service (port and protocol) the client is trying to reach. E.g.,
service-http(TCP/80),service-https(TCP/443), or a custom service object. - Source Address: The original source IP address(es) of the client. Often set to "any" for public services, but can be restricted to specific IPs or regions for enhanced security.
- Destination Address: This is the key field for DNAT . It's the original public IP address that external clients are connecting to and that you want to NAT. This should be an Address Object representing your public IP.
C. Translated Packet Tab: This tab defines how the packet's destination (and sometimes source for bi-directional) is modified.
-
Destination Address Translation:
-
Translation Type:
-
Static IP:
This is the most common type for DNAT. It translates the original destination IP to a single, specific internal IP address.
- Translated Address: The private IP address of the internal server. This can be an Address Object.
- Translated Port: (Optional) If you need to translate the destination port (e.g., public port 8080 to internal port 80), specify the new port number here. If left blank, the port is not translated.
- Dynamic IP and Port (DIPP): This type is primarily used for Source NAT to translate multiple private IPs to a single public IP with port translation to differentiate sessions. It's generally not the primary choice for typical Destination NAT use cases that map a public IP to an internal server. If selected for destination translation, it implies translating to one IP from a pool, potentially with port mapping, but "Dynamic IP" is usually more straightforward for pool-based DNAT.
-
Dynamic IP:
Less common for traditional one-to-one DNAT but can be used to translate the original destination IP to an IP address selected from a pool of internal IP addresses (e.g., for basic round-robin distribution to multiple backend servers without a dedicated load balancer).
- Translated Address: An Address Object of type "IP Range" or "FQDN" representing the pool of internal IPs.
- Distribution: PAN-OS offers algorithms like round-robin for distributing sessions among the IPs in the pool.
- None: (Not used for DNAT if destination address translation is the goal)
-
Static IP:
This is the most common type for DNAT. It translates the original destination IP to a single, specific internal IP address.
-
Translation Type:
-
Source Address Translation (Bi-directional NAT):
-
Enable Bi-directional:
Check this box if you want the firewall to automatically create a corresponding SNAT rule for traffic initiated
from
the translated internal server
to
the original external client.
-
Use Case:
Useful if the internal server needs to initiate connections back to the original client using its public IP address as the source IP. For example, if an external client at
1.2.3.4connects to your public server IP203.0.113.10(DNATted to192.168.1.100), and then192.168.1.100needs to initiate a new connection back to1.2.3.4, bi-directional NAT would make192.168.1.100appear as if it's coming from203.0.113.10. -
How it works:
When bi-directional NAT is enabled on a DNAT rule where
Public_IP:Port_Ais translated toPrivate_IP:Port_B, it implies that ifPrivate_IPinitiates traffic to the original source of the DNATted flow, its sourcePrivate_IP:Port_Bwill be translated toPublic_IP:Port_A. - Consideration: Many DNAT scenarios do not require bi-directional NAT, as the return traffic for the initial connection is handled by the session table state. Enable it only if the specific "server initiates back" scenario is required. If you just need the internal server to access the internet generally, a separate, broader SNAT rule is typically used.
Gotcha! (Palo Alto Networks): Bi-directional NAT creates a very specific SNAT. If your internal server needs to initiate connections to other external destinations (not just the original client of the DNAT flow), a separate, more general SNAT rule will be needed for those outbound connections. Bi-directional NAT is not a replacement for general outbound SNAT for the server. -
Use Case:
Useful if the internal server needs to initiate connections back to the original client using its public IP address as the source IP. For example, if an external client at
-
Enable Bi-directional:
Check this box if you want the firewall to automatically create a corresponding SNAT rule for traffic initiated
from
the translated internal server
to
the original external client.
Once configured, click **"OK"** and then **"Commit"** the changes to the firewall.
CLI Equivalents (Brief Overview)
While GUI is preferred for configuration, CLI can be used for verification and advanced troubleshooting. Configuring complex NAT rules via CLI is less common but possible.
Example: Viewing NAT rules (PAN-OS CLI in configuration mode)
# In configuration mode show rulebase nat
Example: Creating a very basic Static DNAT rule (conceptual CLI structure, syntax may vary slightly based on PAN-OS version and specific parameters). This is more complex to do fully via CLI compared to GUI.
# In configuration mode set rulebase nat rules <RULE_NAME> from <SOURCE_ZONE> set rulebase nat rules <RULE_NAME> source <SOURCE_IP_OBJECT_OR_ANY> set rulebase nat rules <RULE_NAME> to <DESTINATION_ZONE_OF_PUBLIC_IP> set rulebase nat rules <RULE_NAME> destination <PUBLIC_IP_OBJECT> set rulebase nat rules <RULE_NAME> service <SERVICE_OBJECT_OR_ANY> set rulebase nat rules <RULE_NAME> to-interface <INCOMING_INTERFACE_OR_ANY> set rulebase nat rules <RULE_NAME> description "My DNAT Rule" set rulebase nat rules <RULE_NAME> destination-translation translated-address <PRIVATE_IP_OBJECT> set rulebase nat rules <RULE_NAME> destination-translation translated-type static-ip # For port translation (optional): # set rulebase nat rules <RULE_NAME> destination-translation translated-port <PORT_NUMBER> # For bi-directional (optional): # set rulebase nat rules <RULE_NAME> bi-directional yes
The `set` commands are used in configuration mode. Use `show` commands in operational mode to view status.
Considerations for Dynamic IP Translated Addresses (for DNAT)
As mentioned, using "Dynamic IP" for the translated address in a DNAT rule means the firewall will pick an IP from a configured pool of internal addresses for new incoming sessions. This can provide a rudimentary form of load distribution or resiliency if one server in the pool goes down (though without health checks, traffic might still be sent to a down server until sessions time out).
- Pool Configuration: The "Translated Address" field would point to an Address Object of type "IP Range" or multiple individual Address objects grouped together.
- Distribution Algorithm: PAN-OS typically uses a round-robin or similar algorithm to pick an IP from the pool for new sessions. Session stickiness (sending traffic from the same client to the same server) is generally maintained for the life of the session once established.
- Use Cases: Suitable for stateless applications or when simple distribution is acceptable. Not a replacement for intelligent load balancers for critical applications.
- Security Policy: The Security Policy destination would still be the original public IP, and the destination zone would be the zone containing the pool of servers.
4. Security Policy Interaction
Understanding how Destination NAT policies interact with Security policies is one of the most critical aspects of configuring a Palo Alto Networks firewall and a common point of confusion.For traffic undergoing Destination NAT (e.g., an external user accessing an internal server):
- NAT Policy Evaluation: Happens before Security Policy evaluation for the first packet of a new session.
-
Security Policy Configuration:
- Source Zone: The zone where the original request originates (e.g., "Untrust").
- Source Address: The original source IP of the client (or "any").
- Destination Zone: The zone where the server actually resides after NAT (e.g., "DMZ", "Trust"). This is the post-NAT destination zone .
- Destination Address: The original public IP address that the client was trying to reach (the pre-NAT destination IP ). The firewall performs the NAT lookup first, identifies the translation, but for the security policy match, it uses the destination IP as it appeared *before* translation.
-
Application/Service:
The application or service the client is requesting (e.g.,
ssl,web-browsing, or the specific service object for the original port).
Clear Example:
-
Public IP:
203.0.113.50(on firewall's Untrust interface, zone "Untrust") -
DNAT Rule: Translates
203.0.113.50(port 443) to internal server192.168.1.100(port 443) which resides in the "DMZ" zone. -
External Client IP:
198.51.100.10
The corresponding Security Policy rule should be:
- Name: Allow_External_to_WebServer_DMZ
- Source Zone: Untrust
-
Source Address:
198.51.100.10(or "any", or a geo-object) -
Destination Zone: DMZ
(This is the zone where the server
192.168.1.100is located) - Destination Address: 203.0.113.50 (This is the public IP address the client originally targeted)
- Application: ssl (or web-browsing if App-ID is used)
- Service: service-https (TCP/443)
- Action: Allow
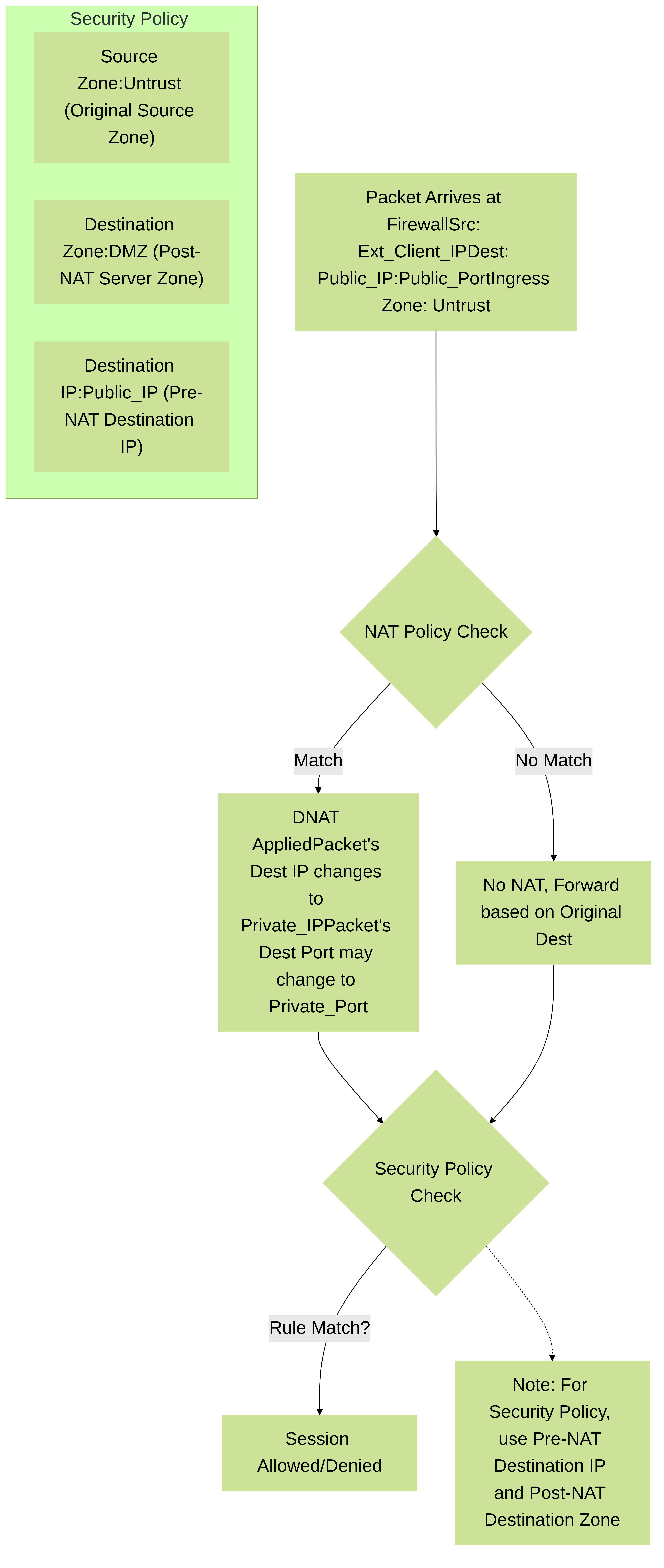
Diagram illustrating the interaction between NAT and Security Policies. For inbound DNAT traffic, the Security Policy uses the original (pre-NAT) destination IP address but the final (post-NAT) destination zone.
5. Best Practices for Destination NAT Configuration
Adhering to best practices ensures your DNAT configurations are secure, efficient, and maintainable.-
Be Specific with Original Destination IPs:
- Instead of using "any" for the "Destination Address" in the Original Packet tab of your NAT rule, always specify the exact public IP address(es) that are being NATted. This prevents unintended NATting of other traffic.
-
Service Specificity:
- In the "Service" field of the Original Packet tab, define the specific service(s) (e.g., TCP/80, TCP/443, TCP/3389) that should trigger the DNAT rule. Avoid using "any" or "application-default" unless absolutely necessary and fully understood. This limits the attack surface.
-
Security Policy Alignment:
- Always create or verify a corresponding Security Policy rule that allows the intended traffic post-NAT. Remember the "Pre-NAT Destination IP, Post-NAT Destination Zone" rule for Security policies.
- Apply appropriate Security Profiles (Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, WildFire) to the allowing Security Policy rule to inspect the DNATted traffic.
-
Naming Conventions:
-
Use clear and consistent naming conventions for NAT rules, Address Objects, and Service Objects. For example:
dnat_WebServer_Ext_to_DMZ,addr_Public_WebServer_IP,addr_Private_WebServer_IP. This greatly improves readability and troubleshooting.
-
Use clear and consistent naming conventions for NAT rules, Address Objects, and Service Objects. For example:
-
Regularly Review and Audit NAT Rules:
- Periodically review your NAT rulebase to remove outdated or unnecessary rules. Unneeded NAT rules, especially DNAT, can pose security risks if they expose internal systems unintentionally.
-
Use FQDN Objects for Translated Addresses Cautiously:
- While you can use FQDN address objects for the "Translated Address" (internal server), be aware of DNS resolution dependencies. The firewall must be able to resolve the FQDN to an IP address. IP address objects are generally more reliable for the translated server IP unless the server's IP changes frequently and DNS is always up-to-date. If an FQDN resolves to multiple IPs, behavior might vary based on PAN-OS version and context (it might use the first resolved IP or a set).
-
Logging and Monitoring NAT Rule Hits:
- While NAT rules themselves don't have direct logging options like Security policies, you monitor their usage by checking session logs (which show NAT applied) and traffic logs (which show security policy hits associated with NATted flows). You can also use the `show counter global filter aspect nat` CLI command to see NAT rule hit counts. For Panorama, log forwarding from firewalls provides centralized visibility.
-
Limit Source Addresses When Possible:
- In the "Source Address" field of the Original Packet tab in the NAT rule (and corresponding Security Policy), if access to the internal service should be restricted to specific external IPs or regions, configure this accordingly. This reduces exposure.
-
Consider Bi-Directional NAT Carefully:
- Only enable bi-directional NAT if there's a specific requirement for the internal server to initiate traffic back to the original external client using the public IP as its source. For general outbound internet access from the server, use a separate SNAT rule.
-
Zone and Interface Specificity:
- Be specific with Source Zone, Destination Zone (original), and Destination Interface in the NAT rule to ensure it only applies to traffic from expected sources and arriving on expected interfaces.
6. Troubleshooting Common Destination NAT Issues
Troubleshooting DNAT involves checking configurations, logs, and packet flows.-
Problem: Connection Fails - Traffic Not Reaching Internal Server
-
Incorrect Security Policy:
- Symptom: Traffic logs show "deny" or "drop" by the default deny rule or an explicit block rule. Session table might show no session or session in DISCARD state.
-
Troubleshooting:
- Verify the Security Policy uses the pre-NAT (public) destination IP and the post-NAT (internal server's) destination zone .
- Ensure the service/application in the Security Policy matches the traffic.
- Check source zone/address in the Security Policy.
- Look at Traffic logs (Monitor > Logs > Traffic) filtering by the public IP and port.
-
NAT Rule Not Matching:
- Symptom: External client cannot connect. Traffic logs might show traffic hitting the public IP but no NAT applied in session details, or the session fails.
-
Troubleshooting:
-
Use the CLI command:
test nat-policy-match source <client_ip> destination <public_ip> protocol <tcp_or_udp_num> destination-port <public_port> source-zone <untrust_zone> destination-zone <untrust_zone_for_public_ip>. This command simulates packet flow and tells you which NAT rule (if any) would match.# Example: test nat-policy-match source 1.2.3.4 destination 203.0.113.10 protocol 6 destination-port 80 source-zone Untrust destination-zone Untrust - Verify all parameters in the "Original Packet" tab of the NAT rule: Source Zone, Destination Zone (of the public IP), Destination Interface, Service, Source Address, and especially Destination Address (public IP). A mismatch in any of these can cause the rule not to trigger.
- Check NAT rule order. A more general rule above your specific DNAT rule might be matching first.
-
Use the CLI command:
-
Translated IP/Port Incorrect or Service Not Listening on Internal Server:
- Symptom: NAT is applied (visible in session details), Security Policy allows, but connection still fails or times out.
-
Troubleshooting:
- Verify the "Translated Address" and "Translated Port" in the NAT rule's "Translated Packet" tab are correct for the internal server.
- Ensure the internal server is actually listening on the translated IP and port. Use tools like `netstat` on the server.
- Check for any host-based firewalls on the internal server that might be blocking the connection.
- Perform a packet capture on the firewall (Monitor > Packet Capture) on the internal interface connecting to the server to see if packets are being sent to the server and if the server is responding.
-
Routing Issues for the Translated IP:
- Symptom: Firewall correctly NATs and forwards the packet, but the internal server cannot send return traffic back to the firewall, or the firewall cannot route to the internal server.
-
Troubleshooting:
- Ensure the internal server has a route back to the firewall for the source IP of the external client (or a default gateway pointing to the firewall's internal interface in the server's subnet). This is critical. If the server's gateway is not the Palo Alto Networks firewall, U-Turn NAT or Policy Based Forwarding might be needed for return traffic to ensure symmetry.
- Verify the firewall has a connected or static route to the subnet of the translated (internal server) IP address.
-
Session Table Shows Incorrect NAT Behavior:
- Symptom: Connection issues, unexpected behavior.
-
Troubleshooting:
-
Use the CLI command
show session id <session_id>to inspect a specific session. Look for "dst translated" or "src translated" flags and the translated IP/ports.# First, find the session ID, e.g., by destination IP: show session all filter destination-ip 203.0.113.10 destination-port 80 # Then view details: show session id 12345 -
If "
इफ्लक्स इंटरफ़ेस NAT है (is NAT-src)" or "एग्रेस इंटरफ़ेस NAT है (is NAT-dst)" flags are unexpected, it points to NAT rule issues.
-
Use the CLI command
-
Global NAT Counters:
- Symptom: Suspect NAT is not occurring at all or for specific rule.
-
Troubleshooting:
-
Use CLI:
show counter global filter aspect nat. This shows various NAT-related counters, including per-rule packet and session counts (if supported clearly for specific rules in your PAN-OS version - often more general counters). This can help determine if any NAT rule is being hit. -
debug nat-policy-matchcan provide verbose logging for NAT policy matching but is resource-intensive and should be used cautiously in production.
-
Use CLI:
-
Incorrect Security Policy:
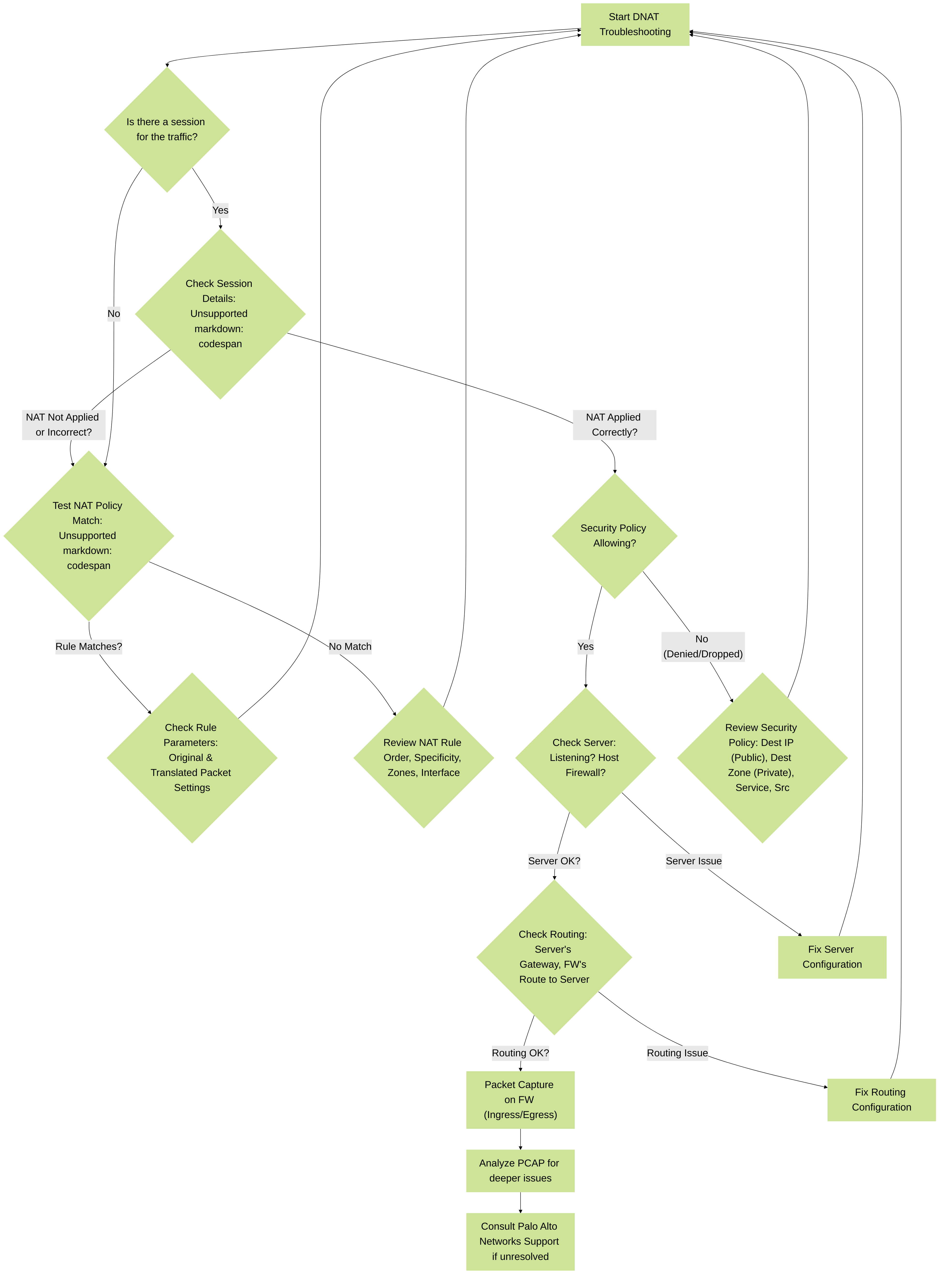
A decision tree for troubleshooting common Destination NAT issues on Palo Alto Networks firewalls.
7. Advanced Considerations
While the core DNAT concepts cover most scenarios, some advanced topics might arise:-
DNAT with High Availability (HA):
- In an HA active/passive pair, NAT policies are synchronized from the active to the passive firewall.
- If the public IP used in the DNAT rule is a floating IP managed by the HA pair, failover should be seamless for NATted sessions (depending on session sync settings and application behavior).
- If the public IP is an interface IP, ARP load sharing (for active/active) or MAC masquerading ensures the new active firewall can take over traffic for that IP. Session information for NATted connections is also synchronized.
-
DNAT and GlobalProtect:
- DNAT can be used to provide access to internal resources for GlobalProtect users. For instance, if GlobalProtect users are assigned IPs from a specific pool and need to access an internal server via a "friendly" IP or port, DNAT can be configured. The source zone in such a NAT rule would be the zone containing GlobalProtect users' traffic.
-
DNAT involving NAT64/NAT46:
- Palo Alto Networks firewalls support NAT64 (translating IPv6 client requests to IPv4 servers) and NAT46 (translating IPv4 client requests to IPv6 servers).
- If you have an IPv6-only client needing to access an IPv4-only internal server, a NAT64 policy (a type of NAT policy) performs the necessary IP and protocol translation. This is a specialized form of DNAT.
- Configuration involves defining NAT64 rules, potentially with DNS64 for hostname resolution.
-
Interaction with App-ID and User-ID:
-
App-ID:
Security policies allowing DNATted traffic can (and should) leverage App-ID. The application identification happens after NAT on the traffic flowing towards the internal server. The Security policy allowing the traffic would specify the application (e.g.,
ms-rdp,web-browsing,ssl). - User-ID: If the source users are known (e.g., internal users in a U-Turn NAT scenario, or specific remote users identified by User-ID methods like GlobalProtect or Captive Portal), User-ID can be used as a match criterion in the Security Policy that permits the DNATted traffic. For traffic from "any" on the internet, User-ID is typically not applicable for the initial inbound connection.
-
App-ID:
Security policies allowing DNATted traffic can (and should) leverage App-ID. The application identification happens after NAT on the traffic flowing towards the internal server. The Security policy allowing the traffic would specify the application (e.g.,
-
DNAT and FQDN Address Objects for Translated (Internal) Server:
-
Using an FQDN object (e.g.,
internalserver.corp.local) as the "Translated Address" in a DNAT rule is possible. The firewall will periodically resolve this FQDN to an IP address. -
Implications:
- The firewall needs reliable DNS resolution.
- Changes to the DNS record for the FQDN will be picked up by the firewall after its DNS cache for that entry expires and it re-resolves. There can be a delay.
- If the FQDN resolves to multiple IP addresses, the firewall typically uses the first IP address returned in the DNS response, or may use the set if the "Dynamic IP" translation type is used with an FQDN object representing a pool.
- Ensure the Time-To-Live (TTL) for the DNS record is appropriate for how quickly you need IP changes to propagate.
-
Using an FQDN object (e.g.,