Understanding NAT & DNS Interaction on Palo Alto Networks Firewalls (PCNSE Focus)
Network Address Translation (NAT) is fundamental for connecting private networks to the public internet and publishing internal services. However, the interplay between NAT and the Domain Name System (DNS) can create specific challenges, particularly the "split-DNS" problem where internal and external users need different IP address resolutions for the same Fully Qualified Domain Name (FQDN). Palo Alto Networks firewalls offer features like DNS Proxy and NAT Rule DNS Rewrite to address these challenges.
Mastering how these features work, when to use them, and how they interact with NAT and Security policies is crucial for effective firewall administration and for success on the PCNSE exam. This article provides a detailed explanation focused on these interactions.
The Problem: Internal Access via Public FQDN
Consider this common setup:
-
An internal web server hosts `www.mycorp.com` at private IP
10.1.1.100(DMZ Zone). -
A Destination NAT (DNAT) rule on the firewall translates incoming traffic to public IP
203.0.113.50(Untrust Zone) to the internal server10.1.1.100. -
The public DNS record for `www.mycorp.com` correctly points to the public IP
203.0.113.50.
The Challenge:
What happens when an internal user (e.g.,
192.168.1.20
in the Trust Zone) tries to browse to `www.mycorp.com`?
-
DNS Resolution:
The internal client queries its configured DNS server.
-
If using an
external DNS server
(e.g., 8.8.8.8), it receives the public IP
203.0.113.50. -
If using an
internal DNS server
that only holds the public record, it also receives the public IP
203.0.113.50.
-
If using an
external DNS server
(e.g., 8.8.8.8), it receives the public IP
-
Connection Attempt:
The client initiates a connection towards the public IP
203.0.113.50. - Firewall Handling: The traffic goes from the Trust zone towards the Untrust zone (based on the route to the public IP). The firewall must now handle this "hairpin" or "U-turn" traffic.
-
U-Turn NAT Requirement:
To make this work, a potentially complex U-Turn NAT configuration is often needed, involving:
- A DNAT rule to translate the public destination back to the private server IP.
- An SNAT rule (often required if client/server are in the same zone) to make the traffic appear to originate from the firewall itself, ensuring return traffic flows correctly.
This U-Turn approach works but adds complexity to NAT policy and can be less efficient as traffic must loop back through the firewall.
Solution: DNS Proxy for Split-DNS
The Palo Alto Networks firewall's DNS Proxy feature provides an elegant solution to the split-DNS problem, often eliminating the need for U-Turn NAT for internal access scenarios.
When configured:
- The firewall acts as an intermediary DNS server for specific internal clients/zones.
- It can intercept DNS queries sent to its own interface IP.
- Based on configured rules and static entries, it can provide different responses to internal clients than what external clients would receive.
- Queries for internal resources can be answered directly by the firewall with the resource's private IP address.
- Queries for external resources can be forwarded by the proxy to actual external DNS servers.
How DNS Proxy Solves the Split-DNS Problem
Using the previous example (`www.mycorp.com` = Public
203.0.113.50
/ Private
10.1.1.100
):
-
Client Configuration:
Internal client
192.168.1.20(Trust Zone) is configured to use the firewall's Trust interface IP (e.g.,192.168.1.1) as its DNS server. - Firewall DNS Proxy Config: A DNS Proxy Object is configured with a Static Entry mapping `www.mycorp.com` to the private IP `10.1.1.100`. This object is applied via a DNS Proxy Rule for traffic from the Trust zone destined for the firewall's IP (`192.168.1.1`).
-
Client DNS Query:
Client sends DNS query for `www.mycorp.com` to
192.168.1.1. - DNS Proxy Rule Match: The firewall's DNS Proxy Rule matches the incoming DNS query.
- Static Entry Lookup: The DNS Proxy Object finds the static entry for `www.mycorp.com`.
-
DNS Proxy Reply:
The firewall
directly replies
to the client with the private IP
10.1.1.100. -
Client Connection:
The client now initiates its connection directly towards the private IP
10.1.1.100. - Result: Traffic flows directly from the Trust zone towards the DMZ zone (where the server resides). No U-Turn NAT is required for this internal access, simplifying NAT and security policies.
DNS Proxy Configuration Overview
Implementing DNS Proxy involves two main components:
-
DNS Proxy Object (
Objects > DNS Proxy):- Name: A descriptive name (e.g., `Internal_DNS_Proxy`).
- Interfaces/IP Addresses: Specify the firewall interface(s) and IP address(es) that will listen for DNS queries from clients. Typically, this is the Layer 3 interface IP address facing the internal clients.
-
DNS Proxy Rules (within the Object):
Define domains to handle.
- Static Entries: Map specific FQDNs to their internal private IP addresses (e.g., `www.mycorp.com` -> `10.1.1.100`). This is the core of split-DNS.
- Domain Forwarding: Define rules to forward queries for other domains (e.g., `*.google.com`, `*.*` for everything else) to specific external DNS servers (Primary/Secondary).
- Cache Settings: Configure DNS caching options (optional).
-
DNS Proxy Policy Rule (
Policies > DNS Proxy):- Name: A descriptive name (e.g., `Allow_Trust_to_DNS_Proxy`).
- Source Zones/Addresses: Specify the internal zones/subnets whose clients will use this DNS Proxy (e.g., Source Zone: `Trust`).
- Destination Interface/Address: Must match the interface/IP configured in the DNS Proxy Object where the firewall is listening for queries.
- Action: Select the DNS Proxy Object configured in step 1.
DNS Proxy Interaction with Security Policy
When DNS Proxy is used effectively for split-DNS, it simplifies Security Policy configuration for internal access to internal resources.
-
DNS Traffic Policy:
You need a Security Policy rule to allow the internal clients to send DNS queries (UDP/53, potentially TCP/53)
to the firewall interface IP
acting as the DNS Proxy server.
- Source Zone: e.g., `Trust`
- Source Address: e.g., `Trust_Subnet`
- Destination Zone: The zone containing the firewall interface acting as DNS server (e.g., `Trust` if the interface is in that zone).
- Destination Address: The firewall interface IP address configured in the DNS Proxy Object.
- Service: `service-dns` (or udp/53, tcp/53)
- Action: `Allow`
-
Data Traffic Policy:
Since the client now connects directly to the server's
private IP
, the Security Policy rule allows this direct inter-zone or intra-zone traffic.
- Source Zone: e.g., `Trust`
- Source Address: e.g., `Trust_Subnet`
- Destination Zone: e.g., `DMZ` (Server's actual zone)
- Destination Address: e.g., `10.1.1.100` (Server's private IP)
- Application/Service: e.g., `ssl`, `web-browsing`
- Action: `Allow`
This avoids the complexity of the U-Turn NAT Security Policy, which needs to match the public destination IP but the internal destination zone.
Alternative: NAT Rule DNS Rewrite Option
Separate from the DNS Proxy feature, individual NAT rules have a "DNS Rewrite" checkbox. This feature serves a different purpose than the primary split-DNS goal addressed by DNS Proxy.
NAT Rule DNS Rewrite inspects the payload of DNS responses that pass through the firewall *as part of the flow matching that specific NAT rule*. It modifies IP addresses found *within* the DNS response data (e.g., in A records, PTR records, TXT records) to be consistent with the address translation performed by that NAT rule itself.
Key Differences from DNS Proxy:
- Trigger: DNS Rewrite acts on DNS responses matching the specific NAT rule it's enabled on. DNS Proxy acts on DNS queries sent *to* the firewall interface configured as a proxy.
- Purpose: DNS Rewrite fixes inconsistencies *within DNS payloads* caused by NAT. DNS Proxy provides different DNS answers based on the querier's location (split-DNS).
- Configuration: DNS Rewrite is an option within a NAT rule. DNS Proxy uses separate Objects and Policies.
While DNS Rewrite *can* sometimes be manipulated to achieve a split-DNS-like effect, DNS Proxy is the dedicated and recommended feature for the standard split-DNS use case (internal clients getting internal IPs).
NAT Rule DNS Rewrite (Reverse)
Direction: Translates IPs in the DNS response payload from the Translated (External/Public) IP back to the Original (Internal/Private) IP defined in the NAT rule.
Primary Use Case: Used with Static Source NAT .
Scenario:
An internal server (
10.1.1.10
) has a Static SNAT rule mapping its source IP to public IP
203.0.113.10
for outbound connections. If this server queries something externally (e.g., performs a PTR lookup on
203.0.113.10
, or interacts with a service that reflects its public IP back in a DNS record), the DNS response packet coming back towards the server (destined for
203.0.113.10
before reverse NAT) might contain
203.0.113.10
within its data payload.
Action:
With DNS Rewrite (Reverse) enabled on the Static SNAT rule, as the firewall processes the return DNS response (destined for
10.1.1.10
after reverse DNAT of the destination), it inspects the payload. If it finds
203.0.113.10
, it rewrites it to
10.1.1.10
before delivering the packet to the internal server.
Configuration: Check "DNS Rewrite" and select "Reverse" in the Translated Packet tab of the Static Source NAT rule.
NAT Rule DNS Rewrite (Forward)
Direction: Translates IPs in the DNS response payload from the Original (Internal/Private) IP to the Translated (External/Public) IP defined in the NAT rule.
Primary Use Case: Used with Static Destination NAT , although less common than using DNS Proxy for the client-side resolution.
Scenario:
An internal authoritative DNS server (
10.2.2.20
) is published using DNAT (
203.0.113.20
->
10.2.2.20
). An external client queries this DNS server. The internal DNS server responds with an 'A' record containing the *private* IP of another internal server (e.g.,
10.1.1.100
). This private IP is useless to the external client.
Action:
Assume another DNAT rule exists mapping public
203.0.113.100
to private
10.1.1.100
. With DNS Rewrite (Forward) enabled on the *outbound* flow of the DNS response (often tied to the DNAT rule for the DNS server or a broader rule), the firewall inspects the payload. It finds
10.1.1.100
and rewrites it to its corresponding public IP
203.0.113.100
before sending the response to the external client.
Configuration: Check "DNS Rewrite" and select "Forward" in the Translated Packet tab of the relevant NAT rule (could be the DNAT for the DNS server or a related rule handling the response flow).
Choosing Between DNS Proxy and NAT DNS Rewrite
- For Split-DNS (Internal clients needing internal IPs for internal FQDNs): Use DNS Proxy . This is the dedicated feature. Configure clients to use the firewall as DNS server, create static entries in the DNS Proxy Object, and apply via DNS Proxy Policy.
- For fixing DNS payload IPs related to SNAT: Use NAT Rule DNS Rewrite (Reverse) on the relevant Static Source NAT rule.
- For fixing DNS payload IPs related to DNAT (less common): Use NAT Rule DNS Rewrite (Forward) on the relevant DNAT rule (or associated outbound rule), but consider if DNS Proxy for internal clients is a better overall approach.
Diagram: Sequence - DNS Proxy Flow (Split-DNS)
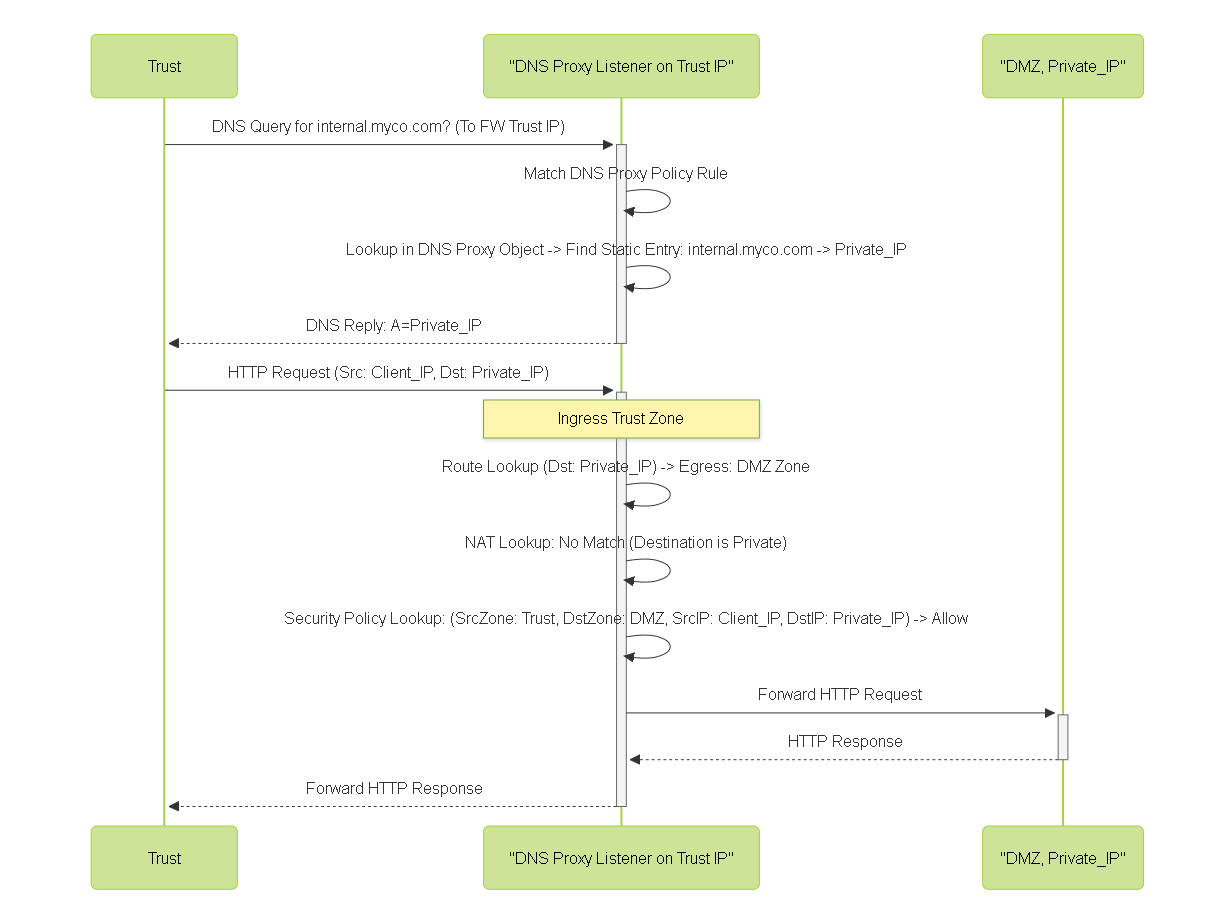
Sequence diagram illustrating how DNS Proxy intercepts a query to the firewall, uses a static entry to reply with the internal IP, and allows direct internal connection, avoiding U-Turn NAT.
Diagram: Sequence - NAT Rule DNS Rewrite (Reverse)
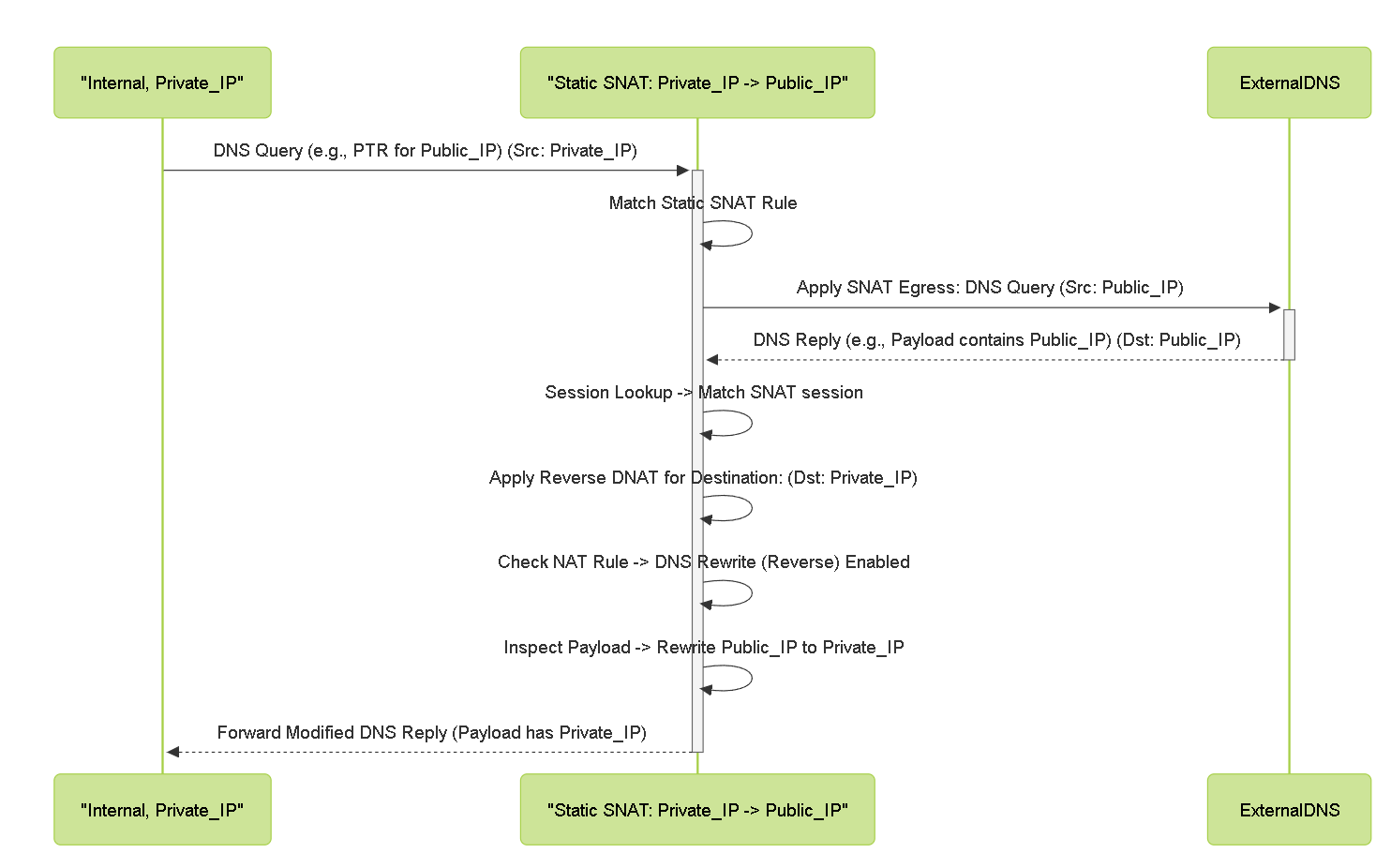
Sequence diagram showing DNS Rewrite (Reverse) modifying a DNS response payload containing the server's NAT'd public IP back to its private IP before delivery.
Diagram: Sequence - NAT Rule DNS Rewrite (Forward)
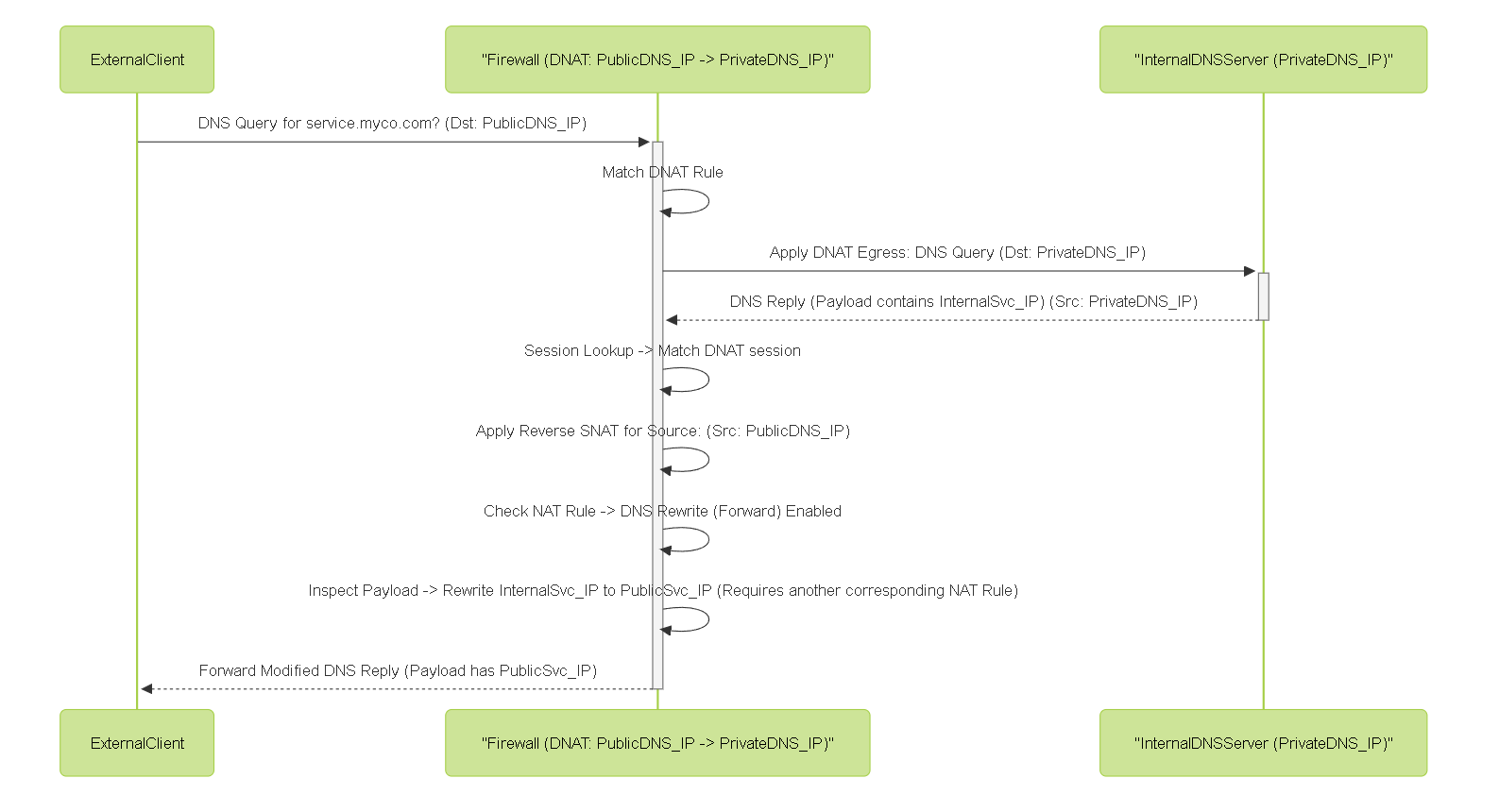
Sequence diagram illustrating DNS Rewrite (Forward) modifying a DNS response payload from an internal DNS server, changing an internal service IP to its public equivalent.
Diagram: Flowchart - DNS Proxy vs NAT DNS Rewrite
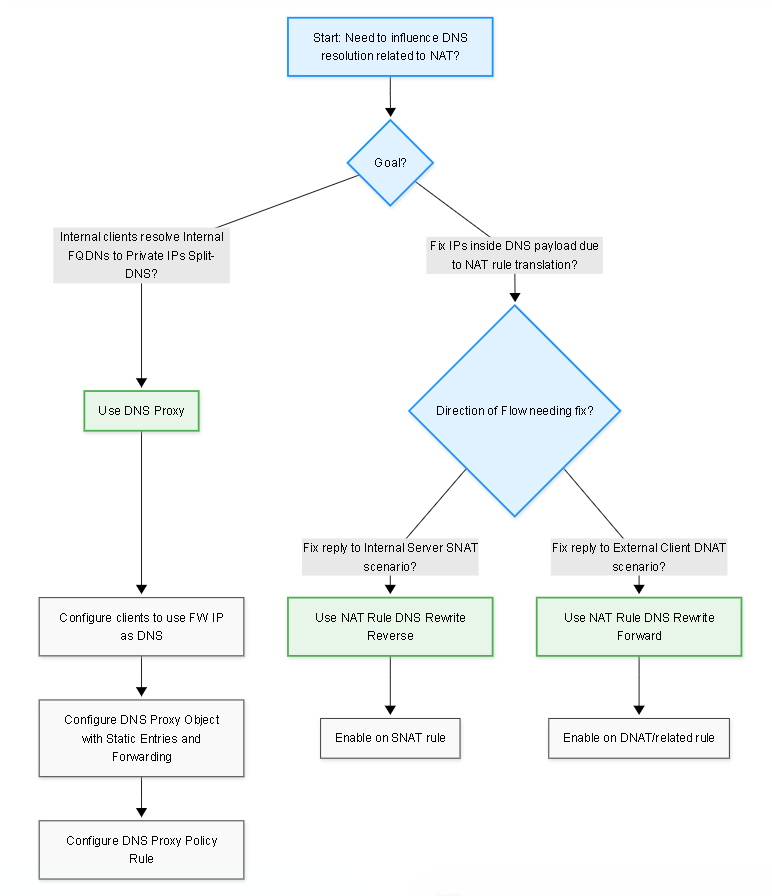
Flowchart guiding the choice between DNS Proxy and NAT Rule DNS Rewrite based on the problem being solved.
PCNSE Exam Focus Summary (NAT & DNS)
Key takeaways for the PCNSE exam regarding NAT and DNS interaction:
- Split-DNS Problem: Understand why internal clients resolving public FQDNs for internal resources can lead to issues requiring U-Turn NAT.
- DNS Proxy for Split-DNS: Know this is the primary solution. Understand its mechanism (intercepting queries to the firewall, using static entries). Know the configuration requirements (clients use firewall IP, DNS Proxy Object, DNS Proxy Policy).
- DNS Proxy Security Policy: Understand that the data traffic flows directly internal-to-internal, and the security policy must allow this based on private IPs and actual zones. Remember the policy needed to allow DNS queries *to* the proxy itself.
- NAT Rule DNS Rewrite: Understand its distinct purpose (modifying DNS response payloads to match NAT rule translations). Differentiate 'Reverse' (for SNAT) and 'Forward' (for DNAT) use cases. Know it's configured within the NAT rule itself.
- When to Use Which: Prioritize DNS Proxy for standard split-DNS. Use NAT Rule DNS Rewrite for fixing payload inconsistencies directly related to a NAT rule's translation.
- U-Turn NAT Awareness: Recognize scenarios where DNS Proxy/Rewrite is *not* used, meaning U-Turn NAT might still be required, and recall its configuration principles (DNAT, conditional SNAT, "Pre-NAT IP, Post-NAT Zone" Security Policy).
PCNSE Style Quiz: NAT & DNS Interaction
Test your understanding with these 20 questions focused on NAT, DNS Proxy, and DNS Rewrite: