PAN-OS NAT64 Explained (PCNSE Focus)
As networks increasingly adopt IPv6, the need for interoperability between IPv6-only segments and the vast number of remaining IPv4-only resources becomes critical. NAT64, often paired with DNS64, provides a vital translation mechanism to bridge this gap. Understanding NAT64 principles, configuration, and its interaction with security policies on Palo Alto Networks firewalls is an important topic for the PCNSE exam.
This article provides a comprehensive explanation of NAT64 on PAN-OS, focusing on the concepts and details relevant for PCNSE preparation, including configuration steps, traffic flow, and security considerations.
What is NAT64?
NAT64 is a stateful Network Address and Protocol Translation technology, primarily defined in RFC 6146, designed to allow IPv6-only clients to initiate connections to IPv4-only servers . It acts as a gateway between IPv6 and IPv4 networks.
Key functions include:
- Address Translation (IPv6 -> IPv4): Translates the client's IPv6 source address to an IPv4 source address (from the firewall's pool/interface). It also translates the specially formatted IPv6 destination address (containing the embedded IPv4 address) back to the actual IPv4 destination address.
- Address Translation (IPv4 -> IPv6): Translates the server's IPv4 source address back into the synthesized IPv6 format and translates the firewall's IPv4 destination address (the one used for SNAT) back to the original client's IPv6 address for return traffic.
- Protocol Translation: Handles necessary header conversions between IPv6 and IPv4.
- State Maintenance: Keeps track of active sessions to correctly translate return traffic.
- Port Translation (NAPT64): Typically, NAT64 implementations also perform port translation (Network Address Port Translation 64), allowing multiple IPv6 clients to share a single (or few) IPv4 addresses for the source translation, similar to standard IPv4 PAT/DIPP.
Essentially, NAT64 makes IPv4-only servers appear as if they have IPv6 addresses to the IPv6-only clients.
How NAT64 Works (Typically with DNS64)
While NAT64 handles the IP-level translation, clients need a way to discover the "IPv6 address" of an IPv4-only server. This is where DNS64 (RFC 6147) usually comes in.
Here's the typical process:
- Client DNS Query: An IPv6-only client wants to reach `www.ipv4-server.com`. It sends a DNS query for an AAAA (IPv6) record to its configured DNS server, which is often a DNS64 server.
-
DNS64 Server Action:
- The DNS64 server first attempts to resolve the AAAA record directly.
- If no AAAA record exists, it queries for an A (IPv4) record (e.g., finds `198.51.100.10`).
- The DNS64 server synthesizes an AAAA record by embedding the received IPv4 address (`198.51.100.10`) into a predefined NAT64 prefix.
-
NAT64 Prefix:
This is a specific IPv6 prefix designated for NAT64 synthesis. The well-known prefix (WKP) is
64:ff9b::/96, but network-specific prefixes (NSPs) can also be used. -
Synthesized Address Example (using WKP):
64:ff9b::198.51.100.10(often written in hex as64:ff9b::c633:640a).
-
DNS Response to Client:
The DNS64 server returns the synthesized AAAA record (
64:ff9b::c633:640a) to the IPv6 client. -
Client Initiates Connection:
The client, unaware it's a synthesized address, initiates an IPv6 connection towards
64:ff9b::c633:640a. - Routing to NAT64 Gateway: The network routes traffic destined for the NAT64 prefix towards the NAT64 gateway (the Palo Alto Networks firewall).
- NAT64 Gateway Translation: The firewall receives the IPv6 packet, identifies it as NAT64 traffic based on the destination address matching the configured NAT64 prefix, and performs the translation (details in the next section).
PAN-OS NAT64 Configuration Details
Configuring NAT64 on a Palo Alto Networks firewall involves creating a specific type of NAT rule under
Policies > NAT
.
- Create NAT Rule: Click "Add".
-
General Tab:
- Rule Name: Descriptive name (e.g., `NAT64_Internal_to_Internet`).
-
NAT Type: Select
nat64from the dropdown. - Ensure the rule is Enabled.
-
Original Packet Tab:
Defines the IPv6 traffic entering the firewall that needs translation.
- Source Zone: The zone containing the IPv6-only clients (e.g., `Zone_IPv6_Clients`).
- Destination Zone: The zone towards which the translated IPv4 traffic will be routed (usually the zone holding the default IPv4 route, e.g., `Zone_Untrust_IPv4`).
- Source Address: Typically `any` or a specific IPv6 prefix for your internal clients.
- Destination Address: Crucially, set this to the NAT64 Prefix (e.g., `64:ff9b::/96` or your configured Network-Specific Prefix). This is how the firewall identifies traffic requiring NAT64 processing.
- Service: Usually `any`, or specific services if needed.
-
Translated Packet Tab:
Defines how the source address is translated to IPv4.
-
Source Address Translation:
-
Type: Most commonly
Dynamic IP and Port(for NAPT64). -
Address Type: Choose either
Interface Address(select the firewall's IPv4 interface in the destination zone) orTranslated Address(select an Address Object representing an IPv4 pool). - Interface: Required if using Interface Address.
-
Type: Most commonly
-
Destination Address Translation:
-
Type:
None. - Important: Do NOT configure destination translation here. The firewall automatically extracts the destination IPv4 address from the original IPv6 destination based on the NAT64 prefix matched in the Original Packet tab.
-
Type:
-
Source Address Translation:
- Click OK and Commit.
NAT64 Traffic Flow Example
Let's trace a packet using the following details:
-
IPv6 Client:
2001:db8:10:1::100(Zone: IPv6_Trust) -
NAT64 Prefix:
64:ff9b::/96 -
IPv4 Server:
198.51.100.50(Zone: IPv4_Untrust) -
Firewall IPv4 SNAT Address:
203.0.113.10(Firewall's IPv4_Untrust interface IP)
Forward Path (Client -> Server)
-
Client sends packet:
-
Source IP:
2001:db8:10:1::100 -
Destination IP:
64:ff9b::198.51.100.50(Synthesized by DNS64)
-
Source IP:
- Firewall receives packet on IPv6_Trust interface.
- NAT rule lookup matches NAT64 rule (Original Dst Addr = 64:ff9b::/96).
- Security Policy lookup (Details next section).
- Firewall prepares to forward packet out IPv4_Untrust interface.
-
NAT64 Applied at Egress:
-
Original Source
2001:db8:10:1::100translated to203.0.113.10(plus a source port). -
Original Destination
64:ff9b::198.51.100.50translated to198.51.100.50(IPv4 extracted).
-
Original Source
-
Firewall sends packet:
-
Source IP:
203.0.113.10(and translated port) -
Destination IP:
198.51.100.50
-
Source IP:
Return Path (Server -> Client)
-
Server sends reply packet:
-
Source IP:
198.51.100.50 -
Destination IP:
203.0.113.10(Firewall's SNAT IP)
-
Source IP:
- Firewall receives packet on IPv4_Untrust interface.
- Firewall performs session lookup and finds the existing NAT64 session state.
- Security Policy lookup for return traffic.
- Firewall prepares to forward packet out IPv6_Trust interface.
-
Reverse NAT64 Applied at Egress:
-
Original Source
198.51.100.50translated back to64:ff9b::198.51.100.50. -
Original Destination
203.0.113.10(and port) translated back to2001:db8:10:1::100(and original port).
-
Original Source
-
Firewall sends packet:
-
Source IP:
64:ff9b::198.51.100.50 -
Destination IP:
2001:db8:10:1::100
-
Source IP:
NAT64 Interaction with Security Policy
A common point of confusion is how to write the Security Policy rule to allow NAT64 traffic. As with all NAT, the Security Policy rule uses pre-NAT addresses but the final (post-NAT) destination zone .
For typical NAT64 (IPv6 client to IPv4 internet server):
- Source Zone: Zone where the IPv6 clients reside (e.g., `IPv6_Trust`).
- Source Address: `any` or the specific internal IPv6 client prefix.
- Destination Zone: Zone where the translated IPv4 servers reside (e.g., `IPv4_Untrust`). This is the zone determined *after* the NAT64 translation identifies the target IPv4 address and finds its route.
-
Destination Address:
This should match the NAT64 Prefix
used in the NAT rule (e.g.,
64:ff9b::/96). The security policy lookup happens *before* the final IPv4 address is extracted for egress, but *after* the firewall has identified the traffic as belonging to the NAT64 prefix based on the initial destination address lookup. - Application/Service: Define as required (e.g., `any`, `web-browsing`).
- Action: `Allow`.
Example Security Rule for NAT64
Given:
- IPv6 Client Zone: `Internal_v6`
- IPv4 Server Zone: `Internet_v4`
- NAT64 Prefix Used: `64:ff9b::/96`
Security Rule Configuration:
- Name: `Allow_NAT64_Outbound`
- Source Zone: `Internal_v6`
- Source Address: `any` (or specific IPv6 subnet)
- Destination Zone: `Internet_v4`
- Destination Address: `64:ff9b::/96` (Create an Address Object for this prefix)
- Application: `any`
- Service: `any`
- Action: `Allow`
Diagram: Sequence - DNS64 & NAT64 Interaction
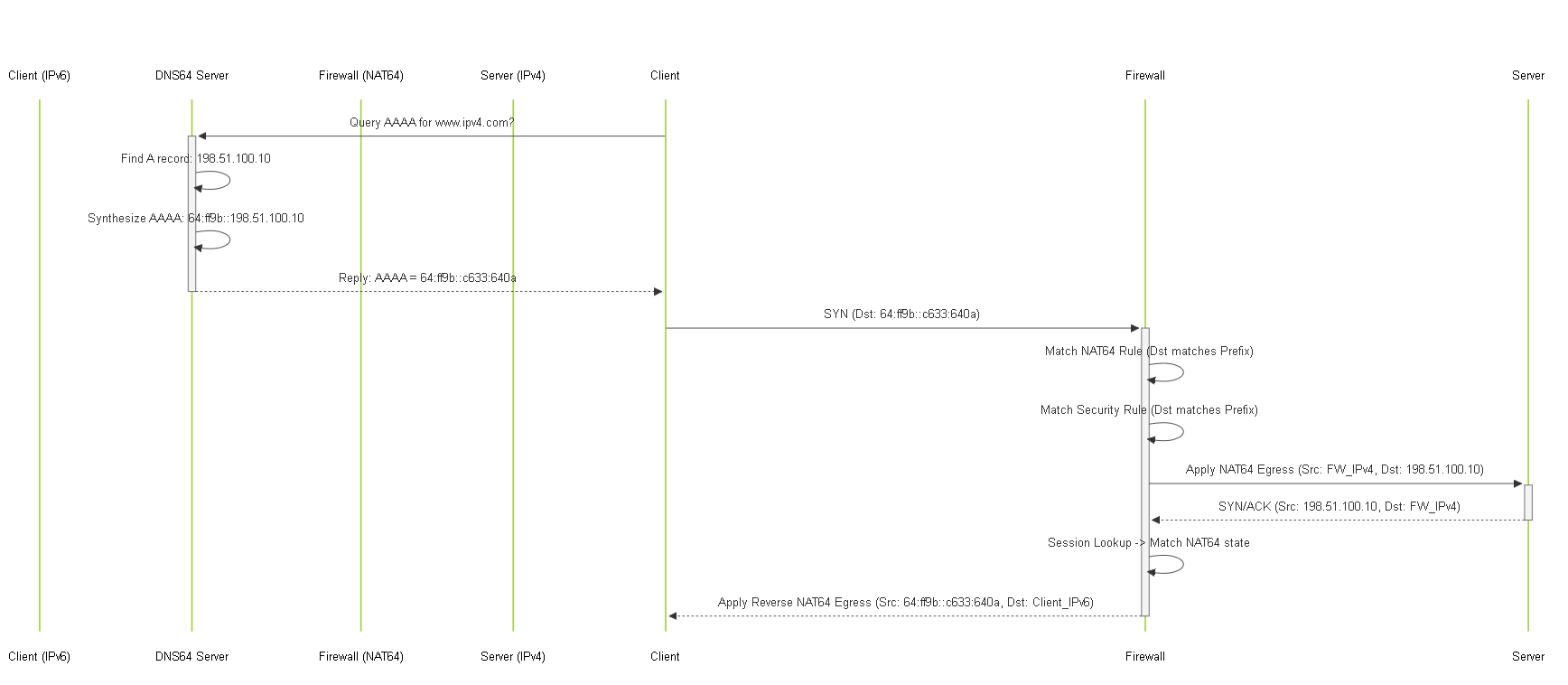
Sequence diagram showing the combined flow involving DNS64 for discovery and NAT64 for translation.
Diagram: Flowchart - Simplified NAT64 Process
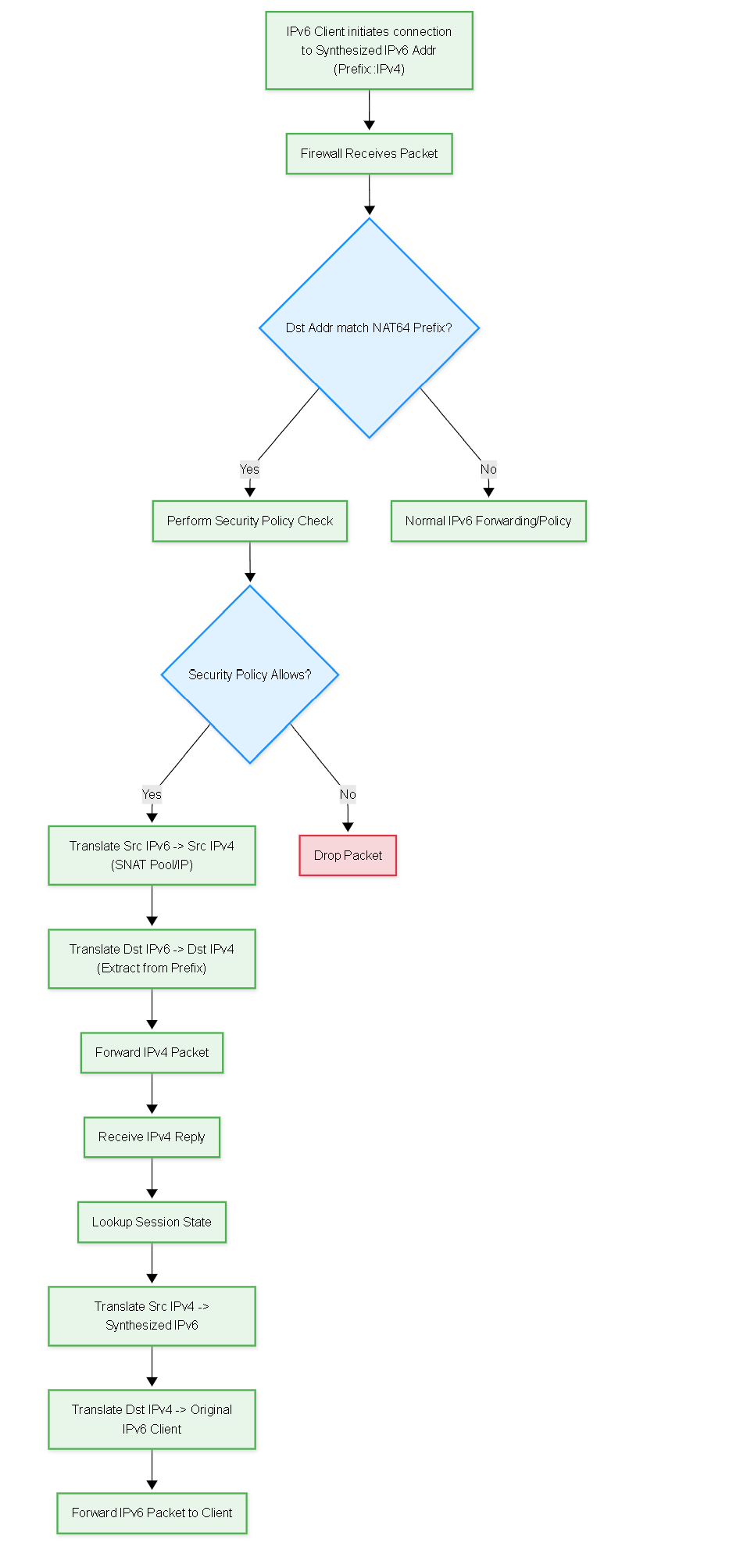
Simplified flowchart outlining the key steps in the NAT64 translation process on the firewall.
Diagram: Graph - NAT64 IP Address Relationships
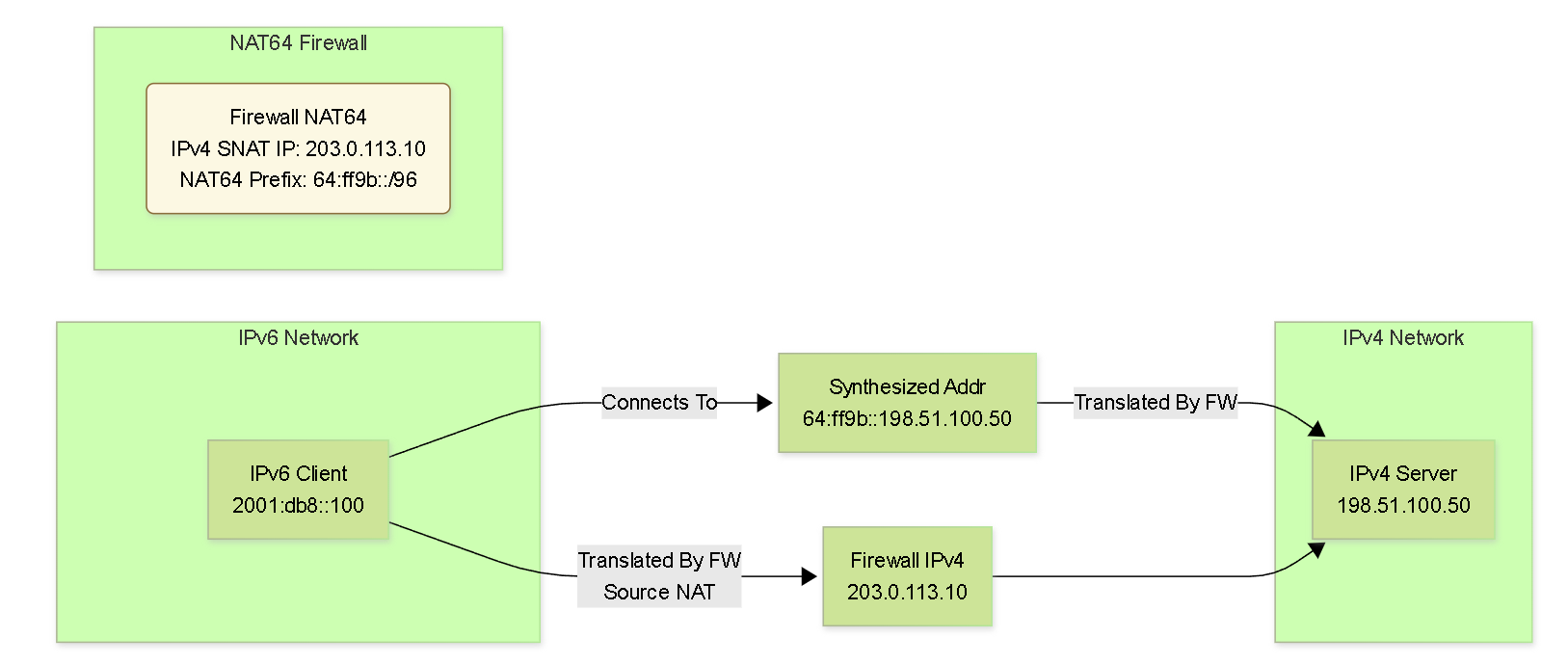
Graph showing the relationship between the original IPs, the synthesized address, and the translated IPs during NAT64.
PCNSE Exam Focus Summary (NAT64)
For the PCNSE exam, concentrate on these NAT64 aspects:
- Purpose: Understand NAT64 as an IPv6 transition mechanism enabling IPv6-only clients to reach IPv4-only servers.
-
DNS64 Role:
Know that DNS64 works with NAT64 to synthesize AAAA records from A records using a NAT64 prefix (e.g., the well-known
64:ff9b::/96). -
PAN-OS Configuration:
- NAT Rule Type: Must be set to `nat64`.
- Original Packet Destination Address: Must match the NAT64 Prefix being used.
- Translated Packet Destination Address: Must be `None`.
- Translated Packet Source Address: Configure DIPP (usually) using an IPv4 interface IP or pool.
- Traffic Flow: Understand the translation process - IPv6 source to IPv4 source, synthesized IPv6 destination to actual IPv4 destination, and the reverse for reply traffic.
- Security Policy Interaction: This is critical. The Security Policy rule allowing NAT64 traffic matches on the original (pre-NAT) source IPv6 address and the NAT64 Prefix as the destination address, with the destination zone being the zone of the actual IPv4 server.
- Distinction from NPTv6: Recognize that NAT64 is stateful v6-to-v4 translation, while NPTv6 is stateless v6-to-v6 prefix translation.
PCNSE Style Quiz: NAT64
Test your understanding with these 20 questions focused on NAT64: