Palo Alto Networks NAT Policies: PCNSE Essentials
Network Address Translation (NAT) is a fundamental concept in modern networking and a critical component of Palo Alto Networks firewall configuration.
NAT allows devices using private IP addresses (like those defined in RFC 1918) to communicate with external networks (like the internet) which use public IP addresses. This article focuses on the NAT concepts and configurations most relevant for PCNSE candidates.
IPv4 NAT Types in PAN-OS
PAN-OS supports several types of NAT to address various network requirements. Understanding the purpose and configuration of each is crucial.
-
Source NAT (SNAT):
Translates the
source IP address
(and potentially port) of packets, typically used for outbound traffic. This allows internal clients with private IPs to access external resources like the internet using a public IP address assigned by the firewall.
- Dynamic IP and Port (DIPP / PAT): This is the most common form of SNAT, often called Port Address Translation (PAT). It allows multiple internal hosts to share a single public IP address (or a pool of addresses) by translating both the source IP and source port number. The firewall maps each unique internal IP:Port combination to a unique translated IP:Port combination. It can use IP addresses from a defined pool or the IP address of the egress interface itself.
- Dynamic IP (DIP): Translates the source IP address to the next available IP address from a configured pool, but keeps the original source port unchanged. This provides a one-to-one mapping dynamically, but requires a pool of translated IPs at least as large as the number of concurrent hosts needing translation. If the pool is exhausted, new connections may be dropped unless DIPP fallback is enabled.
- Static IP: Creates a fixed, one-to-one mapping between a specific internal source IP address and a specific external source IP address. The source port is typically unchanged. This ensures a consistent translated source IP for a specific internal host.
-
Destination NAT (DNAT):
Translates the
destination IP address
(and potentially port) of packets, typically used for inbound traffic. This allows external clients to access internal servers (e.g., web servers, mail servers) hosted with private IP addresses.
- Static IP: Creates a fixed, one-to-one mapping between a specific public destination IP address and a specific internal private IP address. It can optionally translate the destination port (Port Forwarding). This is commonly used to publish internal services.
- Port Forwarding: A specific form of Static Destination NAT where the destination port is also translated (e.g., external port 8080 translates to internal server port 80).
- No NAT: An explicit configuration option within a NAT rule to specify that matching traffic should *not* undergo any NAT translation. This is useful for excluding specific traffic (e.g., internal-to-internal, specific servers) from broader NAT rules.
- U-Turn NAT: A specific scenario (not a distinct NAT type setting) where internal users access an internal server using its external, public IP address. This typically requires both a Destination NAT rule (to translate the public destination IP back to the private server IP) and potentially a Source NAT rule (so the server sees the traffic originating from the firewall's internal interface, allowing return traffic to flow correctly).
- Bi-Directional NAT: Achieved by configuring a Static Source NAT rule and checking the "Bi-directional" option. This simultaneously creates a corresponding Static Destination NAT mapping, useful when a specific internal host needs both a consistent outbound translated IP and needs to be reachable inbound via that same translated IP.
Dynamic IP and Port (DIPP) NAT Oversubscription
When using DIPP NAT, especially with a single translated IP address (like the egress interface IP), a potential issue is port exhaustion . A single IPv4 address has 65,535 possible TCP/UDP ports. When many internal clients initiate outbound connections, the firewall must assign a unique translated source port for each session originating from the shared public IP. In high-traffic environments, the available ports can be depleted, preventing new connections.
To mitigate this, PAN-OS implements DIPP NAT Oversubscription . This feature allows the firewall to reuse the same translated IP address and port combination multiple times for concurrent sessions, effectively multiplying the available session capacity.
Key Points about Oversubscription:
- Rates: The oversubscription rate can typically be set to 1x (no oversubscription), 2x, 4x, or 8x, depending on the firewall model. The default rate also varies by model.
- Global Setting: The oversubscription rate is a global setting configured under Device > Setup > Session > Session Settings .
- Resource Consumption: Higher oversubscription rates allow more concurrent sessions but consume more memory resources, even if the extra capacity isn't fully utilized.
- Trade-offs: Administrators can adjust the rate to balance scalability (supporting more users with fewer IPs) against resource consumption. Setting it to 1x disables oversubscription.
- Limit Interaction: If configuring a high oversubscription rate causes a single NAT rule to potentially exceed the 256 translated IP address limit, the firewall may automatically reduce the rate for that rule during commit.
Understanding the 256 Translated IP Addresses Limit per NAT Rule
A specific limitation within PAN-OS NAT configuration is that a single NAT policy rule can reference a maximum of 256 unique translated IP addresses in its translated packet definition. This applies to the pool of addresses configured for source or destination translation within that one rule.
Implications:
- Pool Size: If you define a NAT pool (e.g., using an Address Object of type IP Range or IP Netmask) for the 'Translated Address' field in a NAT rule, that pool cannot contain more than 256 individual IP addresses.
- Configuration Commit: If a rule attempts to define more than 256 translated IPs, the firewall might try to automatically reduce the configured DIPP oversubscription rate during commit to comply. However, if the number of IPs fundamentally exceeds 256, or if the total number of translated IPs across *all* NAT rules exceeds the platform's overall limit, the commit operation will fail.
- Workaround: If you need to utilize a pool larger than 256 public IPs for translation, you must split the pool across multiple NAT rules. For example, if you have 500 public IPs, you could create two NAT rules, each using a pool of 250 IPs, targeting the same original traffic.
Example:
An administrator needs to configure Source NAT for internal users using a public IP block of 203.0.113.0/23 (which contains 512 addresses). They cannot create a single NAT rule using 203.0.113.0/23 as the translated address pool.
Solution: Create two separate NAT rules:
- Rule 1: Matches the original traffic, translates using pool 203.0.113.0/24 (256 IPs).
- Rule 2: Matches the same original traffic, translates using pool 203.0.114.0/24 (256 IPs).
Place these rules adjacent to each other. The firewall will distribute sessions across the pools defined in these rules.
IPv6 NAT Support (NAT64 and NPTv6)
While IPv6 aims to reduce the need for NAT due to its vast address space, specific scenarios still require translation mechanisms, which PAN-OS supports.
- NAT64: Enables communication between IPv6-only clients and IPv4-only servers. It translates the source IPv6 address of the client into an IPv4 address (typically from a pool) and the destination IPv4 address of the server into a specific IPv6 format (often using a predefined prefix like 64:ff9b::/96 combined with the IPv4 address). This is a key technology for IPv6 transition phases.
- NPTv6 (Network Prefix Translation for IPv6): Defined in RFC 6296, NPTv6 provides a stateless 1:1 translation of IPv6 prefixes while keeping the host portion (interface identifier) of the address unchanged.
NAT Policy Configuration
NAT rules are configured under Policies > NAT in the PAN-OS web interface or via CLI.
Each NAT rule consists of two main parts:
-
Original Packet Tab:
Defines the traffic to be matched for potential translation. Key criteria include:
- Source Zone(s)
- Destination Zone
- Destination Interface (Optional, useful for specificity, especially with multiple paths/ISPs)
- Service (e.g., tcp/80, any)
- Source Address(es)
- Destination Address(es)
The Source and Destination Zones specified here are based on the routing lookup for the original (pre-NAT) source and destination IP addresses. -
Translated Packet Tab:
Defines how the matched packet's addresses/ports should be translated upon egress. Key settings include:
- Source Address Translation: Specifies the type (None, Dynamic IP and Port, Dynamic IP, Static IP) and the translated IP address(es) (Interface IP, specific address objects/pools).
- Destination Address Translation: Specifies the type (typically Static IP for DNAT) and the translated IP address and optional port.
- Bi-directional Option (for Static Source NAT)
Rule Ordering
NAT rules are processed sequentially from top to bottom . The firewall applies the first rule that matches the packet and stops processing further NAT rules for that session.
Packet Processing Flow and NAT
Understanding where NAT fits into the overall PAN-OS packet flow is critical for both configuration and troubleshooting. Here's a simplified view relevant to NAT:
- Ingress: Packet arrives at an ingress interface. Basic validation occurs. The source zone is determined based on the ingress interface.
-
Session Setup (Slow Path - First Packet):
- Forwarding Lookup (Route Lookup): The firewall performs a route lookup based on the original destination IP address to determine the egress interface and initial destination zone.
-
NAT Policy Lookup:
The firewall evaluates the NAT policy rules (top-down) based on the original packet's source zone, destination zone (determined in the previous step), source/destination IPs, etc.
-
If a matching NAT rule is found:
- Destination NAT Check: If the rule involves Destination NAT, the firewall performs a *second* route lookup based on the translated (post-NAT) destination IP address . This second lookup determines the *final* destination zone used for the Security Policy evaluation.
- Source NAT Check: If the rule involves Source NAT, the firewall checks for resource availability (e.g., IPs/ports in the pool) but doesn't apply the translation yet.
- If no NAT rule matches, processing continues without planned translation.
-
If a matching NAT rule is found:
-
Security Policy Lookup:
The firewall evaluates Security Policy rules (top-down). Crucially, this lookup uses:
- Original (Pre-NAT) Source and Destination IP addresses.
- Source Zone (from ingress interface).
- Final (Post-NAT) Destination Zone (determined after route lookups, considering potential DNAT).
- Session Allocation: If allowed by Security Policy, a session is created in the session table, including the NAT translation details if applicable.
- Fast Path (Subsequent Packets): Packets belonging to an existing session bypass the lookups in the slow path and are processed based on the established session state.
- Forwarding/Egress: As the packet leaves the firewall via the egress interface, the actual NAT translation (changing IP addresses/ports in the packet header) is performed if specified in the matched NAT rule during session setup.
Interaction with Security Policies
The interplay between NAT and Security policies is a frequent source of confusion and a common topic in PCNSE exam questions. Remember these critical points:
- Security Policy Allows Traffic First: For NAT to even be considered or applied, the underlying traffic flow must first be permitted by a Security Policy rule. NAT rules do not allow traffic; they only translate addresses/ports for traffic that is already allowed.
-
Security Policy Matching Criteria:
- Addresses: Security policy rules ALWAYS match against the original (pre-NAT) source and destination IP addresses.
-
Zones:
- The Source Zone is always the zone of the ingress interface where the packet arrived.
- The Destination Zone is the zone determined *after* the route lookups, including the second lookup performed if Destination NAT is applied. Therefore, the Security Policy uses the post-NAT destination zone .
Example: Destination NAT for Web Server
- Internal Web Server: 192.168.10.100 (DMZ Zone)
- Public IP for Server: 203.0.113.50 (Untrust Zone interface IP)
- External Client: Any IP (Untrust Zone)
Configuration Steps:
-
DNAT Rule:
- Original Packet: Source Zone: Untrust, Dest Zone: Untrust, Dest IP: 203.0.113.50
- Translated Packet: Dest Translation IP: 192.168.10.100
Note: The NAT rule destination zone is 'Untrust' because the *original* destination IP (203.0.113.50) is routed via the Untrust interface/zone. -
Security Policy Rule:
- Source Zone: Untrust
- Source Address: Any
- Destination Zone: DMZ (This is the Post-NAT zone, where 192.168.10.100 resides)
- Destination Address: 203.0.113.50 (This is the Pre-NAT IP the client targets)
- Application/Service: http, https
- Action: Allow
Note: The Security rule destination zone is 'DMZ' (Post-NAT), but the destination address is '203.0.113.50' (Pre-NAT).
NAT Best Practices
Following best practices ensures efficient, manageable, and secure NAT configurations:
- Use Specific Rules: Avoid overly broad NAT rules. Match on specific zones, addresses, and services whenever possible.
- Rule Ordering: Place more specific rules (e.g., No NAT, Static NAT) before general rules (e.g., DIPP for general internet access).
- Address Objects: Use descriptive Address Objects and Address Groups for original and translated addresses. Consider a naming convention (e.g., `NAT_Pool_Web`, `Server_Private_IP`) to easily identify objects used in NAT policies.
- Minimize Unused Rules: Regularly audit and remove NAT rules that are no longer needed to simplify the rulebase and reduce potential conflicts.
- Use DIPP Intelligently: Use DIPP with interface address for simple outbound access. Use DIPP with address pools when you need more control, scalability, or specific source IPs.
- Consider Oversubscription Needs: Adjust the global DIPP oversubscription rate based on your environment's needs and firewall resources. Don't leave it at the maximum if not required.
- IPv6 Preference: For IPv6-to-IPv6 scenarios requiring prefix mapping, prefer NPTv6 over NAT64 where possible to maintain better end-to-end transparency.
- Logging and Monitoring: Ensure appropriate logging is enabled for NAT rules (usually via the corresponding Security Policy rules) to aid troubleshooting. Monitor NAT resource utilization (e.g., pool usage, session limits).
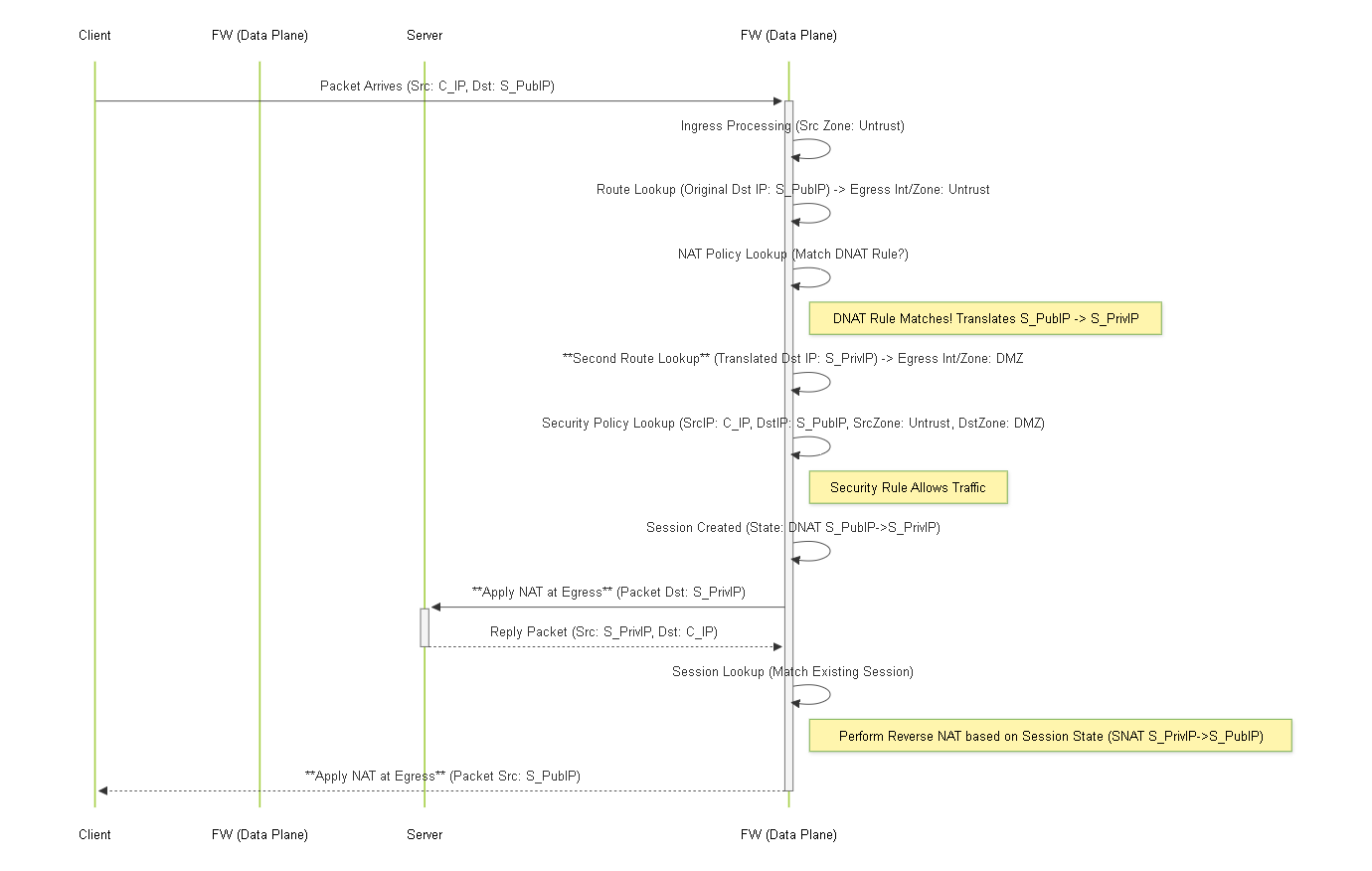
Sequence diagram illustrating packet flow, highlighting NAT evaluation, the second route lookup for DNAT, security policy evaluation using pre-NAT IPs/post-NAT zone, and NAT application at egress.
Diagram: Simplified NAT Type Decision Flowchart
This flowchart outlines basic logic for choosing a NAT type.
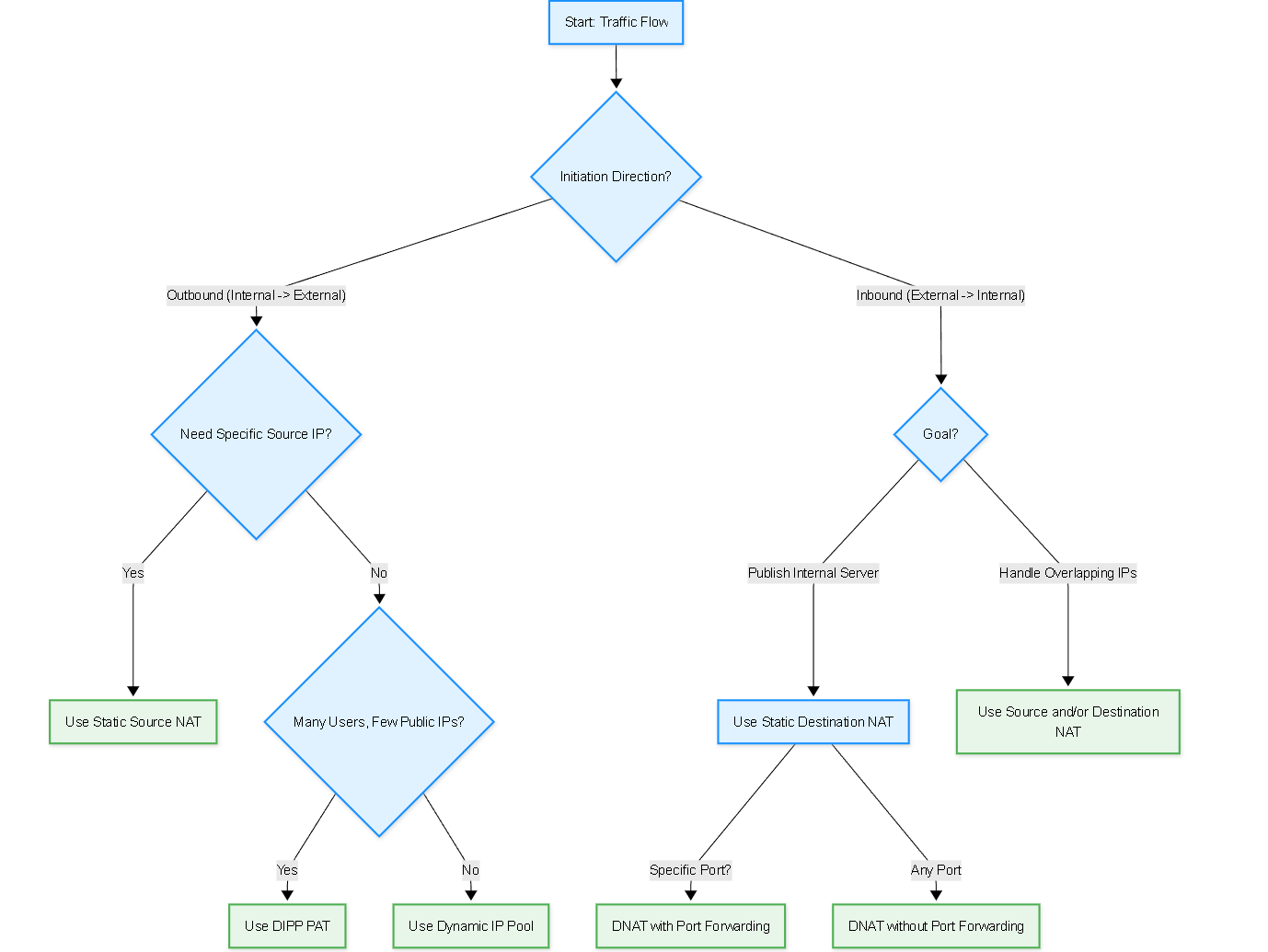
Simplified flowchart for selecting an appropriate NAT type based on traffic direction and requirements.
Diagram: NAT Session State
Illustrates possible states related to NAT during session setup.
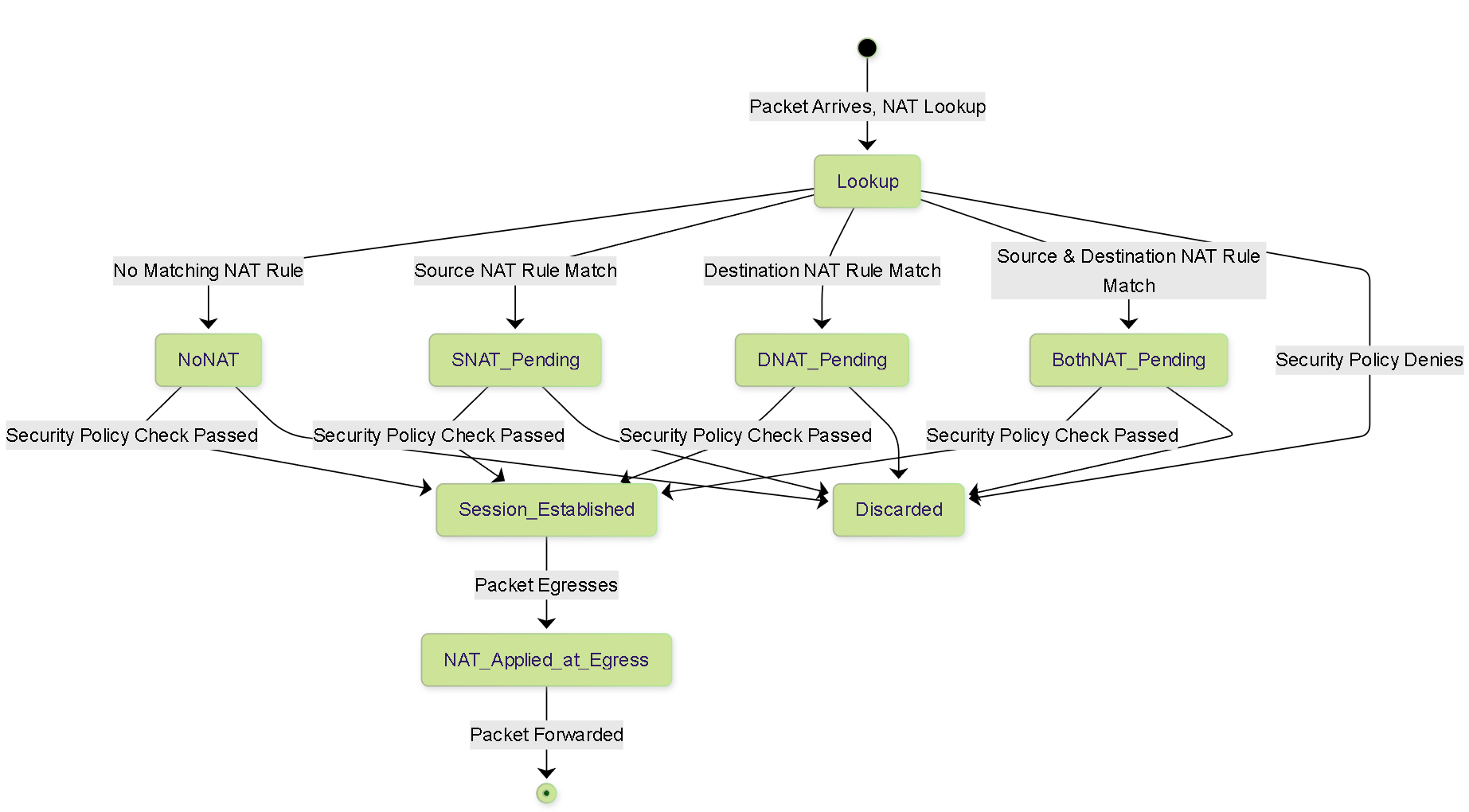
State diagram showing simplified NAT states during session establishment and application at egress.
Diagram: NAT Relationship Graph (DIPP Example)
Visualizes multiple internal clients sharing a single public IP via DIPP NAT.
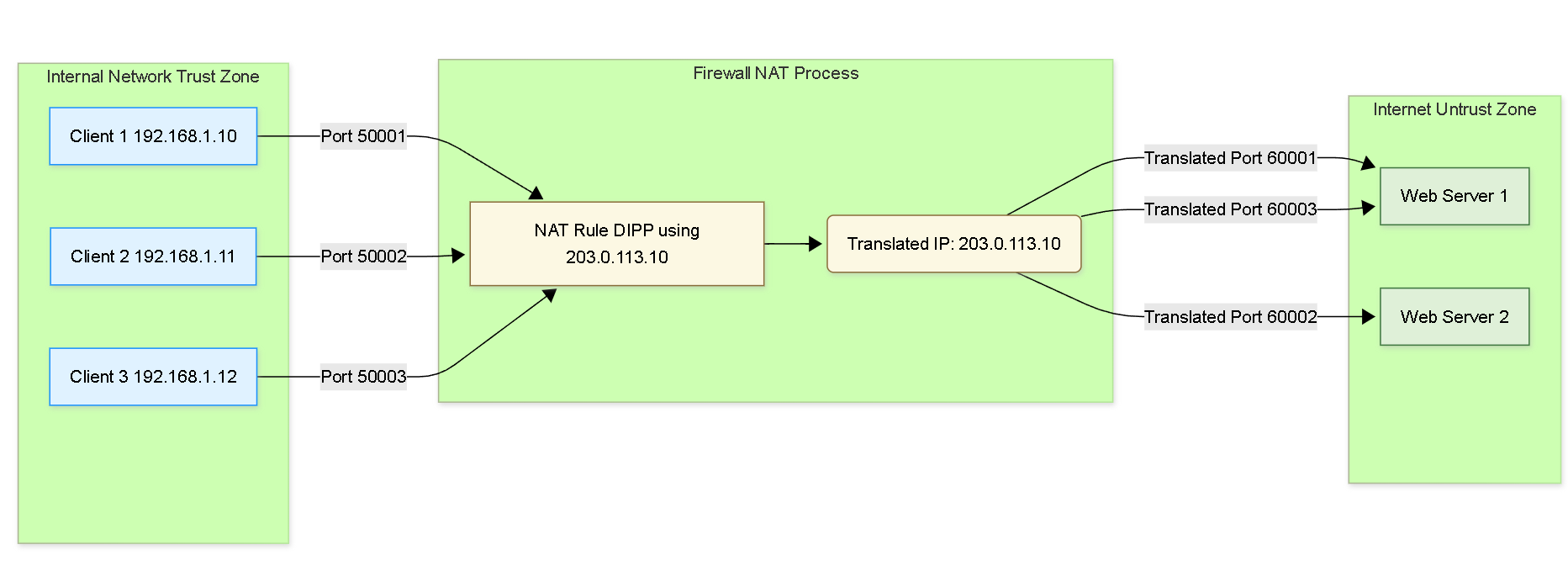
Graph showing multiple internal clients being translated to a single public IP using different source ports (DIPP/PAT).
PCNSE Exam Focus Summary for NAT
Based on the PCNSE objectives and common discussion points, focus on these NAT areas for the exam:
- Packet Flow & Policy Interaction: This is paramount. Understand precisely when NAT is evaluated vs. applied and how Security Policies use pre-NAT IPs and post-NAT zones.
- NAT Types: Differentiate Source NAT (DIPP, Dynamic IP, Static) and Destination NAT (Static, Port Forwarding). Know their primary use cases.
- Rule Configuration: Understand the components of a NAT rule (Original/Translated Packet tabs) and the significance of Source/Destination Zones, Addresses, and Service fields.
- Rule Ordering: Know that NAT rules are processed top-down, first match wins, and specific rules must precede general rules.
- DIPP Oversubscription: Understand the concept, purpose (port exhaustion mitigation), configuration location (Device > Setup > Session), and implications (scalability vs. resources).
- Translated IP Limit: Remember the 256 translated IP address limit per NAT rule and its implications for large pools.
- IPv6 NAT: Be aware of NAT64 and NPTv6 and their purposes in IPv6 environments.
- U-Turn NAT: Understand the concept and the need for potentially both DNAT and SNAT rules to make it work correctly.
- Troubleshooting: While less direct, understanding the flow helps troubleshoot NAT issues (e.g., checking session table, logs, `test nat-policy-match` CLI command).
Potential PCNSE Questions (Based on Web Findings)
Based on online discussions, practice exams, and study guides, here are examples of the *types* of questions you might encounter related to NAT:
- An administrator configures a Destination NAT rule to translate public IP 203.0.113.10 (Untrust Zone) to internal server 10.1.1.50 (DMZ Zone). What should the Destination Zone and Destination Address be in the corresponding Security Policy rule allowing external users (Untrust Zone) access? (Hint: Pre-NAT IP, Post-NAT Zone).
- Which type of Source NAT allows multiple internal clients to share a single translated IP address by modifying the source port? (Hint: DIPP).
- An administrator needs to ensure server 192.168.5.10 is *never* subject to source NAT, while all other hosts in the 192.168.5.0/24 network use DIPP NAT for internet access. How should the NAT rules be ordered? (Hint: Specific "No NAT" rule first).
- Where in the PAN-OS GUI is the DIPP NAT Oversubscription rate configured? (Hint: Device > Setup > Session).
- A firewall is configured with DIPP NAT using the egress interface IP address. Users report intermittent connection failures during peak hours. What is a likely cause? (Hint: Port Exhaustion).
- Which NAT type provides a stateless 1:1 mapping between IPv6 prefixes, preserving the host identifier? (Hint: NPTv6).
- When does the actual modification of IP addresses and ports occur for a packet matching a NAT rule? (Hint: At egress).
- What is the maximum number of translated IP addresses that can be configured within a single NAT rule's translated address pool? (Hint: 256).
- An internal user (10.10.10.5) needs to access an internal web server (10.20.20.5) using its public IP address (203.0.113.20). What type of NAT configuration is required? (Hint: U-Turn NAT, likely needing DNAT and maybe SNAT).
- True or False: A NAT policy rule itself can permit or deny traffic flow through the firewall. (Hint: False, Security Policy does this).
Focus on the interaction between NAT rules and Security rules, the specific use cases for each NAT type, and key configuration parameters like Oversubscription.
PCNSE Style Quiz: PAN-OS NAT
Test your understanding with these 20 questions: