Advanced Palo Alto Networks NAT Examples (PCNSE Focus)
Network Address Translation (NAT) is a core function of Palo Alto Networks firewalls, enabling communication between different addressing realms and facilitating secure access.
This article revisits NAT fundamentals and then dives into advanced use cases crucial for the PCNSE, such as U-Turn NAT, NAT with DNS considerations, handling overlapping IP spaces with NAT, and bi-directional translation. We will explore configuration nuances and the critical relationship between NAT and Security policies, referencing official Palo Alto Networks documentation throughout.
NAT Basics Recap: Types of NAT
Before diving into advanced scenarios, let's quickly recap the fundamental NAT types available in PAN-OS:
-
Source NAT (SNAT):
Translates the source IP address (and potentially port). Primarily used for outbound traffic (internal users to external resources).
- Dynamic IP and Port (DIPP/PAT): Many-to-one or many-to-few mapping using port translation. Most common type for internet access. Can use interface IPs or pools.
- Dynamic IP (DIP): Many-to-many mapping using a pool of IPs, preserving the original source port. Requires a sufficient pool size.
- Static IP: One-to-one mapping of a specific internal source IP to a specific translated source IP.
-
Destination NAT (DNAT):
Translates the destination IP address (and potentially port). Primarily used for inbound traffic (external users to internal resources).
- Static IP: One-to-one mapping of a public destination IP to a private internal server IP. Optionally translates the port (Port Forwarding). Used for publishing services.
- No NAT: Explicitly bypasses NAT for matching traffic. Crucial for excluding specific flows from broader NAT rules.
- Bi-Directional NAT: A configuration shortcut using a Static Source NAT rule with the "Bi-directional" option checked to create both the SNAT and corresponding DNAT mappings simultaneously.
NAT Basics Recap: Policy Structure & Order
NAT rules are configured under Policies > NAT and evaluated sequentially.
Key Components of a NAT Rule:
- General Tab: Name, Description, Tags, Rule Enable/Disable.
-
Original Packet Tab:
Defines the traffic to match.
- Source/Destination Zones (based on original IP route lookup)
- Destination Interface (optional, adds specificity)
- Service (TCP/UDP port, application, etc.)
- Source/Destination Addresses (pre-NAT IPs)
-
Translated Packet Tab:
Defines the translation action.
- Source Address Translation (Type: None, DIPP, DIP, Static; Translated Address: Interface IP, Pool object)
- Destination Address Translation (Type: Static; Translated Address/Port)
- DNS Rewrite Option (for DNAT Static)
- Bi-directional Option (for SNAT Static)
Rule Order:
- Processed Top-Down .
- First rule that fully matches the packet is applied.
- No further NAT rules are evaluated for that session.
- Critical: More specific rules (e.g., No NAT for server-to-server, Static NAT for a specific server) MUST be placed ABOVE general rules (e.g., DIPP for all internal subnets to Internet).
NAT Basics Recap: Packet Flow & Security Policy Interaction
The precise interaction between NAT and Security Policy evaluation within the packet flow is a cornerstone of PAN-OS operation and vital for the PCNSE.
Simplified Packet Flow (First Packet / Slow Path):
- Ingress & Initial Route Lookup: Packet arrives, source zone determined. Route lookup based on original destination IP determines initial destination zone.
- NAT Policy Lookup: Evaluated top-down based on original packet attributes (Zones, IPs, Service).
- Potential Second Route Lookup (DNAT): If a DNAT rule matches, a second route lookup occurs using the translated destination IP . This determines the final destination zone used for Security Policy lookup.
-
Security Policy Lookup:
Evaluated top-down.
- Matches on Pre-NAT (Original) Source and Destination IP Addresses.
- Matches on Post-NAT (Final) Destination Zone.
- Matches on Source Zone (from ingress).
- Session Installation: If allowed by Security Policy, session created, including NAT translation details if applicable.
- Egress & Translation Application: Packet forwarded. Actual IP/port modification occurs at egress based on the matched NAT rule.
NAT Basics Recap: DIPP & Oversubscription
Dynamic IP and Port (DIPP), also known as Port Address Translation (PAT), is essential for conserving public IP addresses.
- Mechanism: Translates both source IP and source port, allowing multiple internal hosts to share one or a few public IPs. The firewall maintains a session table mapping unique internal [IP:Port] pairs to unique translated [IP:Port] pairs.
- Port Exhaustion: A single translated IP has ~64k usable ports. High session volume can exhaust available ports, leading to connection failures.
-
DIPP Oversubscription:
Allows the firewall to reuse the same translated IP:Port pair for multiple concurrent sessions, provided the full 5-tuple (SrcIP, SrcPort, DstIP, DstPort, Proto) is unique for each session.
-
Configured globally:
Device > Setup > Session > Session Settings > NAT Oversubscription Rate. - Rates (model dependent): 1x (off), 2x, 4x, 8x.
- Increases session capacity but consumes more memory.
-
Configured globally:
- Translated IP Limit: A single NAT rule can only reference up to 256 translated IPs. Larger pools require multiple rules.
Advanced NAT Scenario: U-Turn NAT
U-Turn NAT enables an internal client to access an internal server using the server's external public IP address (or an FQDN resolving to it). This is needed when internal users need to reach internal resources the same way external users do.
Configuration Steps & Considerations
-
Destination NAT Rule (Mandatory):
Translates the public destination IP back to the server's private IP.
- Original Packet: Source Zone (Client Zone), Destination Zone (Zone associated with Public IP, usually Untrust), Destination IP (Server Public IP).
- Translated Packet: Destination Address Translation (Server Private IP).
-
Source NAT Rule (Conditional - Usually Needed if Client/Server in SAME Zone):
Translates the client's source IP to the firewall's interface IP in the server's zone to ensure symmetric routing.
- Original Packet: Same as DNAT rule above.
- Translated Packet: Source Address Translation (Type: DIPP, Interface Address: Firewall Interface in Server's Zone).
-
Security Policy Rule:
Allows traffic based on "Pre-NAT IP, Post-NAT Zone".
- Source Zone: Client Zone.
- Destination Zone: Server's Actual Zone (Post-DNAT).
- Source Address: Client IP/Subnet.
- Destination Address: Server's Public IP (Pre-NAT).
- Action: Allow.
- Rule Order: U-Turn NAT rule(s) must be placed above general outbound SNAT rules.
Example: Client and Server in Different Zones (Trust/DMZ)
- Client: 192.168.1.10 (Trust)
- Server: 10.10.10.50 (DMZ)
- Server Public IP: 203.0.113.5 (Untrust)
Required Config:
- DNAT Rule: Orig: SrcZone Trust, DstZone Untrust, DstIP 203.0.113.5; Translated: DstIP 10.10.10.50. (SNAT likely not needed here in the U-Turn rule itself).
- Security Rule: SrcZone Trust, SrcIP 192.168.1.10, DstZone DMZ, DstIP 203.0.113.5, Action Allow.
- Place DNAT rule above any general SNAT rule for 192.168.1.10.
Example: Client and Server in Same Zone (Trust)
- Client: 192.168.1.10 (Trust)
- Server: 192.168.1.50 (Trust)
- Server Public IP: 203.0.113.5 (Untrust)
- Firewall Trust IP: 192.168.1.1
Required Config:
- U-Turn NAT Rule (Combined DNAT+SNAT): Orig: SrcZone Trust, DstZone Untrust, DstIP 203.0.113.5; Translated: SNAT Type DIPP, Interface 192.168.1.1; DNAT DstIP 192.168.1.50.
- Security Rule: SrcZone Trust, SrcIP 192.168.1.10, DstZone Trust, DstIP 203.0.113.5, Action Allow. (Default intrazone might allow, but explicit is better).
- Place U-Turn NAT rule above any general SNAT rule for 192.168.1.10.
Advanced NAT Scenario: NAT and DNS Rewrite
Using DNAT to publish servers can cause issues when internal clients resolve the server's FQDN. Depending on the DNS server used (internal/external) and its records, the client might receive the server's private IP (bypassing the firewall) or its public IP (requiring U-Turn NAT). PAN-OS DNS Rewrite , configured on DNAT rules, solves this "split-DNS" issue.
How DNS Rewrite Works
The firewall inspects DNS responses. If the IP address in the response matches the Original or Translated Destination IP in a DNAT rule with DNS Rewrite enabled, the firewall modifies the response IP before sending it to the client.
- Forward Direction: Rewrites the Public IP (Original Destination) in the DNS response to the Private IP (Translated Destination). Use case: Internal client queries an internal DNS server holding the public 'A' record. This allows the client to connect directly to the private IP.
- Reverse Direction: Rewrites the Private IP (Translated Destination) in the DNS response to the Public IP (Original Destination). Use case: Internal client queries an external DNS server which incorrectly returns the private IP. This ensures the client targets the correct public IP for DNAT.
Configuration is done on the Translated Packet tab of the DNAT Static IP rule.
Example: DNS Rewrite (Forward)
- Client: 192.168.1.10 (Trust)
- Internal DNS: 192.168.1.5 (Trust), Record: `web.corp.com -> 203.0.113.88`
- Web Server: 10.1.1.88 (DMZ)
- Public IP: 203.0.113.88 (Untrust)
Config:
- DNAT Rule: Orig: SrcZone any, DstZone Untrust, DstIP 203.0.113.88; Translated: DstIP 10.1.1.88, DNS Rewrite: Forward .
- Flow: Client queries Internal DNS -> DNS replies 203.0.113.88 -> Firewall sees reply, matches DNAT rule, rewrites IP to 10.1.1.88 -> Client receives 10.1.1.88 -> Client connects directly to 10.1.1.88.
- Benefit: Avoids U-Turn NAT complexity. Requires Trust-to-DMZ security policy for 10.1.1.88.
Advanced NAT Scenario: NAT for Overlapping IP Subnets
When connecting networks that unfortunately use the same private IP address ranges (e.g., two companies using 192.168.1.0/24 connect via VPN), NAT can be used to create unique, non-overlapping "virtual" addresses for communication across the connection.
This typically involves creating both Source and Destination NAT rules on both sides of the connection.
Example: Site-to-Site VPN with Overlapping Subnets
- Your LAN: 192.168.1.0/24
- Partner LAN: 192.168.1.0/24
- Your Virtual Mapping for Partner: 10.10.1.0/24
- Partner's Virtual Mapping for You: 10.20.1.0/24
On Your Firewall:
-
SNAT Rule (Outbound to Partner):
- Original: Src: 192.168.1.0/24, Dst: 10.10.1.0/24 (Partner's Virtual)
- Translated: Source: 10.20.1.0/24 (or a specific IP like firewall interface in this range) , Dest: Unchanged
- Purpose: Makes your traffic appear to come from your unique virtual range.
-
DNAT Rule (Inbound from Partner):
- Original: Src: 10.10.1.0/24 (Partner's Virtual), Dst: 10.20.1.0/24 (Your Virtual)
- Translated: Source: Unchanged, Dest: 192.168.1.0/24
- Purpose: Translates traffic destined for your virtual range back to your real internal range.
- Routing & Security Policy: Based on the virtual/translated addresses (10.10.1.0/24 and 10.20.1.0/24).
The partner firewall configures the inverse NAT rules.
Advanced NAT Scenario: Bi-Directional NAT
Bi-directional NAT provides a convenient way to configure a 1:1 mapping for both source and destination translation using a single rule.
Use Case: An internal host (e.g., a specific server or device) must consistently use a specific public IP when initiating outbound connections, AND external hosts must be able to reach that internal host by targeting the same public IP.
Configuration
Instead of creating a Static SNAT rule and a separate Static DNAT rule, you configure only one rule:
- Create a NAT rule.
-
Original Packet:
- Source Zone: Server's Zone
- Source Address: Server's Private IP
- Destination Zone: Any zone the server might initiate traffic towards (e.g., Untrust)
- Destination Address: Any
-
Translated Packet:
- Source Address Translation Type: Static IP
- Translated Address: The desired Public IP
- Destination Address Translation: None
- Check the "Bi-directional" checkbox.
Checking "Bi-directional" implicitly creates the reverse DNAT mapping. Traffic originating externally destined for the "Translated Address" (the Public IP) will be destination NAT'd to the "Source Address" (the Server's Private IP) specified in the Original Packet tab.
NAT Basics Recap: IPv6 NAT (NAT64 / NPTv6)
PAN-OS supports specific NAT functionalities for IPv6 transition and connectivity:
- NAT64: Translates between IPv6 and IPv4 networks, allowing IPv6-only clients to reach IPv4-only servers. It involves translating both source (IPv6->IPv4 pool) and destination (IPv4->Synthesized IPv6 using a prefix like 64:ff9b::/96). Essential for migration phases.
- NPTv6 (Network Prefix Translation for IPv6): Performs a stateless, 1:1 translation of an IPv6 prefix while preserving the Interface ID (host portion). Defined in RFC 6296. Used for scenarios like ISP prefix changes or multi-homing without breaking end-to-end connectivity principles as much as stateful NAT would. Requires NDP Proxy.
Diagram: Sequence - Basic Packet Flow with NAT
Recapping the essential NAT and Security Policy evaluation sequence.
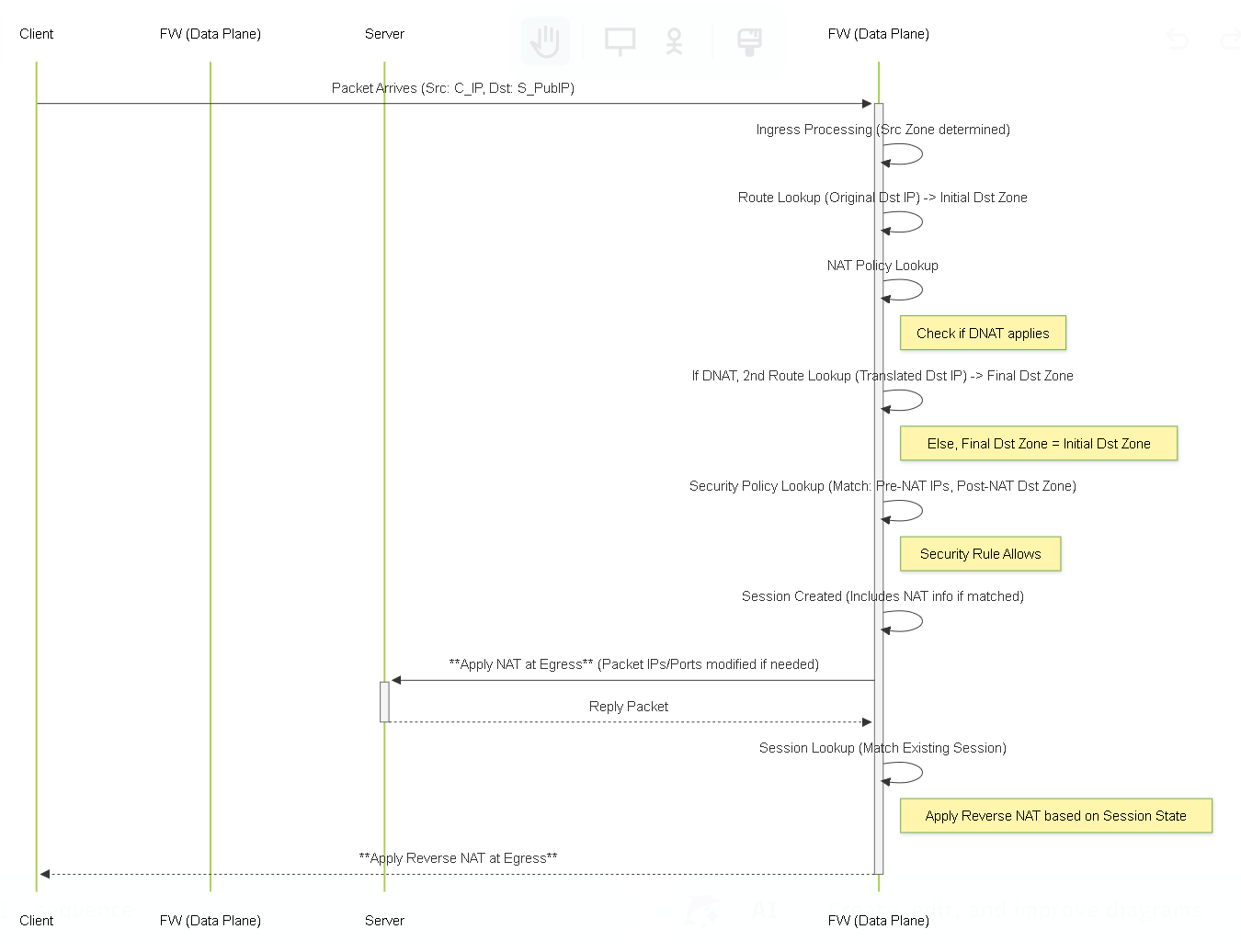
Sequence diagram highlighting the key stages: initial routing, NAT lookup, potential second routing (DNAT), Security lookup (Pre-NAT IP, Post-NAT Zone), and NAT application at egress.
Diagram: Flowchart - Simplified NAT Type Choice
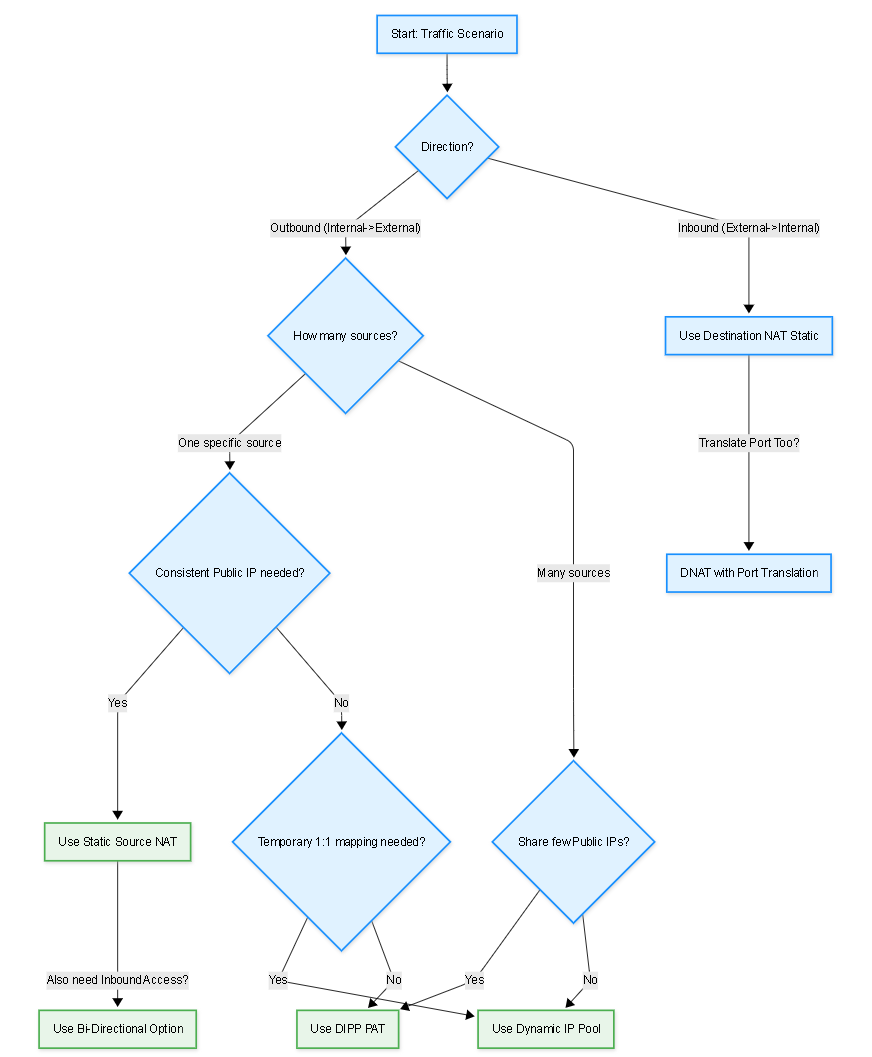
Flowchart providing a simplified decision path for selecting common IPv4 NAT types.
Diagram: Sequence - U-Turn NAT (Same Zone Example)
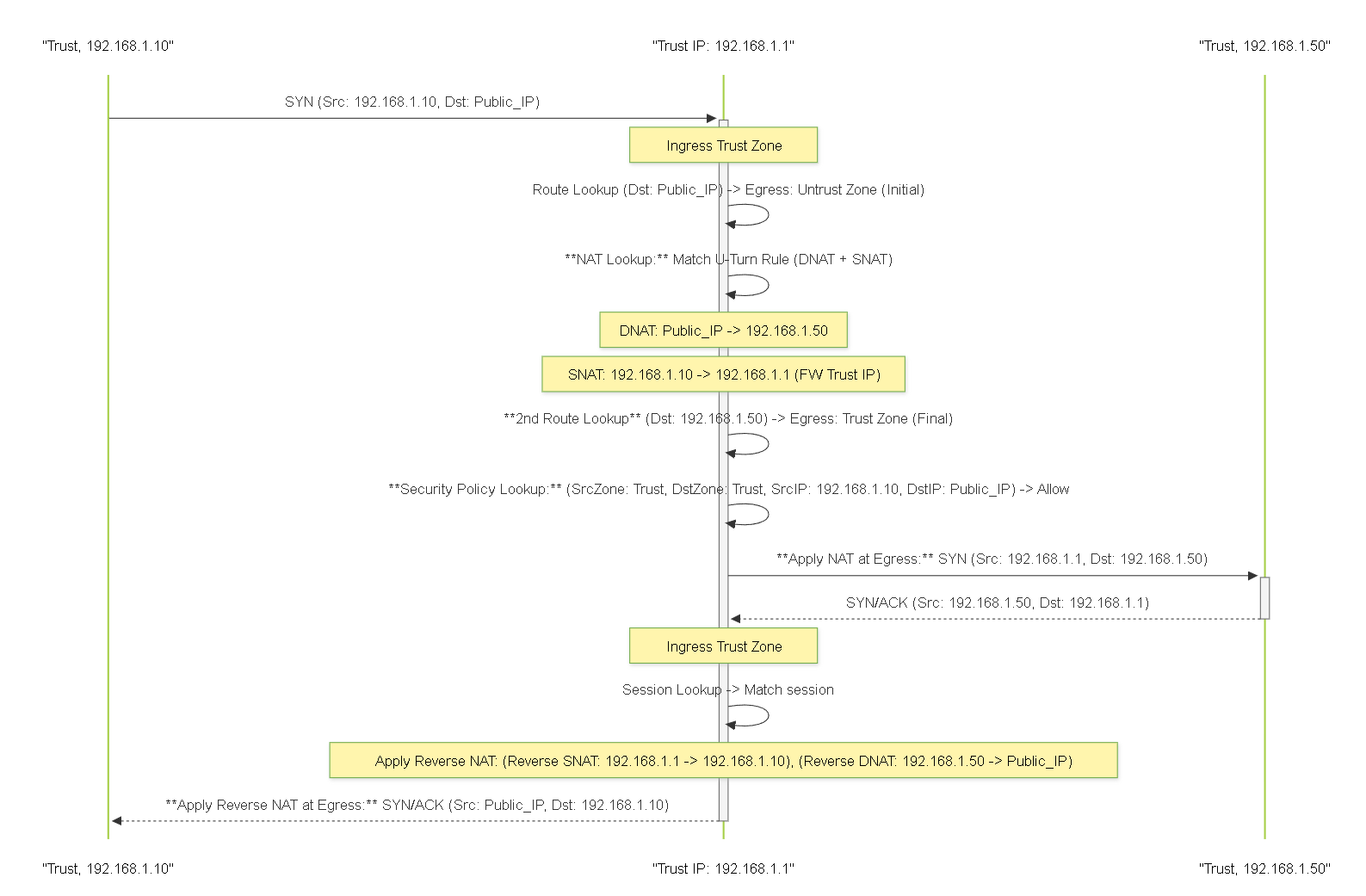
Sequence diagram for U-Turn NAT where Client and Server are in the same zone, showing the required SNAT step.
Diagram: Sequence - DNS Rewrite (Forward Example)
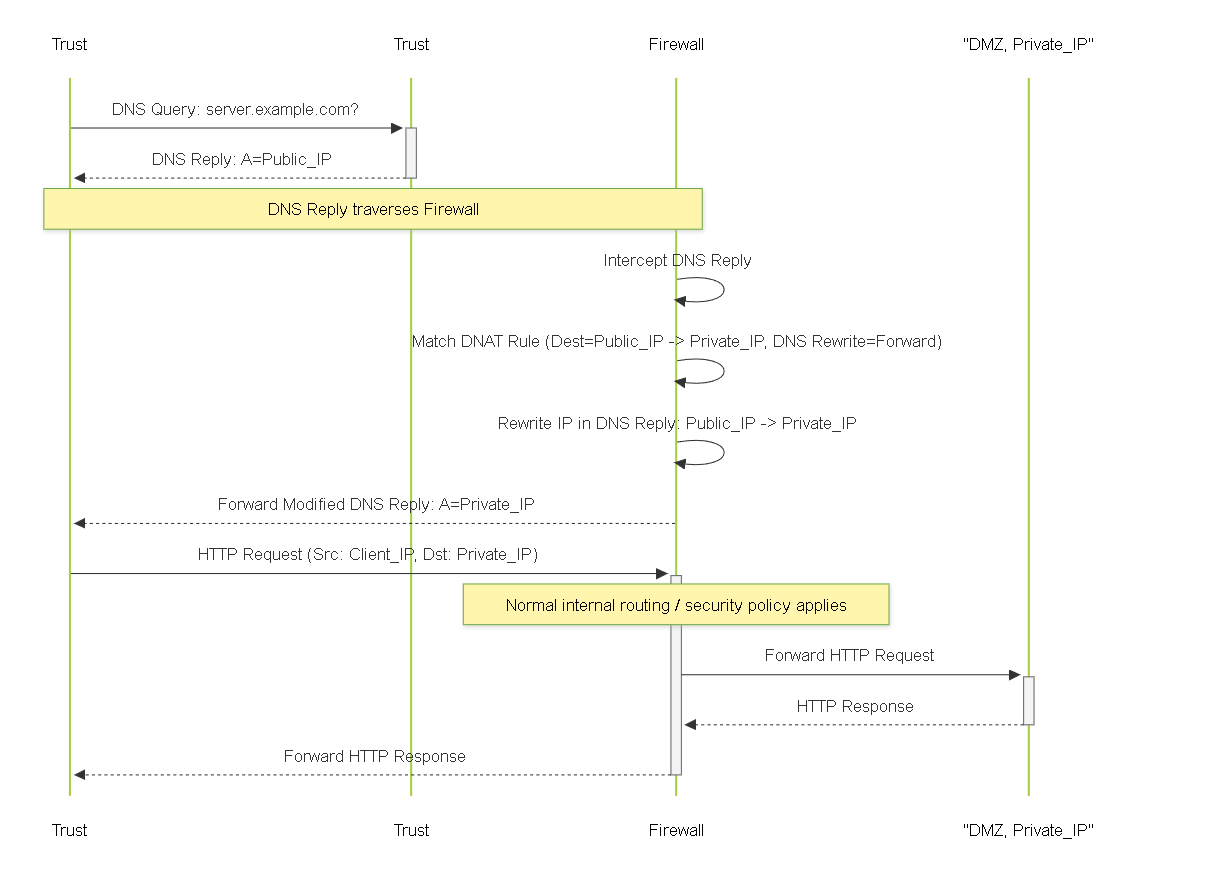
Sequence diagram showing DNS Rewrite (Forward) where the firewall modifies the DNS response from an internal server containing a public IP.
Diagram: Graph - NAT for Overlapping IPs
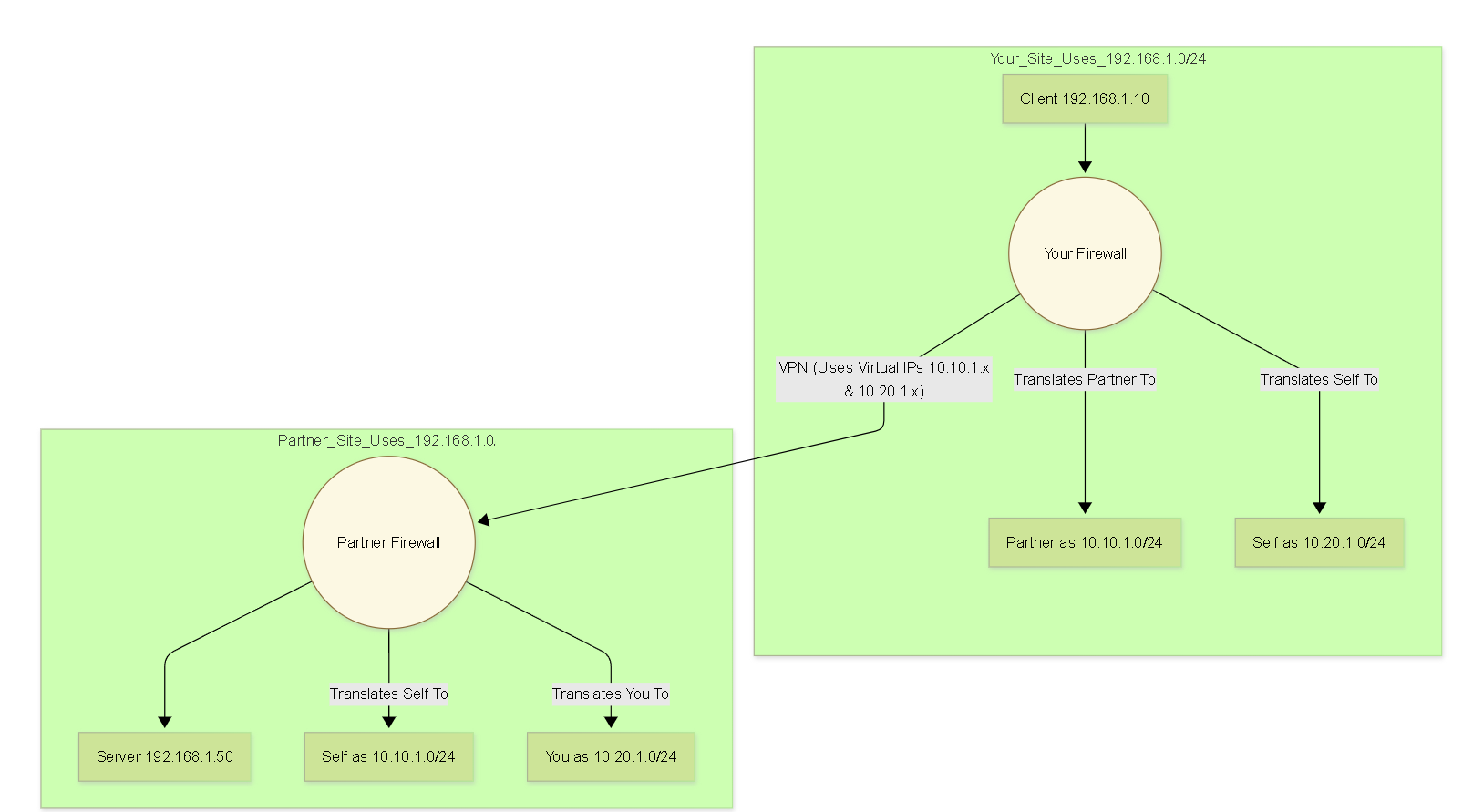
Conceptual graph showing how NAT creates distinct virtual address spaces (10.x.x.x) to allow communication between sites with overlapping internal IPs (192.168.1.x).
PCNSE Exam Focus Summary (Advanced NAT)
Key NAT areas emphasized for the PCNSE exam include:
- Packet Flow & Security Policy Interaction: The absolute core concept. Master "Pre-NAT IP, Post-NAT Zone" for Security Policy evaluation. Understand the timing of NAT evaluation vs. application and the second route lookup for DNAT.
- NAT Rule Logic and Order: Understand all components of Original and Translated Packet tabs. Know top-down, first-match processing and why specific rules (Static, No NAT, U-Turn) must precede general rules (DIPP).
- U-Turn NAT: Configuration requirements (DNAT always, SNAT conditional - especially same-zone), purpose, Security Policy rules, and rule placement.
- NAT & DNS Rewrite: Solve the split-DNS problem. Know the 'Forward' (Public->Private) and 'Reverse' (Private->Public) directions and when each applies based on DNS server location relative to the client. Configuration location (DNAT rule).
- NAT Types and Use Cases: Differentiate and apply SNAT (DIPP, DIP, Static), DNAT (Static, Port Forwarding), No NAT, and Bi-directional NAT based on scenario requirements.
- DIPP & Related Concepts: Oversubscription purpose and configuration, port exhaustion, interface IP vs. pool usage, 256 translated IP limit per rule.
- IPv6 NAT: Understand the roles of NAT64 and NPTv6.
- NAT for Overlapping IPs: Conceptual understanding of using paired SNAT/DNAT rules for translation, especially in VPNs.
PCNSE Style Quiz: Advanced NAT
Test your understanding with these 20 questions focused on advanced NAT scenarios: